Panel IV—
Partnering for National Security
INTRODUCTION
William B. Bonvillian
Office of Senator Lieberman
Mr. Bonvillian, who had been involved in shaping the homeland security legislation, conceded that it had been a “struggle,” at least partly because it was located “in an unclear legislative area.” He suggested that the panel could help answer one of the most difficult design questions—how to create the government-industry interaction that is necessary to stimulate the innovations that will be needed by the Department of Homeland Security.
One reason to hope this might be possible, he said, was that Congress had succeeded in crafting an apparatus within the legislation that supports scientific and technological innovation. On this, he said, Congress had showed a “remarkable and bipartisan consensus” that was “heartening.”
In countering bioterrorism, he said, the largest research portion of the R&D challenge is on “the biothreat side.” In the physical sciences, the issue is more developmental: the need for better sensors, detection, knowledge management, data mining, information technology, and physical protection.
He listed some of the other major challenges:
-
While the R&D challenge is major, the deployment challenge is “huge.” Some 85 percent of the nation’s critical infrastructure is in private hands, he
-
said; this meant that “technology transition is going to be crucial for this new department.”
-
The new department had a big information management problem. The department is large, and it needs to exchange information with the other agencies it interacts with, and those agencies represent a large part of the federal government.
-
Most of the R&D on homeland security would continue to be performed outside the new department. The contributions of DoD, NASA, DoE, and NIH would dwarf what occurred in the new department. The challenge was “get all these players operating on a common R&D roadmap.”
Key Elements in the New Department
He reviewed some of the key elements in the new department. First, the S&T activities were headed by an undersecretary. It was necessary to have an individual with sufficient rank and title, he said, to gain the attention of peers in this complex interagency process. Second, the new department was designed to include a DARPA-like entity to emulate one of the roles DARPA23 had played: to use its funding to leverage contributions from service R&D and from R&D centers throughout the defense research establishment. He credited DARPA with “playing a coordinating role and encouraging concentration and focus within DoD.” That, he said, would be the objective for this one significant piece of the Department of Homeland Security. “It will have DARPA’s leanness, its flexibility of personnel, access to talent, and freedom from some Civil Service limitations that are not appropriate for a scientific organization—in other words, the procurement flexibility that DARPA’s used so effectively over the years.” He said that HSARPA would also have an acceleration fund, with a “significant” level of funding. The goal, he said, was to enable it to leverage participation and cooperation across a whole series of agencies, in addition to what the department is undertaking, and also to involve the private sector.
A third element of the DHS research plan was the use of the FFRDC24 concept. The undersecretary of S&T would be able both to establish an FFRDC and to have ready access to existing FFRDCs. One of the central recommendations by the National Academies in their homeland security conclusions was the recommendation that an FFRDC should play a key role, particularly in the areas of threat and risk assessment and risk management.
Other elements, he said, remained to be worked out. One was a mechanism to coordinate among the various agencies that would be involved. The Senate bill proposed a coordination council, with statutory framework, tasked to develop an interagency technology roadmap for homeland security. It would also have private sector participation, advice, and support.
Another element to be added was a mechanism that served as a clearinghouse. One of its jobs would be to evaluate private-sector technology solutions. After the 9/11 attack, he said, DoD was inundated with technology suggestions that it had still not been able to sort and respond to. A clearinghouse was needed to manage, identify, and evaluate national technological opportunities that might be relevant to the new department’s and the nation’s needs.
A third job for the new entity would be to play a significant role in encouraging and sponsoring technology transition. In addition to the problem of coherence in technology development outside the department, he said, there is “a huge problem inside.” The DHS was enlisting the collaboration of numerous entities from different agencies in the government that did not have a history of close cooperation. DHS will need to have them to cooperate, and to have interoperable systems in order to function efficiently.
A Lack of Good Models
The implication was that these entities would have to pair up more closely than they had in the past. Mr. Bonvillian described several models that had already been tried, with less than perfect outcomes. In one, DoD had managed the different jurisdictions responsible for ports, aviation, and border security by joining acquisition and technology beneath the same undersecretary and paralleling that structure with assistant secretaries in the services. A criticism of that model has been that acquisition became the main focus, with technology acting as the “bill payer,” in effect, for acquisition activities. For DHS, he said, a different approach would be tried, making the S&T function more independent. But how do you get technological coherence if you separate S&T? he asked. “By having the undersecretary for S&T serve as a technology officer for the department, in a business sense,” he said, “and ensuring that the undersecretary has the sign-off on the testing and evaluation process.” This would create a clear point well before procurement where technology, interoperability, and connections are ensured.
He said there was also an “understood” strategy for private-sector involvement at an early stage. The challenge was that pharmaceutical and biotech companies, which make vaccines and other drugs, need a market incentive to justify R&D investments. The possibility of a public health disaster was not an incentive that would draw a biotech firm into the biothreat business. The government needs to help firms develop business plans and find new incentives, such as intellectual property incentives and procurement incentives. “I would argue,” he said, “that
there are other areas where that same kind of creative thinking is going to have to go on in the private sector.”
He noted that this was the first significant new science and technology agency the government had created in 45 years. The government had generally had a policy of decentralizing science, which had brought many advantages. There is no “science czar” or science ministry; instead, there are many actors pursuing different missions. There are advantages to this diversity, including the research power of multiple points of view and approaches, the opportunity for research entrepreneurship, and the good chance of avoiding the mistakes that often occur when a centralized science bureaucracy dominates decision making.
The downside becomes apparent when the government needs to build cross-agency and cross-discipline collaboration, as it does in the case of homeland security. “We’re in an era where advances come out of cross-disciplinary work,” he said. “How do you create those connections? We haven’t been able to do that very well in our science portfolio.” The new DHS, which had a bipartisan consensus, would try to deal with that problem by using the acceleration fund as an incentive for interagency cooperation. It also planned to use the interagency council and a technology roadmap from that council.
Better Management of Technology Transition
Mr. Bonvillian also addressed the underlying issue of technology transition, because of the need to have the full cooperation of the private sector. He described a clearinghouse mechanism to enhance private-sector participation, with the goal of a non-bureaucratic entity that is lean, entrepreneurial, flexible in its procurement practices, and has access to quality talent. Obviously, he said, one could not “write culture into a statute,” so much would depend on the original leadership of the department. A helpful beginning would be to enable private-sector leadership rather than government leadership in critical areas.
He concluded by pointing to the need to “tackle the whole information management challenge within this department and connect it to other entities—for example, in the area of intelligence.” He predicted that the new department would be one of the largest collectors of information in the government—“staggering amounts of information coming in about people and goods and cargoes and items entering and departing this country.” That information, he said, would be worthless unless it connects with the knowledge of threats or can be analyzed to develop information about threats. This would require efforts to build strong information management, and to integrate the department’s R&D, including effective connections and opportunities with the private sector.
“That’s a background of what we’re aiming for in this new department,” he said, “and some of the challenges that Congress has been addressing.”
OVERCOMING INFORMATION OVERLOAD
Anne K. Altman
IBM Corporation
Dr. Altman, who manages IBM’s relationships with the federal government, said that the “overwhelming amount of information” that many organizations, especially government agencies, must deal with today constitutes a daunting challenge. She said she would talk about some of the insights she and her colleagues at IBM had gained from working with other large organizations with information challenges.
She divided those insights into three areas. The first was the need to develop an integrated information architecture—one that actually serves to achieve its objectives. The second was to create partnerships to collect and manage information—not just government sharing with government, and government with academia, but government with business and government with citizens. The third was to implement technologies and public policies that ultimately enhance the government’s ability to partner and achieve its missions.
She opened with a brief discussion of the new Transportation Security Administration to illustrate “just how overwhelming the information challenge can be.” She described the multiple data exchanges between the government and the private sector generated by each passenger who boards a commercial airplane in the United States. She saw this process as a “powerful statement of the direction and vision of coordinated information.” What the process illustrated, she said, was the future of passenger transport and security that is TSA’s mission. The TSA describes its mission as ensuring the freedom of movement of passengers and cargo.
Every day, Dr. Altman said, some 1.6 million passengers board commercial airplanes in the United States, bringing three million pieces of luggage to 429 airports.25 She began with the private-sector data. For each passenger, data are collected by the travel agent, the airline, a rental car agency, perhaps the airport authority, and a credit card company. Information collected by the government might include passenger lists (which in the future would be pre-screened and compared with law-enforcement databases); information from the FBI, the INS, and perhaps the CIA; perhaps a tip from a citizen that is “used and massaged” in evaluating a passenger profile. In addition, carry-on bags are scanned; checked bags are examined for explosives; and video cameras record passengers’ movements in strategic locations.
She noted that airport security is just one component of the Borders and Transportation component of the homeland defense mission. The additional five
components are Intelligence and Warning, Domestic Counterterrorism, Infrastructure Protection, Catastrophic Threats, and Emergency Preparedness and Response. And each component must have an information strategy that is integrated with the strategy of every other component.
In the case of port security, for example, she said that U.S. ports handle 16 million containers annually, or 44,000 containers a day, delivering nearly half of all imported goods. Across its borders, the country admits every year some 11 million trucks, 2 million rail cars, and 330 million legal visitors. For all of this flow of people and goods data must be collected and managed.
For the new DHS, the six primary missions are to be accomplished by 22 organizations described in the legislation (see Figure 19). Each organization must coordinate people, processes, and information structures and systems. The chart demonstrates the possibility of a common information strategy across the six homeland defense missions.
She said that it was likely that the same information could be used to achieve multiple objectives across this organization, so that an overarching architecture must exist to make critical information available to execute this mission. There were important principles to follow if the U.S. is to be the world leader in using
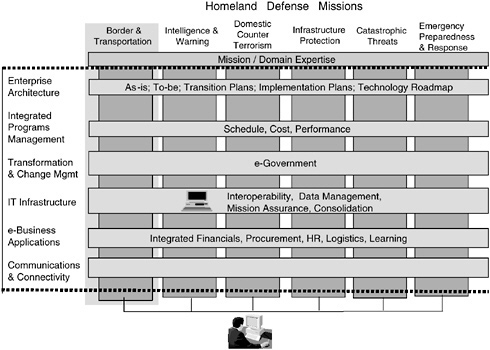
FIGURE 19 Partnership opportunity—Apply common information strategy across missions.
information to achieve Homeland Security. Federal agencies must not only work out on how they will share data among themselves, but also with local, state, and foreign governments, with the private sector, with academic institutions, and with citizens. She said that the challenge was much like that encountered during a merger in the private sector, “although I think this is perhaps the largest and most expensive merger ever attempted.” Nevertheless, she suggested that policy leaders should draw on the experience of the private sector, which had successfully merged people, processes and information systems in ways that not only minimizes the cultural impact, but maximizes the overall effectiveness of the merger.
Two Keys to Successful Partnerships
There are two keys, she said, to successful partnerships. One is technology and one is public policy.
For technology, she discussed her experience in meeting with customers after September 11. At major federal agencies, she discussed their concerns about how to respond and be proactive in the future. Three questions came up: the first was how to get old and new data systems to communicate. The second was how to link together information that resides outside a particular organization. The third was how to link and connect data from a variety of disparate data sources.
She illustrated a tool called WebSphere, a type of software called middleware, that had been developed to address these concerns. This tool is designed to enable systems to communicate and conduct a wide range of information services and transactions. In the middle was a “discovery link,” which creates a “federated data base,” developed by IBM in the life sciences arena to help in drug discovery. This technology could enable agencies to connect disparate data sources—text, video, audio, and other types of data—as if they were part of one common database.
Lastly, she discussed “Web Fountain,” an advanced information discovery system that allows users to locate information that resides outside their organization. “What’s exciting,” she said, “is that it’s a blending of the known information you have with information perhaps out on the Internet; it allows for rich trend, pattern and ultimately relationship detection, a powerful tool for the needs of homeland security.”
Expanding government’s ability to share and access data does raise many questions about privacy and security, she said. Law enforcement sources cannot be compromised, and companies have to be assured of unfettered access to sensitive data. Technology offers many of the answers. In fact, she said, IBM has a technology that can be employed to protect the anonymity of sources of information, which may facilitate the ability to share sensitive data between organizations.
But data security and privacy require much more than technology, she suggested. They require thoughtful policy. She said that policy decisions by
lawmakers and federal executives are the foundation for long-term success. She listed public policies that are key to successful technology partnerships:
-
Open, standards-based infrastructure
-
Government as early adapter
-
Review restrictions to data sharing
-
Security and privacy
-
Cultural change and leadership
-
Critical skill sets
-
Indemnification for business
-
Research and development
-
Investment in information technology
The Argument for Open, Standards-Based Platforms
She highlighted two of these, beginning with open, standards-based infrastructure.26 The development of an information architecture or framework is critical, she said. Software comprises this framework, and it has to be built on open, standards-based technology. Standards-based computing with interoperability is critical for a number of reasons. It permits the user more choices; it enables end-to-end administration and security; it is necessary for multi-vendor, multi-platform computing; and it permits easier collaboration and integration of information sharing.
She said that when IBM began restructuring its own IT infrastructure in 1993, the company had to step back and define a consistent architecture for the corporation—a large challenge for a company of 350,000 people operating in 150 countries. It decided to move to a standards-based system. One step was to consolidate 155 data centers into the current number of seven. Another step was to replace 31 segregated networks by a single network. IT costs were cut by 25 percent, saving the company billions of dollars. She said that the federal government could achieve the same kinds of results, since it was already very dependent on open, standards-based infrastructure.
The second important policy she suggested was that government should be an early adapter of new technologies. “We’ve heard how important this is as we apply new technologies,” she said. “But for some technologies, government may be the only entity with the size, the resources, and the mission to bring advances forward.” She said this often meant bringing “true laboratory, detailed research”
out of the lab and into the marketplace. An example she cited as important to her business was supercomputing. Without the a good partnership between industry and government, she said, it was unlikely that either partner could have produced the significant advances in commercial supercomputing “in this country or the world.” She recommended that government leaders enable cutting edge technologies by smart investments that create new abilities for homeland defense.
Dr. Altman summarized her discussion of information overload by saying that integrated information architecture was the first and most important area to consider. Success depends largely on organizing information lines and applying a common information strategy across the missions of various agencies. “We all know,” she said, “that disjointed information silos residing in many agencies will not get the job done. So government leaders need a free flow of information across their organizations and information systems that facilitate that.”
The second area she discussed was partnerships. “It’s a complex arena,” she said, “and no one can go it alone.” Partnerships need to draw on the combined expertise of government, business, academic institutions, and citizens. Each member of this partnership brings unique information and abilities for optimizing homeland defense decision making.
The third area was technology. “I think technology is key to cementing the partnership,” she said. “We believe that it’s the underpinning of open, standards-based architecture, allowing communication between various systems.”
She said she had recently been asked how a business model translates into information technology. Ultimately, she said, business models translate into the software that is enabled through middleware, “and if we don’t depend on that open, standards-based approach, ultimately these business models will fail.”
Her last topic was public policy. “We should embrace sound public policies,” she said, “that enhance our ability to exploit technology and achieve missions.” This, she said, means intelligent investment in technology, research, and skills development. It means balancing the need to collect and share data with the need for appropriate security and privacy policy. And it means leadership—to promote interagency cooperation and to serve as an early adopter of critical technologies and standards.
NEW TECHNOLOGIES FOR NEW THREATS
Ronald M. Sega
Department of Defense
Dr. Sega began by saying that partnerships are very important to the Department of Defense (DoD), especially during its current transformation toward the new century. The current century, he said, is expected to be characterized by more uncertainty, and to demand a higher rate of technological change to prepare for that uncertainty.
The general direction of the DoD’s transformation was defined in the Quadrennial Defense Review (QDR) submitted to Congress on September 30, 2001, which emphasized three cross-cutting initiatives: (1) national aerospace, (2) surveillance and knowledge, and (3) energy and power. The QDR included the following statement about transformation: “The evolution and deployment of combat capabilities provide revolutionary asymmetric advantages to our forces.” The concept of asymmetry, he said, implies that “things are not the way they were in the twentieth century, as evidenced by the current global war on terrorism.”27
The “critical capabilities” expected to bring about advantages were these:
Protect bases of operations
The DoD moved quickly after September 11 to combat terrorism, strengthen chemical and biological defenses, bolster missile defense, and plan for consequence management. On September 19, he said, only eight days after the terrorist attacks on the World Trade Center, the DoD formed a Combat and Terrorism Technology Task Force, bringing together leadership of the services and agencies. Two days later the task force had identified roughly 150 candidate technologies that could be brought to bear within approximately 30 days. A week or so after that it added additional participation from other agencies. On September 21, the group also decided to accelerate the development of several technologies, and was able to bring them into the field before the end of the year.
Conduct information operations
This included defensive information operations (IO) and information assurance. The strategy was to be able to communicate among all segments in the services and among all coalition partners.
Project and sustain U.S. forces
Top priorities were the detection of chemical, biological, radiological, and nuclear threats, as well as mines and other explosives.
Deny the enemy sanctuary
This involved a strategy of persistent surveillance, tracking, and rapid engagement with precision strikes. Tools included remote sensing and Enhanced
C4ISR (Command, Control, Communications, Computers, Intelligence, Surveillance, Reconnaissance). “We’ve been doing that for a while,” said Dr. Sega, “and the theme is to know the space in which you’re operating. That may be an urban warfare environment, including just a few city blocks; it may be a battle space; it may be the country.” Denying sanctuary also makes use of unmanned aerial vehicles, long-range precision strikes, small-diameter munitions, and munitions to defeat hard and deeply buried targets. He added that the DoD had just created a new entity called the Northern Command, which was “responsible for the defense of North America.”28 The command plays a defensive role, and also supports civil authorities when requested for consequence management.
Conduct space operations
The primary goals of this mission are to ensure access to space, protect space assets, conduct space surveillance and overview, control space, and make use of sub-orbital space vehicles. An essential capability is to be able to cue other sensing systems.
Leverage information technologies
High-capacity, interoperable communications are essential to allow the Army, Navy, and Air Force to communicate with one another, said Dr. Sega. It is also important for coalition partners and the new Northern Command to communicate with civil authorities. The North American Air Defense Command in Cheyenne Mountain must be able to communicate with the air traffic control system controlled by the Federal Aviation Administration. “Technology can improve how we do that,” he said, “and reduce the labor required.”
Attributes of the new defensive strategy include knowledge, agility, speed, and lethality. Each, he said, is important for approaching the next century.
Major DoD Initiatives
The first initiative that takes advantage of these attributes is the National Aerospace Initiative. Its projects are organized under the headings of hypersonics,
space access, and space technology. A key partner in this initiative is NASA. An underlying objective of the initiative, he said, is to increase speed, eventually moving toward another generation of reusable launch vehicle. A goal is to reach roughly mach 12 by 2004 and to develop missiles and aircraft with access to space. This initiative will develop partners in the federal government and industry.
One example is a Hypersonic Flight Demonstration Program sponsored jointly by the Navy and DARPA. A 183-foot-long “scramjet” vehicle had been tested successfully at mach 6.5 at 100,000 feet nearly daily for several months, and since that time in a wind tunnel. The project was supported by technical direction from academia (Johns Hopkins University) and from industry (Boeing). “It’s important to bring together resources from across government and into the private sector,” he said.
A second initiative is Surveillance and Knowledge Systems, which includes sensors and unmanned vehicles, high-bandwidth communications, information and knowledge management systems, and cyber warfare. It has direct applicability to NORTHCOM, with some of its activities being performed by other agencies. He stressed the importance of biosensors; the DoD volunteered in the fall of 2001 to help in the effort to calculate the anthrax mortality curve, and to help the postal services calculate the right level of electronic, gamma, and x-radiation for irradiating letters and packages.
He also stressed the importance of high-bandwidth communications, and the “information assurance” that underlies cyber warfare. “We do have to bring together this information, and an understanding of our environment, so our knowl-
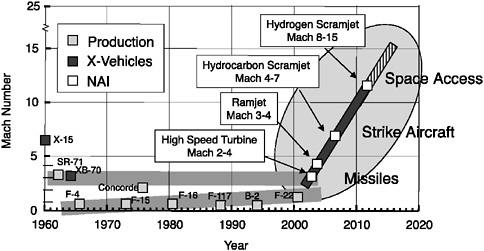
FIGURE 20 National aerospace initiative—Hypersonics.
edge systems will become increasingly important.” These systems are now important down to the perspective of the single soldier in the field, he said, who is able to exchange information and digital resources with an operations center. Surveillance and knowledge has become a central part of understanding the warfare environment. A side benefit, he said, is the ability to gather additional information about atmospheric temperature, pressure, and humidity that can enhance weather forecasting, climatology, and other research.
He listed a number of “near-term transformation capabilities,” including knowledge management, communications and networking, sensing, and information security. Examples included adaptive sensor webs, multilevel fusion, sense making—building cognitive bridges between understanding and deciding—decision making, modeling and simulation. These areas would all blend activities being done at universities with those at industry and other government agencies.
In the area of energy and power, the agency had looked at programs industry has launched and areas where government needs are complementary. On some areas, partnerships will be formed, and the DoD was then mapping that out.
Technology Transition is “Critically Important”
Technology transition he described as “critically important.” It would be done in a variety of ways, depending on the complexity of systems and available partners. “Flexibility is one of the keys,” he said, “whether it is a rapid method for just a few of these or a major acquisition program. You need different mechanisms to have effective transitions.” It is important, he said, to emphasize systems engineering from the outset of each program, especially as systems become more complex. As an example, he said that at the September 21 meeting, the task force decided to accelerate development of a thermobaric rocket designed to strike targets hidden within hardened, deeply buried tunnel complexes.29 “We were at a basic chemistry state in the Navy in October, doing laboratory tests, modeling, and simulation. By November were doing static tests in Nevada. On December 14 we had a flight test.” A partnership consisting of the Navy, Air Force, Defense Threat Reduction Agency, DoD, and industry moved the program from basic science to a certified system in less than 90 days. “So you can go quickly,” he said, “and in some areas we’re trying to go faster than that.”
He stepped back in perspective to discuss relative investment of the DoD in the U.S. and worldwide research base since World War II (see Figure 21). In 1965, he said, the DoD was supporting about 25 percent of all R&D, both U.S. and worldwide. At the current time, the DoD supports less than 5 percent of U.S.
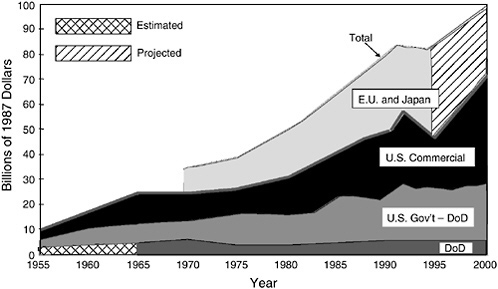
FIGURE 21 U.S. and worldwide research base since World War II. SOURCE: Report of the Defense Science Board Task Force on the Technology Capabilities of Non-DoD Providers, June 2000; Data provided by the Organization for Economic Cooperation and Development and National Science Foundation.
and worldwide research. “That means,” he said, “that in the DoD we need to work with and take advantage of all the research that’s being done outside the department. A lot is in the United States, some is outside. But much of that is also available to an adversary. So we need to make sure that every dollar we spend is highly leveraged, so we will in fact have a technological advantage if the time requires it.”
In summary, he said, technology is the foundation for DoD objectives into the future. “We are aligning our programs with these general goals across services and agencies, and collaborating with others outside the DoD. We provide an integrated approach to the effort, and I believe that increasing partnerships is going to be key for national security.” Combating terrorism with technology is also a model others are using, including NATO, with whom the U.S. has collaborated in applying technology against terrorism.
He concluded with a word about manpower, and the need for more trained scientists and engineers. “If we want to continue to innovate,” he advised, “we’re going to have to pay attention to the workforce. In that area we’re all in this together.”
SECURITY CHALLENGES IN AN OPEN ECONOMY
Steve Flynn
Council on Foreign Relations
Mr. Flynn started his lecture by saying the nation faces the “daunting challenge” of “transforming a security paradigm that was built for the federal government exclusively” into a partnership involving the rest of civil society. He mentioned that his lecture would cover three general points surrounding this much needed paradigm shift: (1) Such a partnership would not be possible unless the organizers convey a genuine sense of urgency. (2) There are “a few axioms” that might guide a sustainable private-public relationship with regard to security. (3) There is an example of how this might be accomplished by taking advantage of a great but under-appreciated strength of our society—the ability to draw on public-private relationships at the local and community levels.
After outlining his talk, Mr. Flynn commented that “America, a year later, is dangerously under-protected and unprepared for a catastrophic terrorist act.” He suggested that the nation was in a more dangerous time, post-September 11, for three reasons.
-
We have discovered that “David” can attack “Goliath”; that sheer force cannot always defend against asymmetric and unexpected tactics.
-
Enemies of the United States might previously have been restrained by America’s “superman aura,” or “the perception that there was a CIA agent under every rock, a satellite over every head.” September 11 demonstrated that whatever such buffer might have existed had been removed, and our civil society had been found to be “wide open.” “We don’t have protection built here,” he said. “We built our civil society largely for efficiencies and for integration and all that goes with it, and we didn’t put up much protection.”
-
The most compelling reason is that “most of the damage done post-September 11 is what we did to ourselves.” As an illustration, he described our “reflexive response” in first grounding all civil aviation, and then closing our seaports and effectively sealing up the borders with Mexico and with Canada. “We did something no one else could do,” said Mr. Flynn. “We imposed a blockade on our own economy as an effort to make ourselves more secure.” We essentially tried to “freeze globalization” in order to sort out what had happened.
That mistake, he said, was quickly apparent. Within two days, after closing the Ambassador Bridge between Detroit and Ontario had created an 18-hour queue, Daimler Chrysler reported they would be closing an assembly plant on the following day; Ford Motor Co. announced that they would be closing five assembly plants during the following week.
Efficient Systems May Not Be Secure Systems
The global trading system, according to Mr. Flynn, was built to maximize “efficiency, low cost, and reliability.” “It had no security built into it and the folks who were responsible for filtering the bad from the good basically stopped trying a long time ago.” He suggested that the only tool at the disposal of the surface and maritime transportation systems is “a kill switch,” the ability to shut down whole system.
He recalled that it had taken the nation three days to perform security inspections of all commercial aircraft after September 11. To complete an analogous inspection of all cargo containers in the United States would probably take more than six months. At any given time, there are some 16 million containers in use around the world. Because they cost only about $1500 apiece, they are relatively easy to purchase, to fill with cargo, and then, with minimal documentation, to deliver to any container port in the world. This system moves some 80 percent of the world’s general cargo, he said. “It allows you to move 15 tons of material from Europe to the United States, on the average, or from Asia, for $900–1200.”
This container system, he said, is what makes outsourcing possible: the ability to send work abroad and use highly compressed production cycles to quickly move products from the design stage to development and back to consumers in the U.S. or elsewhere. The resulting ability of companies to maintain “razor-thin” inventories has been a significant part of U.S. competitiveness over the last ten years, which capitalizes on this revolution in transportation.
This is, however, a system largely without security. Its architects built it for low cost, efficiency, and reliability. Security was viewed as something that worked against the system: raising costs, undermining efficiency, and undermining reliability. “For someone like myself,” he said, “who has spent the last ten years talking about this with the architects of the container system, I was like the teetotaler at the New Year’s Eve party. Now we are trying to retrofit security into this system. The approach we’re taking is like trying to retrofit a split-level ranch house to make it handicapped-accessible. It’s expensive, it’s ugly and likely to not work very well.”
“How can we develop the right approach?” he asked. The key, he suggested, was to realize that many things we do for single-point security in fact make society less secure. This is important to identify, he said, because it offers the opportunity to see how security and efficiency are not opposed, but can come together. He offered the example of security at the U.S.-Mexico border crossing in Laredo, Texas. “You could not design a better system for organized crime,” said Mr. Flynn, “than we have at the secure border in Laredo.”
The problem begins with the long delays for truck inspection. Since the owner of a quarter-million-dollar load cannot afford a typical six-hour delay, the market has developed its own practical solution. In a typical scenario, a long-haul truck approaches Laredo from the north and drops its trailer at a depot in North Laredo.
A short-haul truck comes to pick up the load and take it to a Mexican customs broker, who verifies its compliance with Mexican customs law. The short-haul truck then gets in line at the border, crosses some hours later, and drops the load at a depot on the Mexican side. There it is picked up by a Mexican long-haul driver and taken to the interior. The mean pay for short-haul drayage is close to $750 a load, whether it takes six hours or an hour and a half. These short-haul firms are typically mom-and-pop firms using worn-out tractors, and the fee is reasonable. The system itself, however, introduces a new degree of inefficiency, corruption, and opportunities to circumvent security.
As a result, he said, after “hardening” the border in response to September 11 and increasing inspection times, the border today is less policeable and less secure than it was ten years ago. A corollary to that conclusion is that the more efficient the system is, the more policeable it becomes. An efficient system brings confidence about where a load of cargo originated and the chain of custody it has followed through the system. There is a security rationale to address and redress the “keystone cop” type of regulatory oversight that plagues the current border system. At the same time, this rationale would now be resisted by the mom-and-pop employment that thrives on the current system.
He used the analogy of the national Interstate Highway system. Although the official rationale for the system was to provide an infrastructure for national defensive mobilization, the real benefits have been commercial rather than defensive. President Eisenhower, in promoting the system, had to overcome the same kind of local resistance from local communities and states that did not want to lose locally owned restaurants and the local road-building that was a major source of graft in every state.
A Secure System: Tracking and a “Chain of Custody”
For both trucks and containers, Mr. Flynn urged reforms that would both focus more sharply on the fundamental objective of security and do away with the kind of inefficiencies that had given rise to the short-haul trucks in Laredo. As an example, he reviewed how the movement of the 16 million containers might be done more securely. At its heart, he said, container security requires two elements: “First, can I have any confidence that what’s been loaded into this conveyance is legitimate and authorized. And second, when it’s on the move, do I have any confidence that it hasn’t been intercepted or compromised.”
If the answer to both those questions is yes, he said, there is no need to interrupt the commercial flow of containers and provoke the negative economic results that would surely follow. Instead, one goal of a more secure system would be to expedite the flow of containers. Goods are most vulnerable when they are at rest, he said. Another goal of a more secure system would be to create an effective public-private partnership. The tools needed to do that begin with information. The system needs to know as early as possible what cargo is moving toward
your shores so you can assess its legitimacy. Next, it needs an auditing capability that provides confidence that the cargo is legitimate and authorized. Finally, it needs a chain of custody that provides confidence as it moves through the system that each link in the chain is in fact low risk.
How can such a system be built? he asked. It would require both sensors that reliably report on the integrity of the interior of the container, and a system of tracking. Tracking, he said, is critical for several reasons. Most important, the only way to act on information that the integrity of a cargo has been compromised is to know exactly where the cargo is going. At present, the information that a chemical weapon is bound for the United States in a container does not provide security because there is no tracking system that identifies the port to which the container is headed. Without such knowledge, the information could lead only to mass disruption. A complete itinerary is needed to make the intelligence actionable. Also, the information allows for forensic analysis, which would be critical in restoring confidence after an event.
Good Tracking Brings Commercial Benefits
A good tracking system would also bring large benefits to the private sector worlds of shipping and merchandising. The whole world of supply chains and international logistics would benefit from a more efficient system of transit visibility and accountability—at the same time it would allow for public-sector policing. Shippers could write tighter contractual agreements with transportation providers, manage more complicated outsourcing schemes, and design even tighter production cycles. A company that knows with certainty where its products are can maintain thinner inventories. A previous effort toward supply chain visibility was not able to gain momentum; a security rationale would probably help reignite that movement.
Mr. Flynn said he had been working for the past year on an initiative of this type called Operation Safe Commerce. He had begun by approaching a company called Osram Sylvania, which makes light bulbs in Slovakia and has a distribution center in New Hampshire. In the wake of September 11, Osram Sylvania was eager for ideas about making their supply line more secure, and the company agreed to act as a test bed for research on how to do this. They agreed to let Operation Safe Commerce put sensors on their products and serve as a “real supply chain for real R&D” across the world.
To oversee this research, Mr. Flynn invited the U.S. attorneys of New Hampshire and Vermont, the district commander of the Coast Guard, the regional director of U.S. Customs and Border Protection, and the regional director of the Immigration and Naturalization Service. The TISHWIG released $200,000 to perform a test run in May and June 2002. Mr. Flynn said that that amount equaled the total funds spent by the United States on container security during the past year, compared with $200 million a month on baggage screening.
It turned out that the technology design suffered from a lack of communication among the engineers who created it and law enforcement experts who judged it too visible, but as a proof of concept it was a success. The tracking device arrived without incident in New Hampshire, as scheduled.
Mr. Flynn said that the good results of this concept and of the preliminary experiment should draw the support of the private sector—especially if the alternative to a tracking system is the threat of a shutdown in some portion of the container system. He estimated that a shutdown would cost about a billion dollars a day for the first five days, and then begin to rise rapidly as the entire container system slowed to a halt.
He summarized by reiterating his support for security solutions based on the actual operational features of ports and border systems. While the search for solutions needs the support of Washington, he said, solutions are most likely to be found “where the rubber hits the road,” by employees of the port authority, by U.S. attorneys, and by people working in the field. “Bring the R&D down to those levels and do it quickly,” he advised. “By engaging those folks, I think we’re going to get somewhere in the kind of hurry we need.”
DISCUSSION
A questioner who had worked in the DoD noted that he had heard no discussion of the importance of a systems approach. He referred to the need for “a whole systems acquisition process,” which includes mission analytic work and a technology-based acquisition strategy to solve problems. He cautioned that such an approach should not be left out of the thinking of the workshop, and advised against a strategy that was too narrowly “a fixation on a technology innovation agenda.”
Dr. Sega said he agreed that “systems are critical here. We’re talking about a network, with different systems, all of which have to interface effectively.” He said that systems included people in the field, connecting back to numerous agencies and other people in the field, and IT systems, and systems development as you begin to tackle the task. “I couldn’t agree more that a systems approach is going to be critical here, and I think Steve Flynn really was talking about systems.”
Mr. Flynn readily agreed that “a single point approach can backfire on you from a security standpoint as well as an efficiency standpoint.” The essence of Operation Safe Commerce, he said, was to look at how the real world works; it is intermodal and global. The most realistic way to do security gap analysis, he said, is to examine the entire system in question without preconception about where the real problems—or solutions—would be found. Some of them would be in paperwork, some in relationships, and some in the standards used by terminal operators. “We need all that data,” he said.
The second stage, he said, would be to apply the appropriate R&D for addressing those gaps along the entire length of the container transportation system. He said that his real concern was that someone would examine only the individual parts of the system in isolation; “that’s not how the real world works.” He gave the example of developing sensors that might work in one part of the system but not in another: “Some are designed to work well in railroad cars, but don’t work well in salt water; or they don’t do well when they are dropped eight stories by a gantry crane.” The key, he said, is that the research and development has to be applied to an actual supply chain, under real-life working conditions, in order to win the confidence of the commercial world and the public. “Otherwise, he said, “we haven’t done anything but waste money. It’s all about a systems approach.”
Dr. Altman recalled the example of the Transportation Security Agency, where a systems approach had to be applied to the business vision of how TSA would operate. Unlike systems in the past that might have been closed systems, she said, this was an open system with connections to a variety of different sources of input and output.
A questioner reminded the participants that the data needed at decision making points in the system required program managers who are both “techno-literate in the information age” and able to have a “program management sense” of an acquisition strategy that uses cutting-edge, high-performance technologies.
The Need for Behavioral and Social Research
Another discussant reminded participants not to leave out the behavioral and social sciences in addressing terrorism. “Whole systems have people in them,” he said, “and as Dr. Altman just said, the systems are open.” He said that a bioterrorist incident would create public problems that have to be dealt with by behavioral and social scientists. First, how do you get people to abide voluntarily by quarantine rules? This is essential to prevent the spread of an infectious agent: How can people be prevented from panic and creating gridlock on evacuation roads that would block response equipment from reaching the site of the incident?
Second, he said, working within systems brought two challenges. One is how to bring different elements of technology together, and the other is how to bring disparate elements of the culture together. A area of social science called organization development develops skills in inducing people to work with technology and with each other. He urged his audience not to lose sight of the need to take both scientific and human systems approaches to these problems.
Mr. Flynn expressed strong agreement. He said that a challenge in seeking funding for the first phase of Operation Safe Commerce was that no one wanted to pay for the human part of the process. “Everybody would pay for a new sensor,
a new sniffer, gadgetry to hand around, but they didn’t want to pay for convening the meeting among Customs, Coast Guard, INS, and attorneys general.”
Another issue, he went on, was the tendency to use all manners of technology that may or may not be appropriate, such as sensors designed for sanitized facilities. He cited an incident that startled security forces and much of the country in September 2002 when a container ship approaching New York harbor was seized on the basis of misinterpreted radiation readings. Inspectors had not been properly trained, and port personnel had not been sufficiently briefed to deal with such an alert, and the public was unsettled by rumors for many days.30
“Ports are complicated urban environments,” said Mr. Flynn. “If we use technology developed in isolation from that world, it won’t work, and the agents lose all confidence in the devices. People haven’t been trained to use them and there’s no backup support when something goes wrong. These kinds of training investments must be made, and hopefully someone from behavioral and social sciences will point that out before we throw around more technology and cause more mischief.”
Dr. Altman said that many lessons could be learned from private enterprise about social and cultural adaptation to change. Certainly, she said, an imperative like an impending or existing terrorist event creates the impetus for change. In industry, she said, “we have learned through leadership and very specific approaches to change the culture rapidly in such a way that many people, even across companies, embrace change very rapidly and accept it as a means of improving the ability to execute.” She urged a careful look at such lessons.
Better Training for First Responders
A discussant referred to a recent report by the Federation of American Scientists on how the nation might improve training for those likely to face the consequences of terrorist acts.31 To begin with, he said, first responders would have to learn new behaviors of reaction and response to terrorist threats. It was well known to behavioral scientists, he said, that typical training programs anticipate a
memory retention of six months or less, and in an effort to increase this, military and other scientists were beginning to learn more about how people learn. This knowledge could be used to develop more efficient and effective training for the military and response communities. “We’ve managed to wire all our schools,” said the discussant, “but we have almost no educational content transmitted through those wires—much less sophisticated content that truly enhances the learning process.” He said that the Federation of American Scientists was working with NORTHCOM and the National Guard, among others, to develop sophisticated training content that would take advantage of new learning techniques from the behavioral sciences.
Mr. Flynn said he had been asking himself how much security is truly needed. He said that no matter how much we invest in a safer homeland, there would inevitably be “incidents,” because the United States is an open society and “we’re in a dangerous world, and there are people out there who are intent on causing harm.” But should there be an incident, he said, an essential task is to determine whether it was a result of a correctible breach in security or of an absence of security. “If people view it as a breach in security,” he said, “there will be a strategic pause, and then we’ll get back to life as we sort it out. If they view it as the absence of security, they’ll want to shut down the system until security can be put in place.”
He said that the “military value” of catastrophic terrorism comes not from “killing people atop a landmark” but from the “profound disruption created by the incidents themselves.” With an appropriate level of security, there is a low risk of mass disruption, he said, because people are willing to go through the “strategic pause” instead of “shutting down the system” until security is put in place. With this kind of behavior, he said, “you have deterrence.” A terrorist would say, “Why would I bother to commit terrorism if it would simply accomplish a mass murder or vandalism with no tangible impact on U.S. power?” “This is something that our adversaries would consider before they commit these horrific acts,” he said.
He called this “as much the guts of a counter-terrorism strategy as going to the source of al Queda.” The key, he said, is that security is like safety; it is not an end in itself. Security is found in sustainable systems, such as global networks of trade, finance, labor, information, and transportation—that continue to function even in a world that contains people with malicious intent who want to disrupt those systems. The objective is to build enough safeguards and resiliency into the system to sustain it even during or after attack.
A second part of that objective, he said, is to think of safeguards and resiliency throughout the international extent of such systems. “If we keep this narrowly focused on the homeland,” he said, “it’s a bit like hiring a network security manager who says I’m just going to protect the server next to my desk; the others are too far away.” Even though maintaining systems in an international context is far more complex, he said, it must be done.






















