3
The Social Security Administration’s Information Technology—Present and Future
As the Social Security Administration’s (SSA’s) workload increases, technological change continues and brings with it a corresponding increase in the online service expectations of at least some segments of its clientele. Unlike earlier retirees, the baby boom generation is more computer-literate and Internet-savvy and is likely to retain these traits after reaching retirement age.1 Thus, it should be expected that the SSA’s various beneficiaries and other user communities will continue to be adept at keeping pace with these technological changes. Broader and more systematic attention to technical and social trends will be warranted. Further, to achieve a forward-looking electronic services strategy in any organization requires an understanding of the organization’s current technological capacities coupled with an understanding of trends in important and relevant information technology (IT) and user expectations. This chapter provides a high-level assessment and set of impressions regarding the SSA’s current IT infrastructure, its database technology and conversion strategy in particular, external technological trends, a brief overview of user expectations and projected demographics, and how they all can affect prospects for effective electronic services, now and in the future.
INFORMATION TECHNOLOGY INFRASTRUCTURE
The IT infrastructure of an organization encompasses hardware, software, databases, applications (including Web services) along with security processes and, for the purposes of this report, software-development policies and practices. This section briefly describes the committee’s assessment of various of these parts of the SSA’s IT infrastructure. It focuses particularly, however, on the underlying databases and database architecture, as these are especially key components of any effective electronic services strategy and application suite (see Box 3.1 for more on the centrality of databases to electronic services provision).2
Hardware Infrastructure
The SSA organizes its hardware and IT infrastructure3 in three tiers: local/departmental, remote operations control centers (ROCCs), and headquarters. There are numerous local offices; six ROCCs located in Pennsylvania, New York, Illinois, Missouri, California, and Alabama; and one headquarters facility, the National Computer Center (NCC), located in Baltimore, Maryland.
The hardware in the local offices consists primarily of personal computers (PCs) running the Microsoft Windows operating system, plus a local file server, all connected using standard local area network (LAN) technology. Desktop machines are upgraded regularly on a 3- or 4-year cycle. In addition to access to the local servers, local PCs also have access to the servers at the ROCCs through virtual private network (VPN) connections. The ROCCs run standard Unix servers from a mix of vendors and again are connected using standard LAN technology.
The bulk of the SSA programmatic applications run at the NCC. The NCC hardware configuration is typical of a large financial services organization. It consists of a variety of hardware configurations, including midsized servers running both Windows and Unix with their own storage volumes, six IBM Parallel Sysplex mainframe systems, and a large data-storage farm implemented using storage area network (SAN) technology from EMC Corporation. Most of the programmatic data sets reside on the
|
2 |
Note that this overview is of necessity brief and based on comparatively small amounts of data and input. A comprehensive assessment of such a large organization’s IT infrastructure was outside the scope of this committee’s activities; the committee tried to focus particularly on the capabilities and functionalities related to electronic services provision. |
|
3 |
Factual details about the SSA’s IT infrastructure in this section are from Social Security Administration, Information Resources Management Strategic Plan (2005), especially pp. 85-224 (hereafter cited as Social Security Administration, Information Resources Management Strategic Plan (2005)), available at http://www.socialsecurity.gov/irm/IRM_2005.pdf, accessed June 20, 2007. |
|
BOX 3.1 Modern Database Technology Is Critical to the SSA The rapid growth in the development of large-scale electronic services has been strongly supported by rapidly growing understanding of the anatomy of such services and by advances in supporting the development and deployment of their component parts. The data-management component is the most critical component—online services 24 hours a day, 7 days a week (24/7) are as dependent on the data-management component as an automobile is on its engine. Virtually any information technology (IT) application, whether it is in the public or the private sector, is about data. In the case of the Social Security Administration (SSA), the central data comprise the information that the SSA has about its core constituents—essentially every person and business in the country. That is at the very core of the agency’s mission—it keeps track of everyone: who they are, who their families are, where they live, what they have earned each year, what they or their employers on their behalf have paid to the SSA. This is all data. It is what drives everything that the SSA does. All of the SSA processes and services are centered on those data—they read the data, they record changes to it, they note what is happening to it, and so on. The data are the model that the SSA has of everyone—they are its computerized model of the world that the SSA exists to manage. Electronic services must rely pivotally on appropriate database services. Requested services may simply require access to up-to-the-minute information, in which case this must be available from an archival data store that is capable of receiving and processing updated information in real time. The privacy of this information, however, must be carefully guarded, and its security from loss or tampering must also be ensured. These demanding requirements must be supported by the archival data-storage component. The services requested may also entail modification of archival information (for example, adding in the latest Social Security employer deposit, or logging the payment of a monthly benefit). Here too, the data-storage component is relied on for assuring the provision of the appropri- |
EMC storage arrays so that they are available from any of the mainframes. All of the machines are interconnected using standard LAN technology, which is protected from outside access by a firewall.
The SSA’s continued dependence on Customer Information Control System (CICS), Virtual Storage Access Method (VSAM), and the crucial Master Data Access Method (MADAM) software currently restricts the SSA to IBM mainframes for the bulk of its programmatic data. As discussed below, migrating these data to a relational database system would offer the SSA an opportunity to consider hardware alternatives with more performance at a much lower cost. For example, since the mid-1980s, the software company Teradata has provided the retail and banking sectors with scalable database technology based on the use of scalable servers constructed from commodity hardware components. In 2004, Wal-Mart had
|
ate capabilities. Thus, the data-storage component must be capable of immediate updating as well. The challenges entailed in developing such data stores clearly are considerable: they must be incorruptible, persistent in perpetuity, even in the face of attempts to corrupt them, and must also support being able to be updated in real time. Considerable research and commercial development, however, have led to the availability of such databases. Support for 24/7 access to electronic services requires that all components be capable of providing appropriate support. Thus, clearly, the services promised by an inviting user interface can only be provided if an appropriately powerful database is a component of the application. Today, though, the SSA is using a decades-old database system. The Master Data Access Method (MADAM) is based on a 40-year-old proprietary record-based file/index system that ran on IBM 360s and still runs on their modern mainframe hardware. The fact that the SSA’s equivalent of the “corporate jewels” are stored using decades-old technology is alarming and needs to change. As Chapter 3 in this report points out, modern database technology can readily manage the amount of data that the SSA has. Moreover, the number of IT professionals having the background and skills to maintain the current MADAM database and surrounding applications is very small, and dwindling. Few people today know how to deal with mainframes and the kind of software that MADAM is based on. In the relatively near future, there may be none. By contrast, Structured Query Language (SQL) developers are ubiquitous. The SSA needs to move forward quickly in this area so that it can develop new services and processes using the many skilled developers and system administrators and performance tuners available in the modern job market. Otherwise it will continue to operate in the “old days” of multi-hour batch updates and backups, fragile software that few know how to tune or manage, and so on. The SSA will not be able to provide effective 24/7 services that way, nor will it be able to add new data to support new services easily. Modernizing the underlying databases that support the SSA’s activities is critical to the agency’s effectiveness in the realm of electronic services. |
almost 500 terabytes (TB) of operational data stored on its 1,000 processor Teradata configuration.4 Other scalable database alternatives include IBM’s relational database system product DB2/PE (Parallel Edition), Oracle 10g, and products from vendors such as Netezza and Datallegro. The adoption of scalable database technology and clusters of commodity processors to handle even the very largest database tasks is expected to accelerate as databases of all forms and types continue to grow. Exploration of the use
|
4 |
Constance L. Hays, “What Wal-Mart Knows About Customers’ Habits,” New York Times Business Section, Nov. 14, 2004, available at http://www.nytimes.com/2004/11/14/business/yourmoney/14wal.html, accessed June 14, 2007; and Charles Babcock, “Data, Data Everywhere,” Information Week, Jan. 9, 2006, available at http://www.informationweek.com/story/showArticle.jhtml?articleID=175801775, accessed June 20, 2007. |
of this sort of technology as part of a migration plan from MADAM to relational database technology would likely be fruitful.
Redundancy and backups are of course essential to data integrity and availability—and ultimately to business continuity. One means for meeting this need is through the use of data replication to provide the capability to switch over automatically to spare components that provide for continuity of operations. In general, the reason that such replication is important is that, although backup tapes are kept off-site in a secure location to prevent significant data loss, without replication a major disaster at the primary site could leave the SSA unable to access its master database until a replacement facility was up and running.
In this study, the committee was unable to obtain information from the SSA regarding data replication and failover plans for handling disaster recovery owing to security sensitivities. Therefore, rather than evaluating the agency’s current or planned capabilities in this regard, the committee notes that various approaches to addressing this challenge are possible and are supported by modern database systems and architectures. However, in the committee’s view, realizing a modern data-replication and disaster recovery strategy could be significantly hindered by the SSA’s use of decades-old database technology for storing the majority of its programmatic data (see the discussion of MADAM in the following sections). The antiquated MADAM database system and technology are difficult to replicate using current technology (see below), and the custom modifications that would be needed to do so would be very costly and would require scarce expertise.
Software Infrastructure
Each of the three SSA organizational tiers runs slightly different software.5 At the local/departmental level, both the desktop PCs and the servers run Windows NT and the usual suite of Microsoft productivity tools. Microsoft Access is run on the desktop PCs, and the local/departmental servers run Structured Query Language (SQL) Server. As is typical for large organizations, the desktops are used for running a broad spectrum of applications, including administrative applications (for example, payroll and travel); management information applications (for example, report generation); and programmatic applications (for example, data entry). Although the applications are currently a mix of client-server
|
5 |
Factual details about the SSA’s IT infrastructure in this subsection are drawn from Social Security Administration, Information Resources Management Strategic Plan (2005), especially pp. 85-224; available at http://www.socialsecurity.gov/irm/IRM_2005.pdf, accessed June 20, 2007. |
and Web-based applications, the SSA is in the process of replacing most or all of the client-server applications with Web-based versions. Both types of applications are used to communicate with servers located at all three tiers: local, ROCCs, and NCC. The servers at the ROCCs are a combination of Unix and Windows NT servers. Both Oracle and SQL Server database systems are used at this tier. The NCC hosts servers running Windows NT, Unix, and IBM’s z/OS operating system. SQL Server is run on the Windows servers, Oracle runs on the Unix servers, and a combination of DB2, Computer Associates Integrated Database Management System (CA-IDMS), MADAM, and VSAM run on the IBM Parallel Sysplex servers.
The databases housed on the servers at the NCC can be roughly divided into three categories: programmatic, administrative, and management information (MI). The programmatic databases are organized into separate operational data stores; they include Title II (administering disability, old age, and survivor benefits); Title XVI (administering Supplemental Security Income [SSI]); Disability (determination, control, and tracking); Earnings (recording of annual wage reporting by employers and benefit reports); and Enumeration (allocation and verification of Social Security numbers [SSNs]). The administrative database is a separate operational data store that includes information on SSA employees, facilities, and finances. Each of these operational data stores feeds abstracted and aggregated information into a data warehouse that is used to support management decision-making processes based on both current and historical data. The schemas for each of these databases are consolidated in a metadata database. See Figure 3.1 for a graphical depiction of the SSA’s Management Information Database Architecture.
The MI data warehouse is hosted using Oracle running on the Unix servers. The administrative databases and associated applications are currently in the process of being migrated to a combination of DB2 running on one of the SSA mainframes and Oracle running on a Unix server.
With the exception of the Disability database, which is housed on DB2 on a mainframe, the primary programmatic databases including Title II, Title XVI, Earnings, and Enumeration are stored on a SAN and manipulated using a combination of CA-IDMS, MADAM, and IBM’s VSAM.
While the names DB2 and Oracle will likely be familiar to the casual reader, it is highly unlikely that CA-IDMS, MADAM, and VSAM will be. CA-IDMS is an implementation of the Conference on Data Systems Languages (CODASYL) data model. The company that actually built IDMS (Cullinet) went out of business in 1989, at which time Computer Associates acquired the rights to Cullinet’s system and its customers. The CODASYL data model was popular in the early to mid-1970s, but by approximately 1980 most experts in the data-management field had
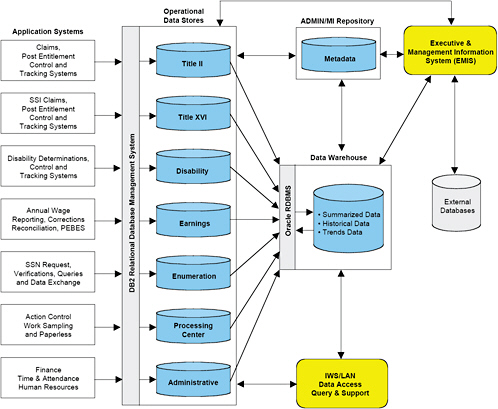
FIGURE 3.1 The Social Security Administration’s Management Information Database Architecture.
NOTE: SSI, Supplemental Security Income; PEBES, Personal Earnings and Benefit Estimate Statement; SSN, Social Security number; ADMIN/MI, administrative and management information; RDBMS, relational database management system; IWS/LAN, intelligent workstation/local area network.
SOURCE: Social Security Administration, “SSA Data Architecture,” Version 1.0, Dec. 9, 2002, p. 22. (Courtesy of the Social Security Administration.)
concluded that the relational data model was superior.6 In addition, CODASYL database systems are almost exclusively accessed by applica-
|
6 |
For a timeline history of databases, see International Federation for Information Processing Working Group 9.7, “A Brief History of Database Systems,” in History of Computing, last modified Dec. 5, 2004, available at http://www.comphist.org/computing_history/new_page_9.htm, accessed June 20, 2007. For discussion of the foundations of database systems, see Raghu Ramakrishnan and Johannes Gehrke, Database Management Systems, New York: McGraw-Hill Higher Education, 2002, especially Ch. 3 (hereafter cited as R. Ramakrishnan and J. Gehrke, Database Management Systems). A mid-1970s comparison of the CODASYL and relational approaches is presented in Ann S. Michaels, Benjamin Mittman, and C. Robert Carlson, “A Comparison of the Relational and CODASYL Approaches to Data-Base Management,” ACM Computing Surveys 8(1):125-151, March 1976. |
tions written in Common Business-Oriented Language (COBOL), which, as the oldest business-oriented programming language in the history of computing, is now generally considered to be obsolete, understood by only an increasingly small fraction of the practitioner community.
One drawback is that applications written in COBOL/CODASYL are more cumbersome to maintain compared with those implemented using modern technology. An application written in COBOL against a CODASYL database management system (DBMS) such as CA-IDMS is typically 10 to 100 times longer (in lines of application code) than an equivalent application written in C++ or Java against a relational database system. The main reason for this difference is that the database requests against a relational database system are written in SQL, the declarative data manipulation language that is the mainstay of relational databases and modern IT organizations. Simply put, SQL allows applications developers to request data by saying “what” they want, not “how” they want the system to obtain the data. The underlying relational DBMS optimizes the application’s request based on how the data are physically organized and indexed and what the current data statistics look like. This provides orders-of-magnitude code reduction and productivity gains relative to CODASYL database applications.
CODASYL applications are extremely difficult to write, debug, and maintain in comparison with today’s mainstream data-centric application-development technologies. The SSA’s dependence on CODASYL and COBOL for MADAM represents a severe handicap because of these difficulties in developing, refining, and maintaining the demanding applications needed to meet the current requirements of SSA’s diverse constituencies.
Another drawback is that COBOL itself will eventually become a “dead language.” It is rare today for new applications to be written in COBOL, and the dwindling number of existing COBOL/CODASYL applications is being steadily replaced by versions written in contemporary languages such as C, C++, or Java, or scripting languages such as PHP or Perl, using SQL (or SQL-based programming tools) for database access. This is due to the much more productive database programming capabilities and associated benefits that these combinations of technologies offer. In fact, COBOL and CODASYL are no longer taught in college and university computer science departments, and the number of programmers who are conversant with COBOL and CODASYL programming has become quite small and is shrinking rapidly. Thus, in addition to the SSA’s being dependent on a set of low-productivity technologies, it is likely to become increasingly difficult for the agency to recruit and retain the pool of IT developers needed to meet its current and future IT needs.
In summary, these issues represent major challenges for the SSA going forward. Specifically, because such outdated technology is used for the
SSA’s master database, it raises barriers in terms of the feasibility of linking it to new Internet applications. In addition, it causes applications to be unavailable for 24/7 access, because this technology requires downtime for updates in batch windows (see below). Some software for MADAM is written in assembly language and so closely coupled to the operating system (OS) that any changes in the OS require testing of the database. Finally, the cost and increasing scarcity of relevant custom programming expertise is making the maintenance of this technology increasing difficult and problematic. The SSA is not unaware of these issues, which have also been raised in earlier reports and studies (some are cited below). Indeed, the SSA reported to the committee that it was exploring converting to a newer technology, but the committee nevertheless has concerns about the conversion process, as discussed below.
MADAM and the MADAM Conversion Process
The SSA’s Master Data Access Method, MADAM, is a database system that was developed in-house by SSA staff in the early 1980s when the SSA converted from tape to disk storage for its data sets. In 1986, the congressional Office of Technology Assessment (OTA) issued a report entitled The Social Security Administration and Information Technology. As part of that report, OTA expressed concerns about the use of MADAM instead of a commercial database system:
The most controversial accomplishment of the data integration effort is perhaps the Master Data Access Method, or MADAM, the file management system that SSA developed when it converted from tape to disk storage. Many experts thought that SSA should have sought or adopted off-the-shelf software for this purpose which would be maintained by vendors, rather than developing its own which it must maintain (that is, improve, modify, and update). MADAM may well be incompatible with future mainframe operating systems, database management systems, and fourth generation languages. The SSA incurs future risks of incompatibility and long-term maintenance costs. In the short term, there are also risks and costs. MADAM is apparently a very complicated and poorly documented system, so that only a small group of people are sufficiently knowledgeable to operate it, yet it is the basis of the SSA’s data management. This constitutes a particular vulnerability to smooth operations if there is any short-term emergency, sudden work force reduction, or drastic reorganization.7
|
7 |
U.S. Congress, Office of Technology Assessment, The Social Security Administration and Information Technology, OTA-CIT-311, Washington, D.C.: U.S. Government Printing Office, 1986, p. 43 (NTIS Order PB87-136834), also available at http://www.ssa.gov/history/pdf/ota86.pdf, accessed June 20, 2007. |
Despite those concerns, the committee notes that MADAM is still functioning, 20 years later. However, the vulnerability factors, including workforce issues that OTA noted, still pertain.
MADAM is layered on top of IBM’s Virtual Storage Access Method product (VSAM is IBM’s indexed file management package, based on the use of B-trees to support searching8), which allows it to run in a Parallel Sysplex environment. It appears, however, that updates to the central MADAM database are done primarily (if not exclusively) in a batch mode. New data (for example, batches of earnings reports) are first inserted into CA-IDMS and then batch loaded into MADAM during a nightly batch window (based on information that the committee received from the SSA, this window is 1:00 a.m. to 5:00 a.m. during the week and longer on the weekends). The large batch window is required to update the MADAM database daily; this scheduled downtime makes 24/7 operation of online services impossible without the implementation of some sort of complex caching and merging mechanism that could allow online services to overlap the batch window.
The continued use of the CA-IDMS/MADAM combination of technologies represents a significant barrier to the SSA goal of providing improved and expanded electronic services to users. One issue is that Java Platform, Enterprise Edition (J2EE) application servers, such as the IBM WebSphere product that the SSA is using to deliver new Internet applications, typically communicate with databases using Java and SQL, not through COBOL and CODASYL record-level operations. Connecting WebSphere applications to CA-IDMS and MADAM will involve custom adaptors that are difficult to program against from within a J2EE environment and that cannot reap the usual benefits of the productivity tools and technologies available to “normal” J2EE developers.
It is also worth noting that, aside from the software issues, the continued use of CA-IDMS and MADAM serve to lock the SSA into a particular expensive hardware and software combination. Both pieces of software only run on high-end IBM mainframes, making it impossible for the SSA to take advantage of potentially lower cost alternatives such as scalable Unix clusters or parallel database systems such as IBM DB2/PE, Oracle 10g, or NCR Teradata, among others.
One justification sometimes offered for the continued use of MADAM is its size. The argument is that the SSA databases are so large that they can only be handled by custom software. Although this argument may have been valid 20 years ago, the SSA databases are no longer uniquely
large by modern enterprise standards. As of 2005, the SSA’s programmatic databases had a total size of about 30 TB9 (a terabyte is 1 trillion bytes). Proprietary concerns make it difficult to obtain published data on commercial enterprise database sizes and workloads in order to identify those that rival the SSA’s database in terms of size and number of transactions. However, published data indicate that commercial systems handle very large relational databases, and relational databases with very large workloads. By way of comparative example, the customer database for Verizon, a major U.S. telecommunications company, consists of 50 billion records and 47 TB, and this database does not include data concerning the company’s wireless customers.10 Verizon’s database is currently housed on a cluster of Windows Servers running Microsoft SQL Server—using commercial off-the-shelf relational database technology. Moreover, the annual Winter survey11 lists a number of commercial relational database instances in the 20 TB to 100 TB range, and these databases are all managed by standard relational database products, each typically housed on Unix or Windows clusters. In terms of system load, SSA’s workload approaches 50 million CICS transactions a day.12 The 2005 Winter survey indicates that standard relational database systems in use at telecommunications companies and banks typically handle well over 1 million transactions per hour, with one system in the report having a peak workload of 28 million transactions per hour. This system handles this transaction load using DB2 running on Unix. It is the committee’s opinion that the capabilities of commercial relational database products in 2007 have now overcome any technical rationale that might justify the SSA’s continued reliance on decades-old, custom data-management technology.
Selecting a MADAM Conversion Strategy
The SSA has taken some steps to explore MADAM alternatives. A 2002 report describing the SSA’s data architecture plans states that “efforts will be made to determine what portions of the [MADAM] data could be
|
9 |
See Social Security Administration, Information Resources Management Strategic Plan (2005), p. 168, available at http://www.socialsecurity.gov/irm/IRM_2005.pdf, accessed June 20, 2007. The SSA has a total of 110 terabytes of mainframe data stores, and the SSA’s client-server data stores maintain 80 terabytes (ibid., p. 5). |
|
10 |
Personal communication from Michael Brodie, Distinguished Architect, Verizon Communications, to David J. DeWitt and Michael Carey, e-mail, Feb. 20, 2006. |
|
11 |
This survey is available from Winter Corporation, Waltham, Mass., http://www.wintercorp.com. |
|
12 |
The SSA reported that, in 2004, its mainframe and client-server databases had supported some 42 million individual data transactions a day. Social Security Administration, Information Resources Management Strategic Plan (2005), p. 5. |
managed by DB2.”13 The same language appears on page 130 of the 2005 SSA Information Resources Management Strategic Plan.14 The scale and scope of the committee’s investigation did not allow for an in-depth analysis of what progress has been made. However, it is clear that, given the state of relational database technology in 2007, the actual answer today to the question of what portions of MADAM data could be managed by DB2 (or another modern database solution) is simply, “All of it.”
As part of this study, the committee requested documentation for MADAM and any available documents related to the SSA’s ongoing MADAM-to-DB2 conversion process, especially the results of SSA pilot or feasibility studies. The following discussion is based on the documents received by the committee and conversations with SSA staff.
During the process of selecting its conversion strategy for MADAM, the SSA appears to have relied on one contractor for technical expertise. In January 2003, the SSA took delivery of a study entitled MADAM Alternative Evaluation, conducted by the consulting firm YL&A.15 This study focused on alternative strategies for converting the SSA’s master files, which are currently managed by the MADAM software, to DB2, IBM’s relational database system product. After reviewing the MADAM database system and related applications software in some detail, the YL&A consultants concluded that:
The MADAM, AIF, and Builder/Spreader software is a collection of custom code written in IBM assembler language (ALC). It is tightly coupled with the operating system, is extremely complicated, and can only be supported by a limited number of extremely talented application developers. In fact, MADAM is so tied to the operating system that any change to the operating system has to be tested for its impact on MADAM. There is some fear that future operating system changes may render MADAM unusable and the talent need [sic] to remedy the situation may no longer be accessible.16
The MADAM Alternative Evaluation report begins with a brief overview of the different master files and the advantages that switching to a commercial relational database system such as DB2 would provide, even if DB2 proves to be slower for certain operations. Section 5 of that report proposes five alternative proof-of-concept (POC) studies that the SSA
could undertake to evaluate the difficulty of replacing MADAM with DB2 and recommends selecting the Supplemental Security Income Records (SSR) database for a POC conversion effort.
The same report also considers alternative approaches to converting the SSA’s various applications (for example, the programs that do things like issuing monthly checks). It appears that the bulk of these applications are currently written in IBM assembly language17 and make use of an abstraction layer known as the Application Interface Facility (AIF) that is built on top of the various MADAM files.
The existence of such an interface provides a number of alternative ways of converting the actual applications. For example, one could conceivably rewrite the AIF software to make DB2 calls instead of MADAM calls. This would make it theoretically possible to run the existing applications without modification. Although this sounds very appealing at first glance, it in effect turns DB2 into a MADAM simulator. This is not a useful approach in the long term because it would forgo many of the reasons for doing the conversion in the first place, and it almost certainly would sacrifice long-term flexibility and performance for short-term gains. (See the next section for more on architecture.)
A second, 2004 report from YL&A entitled SSR Master File to DB2 Conversion Deliverables Detail Document18 describes the results of the POC study recommended by YL&A in its January 2003 report to convert a portion of the records in the SSR master file to DB2. Unfortunately, this second report does not contain key details of the POC study (for example, the DB2 schema used); hence it is not possible for the committee to evaluate the results of the study or the approach adopted. Certain things suggested in the 2004 report do, however, cause concern, as elaborated below.
As noted above, the POC that YL&A and the SSA executed adopted the philosophy that any MADAM-to-DB2 conversion should have little or no impact on existing applications. As a consequence of this decision, the resulting database design was severely compromised with individual SSR records “stored in as many as 46 DB2 tables.”19 Such an approach is almost certainly going to experience poor performance, suffer from numerous potential update anomalies, and almost inevitably be the source of numerous long-term complications if actually adopted. The proposal of such a design in the first place is very surprising and illustrates the inadvisability of adopting a MADAM-to-DB2 conversion approach that does
not include a rewrite of the actual applications to make DB2 calls directly. (Furthermore, if 46 tables were really needed, the use of views might be preferable, instead of actually storing an individual record 46 times.)
Another issue is the apparent failure of the YL&A studies to consider other large-scale relational database management system (RDBMS) technologies. There are several other vendors in addition to IBM (DB2), and these vary in their performance, functionality, and scaling capabilities. However, the YL&A report does not enumerate the SSA’s requirements and evaluate other leading vendors’ systems20 against them, thus not enabling the SSA to make the most informed selection.
Migrating legacy databases of the size and vintage of MADAM is fraught with challenges.21 While long-established enterprises (such as major telecommunications companies) have faced the challenges of migrating legacy applications and databases, seldom if ever are databases migrated from one platform to another unless the target database is a close match to the source database, in which case, the process is relatively straightforward. Consulting firms and DBMS vendors (for example, IBM, Oracle, and Microsoft) are in the business of database migration with database-migration tools and factories. While these factories and tools address the database migration, they are less able to deal with the greatest cost and complexity, namely, all software above the database layer—middle-ware, application programming interfaces (APIs), and thousands of calls throughout known and unknown applications that access the database. Hence, database migration for similarly structured targets and sources is relatively straightforward, while migrating the software stack above it is almost never straightforward. It is unlikely that the structure of SSA’s MADAM is close to what would be required of a new database to support SSA’s e-government and related requirements. Hence, it is unlikely that any conventional database-migration strategies or tools would be applicable.
With very rare exceptions, major companies have not attempted direct translation of mainframe databases from one platform to another without significantly affecting applications. The rare cases involve large VSAM files using powerful tool sets for VSAM to significantly manipulate the
files prior to their being imported into Information Management System (IMS) or DB2 databases aided by migration tools designed by IBM and others for the migration of VSAM to IMS or DB2. Most successful cases have involved completely replacing the legacy applications and databases with entirely new applications and databases. In such cases, legacy databases are not migrated in toto into new databases, but instead the necessary information content is extracted and incorporated into the new databases. The legacy applications and databases are then capped on a specific cutoff date, after which time all new transactions are redirected to the new applications and databases. For operational, regulatory, and other reasons, the legacy databases and their applications are usually maintained in case access to information that had been in use prior to the cutoff date is ever needed. The new applications and databases then become the systems of record for all transactions from the legacy system cutoff date or the new systems production date forward. This methodology eliminates the challenges involved in attempting to migrate the totality of all legacy data, structures, and other artifacts from legacy databases to new databases. It also frees the new databases and applications to focus on current and future requirements, similar to those associated with the SSA’s e-government strategy.
Finding: In 1986, the Office of Technology Assessment alerted the SSA to the technology and technological risks inherent in its Master Data Access Method, or MADAM. Today, MADAM and the SSA’s current data-management approach continue to pose increasing risks. The approach faces increasing limits in the availability of staff who understand and can support the SSA’s technologically obsolete, custom solution. In addition, the approach precludes the use of valuable new technological capabilities and requires interruptions in service for batch updates, both of which impede the provision of desirable new e-services.
Recommendation: As it makes decisions about future directions for its database technology, the SSA should give considerable weight to the implications of those decisions for the effectiveness and efficiency of current and future electronic service delivery and should be open to the introduction of new technologies.
Architecture
In addition to specific database challenges, architectural considerations are a key component of a successful electronic services strategy. It is beyond the scope of this report to recommend a specific architectural
approach. In principle, however, the SSA will need to develop a data-management strategy and architecture. Doing so entails developing a data-management architecture that includes appropriate storage to meet the requirements of the organization’s e-government strategy and other operations. In addition, it entails the development of a migration strategy and supporting architecture for capturing the needed pre-replacement information and making it available as part of the new data-management architecture. Where possible, the replacement should be incremental in order to minimize risk and to minimize interruption of the agency’s workload and operations. The data-management architecture should be an integral part of the next-generation architecture.
While the SSA has some modern technology components—for example, its Web site and security practices—the core technologies, such as data management, are outdated and pose significant risks and limitations to the SSA’s operations and impose constraints on the SSA’s ability to achieve an electronic services strategy comparable with those in the private sector (see Chapter 2). In addition to data management, user interaction, and of course security, architectural considerations loom large in the necessary transition. The committee does not recommend a particular future architecture, but a number of questions should be addressed as the SSA moves forward. What would that target architecture be? How would the SSA migrate from the current architecture to the target incrementally without disrupting its operations and at the same time improving productivity, responsiveness, and new services and lowering cost? The data-management issue should not be addressed without a target architecture. The data-management challenge is an integral part of a larger challenge, the architecture.
The committee acknowledges that it is easy, from the outside, to counsel a radical reengineering of an outdated legacy system, while it is very much harder to build a case for the major expense and downside risks entailed in the retirement of such a system with its large historical investment. The SSA, in addition to the technical considerations outlined here, will also need to take into account congressional attention and the likely inevitable congressional hearings and newspaper headlines that will ensue if the reengineering efforts result in even a single month in which Social Security checks do not go out on time. Because the committee did not receive detailed information about the current nature and status of the SSA’s MADAM conversion effort, it did not reach conclusions as to whether any ongoing activities should stop. However, as described above, the committee does have concerns about some of the technical advice that the SSA has received regarding conversion. The SSA thus should look broadly for advice as it plans and executes its MADAM conversion effort and architectural overhaul.
In seeking broader technical advice, the SSA might, for example, establish an external advisory board consisting of experts from the database software industry, several large commercial enterprises (financial services and telecommunications companies) that have deployed large relational databases, and academics to oversee the MADAM conversion effort. Relying on a comparatively narrow range of expertise to architect such a massive conversion effort creates needless risks for successful outcomes. In many ways, the SSA is at a critical crossroads. The way forward is difficult and risky, but standing still is risky as well. The committee believes that the best way to move forward is to ensure that the SSA has the best possible technical advice—both to guide the agency and to provide context and insights on managing the inevitable glitches that will occur.
Finding: The scope and scale of the challenges that the SSA faces with regard to its database conversion strategy merit the input of a broad range of expertise.
Recommendation: In continuing to develop its conversion strategy and long-term services strategy, the SSA should draw on a broad range of technical expertise—including but not limited to database software experts, software engineers, software security experts, financial services experts, large-scale commercial service providers, and systems architecture experts—and put systematic mechanisms in place so that it can hear and learn from outside advisers.
Other Applications
As indicated above, the key programmatic SSA applications22 are the following:
-
Title II: Administering disability, old age, and survivor benefits;
-
Title XVI: Administering Supplemental Security Income;
-
Earnings: Recording of annual wage reports;
-
Enumeration: Allocation and verification of Social Security numbers; and
-
Disability: Determination, control, and tracking of disability claims.
Of these key applications, all but Disability are implemented as batch applications against the CA-IDMS and MADAM databases, with CICS being used to drive “green-screen” application interfaces.23
Over the past few years, the SSA, as part of its Electronic Disability process (eDIB) and paperless claims effort,24 working in partnership with state Disability Determination Services (DDS) offices, has implemented an electronic version of the disability determination process using Web-Sphere and DB2. With this new system, users can initiate claims either over the Internet through the SSA Web site or at their local disability office. As a claim is assembled, all the supporting medical evidence (for example, x-rays, doctor’s and laboratory reports, and so on) is digitized and stored in the DB2 database (using DB2 large object capabilities) along with the other details of the claim. At the time of this writing, the eDIB application was still in the process of being rolled out state by state. Use of eDIB will reportedly cost $850 million over a 7-year life cycle, and the SSA expects to reap $1.3 billion in total savings (including postage and file-storage costs) from eDIB and to cut more than 3 months from the average time required to process a disability claim.25
Although the eDIB effort is certainly a step in the right direction, the implementation is basically an electronic “copy” of the formerly paper-based process. The electronic folder that is ultimately assembled using the application process closely resembles the paper folder that it replaces. This is a good first step, and the approach provides a natural online transition for users of the system, but it misses a number of opportunities for enhancement. For example, with the current electronic folder, all supporting documents—including not just multimedia artifacts such as x-rays and photographs, but also all doctors’ reports, laboratory reports, and so on—are converted to images encoded in the Tagged Image File Format (TIFF) format. This approach does succeed in archiving the documents but makes it impossible to index and search them without resorting to
|
23 |
“Green screen” is common usage to refer to the monochrome-display cathode ray tubes (CRTs) used as computer monitors, predominantly in the 1970s and 1980s. A green phosphor was used, producing green characters on a dark background; some early CRT monitors used orange phosphors. |
|
24 |
The eDIB process is intended to provide better and more timely service to claimants, in part by replacing voluminous paper case files with electronic files. In contrast to transferring the electronic case files used for “paperless” claims processing, locating and physically transferring paper files when a disability claimant requests a hearing used to take a month or more. The SSA describes its eDIB and paperless processing approaches in Social Security Administration, Information Resources Management Strategic Plan (2005), available at http://www.socialsecurity.gov/irm/IRM_2005.pdf, accessed June 20, 2007. |
|
25 |
Mary Mosquera, “Case Files Travel Lighter, Faster,” Government Computer News, Oct. 9, 2006, available at http://www.gcn.com/print/25_30/42177-1.html, accessed June 14, 2007. |
optical character recognition of the image files, a process that will introduce errors. In contrast, if doctors’ reports were captured and stored in the database in a format such as Word documents or Portable Document Format (PDF), they could readily be indexed and searched. This would greatly enhance the accessibility and usability of the data in the eDIB database. In the future, as machine-readable standards for electronic patient records take the place of handwritten notes and other unstructured documents, it would be useful to be able to store such records directly in the disability database.26
Web and Internet Services
The SSA’s public Web site (http://www.ssa.gov) is a primary access point for many users of electronic services. Although the previous components of the agency’s IT infrastructure all play a role in electronic service provision—the database technologies and architectures in particular are key—the Web site typically provides the first impression and the bulk of the interaction experience for most users. Thus, attention to interface considerations, information architecture, and an intuitive and informative user experience is critical.
Although the SSA was one of the first government agencies to have a Web site, it is now several years behind what commercial e-commerce and financial services sites are providing today (see Chapter 2 for more on expectations and offerings of world-class financial institutions). The current SSA Web site is largely a site for dispensing information about SSA programs, with capability for some (partial) online benefits applications and some retirement-planning calculations that require user-provided earnings and estimated benefit data. Thus, for example, a very basic operation that one might expect to find, being able to view one’s earnings history, is not supported at the time of this writing. The problem is more a policy issue than a technical one, and it may stem in part from a 1997 episode, when the SSA made an initial attempt to provide online services without completely thinking through the approach to security (specifically, only the SSN, mother’s maiden name, and state of birth were used for account authentication) and was strongly criticized as a result. However, given the widespread public adoption of online and secure access to bank and brokerage accounts that has occurred during the intervening
period of about 10 years, it seems possible that there may have been a change in the public’s attitudes about trade-offs between privacy protection and the benefits associated with having online access to confidential financial information. Accordingly, the SSA should continue to monitor public attitudes toward online access to sensitive personal information in order to determine if and how the SSA might furnish individual records and data online in ways that are consistent with contemporary practices, that present minimal and acceptable risk, and that are acceptable to the users of its services.
The current SSA Web site is limited in several additional ways. First, only a subset of the information on the SSA site is available in a language other than English. Furthermore, the online application for Social Security retirement and disability benefits is only available in English and, at the time of writing of this report, was only accessible using particular browsers.27 The benefits application pages explicitly state that there is no support for users of Apple or WebTV systems. As noted in Chapter 2, this situation should not be allowed to persist, as this level of services falls short of the current state of cross-browser and cross-platform compatibility found in such commercial sectors as financial services and telecommunications.
Future Directions for Software Development
A number of trends in the computer software-development and applications arenas will be relevant to the SSA as it updates its systems and develops its strategy for electronic services. These trends, which should be watched and leveraged over time,28 include the following:
-
The Service-Oriented Architecture (SOA)29 wave,
|
27 |
On October 24, 2006, the SSA Web site section “Social Security Claims” at https://s044a90.ssa.gov/apps6z/ISBA/main.html had the following message: “Note to Mac and Web TV Users: This Internet service does not support Mac or Web TV browsers. If you are a Mac/Web TV user, please call one of the toll-free numbers listed on the page. Our representatives can arrange for your application to be taken over the phone or in person at a Social Security office.” |
|
28 |
Names of specific companies and technologies are offered simply as examples. The committee does not necessarily endorse or recommend any particular company or technology. |
|
29 |
See, for example, M. Huhns and M. Singh, “Service-Oriented Computing: Key Concepts and Principles,” IEEE Internet Computing 1(9):75-81, 2005; G. Alonso, F. Casati, H. Kuno, and V. Machiraju, Web Services: Concepts, Architectures, and Applications, Berlin/Heidelberg: Springer-Verlag, 2004; M. Singh and M. Huhns, Service-Oriented Computing: Semantics, Processes, Agents, West Sussex, England: Wiley, 2005. See also the work of the OASIS SOA Reference Model technical committee at http://www.oasis-open.org/committees/tc_home.php?wg_abbrev=soa-rm, accessed June 20, 2007. |
-
Software as services and resulting value-added service and third-party software opportunities,
-
The proliferation of Extensible Markup Language (XML) and its impact both on search and on record format standardization efforts,
-
Advances in data mining and machine learning techniques,
-
Continued advances in commercial database technology, and
-
Advances in interactive applications.
SOA is one of the most highly touted trends in enterprise IT software today. Like the SSA, virtually every large enterprise today runs on a heterogeneous collection of software applications, some off the shelf (for example, SAP, PeopleSoft, Siebel, Oracle) and some in-house (and often mainframe-based) applications that would be difficult or expensive to replace. In order to automate more of their business processes to offer new and enhanced services to various stakeholder groups, enterprises often need to develop new applications that integrate functionality and data from multiple existing applications. Responding to this need, software research in the 1990s focused on “megaprogramming,”30 workflow systems technology, and distributed component-based programming models. The fruits of that research—and of the corresponding industrial activity in the area—include XML-based Web services and new, high-level programming approaches and tools for building new applications by composing existing services (also known as “programming by composition”). The SOA trend and its associated tools are likely to be very relevant to the SSA, providing high-productivity tools for service-enabling the agency’s existing applications and for using and/or reusing the resulting component services in constructing new online services and internal applications.
A companion trend to the one involving SOA and high-productivity tools for service composition is the availability of tools for business activity monitoring (BAM) and/or business process analysis (BPA). These tools support the modeling, monitoring, and gathering of analytic information about the day-to-day operations of business processes. Such tools, which are rapidly maturing, could enable the SSA to gain visibility into the efficiency and performance of its business processes, providing information that could then be used to diagnose bottlenecks and other problems and to tune or adapt its processes over time to provide better service to its users and clients. Disability-claim processing, a complex and lengthy SSA process, seems to be a particularly appropriate target for such monitoring and analysis tools. Other tools will be able to analyze process
definitions in order to identify process defects that could lead to incorrect outcomes.
Another related and very relevant trend is the “software as a service” trend. Rather than building and selling software packages that enterprises must then install, manage, and maintain or upgrade, a number of companies are starting to offer “software as a service”—they build and manage vertical applications that are available to enterprises through a combination of Web services and interactive Web pages.31 Another relevant example is in the tax preparation software market, where companies including H&R Block and TurboTax are now offering tax preparation online as well as through client-installed software packages. The types of services and interactive client applications that these industries are now offering are not unlike the services needed by SSA partners and clients, particularly for complex functions such as disability-claim preparation and planning, “what if” planning for various benefits (such as online retirement planning, assistance with prescription drug program selection, and impact analysis of change in employment status), representative payment, annual wage reporting, and so on.
Trends in data formats and standardization thereof, notably centered on XML, are very relevant to the SSA. In the past several years, XML has taken the machine-to-machine Internet data-transfer field by storm, not unlike the impact that HyperText Markup Language (HTML) had on the machine-to-person side of the Internet. XML is now central to data interchange both within and between enterprises. As a result, it is now also at the heart of many efforts for standardizing electronic documents for use in a wide variety of fields, including insurance, law, manufacturing, business, and of course health care (e.g., the Health Level Seven, or HL7 initiative32). Continued adoption of XML and associated schema standards for data interchange appears likely to offer the SSA significant future opportunities to streamline and automate its interactions with many of its user communities, such as other government agencies and nongovernment business partners.
Another significant data-format trend is the use of XML as a file format for office automation software, such as the Organization for the Advancement of Structured Information Standards (OASIS) Open Document Format for Office Applications and the new Microsoft Office open
|
31 |
SalesForce.com is a leading example of this class of software vendor—it provides a leading customer relationship management (CRM) application via this “software as a service” model. The significant traction that SalesForce.com has in the CRM marketplace is an indication of the potential for this model. |
|
32 |
HL7 is one of several American National Standards Institute (ANSI)-accredited Standards Developing Organizations operating in the health care arena. HL7’s domain is clinical and administrative data. |
XML formats. These trends could open up many types of electronic documents—an SSA example might be various reports related to disability claims—to broad and efficient searching (subject, of course, to stringent access control in order to protect privacy) and more advanced XML-based semistructured content search technologies as they are developed. Such technologies should provide the SSA with powerful search capabilities that can be leveraged for disability-claims processing and related services in the future.
Moving to a different technology area, the past decade has seen great advances in the area sometimes referred to as Knowledge and Data Discovery. Significant advances have been made in the areas of data mining and machine learning, giving rise to a number of new approaches to mining very large sets of data, building and maintaining classification networks, and so on. These advances are being exploited today in a number of industries and government agencies that face problems not unlike those that confront the SSA. The insurance industry is successfully using these advances to speed claim analysis and provide enhanced automatic fraud detection, while the financial industry is using these advances to automate much of the loan origination process (such as for mortgage lending). As the SSA seeks to improve the quality and timeliness of service to its constituents, it stands to benefit from the use of these advances as well. As an example, it seems well within the capabilities of this technology for the SSA to automate fully the classification of “simple” disability claims. Presumably the SSA would wish to ensure some level of human monitoring of such automated classification, but efficiencies would certainly still be obtained. This technology could also be put to work on the other end of the process to look for patterns indicating potential fraud.
Last but not least, advances continue in the database-management field as well, and the SSA is definitely a strong candidate for benefiting from these advances. As discussed elsewhere in the report, relational database system technology has made huge strides in the 35 years since its inception, having gone from theoretical speculation in 1970 to serious commercial offerings in 1980 to a booming industry in 1990 to the heart of almost every serious enterprise’s IT infrastructure today. Telecommunications and financial services companies manage many terabytes of data today using commercial off-the-shelf relational database management systems. Relational database technology today is on the verge of commoditization on the lower end, and on the higher end there are a number of high-performance, highly scalable systems available that provide integrated replication services for failover and disaster recovery. Moreover, most of these systems provide support for advanced “large” or “multimedia” data types, including text, images, geospatial data, and XML—essentially every imaginable data type that the SSA needs to store,
manage, and search. Also as mentioned earlier, database technology limitations are definitely no longer a reason for the SSA to rely on the use of in-house data management solutions.
As with the case of best practices described in Chapter 2, trends in technology development and deployment should also be monitored carefully for their potential relevance to the SSA. There are a number of technologies on the horizon—this section mentions several exemplars—that appear to be gaining significant traction in other IT sectors and that may be of great use to the SSA. These should be monitored and adopted as appropriate—they may not all mature at the same rate or at the same time, or even soon.
SECURITY, PRIVACY, AND AUTHENTICATION
Like other institutions, the SSA faces an onslaught of information and computer security challenges, including attempted break-ins, theft, tampering, and phishing. And, as with any other large organization, the SSA will also inevitably face challenges in dealing with the problem of having insiders participate in facilitating violations of privacy and security, the so-called insider problem.33 In recognition of these challenges, there is understandably a very strong security focus underlying the SSA’s IT efforts. In the committee’s view, the SSA clearly takes the problem of security very seriously and appears to have adopted best industry practices. The SSA views its user community as consisting of four distinct groups: employees and trusted individuals, government agencies, nongovernment business partners, and the general public. Identification, authentication, and authorization are handled differently for each of these groups.
Internally, the SSA security team is organized into four subteams, as follows:
-
The policy group sets security policies.
-
The standards group creates standards that embody the policies set by the policy group.
-
The execute group implements the organization’s security policies in software and architecture.
-
The oversight group ensures that SSA IT projects use the appropri-
|
33 |
“White Paper: Cyber-Security and the Insider Threat to Classified Information,” a non-reviewed summary prepared by the National Research Council’s Computer Science and Telecommunications Board, 2001, available at http://cstb.org/whitepaper_insiderthreat, accessed June 15, 2007. See also M. Bishop, Computer Security: Art and Science, New York: Addison-Wesley Professional, 2002, p. 21. |
-
ate tools and that the resulting implementations match the established policies.
The SSA also does regular penetration testing of its Web site; this is one of the responsibilities of its Intrusion Protection Team, which is made up of both SSA employees and outside penetration testing specialists. In addition, the SSA has a contract with an external vendor (IBM Managed Security Services) for providing real-time intrusion-detection services.
These security approaches are aimed at, among other things, protecting the integrity and confidentiality of the data that SSA maintains. In terms of SSA’s approach to privacy from a policy standpoint, the SSA Web site states that with regard to government information exchange, “The privacy of all personal information SSA maintains in its databases is protected and controlled by a number of Federal statutes, including section 1106 of the Social Security Act, the Privacy Act of 1974, section 6103 of the Internal Revenue Code, and related Social Security regulations and policies.”34
In the case of the SSA’s electronic services in particular, the issue of privacy typically revolves around how and why individual data are accessed or disclosed and to what extent individuals can control access to their data. As is often the case, privacy overlaps security in that confidentiality mechanisms provide the tools used to control access to data and to monitor to whom the SSA allows access to customer data. The SSA collects financial and medical data about individuals, as well as customer service data. The former support the SSA’s goals of financial stewardship and service provision; the latter improves the SSA’s ability to provide that service. There are likely cases in which those who need access to customer service data will not need access to the financial or medical data and vice versa. Thus, keeping these types of data separate and secure unless, perhaps, when there is a programmatic need for both types of data (for example, when paying medical bills) can serve to protect privacy while not compromising needed service provision.
Authentication
Authentication—both technological measures that authenticate individuals and ways to perform authentication that respect privacy—was discussed at length in a previous National Research Council report that
|
34 |
See http://www.ssa.gov/gix/privacyinfo.html, accessed June 20, 2007. In addition, the SSA’s privacy policy for its online offerings is available at http://www.ssa.gov/privacy.html, accessed June 20, 2007. |
was partially funded by the SSA.35 Authentication issues, including the existence and use of a unique identifier such as the SSN, continue to be highly controversial and continue to hinder progress on providing a wide range of electronic services. For example, comprehensive authentication across multiple applications would allow the SSA’s clients to authenticate once per session, without having to reenter their data in order to conduct transactions related to separate applications or programs. The committee conjectures that part of the problem in moving forward with comprehensive online authentication solutions is the recognition that any security or privacy breach may result in chastisement by Congress. Furthermore, commercial sites generally factor the financial cost of a certain potential level of fraud into their basic cost structure. Commercial organizations reason that it can be less expensive to tolerate certain improbable potential losses than to try to prevent them at any cost. As with other financial institutions that face trade-offs between security and accessibility, in most cases the costs of security breaches to the SSA may be more a matter of reputation than of finance. Although the risk-cost or risk-benefit analyses can be challenging, it is nevertheless important for the SSA to weigh the agency and public benefits from expanding electronic service functionalities against the incremental risks and costs.
For its current online suite of services, the SSA’s solution to the authentication problem is to do initial password assignments through the U.S. mail. (And, indeed, some financial institutions still use a Postal Service channel for initial verification when setting up online authentication for an individual.) In June 2006, individuals already receiving benefits could apply online for a temporary password request code (PRC) by providing their date of birth and SSN through a secure transmission. (The SSN itself cannot be used as a secure password/secret; see Box 3.2 for more on the SSN as an identifier.) At that time, the SSA Web site indicated that a person could expect to wait at least 15 days for a temporary PRC to be mailed to his or her address of record. Once a beneficiary has a temporary PRC, he or she can use it to create a permanent password. Logging in allows a person to check personal information and benefits; see his or her address, telephone number, direct deposit, and Medicare and payment information; change the address and/or telephone number in the SSA’s records; request or change direct deposit; start direct deposit of checks or change
|
BOX 3.2 The SSN as Identifier and Authenticator Social Security numbers (SSNs) are nine-digit numbers whose first three digits are related to the geographic location where the SSN was issued. The SSN concept was originally created in 1935-1936 to keep track of workers’ earnings. After Executive Order 9397, issued in 1943, required federal agencies to use the SSN to identify persons in any new federal systems-of-records systems, its use as an identifier in these systems grew, but slowly, for nearly 20 years. Then, in 1961, the Civil Service Commission began using the SSN to identify federal employees; the Internal Revenue Service began using it as the official taxpayer identification number the next year. As computers came into more widespread use, the use of the SSN as an identifier by federal, state, and local governments and private-sector organizations grew very rapidly. No legislation prohibited broad use of the SSN. Indeed, in 1970, congressional concerns about welfare fraud and unauthorized workers led to amendments to the Social Security Act authorizing the Social Security Administration (SSA) to assign SSNs to legally admitted noncitizens entering the United States and to people applying for or receiving federal benefits. Subsequent legislation continued to expand the use of the SSN—for example, as a condition of eligibility for federal assistance or loan programs; for use by states as part of their own tax processing, public assistance, driver’s license, or motor vehicle registration functions; for use in child support enforcement; and for military Selective Service (draft) purposes. According to the SSA, there are now 27 authorized uses of the SSN as the identifier for record-keeping or matching criteria.1 Although numerous laws authorize and/or require the use of the SSN as an identifier, no federal law regulates its overall use. Some federal laws restrict the use of SSNs in certain programs to specific uses and prohibit unauthorized disclosure, but there is no federal law regulating or restricting the use of SSNs by the private sector.2 Their use as a de facto near-universal identifier has proven to be problematic—resulting in easier paths to identity theft and credit fraud.
|
the current direct deposit to another account or financial institution; and change the password.36
|
36 |
Information obtained from the SSA’s Web site at https://s3abaca.ssa.gov/pro/passregi/passserv.shtml, accessed June 23, 2006. In June 2007, the SSA’s updated Web site has new information indicating that a current beneficiary or a person who has recently applied for benefits can request a password. See https://s044a90.ssa.gov/apps6z/ACU_LDPG/landingpage, |
|
When possible, most institutions are now moving away from use of the SSN (for example, as student identification [IDs], subscriber IDs, customer IDs, and so on). Given the widespread use of the SSN and its increasing exposure to potential misuse (for example, from lost or compromised government and corporate data containing millions of individuals’ SSNs and other identifying information), knowledge of an SSN should not be the only information required for an individual to authenticate himself or herself to the SSA or any other institution. Indeed, as the SSN contains only 9 digits (making for a maximum of 1 billion different SSNs), and the number of issued SSNs exceeds 400 million,3 there is at least a 40 percent probability that a randomly generated 9-digit number will be someone’s SSN. Thus, the security risk from relying solely on the SSN for authentication is large and growing. In comparison, American Express card account numbers are 14 digits long, Visa/MasterCard account numbers are 16 digits long, and both have a 3- or 4-digit security code marked on the card to prevent fraud.4 Additional information related to an account (for example, the billing zip code, a personal identification number, or details about a recent transaction) is often required when interacting with a financial institution in a way that could compromise an account. The security of the SSN, given its ubiquity and comparative simplicity, is a challenge. Addressing this challenge involves not just the SSA but also the multiplicity of federal, state, local, and private-sector entities that use the Social Security number to identify individuals or accounts.
|
Note that a user’s password is not sufficient to view his or her earnings history online. Indeed, only current beneficiaries can get passwords.
|
accessed June 20, 2007. In 2007, as in 2006, the password request functions are not available 24/7, and the SSA’s Web site indicates that the waiting period for receiving a temporary PRC by mail can be up to 15 days. See https://s044a90.ssa.gov/apps6z/ACU_LDPG/landingpage, accessed June 20, 2007. |
A beneficiary’s password is, however, sufficient to change the bank account to which direct deposits are made. The committee conjectures that the former may be considered not merely a security risk but also a more emotionally laden privacy risk, even as security breaches regarding the earnings history are less likely to have real financial consequences than would security breaches regarding bank accounts and direct deposits. It is unclear whether this policy is a carefully considered choice, resulting from a rigorous cost-benefit analysis, or an unintended consequence of various privacy and security policies influenced by oversight probes.
Security and Privacy in a Dynamic Environment
In addition to continuing changes in hardware, software, and the ways in which people will choose to access services, large organizations such as the SSA will also have to address how their security, privacy, and authentication policies may need to change over time. Over the next decades, the SSA will face many challenges—both internal and external—in maintaining privacy and security. The external challenges will arise from entities that wish to obtain information or access for which they are not authorized. The internal challenges will come from entities that are authorized to have access or information but the authorized entities abuse or misuse it, or even just make a mistake.
The set of policies that define security, privacy, and authentication for the SSA are controlled not only by the agency itself but also by external factors such as statutes and regulations (see Appendix D regarding some of the relevant statutes). The agency is constrained to choose mechanisms to enforce these policies in a way that complies with the goals and constraints under which it functions. In particular, the SSA’s entire e-government approach must view security, privacy, and authentication policies in the context of the agency as a whole, with electronic services as part of an overall service-delivery strategy (see Chapter 4).
Numerous approaches to information system security (in this case encompassing privacy and authentication, as well) have been developed by the information security community.37 On the basis of briefings and conversations with SSA technical staff, the committee considers that staff to be well informed in these areas and mindful of the challenges and principles involved.
The SSA consists of several components, each of which manages different sets of systems. Each part of the agency has performed security
|
37 |
See, for example, at http://cstb.org/topic_security/ a listing of numerous reports from the Computer Science and Telecommunications Board on cybersecurity and computer security. |
analyses. According to information given to the committee, the SSA has clearly weighed the risks very heavily. One caution, however, is that such an emphasis may lead to an unnecessary use of mechanisms that impair one or more security services. This can occur because security can be thought of as consisting of three types of services: confidentiality services, integrity services, and availability services. For example, the availability of information is critical for timely transactions and handling of cases. But availability carries with it the risk that the information may be disclosed to unauthorized parties. Hence, limiting availability reduces risks to confidentiality, but it increases risks to availability. The security policy must strike the correct balance between these qualities, and that balance should be determined by risk analysis and cost-benefit analysis.
The factors involved in determining approaches to security and policy include not only the SSA’s internal rules, but also the laws and regulations imposed externally by Congress and by other federal agencies (such as the Office of Management and Budget [OMB]) and court rulings. Further, agreements with state agencies impose additional constraints. Thus, technical concerns are not paramount but are simply one factor to be considered along with these other factors. Clearly, none of the above is meant to suggest that the SSA should not pay appropriate attention to security risks. Both internal controls and measures to address external threats (fraud, hackers, and so on) must be considered. To be most effective, security must be built into a system from the start. Treating it as an add-on or applying Band-Aid-type measures is costly in terms of resources and risk. Although the SSA may not have taken a security-from-the-start approach in all of its previous electronic services projects,38 this report is aimed at encouraging the agency to adopt that posture as it seeks to expand the scope of its electronic services. Admittedly the agency cannot address these challenges alone—as with other government agencies, congressional and/or executive branch (through OMB, for example), involvement could help provide a framework and broader support for SSA actions to offset the threat of potential negative reactions.
|
38 |
See SSA, Assistant Inspector General for Audit, “Evaluation of the Accelerated eDIB System—Third Assessment (A-14-03-13047), December 20, 2002, available at http://www.ssa.gov/oig/ADOBEPDF?A-14-03-13047.pdf, accessed June 29, 2006. The SSA’s Office of the Inspector General (OIG) found that the August 2000 eDIB Program Management Plan “neither addressed security nor evaluated the risks involved in eDib program development. OIG concerns were partially addressed in the November 14, 2001, eDIb Program Management Plan…. However the [2001] plan did not address the risks associated with security, fraud, hackers, and complexity of the system. Instead, the Risk Management Plan addressed development risks, which could be incurred during systems development, such as cost, schedule, integration/technical and mission. While system development risks should be considered, it is as important to address risks that relate to internal controls and security.” |
|
BOX 3.3 General Security Principles In a dynamic and changing environment, the policy and technology questions relating to security and privacy must be revisited on a continuing basis. The following are several useful principles for any large organization developing security policies:
|
This section has focused briefly on three aspects of what is commonly called security: namely, security, privacy, and authentication. Each is different, and presents different challenges. All are intertwined; none can be considered without regard to the other two, and decisions made for one affect the decisions that will have to be made for the other two. A brief summary of general security principles is provided in Box 3.3. Several themes that the SSA should continue to keep in mind when contemplating security, privacy, and authentication policies going forward are these: the larger societal, organizational, and technological contexts of which it will be a part; balancing risks with benefits and avoiding an overemphasis on risk, especially with regard to electronic services (in today’s environment, lack of electronic service adoption is itself a serious risk for an agency facing serious workload and staffing challenges); and the need to be open to the evaluation and adoption of proven industry technologies and tools.
USER INTERFACE
Some of the current barriers to electronic service adoption are external to sponsoring organizations such as the SSA and/or they directly involve users. These include user concerns over privacy and security (discussed previously), the perceived convenience or inconvenience of electronic services, users’ lack of knowledge about available services, the complexity and cost of providing electronic services, and lack of access to Internet-connected devices.39 Privacy concerns may have a significant impact on overall user interfaces and access, because information protection measures being considered at state and federal levels may require users to provide identifying information such as personal identification numbers (PINs) and passwords. For example, encrypted data may require the cus-
|
39 |
Michael Adler and Paul Henman, with Jackie Gulland and Sharon Gaby, Computerisation and E-Government in Social Security: A Comparative International Study, Washington, D.C.: IBM Center for the Business of Government, July 2005; Council for Excellence in Government, Hart-Teeter on behalf of the Council for Excellence in Government, The New E-Government Equation: Ease, Engagement, Privacy and Protection, Washington, D.C.: Council for Excellence in Government, April 2003, available from http://www.excelgov.org/usermedia/images/uploads/PDFs/egovpoll2003.pdf, accessed June 19, 2007; Internal Revenue Service, Findings from the 2002 Wave of e-file Taxpayer Attitudinal Tracking Research, 2002, available at http://www.irs.gov/taxpros/display/0,,i1%3D5%26genericId%3D10121,00.html, accessed May 23, 2002; Nielsen/NetRatings, More Than One Third of All Online Users Log on to Government Sites, New York: Nielsen/Net Ratings Press Release, March 17, 2003, available at http://www.nielsen-netratings.com/press.jsp?section=ne_press_releases&nav=1#2003, accessed June 19, 2007; D.M. West, “E-Government and the Transformation of Service Delivery and Citizen Attitudes,” Public Administration Review 64(1):15-27, 2004; and Elena Larsen and Lee Rainie, The Rise of the E-Citizen: How People Use Government Agencies’ Web Sites, Washington, D.C.: Pew Internet and American Life Project, April 3, 2002, available at http://www.pewinternet.org/reports/toc.asp?Report=57, accessed June 19, 2007. |
tomer to provide identifying information not only over the Web but also in phone calls, so as to authorize the person at the call center to access the caller’s data. This requirement can pose challenges to some customers who may have difficulty remembering such information. Other barriers are internal to sponsoring organizations and arise from institutional and cultural factors: lack of staff, an out-of-date technical infrastructure, competing priorities for resources, lack of institutional readiness, and lack of leadership.40
Fifteen years ago, the major Internet applications were e-mail, file transfer (ftp), and remote log-in (telnet). Nearly all home users accessed online services through dial-up connections. There were no electronic commerce sites. The emergence and burgeoning of the Web has clearly had a dramatic impact on all aspects of our lives, and there is every reason to believe that its impact will only increase. The majority of individuals now in their retirement years are not Web users, and usage currently decreases markedly for those over 70. However, by the time the baby boom generation has finished retiring, in 15 to 20 years, one can reasonably expect Web use by retirees to be much higher. The youngest baby boomers are now in their early 40s and have far different exposure and comfort levels with computers and electronic transactions than did average people in their 40s in the early 1980s. The oldest baby boomers have turned 60, and the majority of them are using the Internet (see below).
There always will be some individuals (of all ages) who will not use electronic services despite efforts to make these services accessible and easy to use. However, other people or institutions may be assisting users with these electronic services; thus, the SSA’s electronic services are not just for use by individual clients, but also by the states, other government agencies, and employers, among others.
In predicting the demand for electronic information and services, it is important to understand the characteristics of Internet users—who will be online and how old will they be—as well as how online demographics will be changing. Key questions include these: Is it true that older people do not use the Internet? What are the projections, especially among baby boomers, for older people using the Internet? Who will use it and what
will they use it to do? Are the users getting help with electronic services, and what are the motivations of those providing the help?
In a partial answer to such questions, the Pew Internet and American Life Project41 reports the following statistics from 2004 survey data:
-
As of February 2004, 22 percent of Americans 65 and over (about 8 million people) use the Internet, compared with 15 percent in 2000 and 2 percent in 1996. The trend is clear. Those who have learned how to use the Internet are expecting to use it in the future. Surprisingly, 77 percent of those with Internet experience have 4 or more years of experience.
-
In the population already 65 and older, Internet use decreases steadily with age: in 2001, about 22 percent of Americans age 65 to 69 used the Internet, compared with about 15 percent of those age 70 to 74, about 8 percent of those age 75 to 80, and about 4 percent of those age 81 to 90.42
-
In that population of Americans 65 and over (see the preceding bullet item), the number of female users equaled the number of male users. Compared with the general population, not surprisingly, these are people with higher incomes and more education. Many more of this set of users access the Internet at home over dial-up, rather than high-speed connections, compared with the general population who go online at home. Only 11 percent of African-Americans 65 and older use the Internet, although 21 percent of English-speaking Hispanics 65 and over use the Internet, the same as for Caucasians in that age range.
-
Of those 65 and older who use the Internet, 94 percent use e-mail and well over half look for health or medical information. By the end of 2003, 60 percent of seniors who used the Internet had visited government Web sites, compared with 40 percent in 2000. Most of these users are online daily.
-
Of more interest are the expectations and talents of the older baby boomers, at the time of the survey 50 to 58 years old; the Pew report calls this population the “Silver Tsunami.” In 2004, Pew found that 62 percent of those 50 to 58 years old used the Internet, compared to 46 percent of those in the 59 to 68 year age range. Only 17 percent of those age 69 and older use the Internet. The older boomers are very much like the younger, Generation X, “eager users.” They embrace e-mail, use instant messaging,
|
41 |
Susannah Fox, Older Americans and the Internet, Pew Internet and American Life Project, Pew Research Center, Washington, D.C., March 25, 2004 (hereafter cited as Susannah Fox, Older Americans and the Internet), available at http://www.pewinternet.org/pdfs/PIP_Seniors_Online_2004.pdf, accessed July 11, 2007. |
|
42 |
Susannah Fox, Wired Seniors, Pew Internet and American Life Project, Pew Research Center, Washington, D.C., Sept. 9, 2001, available at http://www.pewinternet.org/pdfs/PIP_Wired_Seniors_Report.pdf, accessed July 11, 2007. |
-
and often get their news online. “As Internet users in their 50s get older and retire, they are unlikely to give up their wired ways and therefore will transform the wired senior stereotype.”43
-
However, one in four Americans never uses the Internet and is not in a household with Internet access. People over 65 currently make up a large portion of this group.
This last group is sometimes referred to as the “Truly Disconnected,” and its number has not changed over the past 10 years. These are the people who need agents to help them get the information they need. Even though this group may be a relatively small proportion of the general population, it represents a large number of people in absolute terms. There are barriers to these people getting the information that they need. For instance, a number of older people think that they do not need to access the Internet, since many services, such as Social Security, are available through multiple delivery channels. This is an opportunity for education and outreach. In addition, many older people do not own a computer, nor know how to use one. This number will decrease in time, but right now there is clearly a need for third parties or intermediaries to work with the people in this group to get them the information they need. This could be done through organizations similar to commercial tax preparers that help tax filers, through public servants such as reference librarians at public libraries, or through not-for-profit organizations that provide a variety of services to SSA beneficiaries. Just as the financial services institutions discussed in Chapter 2 do not remove all access channels other than electronic services, so the SSA will need to retain and support more traditional approaches to service provision.
Even if older people access Web sites on the Internet, many are difficult to use.44 The Nielsen/Norman Group, a usability consulting firm, has declared that Web sites are twice as hard for older people in general as for younger people to use. In particular, older people have difficulty with small type sizes, low contrast, short links (the target size to be pointed at is small), and rolling pull-down menus. Furthermore, because of short-term memory challenges, if the site does not change the color of the links traversed, older people may have difficulty navigating.45
One set of current usability standards for older people recommends the following:
-
Less text (so that it is easier to remember),
-
Plain language,
-
12 point sans serif font,
-
Strong color contrast,
-
Buttons that can be used to enlarge the type size, increase the text contrast, or read the text out loud, and
-
Consistent page layout (so that people can learn where to look for various things).46
Not surprisingly, efforts to make a site more usable for seniors also increase the usability for all age groups.47 The SSA will also need to keep in mind the requirements of individuals with disabilities or significant physical or cognitive impairments. Although the same principles and approaches may prove useful, ability-specific methodologies may be needed to ensure that the SSA site is as easy to use as possible for people of varying abilities. More generally, what are considered optimal Web site designs and standards will change over time. Remaining aware of best practices and conducting ongoing use testing to evaluate proposed sites and designs are necessary efforts for any institution maintaining an online presence.
ACCESS TECHNOLOGIES
A variety of technology options—cable, digital subscriber line (DSL), fiber-to-the-premises, metropolitan area wireless networks—are enabling increased broadband penetration. Increasingly functional access using handheld devices is available through 3G cellular networks. Although personal computers (whose prices, both absolute and performance-adjusted, have steadily dropped) appear likely to remain the major way that users access the Internet, the SSA, and indeed all government agencies, should expect that other technologies such as mobile phones, Internet-connected televisions, game boxes, and other “thin clients” will provide means for those who are not technologically savvy to use networked information and services. Consequently, the SSA should not continue to expect that most of its customers will be using Internet Explorer (or a similar browser) running on a desktop or laptop PC. To be effective and to meet the likely future needs of its users, the SSA should be prepared to eventually support a wide variety of browsers running on a wide variety of devices ranging
from digital televisions to cellular phones. This is not to say that the SSA will need to be at the forefront in developing these services. Other private-sector industries will undoubtedly lead the way. The agency will need to be mindful of these and related technologies and how they are being deployed and used, and it will need to be prepared to take advantage of them for its own beneficiaries and users when appropriate.
Deep broadband penetration will provide the opportunity for the SSA’s users to interact with the agency using technologies such as text chat or Voice over Internet Protocol (VoIP). For example, when filling out a form, a user might click a help link connecting the user to a live help desk using VoIP or chat (as some online retailers do today). Alternatively, a “stuck” user might click on a context-aware help link that would bring up a segment of video demonstrating how to continue filling out a troublesome part of the online application.48
SUMMARY
Like virtually all other organizations inside or outside the government, the SSA must carefully and regularly examine information technology trends. The agency simply could not perform its functions without the use of technology, and its current reliance on technology will inevitably grow as its workload grows and its access to support resources inevitably fails to keep pace. Thus, it is incumbent on the SSA to keep close track of changes and advances in technology. In some areas, notably security and privacy, the SSA seems to be doing a good job of tracking technology and incorporating current best practices into its processes. In other areas, notably databases, the SSA is not on par with technological advances. Ensuring that the SSA is able to keep pace with technology is not only a technological issue but is also an organizational issue. There are other organizational issues that have a direct bearing on the SSA’s ability to roll out needed electronic services in coming years. These are addressed in Chapter 4.
|
48 |
There are also technologies known as Rich Internet Applications, such as Flash, Asynchronous Java Script and XML (AJAX), and others that allow Web developers to develop richer client-side applications by migrating pieces of an application from the server to the client browser. See, for example, Jesse James Garrett, “AJAX: A New Approach to Web Applications,” Feb. 18, 2005, available at http://www.adaptivepath.com/publications/essays/archives/000385.php, accessed June 20, 2007. The most familiar example of AJAX technology is probably Google maps (http://maps.google.com), which provides the user the ability to “scroll” the map by dragging it with the mouse. This scrolling occurs locally, with the AJAX application asynchronously requesting additional map segments and/or satellite imagery from the Google server. In addition to providing a richer user experience, applications written using AJAX technology reduce the load on the server. On the other hand, such approaches can conflict with the desire to let the user employ “thin clients” to access services. |





































