6
Energy Systems
INTRODUCTION
Our economy and quality of life require a plentiful and continuous supply of energy. Though energy per se accounts for less than 10 percent of our gross national product, much of the balance of the economy will not function without it. Commerce, manufacturing, and employment are all highly dependent on natural gas, refined oil products, and electricity. Health care, schools, and universities are dependent on electricity and, frequently, natural gas. Telecommunications and information technology require a high-quality and reliable electrical power supply. Transportation is most dependent on oil products but also has great need for electricity to manufacture the vehicles and operate airports, traffic management systems, rail transit systems, and terminals. Because our reliance on energy is so great, our vulnerability to an interruption in its supply also is great.
Included among U.S. energy systems are extensive networks of electric generating facilities and transmission lines, natural gas pipelines, oil refineries and pipelines, and coal mines and transport. These systems, and their operators’ emergency-response plans, have been tested by natural disasters such as floods and earthquakes; in general, the affected industries have returned disrupted systems to operation relatively quickly. Sabotage of individual components has also posed a nuisance, but the impacts have generally been manageable. However, the industry’s response capabilities were not designed to handle extensive, well-organized acts of terrorism aimed at key elements of the energy system.
The oil, natural gas, and electrical systems have several broad characteristics in common. Transport can extend over thousands of miles, often through remote
and unprotected lands. The systems are frequently controlled remotely, relying on supervisory control and data acquisition (SCADA) systems. Each system also has certain unique characteristics. Electricity cannot be stored for use when needed, whereas oil and natural gas products can be stored in limited quantities near points of use (thus lessening the impact of a shortage if the supply is interrupted). Also, oil products can be imported from overseas and transported by a variety of modes. Another important difference is that the refineries for converting crude oil into its large family of products are generally very large and complex facilities, located in just a few areas of the country, while the electric generating facilities come in a great range of sizes and are widely distributed throughout the nation. While some oil and gas operations generate their own power, most are highly dependent on electricity for their operations. In turn, about one-fifth of all electric power is generated from natural gas and oil products.
Analysis of possible targets, weapons, and delivery systems and of direct and indirect consequences reveals several very dangerous scenarios. The scenarios of greatest concern involve the electrical system. When service is lost, there are immediate consequences to every person, home, and business. An extended outage of electricity would have profound consequences.
Natural gas supply is also vulnerable, but the use of gas is not as universal as that of electricity. The oil sector has several vulnerable points, but, as noted above, it has backup alternatives. Coal is the least vulnerable and will not be considered in this analysis.
Several recent trends in the energy industries have increased the vulnerability of their infrastructures and made serious loss of service from terrorist attack more likely. To improve efficiency of operations, there has been a rapid increase in the use of automation and computerization; therefore each industry now relies heavily on information management and telecommunications systems. Low margins and various competitive priorities have encouraged industry consolidation, with fewer and bigger facilities and intensive use of assets in place. With no new refineries having been constructed since 1978, average refinery operation is at 93 percent of capacity (EIA, 2001). Control is more centralized, spare parts inventories have been reduced, and subsystems are highly integrated across the entire business. Few or no personnel at key facilities (i.e., electric substations and pipeline pumping stations), congested transmission corridors, and increased reliance on unsecured telecommunications and SCADA systems are common. (SCADA systems are also discussed in Chapter 5.)
This economic and competitive setting has led to reduced investment in system capacity and technology development. For example, annual additions to electrical transmission capacity declined 60 percent in the 5-year period 1990-1995, as compared with 1985-1990. The result is increased reliance on technology developed by vendors and increased outsourcing of key functions such as maintenance and security.
The electricity sector also is changing fundamentally as it incorporates more
competition and deregulation into what had been a highly regulated system. Independent power producers are gaining market share, but they support essentially no research and development and have little corporate infrastructure for issues such as security. Significant restructuring of the equipment-supply industry has occurred as well, with manufacture of some key components moving abroad. Unlike generation, the transmission portion is not being deregulated. This situation is straining the electric system because the priorities and practices of generating companies, transmission entities, and customers differ.
All these trends have led to systems that are highly efficient, productive, and cost-effective, but also subject to increased stress even without the threat of terrorism. Controls, cost competition, and regulatory uncertainty could each, in one way or another, limit the willingness of companies to invest in security upgrades that might seem desirable from a societal point of view.
It is readily apparent that any prolonged interruption of the supply of basic energy—be it electricity, natural gas, or oil products—would be a devastating blow to the nation and its people. This chapter addresses these systems’ vulnerabilities and identifies current means of addressing them, which should be implemented as rapidly as feasible. The chapter then describes key areas for R&D on materials, tools, systems, and methods. These R&D programs should be initiated immediately, and the resulting technologies should also be implemented as rapidly as feasible, although in some cases this could take up to 10 years. Overall, the recommendations in this chapter stress the importance of expediting implementation of technologies to reduce vulnerability due to the urgency of protecting this infrastructure. The most critical recommendations are numbers 6.9, 6.10, 6.11, 6.15, 6.16, and 6.17 below.
More fundamental changes, which might reduce vulnerability still further, are of course possible. Electricity generation might become more decentralized, reducing the impact of the loss of key components. The use of renewable energy resources (e.g., wind and photovoltaics) would complement this trend. The use of energy—oil in particular—could become more efficient, reducing the need for imports and, to some extent, vulnerability to upheavals in the Middle East. The use of alternative fuels derived from renewable energy or coal might grow, reducing dependence on the most vulnerable components of the energy systems. However, all these possibilities also have drawbacks, such as poor economics, unreliability, or remoteness. Furthermore, the U.S. energy systems are massive, and major changes can take decades, even after the technologies are developed. While it is worthwhile pursuing these research options and encouraging a diversity of supply, they will make little or no difference in reducing vulnerability to terrorism over the time frame of this study.
Although the threat of terrorism to our homeland places new requirements on energy infrastructures, the industry can draw on experience elsewhere. Because the national security and defense communities of this country have lived with such requirements for decades, a key element of our strategy must be to
accelerate communication and cooperation between members of those communities and the owners of energy infrastructures, including transfer of technology as appropriate.
ELECTRIC POWER
Introduction
The impact of a prolonged interruption in the electric power supply to any region of the country would be much larger than the economic loss to the energy sector alone. With the introduction of digital technology throughout our society, the cost of outages (e.g., from equipment failure or weather-related incidents) has significantly increased—from $30 billion in 1995 to $119 billion in 2001 (Clemmensen, 1993; EPRI, 2001). The nation’s electric power systems must clearly be made more resilient to terrorist attack.
The electric power system consists of four major components: generation plants, transmission lines and substations, distribution lines and substations, and system operations (the last mentioned may be located within a utility’s service area or may serve a larger set of service territories). Most generation plants consist of fuel supply facilities, generators, turbines, heat exchangers, cooling systems, control systems, and substations that connect to the transmission network. There are about 10,400 generating stations, with a total installed capacity of 786 gigawatts (GW), in the United States (EIA, 2001). Utilities own 82 percent of this generating capacity and independent power producers, the rest. Coal-fired units accounted for about 51 percent of the power generated, with nuclear at 20 percent, oil and gas at 18 percent, and hydropower and other renewable sources at 11 percent. The transmission system includes high-voltage lines, towers, and underground cables, as well as transformers, breakers, relays, and associated control equipment, which is mostly in substations. The distribution system includes the lower-voltage distribution lines and cables, substations, and control equipment. System operations include monitoring, control, and communications equipment.
Utilities have a century of experience to draw upon, and today they make use of ever more sophisticated technology to achieve high reliability and quality of service. However, September 11 has raised additional concerns about the vulnerabilities of these highly integrated systems and the consequences to the people and economy in the event of a terrorist attack.
Representative Vulnerabilities
Two types of terrorist threats are of concern for the electric power system: physical attacks and cyber- and electromagnetic attacks. An isolated assault of either kind on an individual generating station, substation, or control center could
cause a serious but only local disruption. By contrast, a coordinated attack on a selected set of key points in the system could result in a long-term, multistate blackout. While power might be restored in parts of the region within a matter of days or weeks, acute shortages could mandate rolling blackouts for as long as several years. A highly stressed system (e.g., if power imports are high and transmission reserve capacity is low at the time of the attack) would be more vulnerable to cascading failures and the resulting longer-term blackout.1
Targets might include equipment used in the production or transmission of electricity and electronic components used to monitor and control the production, transmission, and flow of electricity, which for the purposes of this chapter are labeled “controls.”
Much of the equipment under consideration is so large that it must be located outdoors, where it is vulnerable to weapons ranging from rifles to laser-guided missiles. Equipment operating at elevated temperatures could also be targeted with heat-seeking missiles. In addition, many of these facilities are vulnerable to military or even homemade bombs. Transmission towers and cables are located in a variety of settings, few of which are fenced or otherwise protected, and thousands of miles of these lines pass through remote sections of the nation. Thus they could be easily approached for attack, with little likelihood that the activity would be observed. Power lines and substations also are vulnerable to chaff, conducting strands draped over lines or equipment to cause short circuits.
The “controls” are mostly located in control rooms at generating facilities, substations, and system-operation centers. These sites generally are fenced off, but they are not hardened—excepting nuclear plant control rooms and a few system control centers. Most facilities are staffed continuously, but there has been a trend in recent years to reduce personnel at substations in favor of automated equipment under remote supervisory control. At each node in the controlled system, monitoring equipment, sensors, and methods of transmitting the data and control signals are colocated with the equipment being controlled or monitored, increasing vulnerability. Physically, these components can be attacked with weapons similar to those mentioned above, with the possible exception of heat-seeking devices.
Control components are also vulnerable to cyber or electromagnetic attack. Cyberattacks would involve intrusion into the control systems via the Internet or the affected utilities’ private networks; many of these networks include modem access, which adds significantly to their vulnerability. Electromagnetic pulse (EMP) attack would involve the introduction of radio-frequency or microwave impulses into the circuitry of the control systems, upsetting their electronics and leading to network destabilization and outage. Such outages could be serious, but they are unlikely to require the replacement of much equipment.
The most insidious and economically harmful attack would be one that exploits the vulnerabilities of an integrated electric power grid. “A chain is only as strong as its weakest link” applies here. Simultaneous attacks on a few critical components of the grid could result in a widespread and extended blackout. Conceivably, they could also cause the grid to collapse, with cascading failures in equipment far from the attacks, leading to an even larger, longer-term blackout. In either case, the failure would be caused by the system’s inability to recover from a multipoint, or “n minus k,” attack (on k points of a network that has a total of n nodes). A single “n minus 1” failure event (or even an “n minus 2” event, under certain circumstances) probably could be handled by current contingency plans, which utilities have used for decades in reacting to natural disasters or major equipment failures. Recognition of an attack in progress, and initiation of a system-level response to minimize the harm being done, must occur within a very short time frame—even just a few seconds. However, distinguishing between a routine failure and the start of a series of planned attacks is a very difficult challenge.
The duration of a terrorist-caused blackout or curtailment would depend on the extent of the failure and the availability of replacement components and skilled personnel to make the repairs. Certain components of the electrical system are of particular concern because few spares are available nationally, and new replacements could take several years to procure. The shortage could be alleviated in part by activating available ties to adjacent systems and utilizing local generating units, but rolling blackouts (as distasteful and economically damaging as these are) could be needed.
Attacks on nuclear power plants could have special consequences for the nation’s electric systems. The outage of a single nuclear station would have an impact similar to the outage of any other large generation site. However, the uniqueness of nuclear power, both from a public and regulatory perspective, could result in a much wider impact. Under those circumstances, the U.S. Nuclear Regulatory Commission (USNRC) might require all operating nuclear units to shut down until their safety could be assessed by the USNRC and/or additional security measures could be carried out. In either case, the sudden removal of that capacity—about 20 percent of the nation’s generating pool—would put a severe strain on the rest of the system. For some regions of the nation, the generating
capacity loss could approach 40 per cent of the currently available generating capacity.
Implementation of Existing Technology
Redirecting and Prioritizing Security Attention
This country’s electric power systems have some attributes that may hinder the implementation of security-based improvements. By their very nature, the systems are geographically distributed, making them difficult to protect. Historically, analysis has focused on threats from natural disasters; security from malevolent attack has generally not been a high priority. With the exception of nuclear power plants, the main purpose of security at most electrical facilities has been to keep people out for their own safety, not to deter terrorists. Reserve capacity (the difference between installed capacity and the amount that’s necessary to meet peak demand) has become small for generation, transmission, and distribution; highly stressed systems are less resilient in the face of upsets and take longer to recover. Deregulation has encouraged efficiency, invested-cost utilization, and return on investment rather than redundancy, reliability, and security. For the same reasons, power companies keep fewer spares on hand. Utilities have also reduced their support for research and development;1 in particular, new protection schemes for countering cyberthreats seriously lag the rapidly advancing cyberweapons available. Another consideration is insider threats. These have been difficult to address because of workplace privacy and individual rights issues, which continue to inhibit the use of screening and profiling tools.
Recommendation 6.1: The federal government should review the current institutional and market settings to determine what, if anything, should be done to facilitate actions for improving the security and resilience of the country’s electric power system.
Tools for Identifying System Vulnerabilities to Terrorist Attacks
For a utility or independent power producer, one of the most significant challenges will be to direct its often limited resources to protecting its most important elements. This prioritization must take into account possible threats, probability of threat, consequences of attack, and response capability. At the same time, because the U.S. transmission grids are largely integrated with the
Canadian and Mexican grids, those systems must likewise be analyzed and their hardening plans coordinated with those of the United States. The defense and national security communities in the country have developed tools for vulnerability analysis of physical sites and have used them extensively for over 20 years. Recently, there has been some success in transferring these tools to parts of the energy infrastructure. They should be made available to the rest of the electric power industry. By applying these analytical tools to all critical grid components, the systems approach to electric power security would identify key vulnerabilities in a facility and determine the relative value of possible security-upgrade options. These tools should include methods that help define appropriate use of (1) surveillance of critical sites and equipment, (2) hardening selected sites, (3) barriers to prevent intrusion, and (4) masking of selected equipment.
Recommendation 6.2: The electric power industry (as well as the oil and natural gas industries, discussed later in this chapter) should undertake near-term studies to identify vulnerabilities to physical attack on equipment and controls. These studies should include connected Canadian and Mexican assets. The tools for analysis of vulnerabilities used in the defense community should be transferred to the energy operators for these studies, along with adequate training in their application.
For the nation as a whole, the identification of vulnerabilities requires sophisticated models and simulations of the infrastructure. Because these efforts will require a great deal of information (most of it not easily available to any one individual player) on such issues as threats and interdependencies, some infrastructural segments have started establishing information sharing and analysis centers. This is largely an ad hoc phenomenon, which should be placed on an organized, rational basis. In so doing, sensitive data on equipment, its location, and its vulnerability will have to be examined and protected from those lacking a need to know, necessitating an information classification system. This issue is germane to the oil and natural gas sectors as well.
Recommendation 6.3: Action should be taken to facilitate information sharing between energy sector components. Specifically, the government needs to adjust its policies in order to allow a reasonable balance between the industry’s access to information on vulnerabilities and threat scenarios, on the one hand, and the protection of such information to ensure national security, on the other. In addition, industry’s concerns about antitrust and liability issues, as well as freedom-of-information (FOIA) risks, need to be addressed. Government support for energy sector information sharing and analysis centers is essential. Also, the security classification system for information must be reviewed, and modified accordingly, in light of the new terrorist threats.
Addressing System Vulnerabilities
After implementing the above, the next step should be for the industry to analyze the system’s specific components, probably through the regional reliability planning councils. It would then be possible for the utilities, independent system operators (ISOs), and regional transmission operators (RTOs) to determine which components are most vulnerable from a system perspective.
Once determined, these components should be given the highest priority for hardening and protection, including enhanced surveillance and response, fortified barriers to intrusion (both by land and from the air), installation of bulletproof walls around equipment vulnerable to firearms, and, possibly, installation of redundant, geographically separated systems.
Industry also should examine how to expedite recovery from a widespread attack. This should include a review of current sparing philosophy for critical components. “Business as usual” is not likely to be an adequate approach. Increased redundancy also would be useful, such as with control systems, which could be decentralized and designed with duplicate backups to minimize the loss of control from an attack. Utilities and other operators also should plan for a “black start” following a large-scale blackout. Location of critical equipment to accomplish this might be aided by the use of simulation models, threat scenarios, and system models to deal with the multiplicity of challenges. This action may be augmented in the future by the development of an adaptive grid, as discussed below in Recommendation 6.16.
Recommendation 6.4: Utilities, independent system operators (ISOs), and regional transmission operators (RTOs) should identify the most critical equipment for protection in their respective domains. This protection, where it does not already exist, should then be accomplished with available technology, including (1) increased surveillance of critical sites and equipment, (2) hardening of selected sites, (3) installation of barriers to prevent motor-vehicle or rail intrusion, and (4) masking of thermal signatures of selected equipment. As part of this examination, policies for critical-equipment spare parts should be reviewed, including consideration of cooperative efforts for employing regionally based and coordinated spares centers.
The possibility of cascading damage from an attack on the transmission lines themselves could be reduced by developing and implementing new designs for conductors, towers, and transmission corridors. Although the industry has examined this problem for weather-related and other circumstances, what is now needed is a top-to-bottom review that assumes a deliberate and extensive attack.
Recommendation 6.5: An immediate review of electric transmission lines should be initiated, through the Federal Energy Regulatory Commission (FERC) and the regional reliability councils, to identify opportunities for
retrofit actions that would protect existing facilities from cascading damage after an attack.
Provision for Emergency Federal Policy to Facilitate Recovery from a Catastrophic Shutdown of Electric Power Facilities
Catastrophic terrorist attacks will not only disrupt the system, they will also require follow-up investigations that may necessitate treating parts of electric power facilities as crime scenes. Under these circumstances, business-as-usual regulations could prove a hindrance. Thus there is a need for government and industry to identify statutory authority for certain temporary measures.
Recommendation 6.6: Government, through the Office of Homeland Security, should identify statutory authority that will permit emergency actions to be taken and temporary changes in regulations to be adopted, after an attack, to reestablish service. To the extent feasible, the government and industry should collaborate in preplanning specific actions and changes in regulations, based on reasonably anticipated service disruptions. This capability, which applies to the natural gas and oil sectors as well, should be in place prior to a catastrophic disruption in the supply.
Paying for Security Improvements and Recovering Investments
All of these actions to improve security and the ability to recover from an attack will require investments in facilities and equipment. However, as noted, the environment created by deregulation has compelled utilities to control costs tightly. One consequence has been the reduction in reserve capacities, resulting in the greater utilization of equipment by routinely operating it closer to its capacity limits. The existing mechanisms for cost recovery—ranging from rate relief to competitive market forces—must be reviewed and appropriate incentives developed in order to encourage investments under these changed circumstances.
Recommendation 6.7: Both FERC and the state utility commissions (perhaps through the National Association of Regulatory Utility Commissioners) should allow certain counterterrorism costs—specifically, for actions taken to reduce the vulnerability of critical equipment within an electric utility’s operation and to speed recovery following an attack—to be included in the rates that the utility can charge for its services. The federal government also should consider the use of incentives for investments made for security purposes in a competitive market environment.
Allowable actions could include simulation-model development and deployment, increasing surveillance, hardening of sites, retrofitting transmission lines against cascading failure, increasing operating margins, decentralizing control systems, and increasing the availability and numbers of critical equipment spares.
It is also recommended that a dialogue between private sector executives and government policy makers be initiated to define their respective roles in implementing security and response capabilities against terrorist attacks. This dialogue is also needed for defining federal and private sector roles in related R&D. Resolving the issues of who pays for security and system-hardening improvements, and how the accompanying investments are to be recovered, must be an early priority for leaders in all relevant sectors.
Recommendation 6.8: A clear and coordinated strategy should be developed and agreed upon by the federal government, the electric power industry, and the equipment suppliers. This strategy must include (1) the definitions of proper roles for each sector, (2) review of the current R&D programs of the three parties for relevance and added support, (3) coordination on the part of the federal government, through DOE, of relevant research and development being done in various other federal agencies, including the national laboratories, (4) coordination by industries of their R&D efforts through appropriate associations (e.g., the Electric Power Research Institute (EPRI) for the electric utilities), (5) involvement of the regulatory community, through the Federal Energy Regulatory Commission (FERC) and the National Association of Regulatory Utility Commissioners (NARUC), for appropriate rate-base considerations, and (6) government-developed incentives to expedite the early introduction of technology and equipment.
Defending Against Cyberattack
In addition to protecting equipment and facilities from physical attack, the potential for attack on control systems needs urgent attention. The manner in which data are transmitted between control points should be reviewed in order to improve security and reduce the potential for hacking or disruption. Encryption and other in-place defensive mechanisms need to be reviewed and upgraded where indicated. However, as discussed above (and below), the decision to commence security upgrades—whether by a power producer, a transmission provider, or another party—requires resolution of questions regarding who is to pay and how that investment is to be recovered. These issues are as relevant to the gas and oil sectors as they are to the electric power system.
Recommendation 6.9: The manner in which data are transmitted between control points and/or SCADA systems should be reviewed by their owners in order to improve security and reduce the potential for hacking or disruption. In addition, firewalls and procedures for detecting cyberintrusions should be reviewed in order to prevent or reduce the threat of cyberattack on control systems. Additionally, it is recommended that efforts under way for cybersecurity in other areas (such as the national laboratories) be translated into the energy systems environment. Finally, any such systems and devices should be reviewed by appropriate standards-setting groups and
vendors. Coordination should occur through DOE and the Office of Homeland Security.
Research and Development Priorities and Strategies
While much can be done with current technology, additional options are needed in physical protection; equipment redesign for inherent robustness; cybersystem protection and robust information technology (IT) architecture; system modeling for vulnerability analysis; and architecture and supporting technology for flexible, adaptive power systems for impact mitigation. The fraction-of-a-second response times of a power grid allow very little margin for countering the effects of an attack. Therefore, prevention of attacks should have a high priority. Technologies that support automated, split-second action may be difficult to develop but could be crucial in limiting the consequences of an attack. In addition, the costs of current technologies can be reduced through R&D, increasing their level of applicability.
Extra-High-Voltage (EHV) Transformers
The physical design of critical equipment should be modified—for robustness, hardening, blast mitigation, quick repair, and barriers to minimize direct assault (including from the air)—to reduce its physical vulnerability. For example, certain key technologies with identifiable heat signatures should be reviewed for masking those signatures, thereby deceiving terrorists’ detection and targeting. The national security and defense communities in this country have developed, over the decades, many design philosophies for achieving reduced vulnerability. These ideas should be studied and aggressively adapted to the power grid.
One area of particular concern is the vulnerability of EHV transformers. These are critical components of the grid. The number of spares available in the nation is very limited, and replacements would require many months to manufacture and ship from foreign suppliers. Building on the general design philosophy of the U.S. Army for small, modular tanks for rapid overseas deployment, a possible solution might be the development of a modular, lightweight, universal EHV transformer for use in the instances envisioned here—namely, the rapid restoration of the ability to deliver power in the event of a widespread attack on a utility grid system.
Research should be undertaken to determine if such a modular universal EHV transformer might be developed. It would be smaller, cheaper, and more transportable than the large, custom-designed EHV transformers currently used in substations. Modular units might be used individually or in multiunit sets to replace EHV units that had suffered damage. Modular units would likely be less efficient and have a lower power rating, but they would be sufficiently affordable to be stockpiled at ISO or RTO sites and used as temporary equipment in the
event of a major loss. They would be analogous to the small spare tire supplied with some cars: vital in an emergency, but to be replaced as soon as possible. They might also be used on a short-term basis where load exceeded capacity; however, such use should be of short duration so as not to preclude their use for the purposes described here. Equipment suppliers must take the lead here, but funding support must come from the federal government (see subsection “New Electric Energy R&D Programs”). EPRI could provide the organizational framework to engage suppliers in precompetitive R&D.
Recommendation 6.10: Research should be undertaken jointly by DOE and the industry (represented by EPRI) to determine if a modular universal EHV transformer might be developed for application throughout the U.S. electric industry.
Advanced Intrusion Detection Systems
Most transmission systems cover many miles and are unattended. The present method of monitoring thousands of miles of rights-of-way—visual inspection, by truck or aircraft—is inadequate to defend the system against terrorism. Operators need new surveillance technologies that hold promise for frequent monitoring and highly reliable detection of unwanted activity. The best sources for these technologies would be the work on drone aircraft, satellite-surveillance technology, intelligent-software-based analysis, change-detection sensors, and intrusion-detection cables that is currently under way in various defense and intelligence agencies. These technologies would have to be adapted to energy systems, which should be done as a public-private partnership with cost sharing. The main obstacle probably would be information classification and “need to know.” It would be best to coordinate such research with industry through EPRI. As noted in the discussion of the oil and gas sectors, this issue is relevant to all three energy sectors.
Recommendation 6.11: Surveillance technologies developed for defense and intelligence agencies should be investigated for their usefulness in defending against terrorist attacks on widely distributed oil, gas, and electric transmission assets. These technologies could include drone aircraft, satellite-surveillance technology, intelligent-software-based analysis of surveillance images to scan for unwanted activity, change-detection sensors, and intrusion-detection cables designed to sense unusual vibrations or noises. The Office of Homeland Security should be the coordinator of these efforts.
Structural Materials Enhancement
A key aspect of hardening existing facilities against physical attack is retrofitting structures to increase their resistance to blast shock and fire. Manufacturing, application, and implementation methods must be developed for upgrading
energy-sector facilities at reasonable cost. Materials specifically hardened against explosions and fire are being developed for other uses, and this work could be applied to the energy sector.
Recommendation 6.12: Research and development for hardening energy-system assets against blast shock and fire should be conducted by DOE. Areas of focus might include material coatings and surface-applied structural enhancements.
Cyberthreats
Advanced hardware and software to protect SCADA systems, plant control systems, and overall system controls are needed. Included in this category would be intelligent-agent-based networks to monitor and respond to cyber threats, better encryption methodology, and real-time barriers to intrusion through better architecture and firewalls. This technology development crosscuts many infrastructure areas. R&D currently under way or soon to be initiated, both in federal government and private sector programs, should be applied to the electric power system, supplemented by R&D directed by EPRI (see Recommendation 6.9).
A cyberattack from within, brought about by a disgruntled employee or a terrorist plant, could be particularly damaging. R&D is needed on ways to detect and counter this threat for critical components.
Recommendation 6.13: The technologies discussed in Recommendation 6.9 should be further developed for maximum utility in the electric sector. In addition, to counter internal cyber threats, smart controls should be developed and deployed that limit the manipulation of the system outside normal operating settings—perhaps utilizing artificial intelligence or redundant controls.
Electromagnetic Pulse
EMP has long been a consideration for regional vulnerability under nuclear attack scenarios. Relatively simple devices can produce the same effect on a much smaller and more local scale. To counter such threats, lower-cost electronic shielding needs to be developed and employed to protect critical components.
Defensive Systems
Protecting facilities and systems deemed to be most critical from air attacks is a significant challenge. Facility hardening may not be feasible using conventional approaches, and more sophisticated methods, such as underground siting, could be prohibitively expensive, even for new facilities. The selective use of
active systems—i.e., weapons—needs to be investigated. Such weapons might include surface-to-air missiles in combination with doubly redundant safeguards against unintended launch, as well as nonlethal systems such as directed-energy weapons and energetic-particle shields. Defensive structures, such as structures that would disrupt an incoming aircraft, should also be investigated. These efforts should include model development validated by subscale and full-scale tests. Such innovations in defense may provide cost-effective solutions when combined with traditional security and hardening. These issues also pertain to the oil and gas sectors, as noted later.
Recommendation 6.14: Defensive systems, for use at the most critical assets of the energy infrastructure, should be studied and developed. Such systems would be used in combination with traditional security and hardening methods. In addition, the deployment of weapons, lethal and nonlethal, should be reviewed.
Simulation Models for Analysis and Management
Models can help solve some of the problems of protecting electric power systems from terrorist threats. Regional models of the power grid—such as the Texas grid model for the Houston area, which has been used for analysis of outages—must be expanded and interdependency modeling accelerated (Patton et al., 1999). In that spirit, a federally funded center for interdependency modeling has recently been established (the National Infrastructure Simulation and Analysis Center). Because coordination, perhaps through EPRI, will be essential to obtain data from the power industry, this is a clear opportunity for a federal-private partnership. Also, the sophisticated level of the needed modeling will require state-of-the-art computational tools available at DOE’s national laboratories. Protection of the resulting information on the vulnerability of key nodes in the electric power system will demand the highest level of security classification.
Recommendation 6.15: Improved simulation-design tools for modeling the prevention, response, and recovery of energy systems and for analyzing a variety of terrorist-threat scenarios should be developed, under DOE leadership, at the national laboratories. These models would have the following functions: (1) help planners, from the perspective of regional and nationwide system protection, to identify assets for vulnerability assessment; (2) model regional and national power-grid interdependencies to more accurately evaluate each component and node of the infrastructure; (3) determine the most vulnerable sites in the system; (4) test and validate proposed mechanisms to prevent cascading and broad-area effects; and (5) analyze the vulnerabilities of interdependent infrastructures (e.g., the effects of electric power outages on the water supply system).
Intelligent, Adaptive Power Grid
Under normal conditions, the electric power grid is controlled to balance changes in demand with changes in generation. In the event of a broad-based terrorist attack on multiple nodes, controls would be unable to reachieve balance. The result could be outage of an entire grid, with the possible cascading of such effects into other regional grids. Innovation to create a more flexible grid structure is clearly needed.
Recommendation 6.16: Technology should be developed for an intelligent, adaptive power grid that combines a threat-warning system with a distributed-intelligent-agent system. This grid would be able to rapidly respond with graceful system failure and rapid power recovery. It would make use of adaptive islanding—a concept employing fast-acting sensors and controls to “island” parts of the grid as the rest comes down—and technologies such as storage units positioned at key points to minimize damage during shutdown. The system would need to be able to differentiate between a single component failure and the kind of concurrent or closely coupled serial failures at several key nodes that would indicate the onset of a concerted attack.
The trend over time has been to large, remote generating plants, which require large, complex transmission systems. Today there is a growing interest in distributed generation—generators of more modest size in close proximity to load centers. This trend may lead to a more flexible grid in which islanding to maintain key loads is easier to achieve. Improved security from distributed generation should be credited when planning the future of the grid.
Change in the electric power infrastructure will, of necessity, be evolutionary, not revolutionary. As such, implementing new technology for intelligent, adaptive power grids will take time and resources. Recovery of the invested funds through rate mechanisms or in some part through homeland security funding must be examined. Change will also require adjustments in the philosophy of operation of the whole electric-power-grid structure. Thus, industry organizations such as EPRI will need to play a major role (see Recommendation 6.8).
It is clear that we cannot totally prevent a terrorist attack on electric power systems; the question is what can be done to mitigate the effects of such an attack. This intelligent adaptive grid is a new approach and one that could provide resiliency to the grid in a new manner. It entails long-term R&D and will require new technology, some of which is made possible by advances in microelectronics and controls technology.
There is some work under way at EPRI with DOD cosponsorship, on an intelligent, self-healing grid. Since sensors and control systems are integral parts of this concept, the DOE national laboratories must be key participants in the effort. The work spans the range from research through development, so it is appropriate that the funding be shared among government (DOE and DOD), industry (through EPRI), and equipment vendors.
Deployment would be the responsibility of the utilities and ISOs. Vendors will receive the technology transferred from the national labs and EPRI and will in turn commercialize it. The mechanism for development and deployment is well-established, public–private partnerships and transfer of technology from federal investment. Incentives for initial deployment will require support and incentives from FERC and state regulators.
Existing Electric Energy Research and Development Programs
Research and development are mainly supported through three sets of sponsors:
-
The Department of Energy program includes technology development in superconductivity, energy storage, grid reliability, analytical tools, advanced power generation, environmental controls, energy management, and combustion research. If fully developed and implemented, some of these technologies—such as distributed generators based on fuel cells or microturbines—could play a role in making energy systems more resilient in the face of terrorist attacks. Although DOE responded quickly to the recommendations of the Presidential Commission on Critical Infrastructure Protection—it recently established the National Infrastructure Simulation and Analysis Center, as noted above—infrastructure per se has not received a high level of budgetary support. DOE also sponsors technology development in physical-security technology to protect its own facilities, as well as those of DOD and the Department of State.
-
The utilities have long funded a high-quality and valuable R&D program through a cooperative effort led by EPRI, some of which has been concerned with infrastructure. However, it must be noted that investment for this effort has dropped, at least in part because of deregulation.
-
Manufacturers of equipment such as transformers, high-voltage components, and control systems fund technology development internally. However, such efforts are mainly focused on incremental improvements, especially in advanced generation technologies.
These R&D programs should be reviewed for their relevance to improving the security of the electrical supply and transmission systems. Those that meet the standard should then be accelerated, through appropriate funding and assignment of technical resources, and challenged with negotiated deadlines for delivery of results. This may require additional federal funding support.
New Electric Energy R&D Programs
As noted above, the electric utility industry, under historical regulation, had a mechanism at EPRI for carrying out R&D. This mechanism allowed R&D to
be performed in a noncompetitive environment and involved DOE in efforts focused on the longer term; the equipment manufacturers contributed to this collaboration as well. In this way, three entities worked together on bigger efforts than any one of them could do alone.
A similar approach is needed for the counterterrorism R&D agenda. It is clear that for equipment-related research (on inherently hardened equipment and modular transformers, for example), the suppliers must play a fundamental role. But it would be difficult for them to shoulder the entire cost, and in any case significant innovation needs a broader involvement from the nation’s science and technology communities. Financial support, principally from government—directly from DOE and via rate adjustments from FERC and the various state commissions—will be needed. Tax breaks and risk financing for the installation of new security-related equipment should also be considered.
Research and development to achieve an intelligent, adaptive power grid will require the participation of experts in fields such as microelectronic systems, sensors, distributed intelligence, and communication. The research already under way in these areas for military applications should be brought to bear on counterterrorism as well. A public–private partnership is recommended, with the industry’s involvement coordinated by EPRI and the federal research organized, managed, and leveraged from defense work, where indicated, through DOE (see Recommendation 6.8). R&D on enhancements to structural materials is a crosscutting issue for many infrastructures. It should draw on appropriate expertise in the universities and research laboratories, with industry-unique R&D managed by EPRI.
Defensive systems research should draw extensively on the work of the defense and national security R&D communities. Weapon systems development should remain a DOD-led activity, with industry interface managed through the regulatory agencies and appropriate industry associations.
A great deal of work on cyberthreats is under way in the private sector as well as at the federal level. These efforts should be adapted to the particular needs of the electric utility industry, both in communications systems and SCADA systems. Interfaces with equipment control systems must of course involve the equipment suppliers, with support from the government and the industry through EPRI.
The areas of simulation tools, vulnerability analysis, and model development will require the best intellectual resources of the industry, the cooperation of regulators, and the involvement of the federal government as a source of funding as well as of technical input, primarily through the national labs. EPRI should serve as coordinator.
Unfortunately, DOE’s programs on electric power systems have virtually disappeared in recent years. But in 1999 and 2000, the Department undertook portfolio analyses, and electricity infrastructure was identified as a critical research need, as it is in this chapter. Such programs should therefore be revived,
with particular focus on the hardware and software goals described above and on coordinating the larger studies of national importance—for example, those involving simulation and grid structure. The importance of this work underscores the need for these programs to be managed at the level of the Undersecretary of Energy.
Summary
R&D on the electric power infrastructure, including not only generation but also control systems, communications, and sensors, has not received the attention it deserves in order to meet the sorts of threats listed here. While industry (both manufacturers and utilities) can be called upon to help correct this omission, significant improvements will occur only if the U.S. government takes a leading role.
In the face of a restructured and highly competitive electricity marketplace, government determines the right set of policies and incentives for electric systems to become more resilient and capable of withstanding coordinated attacks. It is not clear, however, just what incentives would attract private investment for building redundancy, toughness, reliability, and the capacity to recover quickly from an attack. While it is clear that some of the current R&D and investment in new equipment and systems will have a beneficial effect on counterterrorrism goals, additional measures will be required.
For example, would an approach similar to the Strategic Petroleum Reserve be feasible? That is, could a “strategic electricity reserve” be constructed that would include critical equipment spares placed near important urban centers of the country? How might public–private partnering—bringing to bear the full capabilities of the industry, its suppliers, and the federal government, including efforts under way at the national laboratories—enter into this concept as well as into fulfilling the longer-term R&D needs? How, for instance, might increased reserve generation capacity be provided? Such questions must be throughly addressed if we are to adequately protect the nation’s electric power system, its economy, and the well-being of its people.
Recommendation 6.17: A coordinating council should be formed to ensure that the necessary research on electric power systems is carried out, that the resulting technologies have a route to market, that implementation is done expeditiously, and that the costs are recovered through appropriate incentives, fees, rate adjustments, or other funding mechanisms. The council should include, but not be limited to, representation from the North American Electric Reliability Council, DOE, the Office of Homeland Security, NARUC, EPRI and other utility industry groups, manufacturers, and ISOs and RTOs.
OIL AND NATURAL GAS
Introduction
Oil and natural gas are essential energy sources for our economy. Oil products provide 97 percent of the energy used in the transportation sector. Natural gas provides over 25 percent of residential and industrial energy needs (not including the electricity generated from it). Together, these fuels account for almost 62 percent of all energy used in the United States (EIA, 2001). A significant disruption to either of these basic sources—that is, one that lasted for more than a few days—would have serious consequences for the U.S. economy and the health and well-being of the population (NPC, 2001; Badolato, 2002). Because of the importance of oil and gas to the nation and the large number of companies and vendors in the industry, it is important that the industry and government jointly establish a security standard consistent with a post-9/11 world.
The oil products supply system includes 161 oil refineries. The natural gas system includes 726 gas-processing plants. Extensive but separate pipeline networks provide for transport: 1,280,000 miles of gathering, transmission, and distribution lines for natural gas and 220,000 miles of crude oil and oil products lines. Attacks on the natural gas system are more likely to have catastrophic consequences, but oil has its weak points also.
The vulnerability of each of these systems is discussed first. Many of the current implementation issues and longer-term R&D needs are similar for the two systems, so they are treated together. Several of the recommendations in the electric power discussion have equal applicability to oil and gas. These are numbers 6.2, 6.3, 6.6, 6.9, 6.11, 6.12, and 6.15.
Natural Gas Systems
The U.S. natural gas infrastructure, together with the portion of the Canadian system that serves the United States, is very large. The U.S. system alone consists of over 276,000 gas wells, some of them in locations as much as 100 miles offshore, 45,000 miles of gathering pipeline, 410 underground storage fields, 54 complete liquefied natural gas (LNG) facilities, 254,000 miles of transmission pipelines, and 980,000 miles of local-distribution pipelines (NPC, 2001). This vast network, privately owned and operated, was built to meet market demand and was designed for maintainability, with safety as a constant requirement. Vandalism was taken into consideration, but the facilities were not designed and built to withstand terrorist attack.
Several components of the natural gas infrastructure could be considered attractive targets for terrorists (see Figure 6.1):
-
Transmission pipelines, including those from offshore collecting sites;
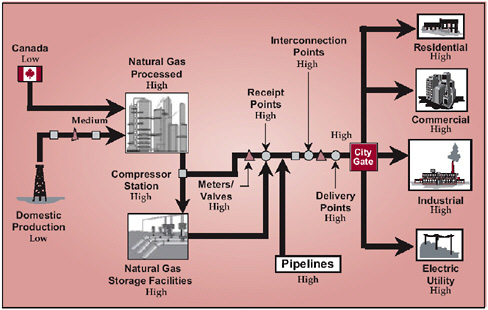
FIGURE 6.1 Physical vulnerabilities of the natural gas infrastructure. SOURCE: National Petroleum Council (2001), p. 34.
-
Pipeline interconnections (facilities where one pipeline can be connected through a set of valves and crossovers to other pipelines);
-
Compressor stations (where gas compressors, driven by large electric motors or gas-fired engines, pressurize the gas to facilitate its movement through the pipelines);
-
City Gates (stations where high-pressure gas from the transmission line is transferred to delivery pipelines at lower pressures for distribution to cities);
-
Liquefied natural gas facilities (where the gas is liquefied by compression and cooling and then placed in special containment vessels, such as ships, or where the LNG is taken from the containment vessels and gasified for delivery into the city pipeline distribution system); and
-
Control systems, where all of the above functions and processes are controlled and monitored.
Any of these facilities would be vulnerable to a deliberate attack. It could take the form of a direct assault by a small team of terrorists using any weapons and explosives readily available, or it could be in the form of sabotage performed by an insider. A cyberattack on the control system is possible via the Internet, by using radio-frequency devices to scramble microwave signals, or by physical occupation of the control center. Under present conditions, a well-planned and coordinated terrorist attack could take out the nation’s gas transmission systems
and keep key pipelines out of service for an extended period of time. The resulting loss of this basic energy supply to large areas of the United States would affect home heating, electric power generation, and business and industry, causing enormous personal and economic damage.
Representative Vulnerabilities
Transmission Pipelines. Natural gas pipelines present appealing targets. Natural gas is produced in concentrated areas, generally along the Gulf Coast, in the Rocky Mountain region, and Alaska, or imported from Mexico and Canada. It must be transported to 1,500 regional and local distribution companies (LDCs) via a comparatively small number of long-distance transmission lines. The Northeast, North Central, and Pacific Coast regions of the United States depend on supplies delivered by these large, long-distance pipeline networks, and there are no viable alternatives to this arrangement. While the pipeline network has a degree of interconnectivity that provides the ability to reroute, several regions are totally dependent on a single major pipeline system. The inter- and intrastate transmission system is characterized by large, buried, high-pressure pipelines, intricate systems of computerized valves, aboveground compressor stations, exposed (and marked) rights of way, and river crossings. Close security over these transmission systems is very difficult because they cover such extensive geographic areas; to deal with interruptions and any malicious damage to these systems, emphasis has historically been on response after detection. The control systems, when in operation, are able to rapidly detect loss of pipeline pressure or abnormal indicators in a pipeline system. Typically, automatic shutdown systems are activated to isolate the problem and provide the opportunity for a repair team to go to the site, assess the situation, and effect repairs. Another option is for the control-system personnel to manually close valves and isolate a problem area. These response scenarios are designed to handle relatively normal interruptions of service. They were not intended for, and are not adequate to deal with, the types of terrorist threats that now must be considered.
Pipeline Interconnections. Pipeline interconnections typically involve large valves, manifold piping, and controllers. Receipt and delivery points with valve interconnections are also found in all pipeline systems; they are located both within individual systems and between pipelines of different transmission companies. The loss of an individual interconnection may not be very serious, but interconnections become critical components with the loss of transmission lines or when they are associated, say, with a major gas storage facility. Interconnections are aboveground and protected by nothing more than chain-link fences unless they are part of a larger facility. Terrorists could easily identify pipeline interconnections that are located in remote areas and breach the chain-link fence. Destruction of an interconnection would eliminate the possibility of rerouting
flows and also could prevent drawing from storage facilities. Attackers could destroy the interconnection facilities with explosives, which would also provide the opportunity for immediate media attention. The spectacular fire and destruction that could be expected from such an attack would meet the terrorists’ need for recognition. Because these valves and connections are frequently of unique design, replacement could take months. Premature shutdown of an interconnection valve is another vulnerability. Attackers could shut off valves physically or through takeover of the SCADA system.
Compressor Stations. Natural gas pipelines typically have compressor stations placed about every 60 miles along the route to maintain high pressure (typically 700-800 psi, although pressures can be as high as 1,400 psi). Compressor stations are large facilities that can cost more than $40 million apiece. Their operating components include valves, compressor units, prime movers to drive the compressors, and various piping and controllers. These stations are usually staffed with small maintenance or operating crews, but today some are unattended, being operated instead through remote SCADA systems. Even when staffed, physical security at compressor stations is generally minimal—intrusion alarms, sensors, and surveillance devices are not usually in use. Compressor stations tend to be noisy, so they are often located in remote areas. These stations would be relatively easy targets, particularly during the night when lightly staffed. Compressor stations typically have systems to shut down compressors and activate isolation valves to shut off all gas flow—that way, the risk of explosions and fires is minimized in case of a line break. However, these protective systems would probably be ineffective in a terrorist attack; it would likely occur too rapidly for an operator to have time to activate the isolation valves.
The impact of the loss of a compressor station would vary with season, the number of stations on the pipeline, and the location. During a seasonal peak period, the loss of one compressor station, assuming the pipeline itself was not interrupted, would cause a 25 percent reduction in flow. The duration of the disruption would depend on the components damaged or destroyed. Some components require long lead times for replacement or major repairs because they are not stocked as spare parts, given their high cost and reliability. The loss of two or three compressor stations in a series (or the first compressor station in the series) on any major pipeline could halt its operation for an extended period while repairs were being completed.
City Gates. City Gate stations are where local distribution companies (LDCs) receive gas from the transmission pipeline for their distribution systems. City Gates are essentially interconnections that are critical nodes in the system. The loss of a City Gate station can disrupt service to a large metropolitan area because typically little or no rerouting can be performed, especially during peak periods. City Gate patterns differ among LDCs. Smaller cities and towns may have one
City Gate connection, making that interconnection extremely important to those communities. Major cities such as Chicago may have six or more City Gate stations, which reduces the impact from a disruption at one station; however, during peak periods the disruption of even one City Gate would have the potential to take the whole system down. Today City Gates are often easily identified and poorly protected. Again, the only protection, typically, is a chain-link fence, and repair and restoration of a lost City Gate could take months. Meanwhile, the lack of gas supply—for instance, to a Northeastern city during a cold winter—could cause substantial numbers of illnesses, deaths, and economic hardship.
Similarly, pressure loss could disrupt service to the entire city for extended periods of time. And when service is finally restored, a significant problem would still exist. Every nonelectronic pilot light in the service area would have to be manually relit in order to avoid explosions.
Pipeline Control Systems. Natural gas pipelines typically are controlled remotely, often via microwave communication systems. The destruction of microwave towers could cause significant damage to gas pipelines. These important communication links for the control system are spread throughout the country, easily identifiable, and difficult to protect. Backup telephone control could be employed, but this would increase demand for staff to carry out the manual operations. Companies with sufficient redundancy in their communications/control systems may be less vulnerable to this type of attack.
SCADA equipment consists of sensors, computers, telecommunications links, and other mechanisms that allow station operators to monitor operating conditions and maintain control. Highly developed SCADA systems permit the remote control of valves and compressors. Loss of the SCADA system (or a cyberattack on it) could therefore have serious consequences for operations both on transmission pipelines and, increasingly, within the LDC’s territory.
Liquefied Natural Gas. LNG is produced by compressing and cooling natural gas into a liquid for easier transportation—typically by specially designed and built LNG tanker ships. Damage or leakage in an LNG tanker ship or land-based storage tanks could cause an explosion if gas vapors are ignited. The resulting large fire could cause additional fires and human casualties over a large area. Because of this danger, LNG ships and facilities are afforded special security and safety measures commensurate with the threat, and LNG port facilities are carefully designed and constructed to maximize safety. The U.S. Department of Transportation has regulatory oversight, including security authorization, over LNG facilities, so that, like nuclear power plants, they have significant safety and security programs.
LNG security regulations include standards for access control, perimeter protection, barrier strength, patrols, inspections, warning communications, monitoring systems, lighting/power needs, and personnel training and qualification
requirements. The facilities are equipped to handle natural disasters and some terrorist attacks.
Oil and Refined Products
The United States has over 600,000 oil wells, 161 oil refineries, 2,000 oil storage terminals, and about 74,000 miles each of crude and product transmission pipelines. Additional pipelines connect petroleum resources from Mexico and Canada, as well as from platforms and fields up to 100 miles offshore in the Gulf of Mexico, to U.S. storage and refineries. Almost all these assets are privately owned and operated (NPC, 2001). Recent trends in the industry have been toward consolidation, resulting in fewer but larger companies seeking greater efficiency and increased returns on their sizeable investments.
The most vulnerable components of the oil industry infrastructure are its refineries and pipeline pumping stations. Over 40 percent of the refining capacity in the United States is concentrated in Texas and Louisiana, and approximately 60 percent of the Northeast’s refined oil products come from these refineries, mostly by pipeline. Even with this concentration, however, a single attack on one component of the infrastructure would not be catastrophic. Offshore oil platforms are also inherently vulnerable to a number of attack scenarios; however the loss of a platform, while likely a spectacular event and a costly one for the crew and the owners, would not rise to the level of being catastrophic for the nation as a whole. Coordinated attacks on multiple key targets could have serious regional impact—including, under some conditions, many fatalities, but the probability of catastrophic impact is much less than in the electric and gas sectors because of the ability to store and import oil products and crude oil.
Representative Vulnerabilities
The physical vulnerabilities of the oil infrastructure are shown in Figure 6.2.
Refineries. Refineries are the centerpieces of the oil products infrastructure. They are complex sets of process units, many of which are custom-built for the task. Major process components, such as the crude distillation or catalytic cracking units, are one of a kind. If such units were lost through a terrorist attack, it could take months or years to rebuild them and bring them back on line. However, most large refineries are made up of several trains of similar process units. Thus in order to bring down an entire refinery for a long time, a highly coordinated attack would be required. Refineries are also vulnerable to attacks on other infrastructures. For example, their sensor and fire-suppression systems are generally reliant on the electricity and water infrastructures.
For institutional, environmental, and financial reasons, no new refineries have been built in the United States in recent years. One result is that the
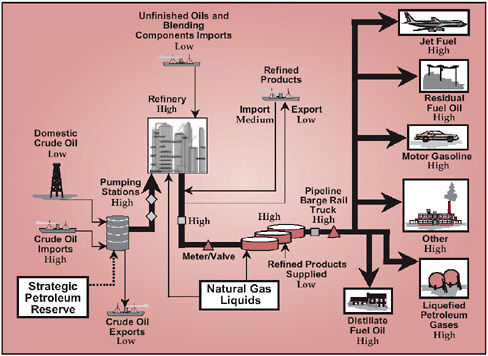
FIGURE 6.2 Oil system vulnerabilities. SOURCE: National Petroleum Council (2001), p. 33.
facilities in place are operating at 93 percent of capacity. Another is increased production at existing facilities. Refineries have, in many cases, installed equipment and tankage close to their fence lines. Meanwhile, some neighboring communities have allowed commercial and residential developments to be built right up to the other side of the fence. Problems within the refineries could directly affect many people. In particular, a few refineries have process units that use toxic chemicals. An attack on one of these units that ruptured one of the associated containment vessels could cause the release of a cloud of toxic gas, which could result in major loss of life. This is the most significant vulnerability of refining with respect to catastrophic terrorism.
Refineries are required to produce over 80 different blends of gasoline to satisfy the diverse environmental regulations throughout the country, making it difficult to replace a gasoline supply in a particular local area when an outage occurs. For example, California could face a fuel shortage following a coordinated attack on its refineries because there is limited ability to supply its uniquely specified fuels from other regions. This impact could be mitigated if the state and federal governments relaxed their location-specific fuel requirements in case of a catastrophic event.
Pumping Stations for Crude Oil and Refined Product. A coordinated attack on several key pumping stations for crude oil or refined products could lead to serious economic disruption. For example, a significant portion of the product used in the Northeast comes from the Gulf Coast by pipeline. Pumping stations are generally, but not always, unstaffed large facilities covering several acres. The pumps may be in the open or housed inside a sheet-metal building. Pumping stations are typically fenced, but they usually have no intrusion detection system. Unfortunately, because the main and backup power transformers for these sites are often colocated with the pumping station, all power supplies could easily be taken out at the same time.
Pumping stations tend to be remotely monitored and controlled through SCADA systems that communicate with a remote control center. The loss of a pump or other single component at a pumping station can usually be handled routinely with existing spares. However, the outage following a terrorist attack that destroys a large amount of equipment could last at least 4 months if replacement pumps and drivers are available, and perhaps 8 months to a year if they are not. In the meantime, supply at the end points of the pipeline would be greatly curtailed, although ships, barges, tank trucks, and trains might be employed to deliver essential products to those in greatest need.
Command, Control, and Communications. SCADA systems are vital to the operation of many facets of the oil business, including pipelines and refineries. SCADAs are particularly vulnerable to cyberattack because they were initially designed without consideration of security. At times, operators allow direct connections between a critical control network and the company’s local area networks or the Internet; intranets and the Internet are common vehicles for cyberattack, by insiders or outside hackers (Teumim, 2002). In addition, pipelines use radio-frequency and microwave systems to transmit data and to operate remotely. These wireless transmission systems are vulnerable to intrusion.
SCADA systems also are increasingly integrated into company business systems, making them even more accessible to cyberattack. The industry has not been exposed to the large-scale, sophisticated cyberattacks experienced by the financial sector and by government defense and intelligence agencies, but these may just be a matter of time. Some SCADA design companies and operators are introducing security elements into their SCADA systems to prevent intrusion, but wider application of existing security technology and development of more robust technology are needed.
In addition to cyberattack, physical attack on the pipeline or refinery control centers that house the SCADA systems would cause major disruptions, which could be very difficult to remedy quickly. The industry would also be vulnerable to disruptions caused by the loss of electricity and water supplies needed to run pipelines and refineries.
Implementation of Existing Technology
Implement Vulnerability Analysis to Identify Key Assets for Protection
The facilities of the oil and gas infrastructures are vast and complex, covering large geographic areas and involving numerous components. Tools for vulnerability assessment and prioritization of key assets in these systems must be used to ensure that owners’ limited resources are applied effectively. Such tools have been used extensively in the national security and defense communities, and it is recommended that they be aggressively directed to energy infrastructures as well (see Recommendation 6.2).
Create Incentives for the Deployment of Terrorist-Resistant Cybersystems
The oil and gas industries are dependent on cybersystems. Because these industries have not yet suffered the consequences of sophisticated cyberattacks, their expertise on high-security cybersystems is relatively undeveloped; until September 11, they had little incentive to consider the use of these often-expensive security measures. The situation has now changed, and the industries—along with their vendors, standard-setting organizations, and technology suppliers—need to develop and deploy more robust terrorist-resistant cybersystems (see Recommendation 6.9). A partnership with government, perhaps through the national laboratories, might be an appropriate way to pursue this goal.
Improve Dissemination of Information on Threats
Individual companies need timely information on potential attacks in order to take actions that deter them or minimize their impact. A reasonable balance is needed between corporate America’s need to know its own risks and the need to secure information for homeland and national security.
Industries, including oil and gas, need a mechanism such as an information sharing and analysis center for receiving and disseminating critical real-time threat information. In fact, the oil and gas industries are in the process of forming such a center. However, one consequence of the industry’s highly competitive nature is that industry members are often reluctant to share information with the government if by so doing that information may later be accessed and exposed through a Freedom of Information Act (FOIA) request. FOIA should therefore be modified to exempt information on critical-infrastructure protection (NPC, 2001). Members of the oil and gas industries are also concerned about antitrust and liability issues. All parties must realize that the business-as-usual environment of the past is clearly not suited to the defense of our homeland today, but companies will need to see some changes in government policy to be confident they can move forward without causing new problems for themselves (see Recommendation 6.3).
Provide for Emergency Federal Policy to Facilitate Recovery from a Catastrophic Shutdown of Oil and Gas Facilities
For example, carrying out existing crime-scene restrictions at the site of a gas-pipeline catastrophe could unduly delay emergency repairs. Another example is the large number (80+) of individual gasoline blends required to satisfy various local environmental regulations across the country. Requiring industry to replace all those blends lost in a terrorist attack on refineries or pipelines would seriously hinder recovery. Government and industry should identify and approve temporary measures—and put them in place prior to a catastrophic disruption in the supply—to permit emergency actions for a stipulated time that would facilitate energy-supply recovery (see Recommendation 6.6).
Harden Facilities by Deploying Known Technology
The science and engineering of security technologies have been extensively explored and applied by this country’s national security and defense communities. The oil and gas industries must now consider applying technologies as well. For example, pipeline systems nodes, junction points, compressor stations, and control centers could be hardened by applying known technology not normally employed by oil and gas operators before September 11. Moreover, as industries continue to assess their own particular vulnerabilities, whatever gaps exist and whatever additional R&D may be needed should become clearer. For example, R&D could reduce the cost of protecting key equipment (see Recommendation 6.4).
Reduce the Potential for Toxic Gas Emissions
Some refineries could release highly toxic chemicals in a gaseous cloud if a reactor were ruptured. Technology has been developed and is commercially available to mitigate this risk. In view of the higher threat level, the oil industry needs to reassess vulnerabilities in refineries where the new technology has not yet been applied.
Recommendation 6.18: In view of the increased threat level, oil refineries using process technology that could release toxic gases should be encouraged to install available technology to mitigate that risk.
Research and Development Priorities and Strategies
There is a variety of areas where new science and technology can help reduce or eliminate the impact of a terrorist attack on oil and gas systems.
Special-Purpose Sensor and Monitoring Systems
Oil or gas systems might be shut down for months or even years if particular critical processing units are damaged. Most refineries have capable perimeter security, while pipelines have only minimal security. In either case, there is a risk that intruders could gain access and detonate an explosive near critical equipment. New high-sensitivity devices for detecting explosive material need to be developed for use in oil and gas environments. Used in combination with communication and control systems, such devices could alert remote operators to a threat and the need to take mitigating steps. This research could be managed by DOE and should draw on current sensor-development work in universities and the national laboratories. Industry-unique issues could be integrated into this R&D, perhaps through such industry groups as the National Petroleum Council.
An alternative to the installation of many fixed-position sensors and support systems would be the use of robotic units with intelligence that could prowl the production units, testing for potential signs of attack. These robotic units could also make good use of video and manipulator systems to allow personnel to examine a suspicious object without risk of exposure. Robotics is further covered in Chapter 11.
Holistic Simulation and Operating Models
Oil and gas operations models need improvements to handle the threat of terrorist attacks. Holistic models should be developed that incorporate the complexity of interdependent systems (water and electricity, for example) and systemwide vulnerabilities to the newly recognized terrorism threat (see Recommendation 6.15). These models could improve the analysis of system vulnerability to attack and indicate (as well as expedite) the appropriate responses should an attack occur. Integrated multisensor warning systems (MWS) should be developed that would recognize unanticipated activities and provide real-time information to the holistic operating models.
Recommendation 6.19: Integrated multisensor warning systems (MWS) should be developed for the oil and gas industries in order to enhance response, control, and postevent analysis. These MWS would recognize unanticipated activities and provide information to new, holistic operating models.
Advanced control systems would take instructions from these holistic operations models to mitigate the consequences of an attack; for example, control equipment might isolate critical components of the network or reduce the volume of the hydrocarbon or chemical released. The modeling of individual facilities would best be conducted by the oil and gas industries themselves. The develop-
ment of models of the interdependencies of infrastructures, however, should leverage the work of the newly established National Infrastructure Simulation and Analysis Center, with industry involvement coordinated through a group such as the National Petroleum Council. Federal funding for this modeling, which might be managed by DOE, is essential.
High-Reliability System Instrumentation
Current instrumentation for monitoring the health of key systems (e.g., pipelines) is sometimes plagued with sensor failure or unacceptably high false-alarm rates. With terrorist attacks a realistic threat, the performance of these technologies must be improved. Tools for high-reliability system design, self-monitoring sensors to detect the onset of failure, and error-checking algorithms should be developed to transform these technologies so that they can provide real-time monitoring for reliable detection of an attack.
Recommendation 6.20: Tools for high-reliability system design, self-monitoring sensors to detect the onset of failure, and error-checking algorithms should be developed to increase the reliability of monitoring in the oil and gas industries.
This R&D would best be accomplished through a public–private partnership between industry and the federal government—specifically, DOE—with industry participation coordinated through a group such as the National Petroleum Council.
Advanced Intrusion Detection Systems
Improved surveillance techniques for the extended rights-of-way of pipeline systems are needed. The present method of monitoring thousands of miles of pipeline right-of-way—through visual inspection in an overflight—is inadequate. Pipeline operators need new surveillance techniques capable of highly reliable detection of unwanted activity. Surveillance technologies developed for defense and intelligence agencies may be useful in defending against terrorist attacks, as well as against simple right-of-way encroachments, on widely distributed oil and gas assets. These technologies could include remotely operated drone aircraft, satellite surveillance systems, intelligent-software-based analysis of surveillance images to scan for unwanted activity, change-detecting sensors, and intrusion-detection cables designed to sense unusual vibrations or noises (see Recommendation 6.11). Intrusion detection technology R&D could be managed through the existing DOD and DOE programs. Its application to the oil and gas industries could be coordinated by industry groups such as the National Petroleum Council.
Cybersecurity
The oil and gas industries must update security for their information technology and telecommunication infrastructures. Technologies are needed that could contain the impacts of an information system intrusion or cyberattack so that the complete system or dependent infrastructures remain relatively unaffected. Another focus should be identifying and managing risk to infrastructures and information, with emphasis on impact, consequences, and effect across multiple components and operators.
For example, in the energy industries, SCADA systems are increasingly being linked with other systems (such as electronic business systems) through the Internet, and they are thus becoming more vulnerable to cyberintrusion. The SCADA security issue is widely felt not only in the energy industries but in virtually all industries—in fact, in operating facilities of all types. Cost-effective solutions to SCADA security problems are therefore widely, and urgently, needed (see Recommendation 6.9). The public- and private-sector R&D aimed at broad application in this area should be leveraged to address unique issues of the oil and gas industries. As in other such endeavors, industry involvement could be coordinated through a body like the National Petroleum Council, with federal management through DOE.
The oil and gas industries are each made up of a few very large companies and many smaller companies. The large companies make some investment in R&D for security improvement, while the smaller companies typically do not. Even for large companies, however, it is difficult to justify investing in security R&D at the level society might desire or, given their highly competitive nature, to share their results. There is a need for government and industry to jointly share the cost and execution of the needed research and development. The government needs to share the security expertise it has with industry as appropriate, and this is an issue that pertains across the energy industry.
Recommendation 6.21: The federal government and the energy industry should together establish appropriate security goals. Building on this alignment, government should cooperate with industry to establish joint security-performance expectations and to define the respective roles and responsibilities of each in ensuring such performance. Industry should design the security measures and procedures needed to achieve the established security goals. Industry also should provide a mechanism to ensure that expectations will be achieved across the spectrum of firms in the industry.
REFERENCES
Ayres, Drummond. 2001. “Energy Chief Issues an Ultimatum on Power Lines,” Civil Engineering, December.
Badolato, Ed. Energy and Terrorism, forthcoming book to be published in 2002.
Bagli, Charles. 2002. “Seeking Safety, Manhattan Firms Are Scattering,” New York Times, January 29.
Clemmensen, J. 1993. “A Systems Approach to Power Quality,” Proceedings of Power Quality ’89, as cited in “Storing Power for Critical Loads,” IEEE Spectrum, June.
Electric Power Research Institute. 2001. Report by the Consortium for Electric Infrastructure to Support a Digital Society, “The Cost of Power Disturbances to the Industrial and Digital Economy,” EPRI Journal OnLine, July 23.
Energy Information Administration, Department of Energy. 2001. Annual Energy Review 2000, DOE/EIA-0384, Washington, D.C.
Loomis, William. 2001. “Super-Grid Transformer Defense,” presentation to North American Energy Reliability Council, Critical Infrastructure Working Group, Lake Buena Vista, Fla., December 10-11.
McIntyre, K.J. 1998. “By Holding Back, Power Company Pays: Mercury Energy Ltd.,” Business Insurance 32(29).
National Petroleum Council. 2001. Securing Oil and Gas Infrastructures in the New Economy, Washington, D.C., June.
Office of Technology Assessment. 1990. “Physical Vulnerability of Electric Systems to Natural Disasters and Sabotage,” OTA-E-453, U.S. Government Printing Office, Washington, D.C., June.
Oman, Paul, Edmund Schweitzer, and Jeff Roberts. 2001. Protecting the Grid from Cyber Attack Part I: Recognizing Our Vulnerabilities, November. See <www.pennet.com>.
Patton, A., C. Singh, D. Robinson. 1999. “N-area Reliability Analysis Techniques,” 13th International Power Systems Computation Conference, Trondheim, Norway, June.
Ragan, Patrick T., et al. 2002. “Chemical Plant Safety,” Chemical Engineering Progress, February, p. 62.
Teumim, David J. 2002. “Are Your Plants and Pipelines Safe from Cyber Attack?” Chemical Engineering Progress, February, p. 69.
U.S. Department of Energy. 2001. Critical Infrastructure Interdependencies: Impact of the September 11 Terrorist Attacks on the World Trade Center, Washington, D.C., November.

































