Cybercrime and Cyberterrorism
Mikhail P. Sychev*
N.E. Bauman Moscow State Technical University
The world community has entered the age of the information boom. Modern civilization is directly dependent on new telecommunications technologies, which are used in almost all spheres of human activity. The development of information technologies, with the irrevocable changes they have brought in the ways people live and interact, has also displayed a negative side by reducing society’s confidence in the inalienable right to the protection of privacy. Each of us is becoming increasingly dependent on the information circulating in global computer networks, on its reliability, protection, and security.
The Internet began to be created in the 1970s. In 1998, 143 million people had access to it, and by 2001 the number of users had reached 700 million. The Internet first appeared in Russia in August 1990. The country is experiencing a computer boom, and although it lags significantly behind developed foreign countries, the Russian segment of the Internet already has about 6 million users.
The development of information and network technologies has led to the appearance of so-called cybercrime. Although the term cybercrime is not yet established in Russian law, the concept has become firmly established in practice. The category of cybercrime could include unauthorized access to computer information; the creation, use, and distribution of malicious computer programs (including via the Internet); disruption of the normal operations of computers or information networks; illegal seizure of information resources; illegal sale and distribution of special-purpose radioelectronic devices; forgery of documents with the help of computer technologies; distribution of unlicensed computer software; financial machinations over the Internet; and several other crimes. The
common characteristics of such crimes include the following: As a rule they have no physical manifestations, and they are distinguished by a high degree of latency, that is, they occur undetected, which according to expert assessments reaches 85 to 90 percent in Russia.
Cybercriminals are using various types of attacks that allow them to penetrate corporate networks, seize control over them, or block exchanges of information. They also use computer viruses, including network worms, which modify or delete data or block the operation of computer systems; logic bombs, which are activated under certain conditions; or Trojan horses, which send various data from an infected computer to their “owners” over the Internet.
The weapons of cybercriminals are constantly being improved, and their tools for mounting information attacks are becoming increasingly refined. In the future, we can expect to see new nontraditional types of network attacks and computer crimes.
Today, such new concepts as information security and, more precisely, network security have entered our lives. For example, the first known virus transmitted over the Internet, HAPPY-99, appeared in January 1999. It is believed (although not officially proven) that this virus, which affected the entire global network, appeared first in Russia and was created to obtain access to the passwords of customers of many Western banks.
The U.S.-based Computer Security Institute has reported that in 1999 about 90 percent of major firms and governmental organizations surveyed had discovered security violations of their computer systems. Furthermore, 70 percent of these firms and organizations noted that these violations were the result of intentional actions by criminal elements working over the Internet. According to the results of a poll of 273 organizations, it was determined that their financial losses totaled more than $265 million, or an average of about $1 million per organization. The survey also found that attacks by hackers against major companies increased by 79 percent from July to December 2001.
In April 2001 a Russian hacker broke into the Internet server of a company in the U.S. city of McLean, Virginia, that provides online banking services. He demanded to be paid not to distribute the confidential data and to destroy them instead. According to information from leading research firms, the worldwide volume of damage from malicious programs totaled about $14.5 million in 2002. But, as many companies often hide the real extent of the damage, it could easily be double that figure.
In October 2002, American intelligence services reported on the most serious attack on root DNS (Domain Name System) servers in the history of the Internet. According to information from the National Infrastructure Protection Center of the U.S. Federal Bureau of Investigations, during the attack, 7 of the 13 servers managing global Internet traffic stopped responding to user requests, and the operation of two other servers was intermittently interrupted. The root servers had been targeted to receive an enormous number of incorrect requests,
and as a result, they were forced to handle a volume 30–40 times higher than normal. There were no serious disruptions to the Internet only because the duration of the attack was short, just one hour. However, if a longer attack were to occur or a greater number of root servers were to fail, the normal operation of the Internet could be disrupted. Among the computers most affected by the root server attack were those at the Information Center of the U.S. Department of Defense. Outside the United States, root servers failed in Tokyo and Stockholm. As the Russian group SecurityLab learned, the attack on the DNS servers was carried out by the Russian hacker ech0, a former member of the Nerf Security Group. This was not the first act of sabotage by the Nerf Security Group against the United States. In September 2002 they broke into the website of the U.S. Department of State, an attack that was initially thought to be a terrorist act on the part of Osama bin Laden.
In March 2003 a U.S. hacker temporarily managed to “occupy” the website of the official Iraqi news agency INA, placing calls for the overthrow of Saddam Hussein on one of its pages. Computer hackers thought to be from Brazil gained access to Cuban websites and posted comments directed against U.S. President George W. Bush and the possible war against Iraq.
Also in March 2003 an unknown hacker pretending to be Finnish Prime Minister Paavo Lipponen used his electronic mail address to inform the president of Russia of Finland’s intention to take back Karelia, sending copies of this message to the international media and various diplomatic posts. A note at the bottom of the message indicated that its contents were not to be taken seriously.
Hackers are sometimes considered modern technical hooligans. By joining together in groups, hackers are becoming more dangerous and could bring down not only isolated websites but also entire zones of the Internet. Organized crime groups are increasingly using the capabilities of the Internet to carry out swindling operations in e-commerce and the credit and financial sphere and to provide information support for drug trafficking. Also becoming increasingly widespread are extortion attempts in the registration of domain names coinciding with the names of well-known political and governmental figures and major firms and companies. A sharp increase is forecast in the number of such crimes owing to the increasing numbers of Internet users.
A particular concern is that global computer networks present unique new opportunities for facilitating the laundering of proceeds from criminal activity. This phenomenon is manifested in the creation and operation of so-called virtual banks. The main problem is that such banks operate with very little control or oversight, and it is not always clear where crimes involving them are committed. The virtual blackmail industry is also broadly developed on the Internet, and blackmail often subsequently leads to racketeering. Online casinos are generally chosen as targets for such crimes, since as a rule they bring in substantial profits for their owners. On the Internet, everything happens just as it does in “real” life. A group of hackers attacks a casino site during its most profitable hours and
issues an ultimatum to the management. If they refuse to pay, the hackers will begin attacking with enviable persistence, and in the end, the online casino owners usually submit.
Cybercrime is growing exponentially, as illustrated by data from the CERT Coordination Center (see Figure 1). It would be possible to attempt to predict that already in 2003 the number of incidents involving computer security violations will exceed 170,000, essentially equal to the number of incidents recorded by CERT for the entire information collection period beginning in 1988.
Meanwhile, according to CERT data, the number of computer system bugs also continues to increase (see Figure 2). It is predicted that almost 7,200 such bugs will be found during 2003. Attacks on computer systems have become so frequent that after the widespread circulation of the LoveBug virus, the Pentagon decided to adopt a special InfoCon virus threat scale analogous to the DefCon scale for military threats or ThreatCon for terrorist threat. In the opinion of military experts, this will help to coordinate efforts in an emergency.
The world community is fully conscious of the level of potential consequences from the threat of cyberterrorism, and as a result, representatives of European Community member states as well as the United States, Canada, and Japan signed the International Convention on Cybercrime in November 2001. This convention defines cybercrime as crimes committed in the information en-
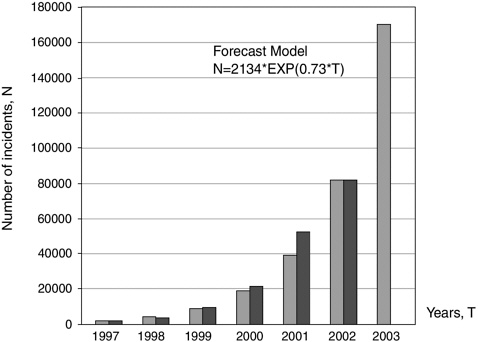
FIGURE 1 Trends for incidents involving computer security violations.
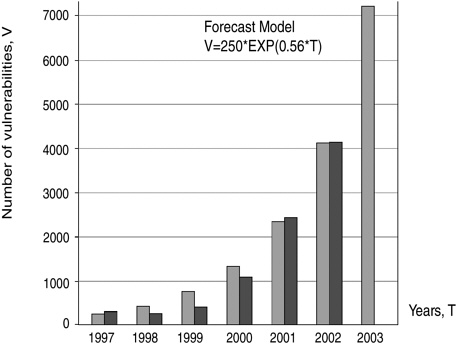
FIGURE 2 Trends for the number of computer system bugs.
vironment, against information resources, or with the help of information technologies.
With the aim of intensifying the struggle against cybercrime, the convention calls for close cooperation among law enforcement agencies in the various countries and assigns them very broad powers. However, in the opinion of several experts, the individual articles of the convention in fact assign too many powers to these agencies. As a result, certain difficulties could arise in getting states with more liberal laws to adhere to it.
Obviously, the situation in Russia is not yet so tense because its computer networks are far less developed, but soon it will escalate significantly, and we are well aware of the realities of the modern cybercriminal world. The first hackers appeared in Russia in 1994. The first and most famous Russian hacker was Vladimir Levin. He managed to penetrate the seemingly impervious security system of the American company Citibank. In 2002, Russia already registered 3,371 computer information-related crimes, with more than 90 percent of these being crimes related to unauthorized access to information resources, or so-called computer break-ins. American intelligence services caught up with Levin in 1994, and he spent five years in an American prison.1 However, under Russian legislation Levin was not guilty, for at that time Russia had no laws covering computer crimes.
The Criminal Code of the Russian Federation now includes articles establishing penalties for types of crimes that were previously not described. Chapter 28 of the code, Crimes in the Computer Information Sphere, consists of three articles outlining the penalties for unlawful access to computer information (Article 272); creation, use, and dissemination of malicious computer programs (Article 273); and violation of rules for the operation of computers, computer systems, and networks (Article 274). It should be noted that these articles of the criminal code do work. For example, in 2001 alone, the number of crimes registered under articles 272–274 increased by almost 150 percent over the level recorded in 2000.
Cybercrime is not limited only to crimes committed over the Internet. It is increasingly impacting all types of crimes committed in spheres where information, information resources, and computers represent targets, means, or tools for crime. If crimes are planned and committed with the aim of violating public security, frightening the population, or pressuring the authorities to act in a particular way, then their intent, execution, and results are in full accord with the definition of terrorist acts and are typical manifestations of a fundamentally new type of terrorism—cyberterrorism.
In accordance with the general definition, terrorism is the intentional or targeted use of violence or threat of violence to force society, the state, or the government to meet the political, economic, religious, or ideological objectives of a terrorist organization. A terrorist act entails an emotional impact on public opinion, engenders sentiments of fear and panic in society, leads to the loss of trust in the authorities, and ultimately causes political instability. Terrorism is a political crime directed against the interests of the public and the security of the state, society, and individual citizens.
Unfortunately, the general concept and specific elements of cyberterrorism are not fully covered in either the Russian Criminal Code or Russian Federation Law No. 130-FZ on Combating Terrorism (July 25, 1998), even with the amendments and additions made after the events of October 2002 in Moscow.
There are various interpretations of the term cyberterrorism. It is often difficult to make a clear distinction between cybercrime and cyberterrorism. Nevertheless, cyberterrorism differs from other criminal forms of action in cyberspace primarily in its goals, which are those common to political terrorism in general. The cyberterrorist differs substantially from the hacker, computer hooligan, or computer thief, whose actions are motivated by greed or hooliganism. The main tactics of cyberterrorism include ensuring that this form of cybercrime has dangerous consequences, is well known by the population, has broad public resonance, and creates an atmosphere that threatens repetition of the act without identifying a particular target. Cyberterrorism is oriented toward using various forms and methods of knocking out the information infrastructure of a state or using the information infrastructure to create a situation producing catastrophic consequences for society and the state.
It must be noted that this form of terrorism has its own special characteristics. It creates a particular concern that extremist groups, separatist forces, and proponents of ideas contrary to universal human values are striving to make intensive use of modern cutting-edge information technologies to promote their ideologies and achieve their goals. As a result, we can already speak of cyberterrorism as presenting a real threat of a new form of terrorist activity to individual countries and to the world community in general.
Given the current growing number of acts of international terrorism, which presents a danger to people’s lives and welfare, threatens the peace and security of all states, and undermines trust in the state authorities, it is vitally important to provide protection against this type of criminal activity. Therefore, a heightened level of international cooperation is now needed for scientific research on preventing and suppressing acts of cyberterrorism.
Most importantly, scientific research is needed to develop a unified conceptual framework. Further review and corrections are also needed regarding laws, regulations, and other legal documents on this type of crime, including those governing international activities. Research work aimed at creating modern technologies for detecting and preventing network attacks and neutralizing criminal actions against information resources is of the highest significance. Of course, all of this is impossible without improvements in the multitiered system for training personnel in the information security field.
Finally, another important scientific problem faced by the international community is that of developing the scientific and methodological foundations for joint research projects on countering cybercrime and cyberterrorism.







