2
Indications and Warning Technologies
INTRODUCTION
Within the Army homeland security (HLS) framework, indications and warning (I and W) would be classed as a pre-event undertaking. I and W generally refers to the ability to detect events leading up to an attack. These events might involve enemy planning of the attack, its identification of targets of the attack, its acquisition of materials needed for the attack, its positioning of materials to carry out the attack, and, finally, its launch of the attack itself. Much of this is the province of the intelligence community within the civilian sector rather than of the Deputy Assistant Secretary of the Army for Science and Technology (DASA (S&T)). However, as materiel is moved so as to become an imminent threat to the Army, the science and technology (S&T) necessary to allow the Army to detect the presence of this material or its movement is the legitimate responsibility of DASA (R&T), as is the S&T associated with detecting the launch of the attack itself. In some cases the S&T resources necessary to meet these responsibilities reside with other agencies.
Since the Army will have a significant role in responding to any use of weapons of mass destruction (WMD),1 this study focused on the physical detection of or the movement of explosives (nuclear and conventional), radioisotopes, chemical agents, and/or biological agents and the identification of related S&T, which is cross-cutting in character. The Army is responsible for defending its own forces at home and abroad and will need to acquire the technology to do so
regardless of which agency is responsible for the development of that technology. For this reason, in the summary charts that follow some areas that are designated as very important to the Objective Force and to HLS are nonetheless assigned a low priority for the use of Army S&T funds. This does not necessarily mean that the expenditure of S&T funds for these areas has a low priority; rather, it often means that organizations other than the Army are responsible for the required S&T investments.2 The committee found cross-cutting technologies3 such as the networking of distributed sensors, data fusion and advanced materials that are strong contenders for Army S&T and that would also be of great benefit to the WMD detection problem.
The traditional I and W for threats to Army facilities have also been considered briefly. In many cases the current imaging sensors and other perimeter systems may be adequate as available; in other cases they are being improved through research and development (R&D). Signature analysis for terrorist activities is a very difficult problem from a purely S&T point of view. However, gains may be possible by using some of the cross-cutting technologies. Examples include face recognition algorithms embedded in image sensor processors. Alternatively, more complex processing could be embedded in sensors that are designed to dramatically enhance performance by drawing on novel bioinspired architectures and on large databases of known terrorists. The committee did not include the acoustic, seismic, and radio frequency (RF) sensors used for perimeter defense in this chapter, but it discusses them in other chapters.
The remainder of this section briefly summarizes technologies for detecting nuclear weapons and radioisotopes, conventional explosives, chemical agents, and biological agents, along with the relevant cross-cutting technologies. The study was of short duration, and the committee does not claim completeness. The scope of the S&T covered by this study is so broad that a complete analysis would be a massive undertaking. The approach was to illustrate the types of technology employed and the various stages of development by using a number of examples.
SENSOR TECHNOLOGIES
Traditional Imaging Sensors
The committee first mentions the advanced, high-performance imaging systems that infuse all aspects of national security and defense and also have rel-
evance for HLS in I and W as well as in denial and survivability (Chapter 3). High-performance sensors, which image in a broad range of spectral bands, are a high priority for numerous theater and national missile defense platforms. The Department of Defense (DoD) in general and the Army specifically have broad programs in imaging sensors. Applications in addition to infrared (IR) imaging—such as techniques for sensing threats due to harmful chemical and biological agents—may be incorporated in different sensor suites. These system applications would require narrow spectral discrimination over broad spectral bands, low-light-level detection, increased sensitivity, and the ability to perform multifunctional imaging.
Detectors with responsivity in the IR atmospheric transmission band are desirable for the detection of terrestrial sources against a 300 K background. The main detectors currently available or in research include the following:
-
HgCdTe imaging IR arrays,
-
Uncooled bolometer arrays,
-
GaAs quantum well arrays,
-
GeSi internal photoemission detectors,
-
GaSb intersubband and Type II detectors, and
-
GaN detectors.
In addition to the thermal sensors described above, the Army has relied very heavily on night vision goggles as a primary imaging technology to support night operations. These goggles are used both for target acquisition and navigation, including pilotage. As an image intensification device, night vision goggles rely on the amplification of ambient light, such as starlight or moonlight. The Army is currently working on the fourth-generation image intensification device, with each generation of device becoming progressively smaller and more efficient.
The Army has broad programs in most of the above-listed detectors, particularly the first three, and there is ongoing research for improving their performance as well as for studying the causes and modes of degradation and failure. DARPA has several ongoing programs in lasers and nitride detectors for the ultraviolet and solar blind regions. In a situation where chemical or biological agents have been released into the atmosphere, this technology may be significant for standoff chemical and biological detection, as biological agents in particular have very specific signatures of absorption or emission in the ultraviolet portion of the spectrum.4Table 2-1 describes traditional imaging sensors.
TABLE 2-1 Technologies for Perimeter Defense and Warninga
|
Technology |
Characteristics |
Availabilityb (R, N, F) |
Priority for Army S&Tc |
Multiused (H, O, C) |
|
HgCdTe imaging LWIR arrayse |
Material of choice to fabricate high-performance detector arrays. Energy gap can be tailored in the range from 1.4 to 20 microns. |
R |
High |
H, O, C |
|
Uncooled bolometer arrayse |
Utilizes temperature-dependent dielectric constants and operates at room temperature. BaSiTiO3 (BST) is ferroelectric below a Curie temperature (Tc) of nearly 300 K. Current devices are optimized for response in the mid- and long-wave IR band, but in principle future bolometers can be made with a wide variety of responses using different absorptive coatings. |
R-N |
High |
H, O, C |
|
GaAs quantum well arrayse |
A quantum well detector can be thought of as a type of extrinsic photoconductor in which the bound electrons reside inside the quantum wells instead of on dopant ions. |
R-N |
High |
H, O, C |
|
GeSi internal photoemission detectors |
Makes use of the high internal photoemission of the GeSi alloy. |
N-F |
Low |
H, O, C |
|
GaSb intersubband and Type II detectorsf |
Potential for tunability and design |
F |
Low |
H, O, C |
|
GaN UV detectors for solar blind applicationsg |
UV light selectively ionizes chemical agents. Ion detector determines concentration |
F |
Highh |
H, O, C |
|
NOTE: LWIR, long-wave infrared; UV, ultraviolet. aImpacts chemical and biological technologies. bAvailability: R, ready (TRL 8-9); N, near-term (TRL 4-7); F, far-term (TRL 1-3). cPriority for Army S&T (investment): low, someone else has mission or technology is ready and available; medium, useful but of limited impact and some investment needed; high, very important, no one else working on it, considerable investment needed. dMultiuse: H, Army homeland security; O, Objective Force; C, civilian (first responders and others). eWestervelt et al. (1991). fNRL (1998). gDARPA (2002a,b). hDoes not include acoustic, seismic, and radio frequency sensors, which are additional perimeter defense technologies. |
||||
In the process of collecting material for this chapter, data on the performance of many different sensors were examined. As one would expect, the performance or utility of individual sensor technologies was dependent on the environment in which they were used. This led to some confusion in comparing performance among sensors. A consistent methodology would be helpful for reporting the performance of sensors in the environments in which they will actually be used. It makes little sense, for example, to present data on the sensitivity of a particular diagnostic methodology without also presenting the trade-off with specificity.5 The NRC study Making the Nation Safer (NRC, 2002) calls for the following system-design approach:
-
Establishment of standards for response time and field stability/durability, for example, for detection of WMD;
-
Use of two-level sensor systems in which a low false-alarm-rate sensor with low specificity triggers a second sensor with a higher false-alarm rate but higher specificity;
-
Use of multiple sensors and reasoning algorithms to obtain lower overall false-alarm probability, to predict contamination spread, and to provide guidance for recovery actions; and
-
Use of networked sensors to provide wide-area protection of high-threat targets.
Conclusion 2-1. In conducting the survey it was often difficult to obtain authoritative and certified data on the real-world performance of many of the indicators and warning sensors in use or in development. This difficulty also applied to data on sensitivity and noise characteristics.
Recommendation 2-1. It is critically important that all sensors not only be well characterized at the point of purchase but also be regularly rechecked by competent technicians. Software used to integrate disparate sensors should be well documented and checked against standardized problems.
Chemical Agents
A number of different technologies are in use or in development for the detection of chemical agents. The agents are typically released by some means
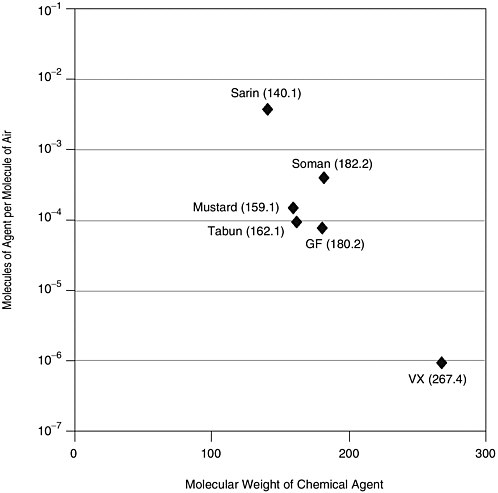
FIGURE 2-1 Vapor pressure concentrations for a number of chemical agents. SOURCE: Nerve agent data from Augerson (2000); mustard agent data from U.S. Army (undated).
into the atmosphere, where they form toxic clouds that are moved by atmospheric winds or by ventilation systems. The most desirable situation would detect these agents before they are released into the atmosphere. For weaponized agents this will be difficult. Figure 2-1 provides the vapor pressure concentrations for a number of chemical agents.
When compared with explosives, the chemical agents shown in Figure 2-1 are high-vapor-pressure substances. These concentrations will be easily detected with a number of technologies (however, VX will stress the state of the art for detection in realistic environments).
The acceptable exposure levels, however, are much lower than the vapor pressure levels. Figure 2-2 provides the atmospheric exposure limits (AEL) for a variety of chemical agents.
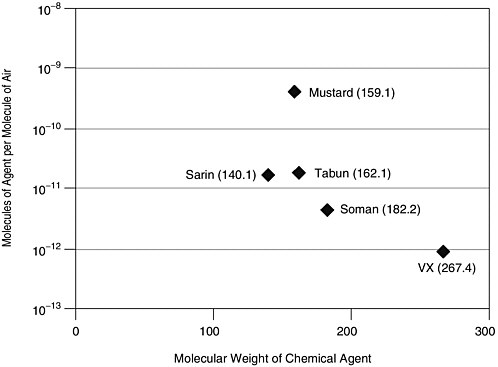
FIGURE 2-2 Atmospheric exposure limits for a variety of chemical agents. SOURCES: Nerve agent data take from Augerson (2000), CMS (undated); mustard agent data from U.S. Army (undated), CMS (undated).
These concentrations are more like those of the most-difficult-to-detect explosives, and one can expect similar problems with sensitivity and false alarms when operating in realistic, dirty environments. In clean environments where interfering substances can be kept to a minimum, the detection of trace amounts of chemical agents is more straightforward. Table 2-2 provides examples of means of chemical agent detection.
The use of industrial chemicals to cause harm should receive serious attention. If industrial chemicals are introduced into the atmosphere, they may be easier to detect than chemical warfare agents. At room temperature, chlorine, for example, has a vapor pressure an order of magnitude higher than air, while the vapor pressure of phosgene is about 50 percent higher than that of air; the vapor pressure of hydrogen cyanide is approximately the same as that of air, and the vapor pressure of methyl isocyanate is roughly half the vapor pressure of air. Also, because these chemicals are used routinely for industrial processing there is substantial experience in monitoring their presence at levels established by the Surgeon General as safe. The problem, of course, is that all of the monitoring is done in the industrial environments where these chemicals are expected to be present. Terrorists could employ these chemicals in locations where they would not be expected. This creates a sensor distribution problem.
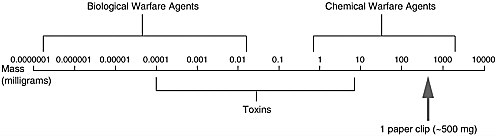
FIGURE 2-3 Comparative toxicity (amount needed to incapacitate) of biological agents, toxins, and chemical agents. SOURCE: NIJ (2001).
It should be noted that a number of these technologies also have relevance to the detection of conventional explosives and are therefore appropriate candidates for Army S&T investments for that purpose. Ion mobility spectrometry has broad application. The measurement presents a mass spectrum for fragments that are introduced into a drift chamber. Interpretation of this mass spectrum is where specific subject matter expertise comes into play. Interpretation of the spectrum for biological applications requires very different expertise than, say, interpretation of the spectrum collected in an explosives detection test. This technology could certainly be considered as cross-cutting in much the same sense that quantum dots technology is cross-cutting in its applications.
Biological Agents
The point detection of biological agents is qualitatively different from that of chemical agents. This is seen in Figure 2-3, which compares the amount of biological agent needed to incapacitate an individual with the amounts of chemical agent and toxin needed to incapacitate. Many orders of magnitude less biological agent is required.
Most devices for the physical detection of biological agents require that the agent be in the environment. A typical biodetection system involves a queuing, detection, discrimination, and identification sequence. This sequence requires that samples be purified and concentrated so that other species that could potentially interfere with detection of the target agent are reduced to a minimal level. Some of the technologies that are utilized or are under investigation for implementing this sequence are listed in Table 2-3.
There are many promising opportunities for investing S&T funding in support of biological agent detectors. Responsibility for this area, however, has been assigned to the Joint Project Office for Chemical Biological Defense. This limits the investment of Army S&T funding in this important area. There are, however, some undertakings also relevant to explosives detection and many other undertakings relevant to the Objective Force that are within the purview of the DASA (R&T) and that can help advance biodetection S&T. Some of these will be mentioned the next section.
TABLE 2-2 Technologies for Chemical Agent Detection
|
Technology |
Characteristics |
Availabilitya (R, N, F) |
Priority for Army S&Tb |
Multiusec (H, O, C) |
|
Enzymatic paper |
Detects nerve gas at ~ppb, HC at ~10 ppm, and mustard gas at ~ppb. Inexpensive, prone to false positives. |
R |
Low |
H, O |
|
Ion mobility spectroscopy |
Detects nerve gas at ~6 ppb and mustard gas at ~10 ppb. 1-2 minutes. Erroneous detection from interference, e.g., smoke. |
R-N |
Mediumd |
H, O, C |
|
Photo acoustic IR spectroscopy |
Highly selective. Sensitive to external vibration. |
R-N |
Mediumd |
H, O, C |
|
Differential absorption light detection |
Tracks identified clouds. Sensitive to environmental noise. |
R-N |
Low |
H, O, C |
|
Passive IR detection |
Direct measurement of IR emission or absorption from chemical agent cloud. |
R-N |
Low |
H, O, C |
|
Photo ionization |
UV light selectively ionizes chemical agents. Ion detector determines concentration. |
R-N |
Mediumd |
H, O, C |
|
Flame photometry |
Flame color determines concentration of sulfur and phosphorous. Highly sensitive. Prone to false positives. |
R-N |
Low |
H, O, C |
|
Gas chromatography |
Vapor separation through a column improves flame photometry. |
R-N |
Mediumd |
H, O, C |
|
Surface acoustic wave |
Surface absorption of chemical agents changes resonance frequency. Measures many chemical agents simultaneously. |
R-N |
Medium |
H, O, C |
|
NOTE: ppb, parts per billion; ppm, parts per million; UV, ultraviolet. aAvailability: R, ready (TRL 8-9); N, near-term (TRL 4-7); F, far-term (TRL 1-3). bPriority for Army S&T (investment): low, someone else has mission or technology is ready and available; medium, useful but of limited impact and some investment needed; high, very important, no one else working on it, considerable investment needed. cMultiuse: H, Army homeland security; O, Objective Force; C, civilian (first responders and others). dImpacts chemical and biological technologies. |
||||
|
SOURCE: Davis and Kelen (2001). |
||||
TABLE 2-3 Technologies for Biological Agent Detection
|
Technology |
Characteristics |
Availabilitya (R, N, F) |
Priority for Army S&Tb |
Multiusec (H, O, C) |
|
Measures relative number of particles in a given size range. Nonspecific, empirical. |
R |
Low |
H, O, C |
|
|
Measures relative number of particles in a given size range and discriminates between nonbiological entities and biological entities. |
R |
Low |
H, O, C |
|
|
Measures physical and chemical characteristics of cells. |
R |
Low |
H, O, C |
|
|
Pyrolysise |
Uses controlled rapid heating to decompose complex organic molecules into fragments that may have distinct chemical signatures. |
R |
Low |
H, O, C |
|
Mass spectrometryd |
Determines structure and molecular weight of biomolecule fragments. |
R-N |
Low |
H, O, C |
|
Gas chromatographye |
Separates components in gaseous mixture. |
R-N |
Mediumf |
H, O, C |
|
Ion mobility spectrometrye |
Measures ion drift times through buffer gas in drift tube. |
R-N |
Mediumf |
H, O, C |
|
Flame photometrye |
Measures phosphorus emission lines from gas-phase biomolecule fragments. |
R |
Low |
H, O, C |
|
Detects and measures specific binding of antigens with their corresponding antibodies or gene abundance. |
R-N |
Mediumf |
H, O, C |
|
|
DNA microarrays |
Monitors thousands of genes simultaneously. |
F |
Highf |
H, O, C |
|
Uses unique DNA structure of biological organism to identify pathogens and BW agents. |
R-F |
Low |
H, O, C |
|
|
Combinatorial peptides |
Uses massive libraries for screening. |
F |
High |
H, O, C |
|
Capillary electrophoresise |
Allows rapid separation of ions and subsequent detection of separated species. |
R |
Low |
H, O, C |
|
Ion channel switche |
Exploits selective movement of ions across biological membranes. |
F |
Low |
H, O, C |
|
Cell-basede |
Exploits electrical activity of cells to detect broad range of agents. |
F |
Low |
H, O, C |
|
Raman scatteringe |
Matches observed Raman spectra against library of predetermined signatures. |
N-F |
Highf |
H, O, C |
|
NOTE: BW, biological warfare; PCR, polymerase chain reaction. aAvailability: R, ready (TRL 8-9); N, near-term (TRL 4-7); F, far-term (TRL 1-3). bPriority for Army S&T (investment): low, someone else has mission or technology is ready and available; medium, useful but of limited impact and some investment needed; high, very important, no one else working on it, considerable investment needed. cMultiuse: H, Army homeland security; O, Objective Force; C, civilian (first responders and others). dNIJ (2001). eNATIBO (2001). fImpacts chemical and biological technologies. |
||||
Nuclear Materials
In the case of nuclear weapons, the primary fissionable isotopes of interest are uranium-235, plutonium-239, and uranium-233. Consider, for example, a plutonium weapon: the signatures from spontaneous decay processes will be gamma rays and neutrons, which are detectable at a distance. Assuming scattering but no neutron capture between the weapon and the detector, the weapon neutron flux from spontaneous fission will equal the background neutron flux at about 15 m from the weapon.6 If one wishes to detect at a longer distance the spontaneous neutron output from the plutonium weapon, one must deploy detectors capable of detecting excess thermal neutrons at levels below the background flux level. A similar situation exists for gamma radiation from plutonium. However, U-235 is more difficult to detect since it has a low spontaneous fission rate and therefore does not provide a strong neutron signal. It does have a low-energy gamma-ray emission spectrum with well-understood structure. This gamma-radiation emission spectrum is used for detecting and identifying U-235-based weapons. The detection range is quite limited due to the low gamma-ray energy and the natural background of gamma radiation. This problem has been studied for many years, and a variety of technologies have emerged, some of which are quite well understood and others of which are relatively new. Uranium-233 is of marginal interest because there is so little of it in the world. Table 2-4 describes technologies that are in development or currently used for the detection of neutrons and gamma rays in the nuclear weapons context.
The detection ranges for these technologies are relatively short, and they are best deployed in a choke point or a portal situation. This area is extremely important, but responsibility for conducting the appropriate S&T resides with the Department of Energy and the Defense Threat Reduction Agency (DTRA). As a result, the appropriateness of expending Army S&T funds was rated low. However, the impact of Army S&T investments in areas such as perimeter defense, miniaturized sensor technology, networked sensors, and data fusion could have a great influence on detection of nuclear materials.
The principal objective of a radiological dispersion weapon (“dirty bomb”) is to spread radioactive material by detonating a conventional explosive in proximity to the radioactive material or by spreading radioactive material as an aerosol. Any radioactive material could be used for this purpose. It is expected that the main source of such weapons would be materials used for hospital radiation therapy (such as iodine-125, cobalt-60, or cesium-137), radio pharmaceuticals (such as iodine-131, iodine-123, technetium-99, and xenon-134), or nuclear power
plant spent fuel rods, which contain fission products. These materials are principally gamma-ray emitters, and the detection would involve gamma-ray detection technologies such as those listed in Table 2-4.
All of the nuclear materials detectors mentioned above have relatively short detection ranges and are best suited for choke point or portal geometries or where there is good intelligence on where the material is located. The same will be true for the detectors of the other substances to be discussed in this section. It seems unlikely that the nation can afford to create, equip, and staff enough portals to make negligible the probability of dangerous materials entering the country.
Conventional Explosives
The majority of terrorist attacks against U.S. forces, facilities, and citizens have involved the use of conventional explosives. The detection and tracking of these explosives are therefore of great importance for HLS and are highly applicable to the Objective Force. Conventional explosive detection technologies generally fall into two categories: vapor-phase detection and bulk detection. Figure 2-4 provides some insight into the vapor pressures of the better-known explosives.
As can be seen from Figure 2-4, the vapor pressure of explosives varies over a wide range, with the older explosives having vapor pressures measured in parts per million (ppm) relative to atmospheric pressure and the more modern explosives having vapor pressures in the range of parts per trillion (ppt).
A number of technologies are under development to examine the feasibility of detecting the vapor phase of explosives. Table 2-5 describes examples of devices that work by such detection.
It should be quite clear from Figure 2-4 and Table 2-5 that for modern explosives, vapor-phase detection of explosives will be limited to detectors in close proximity to the explosives or will require very substantial concentration of the explosive vapors at a distance from the explosive. At these very low detection levels, interfering species will clearly be a big issue.
Army weapons and explosives in transit or in storage can be an attractive target for theft or diversion by terrorists. Surface-to-air missiles, antivehicle weapons, mines, and bulk explosives are particularly well suited for terror attacks. On a broader scale, it would be in the interest of the United States if international protocols were established that call for the insertion of detection markers7 and identification taggants8 into all legitimately manufactured explosives worldwide to assist both detection and forensic analysis. This was discussed in the NRC report Containing the Threat from Illegal Bombings (1998).
TABLE 2-4 Technologies for the Detection of Neutrons and Gamma Rays in the Nuclear Weapons Context
|
Functionality |
Technology |
Characteristics |
Availabilitya (R, N, F) |
Priority for Army S&Tb |
Multiusec (H, O, C) |
|
Passive gamma-ray detection |
Sodium iodide crystals and PMTd |
Robust, high false-alarm rate at high sensitivity, poor spectral resolution. |
R |
Low |
H, O, C |
|
Germanium crystalsd |
Sophisticated instrument, needs refrigeration, very high resolution (does not make mistakes). |
R |
Low |
H, O, C |
|
|
Mercuric iodidee |
Intermediate spectral resolution, solid state, robust, relatively expensive. |
R-N |
Low |
H, O, C |
|
|
CdZnTef |
Intermediate spectral resolution, solid state, relatively expensive. |
R-F |
Low |
H, O, C |
|
|
Passive neutron detection |
Silicon stripf |
Solid state, good energy resolution, 30ºC. |
F |
Low |
H, O, C |
|
Scintillating glass fibersh |
Robust, good energy resolution, room temperature. |
N-F |
Low |
H, O, C |
|
|
Scintillating glass fibersh |
Robust, solid state, fabricated to desired geometry. |
R-N |
Low |
H, O, C |
|
|
CMOS/SOId |
Relatively inexpensive, small, no database on utility in real world. |
N-F |
Low |
H, O |
|
Nonspecific particle counter |
Geiger counters, simple ionization chamberd |
Not specific, low sensitivity, relatively inexpensive. |
R |
Low |
H, O, C |
|
Neutron spectroscopy |
Pulsed neutron sourcei |
Sophisticated instrument, radiation hazard. |
R-N |
Low |
H, O |
|
Active gamma-ray scanner |
Pulse power or radioactive gamma sourcej |
Robust technology, radiation hazard, good spatial resolution and imaging. |
R |
Low |
H, O, C |
|
NOTE: PMT, photomultiplier tube; CMOS, complementary metal oxide semiconductor; SOI, silicon on insulator. aAvailability: R, ready (TRL 8-9); N, near-term (TRL 4-7); F, far-term (TRL 1-3). bPriority for Army S&T (investment): low, someone else has mission or technology is ready and available; medium, useful but of limited impact and some investment needed; high, very important, no one else working on it, considerable investment needed. cMultiuse: H, Army homeland security; O, Objective Force; C, civilian (first responders and others). dLBNL (2001); personal communications between R. Whitlock and R. August, U.S. Naval Research Laboratory, and Tim Coffey, Committ ee on Army Science and Technology for Homeland Defense, November 2001. eContech (2000). fLBNL (2002); personal communications between J. Kurfess, U.S. Naval Research Laboratory, and Tim Coffey, Committee on Army Scie nce and Technology for Homeland Security, April 2002. gLBNL (2002); personal communications between J. Kurfess, U.S. Naval Research Laboratory, and Tim Coffey, Committee on Army Scie nce and Technology for Homeland Security, April 2002. hNSSS (2000). iLBNL (2001) and Seymour et al. (1999). jSAIC (2002). |
|||||
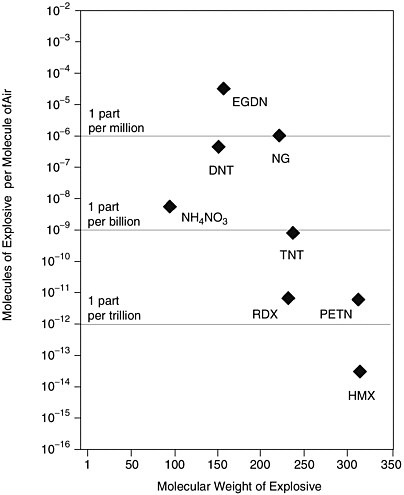
FIGURE 2-4 Vapor pressure associated with the better-known explosives. SOURCE: Adapted from NIJ (1999).
Modern explosives manufactured to include higher-vapor-pressure taggants will have longer detection ranges. The inclusion of such markers will, of course, make military explosives somewhat easier to detect, which may have implications for operational security (OPSEC). However, since the black market in military explosives is of concern to HLS, the OPSEC implications of markers may represent an acceptable trade-off.
Conclusion 2-2. Technologies should be pursued that (1) deny theft or diversion by maintaining real-time inventory control, then tracking if control is lost or (2) reduce the utility of such equipment to terrorists. Incorporation of detection markers and identification taggants into all legitimately manu-
TABLE 2-5 Technologies for Vapor-Phase Explosive Detectors
|
Technology |
Characteristics |
Availabilitya (R, N, F) |
Priority for Army S&Tb |
Multiusec (H, O, C) |
|
Detects at parts per billion level. Must be close to explosive or chemical. Noise limits become a problem at low signal levels. Fundamental problem in selectivity and resolution. Shows promise for increased detection in low concentrations. |
R-N |
Medium |
H, O, C |
|
|
Detects at parts per billion level. Must be close to explosive or chemical, needs improved SNR. |
N |
High |
H, O, C |
|
|
Fluorescent polymersd |
Detects at parts per trillion level (in principle). Must be close to explosive or chemical, needs improved SNR. Demonstrated at parts per billion in reliable system. |
R-N |
High |
H, O, C |
|
Detects at parts per billion level. Must be close to explosive or chemical, must be able to desorb the explosive vapors for system to be useful. |
R-N |
Medium |
H, O, C |
|
|
Surface-enhanced Raman spectroscopyd |
Detects at parts per billion. Portable, must be close to explosive. |
N-F |
High |
H, O, C |
|
Immunoassay (biosensors)d |
Detects parts per billion. Must be close to explosive. Potential for increased sensitivity. |
N-F |
High |
H, O, C |
|
NOTE: SNR, signal-to-noise ratio; SAW, surface acoustic wave. aAvailability: R, ready (TRL 8-9); N, near-term (TRL 4-7); F, far-term (TRL 1-3). bPriority for Army S&T (investment): low, someone else has mission or technology is ready and available; medium, useful but of limited impact and some investment needed; high, very important, no one else working on it, considerable investment needed. cMultiuse: H, Army homeland security; O, Objective Force; C, civilian (first responders and others) dWard et al. (2001). eLewis et al. (1997). fBruschini and Gros (1997). gU.S. Navy (2002). |
||||
factured low-vapor-pressure explosives will assist in both detection and forensic analysis.
Recommendation 2-2. An international convention requiring the incorporation of detection markers and identification taggants should be sought.
Bulk-phase detection of explosives generally involves some form of interrogation of the explosive. All of the systems require close proximity to the material being interrogated. Table 2-6 describes examples of bulk explosive detection.
Conclusion 2-3. The physical detection of dangerous packaged materials (nuclear weapons, radiological weapons, chemical weapons, biological weapons, and explosive weapons) is an extremely difficult and stressing task, even when the materials are forced through choke points.
CROSS-CUTTING TECHNOLOGIES
It is quite clear that the great majority of technologies for the physical detection of nuclear weapons, radiological weapons, conventional explosives, chemical agents, and biological agents require close proximity to the weapon. Detection of chemical or biological aerosol clouds at a distance is possible. However at that point, the attack is already under way. Similarly, the use of health and medical surveillance, while very desirable, is a post-attack undertaking. The most desirable indication and warning would signal the presence of dangerous material before an attack has begun. While efforts should continue to improve pre-event detection ranges for individual sensors, it is clear that the laws of physics, chemistry, and biology will impose severe limits on these ranges. This would seem to leave two options for the physical detection of dangerous materials:
-
One option is to force all material to move through choke points or portals. This will bring the detectors and the dangerous materials into proximity, thereby easing the burden on detector technology.
-
The second option would involve distributing large numbers of detectors, making it difficult to avoid detection by avoiding choke points and portal systems. This second option would require inexpensive detectors that can be widely proliferated. It would also require sophisticated networking of the detectors and the development of systems to intelligently interpret the data provided by them.
The distributed network would involve fixed sensors and mobile sensors deployed on various platforms, including autonomous unmanned air, space, ground, and underwater vehicles. This option opens up substantial opportunities for the investment of Army S&T resources because the S&T involved is appli-
cable to the Army for more than just nuclear weapons detection or chemical and biological agent detection. For example, the intelligent networking of sensors involves S&T that cuts across many applications of interest to the Objective Force, including perimeter defense, tracking, identification, and targeting. Similarly, the S&T needed to develop inexpensive small sensors for wide proliferation would involve studies that are much broader than those specific to HLS. Indeed, the most significant advances in detection technologies may come from the innovative combination of very disparate technologies into compact integrated sensor suites. The S&T for the required autonomous unmanned sensor platforms is of great interest to the Objective Force and will have an important impact. Learning how to do all of this will be of very broad interest to the Army.
In addition to existing or anticipated ideas for detection, the committee thought it worthwhile to highlight more speculative means for detection in Box 2-1.
There are many examples where cross-cutting technologies have had an impact well beyond that initially envisioned. Consider the case of fiber-optic sensors. These were originally developed by the DoD to provide for the sensitive detection of acoustic, magnetic, and strain signatures. In one variation, these detectors utilize evanescent field excitation, whereby a portion of the light traveling in the fiber core penetrates the surrounding medium with the power of the evanescent field decaying exponentially from the fiber core. Through a clever combination of surface chemistry, biological or chemical receptors can be bound to the surface of the cladding. By introducing a fluorophore into this arrangement and monitoring the change in fluorescence that occurs when specific binding takes place at the surface of the fiber it was possible to create a fiber-optic detector for certain chemicals and biological entities. This is an example where S&T developed by DoD for purposes having nothing to do with chemical or biological detection has made an important contribution to the detection of biological agents.
As another example, consider the S&T that has been supported by DoD in semiconductor quantum-dot nanocrystals. These quantum dots have been shown to have emission spectra that may be tuned by changing the quantum-dot radius. For example, quantum dots may be fabricated so that a 2-nanometer particle glows bright green while a larger 5-nanometer particle glows red in the presence of white light. These developments originally had nothing to do with the detection of chemical or biological agents, but the dual-use potential was found through clever chemistry. The utility of this approach is limited by the efficiency of the immunoassay or the DNA identification technique. It remains to be seen whether or not a viable detection system can be developed for quantum dots.
It should be clear from the above discussion that the cross-cutting technologies could have a broad impact and should be of very great interest to the DASA (R&T). Some examples of relevant cross-cutting technologies are shown in Table 2-7.
TABLE 2-6 Technologies for Bulk Explosive Detection
|
Technology |
Characteristics |
Availabilitya (R, N, F) |
Priority for Army S&Tb |
Multiusec (H, O, C) |
|
Portal system provides 2-D images. |
R |
Low |
H, O, C |
|
|
Transmission gamma raye |
Portal system provides 2-D images. |
R |
Low |
H, O, C |
|
Backscatter x-raye |
Finds low-atomic-number elements (C, H, O, N). Requires close proximity and sophisticated interpretation. |
R-N |
Low |
H, O, C |
|
X-ray and gamma-ray tomographye |
Portal system provides 3-D images. |
R |
Low |
H, O, C |
|
Portal system: capture of thermal neutron by nitrogen gives 10.8 MeV gamma ray. |
R-N |
Low |
H, O, C |
|
|
Fast neutron analysis (FNA)e |
Portal system: stimulates gamma radiation from elements being irradiated. |
R-N |
Low |
H, O, C |
TABLE 2-7 Examples of Cross-Cutting Technologies
|
Application |
Technology |
Characteristics |
Availabilitya (R, N, F) |
Priority for Army S&Tb |
Multiusec (H, O, C) |
|
Detection and tracking |
Sensor networking (see Box 2-1) |
Gathers data from a wide variety of spatially distributed sensors. |
N-F |
High |
H, O, C |
|
Sensor fusion |
Intelligently combines, correlates, and interprets data from distributed sensors. |
N-F |
High |
H, O, C |
|
|
Anomaly detection |
Examines data from networked sensors to discover patterns, unusual behavior, etc. |
N-F |
High |
H, O, C |
|
|
Surveillance platforms (UAVs, UGVs, UUVs) |
Small autonomous vehicles for carrying sensor payloads as part of distributed sensor network. |
R-F |
High |
H, O, C |
|
|
Perimeter surveillance |
IR, RF, acoustic, seismic, etc. techniques |
Monitors for intrusion into predetermined spaces (encampments, facilities, borders, etc.). |
R-N |
High |
H, O, C |
|
BOX 2-1 Speculation on Means of Detection Using the Existing Telecommunications Infrastructure The committee notes in Table 2-4 that glass fibers subjected to gamma radiation near background levels scintillate. Although the scintillation is weak, it is detectable and the effect is used to detect gamma radiation. The telecommunications industry has introduced a good deal of glass fiber into the country’s infrastructure. Those fibers that are above ground undoubtedly exhibit some level of optical noise due to the gamma radiation background. This background radiation level will increase if a gamma radiation source approaches the fiber. If this were detectable, then the telecommunication optical fiber infrastructure might itself serve as a distributed network of gamma-radiation detectors. As another example, consider the fact that the natural background of thermal neutrons has been shown to cause single-event upsets in microelectronics. The thermal neutrons interact with the boron-10 fraction of boron dopants, producing alpha particles. The energy deposited by the alpha particles causes the upsets. Perhaps this effect could be exploited to produce a highly distributed thermal neutron detection system by incorporating a special boron-doped chip in cell phones. When a phone “shakes hands” with a cell tower, it could pass a neutron anomaly message and its GPS coordinates, if equipped to do so. If something like this were feasible it would result in a worldwide distributed network of thermal neutron detectors. |
SUMMARY
A new approach is required for the indication and warning stage for chemical, biological, radiological, nuclear, or high explosive weapons. There are many opportunities for the Army S&T program to help in defining that new approach. The new approach might involve the proliferation of small but competent sensor systems into some sort of intelligent network. Exploitation of the nation’s existing infrastructure should be examined. Such an undertaking would require expanding the community currently working on indications and warning. The collective skills of this community might enable a new class of detector system that makes it difficult to position terrorist weapons so that they are a threat to U.S. forces or to the general population. This distributed sensors approach offers many important opportunities for investigation by the Army S&T program.
The Army’s role in funding S&T for detectors of CBRNE weapons is very limited. There are, however, numerous opportunities for synergy among legitimate Army S&T investments and the investments of others in detector technologies. This is especially true of cross-cutting technologies.
Many important contributions to I and W sensor capability are likely to come from developments in fields not traditionally associated with CBRNE weapons
or the detection thereof. The stovepipe communities,9 funding agencies, and funding mechanisms that have been set up in CBRNE weapons areas, while very effective in cases where it is known how to solve a problem, can be counterproductive in this situation.
The interrelationships needed among the sensor networks and for the broader intelligence collection activity are difficult to establish, for technical, cultural, and legal reasons. Nevertheless, the committee envisioned a situation where the relevant sensor networks would be queued as a result of intelligence findings, with the intelligence community tasked to undertake focused collection efforts if the sensor networks picked up unusual activity. There are serious scientific and technical questions here even if the cultural and legal issues can be resolved. For example, the ability to quickly and reliably search massive databases for anomalous activity would be critical for the implementation of this recommendation. It may be necessary to create a research organization to resolve this problem, and it is unlikely that any one institution can take this on. A consortium approach might work, but it would be confronted by serious if not insurmountable security classification problems.
Conclusion 2-4. A purely technical solution to the indications and warning problem based upon sensors, even networked sensors, is unlikely. Establishing the proper interrelationships among the sensor networks and the broader intelligence collection activity will be crucial for properly queuing the sensor network.
Recommendation 2-4a. The Army should ensure from the outset that the necessary interrelationships among the sensor networks and the broader intelligence collection activity are established and maintained as a coherent undertaking.
Recommendation 2-4b. Army science and technology should aggressively seek out and invest in those cross-cutting sciences and technologies that will benefit both the Objective Force and the homeland security requirement to detect weapons of mass destruction.
REFERENCES
Augerson, W.S. 2000. A Review of the Scientific Literature as it Pertains to Gulf War Illnesses, Volume 5: Chemical and Biological Warfare Agents. Available online at <http://www.rand.org/publications/MR/MR1018.5/MR1018.5.pdf/>. Accessed on October 10, 2002.
Bruschini, C., and B. Gros. 1997. A Survey of Current Sensor Technology Research for the Detection of Landmines. Available online at <http://diwww.epfl.ch/lami/detec/susdemsurvey.html>. Accessed on September 24, 2002.
CMS (CMS Field Systems). Undated. Chemical Warfare Agent Air Monitoring Systems. Available online at <http://www.nbcindustrygroup.com/cms.htm>. Accessed on October 10, 2002.
Contech (Constellation Technology). 2000. Mercuric Iodide Detectors. Available online at <http://www.contech.com/Mercuric_Iodide_Catalog..htm>. Accessed on September 24, 2002.
DARPA (Defense Advanced Research Projects Agency). 2002a. Semiconductor Ultraviolet Optical Sources (SUVOS). Available online at <http://www.darpa.mil/mto/suvos/index.html>. Accessed on October 2, 2002.
DARPA. 2002b. Solar Blind Detectors. Available online at <http://www.darpa.mil/MTO/SBD/index.html>. Accessed on October 2, 2002.
Davis, G., and G. Kelen. 2001. CBRNE-Chemical Detection Equipment, October 15. Available online at <http://www.emedicine.com/emerg/topic924.htm>. Accessed on September 23, 2002.
LBNL (Lawrence Berkeley National Laboratory). 2001. Nuclear Science—A Guide to the Nuclear Science Wall Chart: Tools of Nuclear Science. Available online at <http://www.lbl.gov/abc/wallchart/teachersguide/pdf/Ch12-toolsofNuclear%20Sci%20doc.pdf>. Accessed on September 24, 2002.
LBNL. 2002. Radiation Detectors Capabilities. Available online at <http://engineering.lbl.gov/cap/capdetail.asp?CapCode=RadDet>. Accessed on September 24, 2002.
Lewis, N.S., M.C. Lonergan, E.J. Severin, B.J. Doleman, and R.H. Grubbs. 1997. Array-based vapor sensing using chemically sensitive carbon black-polymer resistors. Pp. 660-670 in Detection and Remediation Technologies for Mines and Minelike Targets II, Proceedings of SPIE, vol. 3079, A.C. Dubey and R.L. Barnard, eds. Bellingham, Wash.: The International Society for Optical Engineering.
NATIBO (North American Technology and Industrial Base Organization). 2001. Biological Detection System Technologies Technology and Industrial Base Study, February. Available online at <http://www.dtic.mil/natibo/>. Accessed on September 23, 2002.
NIJ (National Institute of Justice). 1999. Guide for the Selection of Commercial Explosives Detection Systems for Law Enforcement Applications, NIJ Guide 100-99, December. Washington, D.C.: National Institute of Justice.
NIJ. 2001. An Introduction to Biological Agent Detection Equipment for Emergency First Responders, NIJ Guide 101–00, December. Available online at <http://www.ncjrs.org/pdffiles1/nij/190747.pdf>. Accessed on September 23, 2002.
NRC (National Research Council). 1996. Airline Passenger Security Screening: New Technologies and Implementation Issues. Washington, D.C.: National Academy Press.
NRC. 1998. Containing the Threat from Illegal Bombings: An Integrated National Strategy for Marking, Tagging, Rendering Inert, and Licensing Explosives and Their Precursors. Washington, D.C.: National Academy Press.
NRC. 2002. Making the Nation Safer: The Role of Science and Technology in Countering Terrorism. Washington, D.C.: National Academies Press.
NRL (Naval Research Laboratory). 1998. InAs/InGaSb Infrared Lasers and Detectors. Available online at <http://sinh.nrl.navy.mil/code6870/reprints/las&det.PDF>. Accessed on October 2, 2002.
NSSS (Nuclear Safeguards and Security Systems LLC). 2000. Why Neutrons. Available online at <http://www.nucsafe.com/puma/why_neutrons.htm>. Accessed on September 24, 2002.
SAIC (Science Applications International Corporation). 2002. Portal VACIS™ Technical Specifications. Available online at <http://www.saic.com/products/security/portal-vacis/portal-vacistech.html>. Accessed on September 24, 2002.
Seymour, R.S., R.A. Craig, M. Bliss, B. Richardson, C.D. Hull, and D.S. Barnett. 1999. Performance of a neutron-sensitive scintillating glass fiber panel for portal, freight, and vehicle monitoring. Pp. 148-155 in Nuclear Waste Instrumentation Engineering, Proceedings of SPIE, vol. 3536, D.E. Robertson, ed. Bellingham, Wash.: The International Society for Optical Engineering.
U.S. Army. Undated. U.S. Army Center for Health Promotion and Preventive Medicine Detailed Facts About Sulfur Mustard Agents H and HD. Available online at <http://chppm-www.apgea.army.mil/dts/docs/dethhd.pdf>. Accessed on October 10, 2002.
U.S. Navy. 2002. Department of the Navy Explosive Detection Equipment Program–Explosives. Available online at <http://explosivedetection.nfesc.navy.mil/explosives.htm>. Accessed on September 24, 2002.
Ward, K.B., A. Ervin, J.R. Deschamps, and A.W. Kusterbeck. 2001. Force protection: Explosives detection experts workshop, NRL/MR-MM/6900—01-8564, CDROM. Arlington, Va.: Office of Naval Research.
Westervelt, R., J. Sullivan, and N. Lewis. 1991. Imaging Infra-red Detectors. JASON report number JSR-91-600. McLean, Va.: Mitre Corporation.





























