1
Technology and Applications
Identification is a powerful capability, useful in classifying, counting, and organizing objects. These operations are essential to many aspects of modern life, including manufacturing, the logistics of distribution, and the various stages of supply chains, and they operate on scales ranging from the level of the individual consumer to that of global trade. In the past, identification was done visually—by observing characteristics of objects. When copies of manufactured objects that are essentially identical have to be identified, distinguishing markings have been added. Efficient and accurate means are needed to recognize the markings and thus determine the identity of the marked objects. Therefore, an identification system consists of identifying markings and readers of those markings. The first readers were human beings; technical innovations subsequently resulted in photodetectors, cameras, and lasers being used as readers. The markings have evolved into the popular bar code that is printed on almost every package and item.
Radio frequency identification (RFID) is a means of identifying objects by interrogating a unique characteristic of the object (such as a unique identifying number stored on a silicon chip attached to the object) using radio waves.1 This technology promises orders-of-magnitude greater efficiency and accuracy than were possible previous technologies. Although RFID is not a recent development,2 advances in semiconductor technology have now made this method practical and much more cost-effective. RFID has many advantages over visual markings—primary among them the ability to identify objects without the requirement of line of sight. This means that objects can be identified even when they are tightly packed together or their surface markings are removed, marred, or obscured.
The elements added to objects to facilitate identification in this way are called RFID tags. Tags consist of at least two basic subsystems: (1) a memory element that holds an identification
|
1 |
For more background information on RFID, see Roy Want, 2004, “RFID: A Key to Automating Everything,” Scientific American, January, pp. 56–65. See also Brian Dipert, 2004, “Reading Between the Lines: RFIDs Confront the Venerable Bar Code,” EDN Magazine, October 14, available online at <http://www.edn.com/index.asp?layout=articlePrint&articleID=CA468418>, accessed December 14, 2004. |
|
2 |
Indeed, one workshop participant argued that RFID has been around since 1886, with Hertz’s experiments in radio frequency propagation over a 1 meter range and developed into its first practical application in a half-ton tag used to identify friend or foe in aircraft in 1942. For comparison, bar codes were invented at Drexel University in 1948 and started becoming practical in 1962 with the advent of laser readers for codes printed with inexpensive ink. See also Harry Stockman, 1948, “Communication by Means of Reflected Power,” in Proceedings of the IRE [Institute of Radio Engineers], October, pp. 1196-1204, for an early description of the theory and implementation of RFID. |
number (a string of binary values) or some other identifying characteristic, and (2) an antenna to radiate or reradiate radio frequency (RF) energy, modulated by the identification number, to an apparatus that can detect that modulation and thus the identification value. Many variations of these two elements are possible, giving RFID tags quite a wide range of capabilities, as discussed below.
RFID VARIABLES
This section provides an overview of some of the components of an RFID system. It is important to note that, although many variations are available in each of the elements of an RFID tag, the variations are not necessarily available in all combinations. For example, a tag that can be read from a long way off will most likely require its own power source; a tag with no battery may be limited to a range of a few tens of meters. Some of the parameters to consider when evaluating or analyzing RFID systems are power requirements, the method of coupling between readers and tags, the receiving sensitivity and power output of antennas, the power requirements of the RFID tag chip (if the identifying tag uses a chip), and the frequency of operation. Several choices are usually available for each of these parameters, but the field of available tags is not simply the outer-product of all these options, because some combinations are not technically feasible or cost-effective.
Tags
The Basic RFID Tag
The simplest version of an RFID tag is a passive identification (ID) tag. It does not contain its own power source but instead harvests the power it needs from the reader’s RF emissions.3 It holds only a unique identifier and no other state information. When a reader reads the tag’s ID, it typically uses the ID to index a database that contains more expansive information about the object. For example, a tag on a package of pharmaceuticals may point to a database entry about the provenance of the drugs in the package, the distribution history of the package, and its final destination. As another example, electronic-article surveillance (EAS) systems currently employed extensively in libraries use the physical characteristics of a magnetic ribbon to backscatter a unique signature.
The coupled design of the reader and the tag antenna determines the range at which the tag’s ID can be read. Since this basic RFID tag is entirely dependent on getting power from the reader, the range with today’s technology tends to be quite limited, varying from near contact (so-called contactless technologies—such as some smart cards) to a maximum of about 15 meters (for many of the tags currently in supply-chain trials). Other complications in the reading process include the presence of multiple tags, interference from other radio sources (and in particular other readers), the absorption of radio energy by different materials between the tag and the reader,4 and the fact that reader transmission power is limited by regulatory bodies (see below).
For certain frequencies of operation, particularly problematic barriers between tags and readers are metal and water (present in large quantities in human bodies), making it difficult to tag many individual items found in supermarkets.
Tags with Extended Memory
Expanding the memory capacity of an RFID tag allows the object to store data about itself in addition to its ID. Extended memory is a particularly useful capability when a tag is read by a reader that is not connected to a database of information about that tag. This disconnection might be due either to limited network connectivity or limited access (for example, as a result of being in a different administrative domain without access rights to that database).
Tags with Sensing Capability
Adding even a simple sensor to an RFID tag can radically increase its utility. Even if only a single bit of the tag’s data comes from an integrated sensor, it can radically change usage models. For example, a sensor to detect whether a package has been opened can be as simple as a thin wire that gets cut when the package is opened, thereby toggling a bit in the tag’s identifying number. A temperature-threshold sensor can inform a reader that a tag at some point reached a temperature higher than recommended—a useful capability in food and drug distribution.
Tags with Their Own Power Sources
Enhancing the communication range of RFID tags opens up many more applications. Enhancing range can be most easily accomplished by giving tags their own power sources. Of course, the capacity of the batteries used will have a large impact on the usage models for this class of tags. Depending on how often a tag is asked to transmit, its local battery may last anywhere from days to years. However, a self-contained power source allows the tag to have more interesting sensors that, in addition, can be used even when the tag is not near a reader to repeatedly sample some aspect of the environment at regular intervals.
Tags That Can Communicate with Other Tags
At the opposite end of the spectrum from basic tags that can only supply an ID to a reader are RFID tags that can communicate in a peer-to-peer fashion under their own power. These (along with some kinds of tag readers) can be thought of as nodes of a sensor network (the subject of a recent study by the National Research Council’s Computer Science and Telecommunications Board5).
Tag Costs and Materials
Today’s RFID tags vary in cost from a fraction of a U.S. dollar (read-only, passive tags) to several hundred U.S. dollars (active tags with their own power source and sensing capability). Tag costs are dominated by the interconnection of the silicon chip and antenna and their assembly into a package. They can weigh fractions of a gram (consisting of a small silicon chip and a thin antenna on mylar substrate). Ranges vary from 0.02 meter to 1 meter for near-field tags, to 15 meters for far-field tags, and up to 300 meters for high-end active tags, with every range in between also available. The antenna is the largest component of a tag. Tag antennas vary from less than a millimeter for the smallest passive tags (in this case the tag is on the silicon chip) to dozens of centimeters for some far-field tags. Most antennas are made of flexible material,
|
|
more common. With half-duplex, readers and tags do not talk simultaneously; rather, readers talk and tags listen, or vice versa. |
allowing some shaping to different form-factors. Other tags are packaged in epoxy or glass containers so that they can be subjected to washing or injected into animals.
Technologies Adjacent to Tags
Technologies adjacent to RFID tags include the following: sensor networks whose nodes are similar to active tags; contactless smart cards, which are similar to near-field tags but have a bit more processing power; and bar codes, the cheapest tagging technology (just ink on paper). Which sorts of tags or sensors to use is an important consideration for application developers. Variables that should be taken into account include these: read range, orientation independence, operating frequency, multitag reading (rather than one at a time), fast read rates (for example, tags that can function while traveling at high speeds, as when paying highway tolls automatically), resilience to ambient noise and interference, readability when tags are concentrated in a small space, reliability, and maintenance cost (which can vary over a wide range for all tag types, but especially for active tags). Not all of these characteristics are achievable to the desired degrees; some still fall within the realm of open research problems.
Although the difference between peer-to-peer tags and sensor network nodes is not sharply defined, certain characteristics of RFID tags usually distinguish them from sensor network nodes. RFID tags tend to communicate directly to readers (in a star pattern) and do not emphasize the routing of data through a network of peer nodes, as in ad hoc sensor networks. Usage models for tags do not rely on extensive computational capability within the tag itself; instead the reader is expected to provide a conduit to large-scale computational and storage resources. In sensor networks, nodes may be required to cache large amounts of collected data and elaborate them (often with complex digital signal processing algorithms) before communicating summary results to other nodes.
As indicated above, the term RFID is used to refer to a large spectrum of tag capabilities. Clearly, such a wide range leads to a need to standardize so that there is some hope for interoperability between large sets of tags and readers. As discussed in the section below entitled “Standards Bodies and Standards,” early work toward standardization was begun by the International Organization for Standardization (ISO) and by the Massachusetts Institute of Technology’s (MIT’s) Auto-ID Center. The Auto-ID work is now being carried on by an industry consortium known as EPCglobal. EPCglobal has developed a taxonomy of tag classes (see Box 1.1), as well as standard RF signaling protocols between tags and readers, and formats for the storage of identity and data in tags.
Readers and Reader Infrastructure
Readers are the elements complementary to tags in RFID systems, as described in the subsections below. Readers must match the specific needs of tags and act as arbitrators when more than one tag is within their range. Readers communicate with tags and act as the tags’ gateways to other information systems, such as databases that provide data indexed by the read identity. Readers must also coordinate among themselves at multiple levels, as they may interfere with one another’s transmissions when they are in close proximity and need to share the spectrum. Also, they need to get the data that they read to the appropriate destinations so that the data are consistent when accessed by applications—which may involve transferring data from reader to reader as though the readers were nodes in a larger network.
|
BOX 1.1 Within 900 megahertz (MHz) radio frequency identification (RFID), the Auto-ID Center created the following class structure. Although this structure has not been formally adopted by the International Organization for Standardization (ISO), its use is continuing within EPCglobal, an industry consortium. A brief overview of this structure was presented at the workshop and is summarized below. Class-1: Identity Tags (normative) Class-1 identity tags are passive-backscatter read/write tags with the following minimum features:
Class Restrictions (normative) Class-2, Class-3, Class-4, or higher class tags shall not conflict with the operation of, nor degrade the performance of, Class-1 tags located in the same radio frequency environment. Higher-Class Tags (informative) The following class descriptions provide an example of how higher-class tag features might be delineated:
|
Readers of Basic Tags
Reader antennas are designed to radiate energy to tags. For tags that contain an integrated circuit, the tag’s power-harvesting elements must be able to collect enough energy to power the tag’s chip and modulate the reflected signal. The reader must be sensitive enough to pick up this returned signal and interpret it. It is important to note that in passive tags the returned power falls off as the fourth power of the distance, that is, proportionally to 1/d4, where d is the distance from the reader to the tag. This is because the tag returns only some of the power that reaches it. Thus, the typical 1/d2 falloff of RF power is squared—meaning that to double the distance from reader to tag requires 16 times the power—because the RF transmissions must go round-trip.
Limiting factors on readers include the following: the amount of power that the reader can radiate (it is government-regulated), the reader’s receive sensitivity (it is cost-sensitive), the reader’s antenna gain (government-regulated), the size of the tag’s antenna (there are cost and size considerations), the power requirements of the tag (they involve silicon processing), and constraints on the silicon fabrication process (there are engineering and cost considerations). Thus, there are three major classes of limits: (1) those imposed by the government for reasons of safety and spectrum allocation to reduce interference, (2) cost and size considerations based on the uses of the RFID system, and (3) engineering of the silicon and RF designs to make them more efficient in using power and lower in cost.
Each of these classes of limits can have a substantial impact on the design of RFID systems. For example, the operating frequency and bandwidth restrictions in different parts of the world mean that the same type of tag can be read at a rate of 500 tags per second in the United States but at a rate of only 200 tags per second in Europe. Thus, readers are limited by local standards because they generate RF emissions, whereas passive tags typically can work anywhere because the interrogating reader governs their backscatter transmissions.
Reader antennas can be quite sophisticated. Although some antennas try to capture all tags within a regular hemisphere, most are designed to have gain in a particular direction. Directionality enables the reader to focus its energy in a region of interest. The narrowness of the beam determines the angular accuracy. The speed of the identification protocol limits the number of tags that can be read per second and how quickly they can be moving.
Readers employ an arbitration protocol to identify each of a group of multiple tags sequentially. Various arbitration protocols are used in practice, including probabilistic slotted-Aloha, slotted-Aloha with random temporal backoff, deterministic binary-tree traversal, multi-bit deterministic tree traversal, and combinations of these protocols. Reader interference remains a challenge. Because, as described previously, reader signals decay as a square of the distance while passive tag returns decay as a quadratic, there is a fundamental problem in having high densities of readers. Thus, readers may ultimately require operating models that very carefully mitigate interference, just as must be done in multiple-access radio systems.
Readers for Tags with Memory and/or Sensing Capability
Besides reading more data from the tags, readers designed for tags with additional memory and/or sensing capability need to have additional capabilities themselves. One consideration is that of writing tag memory. Tags will most certainly not allow any reader to write into their memories (possibly destroying the data that were there). Thus, some security measures for tags, such as memory locking and password protection, must be in place. Some tags already have their memory arranged in sections with independent access control, so that one organization’s readers can access one area while another organization uses a different area. How
these access rights and passwords are managed is an important issue for the information systems that manage the readers.6
Another consideration in this area is that readers of sensor-enabled tags may be thought of as nodes in a sensor network. They can communicate with multiple tags within their operating range. The tags can provide many sensor readings that can be aggregated and forwarded through the sensor network. Thus, readers may take on the properties and requirements of sensor network nodes.
Readers for Active Tags
Readers for active tags have a range proportional to 1/d2 rather than 1/d4, because these tags have power of their own to use in transmission. To get twice the range between readers and active tags, power output must typically increase only by a factor of 4, rather than by a factor of 16 as for passive tags. Readers and active tags are thus much more comparable in their communication systems, as the communication needs are equivalent. Tags may use a lower transmitting power to conserve energy when communicating with other tags if their usage allows a shorter peer-to-peer range. Readers of active tags can also operate as nodes in a sensor network or simply provide one more communication hop as a gateway between a tag-based sensor network and the information infrastructure.
Today’s reader costs are typically on the order of $100 to $1,000 for near-field readers reading passive tags and $1,000 to $2,000 for far-field readers reading active tags. Costs are likely to decrease rapidly, as the technology is likely to experience large economies of scale. (However, considerable uncertainty surrounds these future economies.) Antenna sizes can be quite small (1 centimeter) for near-field tags, but as large as 0.3 meter to 1.0 meter for some far-field technologies. Active tag readers have antennas comparable in size to those of tags—on the order of a few centimeters.
In summary, readers are the highly regulated elements of RFID systems. They must meet constraints imposed on their frequency of operation and their power output. Thus, they can be limited in the number of tags that they can read per unit of time and in the range at which they can communicate with tags. Active tags provide a way of boosting communication range, but at the same time they make tags more expensive (by requiring a battery) and possibly create a maintenance issue (battery replacement) if the lifetime of the tags needs to be longer than their period of use in a particular scenario. Readers carry out the crucially important function of connecting tags to the information infrastructure and thus to end-user applications.7 How these data are communicated between sources and destinations can make the system quite complex, as the paths may often require connecting across network administrative domains. (This is especially the case in supply-chain management, where tagged packages move from manufacturer to transportation system to distribution center to a possibly different transportation system and, ultimately, to a retail outlet). Finally, readers may need to coordinate among themselves when their ranges overlap, so that they do not interfere with one another’s abilities to communicate with tags.
|
6 |
For more on RFID and security, see S. Sarma, A. Weis, and D. Engels, 2003, “Radio Frequency Identification: Security Risks and Challenges,” RSA Laboratories Cryptobytes, 6(1), pp. 2-8, available online at <http://www.rsasecurity.com/rsalabs/cryptobytes/CryptoBytes_March_2003_lowres.pdf>, accessed December 14, 2004. |
|
7 |
In some cases, it might make sense to instrument the environment with a multihop sensor network of tag readers and to have the tags themselves do less. This arrangement would help increase the longevity and robustness of the tags. It could be extended further by accommodating mobile elements of infrastructure (that is, mobile readers that join, and leave, and rejoin more connected pieces of the reader-tag-sensor-network infrastructure). |
COORDINATING CAPABILITIES AND SYSTEM CONSIDERATIONS
The day is rapidly approaching when every manufactured object could contain an RFID tag of some type. But just because this could be done does not mean that it would make sense to do so. The type of tag, if any, that is most appropriate for a particular use depends on many factors. It is important to reiterate that not all of the properties of tags discussed so far can be found in combination. For example, tags that do not have their own power sources cannot collect sensor data and communicate with other tags.
Figure 1.1 shows, along the horizontal axis of the graph, the range of assets that may require identification. These assets vary from an individual item on a store shelf to a trainload or airplaneload of material. Clearly, a single, higher-cost tag is more appropriate for a plane or truck. An active tag with Global Positioning System (GPS) capability is quite appropriate for these uses: it can be reused and easily maintained; it tags thousands of items as a group. At the other end of the scale, individual consumer items are likely to be tagged with bar codes for the foreseeable future. Even if a tag costs only a few cents, it is difficult to justify except for more expensive items with sizable profit margins. Of course, the value proposition may change in the future as new usage models emerge and consumers possibly become willing to pay the additional costs of tagged items.
Choosing a tag type does not depend solely on the value of the tagged asset. Properties of the reader-tag combination also play an important role. The read range and orientation sensitivity (the latter is sensitive to both the cost and design of the receiver circuit) are probably the most important concerns. Reader density is another important consideration. If fine-grain tracking is required, more readers need to be deployed at smaller intervals. One common case is that assets are tracked only at choke points, such as at warehouse loading docks or on truck beds. Other possibilities include tracking items at the level of a store shelf to enable automatic inventory control.
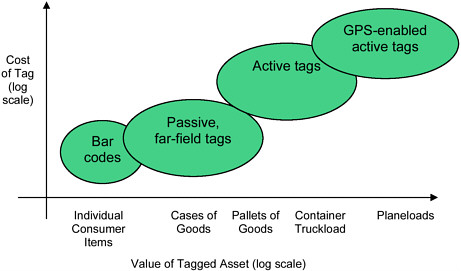
FIGURE 1.1 The types of tags appropriate for different types of assets. Both the vertical scale of tag cost and the horizontal scale of asset value are logarithmic.
What happens to tags as they move through the supply chain is also important. Some tags end up at home with consumers. Tag readers could continue to see such tags wherever customers take the items. It is possible that privacy considerations will require that tags be decommissioned at the retail counter so that they are no longer functional when customers leave the store. What happens to tags on cartons and cases? If not well managed, they could end up polluting the environment—not only physically, but also electromagnetically, by their signals.8 Today, most tags used in the fast-moving consumer goods market have a password-protected kill feature that can permanently disable a tag.
Location is closely coupled with identification. Readers with GPS capabilities that can record their own locations and movements have already been mentioned. This type of reader is likely to be a very popular, although of course GPS capability increases cost.
An interesting adjacent technology for active tags is WiFi (a type of wireless network). The idea is to use WiFi (802.11x) access points as readers. These devices are rapidly gaining ubiquity as wireless networks spread around the planet. They can serve a dual purpose in gathering IDs from tags and reporting their approximate locations—within WiFi range. WiFi-based active tags are already beginning to be marketed commercially. However, as indicated by the focus of discussions at the workshop, and thus much of this report, far-field passive tags are garnering greater attention as they are nearing deployment in supply-chain management both for large retailers and governments.
STANDARDS BODIES AND STANDARDS
As described previously, RFID systems comprise readers and tags along with a back-end infrastructure for data management. Because RFID readers and tags communicate using electromagnetic waves, they are classified as radio systems. RFID systems do not generally have allocated frequency bands, but tend to use the unlicensed frequency ranges classified worldwide as ISM (Industrial-Scientific-Medical) or SRD (Short-Range Devices). As RFID systems become more prevalent, there may be a need to revisit the issue of dedicated spectrum for them, because large-scale RFID deployments may eventually monopolize the ISM or SRD bands.9
When contemplating RFID systems, it is important to realize that radio frequency regulatory requirements are not uniform worldwide. Consequently, RFID tags and readers that cross international boundaries must meet the “lowest common denominator” of competing national and international regulations.10 RFID standards have traditionally been developed using
|
8 |
One possible solution to tag pollution might be to design the reader signals to receive significant responses only from classes of ID sequences of interest (for example, clothing, not food), by having a taxonomy of product types. This could also partially mitigate some surveillance concerns: The reader would collect information only on classes of objects that it is authorized to scan. Other information would never enter the database. |
|
9 |
For more on the challenges of spectrum allocation and spectrum policy, see the Computer Science and Telecommunication Board’s ongoing study on wireless technology prospects and policy options online at <http://cstb.org/project_wireless> and its associated workshop report: National Research Council, 2004, Summary of a Forum on Spectrum Management Policy Reform, The National Academies Press, Washington, D.C. |
|
10 |
The following documents are useful for understanding the range of worldwide regulatory requirements: ISO/IEC (International Organization for Standardization/International Electrotechnical Commission) 18000-1, “Air interface, Part 1—Generic parameters for air interface communications for globally accepted frequencies.” ISO/IEC 18000-6, “Air interface, Part 6—Parameters for air interface communications at 860–930 MHz.” ISO/IEC 3309, “Information technology—Telecommunications and information exchange between systems—High-level data link control (HDLC) procedures—Frame structure.” ISO/IEC 19762-3, “Information technology AIDC techniques—Harmonized vocabulary—Part |
the International Organization for Standardization process. For example, ISO developed the ISO 18000-6A and 18000-6B 900 megahertz (MHz) ultrahigh frequency (UHF) standards, which are used worldwide. In 1999, a joint industry–academic effort at MIT, the Auto-ID Center (for Automatic Identification) created two 900 MHz non-ISO protocols that have met with commercial success. EPCglobal, an outgrowth of EAN International and the Universal Code Council,11 formally took over the commercialization of these protocols from the Auto-ID Center in October 2003. The Auto-ID Center was renamed the Auto-ID Labs and continues its academic effort in advancing RFID technology.
The two protocols are named EPCglobal Class-0 and Class-1 (see Box 1.1 for more information). Unfortunately, for technical and regulatory reasons these protocols are not suitable for adoption as international standards, so EPCglobal undertook to develop a single, worldwide UHF RFID standard, termed Class-1 Generation 2 (Gen2 for short) to replace them. The Gen2 standard was promoted to candidate specification on October 1, 2004, and is expected to be ratified by EPCglobal in December 2004. The SC31 subcommittee within the ISO has already announced that it will incorporate Gen2 into its existing 18000 structure as ISO/IEC 18000-6c as soon as Gen2 is formally ratified by EPCglobal.
The 900 MHz UHF band is rapidly emerging as the preferred RF band for supply-chain applications, primarily for reasons of read speed and range (see Box 1.2 for other RFID frequency bands and standards). Whereas passive 13.56 MHz tags can be read at rates from 10 to 100 tags per second and at a range measured in centimeters, passive 900 MHz UHF tags can be read at rates from 100 to 1,000 tags per second and at a range measured in meters. Specifications under development, such as EPCglobal’s Gen2, will push the read rates above 1,000 tags per second and the read/write range beyond 10 meters. Further driving the adoption of 900 MHz RFID are the mandates from giant retailers Wal-Mart, and Target, from the Department of Defense, and from others that require suppliers to use RFID for tracking and inventory control starting in 2005.
The 900 MHz RFID is not, however, without limitation—indeed, 900 MHz RFID has far greater problems with signal fading due to multipath effects (interfering reflections of the signal that cause adjacent regions to vary dramatically in reception) and signal attenuation by liquids and metals than does 13.56 MHz RFID. But workshop participants observed that regardless of these issues, supply-chain applications are poised to accelerate the adoption of 900 MHz RFID, and with that acceleration, it is hoped, some solutions to these problems may emerge.12
|
|
3: Radio frequency identification (RFID).” U.S. Code of Federal Regulations (CFR), Title 47, Chapter I, Part 15, “Radio frequency devices, U.S. Federal Communications Commission.” European Telecommunications Standards Institute (ETSI), EN 302 208, “Electromagnetic compatibility and radio spectrum matters (ERM)—Radio frequency identification equipment operating in the band 865 MHz to 868 MHz with power levels up to 2 W, Part 1—Technical characteristics and test methods.” European Telecommunications Standards Institute (ETSI), EN 302 208, “Electromagnetic compatibility and radio spectrum matters (ERM)—Radio frequency identification equipment operating in the band 865 MHz to 868 MHz with power levels up to 2 W, Part 2—Harmonized EN under article 3.2 of the R&TTE directive.” EPCglobal™ (2004) EPC™ Tag Data Standards Version 1.1, Rev. 1.24. |
|
11 |
See the Web site <http://www.ean-ucc.org/> for more information. Accessed December 17, 2004. |
|
12 |
It should be noted that most of the standards work under discussion addresses a range of technical specifications as described here. However, these standards do not necessarily address all possible usage models—such as data mining. Some kinds of uses involve more than just tags and readers—that is, they involve the entire system within which the RFID technology is embedded, resulting in vendor-specific implementations. |
|
BOX 1.2 The most common radio frequency identification (RFID) frequency bands and the standards associated with their usage are the following:
NOTE: HF denotes high frequency; UHF, ultra-high frequency; KHz, kilohertz; MHz, megahertz; GHz, gighertz. RFID systems also operate at other frequencies, including 433 MHz, 5.75 GHz, and others, but those that use the frequency ranges listed above are the most common. |
In North America at least, RFID systems and their components have some unique features that are not shared by other users of the ISM band, including dense deployment (eventually hundreds of readers in a retail store), passive backscatter with spectral content usage across international boundaries (that is, tags must work in multiple international environments), and a need for the reader to transmit maximum power so that tags receive sufficient operating energy. Given these issues, sorting out how best to manage interference remains a challenge both for regulatory agencies such as the Federal Communications Commission (FCC) and for industry and standards groups. (See Box 1.3 for more on the FCC constraints for RFID operation in North America.)
APPLICATIONS AND BUSINESS
RFID technologies are being used in a wide variety of applications (see Box 1.4 for a sampling). Besides collecting tolls, probably the most common applications at present are in supply-chain management—monitoring goods as they move around a warehouse, through a factory, between distribution centers, and around the globe. It is for such purposes that Wal-Mart, Target, and the Department of Defense have mandated the use of RFID by their suppliers.
But participants in the workshop pointed out that the potential of this technology goes well beyond supply-chain uses. At a high level, RFID technologies can be viewed as a way to bring together the physical environment and the informational environment in many different contexts. Whereas in the past instrumentation has been possible, RFID allows the easy integration of instrumentation with communication. This combination is what presents such interesting possibilities to those experimenting with the technology in the business world. At the same time, understanding the capacities and limitations of the technology is critical to effective deployment. It is important to recognize the broad range of RFID technologies and to understand the application needs in order to determine what kind of RFID (or other) technology will work best in a given situation.
|
BOX 1.3 The Federal Communications Commission (FCC) authorizes the 902–928 MHz frequency band for unlicensed Industrial-Scientific-Medical (ISM) devices. The following constraints must hold for all users of this band, including radio frequency identification (RFID) readers:
Standardization efforts in RFID and adjacent technologies are needed to guarantee the private sector predictable deployments. Examples include cordless phones, baby monitors, garage door openers, personal digital assistants (PDAs), wireless local area networks (LANs), ultra wideband (UWB), contactless smart cards, and RFID. The FCC periodically reviews its regulatory constraints on the basis of the following considerations:
|
This is a dynamic moment in the life cycle of this technology. Anything and everything seems possible. The cost and capabilities of the various ID technologies—bar codes as well as RFID—continue to improve. The standards process, despite rapid progress, is as yet incomplete. Thus, it is unclear which types of RFID technology will prevail. Many companies are experimenting, but the results are highly proprietary. In place of well-accepted data, anecdotes abound. A current challenge is that much of what is being done with RFID technologies is in a closed-system context—that is, within a company, organization, or small group of organizations. This results in proprietary information that makes it difficult to provide general knowledge about the technology and systems challenges that could help advance understanding within the broader community. In sum, it is very difficult now for a single individual or firm to evaluate the costs and benefits of the technology, even for a well-defined application such as supply-chain management, and still more difficult to evaluate speculative future applications.13
|
13 |
Larry Dignan and Kim S. Nash. 2004. “RFID: Hit or Myth?” eWeek. February 9. Available online at <http://www.eweek.com/article2/0,1759,1524634,00.asp>. Accessed December 14, 2004. |
|
BOX 1.4 Applications of radio frequency identification (RFID) technology are proliferating rapidly. The following list presents a sampling of RFID applications; such a list could not be exhaustive as new uses are reported almost daily. Each application presents technical and social challenges.
|
|
The Supply Chain and Beyond
Supply-chain management has been one of the driving business applications behind RFID. Companies such as Wal-Mart are mandating the use of RFID,14 thus providing incentives for smaller companies to begin incorporating the technology into their inventory management and supply-chain systems. The sheer volume of materials and products moving around the country and the globe on any given day is a powerful motivator for finding increased efficiencies. Much of the focus today is on decentralized supply chains, in which many different organizations are involved in a geographically distributed effort. Workshop participants noted that RFID technologies have the potential to improve the capacity of organizations to “trust but verify” when dealing with partners.
RFID is suggested to add value to several components of the supply chain. At a high level, it can assist in tracking product flows and transmitting demand signals back up the supply
|
14 |
Workshop participants reported that Wal-Mart plans to require EPC tags at the case and pallet level from dozens of its top suppliers by early 2005 and from all of its suppliers in 2007. See also Mark Roberti 2003, “Analysis: RFID—Wal-Mart’s Network Effect,” CIO Insight, September 15, available online at <http://www.cioinsight.com/article2/0,1397,1455103,00.asp>, accessed December 14, 2004. |
chain faster than other methods can, resulting in shorter replenishment cycles. More specifically, RFID systems and the information that they generate can assist in the improved structuring of warehouses, location of goods, optimal production and distribution batches, and so forth. They can also be helpful in ensuring a “first-in, first-out” process when the product being tracked is perishable. They could allow improved monitoring for spoilage, coordination with thermal tags and expiration data, proof of delivery, and various other kinds of information associated with products moving within a supply chain. (Such possibilities, of course, require much more capability than that of simple passive tags.) In general, RFID systems have the potential to provide a vast amount of information on business processes, but it is up to the companies to sort out how to make that information useful.
It was reported at the workshop that at this time several pilot studies and experiments are being run to determine how best to incorporate RFID technologies into supply-chain management strategies. In terms of consumer products, one question that arises is whether it makes sense to place tags on single items, or whether the tags (and associated tracking) should be kept at the pallet or case level. It may turn out to be most cost-effective if only high-value items are tagged (for example, cases full of many individual objects, or large single high-value items such as DVD players). Workshop participants suggested that in many cases pallet scanning rather than item scanning was most effective.
Another issue that arises with respect to consumer products is whether and how to move to a fully RFID-enabled supply chain. One participant observed that Wal-Mart, for example, will most likely have a hybrid system (employing bar codes along with RFID) for years. Understanding the implications of that type of system will be important to moving forward.
For a supplier to a huge customer that requires RFID, there is little difficulty in deciding whether and what kind of RFID to use. For others, however, the problems can be vexing. For example, the idea of continuous, real-time inventory monitoring is an exciting prospect. That sort of application, however, goes beyond the capabilities of the simplest and cheapest RFID tags and readers. One workshop participant described such an application, but the objects tagged were large shipping containers. At that level, more expensive and thus more capable tags and readers may make sense. The dream of continuous inventory monitoring at the item level may for now be just that, a dream.
While supply-chain management is an obvious and noteworthy application of RFID technologies, workshop participants described many other potential applications that businesses might consider. In addition to object tracking within a supply chain, other, related applications include reverse logistics (e.g., tracking returns), quality management, marketing, inventory, accounting, assistance in allocating overhead costs, warranty tracking, and recycling. For example, it was suggested that RFID technologies could assist with quality management by providing information about which items have gone through a problematic section of a production process. Such technologies might also aid in delaying product differentiation—that is, in enabling a large variety of products to be made from common materials and components until feedback via RFID helped determine specifics of needed products. This kind of production process requires extensive communication systems in order to decide exactly which mix of products to make, and RFID could well be a valuable part of such systems. Similarly, by tracking parts and components more precisely, RFID might enable more accurate cost accounting. These and other sorts of applications will all have strategic implications for organizations.
Workshop participants also suggested that RFID technologies could assist in schedule optimization, not just in the supply chain, but in the dispatch of service and delivery vehicles as well as in more efficient deployments (and redeployments) of emergency assets. Again, this type of application relies on more precise information about the location and status of these assets.
Health care and security were also discussed as potential application domains. In health care, virtually every component—including patients, doctors, equipment, and drugs—could be
tagged, tracked, and monitored.15 Closer and more sophisticated supply-chain monitoring enabled by RFID could help prevent drug counterfeiting or tampering and reduce spoilage. Tags on ID cards could help prevent unauthorized entry into restricted areas, and tags on objects could help prevent theft. (It was also pointed out, however, that ill-intentioned people could likely devise ways around such straightforward security measures, for example by spoofing tags. Therefore, more sophisticated measures that change the behavior of the system over time might be necessary.16)
In summary, as seen in the discussion of tags, readers, and architectures, the term RFID technology refers to a broad spectrum of functionalities. RFID technologies can do many things. In a business context, it will be important to identify specific objectives and to understand and select the subset of RFID technologies that offer the needed capabilities.
Consumer-Centered Applications
Discussions at the workshop pointed to a major focus by business on the supply-chain and related RFID issues, while much attention from consumers has been focused on the retail experience. Participants reported that there has been some activity in retail, although not as much as in the supply chain, but that it is harder to build a compelling business case for widespread RFID deployment in a retail environment at this time. The idea of eliminating checkout lines may be appealing, but for now the cost seems prohibitive, and various privacy and security issues remain to be resolved. Nor was it clear whether significant advantages would accrue to consumers or businesses over what current bar codes and handheld scanners offer.
An experiment conducted at an upscale clothing store was reported on. For this experiment all items of clothing were tagged, and kiosks presenting various kinds of information about the products were available for sales staff to consult when working with customers. The results were mixed. Although the sales staff appreciated the ready access to information, they disliked the distractions of operating the system, preferring to focus all their attention on the customers. Also, the company was unable to take advantage of other possible uses of the technology. For example, it did not have the information infrastructure to interpret the frequency with which items were scanned and turn those data into useful information for making inventory and stocking decisions.
This experiment and other reports from workshop participants raised several points to be borne in mind when the deployment of RFID technologies in a retail environment is being considered, if the goal is to do more than provide a faster checkout at the point of sale. It is important to focus carefully on what the retailer and its processes require. Depending on the details of the deployment, RFID technologies and their associated systems could in effect provide too much (or even inappropriate or useless) information, to both sales staff and customers. (See Box 1.5 for more on information overload and RFIDs.) This possibility suggests that careful design, along with good interfaces and effective information management, will be important.17
|
15 |
Jonathan Collins. 2004. “Hospitals Get Healthy Dose of RFID.” RFID Journal. April 27. Available online at <http://www.rfidjournal.com/article/articleview/920/1/1/>, accessed December 14, 2004. |
|
16 |
As with almost all information technology systems, RFIDs will pose security challenges. For more on computer and system security, see the following publications from the National Research Council: Trust in Cyberspace (1999), Cybersecurity Today and Tomorrow: Pay Now or Pay Later (2002), Cryptography’s Role in Securing the Information Society (1996), and Computers at Risk (1991). |
|
17 |
For more on the challenges of managing complexity in technology, see the recent survey of information technology from The Economist: “Keep it Simple,” October 28, 2004, available online at <http://economist.com/surveys/showsurvey.cfm?issue=20041030>, accessed December 14, 2004. |
|
BOX 1.5 One of the issues that came up in many contexts at the Radio Frequencies Identification (RFID) Workshop was information overload associated with RFID system deployments. A purported advantage of RFID technology is that it provides increased information visibility along with improved information flow. However, as the retail experiment that was described at the workshop demonstrated (see the subsection “Consumer-Centered Applications”), this can mean that too much (or unhelpful) information is presented to the end user without an effective way to process, manage, or use it. An increased amount of data, by itself, will not necessarily improve business, so carefully constructing a business case is important. Organizations need to know what they are measuring and why. One of the biggest challenges is determining how to collect the right information and how to provide it at the right time in order to support good business decisions. To do this, the information must be collected well, stored well, and then presented well to the user (be that user a system manager or a customer). Collecting data for its own sake is unlikely to be useful and may often be distracting. The issue of data mining with respect to RFID-generated data was also raised at the workshop. Participants noted that while this topic gets a lot of attention when people talk about RFIDs (and related information technologies), there was not, in their experience, a compelling business case for extensive data mining yet. Demand for data mining would also imply significant changes in the supply chain beyond what RFID for item tracking and some of the other applications require. In a retail context, for example, it was noted that it is not at all clear what it would mean for a business to know that a particular item was picked up and then placed back on the shelf. It is also not clear how much benefit the average retail operation could derive from RFIDs for item tracking beyond what bar codes currently provide. Sophisticated data mining and data organization would seem to be a solution to the challenge of information overload. But both are hard technical problems beyond the scope of the workshop. Similarly, collection of data, especially data identifying individuals, raises obvious privacy concerns (discussed in Chapter 2). RFID technologies pose new challenges in several areas—appropriately and effectively managing the data produced, along with choosing what data to collect, are yet two more.1
|
Also mentioned at the workshop was another application area besides traditional retail sales involving direct consumer interaction with tagged merchandise—that of contactless smart cards for personal finance. It was observed that it is still too early to tell what all of the possible applications might be with respect to financial transactions or in retail environments beyond the supply chain and beyond tracking merchandise (and information about merchandise). There are RFID pilot deployments underway in many different organizations, even museums. It will take time, unfortunately, for the results of these pilot studies to be useful to the public and in various enterprises. There is a high cost in doing these studies, and their results could provide a competitive advantage that an organization may not want to share so readily.
As with many basic, multiuse technologies, it is very likely that innovation in RFID technology will continue and new applications will emerge over time. All such applications, however, will likely raise the social and cultural issues discussed in Chapter 2.
Ongoing Challenges
Throughout the discussion of business needs and applications for RFID technologies, workshop participants noted several persistent technical and policy challenges. At a general level, the stability of the technology and the associated standards will be significant factors influencing the business case regarding RFID. In addition, the Wal-Mart, Department of Defense, and other mandates will have an impact on who uses this technology as well as on how it is used. Participants suggested that making the business case for companies not heavily influenced by those huge organizations will be critical if the technology is to see broader deployment. Some smaller companies may look to RFID as a way to move past (or skip) the use of bar codes, but much affecting whether this might be possible is still at a very experimental stage. Other drivers of regulatory change aside from Department of Defense requirements include those of various governments to provide country-of-origin food labeling, pharmaceutical tracking, other asset tracking, and techniques to prevent counterfeiting. The Department of Homeland Security is also taking an interest in using RFID technologies to secure shipping containers against tampering. Interestingly, depending on the requirements from any of these organizations, active tags may be more likely to be subject to regulation than passive tags.
Although some press accounts would seem to suggest that RFID technology is very simple, in fact there are complications that make large-scale deployments a challenge. For example, choosing where to place the tags on an item is a serious issue for some applications. Most tags cannot be read through liquid or on cans. In addition, while the tags are relatively inexpensive, readers are not. Database and infrastructure requirements also add to the cost of implementation. Typically, it was noted, RFID technology costs can be thought of as roughly evenly divisible between software, hardware, and systems integration. Some workshop participants suggested that the business case has not justified the cost of the technology in many arenas and that experiments with RFID systems are still in their infancy.


















