2
Scenarios, Defensive Concepts, and Detection Architectures
The capabilities of currently available sampling and detection systems have made them increasingly useful for defense against attacks involving aerosol dispersal of biological agents. Over the past decade, a succession of military detection systems has been developed by the United States to protect critical assets and deployed forces. These systems include the Biological Integrated Detection System (BIDS), Joint Portal Shield, and, more recently, the Joint Biological Point Detection System (JBPDS).1 The slow response time of these systems (about 20 minutes plus communication, decision, and response delays) makes them most useful for initiation of medical treatment of exposed personnel following a biological release event. This "detect-to-treat" response can be quite effective in the reduction of casualties, as the effects of many biological warfare agents can be dramatically reduced through timely medical treatment. Even longer detection times can also be valuable for detect-to-treat responses to domestic attacks. For example, the Biological Aerosol Sentry and Information System (BASIS),2 developed by the Department of Energy for domestic deployment at special events, employs a much longer (i.e., several hours) response cycle that allows attainment of the very high levels of certainty that are required for major civilian medical responses.
This chapter introduces several generic but representative scenarios in which a biological aerosol is released against target sets of interest. Taken together, these scenarios encompass many of the most likely and threatening prospects that were presented to the committee in briefings and supporting documentation. Based on these scenarios, the committee lists attributes of detector technologies that are most important in future detect-to-warn architectures and discusses trade-offs among them. Early detection plays a major role in the successful execution of the postulated concepts.
The committee then proposes a framework for consideration of defensive systems. This framework stresses the critical importance of matching detector attributes to the capabilities of the response system. The discussion of detector attributes and architectural principles provides a context for the detailed review of detector technologies in the chapters that follow. Later, in Chapter 10, the committee revisits these principles to address the integration of detection systems within the detect-to-warn defensive
architectures. Chapter 10 also provides more specific insight into factors that influence overall performance, including those that are outside the detection system.
The scenarios and defensive concepts in this report were created to provide guidance on the environments and top-level requirements for the detection systems that enable detect-to-warn architectures. Development of more detailed system specifications and operational concepts was not undertaken as part of this study. Future design efforts that address detect-to-warn systems and their operations must build upon the growing experience base derived from federal demonstration programs, including DoD and its Advanced Concept Technology Demonstration (ACTD) programs. Several past ACTDs (for example, the Joint Biological Remote Warning System) addressed biological defense operations in the field. More recent work in the Restoration of Operations ACTD has focused on protection and response to chemical and biological attacks on fixed sites. The operational concepts developed in these past demonstration programs should be evaluated in future system design studies, although they may be of limited value since none have focused on the detect-to-warn architectures discussed in the study. In addition, a formal red teaming3 and countermeasure evaluation must be a part of the next stages of defensive architecture design. The committee did not evaluate the tactics that could be employed by an attacker to defeat the conceptual defenses postulated in this report.
It should also be noted that the detect-to-warn approaches outlined here are not the only component in a comprehensive system to protect personnel from the effects of a biological attack. An overall biodefense architecture can include medical countermeasures (e.g., vaccines and therapeutics) as well as personal and collective protection systems. An approach for balancing research, development, and deployment efforts in this larger arena is an important research topic but is beyond the scope of this study.
SCENARIO SELECTION AND DEFENSIVE CONCEPTS
Credible scenarios for biological agent release against targets of concern are the starting points for development of defensive concepts and detection system requirements. Attack scenarios can generally be divided into two categories. The first involves outdoor releases designed to threaten distributed target complexes (e.g., military bases, deployed forces, naval task forces) or broad area targets (e.g., cities). The second involves direct attacks on specific facilities through agent release into an interior area or into the intake of the air handling system.
Outdoor Release Scenarios
Outdoor releases that cover a distributed area have long been a focus of military concern. Such attacks can threaten forces in the field, operational bases, seaborne task forces, and other critical power projection assets. Outdoor attacks that employ a fully weaponized agent exploit the full potential for wide area impact offered by biological agents. The scenarios developed in an earlier study effort and provided in support of committee deliberations4 emphasize the effect of outdoor releases on a variety of military targets. These scenarios usually employ a line release of aerosolized agent, although the type of agent employed, the timing and extent of the attack, and the resulting areas impacted differ widely. Others have postulated similar broad area attacks on U.S. cities, frequently employing the same line release deployment schemes.5 While line releases are often the tactic of choice, other options, including point releases, may be more suitable for less sophisticated attackers, for surreptitious release in a protected area, for attack of specific targets, or in response to defensive system deployments.
|
3 |
A "red team" is a group of independent reviewers organized to provide an objective assessment. |
|
4 |
Advanced Systems Concepts Office, Defense Threat Reduction Agency, 2000. NBC Scenarios: 2002-2010, April. |
|
5 |
U.S. Congress, Office of Technology Assessment. 1993. Proliferation of Weapons of Mass Destruction: Assessing the Risk, OTA-ISC-559. Washington, D.C.: U.S. Government Printing Office. Available online at http://www.wws.princeton.edu/cgibin/byteserv.prl/~ota/disk1/1993/9341/9341.PDF. |
A line release can be a very effective deployment tactic for sophisticated attacks against a distributed target complex or broad area target. Such a line attack can be generated by a ground vehicle or low-flying aircraft passing upwind of the target area. The length of the release is primarily determined by the extent of the target area, with appropriate allowance for shifts in wind direction for releases far upwind of the target area. Releases close to the upwind edge of the target area will yield a maximum agent concentration on target, since the cloud will not have time to fully disperse before it passes over the target. This will reduce the potential warning time for the defense, but the higher agent concentrations at the target perimeter may make initial detection of the cloud easier. Meteorological conditions will critically impact the success of an outdoor release. Relatively slow wind speeds and a temperature inversion to contain the agent will result in higher agent concentrations and relatively long dwell times in the target area. The relatively slow wind speeds (i.e., 5 to 8 meters per second) sought by an attacker can work to the benefit of the defense, however. Each kilometer of detector standoff at a wind speed of 5 meters per second buys the defense over 3 minutes for detection and response. An efficiently formed cloud can have lethal effects hundreds of kilometers downwind, although the targeted depth for most military complexes is much smaller. Physical security around bases and other fixed facilities is important to permit forward deployment of defensive assets. This not only increases defensive time lines but also drives up the minimum required release size for the attacker.
A point release of biological agent could be the best choice in some attack scenarios. This might occur when maximum agent concentration and duration of exposure on a specific facility is desired. Surreptitious release from a selected point might also allow closer approach to a targeted facility and avoidance of known detectors upwind of the facility. Such a tactic might be particularly useful against civilian facility targets where a large exclusion zone does not surround the target. The closest possible outdoor point release would be a release into the intake of a facility air-handling system, and this possibility must be addressed by facility defenses (discussed below). Point releases might also be chosen as a less complex way to attack extended targets (such as cities), where complete coverage of a distributed area is not a required outcome.
Facility Release Scenarios
Attacks against specific facilities are of increasing concern to military and civilian planners. An active program (the Immune Buildings Program) is currently being sponsored by the Defense Advanced Research Projects Agency (DARPA) to develop key technologies and systems integration concepts in this area.6 Facility attacks can be mounted with much less sophisticated technologies for agent fabrication and dispersal and require smaller release quantities than outdoor release scenarios. The uncertainties associated with outdoor meteorological conditions and agent durability are reduced or eliminated. Individual facilities can also have major iconic and functional value for both military and civilian organizations and offer the attacker a variety of options. The heating, ventilation, and cooling (HVAC) systems can be used to disperse the agent throughout the facility. The attacker can release agent in an accessible room or region of the facility. Releases directly into the exterior HVAC intakes or interior return ducts leading to air handling units can also be effective.
Military Versus Civilian Scenarios
No major distinctions are drawn between military and civilian targets in discussion of detection and response options. Facility and distributed target complexes for the military have direct analogs in the civilian sector. In many cases, military responses to detection of a biological agent could be more effective than those open to most civilian responders. This is due to the various defensive advantages that can be more easily incorporated into a military environment, including effective personal and collective protection gear, rapid command and control, extensive training, tolerance for disruptive
emergency procedures, and robust health and immunity status of the personnel. However, the fundamental defensive architectures and resulting detection implications are expected to have similar applicability to both military and civilian targets.
DEFENSIVE CONCEPTS AGAINST ATTACKS ON FACILITIES
Consideration of facility defenses for protection against biological attacks was a central focus for the architecture and analysis work of this committee. There were a number of compelling reasons for this emphasis on facility protection. One was the high perceived likelihood that a perpetrator, particularly one constrained by unsophisticated technology or limited agent availability, would choose this path. Another was the potential to provide effective detect-to-warn defenses using relatively near-term detection technologies—for example, bioaerosol detectors (see Chapter 5). The development and demonstration of facility protection systems that employ affordable, near-term technologies would constitute an important step toward realization of a national biological defense strategy. The promise of facility defense, however, depends on several factors. These are outlined below and are examined in greater detail in Chapter 10.
Airflow control and air quality features often found in modern facilities, including isolation of independent air circulation zones and effective filtering, can provide opportunities for detection of releases in areas that have relatively high concentration levels. This is particularly true for interior releases over relatively short intervals (e.g., 1 to 10 minutes) where the local concentration near the release point can far exceed expected background levels. This effect also applies to defense against releases at the air handler outside intakes, although the immediate dilution by clean recirculated air within the air handler return plenum may reduce the relative margin over background levels.
Enclosed facilities offer a rich set of defensive responses that can be employed to reduce exposure of occupants in the event of a biological attack. With sufficient warning and attack characterization, the air handling system can be utilized to halt the spread of the agent. Isolation of separate air handling zones by physical barriers and balanced system operations can also dramatically reduce the extent of agent transport beyond the immediate release area. With early warning, evacuation paths may be cleared by appropriate air handler and exterior access strategies. Several passive measures that do not depend on the detection of a release may also be effective in reducing the magnitude of the attack and delaying its dispersion throughout the facility. Filtration or other air cleaning technologies can provide a substantial drop in agent concentration. New construction standards that increase the isolation of independent air handlers, accompanied by periodic pressure balancing of air handlers, can create facilities that disperse agents much less rapidly. These passive defense measures may also enhance the effectiveness of detectors by reducing reduction of the natural biological aerosol backgrounds inside the facility.
The defensive responses suggested in this study involve isolation of airborne agent near its point of release into the facility. This can often be accomplished by air handler responses that impede movement of the agent away from the release zone. While it is difficult to prevent exposure of facility occupants near the release point, appropriate responses can significantly reduce the exposure of individuals in spaces removed from the release area.
Facilities may also emerge as the core element of defenses against outdoor attacks on distributed target complexes such as military posts or bases. Various protective options that can be incorporated into facilities can be rapidly engaged upon notice of the approach of a threatening cloud. For example, facility air intakes and other external openings could be closed during passage of the cloud over the target complex. The air handling system could be shut down or modified to circulate only internal air. For critical facilities, positive pressure established using highly filtered sources could almost eliminate infiltration from an outdoor cloud. In many cases, particularly during early morning hours when biological release is optimal, a greater fraction of site personnel may be present within facilities rather than in an unprotected outdoors posture. During other periods, a strategy of moving personnel into facilities upon
cloud approach, followed by purging and decontamination of the facilities after cloud transit, may be a useful defensive measure.
DEFENSIVE CONCEPTS AGAINST ATTACKS ON DISTRIBUTED TARGET COMPLEXES
Detect-to-warn systems for defense of outdoor attacks on distributed target complexes must rely on detection of the released agent cloud at the perimeter of the complex or on standoff detection that characterizes the cloud before it reaches the target area.
For current systems that require 25 to 30 minutes to yield high-confidence responses, detectors would need to be deployed far in front of the protected targets in order to effect a detect-to-warn response. (For example, detectors must be placed at least 9 kilometers in front of the target area assuming a 30-minute detection and identification delay for a nominal wind speed of 5 meters per second. Higher wind speeds increase this distance even more.) Detection assets placed far forward of the defended targets also face other problems, including control and security or the possibility that the release points can be between the detectors and the target complex.
The size of the target area and the controlled buffer zone between the target and the perimeter of the controlled area also determine detector array sizing. Detector response time requirements may be particularly stringent in the case of foreign posts or bases, ports of debarkation, and military assets surrounded by cities, where the size of the controlled buffer zone can be very small.
For a line release, the extended cloud length means that a sparsely populated line of detectors will likely be sufficient for cloud detection. Deployment numbers will be driven by the need to prepare for attacks from a range of possible incident wind directions. For more localized point releases, a greater number of detectors will need to be deployed, including some away from the perimeter of the buffer zone. While a denser network of detectors is more costly to deploy, other benefits besides better coverage of attacks accrue. Closely spaced detectors will generally allow a more specific characterization of the direction and magnitude of an attack. They will also make the detection less vulnerable to uncertainties in the local meteorological variations near any given detector. Finally, nearby detectors serve as backups in the case of false alarms or detector malfunctions.
The nominal defensive concept for distributed target complexes hinges on the initial detection of a threatening cloud as far upwind as possible using spectroscopic point detectors at the perimeter of the defended area or standoff detectors that can identify clouds before they reach the defended perimeter. A detection alarm could, if sufficiently certain, trigger various protective actions within the defended complex. Site facilities could be placed in a defensive mode through air handling and physical isolation steps to reduce infiltration of outside air. At-risk personnel could be alerted to utilize protective face masks or seek shelter in a protected facility. Some of these actions, particularly those affecting facility airflows, could be implemented automatically and cause little disruption of activities in the facility.
The peak agent concentration in a line release cloud may be relatively low for attacks sized to threaten only unprotected personnel. If the attack is sized to achieve a high confidence of infection of personnel inside facilities, the incident concentration levels may be significantly higher to overcome the sheltering effects of well-designed facilities. If this is the case, attack levels may exceed background enough to enable rapid, nonspecific detection of the attack. This rapid detection could enable significant defensive actions to be taken, particularly in the control of airflows and intake into the site facilities threatened by the agent cloud. Portions of the potential scenario space in which such defensive responses could be significant are examined in Chapter 10.
Although a scenario involving a biological attack against a broad area (e.g., an urban civilian population) is not an explicit part of this committee's charge, it is worth commenting on some of the similarities and differences between this scenario and an attack on an extended military installation. Defense of broad areas against biological attack is a particularly difficult challenge for a detect-to-warn architecture. If high casualties are the principal goal of an attacker, an arbitrarily placed point release can provide a very large infective plume with relatively low concentration levels. Detection of such a release with an unknown release location will require an array of closely spaced detectors. Furthermore,
detection sensitivity requirements are high for optimally sized releases. The difficulties associated with defenses in this scenario may make a detect-to-treat system the preferred architecture for the foreseeable future.
KEY DETECTION SYSTEM ATTRIBUTES AND TRADE-OFFS
The ability of detector systems to enable effective defensive responses depends on the many attributes that characterize the acquisition and function of the detectors. Often there exist trade-offs among the major performance attributes that are under control of the detector designer. The most critical attributes that determine detector performance and their impact on defensive architecture design are outlined here. Several key trade-offs that drive single-detector design and detection systems design will also be highlighted.
Detector Performance Attributes in Detect-to-Warn Scenarios
The key requirement for facility defense architectures is timely response. Nominally, actionable information within 1 to 2 minutes is desirable. Such rapidly available information can, in some cases, be useful even if it is somewhat uncertain. This is particularly the case where a rapid, though less certain, alarm is followed by more specific verification in a timely fashion.
Required detector sensitivity for detect-to-warn operations depends on a variety of threat and architectural factors. The infectivity of the agent is a critical factor. Some agents require only a dozen or fewer particles to reach an infective dose, while others require thousands. This is illustrated by the infectivity data included in Table 2.1. Required detection sensitivity also depends on the magnitude of the release and the attenuation or dispersion between the release point and detector location. For many scenarios, detection alarm thresholds far above both normal background levels and the lethal levels for humans can be useful when the detector is placed close to the source or when a protective barrier isolates the source from the intended targets. These trade-offs will be explored in later discussions on defensive architectures. In addition to indications of the presence of an agent, detectors that provide estimates of agent concentration can support the characterization and estimation of the future trajectory of an agent cloud.
This specificity permits detectors to identify a small set of agents from a very diverse biological background. It can serve to reduce false alarm rates for detection, though often at the expense of much slower response times. Detectors that are nonspecific, such as those that detect and discriminate only biological versus nonbiological aerosols, can have very high false alarm rates if the alarm threshold is not well above the normal biological background levels. For attacks that result in biological signatures well
TABLE 2.1 Infectivity Levels for Several Biological Agents
|
Biological Agent |
Infectivity Level a |
|
Q fever (Coxiella burnetii) |
<10 |
|
Smallpox (Variola major) |
10-50 |
|
Tularemia (Francisella tularensis) |
30-70 |
|
Plague (Yersinia pestis) |
300-500 |
|
Anthrax (LD50) (bacillus anthracis) |
2,500-55,000 |
|
a In colony-forming units for bacteria and plaque-forming units for viruses. Colony forming units (cfus) are counted colonies that result from either individual culturable organisms or particles containing multiple culturable organisms |
|
above backgrounds, nonspecific detection alarm thresholds may be set high to avoid false alarm issues. Highly specific detection will continue to play an important role in the confirmation of rapid alarms from nonspecific sensors and in the detection of lower concentrations of biological agent that may result from scenarios that employ extended release periods or exterior releases that are drawn into the facility HVAC system.
Technologies that have the capability to recognize a wide array of potential threatening agents will be preferred in defensive applications. The committee also considered nonspecific detectors that respond to the functional impacts of agents on organisms. Such function-based detection processes may become even more important as the potential for engineered threats (e.g., agents created or modified genetically, structurally, or chemically to make them more lethal or less detectable) increases.
The committee notes that there are many other desirable attributes of detection technologies, including low acquisition and maintenance cost, minimal consumables and other logistics needs, high reliability, and capability for continuous operation. Low power requirements, small operational signatures, and compact packaging may also be needed for some specialized applications. Many of these attributes will become more important in the system engineering phase and the integration of the final deployable package.
Detection System Trade-offs
In real-world detection systems, designers must make trade-offs among the detector attributes introduced above. Several dominant trade-offs emerged frequently during consideration of detection technologies. These are outlined below.
Increased sensitivity is often associated with longer processing delays within a detector. For different types of technologies, this delay reflects very different physical constraints. These will be reviewed in conjunction with the specific technologies in later chapters. In addition, the use of longer sampling intervals, higher collection rates, and concentrators can increase system sensitivity at the expense of higher initial costs and longer detection delays. A particularly interesting trade-off exists between detector sensitivity and cost. If inexpensive detectors could be deployed near release points, they would be expected to experience relatively high agent concentrations. This could enable more rapid response and reduce the false alarm rate for even simple detectors. This concept of wide deployment of inexpensive detectors is motivating some developers to come up with the equivalent of a smoke detector for biological agents. (Such devices are called "biological smoke detectors" in this report.)
For the currently envisioned universe of detection technologies, higher specificity is generally associated with longer processing times. The capability for rapid but nonspecific detection has been proven. However, such systems respond to large classes of biological particles, so the ability to deal with false alarms must be an inherent part of the defensive system architecture. Even with highly specific assays, such as PCR or PCR/array hybridization (see Chapter 6), increasing specificity is achieved by amplifying and detecting more nucleic acid loci (higher multiplexing levels), which requires a longer assay time.
While most current detection technologies identify specific types of threat agents, one class of emerging detectors identifies specific functional impacts on surrogates for human cells. Such functional systems are able, in principle, to deal with unknown agents that might be developed by an adversary. These are discussed further in Chapter 9.
KEY ARCHITECTURAL DESIGN PRINCIPLES FOR DETECTION
The utility of a detection system must, in the end, be measured by the extent to which casualties are reduced and critical functions of the target are maintained. Effective response measures that can reduce the impact of an attack following its detection are indispensable in achieving this goal. Detection without the ability to respond can assist in identification and later medical treatment of affected personnel but has no value in the detect-to-warn mission.
The critical role of response options demands an end-to-end systems engineering approach to architecture design. The benefit resulting from investments in new response options might far exceed the impact of similarly costly efforts to improve detection. Improvements in response systems will usually be required to exploit the full capability of a detection system. Furthermore, the nature of the response that is available will often have a strong influence on the best choice of detection architecture.
A key interdependence of detection and response attributes is the relationship between detector false alarm rate and the severity of the response initiated when the detector alarms. For example, the range of active defensive responses can have widely differing impacts on both the personnel within a major facility and its operation. Some response actions, such as changes in HVAC air handler settings, are unlikely to cause near-term disruption of the activities under way within a facility. Actions that have limited or no impact on personnel or operations in an attack area are often termed "low-regret" responses. Other responses have more significant, though perhaps easily reversible, impacts on the personnel or function of a facility, particularly if a false alarm is confirmed in a timely fashion. These might include restraint or even evacuation of personnel, initiation of masking or other individual protective actions, or activation of barriers (e.g., air curtains) that significantly increase the isolation of different areas within the facility. Still other responses could be imagined that generate long-term or irreversible impacts on operations or that have potentially severe impacts on personnel. These might include facility shutdown, personnel decontamination, or initiation of medical treatment protocols. These latter responses can be termed "high-regret" options.
Clearly a detection system with a high false alarm rate cannot be employed to initiate high-regret responses. However, a relatively high false alarm rate detector might be used to trigger low-regret responses if a timely path is available to confirm the presence of a release and either reverse the initial responses or activate higher regret options that further respond to a confirmed event. This fundamental design principle can be exploited to match the performance of a detection system to the unique characteristics of a defended facility or site.
The concept of matching the intensity of the response to the quality of information emerging from the detection system is illustrated in Figure 2.1. Assuming a 1-minute cycle time for detection and decision actions, a false alarm rate of 10-3 (about one per day) might be tolerated for low-regret responses, depending on the nature of the confirmation process. High-regret options will likely require false alarm rates on the order of 10-6 (about one per year) or less. In a real defensive deployment, the impact on the facility operators of various levels of response to false alarms would need to be carefully evaluated. These standards may be very different for civilian and military applications and for different levels of alert status. The fundamental defensive principles remain:
-
The level of response to detector alarms must be commensurate with the level of certainty of the alarm information.
-
For facilities with the potential for graduated response steps, a multistage detection strategy may be optimal to permit early implementation of actions that can be easily reversed.
-
Multistage detection and attack assessment may mandate the inclusion of several detection technologies into the overall system to build an increasingly accurate understanding of the nature of the unfolding attack.
Multistage Detection Architectures
The concept of multistage detection to provide increasingly stringent examination of initial alarms is not new. Such architectures are employed in military detection systems (e.g., the Biological Integrated Detection System, Portal Shield, and the Joint Biological Point Detection System), where fast detectors with relatively high false alarm rates are used to trigger further analysis by more specific detectors. For the military systems, this permits intermittent operation of the identification stages with the attendant reduction in consumables and other detector maintenance. However, this principle could be more generally applied to a much wider range of defensive architectures where earlier, higher false alarm
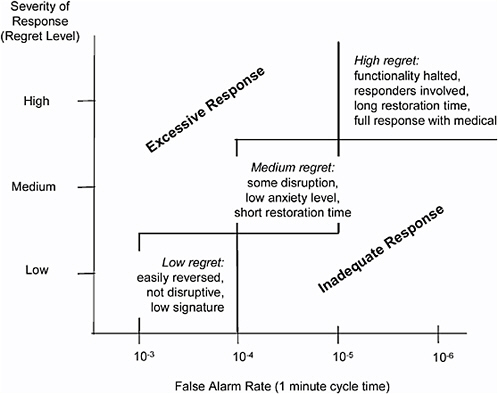
FIGURE 2.1 Matching response to information certainty.
detection stages might be used to initiate low-regret protective responses. Early warnings might also provide useful lead time to permit more successful execution of high-regret responses in the event of confirmation.
A generic multistage architecture is diagramed in Figure 2.2, where three stages of detection plus the essential sample collection and preparation element are indicated. As identifiers improve in speed, specificity, and sensitivity, one might imagine useful systems with two or even a single stage. As discussed in subsequent chapters, the committee believes that rapid, sensitive identifier technologies should be developed that could be operated in parallel with nonspecific detectors (as opposed to the series arrangement discussed for military systems above) to provide a reduced rate of false alarms and better protection against low-level attacks. At present, the response times of detectors that yield positive identification and confirmation of an attack are too slow to be operated in such a parallel manner. The discussions in subsequent chapters that address promising detection technologies will highlight evolutionary technologies that could significantly impact the generic multistage architecture presented here.
The rationale underlying the multistage detection approach can be illustrated by consideration of facility protection architectures. Bioaerosol detectors offer the advantages of being available in the near term, providing a rapid response, and responding to all biological particles, whether known or unknown, existing or novel. However, they are prone to false alarms, particularly if the detected particle concentrations are only slightly above average backgrounds. The relatively uncertain information generated by bioaerosol levels that are not far above background might be used to initiate low-regret responses such as modifications to the normal air handling (e.g., shutdown, airflow reversals, selective venting). Other useful low-regret options are available, including increasing surveillance of the potential
FIGURE 2.2 Generic multistage architecture.
release region, alerting nearby staff to note any irregularities, and reducing the personnel traffic into areas that might be affected should the release be confirmed.
If bioaerosol levels far higher than background are observed, or if a rapid identifier operated in parallel yields a positive report, more significant actions can be initiated. These might include evacuations, temporary personal protection measures, movement restrictions, and other actions that will disrupt or halt normal facility operations. Final confirmation of the attack by the most specific detection system will open the door to a full complement of responses, including medical measures and evaluation of the overall scope of the attack beyond the bounds of the facility. Even for very specific detectors, validation of the presence of an attack by a second detection technology may be valuable when the lowest possible false alarm rate is required.
Detect-to-Warn Architecture Performance
The end-to-end performance of a detect-to-warn architecture will depend on numerous factors, including scenario uncertainties, detection system capabilities, and response effectiveness. Examples of several nominal defenses are postulated and analyzed in Chapter 10. These examples point to the promise of significant defensive capability against some attacks. Many challenging analysis, design, and demonstration tasks remain before this promise is realized, not only for the detection technologies but also for the overall defensive system.










