Executive Summary
BACKGROUND
Aviation security is one of the most important issues confronting our society today. The disastrous hijackings of September 11, 2001, when four commercial aircraft were taken over and used as weapons, and the resulting loss of life and property damage eclipse the impact of all previous terrorist attacks against commercial aviation. The events also dramatically expand the boundaries of the kinds of action that might be employed against civil aviation. The need to ensure public safety and instill confidence will require deploying the very best airport security systems using the combinations of technology and personnel called for by the best intelligence available.
A key responsibility of the Federal Aviation Administration (FAA) and the Transportation Security Administration (TSA) is to guard our nation’s civil aviation system against terrorism and all other threats.1 Fulfillment of this responsibility is unquestionably difficult and complex. The balance among passenger safety, operational capability of existing technology, burden on commercial industries, and efficient utilization of both personnel and financial resources is very complex. Although this balance may change in the coming months and years, it is clear that the commercial aviation industry, the FAA, the TSA, and the U.S. Congress must continue to consider what constitutes a reasonable delay and cost to the passenger while ensuring that adequate security is in place.
As an example, hand searches of baggage have rarely been used because they are expensive and time-consuming. Instead, alternative technologies have been implemented, including x-ray scans of carry-on baggage and computed tomography of checked bags. All these methods remain subject to technology limitations as well as to procedural and operator error. This complexity leads to the need for a total systems approach to aviation security, whereby the individual screening and security components combine to create an overall security greater than that provided by the individual components.
Although an impervious defense against every threat is impossible to achieve, available security resources can be optimized using a systems approach. A system-of-systems architecture embraces the sequence and manner of deployment of various elements of aviation security technology described in Table ES-1. Figure ES-1 illustrates
the paths by which people, baggage, and equipment board a plane.2 This report considers only the aviation security systems listed in Table ES-1 and only some of the threat vectors illustrated in Figure ES-1 and focuses on bombs as the threat objects. The elements of an aviation security system include the following:
-
Those designed to identify or deter potential passenger threats, such as the computer-assisted passenger prescreening system (CAPPS) and positive passenger bag matching (PPBM);
-
Those designed to inspect passenger baggage, such as bulk explosives detection systems (EDSs)3 and explosives-detection equipment (EDE) that check the interior of a bag for explosives and trace explosive detection devices (TEDDs) that check for residual explosive material on the surface of an object being sampled; and
-
Those designed to contain an explosive blast inside an aircraft cargo hold, such as hardened unit loading devices (HULDs).
TABLE ES-1 Selected Aviation Security Equipment and Procedures
|
Technology |
Description |
|
CAPPS |
Computer-assisted passenger prescreening system utilizes a passenger’s reservation record and other databases to identify passengers who will receive further scrutiny. |
|
PPBM |
Positive passenger bag match is a security procedure that matches the passenger’s checked baggage with the passenger to ensure that baggage is not loaded aboard an airplane unless the passenger also boards. |
|
EDSs |
Explosives-detection systems are bulk explosive detection devices that have passed FAA certification tests. To date, these systems use x-ray computed tomography, mainly for the screening of selected checked baggage. |
|
EDD |
An explosives-detection device includes any bulk explosives detection equipment that meets certification for at least one of the FAA explosives. |
|
EDE |
Explosives-detection equipment includes any explosives-detection device or system that nonintrusively senses some physical or chemical property of an object under investigation to determine if it is an explosive. |
|
TEDDs |
Trace explosives detection devices collect particles or vapor to determine if trace explosives are present; they are used, when called for, to screen both carry-on and checked baggage. |
|
HULDs |
Hardened unit load devices are special containers for checked baggage that can contain the effects of an in-flight explosion involving an explosive mass of a given size or less. |
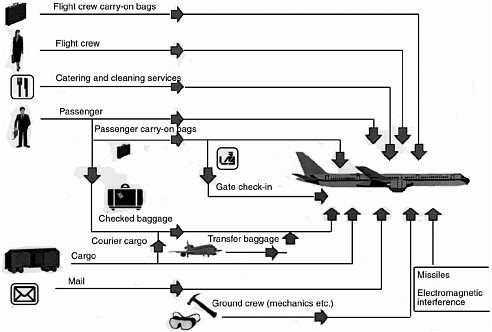
FIGURE ES-1 Threat vectors: the paths by which people, baggage, and equipment board a plane are also the paths by which threats may board a plane. Source: National Research Council. 1999. Assessment of Technologies Deployed to Improve Aviation Security, National Academy Press, Washington, D.C., p. 11.
THE COMMITTEE’S WORK AND FINDINGS
The committee issued its first report in 1999.4 This second report reviews the progress the FAA has made toward implementing the recommendations of that first report. The reader is referred to the first report for basic background material and more detailed information on the rationale for these recommendations. This second report also describes anticipated future committee work on assessment of technologies to improve aviation security.
Although progress is being made by the FAA to resolve the issues addressed in the 1999 recommendations, they are yet to be fully resolved. After reevaluation of the 1999 recommendations, the committee concluded that the recommendations made in its first report continue to have merit and that the FAA should commit adequate funding and personnel to the achievement of those goals. While the terrorist hijacking incidents of September 11, 2001, highlight the need to address new types of threat, the threats
considered by the FAA, which have been the focus of its work until now, continue to require attention. The committee’s recommendations from its 1999 report are summarized in Table ES-2, along with its assessment of progress in implementation of these recommendations.
A number of factors, primarily related to management and resources, have affected the rate of progress in the critical areas outlined in Table ES-2. The FAA has been responsive to the committee’s recommendations, but work is proceeding at a very slow pace in most areas. The complex array of participants in aviation security, including the FAA, the air carriers, the airports, and the passengers, complicates the ability of the FAA to set its own schedule. For example, a task such as deploying EDS in an airport requires coordination with the local airport teams, which might include the following participants:
-
Airport operators (airport authority, city government, state government) and the air carriers, to determine the best equipment placement for the flow of passengers;
-
Air carriers and third-party security companies, to train employees in use of the new equipment;
-
Local law enforcement to coordinate response to alarms from the new equipment, and
-
Local construction companies to construct space and install the new EDSs.
It is nearly impossible for the FAA to make a decision and schedule deployment of equipment without first getting the commitment of all the local participants. In the committee’s opinion, this difficulty of coordination has slowed the deployment effort.
Red-team testing of the CAPPS system needs to be more comprehensive. Testing against historical threats indicated that, once the criteria are understood, the CAPPS system can be effective. However, recent tragic events show that additional action must be taken to make CAPPS more effective in identifying passengers who should undergo additional screening before being allowed on the airplane. They also show that the procedures that follow identification by CAPPS may not be adequate to prevent such tragedies.
Equipment deployment has proceeded through the FAA’s Security Equipment Integrated Product Team (SEIPT), which selects vendors, purchases equipment, and provides coordination between the air carriers, airports, and local law enforcement agencies for installation of the equipment. In concert with the air carriers, SEIPT has instituted advanced planning to facilitate deployment of the security equipment. SEIPT has taken the initiative of bringing all stakeholders into its planning process and provides a good model for the other sectors to follow.
TABLE ES-2 Status of Implementation of Recommendations Made in the Committee’s First Report
|
Issue |
Recommendation |
Current Status |
|
Bulk explosives |
The FAA should measure true and false detection rates during certification testing, and the equipment should better assist operators to identify false alarms. |
True and false detection rates are measured during certification testing, but alarm resolution and frequency of false alarms need improvement. |
|
Trace explosives |
The FAA should develop and implement a program to evaluate the effectiveness of TEDDs. |
A dry transfer standard technique for several explosives has been developed. The same technology needs to be used to produce standards for daily machine setup. This would allow measurement of machine and operator effectiveness. |
|
Passenger screening |
Use of CAPPS and PPBM should continue, and their effectiveness should be tested. |
These systems are operational; however, red teama testing of the CAPPS system needs to be more comprehensive. |
|
Technology deployment |
Congress should continue to support deployment of aviation security detection systems. |
Funding has continued but deployment schedules have not been maintained. |
|
Operator effectiveness |
The FAA should ensure that the operator and detection system combination meets performance requirements. |
For radiographic x-ray equipment, but not all EDSs, the threat image projection system (TIPS) is being implemented and could be used to monitor performance, but TIPS data on individual operators are not currently being saved. |
|
Total architecture for aviation security (TAAS) |
The FAA should develop a TAAS and operational performance measures. |
A system framework is being developed by an FAA analysis team.b The TAAS development is moving too slowly for it to be an effective planning tool. |
|
Security enhancement factor (SEF) |
An SEF should be formulated to measure TAAS performance. |
A relative risk description is in use, and the analysis team also uses SEF. |
|
Five-year plan |
A 5-year plan should be developed in cooperation with all stakeholders. |
A plan outline consisting of ten subplans is in development with only two subplans having been completed so far. |
|
Hardened unit load devices (HULDs) |
Research and development on HULDs should continue. |
Some research and development is proceeding, but HULDs are not in the 5- year plan. |
|
aThe FAA red team performs testing of the security system without the operators being aware that they are being tested. bFAA. 2001. Total Architecture for Aviation Security Office of the Associate Administrator for Civil Aviation Security, Washington, D.C., June. |
||
Despite all the planning, however, the deployment schedules have not been maintained. Deployment of InVision’s CTX 5000 machines has proceeded more slowly than scheduled but has been accomplished. The L3 3DX 6000,5 conversely, although purchased by the FAA at the direction of Congress, has not been fully deployed in airports. The L3 3DX 6000 has demonstrated certification-level detection, false alarm, and bag throughput rates, but the machines themselves are considered too unreliable to deploy in airports, where downtime for unplanned maintenance can wreak havoc with flight schedules.
The development of a TAAS is also proceeding too slowly to allow its use as a planning tool. This tool could help the FAA identify the appropriate mix of technologies and procedures to address aviation security, but at TAAS’s current pace, machines will be deployed in airports before the information from TAAS can be digested and implemented. Costly retrofits and changes in airport architecture may then be required. Additionally, the TAAS methodology must be expanded to include deterrence concepts as a formal element of systems analysis. Deterrence is an extremely important yet unquantified element of aviation security and cries out for inclusion, measurement, and management.
A framework for a deeper understanding and evaluation of human factors and training is also a critical part of the aviation security system. The FAA has taken aggressive action to improve and extend the human factors capability. The use of HULDs is another important area for expanded research and development. Finally, a 5-year plan is in preparation but is incomplete at this time. The largest deficiency in deployment lies in advance planning and the system analyses that guide that planning. Deficiencies in these areas account for the bulk of the observed delays in implementation.
On November 19, 2001, a new aviation security bill was signed by President George W. Bush. The bill mandates a new agency, the Transportation Security Administration (TSA), which will guarantee the security of all modes of travel—air, ground, and sea. The agency will take over from FAA the security rule-making authority, and Congress has given the new undersecretary power to issue directives to make immediate fixes in security. The new agency is expected to pull from the FAA all of its aviation security responsibilities, including monitoring security from the baggage checkpoints to the ramp areas. The law requires that by January 18, 2002, all checked baggage must be screened for bombs. A variety of methods can be used, including explosive-detection devices, bomb-sniffing dogs, and matching of all checked luggage to passengers on board. Bags also can be searched manually. The new law requires that by the end of 2002, all checked luggage be screened using explosive-detection systems. That would require 2000 machines at an estimated cost of $5 billion (installed). The law requires the government to set standards for new screeners by December 19, 2001, develop a system to train employees by January 18, 2002, and transfer all private security contracts to the federal government by February 17, 2002. The law provides for a private security company pilot program starting November 19, 2002. Then after 2 years, the airport operators may elect to continue with private screening companies. The law authorizes the government to levy a passenger fee of up to $10 per round trip. Airlines would contribute about $700 million a year to help finance the new agency.
Certain risks are associated with air travel as they are with any form of transportation, and these risks can be assessed and quantified. In addition to the terrorist threat, natural phenomena, materials and manufacturing issues, operational procedures, and human factors all affect aviation safety. Although passengers have an inherent right to much of the information surrounding these risks, the release of certain information might reduce the effectiveness of security methods designed to prevent adverse actions. Other information might violate privacy protocols. Passengers cannot, for example, know the flight history of all their fellow passengers. In the end, individual air passengers and crew must rely on the entire aviation security architecture, including detection technologies and security personnel, for their safety.







