2
Nuclear Weapons
Transparency and monitoring measures can be employed at several phases in the life cycle of nuclear weapons, which is illustrated schematically in Figure 2-1. As discussed in Box 2-1, the key components of a nuclear weapon are those containing nuclear-explosive materials (NEM).1 These components, together with high-explosive assemblies and various electrical and mechanical components, are assembled into nuclear weapons in specialized facilities; in the United States, this is done at the Pantex plant in Amarillo, Texas. Assembled weapons are transported to military storage facilities, where they are stored pending deployment with a delivery vehicle. Nuclear weapons are operationally deployed and ready for use when they are mated to ballistic missiles and placed in launchers, loaded onto aircraft, or stored at air bases for nuclear-capable aircraft.2 Nuclear weapons may be removed from operational deployment from time to time for inspection and routine maintenance of the weapon or its delivery vehicle and launcher. Weapons also may be kept in long-term storage as spares, as a source of parts for remanufacture or the manufacture of other weapons, or held in reserve as a responsive force that may augment deployed forces. When a decision is made to eliminate a nuclear weapon, it is disassembled and the NEM components are stored for reuse or final disposition.
Past and current arms control agreements kept most of the nuclear weapons life cycle closed to outside scrutiny. As discussed in Chapter 1, nuclear weapons were not considered suitable for direct monitoring and transparency because of their small size, the ease with which they could be concealed, and the secrecy that sur-
|
1 |
NEM are defined in Footnote 3 of Chapter 1; see also Chapter 3 and Appendix A for a further technical discussion. |
|
2 |
This applies to gravity bombs and weapons for ballistic or cruise missiles, which account for the vast majority of the world’s operational nuclear arsenals. In the past, the United States and Russia deployed other types of nuclear weapons, including landmines, artillery shells, depth charges, and weapons for air-defense missiles and torpedoes. In 1991-92 both sides pledged to withdraw from deployment these types of weapons and to dismantle all nuclear landmines, artillery shells, and weapons for short-range missiles (see Chapter 1). The United States has dismantled all of these other types of weapons; Russia may have air-defense and antisubmarine weapons in storage. China may stockpile some of these other types of nuclear weapons. |
rounded them. For the most part, therefore, transparency and monitoring measures extended only to delivery systems (ballistic missiles and their silos, mobile and submarine launchers, strategic bombers, and cruise missiles). Agreed limits on the number of deployed strategic weapons were verified indirectly with counting rules that attributed a certain number of weapons to each deployed delivery system of a particular type. The first Strategic Arms Reduction Treaty (START I), for example, provides for a small number of inspections each year to confirm that the number of weapons on a selected ballistic missile does not exceed the number allowed for that type of missile. There have been no agreed limits on the number of strategic nuclear weapons that can be kept in storage for possible deployment, no declarations or measures to confirm the number of strategic or nonstrategic weapons in the stockpile, and the only measures to confirm that nuclear weapons have been eliminated are those being undertaken in connection with agreements concerning the disposition of highly enriched uranium from dismantled weapons.
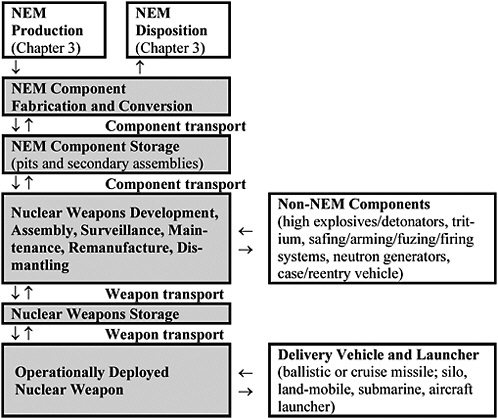
FIGURE 2-1 Life cycle of a nuclear weapon.
This chapter considers several possible measures for transparency and monitoring of nuclear weapon stockpiles. Chapter 3 then considers measures to apply transparency and monitoring to stockpiles of NEM, including current and past production in military and civilian programs and for the disposition of existing and future stocks. The measures related to nuclear weapons stockpiles include declarations of weapon inventories at various levels of detail; on-site inspections and other methods to confirm the accuracy of declarations disaggregated by facility; continuous monitoring of certain weapon stocks, such as excess or retired weapons in storage; transparency measures at weapon assembly facilities to confirm the dismantling and permitted remanufacture of weapons; and declarations and transparency measures covering the storage and fabrication of NEM components (pits and secondary assemblies; see Box 2-1 for an explanation of these terms). Other confidence-building measures that could prove useful include exchanges of information on historical weapon inventories including past assembly and disassembly records, facility design information and operating records, and other records. The various technologies available to support these measures are described and assessed in boxes; the chapter text describes how they might be applied.
The various measures are presented as an integrated package of progressively more demanding steps. We emphasize, however, that some are less sensitive and intrusive and could have value as part of broader confidence-building efforts, even if more formal and intrusive verification initiatives were not adopted.
These forms of “cooperative transparency” could be augmented by information gathered unilaterally by individual states, which is current U.S. arms control and nonproliferation practice. The available methods include “National Technical Means” (NTM) such as satellite imagery collected over a range of wavelengths, imagery from reconnaissance aircraft, data from chemical and radiological detectors on aircraft overflying a country or patrolling just outside its borders, and intercepted electronic communications. They also include information gathered by human sources—clandestine operatives—and information obtained from defectors or “whistle blowers.”
DECLARATIONS OF NUCLEAR WEAPON STOCKS
The logical first step toward increased transparency would be for nuclear weapon states to exchange information on their inven-
tories of nuclear weapons. Alternatively, a declaration or data exchange could be part of a formal agreement. Most arms control agreements have included provisions for initial and subsequent declarations of treaty-limited items; examples include START I, the Treaty on the Elimination of Intermediate-Range Missiles (INF Treaty), the Treaty on Conventional Armed Forces in Europe, and the Chemical Weapons Convention (CWC). In each of these cases, the initial declaration defined a baseline inventory from which the agreed reductions proceeded. A formal agreement has the advantage of precision since it could define the items covered and specify exactly what information is to be exchanged; for example, an agreement might define what constitutes a “nuclear weapon” (see Box 2-1) and specify when a weapon would be considered dismantled or eliminated.
Declarations could also be made unilaterally and informally, with or without the expectation of reciprocation by other nuclear weapon states. The main advantage of voluntary declarations is that they can be accomplished quickly, without lengthy and detailed negotiations. The United States could lead by example, declaring its inventories of weapons and inviting other states to do the same. Given the size of the U.S. nuclear arsenal, making a unilateral declaration would not incur a security risk, but the United States would lose bargaining leverage in negotiating greater transparency if Russia did not reciprocate. The major disadvantage of this approach is that there would be no agreed definitions of exactly what should be declared and therefore no basis for transparency measures to confirm the accuracy of the information provided. This proved to be a problem with the informal Presidential Nuclear Initiatives on nonstrategic nuclear weapons announced by the United States and Russia in 1991-92, where lack of a formal agreement, detailed exchanges of information, or transparency measures at one point led some to charge that Russia was redeploying weapons in violation of its previous pledge, despite Russian denials.3
Proposals for U.S.-Russian Declarations
Proposals for weapon declarations and related transparency measures emerged in the wake of the breakup of the Soviet Union.
In 1992 concern about the safety and security of nuclear weapons and NEM in the former Soviet Union led Senator Joseph Biden to introduce the following amendment to the resolution of ratification for the START I Treaty:
Nuclear Stockpile Weapons Arrangement. Inasmuch as the prospect of a loss of control of nuclear weapons or fissile material in the former Soviet Union could pose a serious threat to the United States and to international peace and security, in connection with any further agreement reducing strategic offensive arms, the President shall seek an appropriate arrangement, including the use of reciprocal inspections, data exchanges, and other cooperative measures, to monitor (A) the numbers of nuclear stockpile weapons on the territory of the parties to this Treaty; and (B) the location and inventory of facilities on the territories of the parties to this treaty capable of producing or processing significant quantities of fissile materials.4
The amendment was interpreted to apply to a future START III treaty, since the START II negotiations were already moving to a conclusion at that time.
In 1994 the United States began trying to gain Russian agreement to greater transparency; since most of these efforts included both weapons and NEM, they are described together here. The United States had several motives for these initiatives: to fulfill the requirements of the Biden Amendment in anticipation of a future START III treaty; to facilitate U.S. assistance to Russia under the Cooperative Threat Reduction (CTR) program; and to bolster international support for the indefinite extension of the Nuclear Non-Proliferation Treaty (NPT). As described elsewhere in this study (see Chapter 3), part of this effort included a significant amount of joint work between the U.S. and Russian nuclear weapons laboratories to explore transparency and monitoring measures that could make this increased openness possible while still protecting sensitive information about weapon designs.
At their summit in September 1994 Presidents Clinton and Yeltsin agreed to “exchange detailed information…on aggregate stockpiles of nuclear warheads, on stocks of fissile materials and on their safety and security. The sides will develop a process for
exchanging this information on a regular basis.”5 Their May 1995 summit statement reaffirmed that the two governments would negotiate agreements on stockpile data exchanges, and called for a third agreement on “other cooperative measures, as necessary to enhance confidence in the reciprocal declarations on fissile material stockpiles.” The two presidents also agreed to “examine and seek to define” possibilities for “intergovernmental arrangements to extend cooperation to further phases of the process of eliminating nuclear weapons.”6
The United States formally presented the draft text of an agreement to Russia in June 1995. The proposal included a call for a confidential exchange of data on current total inventories of weapons and NEM, as well as on the total number of nuclear weapons dismantled each year since 1980 and the type and amount of NEM produced each year since 1970. The Russians declined to discuss the draft, however. According to James Goodby, U.S. chair of the joint working group that had been exploring the arrangements, some Russian members of the group “gave the impression that the scope of the data exchange went well beyond what they were prepared to consider.”7
The United States nonetheless continued to seek agreement on stockpile declarations. At their March 1997 summit in Helsinki, Presidents Clinton and Yeltsin agreed that a START III agreement, to be negotiated following ratification of START II, should include “measures relating to the transparency of strategic warhead inventories and destruction of strategic nuclear warheads” and that transparency measures related to nonstrategic nuclear weapons and to nuclear materials would also be explored.8 When the United States presented a draft protocol dealing with transparency and monitoring for weapons in early 2000 for consideration in connec-
tion with START III, however, the Russians were not interested in pursuing the idea.9 In the end, START II never entered into force, and START III negotiations were never initiated. The obstacles to more far-reaching transparency—in the form of deep-rooted mutual suspicion about motivations, desire to protect sensitive information, and bureaucratic and legal impediments on both sides—are formidable, not least because some of them reflect genuine dilemmas about the balance of risk and benefit.10
Although no formal agreements on stockpile declarations have been achieved, some data have been released on a voluntary basis. No nuclear weapon state has revealed the precise number of nuclear weapons in its current stockpile; however, the United States, the United Kingdom, and France have released some information. The United States released an official accounting of the total number of nuclear weapons in its stockpile each year from 1945 to 1961; the total yield of the stockpile and the number of weapons retired or dismantled each year from 1945 to 1994; and, for fully retired weapon types, the total number assembled each year.11 Although it did not provide such historical details, the United Kingdom has stated that in the future it would maintain fewer than 200 operationally available weapons of a single type.12 In the mid-1990s France announced that it would eliminate its land-based nuclear forces, reduce the number of strategic submarines it would deploy, and dismantle the facilities used to produce NEM for nuclear weapons.13
|
9 |
Rose Gottemoeller, “Parsing the Nuclear Posture Review,” A ACA Panel Discussion With Daryl G. Kimball, Janne E. Nolan, Rose Gottemoeller, and Morton H. Halperin, Arms Control Today 32 (March 2002), pp. 15-21. Available as of January 2005, at: http://www.armscontrol.org/act/2002_03/panelmarch02.asp |
|
10 |
For a discussion of these issues from both U.S. and Russian perspectives, see National Research Council, Overcoming Impediments to U.S.-Russian Cooperation on Nuclear Nonproliferation: Report of a Joint Workshop (Washington, DC: The National Academies Press, 2004). |
|
11 |
Declassification of Certain Characteristics of the United States Nuclear Weapon Stockpile. Fact Sheet (Washington, DC: U.S. Department of Energy, June 27, 1994). Available as of January 2005, at: http://www.osti.gov/html/osti/opennet/document/press/pc26.html. |
|
12 |
British Ministry of Defence, “Strategic Defence Review: Deterrence and Disarmament” (London: Ministry of Defense, July 1998). Available as of January 2005, at: http://www.mod.uk/issues/sdr/deterrence.htm. |
|
13 |
Robert S. Norris, William M. Arkin, Hans M. Kristensen, and Joshua Handler, “French Nuclear Forces,” Bulletin of the Atomic Scientists 57 (July/August 2001), pp. 70-71. |
Levels of Detail in Stockpile Declarations
Information on nuclear weapon stockpiles could be exchanged at various levels of detail, from highly aggregated to data on individual weapons. Table 2-1 illustrates this progression using four levels of detail: total number of weapons; total inventories by weapon type and status; inventories by facility; and a complete itemized inventory.
TABLE 2-1 Illustrative Levels of Detail for Declarations of Weapon Inventories
|
Level |
Type of Information |
|
1 |
Current total number of nuclear weapons of all types. Each year since first test: total number assembled, disassembled, and in the stockpile. For each of next five years: planned number assembled, disassembled, stockpiled. |
|
2 |
Current total number of each weapon type, by status (e.g., operationally deployed, active reserve, inactive reserve, retired/awaiting dismantling). Delivery systems associated with each weapon type. Each year since first test: total number of each weapon type assembled, disassembled, and in the stockpile. For each of next five years: planned number of each type assembled, disassembled, and in the stockpile. |
|
3 |
Name and location of all facilities at which nuclear weapons are currently deployed, stored, assembled, maintained, remanufactured, dismantled, or other otherwise handled. Facility descriptions and site maps indicating each launcher, storage bunker, building, or other site in which nuclear weapons are or may be located. Number of each weapon type at each facility. Name and location of facilities that previously contained weapons. |
|
4 |
For each weapon: serial number, weapon type, status, and current location. |
Total Inventories
The simplest declaration would give the total number of nuclear weapons currently possessed by each state. Even at this gen-
eral level there are technical issues to resolve, such as whether unassembled or partly assembled weapons, test or mock devices, and explosive devices not intended for military use would count as “weapons” for the purposes of the declaration.
The total worldwide stockpile of nuclear weapons is probably around 30,000, of which the arsenals of the United States and Russia constitute 95 percent. China, France, and the United Kingdom collectively account for 3 to 4 percent of the worldwide total, while Israel, India, and Pakistan together account for less than 1 percent. Although actual weapon inventories remain state secrets in each of these countries, we do not find a persuasive security rationale for keeping secret the total number of weapons held by each of the five de jure nuclear weapon states (i.e., the five states recognized as such by the NPT). The potential confidence-building value of such declarations is underscored by the substantial uncertainties in some official U.S. estimates; for example, for Russia this may be as large as “plus or minus 5,000” weapons.14 Most of this is due to large uncertainties about Russia’s stock of nonstrategic weapons, which may account for more than half of the Russian stockpile.
It could also be very useful to declare historical weapon inventories to help build confidence in the accuracy and completeness of declarations of current inventories. States willing to share current data could also be willing to share comparable historical data. Beginning with the year of their first nuclear test, states could give the total number of weapons assembled and disassembled each year and the total number in the stockpile at the end of the year. States also could share information on their future plans for the weapon stockpile, giving, for example, the projected number of weapons to be assembled and dismantled each year for the next five years.
Inventories by Type and Status
The next level of detail would disaggregate total inventories by weapon type and/or associated delivery vehicle. The inventory could be further disaggregated by status, to differentiate between “active” weapons (those ready for immediate military use) and
“inactive” weapons (those without tritium and other limited-life components installed). Active weapons could be divided into operationally deployed weapons (i.e., mated with a ballistic missile or ready for immediate aircraft delivery) and other weapons that could be deployed relatively quickly (i.e., spares and reserves). The inactive inventory might also be further divided into reserve weapons and weapons that have been permanently retired and are awaiting dismantling.
As with total inventories, it could also be useful to release comparable historical data and share future plans. For each weapon type (including types not in the current stockpile), for example, states could declare the number of weapons assembled and disassembled in each year since the first nuclear test and the total number of each type in the stockpile.
Today, inventories by type and status are state secrets. In the case of Russia and the United States, which have exchanged detailed information on deployed strategic forces, such secrecy only serves to protect information on the number of nonstrategic and reserve strategic weapons. We judge that the potential security benefits of exchanging these data outweigh the benefits of continued secrecy.
Facility Inventories
The next level of detail would disaggregate weapon inventories by facility, which would be necessary before states could consider the possibility of inspections or other measures to confirm the accuracy of declarations. At this level, states would declare the name and location of all facilities at which nuclear weapons exist, preferably by type and status. Facility descriptions and site diagrams also could be exchanged, indicating the location of all storage bunkers or other areas where nuclear weapons might be present. The United States and Russia have exchanged information at this level of detail for nuclear delivery systems under the INF and START treaties, in order to facilitate verification of agreed reductions and limits.
Relevant facilities would include intercontinental ballistic missile (ICBM), submarine, and air bases; nuclear weapon storage facilities at other military bases; and facilities at which weapons are assembled, disassembled, or maintained. A declaration could be prepared for each such facility. For example, states could declare the total number of weapons of each type mounted on ICBMs or stored as spares at each ICBM base, the number stored or deployed on submarines based at each port, the number of active and inac-
tive weapons of each type in each storage facility, and so on. (For very small inventories, weapons in transit would need to be declared and controlled as well, since transport systems could in that case conceal a significant fraction of the stockpile.)
Much of this information has already been exchanged by the United States and Russia, as part of the START Treaty. Going beyond START, they could share information on facilities where nonstrategic weapons are deployed, and the location and inventory of weapon storage, maintenance, and assembly-disassembly facilities. It might be argued that providing such information would allow these facilities to be targeted, but it is reasonable to assume that Russia and the United States have already identified and characterized each other’s nuclear weapon facilities, and the military significance of these facilities is much smaller than that of deployed forces in any case.
Serious security concerns would arise if declarations significantly increased the vulnerability of a state’s nuclear forces to attack; for example, declarations that included the location of every nuclear weapon might prove destabilizing if potential adversaries became more confident in their ability to destroy opposing forces (and therefore be tempted to launch a preemptive attack during a crisis) or more afraid of preemptive attack (and therefore more likely to launch nuclear forces before they could be destroyed). This should not be a concern, at least for the United States and Russia, for several reasons. First, the United States, Russia, France, and the United Kingdom maintain submarines at sea (and, in the case of Russia, also mobile ICBMs) that cannot be targeted or confidently destroyed in a preemptive attack. Second, the United States and Russia also deploy silo-based ICBMs that could, at least in principle, be launched on warning of an attack, further inhibiting each other from contemplating a preemptive attack. Third, as discussed below (see “Secure Declarations”), the use of cryptographic tools could allow parties to maintain control over access to the information contained in the declarations, so that the location of every nuclear weapon need not be revealed in advance.
Itemized Inventory
The most detailed declaration would be an itemized inventory. This could take the form of a table with a row for each weapon and columns for the weapon’s serial number, type, date of assembly, status, and location. The table could be extended to include weap-
ons and other nuclear-explosive devices that had been dismantled or destroyed in explosive tests.
Today such itemized inventories would be considered highly sensitive, and the exchange of such information is unlikely to receive serious attention in the near future. That said, sharing and confirming weapon inventories at this level of detail ultimately would be necessary—though not sufficient—to achieve very deep cuts in U.S.-Russian nuclear arsenals. One of the most difficult technical issues associated with very deep cuts would be gaining high confidence in a state’s baseline inventory of nuclear weapons. If a complete, correct baseline inventory could be confidently established, transparency and monitoring to demonstrate that all weapons contained in the inventory (or all but an agreed number) have been dismantled would provide confidence in the accuracy of deep cuts. The Chemical Weapons Convention, which prohibits chemical weapons, requires parties that possess such weapons to declare the precise location and give a detailed inventory of each facility.
Secure Declarations
In the approach described above, access to stockpile data is controlled by limiting the types of information exchanged. As trust and cooperation grew between parties, the level of detail and types of information exchanged could be expanded incrementally, from highly aggregated to itemized declarations. One problem with this incremental approach is that high confidence in the accuracy of declarations would be deferred until the final stages of this process, because simple and aggregated declarations are much easier to falsify than detailed and itemized declarations. In addition, states would be less likely to have confidence in future declarations of smaller nuclear arsenals if there had not been a steady flow of detailed information over the intervening years about the assembly, dismantling, and inventories of each type of weapon, beginning when arsenals were much larger. Early declarations, involving weapons not yet subject to agreed reductions or elimination, would force states to decide, at the outset of the process, whether to make a completely truthful declaration, thereby constraining the potential for cheating or making cheating more detectable at a later date. In some cases, however, disclosure of stockpile data, if made public, could fuel or exacerbate interstate rivalries and put pressure on governments to increase the number of nuclear weapons.
It could take many years to build mutual trust to the point where parties would be willing to exchange complete and detailed stockpile information. In the intervening time, the opportunity for exchanging and confirming information about the assembly or dismantling of weapons would be lost. This could present a “chicken-and-egg” dilemma, in which deeper trust and cooperation depended upon the prior exchanges of information, but these prior exchanges required deep levels of trust and cooperation.
This dilemma could be resolved by using modern information technology. Cryptographic tools are readily available (see Box 2-2) that would allow states to exchange detailed stockpile data while maintaining complete control over access to its contents. In this way, states could begin at an early date to exchange detailed and complete declarations on a regular basis, granting other parties access to selected portions of the data, on a sampling basis or on an agreed schedule. By confirming the accuracy of small random samples of the data, parties would over time develop high confidence that declarations were accurate, even if they never had complete access to the entire declaration. The declarations would, in effect, be placed in “escrow” until such time as both parties agreed to exchange part or all of the information contained therein. Complete access to the declarations might be granted years later and examined for internal consistency and for consistency with information gathered during inspections and with national technical means. This is conceptually similar to a sealed bid that is deposited by a deadline and opened by the auctioneer at a later time, except in this case the envelope can be opened only with the cooperation of the bidder.
One technique for preparing and exchanging secure declarations is encryption. Standard encryption algorithms, such as the Advanced Encryption Standard,15 are routinely used by U.S. government agencies to transmit secret information. To see how encrypted declarations might work, assume that Russia and United States agreed on the data that ultimately should be exchanged and a format for these data. The data file might contain a line or record for each weapon, for example, with each record containing the several data fields: serial number, type, date of assembly, its location and status on a certain date, and so forth. Each record would
|
15 |
National Institute of Standards and Technology, “Specification for the Advanced Encryption Standard,” Federal Information Processing Standards Publication 197 (November 26, 2001). Available as of January 2005, at: http://csrc.nist.gov/publications/fips/fips197/fips-197.pdf. |
also have a large “nonce” field, containing characters chosen at random, so that identical records would not have identical cipher texts. If each record is encrypted with a different cryptographic key, the party making the declaration could control access to each record individually. According to agreed rules, other parties could request decryption of selected records or all the records corresponding to a selected facility. By confirming the accuracy of a small random sample of records (e.g., through site visits), parties could gain confidence in the accuracy of the entire declaration even while most of it remained encrypted. The total number of weapons would be revealed by the total number of records; if desired, separate files could be exchanged for each facility or each category or type of weapon, thereby revealing the total number of weapons of each type or at each facility. If at an early stage parties did not want to reveal the total number of weapons, a large number of nonce records could be included in the declaration.
Another technique for exchanging secure declarations makes use of message digests. A digest is a unique digital fingerprint of a message. Government-approved techniques for producing and using digests (e.g., the “secure hash” algorithm or SHA-1) are routinely and widely used to authenticate electronic signatures and financial transactions.16 No keys are involved. One cannot determine the content of a message from its digest; there simply is not enough information in the digest to allow construction of the matching record, and the nonce field prevents the guessing of a record based on its digest. The digest produced by SHA-1 is secure because it is computationally infeasible to discover a message that corresponds to a particular digest. It is similarly infeasible for the party providing the digest to cheat by producing a second message that produces the same digest.
To see how message digests might be used, assume that a detailed declaration is prepared in an agreed format as described above, with a record for each weapon, and that parties have agreed on an algorithm for producing message digests. The declaring party could produce and provide the inspecting party with a separate digest for each record in the declaration. According to agreed rules, another party could select a particular digest and request
|
16 |
Representative government-approved hashing algorithms may be found in National Institute of Standards and Technology, “Secure Hash Standard,” Federal Information Processing Standards Publication 180-2 (August 1, 2002). Available as of January 2005, at: http://csrc.nist.gov/publications/fips/fips180-2/fips180-2.pdf. For example, the SHA-1 algorithm provides for messages of up to 264 bits (more information than is contained in the largest library) to be digested in just 160 bits (less information than is contained in this sentence). |
revelation of the corresponding record, process this record with the agreed algorithm and confirm that the digest produced is identical to that provided previously, and then verify the accuracy of information contained in the record through site visits, as discussed below. In this way, parties could gain high confidence in the accuracy of the entire declaration, even while most of it was represented only by the corresponding message digests.
Frequency and Confidentiality of Declarations
Informal declarations might be sporadic or a one-time affair, but a formal agreement could be expected to include provisions for the regular exchange or updating of declarations at agreed intervals. The INF and START I treaties, for example, established and successfully implemented a six-month interval for the exchange of data on the number of deployed delivery vehicles and launchers. Regular data exchanges should not impose a significant additional burden on states, as they presumably maintain a complete, detailed, and up-to-date database of weapon inventories for their own use.
In the event of very deep reductions in the number of nuclear weapons, there could be a desire for more frequent exchanges of information. In the long term, it might be possible to update declarations almost continuously; for example, one could construct a system that would continuously monitor weapons in a storage area and report this information on a real-time basis to other parties. One could also write a computer program that would automatically produce, from a state’s official nuclear weapon database, an encrypted declaration or a digest for transmission to other parties every time the official database is changed.
Finally, there is the issue of whether declarations should be made public or kept confidential between the parties. There is precedent for both approaches: the data on nuclear forces exchanged by Russia and the United States under the INF and START treaties were made public; declarations made by parties to the CWC and the NPT are confidential. The 1995 U.S. proposal on weapon and NEM declarations called for a confidential exchange of data between Russia and the United States on weapon inventories.
Although it may seem that a state should be willing to make public any stockpile data that it is prepared to share with potential adversaries, there is an overriding shared interest in preventing the release of information that could be useful to states or groups in-
terested in acquiring nuclear weapons. There may be information, such as the precise locations where nuclear weapons are stored or the measures that are used to protect or account for them, that nuclear weapon states would be willing to share with each other but not more generally, for fear that its release could aid someone wishing to develop or to steal nuclear weapons. As mentioned above, states may also fear that releasing information on the locations of nuclear weapons could trigger public opposition and protests or even terrorist attacks. The United States and its NATO allies, for example, might be reluctant to announce the locations of the small number of nuclear weapons for use on tactical aircraft based in Europe (even though nongovernmental organizations claim to know and have published these locations).17
We believe that confidential declarations can achieve most of the security benefits of increased transparency. If, however, declarations are intended to reassure publics and non-nuclear weapon state governments that nuclear weapon states are reducing their inventories of nuclear weapons, declarations should be made as openly available as possible.
CONFIRMING WEAPON DECLARATIONS
Declarations of weapon stocks could have value as a confidence-building measure even without measures to confirm their accuracy. If, however, declarations were intended to serve as the basis for agreed reductions in nuclear weapon stockpiles, we assume the parties to such an agreement would want verification measures, such as site visits and mutual inspections, to confirm their accuracy. The INF, START, and CWC treaties, for example, all provide for baseline or initial inspections to verify the accuracy of declarations as a prelude to agreed reductions or the elimination of weapons.
Site visits and inspections could have other benefits. By opening up formerly secret facilities, such as nuclear weapon storage sites, other parties can confirm that weapons are stored safely and securely against theft or diversion. This could make it possible for states to learn from each other, facilitating peer review and cooperation in improving the safety and security of weapon handling
|
17 |
See for example, William M. Arkin, Robert S. Norris, and Joshua Handler, “Taking Stock: Worldwide Nuclear Deployments 1998” (Washington, DC: Natural Resources Defense Council, 1998). Available as of January 2005, at: http://www.nrdc.org/nuclear/tkstock/tssum.asp. |
and storage, and setting standards for the extension of agreements on nuclear weapon limits to other states.
This chapter deals only with confirming the accuracy of weapon declarations at declared facilities. Chapter 4 considers the important and difficult issue of confirming the completeness of a declaration—that is, how confident one can be that additional weapons (and NEM) do not exist at other, undeclared facilities.
Operationally Deployed Weapons on Missiles
Russia and the United States have already devised procedures to confirm the number of operationally deployed weapons on missiles. START I provides for on-site inspections at ICBM and sub-marine-launched ballistic missile (SLBM) bases to confirm declarations of launchers and the missile type associated with each launcher. Moreover, the number of ICBM silos and SLBM launch tubes is easily confirmed with photoreconnaissance satellites, and verification of mobile ICBMs is facilitated by START I requirements to openly display upon request all mobile launchers at selected bases and to allow continuous on-site monitoring of assembly facilities for mobile ICBMs. These measures provide high confidence that declarations of deployed ICBMs and SLBMs are accurate and complete.
Under START I, Russia and the United States also specify the number of weapons permitted on each missile type. Each missile of a given type is counted as having the permitted number of weapons. This usually corresponds to the maximum number of weapons with which the missile has been tested or deployed, but START I allows each side to “download” missiles subject to certain limitations; for example, the United States is allowed to reduce the number of weapons permitted on its Minuteman III ICBMs from three to one, and Russia is allowed to reduce the number permitted on its SS-N-18 SLBMs from seven to three. Downloading presumably will be the principal method both sides will employ to comply with the limits established by the Moscow Treaty (e.g., the number of weapons on the Trident II SLBM could be reduced from eight to five).
To help confirm that missiles are armed with no more than the permitted number of weapons, START I provides for a limited number of reentry vehicle inspections of deployed ballistic missiles (silo-based ICBMs, mobile ICBMs in garrison, and SLBMs on submarines in port). Parties may request up to 10 such inspections
per year, with no more than 2 at any given base. The inspecting party selects a particular base and then a particular launcher within the base. The inspected party must demonstrate that the number of reentry vehicles on the selected missile does not exceed the number permitted. In practice, this has been done by removing the missile’s shroud and fitting covers over each reentry vehicle, or fitting over the front section of the missile a hard cover that contains indentations to accommodate each reentry vehicle. Although inspectors cannot see the reentry vehicles, they can verify that the number or shape of the covers could not accommodate more than the permitted number of weapons for that type of missile. In case of ambiguities, START I allows the use of radiation measurements to determine that an object is not a weapon.
If parties deploy fewer than the permitted number of weapons on some missiles, additional procedures may be necessary to confirm a declaration of the actual number of deployed weapons; for example, the inspecting party could determine the number of weapons by moving a radiation detector around the perimeter of the missile. Procedures for using a neutron detector to distinguish between the single-weapon SS-25 missile and the three-weapon SS-20 missile were worked out for the INF Treaty.
Sampling
The START I reentry vehicle inspections illustrate how the design of an inspection system can enable the use of sampling, which can greatly reduce the cost and intrusiveness of verification. With such a system, inspecting a small sample of missiles can produce high confidence in the accuracy of the entire declaration. As a simple example, assume a country has 500 deployed missiles and that four weapons are declared for each missile, for a total of 2,000 declared weapons. Further assume that the country cheats by arming 100 of these missiles with eight weapons, for an actual total of 2,400 weapons (20 percent more than the number declared). If 10 randomly selected missiles were inspected each year, there would be a 90 percent chance of detecting this violation during the first year, and a 99 percent chance after two years.18 Smaller violations
would have a lower but substantial probability of detection; in the above example, after one year there would be a 65 percent chance of detecting a 10 percent increase in the number of weapons, and an 88 percent chance after two years.
Sampling is likely to produce even greater confidence in the accuracy of declarations than indicated by these calculations if inspectors can target facilities where violations are thought to be more likely. If the inspecting party has intelligence information pointing to suspicious activity at particular sites, these sites could be selected for inspection. Similarly, a larger share of the inspection effort could be allocated to those missile types that can be armed with more (perhaps many more) than the declared number of weapons; for example, under reasonable assumptions about weapon loadings and the numbers of deployed missiles, inspection of just four Minuteman III missiles, three Trident II or SS-N-18 missiles, or two SS-19 missiles would give a 90 percent chance of a 20 percent increase detecting in the number of weapons above
|
|
spected is small compared to the total number of missiles. The exact formula is P = 1 – [(N–M)!(N– n)!]/[(N–M–n)!N!], where N is the total number of missiles and M = FN is the number of missiles in violation; in this example, P = 1 – [(400!490!)/(390!500!)] = 0.895 90 percent. Some would interpret this calculation to mean that ten inspections would give 90 percent confidence of compliance, or 90 percent confidence that the actual number of deployed weapons on missiles is less than 2,400. A proper calculation of the confidence in compliance produced by inspections would, however, take into account prior beliefs about the likelihood of cheating. If, for example, the inspecting party believed, before the inspections began, that there was a 10 percent chance of cheating as described above (i.e., a prior probability of compliance of 0.9), then ten inspections that uncovered no evidence of cheating would result in a posterior probability of compliance of 99 percent. The general formula is Pc’ = Pc/[1–P(1–Pc)], where Pc and Pc’ are the prior and posterior probabilities of compliance and P is the probability that the inspections would uncover evidence of cheating if it existed; in the above example, Pc’ = 0.9/[1–(0.895)(0.1)] = 0.9885. The posterior probability of compliance (Pc’) is greater than the probability that inspections would detect cheating (P) if the prior probability of compliance (Pc) is greater than 0.5. |
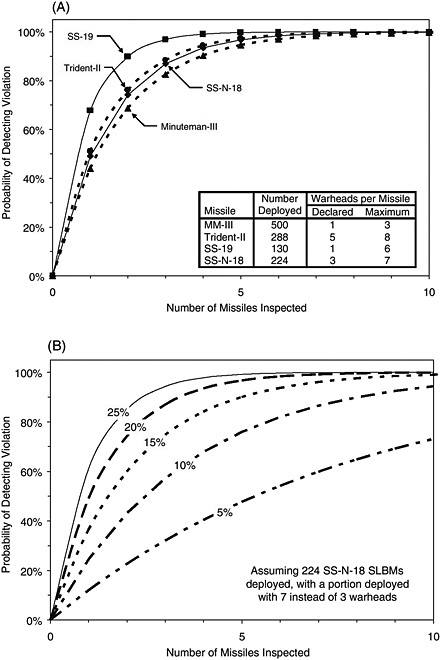
FIGURE 2-2 Illustrative examples of the probability of detection. This figure illustrates examples of the probability of selecting at least one missile armed with more than the declared number of weapons, as a function of the total number of missiles selected for inspection. The top figure assumes that the inspected party has deployed a total of 440 extra weapons (beyond those allowed or declared) on each of four U.S. and Russian missile systems, by arming a portion of the deployed force with the maximum number of weapons the missile can carry. The bottom figure illustrates how the probability of detection varies with the size of the violation, assuming that a portion of the Russian SS-N-18 SLBM is armed with 110, 220, 330, 440, and 550 extra weapons (5, 10, 15, 20, and 25 percent more than the total number of operationally deployed weapons allowed by the Treaty of Moscow).
the limit of 2,200 operationally deployed weapons set by the Treaty of Moscow.19 Doubling the number of inspections would increase the probability of detection to 99 percent. Figure 2-2 illustrates the increase in the probability of detecting a violation with the total number of missiles selected for inspection.
Stored Nuclear Weapons
Today, all nuclear weapons are either deployed or in some type of storage.20 Deployed strategic and nonstrategic weapons are mounted on missiles or are stored at air bases for nuclear-capable aircraft. Spare weapons may be stored at ICBM or SLBM bases and reserve strategic and nonstrategic weapons at central storage facilities. Weapons that have been retired or otherwise scheduled for elimination can be found at disassembly facilities.
Nuclear weapons are stored in special structures that are variously referred to as bunkers, magazines, igloos, or vaults. Individ-ual bunkers, such as those pictured in Figure 2-3, may contain a few to two dozen weapons. Central storage facilities may contain
several dozen such bunkers or a single structure divided into many vaults or bays. Storage facilities are blast resistant and usually earth bermed or located underground in order to limit the damage that would be caused by an accidental detonation of the high explosive in the weapons, and to protect the weapons from attack.

FIGURE 2-3 Storage bunkers at the Pantex weapon assembly plant in Texas.
Thousands of nuclear weapons are stored in the United States at numerous Air Force and Navy bases and the Pantex weapon assembly plant, and a small number of weapons are stored overseas. The corresponding numbers for Russia are less well known. The reduction and consolidation in U.S. and Russian nuclear forces over the last decade means that many facilities at which nuclear weapons were stored in the past are now empty or have been converted to other uses.
In order to confirm declarations of stored weapons, the declaration could include the location of each facility, site maps indicating the weapon storage area and the location of each bunker, and the number of nuclear weapons in each bunker or vault. As with reentry vehicle inspections, parties might be granted an annual quota of weapon storage inspections; for example, 10 per year, with no more than 2 at the same facility. Again, high confidence in the accuracy of the declaration could be achieved based on a small number of inspections. Suppose, for example, that a party had declared a total of 500 storage bunkers with 10 weapons in each bunker
(5,000 declared weapons) but had cheated by doubling the number of weapons in 100 of the bunkers (6,000 weapons, or 20 percent more than the number declared). If 10 randomly-selected bunkers are inspected, there would be a 90 percent chance that at least 1 of the 10 would contain extra weapons.21
Depending on the system, an inspection could begin with the selection of a particular facility from the list of declared storage facilities. The weapon storage area at this facility would immediately stand down; movement of weapons, entry or exit of weapon transport vehicles, and the opening of bunker doors would be suspended until the inspection was completed. Inspectors could then select a particular storage bunker for inspection and confirm that the number of weapons in the bunker matched the number in the declaration. If secure declarations were part of the monitoring system, then the records for that bunker could be provided and compared with the digests that had been provided earlier. Alternatively, the inspecting party could randomly select some number of digests for the facility, request the records corresponding to these digests, and then ask to see the matching weapons. 22
As with any procedure involving nuclear weapons, strict health and safety standards would apply to storage inspections. Inasmuch as personnel enter weapon storage facilities from time to time to take inventory and perform routine maintenance, it seems reasonable to expect that procedures could be developed that would give inspectors access to such facilities without significant risk to themselves or others.
Inspection of the chosen bunker could be accomplished in much the same manner as a regular inventory check: a visual inspection that matched each weapon in the bunker with a weapon in the declaration. It is likely that most weapons are in containers and that a visual inspection would not reveal any sensitive information, but if this were a concern the inspected party could be permitted to cover or drape weapons prior to inspectors entering the bunker.
Once inside the bunker, inspectors would have two basic tasks: identifying the nuclear weapons and matching them to the declaration, and determining that other objects are not nuclear weapons. Regarding the first task, it might be sufficient for the inspected party simply to point out each weapon, because the inspected party would have little incentive to claim that an object is a weapon when it is not. (An exception is when a weapon is retired and slated for dismantling; in this case, the inspecting party would want to make sure that the object about to be dismantled was a genuine weapon.) If parties had exchanged itemized inventories, the inspecting party could check that the serial numbers on the weapons or weapon containers matched the serial numbers given in the declaration. Tags could be used for this purpose instead of serial numbers (see Box 2-3). Discovery of a weapon without a valid serial number or tag would be prima facie evidence of a violation, a fact that greatly increases the power of inspections.
Regarding the second task, it seems likely that most storage bunkers do not contain objects that could be mistaken for nuclear weapons. Exceptions undoubtedly exist, however, and so procedures could be developed to demonstrate that an object is not a nuclear weapon. For objects that are not sensitive, such as an empty canister, this could be done by visual inspection. Otherwise, a simple neutron detector on one side of the canister and a weak neutron source on the other side could be used to confirm that the canister does not contain a nuclear weapon. This is similar to the procedure worked out in START I to confirm that a cruise missile is not armed with a nuclear weapon. The neutrons emitted by the plutonium in a weapon are easily detectable unless the weapon is shielded; the neutron source can be used to determine whether the container absorbs neutrons.
Visual inspection, supplemented by simple radiation measurements, would be a straightforward way to build confidence in weapon declarations. This method is not foolproof, however. It might not be able to detect weapons that do not contain plutonium, because the rate of neutron emission from highly enriched uranium (HEU) is very low. (The use of a detector in conjunction with a low-intensity neutron source would indicate that the object is suspicious, however.) Moreover, some nonweapon objects that may be stored in bunkers (e.g., weapon components, radioisotope thermal generators, or nuclear-explosive-like objects) might emit enough neutrons to be mistaken for a weapon. States may therefore judge that a formal agreement would require a higher degree of assurance that objects declared as weapons are indeed genuine
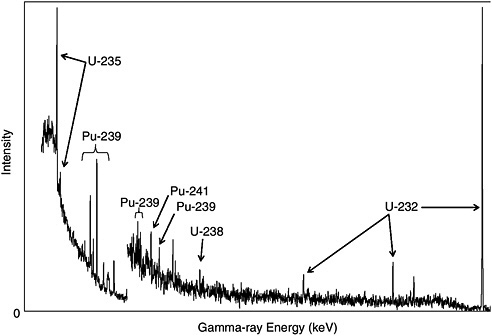
weapons, and that other objects are not weapons. Two general approaches to this problem—the “template” and the “attribute” approaches—are outlined in Box 2-4. We believe, however, that these relatively complicated procedures are better suited for identifying and verifying the authenticity of weapons prior to dismantling than for inspections to confirm declarations.
CONTINUOUS MONITORING OF WEAPON STOCKS
The previous section discussed the use of sampling to confirm periodic declarations of weapon stocks. In some cases, parties might wish to have additional assurance that certain weapons were being kept in a specified location; for example, there could be large numbers of inactive weapons that were retired and awaiting dismantling, or large numbers of nonstrategic weapons that, by agreement, were required to be kept in storage. Transparency measures that provide continuous information about the status of such weapons could help address concerns about their possible redeployment, diversion, or theft.
Several concepts for the continuous monitoring of weapons in storage facilities have been considered, ranging from perimeter-portal systems that monitor the flow of items into and out of a facility to systems that continuously monitor the status of items within a facility. In a perimeter-portal monitoring system, a secure perimeter forces all facility traffic though monitored portals. The perimeter typically is a fence established by the inspected party, the integrity of which is monitored by the inspecting party with various sensors (e.g., cameras, motion/intrusion detectors, acoustic and seismic sensors) mounted just outside the fence, supplemented by occasional foot or vehicle patrols. The portal is typically the facility’s main gate. The inspecting party monitors the portal for the possible entry and exit of controlled items—in this case, nuclear weapons and weapon components. In this way, the inspecting party can continuously monitor changes in the inventory of a facility with only occasional access to its interior (e.g., to establish the initial inventory).
Continuous perimeter-portal monitoring systems were first established at Votkinsk, Russia, and Magna, Utah, to verify the INF Treaty’s ban on the production of the SS-20 and Pershing II mobile intermediate-range missiles. Each party was allowed to perform around-the-clock monitoring for 13 years, including measuring all vehicles entering and leaving the facilities and inspecting any ve-
hicle large enough to contain a prohibited item. Because the Russian SS-25 ICBM, which also was produced at Votkinsk, has a stage that is similar in size to the prohibited SS-20, all SS-25 missile canisters leaving the plant were also subject to radiographic imaging to confirm their identity. Building on the successful INF experience, the START I Treaty extended perimeter-portal monitoring to two missile assembly facilities in Russia and Ukraine to help verify declarations of the total number of mobile ICBMs. Although similar systems and procedures could be applied to monitoring the perimeter of a weapon storage facility, portal monitoring is more challenging in this case because nuclear weapons are much smaller and more easily disguised than ballistic missiles.
As with the weapon storage inspections described above, portal monitoring can be divided into two basic tasks: (1) confirming that objects passing through the portal that are declared to be weapons are, in fact, genuine weapons, and (2) confirming that no other undeclared weapons have entered or left the facility. The first task is fairly straightforward. Facility management would notify the inspecting party that a certain number of weapons would be delivered to or removed from the facility at a given time, and inspectors would confirm the authenticity of a random sample or all of the weapons as discussed above, or using template or attribute identification.
The second task is to confirm that weapons are not being smuggled into or out of the facility, either whole or in parts. In most cases, visual inspection of vehicles combined with neutron and gamma-ray detectors at the portals would be sufficient to provide assurance against the movement of undeclared weapons. If the visual inspection revealed a container large enough to hold a shielded weapon, a low-intensity neutron or gamma-ray source could be placed on one side of the container and a detector on the other side to determine whether it might conceal the presence of a nuclear weapon. The portal could be equipped with radiography equipment to scan selected vehicles, but this would add substantially to the cost of the system unless it significantly reduced the need for human inspectors. If ambiguities arose, the burden of proof would be on the inspected party to demonstrate that objects and vehicles passing through the portal do not contain undeclared nuclear weapons or weapon components.
Although perimeter-portal systems in the past have required the continuous presence of inspectors (the INF and START I treaties allowed up to 30 inspectors), remote monitoring technologies could reduce the need for a continuing human presence and thus
the cost of operating such systems; for example, data from cameras and other sensors that confirm the integrity of a perimeter can be monitored remotely, requiring only periodic visits to test, maintain, or repair the equipment. If there were little vehicle traffic aside from weapon movements that are scheduled well in advance, even portal monitoring could be accomplished with little or no permanent on-site presence, provided provisions were made for rapid response to the loss of remote monitoring capability and for a freeze on all vehicle traffic until the monitors were restored.
A promising variation on this concept is remote monitoring of individual storage bunkers or vaults. One could, for example, mount a variety of sensors—video and infrared cameras, motion sensors, radiation detectors, laser break-beams, vehicle detectors, and the like—outside the access doors to each bunker to detect any attempt to enter and remove weapons. The sensor packages would be equipped with an uninterruptible power supply and housed in enclosures that prevented undetected tampering; sensor data would be encrypted, stored and also transmitted securely via telephone lines and/or satellite to a remote monitoring station. Similar systems are now used by the International Atomic Energy Agency (IAEA) for remote monitoring of the status of nuclear facilities and stocks of nuclear material. Except in an emergency, the inspected party could be required to give several days notice prior to opening the bunker doors, to allow inspectors to arrive and confirm any movement of weapons in or out of the facility.
Alternatively, one could remotely monitor the interior of weapon storage bunkers. The prototype “magazine transparency system” developed at Los Alamos National Laboratory uses a combination of commercially available, off-the-shelf sensors to maintain automatically an inventory of a bunker and detect any movements of weapons.23 During an initial inspection, each weapon storage container is covered with a blanket that contains magnets and a radio frequency identification tag. A video camera detects any scene change and a gaussmeter detects changes in the magnetic field caused by movements of the magnetic blanket; interrogation of the radio frequency tag provides inventory information and additional motion detection. A computer monitors all sensors and triggers an alarm message if movement is detected;
otherwise it sends an “all ok” signal. Measures can be taken to counter the use of intense, externally produced magnetic fields to spoof such systems.
In addition to monitoring facility inventories, one might also wish to monitor or track the movement of weapons between facilities; for example, parties might desire assurance that particular weapons removed from deployment sites were delivered to monitored storage, or that weapons removed from storage were delivered to dismantling facilities. Establishing the authenticity or provenance of items, tracking their movements between facilities, and confirming that they have not been tampered with is sometimes referred to as a “chain of custody.”
The least intrusive way to maintain a chain of custody involves the use of tags and seals. Tags uniquely identify objects; seals are tamper-indicating devices that prevent undetected access (see Box 2-3). Tags and seals must be difficult to remove, alter, or counterfeit without detection, and they must not compromise the safety, security, or reliability of the item to which they are attached or collect information not needed for monitoring. A wide variety of tags and seals have been developed, ranging from bar codes and tamper-indicating tape to electronic tags and seals. Tags and seals are used routinely by the IAEA to safeguard civilian nuclear materials, and were used by the U.N. Special Commission on Iraq to track items that could be used for both civilian and military purposes. Current technology makes available a number of approaches to tag and seal applications that would be extremely difficult to defeat without detection and that should not create legitimate problems for any party.
Chain-of-custody monitoring could begin when a weapon is removed from a delivery vehicle or operational deployment area and placed in a container that is tagged and sealed, or when the authenticity of a weapon is confirmed using a template or an agreed set of attributes. When the weapon enters or leaves a facility, the integrity of the tag and seals would be checked and its identity confirmed using the tag. This procedure could be done by inspectors at the portal to a facility or, if electronic tags and seals were used, the identity and integrity of tags/seals might be checked automatically whenever the canister enters or leaves a monitored facility or storage bunker. The integrity of tags and seals could even be monitored remotely and continuously; for example, Los Alamos National Laboratory has developed a prototype tag and seal that uses a low-cost, off-the-shelf video camera and transmitter to provide remote, continuous surveillance of its integrity as it is moved be-
tween facilities.24 This type of device could be used to monitor weapons as they are transferred from storage to dismantling facilities, and as they move through the dismantling facility.
CONFIRMING WEAPON ELIMINATION
Declarations of weapon stocks and transparency and monitoring measures to confirm their accuracy serve to establish baseline inventories of nuclear weapons. Extending transparency measures to weapon dismantling facilities could help confirm agreed or stated reductions in these inventories and provide assurance that weapons removed from the declared inventory were not simply moved to undeclared locations. There are several options for increasing the transparency of weapon dismantling operations, which draw on the technologies and procedures introduced above. In general, options that provide a higher degree of confidence that weapons have been dismantled come at the cost of greater intrusiveness and impact on normal operations, and require more effort to protect sensitive weapon design information.
Monitored Storage of Weapons and Components
The least intrusive option would involve monitoring the storage of weapons and weapon components, without monitoring the dismantling process itself. The inspected party would declare that a particular weapon was slated for dismantling. The inspecting party could confirm that this weapon was removed from a monitored storage facility; tags and seals on the weapon container could be used to confirm that the same weapon was delivered to the dismantling facility. After the weapon was dismantled, the inspected party would deliver its key components—the pit and secondary assembly—to a monitored storage facility, at which point the weapon would be considered eliminated. The inspecting party could confirm, using templates and attributes, that weapons going into the facility and components coming out were authentic. As before, a system could be designed such that inspection of a relatively small sample could be sufficient to provide a high degree of confidence in the authenticity of all weapons and components. Inspection of a random sample of 22, 45, or 230 objects could detect, with 90 per-
|
24 |
Eric R. Gerdes, Roger G. Johnston, and James E. Doyle, “A Proposed Approach for Monitoring Nuclear Warhead Dismantlement,” Science and Global Security 9 (2001), p. 113. Available as of January 2005, at: http://www.princeton.edu/~globsec/publications/pdf/9_2gerdes.pdf. |
cent probability, violations equal to 10, 5, or 1 percent of the total number of objects; doubling the number of inspections increases the probability of detection to more than 99 percent.25
By itself, this process would not, however, provide high confidence that the declared weapons were dismantled; for example, one could not rule out the possibility that the weapon components delivered to the monitored storage facility were recovered from other (perhaps obsolete) weapons, taken from existing component stores, or newly produced from existing stocks of plutonium and HEU. To rule out such possibilities, the inspecting party would need to have confidence that the components were recovered from the weapon that was delivered to the dismantling facility. This might be accomplished with fission product tagging, pit stuffing, or template or attribute matching.
Fission Product Tagging
It has been suggested that the inspecting party might “tag” weapon components while they are still inside the weapon by irradiating the weapon with neutrons before it is delivered to the dismantling facility.26 This would induce fissions in the plutonium and uranium components, giving them a characteristic gamma-ray signature that could be analyzed after the weapon is dismantled to determine whether it is consistent with the irradiation. A relatively large neutron flux is required to produce a measurable signature over the period required to dismantle a weapon. In addition, the signature probably could be spoofed.
Pit Stuffing
Another approach to component tagging is known as “pit stuffing.”27 As discussed in Box 2-1, nuclear weapons may use hollow-
|
25 |
If the sample size is small compared to the total number of objects (e.g., less than 10 percent), the probability of selecting an object in violation of the declaration depends only on the size of the sample and not the total number from which the sample was chosen. The general formula in this case is P = 1 – (1F)n, where F is the fraction in violation, n is the sample size, and P is the probability that the sample contains at least one object in violation. If the sample size is a larger fraction of the total number of objects, the probability of detection will be higher; see Footnote 18. |
|
26 |
Gerald P Kiernan, et al., “Interim Technical Report on Radiation Signatures for Monitoring Nuclear-Warhead Dismantlement.” JEP-009. Work performed under the auspices of the U.S. Department of Energy by Lawrence Livermore National Laboratory under contract No. W-7405-Eng-48 (April 17, 1997). |
|
27 |
Matthew Bunn, “‘Pit-Stuffing:’ How to Disable Thousands of Warheads and Easily Verify Their Dismantlement,” F.A.S. Public Interest Report (March/April 1998). Available as of January 2005, at: http://www.fas.org/faspir/pir0498.htm#bunn. |
boosted pits—a spherical shell of plutonium penetrated by a thin “pit tube” to admit the tritium-deuterium boost gas from an external reservoir. For such weapon designs, the inspected party could insert something into the pit that could not be removed without disassembling the pit, but which would not unduly complicate the later processing of the pit or disposition of the plutonium. Suggestions have included inserting a fragile wire that would fragment inside or epoxy or some other substance. This could have the additional benefit of rendering the pit and the nuclear weapon immediately unusable, since the wire would prevent a nuclear explosion.28 The pit tube presumably is accessible through a maintenance port in the weapon, because the radioactive decay of tritium, with a half-life of 12 years, requires regular replacement of the external reservoirs. The inspected party could perform the pit-stuffing operation, and the inspecting party could confirm on a sampling basis that the pits were stuffed, both before and after the weapons are dismantled, by taking x-ray images of a small part of the pit or by incorporating tiny amounts of a gamma-ray emitter (e.g., cobalt-60) into the wire and using a high-resolution gamma-ray detector to confirm its presence inside the pit. Alternatively, one might use the pit tube to attach a small tag to the pit (e.g., using wires that spring open in the hollow pit), that could not be removed without detection.
Template or Attribute Matching
Weapon components also might be associated with weapons using templates or attributes (see Boxes 2-4, 2-4A, and 2-4B); for example, the inspected party could present the separated components for templating along with the fully assembled weapon, and the templates could then be used to confirm, on a sampling basis, that the components placed in storage correspond to the type of weapon delivered to the dismantling facility. As always, the challenge would be knowing whether the items presented for templating were authentic. This could be determined by careful monitoring, as described below in “Monitoring Dismantling Operations,” of the dismantling of a randomly selected weapon of each type and using this weapon and its components for the templates. Alterna-
tively, one could determine whether certain attributes of the weapon match those of the corresponding pit or secondary assembly, such as the mass and age of plutonium in the pit or the mass and enrichment of uranium in the secondary assembly.
Perimeter-Portal Monitoring
A straightforward alternative for monitoring weapon elimination would be to equip each dismantling facility with a perimeter-portal monitoring system, similar to that described above for weapon storage facilities. Weapons to be dismantled would arrive at the portal, where their identity and authenticity could be confirmed using tags and seals and, at least on a sampling basis, templates and attributes. Weapons would be considered dismantled when the corresponding pits and secondary assemblies exit the portal for shipment to a component storage facility. Radiation detectors and other equipment and procedures could assure that no undeclared weapons or weapon components could pass through the portal without detection. Inspections of the facility might be permitted before and after dismantling campaigns to provide assurance that large stocks of weapons or components were not accumulating inside. Such facilities are very large, however, and it would be nearly impossible to obtain high confidence that weapons or components were not hidden somewhere inside.
The primary disadvantage of perimeter-portal monitoring is the relatively high cost of establishing and operating the system. Weapon dismantling facilities have very large perimeters; presumably, measures to guard against covert tunnels and passage-ways would be wanted. The portals would need to be heavily instrumented and would require the continuous on-site presence of inspectors to sift through the large volume of traffic in and out—including many items of a sensitive nature—and this could interfere with the normal operation of the facility. On the other hand, the United States and Russia have acquired extensive experience with perimeter-portal monitoring of missile production and assembly facilities under the INF and START treaties, and perimeterportal monitoring of weapon dismantling facilities could help greatly in monitoring weapon assembly and remanufacture (see below).
Monitoring Dismantling Operations
A third option would involve monitoring weapons as they move through the dismantling facility. This could be done—on a continuous basis with remote monitoring equipment or on a sam-
pling basis with on-site inspectors—by monitoring the bays and cells in which the key disassembly operations occur: the separation of the nuclear-explosive device or “physics package” from other weapon components, the subsequent separation of the primary and the secondary assembly, and the separation of the pit from the primary.
Monitoring could begin by escorting inspectors into the empty bays and cells to confirm that there were no hidden entrances and, using radiation detectors, that there were no hidden weapons or stocks of NEM. Inspectors could then monitor the entrance, or sensors could be installed at the bay or cell doors similar to those described above for continuous remote monitoring of weapon storage bunkers. When a weapon container arrived at the entrance, the inspectors or sensors could confirm its identity and authenticity by checking the tags and seals applied earlier (at a storage facility or the entrance to the dismantling facility). After authentication, the tags and seals could be removed and the weapon moved into the bay or cell. Here the first set of disassembly operations could be performed by the inspected party and the various components placed into one or more containers. Containers declared by the inspected party to contain NEM could be tagged and sealed as they left the bay or cell (by inspectors, or by the inspected party under remote observation). Other containers could be checked for the presence of NEM and those without it would not need to be subject to control thereafter. Controlled items could then be tracked to the next bay or cell and the process repeated, until the weapon was completely disassembled and the pit and the secondary assembly were in tagged and sealed containers, ready to be shipped to a monitored storage facility. The inspection protocol could include time limits for each disassembly operation and movements between bays and cells, as well as inspections of bays and cells between dismantling campaigns. With proper design, this type of monitoring system could give a high degree of confidence that particular weapons had been dismantled.
CONFIRMING WEAPON REMANUFACTURE AND ASSEMBLY
Along with monitoring weapon inventories, it would be logical to monitor possible additions to these inventories as well. Transparency measures to confirm the dismantling of weapons would be of limited value without complementary measures to monitor the
assembly of new weapons to provide assurance that no new undeclared weapons were being built. Measures to monitor nuclear weapon components and other inventories of plutonium and HEU and to confirm that plutonium or HEU was not being produced for weapons purposes could provide some assurance that significant numbers of new weapons could not be built without detection. As discussed in Chapter 3, however, it is difficult to establish accurately the baseline inventory of these materials and to rule out the possibility of hidden stockpiles that could be used to produce nuclear weapons. It therefore would be important to monitor weapon assembly facilities for the production of new weapons as well as the elimination of existing weapons.
This task would be simple and straightforward if the fabrication of all nuclear weapons could be ended. But weapons have a finite shelf life due to the aging and decay of high explosives and other materials, and so maintaining a nuclear stockpile over the long term requires the assembly or at least the remanufacture of weapons. Weapons may also be assembled to replace those dismantled or destroyed in routine (non-nuclear) reliability testing or to fix safety and reliability problems that may be uncovered in a particular weapon type. This would be true even if there were substantial reductions in the total stockpile of weapons.
Requirements for weapon assembly are likely to be modest as a result of reductions in weapon inventories and the absence of new types of nuclear weapons. The Bush Administration has indicated that the total U.S. stockpile will be reduced to fewer than 5,000 weapons over the next decade.29 If U.S. weapons are remanufactured every 45 to 60 years,30 the average rate of assembly would be
|
29 |
Colin L. Powell, “Remarks on the US-Russian Strategic Offensive Reductions Treaty,” Testimony before the Senate Foreign Relations Committee (July 9, 2002). Available as of January 2005, at: http://www.state.gov/secretary/rm/2002/11743.htm. See also Linton F. Brooks, “Report to Congress on the Revised Nuclear Warhead Stockpile Plan,” Unclassified Executive Summary. NNSA Press Release, June 3, 2004, and Linton F. Brooks, “U.S. Nuclear Weapons Policies and Programs,” Remarks presented at the Committee on International Security and Arms Control Symposium: Post-Cold War U.S. Nuclear Strategy: A Search for Technical and Policy Common Ground. August 11, 2004. Available as of January 2005, at: http://www7.nationalacademies.org/cisac/Brooks_Presentation.pdf. “In May of this year, the President approved a stockpile plan that will dramatically reduce the current stockpile. As a result of the President’s decision, by 2012, the United States’ nuclear stockpile will be cut almost in half and will be the smallest it has been in several decades” p. 5. |
|
30 |
This corresponds to the current estimate of the minimum lifetime of U.S. plutonium pits. See “Plutonium Aging: Implications for Pit Lifetime,” Appendix G, Modern Pit Facility Draft Environmental Impact Statement National Nuclear Security Administration (June 4, 2003), G-63. Available as of January 2005, at: http://www.mpfeis.com/. |
about 100 per year. Even if, as often assumed, the average lifetime for Russian weapons is two or three times shorter, the assembly rate need not be greater than a few hundred per year. These rates are roughly one-tenth the estimated capacity of existing U.S. and Russian assembly facilities. Reducing the capacity of these facilities could therefore be an important confidence-building measure. (In the case of the United States, the limiting factor at present would be the capacity to produce new plutonium pits, if necessary.) In the short term, one could install seals and monitoring devices on bay and cell doors to confirm that they had not been opened; in the longer term, excess bays and cells or entire facilities could be dismantled. The problem is becoming simpler in Russia, which has reduced the number of large assembly facilities in operation from four to two.
Parties might accommodate the need to continue weapon manufacture simply by agreeing to declare at regular intervals the number of weapons assembled and to permit transparency measures to confirm these declarations. Parties might even agree to permit only the remanufacture of weapons in the existing stockpile or the replacement of existing weapons on a one-for-one basis. In this case, transparency measures could be designed to confirm that a nuclear weapon had been removed from the stockpile for every new or remanufactured weapon added to the stockpile.
Some may argue that transparency measures for weapon remanufacturing might reveal vulnerabilities in the force. If, for example, Russia observed that the United States was rebuilding a particular class of weapons, it might conclude that this weapon type suffered from a major reliability problem. Russia would be likely to discover the existence of such a problem without the benefit of transparency measures, however. This knowledge seems unlikely to affect U.S. security significantly in any case since the United States plans to continue deploying several different weapon types.31 This is not a problem at the force levels permitted in the Moscow Treaty, but maintaining some diversity in weapon types would become important at much lower levels. Moreover, any imagined vulnerability could be dispelled quickly if the United States maintained an appropriate capacity to remanufacture nuclear
weapons. On balance, we believe that greater transparency for stockpile stewardship and remanufacturing activities of potential adversaries is more likely to prove a valuable confidence-building measure than a security concern.
If transparency measures were applied to weapon assembly, they would need to be tightly integrated with the measures adopted for weapon dismantling. If dismantling was confirmed with inspections or automatic tracking of weapons and weapon components between bays and cells within the assembly facility, weapons to be remanufactured or replaced could be tracked in exactly the same manner. The only difference is that new weapon components might enter certain bays and cells, and the end product would be a complete weapon and perhaps the old components.
If perimeter-portal monitoring systems were installed at weapon assembly facilities (e.g., using existing perimeter fences and gates), these could be used to confirm weapon remanufacture as well as dismantling. When a weapon arrived at the portal, for example, the inspected party could declare whether it was to be dismantled, remanufactured, or replaced. For weapons to be remanufactured or reassembled using the same pit and secondary assemblies, one would need only to confirm that the same number of weapons leave the facility; one could, with templates, confirm that the remanufactured weapons are of the same type as those that entered. For weapons that were being replaced or assembled with new components, the old weapons could be dismantled and the components shipped to a storage facility. New pits and secondary assemblies that entered the assembly facility for the declared purpose of assembling replacement weapons could be appropriately tagged and sealed before leaving the facility.
Another useful approach to building confidence is through open technical collaborations and exchanges related to maintaining confidence in the safety and reliability of existing stocks of nuclear weapons and minimizing the remanufacture of weapons. Conferences for scientists and engineers involved with stockpile stewardship could help to clarify the range of technical issues being addressed and the capabilities available for addressing these.32 Exchange of unclassified information regarding the properties of relevant materials—or their surrogates—could offer confidence that key issues in stewardship are being addressed by all parties,
for example. Even if the actual data were not shared, joint monitoring of experiments could also reassure the parties involved that no violations take place (e.g., no nuclear explosion yield during a period of test moratorium). Although some of the research discussed might be only distantly related to the most sensitive areas of work for one side or the other, the understanding provided to all sides by comparing notes at the unclassified level of basic research could enhance other confidence-building measures.
TRANSPARENCY MEASURES FOR NEM COMPONENTS
Because the pits and secondary assemblies that remain after weapons are dismantled could be used to build new weapons, the storage and ultimate elimination of these components could be subject to transparency and monitoring measures similar in nature to those applied to nuclear weapons. Fabricated NEM components are discussed here because many of the transparency measures and technologies discussed above for nuclear weapons could be applied with little modification to these components. Like nuclear weapons, details of component design are sensitive and must be protected. Moreover, unlike bulk NEM, which is discussed in the next chapter, pits and secondary assemblies are discrete objects that could be subject to item accounting.
Declarations
As with nuclear weapons, increased transparency logically would begin with a declaration of weapon component inventories. In the case of a formal declaration, parties would first need to agree on a definition of “weapon component,” such as, for example, “any object or item that contains NEM metal and that has been used or is in a form designed for use in a nuclear-explosive device, but is not part of an assembled device.”
Parties could declare the total number of pits, secondary assemblies, and other components or the total mass of plutonium and HEU contained in these components. This could help build confidence by limiting worst-case assessments of the capacity of other parties to rapidly reconstitute dismantled nuclear weapons. Component inventories could be further disaggregated by weapon type and current location, and ultimately into an itemized list giving the serial number, location, and corresponding weapon type of each
component or container. Even if a complete itemized inventory were considered highly sensitive, it could be safely exchanged in encrypted or digest form and its accuracy confirmed through inspections of a random sample of the items.
Monitored Storage
Declarations of component inventories could be confirmed using the techniques discussed above for nuclear weapons, through a combination of occasional inspections and continuous monitoring of declared storage facilities. The arrangements for the Russian fissile material storage facility at Mayak may be able to serve as a model for such initiatives. In exchange for U.S. financial assistance to construct the Mayak facility, Russia agreed to allow transparency measures to confirm that material placed in the facility was taken from dismantled nuclear weapons, that material in the facility is safe and secure, and that any material removed from the facility was not used for nuclear weapons.
The prototype attribute identification system described in Box 2-4B was developed to confirm that plutonium pits placed in the Mayak facility are authentic; similar systems could be developed for secondary assemblies and other NEM components. Russia has announced that the materials placed in the Mayak facility will be reshaped to remove sensitive weapon design information, ostensibly to facilitate IAEA inspection of the material (see Chapter 3). Although this reshaping would make the materials somewhat less immediately reusable for nuclear weapons, it would also reduce confidence that the material came from a dismantled nuclear weapon. Confidence would be higher if authentication were performed soon after a weapon is dismantled, while the pit and secondary assembly were still in their original forms.
NEM components are typically stored in special sealed canisters. At Mayak, the canisters are to be tagged with a unique identifier and entered into a computerized control and accounting system. According to the U.S. General Accounting Office, a 1999 draft of the Mayak transparency agreement contained the following provisions:
U.S. monitors would be allowed to inspect Mayak six times a year and utilize data generated by Mayak’s material control and accounting system. U.S. monitors would be allowed to spend at least 5 days to conduct the initial inspection. During each inspection, they would be allowed to download recorded data from sensors used by the Russians to identify, scan, and track each container as it passes
through Mayak’s unloading and incoming control rooms. Annually, U.S. monitors would be able to select randomly up to 120 storage shafts and verify the identifying tags on the containers in those shafts against Mayak’s records. U.S. monitors would have the right to scan one container from each of the selected shafts to determine its contents. Russia also would be required to inventory a random number of containers twice a year with U.S. participation.33
Provisions such as this, if ultimately accepted, could provide a high degree of confidence that the data contained in the declaration or control and accounting system are accurate and that components have not been removed from the facility. One hundred and twenty inspections under such rules would provide more than a 99 percent chance of detecting violations involving as few as 4 percent of the canisters. As of early 2005, however, the United States and Russia have not been able to agree on what monitoring measures are to be applied, so it is uncertain how comprehensive any eventual measures may be. Chapter 3 discusses the current situation in more detail.
Component Elimination
Nuclear weapon components are eliminated when they are mechanically and/or chemically converted into bulk materials. Transparency measures to confirm the conversion of HEU weapon components into bulk materials were developed in connection with the HEU purchase agreement, under which the United States agreed to purchase over a 20-year period 500 tons of Russian HEU from dismantled nuclear weapons in the form of low enriched uranium (LEU).34 The main steps in this process are as follows:
-
the HEU weapon component is machined into metal shavings;
-
the metal shavings are oxidized and the resulting oxide chemically purified;
|
33 |
U.S. General Accounting Office, “Weapons of Mass Destruction: Effort to Reduce Russian Arsenals May Cost More, Achieve Less Than Planned,” NSIAD-99-76 (Washington, DC: General Accounting Office, April 13, 1999). Available as of January 2005, at: http://www.gao.gov/archive/1999/ns99076.pdf. |
|
34 |
Throughout this report “ton” refers to metric tons. One metric ton is 2,205 pounds, roughly 10 percent more than an English ton. |
-
the HEU oxide is chemically converted into uranium hexafluoride;
-
the HEU hexafluoride (~ 90 percent uranium-235) is blended with LEU hexafluoride (1.5 percent uranium-235);35 and
-
the resulting LEU hexafluoride (about 4 percent uranium-235) is loaded into cylinders and shipped to the United States for use in the fabrication of fuel for commercial nuclear power reactors.36
Agreed transparency measures include on-site monitoring and reviews of the material control and accounting system documents by U.S. inspectors at the four Russian facilities involved in this process. Russia has similar inspection rights in the United States to confirm that the LEU product is used in the manufacture of reactor fuel. At each stage inspectors can inspect equipment, observe the processing of material, and use portable equipment to measure the enrichment of the uranium. At sites where HEU is blended, the “blend-down monitoring system” automatically and continuously measures the flow and enrichment of the HEU and LEU feed and LEU product flows. These transparency measures provide high confidence that the LEU delivered to the United States was derived from HEU.
By coupling this process with an attribute or template identification system to confirm that the HEU delivered to the facility was in the form of genuine weapon components, one could have similarly high confidence that these components had been eliminated. If such a system had already been used to identify weapon components at the dismantling or storage facility, it would only be necessary to check the integrity of the tags and seals on the canisters when they are delivered to the conversion facilities. Tags and seals could also be used to ensure a “chain of custody” on material that is moved from one facility to another in the conversion process.
The United States and Russia have agreed in principle to dispose of 34 tons of weapon-grade plutonium apiece, but progress toward implementation has stopped. It is expected, however, that
|
35 |
Low-enriched uranium (1.5 percent U-235) is used for blending instead of natural or depleted uranium in order to meet standards on the concentration of U-236 in the LEU product. |
|
36 |
A more detailed description, with photos of the major facilities and operations, may be found on the USEC Web site available as of January 2005, at: http://www.usec.com/v2001_02/HTML/megatons_stepbystep.asp. |
transparency measures similar to those described above would be required for the plutonium disposition agreement. Parties could confirm the authenticity of weapon-grade plutonium delivered to the conversion facility using the attribute method described in Box 2-4B, and monitor the conversion of the plutonium into oxide and the fabrication of the plutonium oxide into reactor fuel (or mixing with high-level waste and subsequent vitrification). Plutonium disposition is covered in more detail in Chapter 3.
Component Fabrication
A complete accounting system would also include additions as well as subtractions to the inventory of key weapon components. Future requirements for component manufacture are largely unknown. Lifetime estimates for U.S. pits and secondary assemblies are in excess of 50 years, in which case fewer than 100 per year would have to be fabricated to maintain a stockpile of 5,000 weapons, and only 10 per year for a stockpile of 500. The United States currently is studying options for constructing a “modern pit facility” that would process old pits and use the plutonium to fabricate new pits. Transparency measures could be negotiated for such facilities that allowed other parties to confirm the rate at which pits were processed and new pits were fabricated. Conceptually, at least, this would be most straightforward with a perimeter-portal monitoring system.
CONCLUSIONS
This chapter has reviewed and assessed the potential of a range of technical tools and methods to monitor all the phases of the nuclear weapon life cycle, from assembly to storage to deployment to dismantling and reuse or elimination. Past and current arms control agreements have provided significant practical experience in the design and implementation of monitoring systems for nuclear weapon delivery systems, including their production and storage. In addition, since the end of the Cold War, U.S. and Russian nuclear weapons laboratories, as part of their broader program of joint threat reduction activities, have carried out substantial cooperative work on extending these arrangements directly to nuclear weapons and their components.
We conclude that:
-
A range of transparency and monitoring measures are available that could be applied to declared stocks at declared sites to cover all the stages of the nuclear weapon life cycle, including
-
declarations of nuclear weapon stocks at progressively increased levels of detail, from all nuclear weapons to declarations by type, status and associated delivery vehicle, to declarations for each weapon by serial number, weapon type, status, and current location;
-
declarations of the name and location of all facilities at which nuclear weapons are currently deployed, stored, assembled, maintained, remanufactured, dismantled, or other otherwise handled, along with detailed information about each site and its operating history;
-
continuous monitoring of weapon stocks at facilities at all stages throughout the nuclear weapon life cycle, either with personnel on site or remotely;
-
confirmation of weapon remanufacture and assembly as well as weapon elimination; and
-
provisions for routine on-site inspections at declared facilities to confirm declarations and any updates, as well as for inspections of both declared and suspect sites in the event of detection of suspicious activity or unexplained discrepancies.
-
Similar measures could be applied to nuclear weapon components.
-
The necessary technical tools are either available today, or could be in hand with some additional development, to support transparency and monitoring measures for declared stocks at declared sites throughout the nuclear weapon life-cycle. These tools draw on the following techniques:
-
Developments in cryptography now widely used in banking and other commercial transactions offer a way to exchange, in a limited and controlled but still very useful way, sensitive information about nuclear weapons that countries would not be willing to share more openly and comprehensively because of security concerns.
-
Methods are available to examine from a short distance the radiation from a nuclear weapon or to interrogate a declared weapon container with an ex-
-
ternal radiation source. The radiation signature can be matched against “templates” of actual nuclear weapons signatures, or some portion of the radiation signatures can be singled out to identify “attributes” that confirm the object is indeed a weapon. These techniques permit identification without revealing sensitive weapon design information.
-
A wide array of tags and seals, ranging from bar codes and tamper-indicating tape to electronic tags and seals, can be applied to containers and storage rooms for weapons and interrogated to check their status.
-
Monitored perimeter-portal systems, which exploit radiation and other distinctive signatures, can be installed and operated to confirm that what enters and leaves any given facility is what it is supposed to be.
-
Facilities and areas within facilities can be equipped with appropriate sensors and accountability systems to monitor declared activity and detect undeclared activity, the recordings from which can either be examined during periodic inspections or uploaded via the Internet or satellites for transmission to a monitoring center.
-
Depending on the design of the system, cooperative application of these transparency and monitoring measures would make it possible to confirm the accuracy of declarations of weapon stocks and to monitor weapon storage, assembly, and disassembly at declared facilities while protecting sensitive weapon design information. (The degree of confidence that can be obtained about the completeness of declarations—that no secret stocks of weapons exist at undeclared facilities—is addressed in Chapter 4.)
-
Some of the less intrusive measures, in particular declarations of current weapons stocks .or of plans for future changes to those stockpiles, can have value in their own right as confidence-building measures. These measures could be undertaken unilaterally or through formal
-
In general, tools and measures that provide a higher degree of confidence come at the cost of greater intrusiveness and potential impact on normal operations. They also require more effort to protect sensitive weapon design information.
-
They are therefore more suited to formal agreements where the rules for the system’s operation can be agreed upon, including provisions for resolving questions or clarifying ambiguities. Experience suggests, however, that reaching such agreements can be a difficult and protracted process.
-
Even a modest subset of the measures outlined here could provide a degree of openness concerning weapon stockpiles and a framework for access to weapon sites that would greatly ease the difficulties of cooperation to improve security of nuclear weapons everywhere against theft or unauthorized use. For the more demanding purpose of monitoring agreements to control or reduce the stocks of nuclear weapons held by nuclear weapon states, the more intrusive measures would also be required.
|
BOX 2-1 The terms “nuclear warhead” and “nuclear weapon” have not been defined with much precision in existing treaties. The Nuclear Non-Proliferation Treaty (NPT) restricts the transfer or acquisition of “nuclear weapons or other nuclear explosive devices” but offers no definition for this term, nor do the treaties that prohibit the deployment of nuclear weapons in space or on the seabed. In the START I Treaty, the term “warhead” is defined simply as “a unit of account used for counting,” and earlier U.S.-Soviet arms control treaties used the term without definition. The most complete definition is given in the 1985 South Pacific Nuclear Free Zone Treaty (Treaty of Rarotonga) and the 1996 African Nuclear-Weapon-Free Zone Treaty (Treaty of Pelindaba): “‘nuclear explosive device’ means any nuclear weapon or other explosive device capable of releasing nuclear energy, irrespective of the purpose for which it could be used. The term includes such a weapon or device in unassembled and partly assembled forms, but does not include the means of transport or delivery of such a weapon or device if separable from and not an indivisible part of it.” This definition is not entirely satisfactory, inasmuch as “capable of releasing nuclear energy” remains undefined, but it under-scores the importance of understanding at what point a weapon is considered dismantled and no longer counted as a “nuclear weapon.” Like past treaties, agreements dealing with weapon transparency measures could simply refer to “nuclear weapons or other nuclear-explosive devices” without adopting a more detailed definition. As discussed in this chapter, there are several approaches for confirming, with varying degrees of confidence, whether or not an object is a weapon. In this way, the term ”weapon” would be defined operationally by the objects that are declared to be weapons and the techniques used to confirm that an object is a weapon. All nuclear weapons include a fission explosive device, which creates a divergent fission chain reaction by rapidly assembling a supercritical mass of nuclear-explosive material (NEM)—plutonium or highly enriched uranium (HEU). (See Chapter 3 and |
|
Appendix A for a further technical discussion of NEM.) Assembly can be accomplished by “implosion,” in which chemical explosives are used to compress a sphere or hollow shell of NEM, or by “gun assembly,” in which one mass of NEM is fired like a bullet into another mass of NEM. Thus, a nuclear explosive might be defined as “any device containing high explosive or propellants and nuclear-explosive material and capable of producing a nuclear explosion.”* The “Little Boy” device used on Hiroshima and the nuclear bombs built by South Africa are examples of gun-type devices. Gun assembly is relatively simple; the Little Boy and South African devices were produced without the benefit of a nuclear test. Gun assembly is inefficient, however, and too slow to permit the use of plutonium. (Unlike HEU, plutonium’s high rate of spontaneous neutron emission guarantees that the chain reaction would start and fizzle out before a sufficiently supercritical mass could be assembled.) Most nuclear weapons use implosion, which is much more efficient than gun assembly. The sphere or shell of NEM at the center of an implosion device, usually clad with beryllium or another metal, is called the “pit.” Either plutonium or HEU (or both) may be used, but plutonium is preferred because the mass of NEM required—and therefore the size of the resulting nuclear weapon—is smaller. The yield of an implosion device can be increased or “boosted” by introducing a mixture of tritium and deuterium gas into the hollow pit. The tritium and deuterium undergo fusion at the high densities and temperatures created by the implosion, producing high-energy neutrons that significantly enhance the fission chain reaction. The “boost gas” typically is stored in an external reservoir and transferred through a tube into the pit just before the weapon is detonated. Because tritium decays with a half-life of 12 years, reservoirs must be replaced on a regular schedule. In a thermonuclear or two-stage weapon, the implosion device is called the “primary.” Thermal radiation from the detonation of the primary is used to compress a physically separate “secondary.” The secondary assembly contains both fusion fuel and in most cases uranium (some or all of which may be HEU); this package, as it is delivered to the weapon assembly facility, is called a “canned subassembly” (CSA) in the United States. Compression of the secondary creates fusion reactions, releasing neutrons that fission the uranium. The secondary is responsible for most of the energy released by a strategic weapon, which is why the primary is |
|
sometimes called a “trigger.” The primary and secondary are housed inside a radiation case; the completed assembly is called the “physics package.” A deliverable nuclear weapon is produced by integrating the physics package with the safing, arming, fuzing, and firing system; neutron generators; batteries; and other components inside a bomb case or reentry vehicle. |
|
BOX 2-2 In secure declarations, each record or line (which, in the case of itemized declarations, might describe the location and characteristics of a particular weapon) can be thought of as sealed in an opaque numbered envelope that cannot be opened without the key to that particular envelope. Opening the envelope by force or stealth is not possible. The declaring party hands a stack of these sealed envelopes to the receiving party. Some time later, according to agreed rules, the receiving party can request the keys that will allow selected envelopes to be opened, to permit the accuracy of the records contained within to be confirmed. The exchange of encrypted declarations as sketched in the text makes use of AES encryption, in which each plain-text line (PL) is encrypted using a publicly known, standard encryption algorithm and a separate, secret key for each PL. The keys can be generated randomly using various techniques, at the option of the declaring party. The encrypted line thus produced by the declaring party is the “cipher line” (CL), which would be transmitted to the receiving party. The declaring party would retain a copy of each PL and the key used for that PL. Disclosure of a particular PL could be achieved by transmitting the corresponding secret key so that the receiving party could decrypt the CL using the same algorithm in decipher mode. Alternatively, the declaring party could supply the PL along with the corresponding key and the receiving party could apply the encryption algorithm to confirm that the previously transmitted CL resulted. Encryption involves protecting new secrets—the encryption keys—in addition to the original information in the declaration, but the keys can be protected at least as well as the original information. No method has yet been found that can break encrypted messages much faster than an exhaustive key search. Thus, if the keys are 128 bits in length, the receiving party would on average have to try 2127 keys to find the correct one to decrypt a given CL, or over 1042 tries to decrypt all of a declaration consisting of 10,000 CLs. This should be computationally infeasible for another 70 years, even if computer speeds continue to double every 18 months, as they have over the last 20 years.* For an extra margin of safety, longer keys can be used; for example, the use of 256 bit keys |
|
would increase the required number of tries to over 1080—about one try for every nucleon in the universe. Another approach is to exchange “message digests” rather than encrypted messages. This is called a “commitment,” because the message digest commits the declaring party to supply a particular message. Cryptographic hash functions are widely used to prepare message digests; for example, the U.S. government-approved Secure Hash Algorithm SHA-1 is used to prepare a 160 bit message digest (MD) from the individual plain-text line PL. SHA-1 is fully disclosed and no deficiency has been noted by the large international community interested in such matters. A brief analysis illustrates that it is impossible to determine or guess the PL (and the warhead data it contains) from its MD. Assume that the 160 bit MD produced by SHA-1 depends on the value and the position of each character in the PL, that the PL includes a nonce field (a string of random characters) of at least 1,024 bits, and that the PL itself is 2,048 bits total. There are 22048 possible PLs and only 2160 possible MDs; thus, each MD corresponds on average to 22048/2160 = 21888 10568 possible instances of PL. The given set of nuclear weapon data might have been combined with any of 21024 10308 instances of the nonce field, producing 10308 possible PLs. Thus, any of the weapon data lines could be used to produce the same MD when paired with very many instances of the nonce field. Therefore, it is fundamentally impossible, even with infinite computing capability, to deduce the original weapon data from the MD. Hash functions are also designed to have “collision resistance” and “preimage resistance.” Collision resistance means that it is computationally infeasible to find two PLs that produce the same MD. This is important, because otherwise the declaring party could commit to two different sets of data for each weapon, and produce whichever value was less damaging at the time. Preimage resistance means that it is computationally infeasible to find a PL that produces a particular MD. This is important, because otherwise the declaring party could find a nonce field which, when combined with any given set of nuclear weapon data (e.g., chosen to match the results of an inspection), would produce the previously exchanged MD, rendering the commitment meaningless. As with encryption, computational infeasibility is a quantitative question rather than a fundamental one, and an extra margin of safety can be obtained by using digests with a larger number of bits. With SHA-1, the declaring party would have to try 2160 trial |
|
hashes to find a preimage and 280 trials to find a collision. The recently approved SHA-256, which produces 256 bit digests, would provide preimaging resistance equivalent to symmetric encryption with 256 bit keys, and collision resistance equivalent to a key size of 128 bits. Additional security could be provided by concatenating the outputs of two or three different hash functions, to guard against the possible future discovery of a collision-finding algorithm for one of the chosen hash functions. |
|
BOX 2-3 A tag is any intrinsic characteristic or applied feature that uniquely and unambiguously identifies a particular item, such as a nuclear weapon or weapon canister. The simplest tag is the serial number or bar code that may already be stamped into or attached to the item. For verification purposes, it may be preferable to use an intrinsic or applied feature that is more difficult to duplicate, remove, or alter without detection. A seal is a tamper-indicating device that prevents undetected access. A seal need not prevent access (e.g., to the contents of a weapon canister); it need only record in some permanent and unambiguous manner that such access has occurred. The absence of a seal is one such unambiguous record. Tags and seals are usually used together; for example, a weapon canister may be tagged and the canister sealed so as to prevent the undetected removal of the weapon inside or the transfer of the tag. The tag and seal can be integrated into the same device; for example, a clamped bundle of optical fibers passed through a hasp can be used both as a unique identifier and as a seal. The distinctive pattern produced when light is transmitted through the bundle of fibers is extremely difficult to reproduce, serving as both a unique identifier and a tamper-revealing seal. The advantage of using tags and seals for verification is that they can provide unambiguous evidence of a violation, even if inspections occur infrequently or if only a small sample of the items are inspected. Discovery of a single weapon without a valid tag or a single canister with a broken seal would be prima facie evidence of a violation. A party wishing to cheat could not introduce weapons or canisters without valid tags and seals into declared facilities without running substantial risk of detection. Many types of tags and seals have been developed for commercial as well as arms control and nonproliferation purposes, ranging from bar codes and tamper-indicating tape to electronic tags and seals. Tags and seals are used routinely by the International Atomic Energy Agency to safeguard civilian nuclear materials and by the U.N. Monitoring, Verification and Inspection Commission (previously the UN Special Commission on Iraq) to track items that could be used for both civilian and military purposes. Several types of tags and seals |
|
were developed for use with the INF and START I treaties and, more recently, for use in nuclear weapon and NEM transparency applications. An “intrinsic” tag or seal takes advantage of unique microscopic features of each item, such as the surface of a metal container or a weld joining the lid and the container. Techniques have been developed to record and compare these microscopic features using plastic castings, scanning electron microscopy, and microvideography. Techniques also have been developed to record and compare the unique acoustic signatures generated when an item is interrogated by sound waves of various frequencies. A “passive” tag or seal is an applied feature, such as a serial number or bar code, that works without electrical power. Examples include various types of fiber optic tags and seals, reflective particle tags (reflective particles dispersed in an applied acrylic film), shrink-wrap (plastic film that is wrapped around items, creating a distinctive pattern), and wire loop seals. An “active” tag or seal, which requires a power supply, can continuously monitor its status and record indications of tampering; some can be interrogated remotely and report their identity and status. These include electronic and radio frequency tags and seals, active fiber optic seals, and smart bolts. Several devices can be integrated into a single tag/seal, including video cameras; motion, temperature, and tamper sensors; memory devices; and radio frequency transmitters. Before selecting a particular tag and seal technology it would be important to carefully think through the procedures for their application, validation, and removal, and to do a complete vulnerability assessment of the potential for counterfeiting, spoofing, and undetected tampering or removal. The challenge is to select technologies and procedures that make counterfeiting and spoofing by the inspected party much more difficult, time consuming, and costly than detection by the inspecting party of such counterfeiting or spoofing. The best choice may be an inexpensive tag or seal that is readily validated in the field, with a small sample collected by the inspecting party for detailed laboratory analysis. Even the simplest devices can be designed with features that are extremely difficult to counterfeit. Vulnerability analysis also must consider the possibility that a tag or seal could hinder the proper operation of an item or could collect intelligence information. Such concerns could be overcome through joint design and manufacture, together with random selection of tags and seals produced by the other party for detailed laboratory examination. |
|
BOX 2-4 Some types of treaty-limited objects are easily and accurately identified; for example, photographic observation—even from a satellite—has been considered sufficient to determine that a ballistic missile or a submarine is authentic. It is similarly easy to determine that other objects are not missiles or submarines. It is not so straightforward, however, to correctly identify a nuclear weapon: to ensure that an object that is declared to be a nuclear weapon really is a nuclear weapon, or that an object that is declared not be a nuclear weapon really is not one. Two general approaches to this problem have been developed: the “template” approach and the “attribute” approach. These are described in more detail in Boxes 2-4A and 2-4B. Templates identify a nuclear weapon or weapon component by matching certain of its characteristics to the characteristics of a weapon or component that is known or believed to be authentic. Attributes identify weapons and components by requiring that they display a certain set of characteristics possessed by all weapons or components. U.S. and Russian nuclear weapon laboratories have done considerable collaborative work to develop both approaches for arms control purposes and have produced several prototype systems to identify both nuclear weapons and weapon components.* Both approaches require measuring an agreed set of characteristics. Most of the template and attribute systems that have been developed use measurements of the radiation (gamma rays and neutrons) emitted during the natural radioactive decay of plutonium and uranium isotopes. These measurements can be used to characterize the composition, mass, shape, and arrangement of these and surrounding materials and thereby can be used to identify an object as a nuclear weapon or weapon component with various degrees of confidence. Each approach has strengths and weaknesses. Attributes identify objects with a single set of measurements; in the template approach, such measurements are compared with those for one or more reference objects. Templates therefore require the storage of information, while attributes do not. Attributes require specifying a set of characteristics that are true of all nuclear weapons or weapon components; templates do not. Templates can identify particular types of nuclear weapons or weapon components; attributes cannot. In general, templates can be far more dif- |
|
ficult to spoof than attributes, assuming that the reference objects are authentic. The attribute approach alone is unlikely to work well for nuclear weapons, due to the difficulty of specifying a set of attributes that would be displayed by all authentic weapons but not by any nonweapon objects. The attribute approach is particularly vulnerable to scenarios in which the inspected party creates a number of low-cost dummy weapons that display the selected set of attributes, which could be substituted for genuine weapons. The inspecting party might believe that the genuine weapons had been retired or dismantled, when only the dummy weapons had been dismantled and the genuine weapons were stored in a secret facility. Templates are better suited to the problem of identifying weapons. The primary disadvantages are the need to create a template for each weapon type, to have confidence that the reference object is an authentic weapon, and the need to securely store templates between inspections. The template approach could be vulnerable to scenarios in which a fake weapon is presented for templating, or in which the signatures of genuine weapons are modified or disguised so that they do not match any template. If parties wish to have high confidence that nuclear weapons are genuine and that other objects are not weapons, it probably will be necessary to combine the template and attribute approaches. Data gathered for a template, for example, could be analyzed to determine whether the object contains certain general characteristics or attributes of an authentic nuclear weapon, such as the presence of a certain minimum amount of weapon-grade plutonium metal and high explosive. In either approach, measurements performed for identification purposes may contain sensitive information about the design of the nuclear weapon or component; this is particularly true for gamma-ray measurements. For this reason, template and attribute identification systems are likely to require an “information barrier” to protect the measurement, storage, and analysis of sensitive data. Only the result of the analysis (e.g., “yes” or “no”) would be transmitted to the inspecting party. Information barriers are described in more detail in Box 2-4C. Before implementing an actual system employing templates or attributes, a critical review should be undertaken to confirm the extent of the real security concerns involved in order to avoid unnecessary complication in the equipment and procedures required. |
|
BOX 2-4A The template approach works by measuring certain characteristics of an object and comparing them with the same set of measurements taken from a reference object (e.g., an authentic weapon of a particular type): the template. If the two sets of measurements match, one can conclude that the object is a weapon of that type. The set of characteristics included in the template could include various combinations of a weapon’s mechanical, thermal, electrical, acoustical, and nuclear properties, but most concepts have relied entirely on gamma-ray emissions. Template systems based on gamma-ray spectra have been used for decades by the United States and Russia to identify their own weapons and weapon components; in Russia these gamma-ray templates are called “radiation passports.” The key components of nuclear weapons contain NEM, which are radioactive. Most of these isotopes emit gamma rays at a particular set of energies, and the isotope can be positively identified by its gamma-ray spectrum. These gamma rays are scattered and absorbed as they pass through materials inside the weapon; the fraction scattered or absorbed depends on the composition and thickness of the material and the energy of the gamma ray. Some isotopes also emit neutrons that, when absorbed by certain materials, result in the emission of gamma rays at particular energies. These many interactions result in a spectrum of gamma rays of various energies and intensities outside the weapon. An example of such a gamma-ray spectrum, recorded with a high-resolution detector, is shown below. More than two dozen peaks can be identified at energies corresponding to the decay of particular plutonium and uranium isotopes or neutron interactions with particular materials. The intensity of the various peaks depends on the exact composition, geometry, and configuration of many weapon materials and components. Weapons and weapon components of different types produce distinguishably different spectra. |
|
tected at all times: when templates are produced, stored, and when they are used to identify objects during inspections. Sensitive data can be protected during template measurement and analysis using an information barrier (see Box 2-4C). Protecting templates between measurements is a special challenge. Templates most likely would be stored on a removable disk or computer chip. The disk or chip must be protected so that the inspected party could not alter the data without detection and the inspecting party could not access the data. This could be done by placing the disk in a safe that requires two combinations to open, one held by each side; additional protection could be provided by encrypting the data with a two-part cryptographic key, with one part held by each side. Alternatively, the inspected party could have sole possession of the template and the information barrier could provide the inspecting party with a digest or “secure hash” of the template when it is made and each time it is subsequently used (see Box 2-2). This digest would uniquely identify the template and unambiguously confirm its authenticity, but the inspected party could not derive any information about the template from the digest. The U.S. Department of Energy has sponsored the development of several template-measuring and information barrier systems. These have demonstrated that a system could be designed for monitoring purposes that would reliably identify weapons while preventing the release of sensitive information. Brookhaven National Laboratory developed the Controlled Intrusiveness Verification Technology (CIVET) system, which was demonstrated to Russian scientists in 1997. Sandia National Laboratories modified CIVET for use with the Radiation Identification System to produce the Trusted Radiation Identification System (TRIS). Tests conducted at the Pantex plant demonstrated that TRIS could reliably identify various types of weapons and weapon components (pits and canned subassemblies). A sample of the TRIS results for templates representing five weapon types appears in the table below. For each template/object combination, the table gives a statistic that measures the goodness of fit between the object’s spectrum and the template. If the object is the same type as that used for the template, the value of the statistic should be about one; a value below a threshold of two or three might be used to indicate a match, with a very low probability of a false negative. In tests the system correctly indicated a match every time the object was the same type of weapon used to |
|
make the template, and correctly indicated no match in all other cases. Similar results were also obtained when identifying pits and canned subassemblies (CSAs), with one exception: the template system could not distinguish between components with very similar designs. This is not a problem in an arms control context, in which there is no need to distinguish between items that are almost identical. Active systems. Template systems based on intrinsic gamma-ray emissions—sometimes called “passive” systems—should work well for U.S. weapons, since they contain plutonium and uranium isotopes that emit penetrating gamma rays that are readily detectable and cannot easily be shielded. The penetrating gamma rays emitted by U.S. HEU are due to very small concentrations of uranium-232—an isotope that does not exist in nature but that is produced in nuclear reactors. U.S. HEU is contaminated with this isotope because uranium recovered from spent nuclear fuel was used to produce enriched uranium. It is believed that HEU in Russia and the other nuclear weapon states is similarly contaminated. It is possible, however, that weapons that contain uncontaminated weapon-grade HEU exist or might be assembled in the future. Because the low-energy gamma rays emitted by uranium-235 are readily absorbed by other weapon materials or easily shielded, the gamma-ray emissions from such weapons may be too weak to provide a useful template, if they do not include plutonium as well.
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
To deal with such problems and provide a more robust template, an external radiation source could be used to stimulate fission in the weapon’s plutonium and uranium components. An example of an “active” system is the Nuclear Material Identification System (NMIS) developed by Oak Ridge National Laboratory, which uses an external neutron source and time coincidence and correlation techniques to accurately characterize fissionable materials using the neutrons and gamma rays emitted during fission events. The external neutron source required is modest, with an emission rate only several times greater than that of a plutonium pit. In a blind experiment, NMIS correctly distinguished between 16 different types of weapons and components, demonstrating its usefulness for template identification. An information barrier would be needed, as the data would contain information about the mass and geometry of the nuclear components. The need for an external neutron source and the greater complexity of the required hardware and software, which would complicate authentication, makes it unlikely that such systems would be used for monitoring purposes unless templates based on intrinsic gamma-ray emissions were judged not to provide the required degree of confidence. Unclassified Templates. There may be several nonradiation types of measurements that could be used as templates to identify nuclear weapons. Templates that do not contain sensitive weapon design information would be useful, because they would eliminate the need for information barriers and would greatly simplify template storage and the certification and authentication of the measurement system. It may be possible, for example, to distinguish weapon types based on a combination of their acoustic, electromagnetic, and/or thermal signatures. Such alternatives have not received as much attention as radiation templates, probably because they are seen as easier to spoof. |
|
BOX 2-4B The attribute approach works by measuring a set of characteristics or “attributes” that should be displayed by all items of a given general type. To satisfy a given attribute, measurements of a weapon or component would have to fall above an agreed threshold or within an agreed range of values. This approach works best for items with the same general composition and design; for example, all plutonium pits contain a certain minimum amount of weapon-grade plutonium metal in a symmetrical shape. The United States developed a prototype attribute system to confirm the authenticity of plutonium pits to be stored in a U.S.-funded facility at Mayak, Russia. This system used six attributes:
The first three attributes were measured with high-resolution gamma-ray spectrometry; for example, the ratio of the intensities of the 642.5 keV and 646.0 keV gamma rays emitted by Pu-240 and Pu-239, respectively, is directly proportional to the Pu-240:Pu-239 ratio. Similarly, the relative intensities of gamma rays emitted by the Am-241 decay products of 14-year half-life Pu-241 can be used to determine its age (the time elapsed since the plutonium was last chemically purified). Plutonium mass was estimated using the number of single, double, and triple neutron events from Pu-240 spontaneous fission recorded by a neutron multiplicity counter, together with the Pu-240:Pu-239 ratio determined by gamma-ray spectrometry. Plutonium symmetry was determined with a neutron multiplicity counter, by requiring that the number of counts in each of eight detectors was within 15 percent of the combined average. The absence of plutonium oxide (a surrogate for the presence of plutonium metal) was measured using data from both detectors. As with templates, an information barrier must be used to protect the sensitive information contained in these radiation meas- |
|
urements (see Box 2-4C). In the system described above, the detectors and computers were housed inside shielded enclosures, all data were stored in volatile memory, and a “security watchdog” monitored the system for unauthorized access. The only output was a set of green or red lights to indicate whether the item being inspected satisfied each of the six attributes. This prototype system was demonstrated to a team of Russian scientists in the Fissile Material Transparency Technology Demonstration held at Los Alamos National Laboratory in August 2000. Although the system was developed to confirm the authenticity of pits, Russia now plans to store excess weapons plutonium in unclassified shapes at the Mayak facility. The attribute approach could be extended to other NEM components. Because HEU emits few high-energy gamma rays and almost no neutrons, passive radiation measurements are able to do little more than indicate the mere presence of HEU. As with templates, an “active” system would be necessary to provide a reasonable set of attributes for components that contain only HEU; for example, the Nuclear Material Identification System (NMIS) described in Box 2-4A could be used with a low-intensity neutron source to determine the mass and enrichment of HEU components. Applying the attribute approach to weapons is less straightforward because it is difficult to specify a single set of attributes that would be displayed by all possible types of nuclear weapons. Different classes of weapon may require different sets of attributes. For weapons that contain a plutonium pit, one might select attributes that indicate the presence of a certain amount of weapon-grade plutonium in a symmetrical shape surrounded by high explosive. The presence of high explosive could be indicated by the gamma rays that are emitted when neutrons are absorbed by nitrogen in the high explosive. As noted in the text, the attribute approach may be best applied to nuclear weapons as a complement to templates, to provide further confidence that items are genuine. A key difference between the attribute and template approach is that attributes cannot be used to identify the particular type of nuclear weapon or component. Whether this is an advantage or disadvantage depends on the nature of the transparency regime and whether parties wish to exchange and confirm declarations that include such details. A key advantage of the attribute approach over the template approach is that identification is based solely on measurements of the item under inspection and there is no need to store sensitive |
|
data for later comparisons. On the other hand, the specification of each attribute must be known to all parties, which could touch on sensitive information, such as the minimum amount of plutonium in a pit. This requirement, together with the need to accommodate differences among the various types of weapons and components and the desire to prevent false negatives (i.e., an authentic weapon or component that fails to display a particular attribute due to measurement error), could lead to thresholds for attributes that are well below the average values for most weapons. The threshold for plutonium mass selected by the United States was set at 0.5 kilograms, for example, which is believed to be well below the average. These factors make the potential for false positives (i.e., a nonweapon object that displays the set of attributes for a weapon) a greater concern for the attribute approach. |
|
BOX 2-4C A key challenge in implementing a template or attribute system is protecting any sensitive weapon design information that may be gathered during the identification process. This can be accomplished by automating the collection, storage, and analysis of data, and by making only the conclusions of the analysis available to the inspectors; for example, a computer could light a green lamp if an object’s gamma-ray spectrum matched the template or an attribute within specified tolerances, or it might report a summary statistic that measures the degree to which the object’s spectrum and the template matched. As illustrated in the figure below, the detector, computer, and template storage are housed inside an “information barrier” which prevents transmission of electronic signals or other surreptitious access to the sensitive data contained inside. Countries could build the systems used to inspect their own weapons, so they could be sure there were no hidden transmitters or storage devices or intentional flaws in the information barrier. 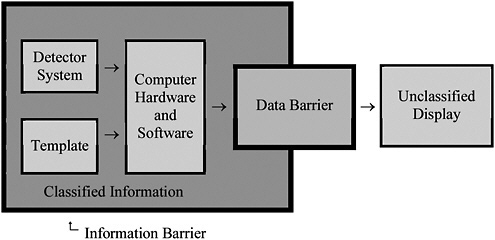 Because an information barrier prevents access to the data and the analysis upon which the results of an inspection are based, the inspecting party must authenticate the system. The inspecting party |
|
must be confident that the results produced by the system accurately describe inspected objects over the full range of possible objects and conditions, and that the system contains no hidden features that could interfere with or bypass the proper analysis or result (e.g., hardware or software changes that produce a green light during every inspection, or that allow the system to respond to remote commands from the inspected party). Authentication can be facilitated by cooperative design of measurement and information barrier systems; thorough documentation; the use of simple, commercially available hardware; and the documentation of all source code for system software. If these guidelines are followed, the system can be authenticated by thoroughly examining the hardware and software and confirming that they correspond to the documented design. The inspected party could build multiple identical units and allow the inspecting party to choose one for weapon inspections and another for detailed examination, including the removal of selected components for laboratory testing. After a system is authenticated, tamper-revealing seals can be placed in key locations to detect any attempt to alter the system. Proper operation of the system over a range of conditions can be checked using a variety of unclassified test objects, which could be provided by either party. As noted in Boxes 2-4A and 2-4B, prototype information barrier systems have been developed by the United States for template and attribute measurement systems, and their use was demonstrated to Russian scientists during the Fissile Material Transparency Technology Demonstration. |