4
Vulnerabilities of Systems for Sensing, Communication, and Control
The operation of a modern electric power system depends on complex systems of sensors and automated and manual controls, all of which are tied together through communication systems. While the direct physical destruction of generators, substations, or power lines may be the most obvious strategy for causing blackouts, activities that compromise the operation of sensors, communication, and control systems by spoofing, jamming, or sending improper commands could also disrupt the system, cause blackouts, and in some cases result in physical damage to key system components. Hacking and cyber attacks are becoming increasingly common.
Most early communication and control systems used in the operation of the electric power system were carefully isolated from the outside world, and were separate from other systems such as corporate enterprise computing. However, economic pressures created incentives for utilities to make greater use of commercially available communications and other equipment that was not originally designed with security in mind. Unfortunately, from a security perspective, such interconnections with office and electronic business systems through other layers of communications have created vulnerabilities. While this problem is now well understood in the industry and corrective actions are being taken, the industry is still in a transition period during which some control systems have been inadvertently exposed to access from the Internet, intranets, and remote dial-up capabilities that are vulnerable to cyber intrusions.
Many elements of the distributed control systems now in use in power systems are also used in a variety of applications in process control, manufacturing, chemical process controls and refineries, transportation, and other critical infrastructure sectors and hence vulnerable to similar modes of attack. Dozens of communication and cyber security intrusions, as well as penetration red-team attacks, have been conducted by DOE, EPRI, electric utilities, commercial security consultants, and others. These “attacks” have uncovered a variety of cyber vulnerabilities including unauthorized access, penetration, and hijacking of control.
While the committee is unaware of any successful hostile cyber attack on the systems that control the operation of a power system, the risks posed by such attacks are sufficiently large to warrant serious consideration, continued improvement of key systems, and high levels of vigilance including careful attention to personnel training and operational procedures.
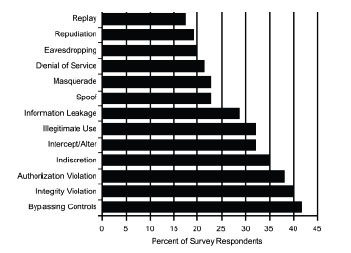
EPRI has conducted a survey of electric utilities to identify their concerns about grid security, cyber security, and communications security (EPRI, 2000). Figure 4.1 ranks the perceived threats to utility control centers. The most likely threats identified were bypassing controls, integrity violations, and authorization violations, with 40 percent of respondents rating the seriousness of each as either a 5 or a 4 on a scale of 0 to 5. Concern about the potential threats generally increased as the size of the utility peak load increased.
SENSING, COMMUNICATION, AND CONTROL SUBSYSTEMS
Functions of Sensing, Communication, and Control Elements of a Typical Power System
Figure 4.2 provides a simplified schematic diagram of the sensing, communication, and control elements of a modern power system. The elements of the system depicted in Figure 4.2 are defined and described below. Further details on the operation of many of these elements are provided in chapter 6.
Energy Management System
The objective of the Emergency Management System (EMS) is to analyze the real-time measurements gathered by the supervisory control and data acquisition (SCADA) system (see next paragraph) to determine the reliability of the present operating condition of the grid, to alert the operators to any vulnerabilities to possible disturbances (contingen-
NOTES:
Authorization violation: Access by an entity that lacks the proper access rights.
Bypassing controls: Exploitation of system flaws or weaknesses by an authorized user in order to acquire unauthorized privileges.
Denial of service: Deliberate impedance of legitimate access to information.
Eavesdropping: Acquisition of information flows, sometimes by “listening” to radio or wireline transmissions, sometimes by analyzing traffic on a local area network.
Illegitimate use: knowingly or unknowingly intruding on system resources.
Indiscretion: Indiscriminate opening of information files and so on.
Information leakage: Unintentional provision of information to a disguised third party.
Integrity violation: Messages and the computer infrastructure subjected to unauthorized modification or destruction.
Intercept/alter: Intercepting and altering information flows, usually by accessing databases and modifying data.
Masquerade: Posing as an authorized user on a network, the most common method used by hackers to gain access to networks, often enabled by having other users’ passwords. A masquerader can view secret information, alter or destroy data, use unauthorized resources, and deny legitimate users access to services.
Replay: Use of information previously captured without necessarily knowing what it means.
Repudiation: Denial by an entity that it undertook some action such as sending a message or receiving information.
Spoof: Occurs when a user or application believes it is using one of the legitimate computer services, while actually performing some different function.
cies), and to calculate possible operational changes that could improve the operational condition (i.e., more optimized in terms of cost and less vulnerable to contingencies). A very important automatic function of an EMS is automatic generation control (AGC), which involves measurements of system frequency interchange power flows, and power plant outputs to regulate system frequency and net power interchange via commands sent to power plants. An EMS always works in concert with a SCADA system, with the SCADA as the front-end component connected directly to the grid and the EMS as the back-end component with the heavy computational capabilities; this combination is referred to as the EMS-SCADA (or just EMS) or simply, the control center. Communication connections between EMSs in neighboring grids are common for the exchange of data describing the real-time conditions in the nearby interconnected system. More details on EMSs and their use in systems monitoring and control are provided in chapter 6 of this report.
Supervisory Control and Data Acquisition
SCADA systems provide three critical functions in the operation of an electric power system: data acquisition, supervisory control, and alarm display. It consists of computers and display units with appropriate applications software, and is connected by a communications system to remote terminal units (RTUs) placed at substations that collect data and perform control of electrical system devices. The SCADA system polls the RTUs periodically to gather the real-time measurement data from all the substations and sends out control signals to the RTUs to control specific equipment. These supervisory control signals can be automatically generated by the SCADA computers or be manually initiated by the operator. The controls can be for operations of many types, such as the opening and closing of circuit breakers and the adjustment of control set points for transformer taps, generation of unit power outputs and voltage levels, DC transmission line flows, and so on. (It should be pointed out that SCADA is a generic name for this class of equipment, which is used for similar applications in many industries, including natural gas pipeline transmission and chemical plants.)
Most power system legacy SCADA systems operate in a several-second sample or polling rate. A separate SCADA system may be used for AGC. Modern SCADA systems may be networked using private Internet protocols, and may use faster sampling rates.
Remote Terminal Unit
RTUs are special-purpose microprocessor-based elements that are located at substations or power stations to interface with all the substation equipment. An RTU is connected to the SCADA system through a communication channel that
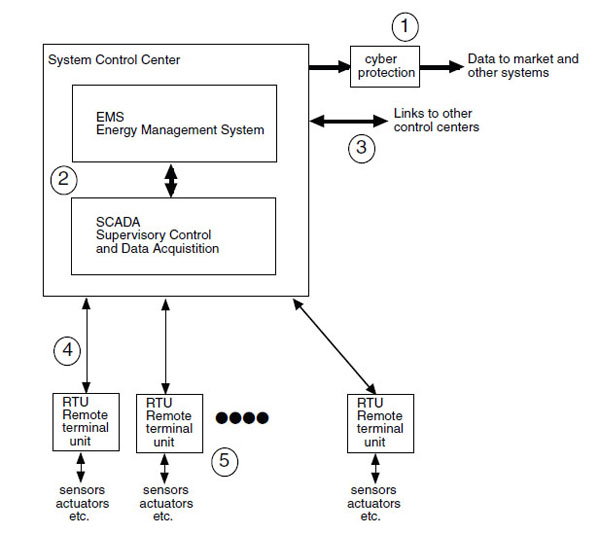
FIGURE 4-2 Simplified diagram of the sensing, communication, and control systems associated with a typical power system. Programmable logic controllers, protective relays, systems to control transformer tap settings and capacitor banks, automated metering systems, and distributed control systems as well as a variety of field devices all operate at this level. NOTE: Numbers refer to points of vulnerability discussed in the text.
uploads measurement data from the station and downloads control orders from the SCADA system. Within the station, the RTU is either directly connected to the equipment being controlled, or (because the new equipment is increasingly being controlled by microprocessors) through intra-station local communication networks. RTUs contain analog-to-digital and digital-to-analog converters, digital inputs for status, and digital or analog output for control.
A newer development is the intelligent electronic device, which often implies a built-in network capability such as Internet Protocol. Networked devices are, of course, more susceptible to cyber attacks. Sensors and the devices discussed below may also be considered intelligent electronic devices.
Programmable Logic Controller
Programmable logic controllers (PLCs) have been used extensively in manufacturing and process industries for many years and are now being used to implement relay and control systems in substations and power plants. PLCs replace binary (Boolean) logic networks of series and parallel combinations of electromechanical coils and contacts. They are used in mission-critical applications such as the special protection systems described in chapter 6, sometimes in fault-tolerant configurations (e.g., triply redundant with two out of three required to agree for an output decision). PLCs have extended input/output (I/O) systems similar to those of transmission substation RTUs. The control outputs can be controlled by software residing in the PLC
and via remote commands from a SCADA system. In some applications, PLCs with RTU-reporting capability may have advantages over conventional RTUs. PLCs can have many real-time communication links inside and outside substations or plants.
A step beyond PLCs are programmable automation controllers (PACs), which include data acquisition, signal processing, monitoring, monitoring/display, and feedback control. In one manufacturer’s product line of hardware and software, for example, the hardware can be either a PC or one of several real-time, embedded control devices.
Protective Relays
Protective relays are mission-critical electromechanical, analog, electronic, or digital controllers designed to respond to system faults and short circuits. When faults occur, the relays must signal the appropriate circuit breakers to trip and isolate the faulty equipment. Distribution system relaying must be coordinated with fuses and reclosures for faults while ignoring cold-load pickup, capacitor-bank switching, and transformer energization. Transmission-line relaying must locate and isolate a fault with sufficient speed to preserve stability, reduce fault damage, and minimize the impact on the power system. Modern digital protective relays can be networked, and settings can be changed remotely. chapter 6 of this report discusses applications and the functional reliability of the control and protection systems.
Automated Metering
Automated metering is designed to upload residential and/or commercial gas and/or electric meter data. These data can then be automatically downloaded to a PC or other device and transmitted to a central collection point. With this technology, real-time communication links exist outside the utility infrastructure.
Plant Distributed Control Systems
Plant distributed control systems (DCSs) are plant-wide control systems used for control and data acquisition. The I/O count can be higher than 20,000 data points. Often, the DCS is used as the plant data highway for communication to and from intelligent field devices, other control systems (such as PLCs), RTUs, and even the corporate data network for enterprise resource planning applications. DCS technology has been developed with operating efficiency and user configurability as drivers, rather than system security. In addition, technologies have been developed that allow remote access, usually via a PC, to view and potentially reconfigure the operating parameters.
Field Devices
Examples of field devices are process instrumentation such as pressure and temperature sensors and chemical analyzers. Other standard types of field devices include electric actuators. Intelligent field devices include electronics to enable field configuration, upload of calibration data, and so on. These devices can be configured offline. They also can have real-time communication links between plant control systems, maintenance management systems, stand-alone PCs, and other devices inside and outside the facility.
As noted above, perhaps the most serious vulnerability to the various sensing, communication, and control subsystems that has developed in recent years, and which is now being rapidly rectified, has been lack of attention to connections from system control centers to the outside world (labeled as 1 in Figure 4.2). If these connections are not treated with great care, and if proper cyber security protection is not provided, they can in principle become a route for attackers from the outside world to create disruption, take control, and cause damage. Recent steps to dramatically improve the security of these links are discussed below.
While some of the operations of an electric power system are automatic, ultimately human operators in the system control center make decisions and take actions to control the operation of the system. Physical threats to such centers and the communication links that flow in and out of them are described in chapter 3. But it is also essential to be concerned about two other factors: the reliability of the operators within the center, and the possibility that insecure code has been added to one of the programs in a center computer. The threats posed by “insiders” are discussed in chapter 5. The risk of a “Trojan horse” or other deleterious program being intentionally embedded in the software of one or more of the control centers is real, and this can only be addressed by careful security measures both within the commercial firms that develop and supply this software, and careful security screening of both utility and outside service personnel who perform software maintenance within the center. Today software security upgrades often are not always supplied to end users, or users do not promptly apply the upgrades for fear of impacts on system performance. Current practice is to apply upgrades after SCADA system vendors thoroughly test and validate them, sometimes delaying deployment by several months.
A third source of vulnerability can arise from the essential links to other system control centers (labeled as 3 in Figure 4.2). Such links are essential for the operation of a large interconnected grid. However, even if the control center (shown as 2 in Figure 4.2) has taken all the necessary steps to protect itself from unauthorized access, either by external electronic logic or direct human intervention, if other control
centers have not taken similar steps, the entire system is vulnerable. That is, the system is no stronger than the weakest link in the chain.
The communication links between the system control center and various devices in the field labeled as 4 in Figure 4.2 are perhaps less worrisome than the items labeled as 1, 2, and 3 but still constitute a source of vulnerability. While obtaining access to the electronic logic of these communication channels and spoofing (i.e., sending a false signal) is always a possibility, a greater concern is jamming, or physical disruption, that would prevent system operators from knowing what is going on in key parts of the system, or from issuing needed commands.
Finally, the myriad devices that sense and control the power system in the field present vulnerabilities. Of particular concern are wireless and dial-up connections that could be monitored, spoofed, jammed, or reprogrammed. For example, if it were possible to reach and reprogram relays that control circuit breakers, considerable physical harm could be inflicted on some devices under some circumstances. However, today such relays can no longer be reached from the outside on most major systems, and new mandatory security regulations are rapidly resulting in corrective action in those few (typically smaller) utilities where it is still possible. Similarly, while wireless systems are seeing greater use, they are typically not employed in vital control systems. Nevertheless, because wireless is often much cheaper to implement than secure hard-wired controls, this is a potential source of vulnerability that warrants continued attention.
None of the protective strategies discussed will be effective without regular programs of staff training, and careful adherence to thoughtfully developed procedures designed to avoid the inadvertent introduction of alien software into SCADA systems, or the creation of interconnections to outside systems that may not be secure, or can be accessed via the Internet or similar means.
TOWARD SECURE SYSTEMS FOR SENSING, COMMUNICATION, AND CONTROL
During the past few years there has been a notable increase in the level of activity and interest in security for SCADA and control system communications both within the U.S. government and within the electric power industry. For example, DOE has created the National SCADA Test Bed, which includes the Idaho National Laboratory, Pacific Northwest National Laboratory, Sandia National Laboratories (SNL), and the National Institute of Standards and Technology (NIST). Work performed by these laboratories includes development of retrofit solutions, testing of vendor products, validation of encryption techniques and algorithms, vulnerability assessments for industry, and assessment of threats to SCADA and control system communications.
The January 2006 “Roadmap to Secure Control Systems in the Energy Sector” (Eisenhauer et al., 2006), the result of an effort co-sponsored by the U.S. Departments of Energy and of Homeland Security in cooperation with Natural Resources Canada, was developed through a collaborative process led by energy owners and operators. The authors explain that the purposes of the roadmap effort were to:
• Define a consensus-based strategy that articulates the cyber security needs of owners and operators in the energy sector;
• Produce a comprehensive plan for improving the security, reliability, and functionality of advanced energy control systems over the next 10 years; and
• Guide efforts by industry, academia, and government and help clarify how each key stakeholder group can contribute to planning, developing, and disseminating security solutions.
The authors note:
[The] Roadmap builds on existing government and industry efforts to improve the security of control systems within the private sector by working through (1) the Electricity Sector Coordinating Council (coordinated by the North American Electric Reliability Council) and (2) the Oil and Natural Gas Sector Coordinating Council (coordinated by the American Petroleum Institute and the American Gas Association). The Roadmap is also intended to help coordinate and guide related control system security efforts, such as the Process Control Systems Forum (PCSF), Process Control Security Requirements Forum (PCSRF), Institute for Information Infrastructure Protection (I3P), International Electricity Infrastructure Assurance Forum (IEIA), Control System Security Center, and National SCADA Test Bed. (Eisenhauer et al., 2006)
Figure 4.3 provides a graphical summary of the results of this effort.
The U.S. Department of Homeland Security’s Advanced Research Projects Agency (HS-ARPA) has recently funded several innovative technology development efforts. These efforts have the potential to yield new and effective tools to help secure SCADA and control systems for the electric power sector as well as for other sectors such as gas and oil, water, and transportation.
Individual companies and industry research organizations have also been active. Two examples are the American Gas Association (AGA) and the Electric Power Research Institute (EPRI). AGA has developed a specification for retrofit security of SCADA and control system communications. EPRI maintains several programs to provide member companies with security solutions for operational systems. However, utilities’ interest in investing in major new initiatives in this area has been modest.
The North American Energy Reliability Council (NERC) Critical Infrastructure Protection Committee (CIPC) develops security standards and guidelines for the electric power
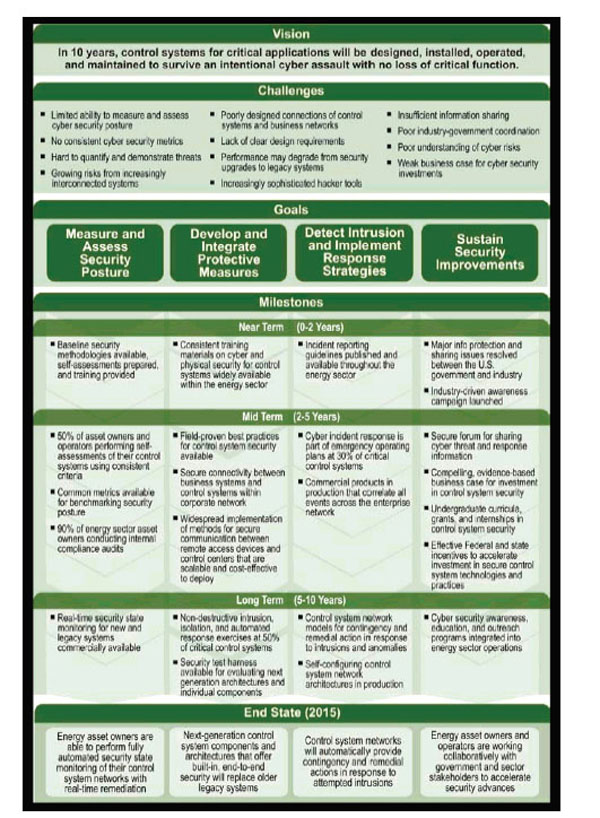
FIGURE 4.3 Road map for achieving secure control systems in the energy sector. SOURCE: Eisenhauer et al. (2006), p. 3.
industry. Formal CIPC representation is determined by the ERC regions, but meetings can be observed by any qualified industry member. A March 2006 report (NERC, 2006) by the NERC Control Systems Security Working Group (CSSWG) and the U.S. Department of Energy National SCADA Test Bed (NSTB) program highlights potential risks that can apply to some electricity sector organizations, describes practices that can help mitigate the risks, and provides a nonprioritized list of the 10 most common and threatening vulnerabilities to control systems in the electric sector based on the combined expertise of the NERC CSSWG members. The list, prepared by the CSSWG, is updated annually. As of March 2006, the top vulnerabilities of control systems and potential mitigation strategies were assessed to be:
• Inadequate policies, procedures, and culture governing control system security;
• Inadequately designed control system networks that lack sufficient defense-in-depth mechanisms;
• Remote access to control systems without appropriate access control;
• Auditable system administration mechanisms (system updates, user metrics, etc.) that are not part of control system implementation;
• Inadequately secured wireless communication;
• Use of a nondedicated communications channel for command and control, such as Internet-based SCADA, and/or inappropriate use of control system network bandwidth for noncontrol purposes (e.g., voice over Internet Protocol, or VoIP);
• Lack of quick and easy tools to detect and report on anomalous or inappropriate activity; inadequate or nonexistent forensic and audit methods;
• Installation of inappropriate applications on critical control system host computers;
• Software used in control systems that is not adequately scrutinized; and
• Control systems command and control data not authenticated.
Electric power utilities typically own and operate at least parts of their own telecommunication systems, which often consist of a fiber-optic or microwave backbone connecting major substations, with spurs to smaller sites. Historically, the energy industry operated closed, tightly controlled networks. Deregulation and the resulting commercial influences have placed new information-sharing demands on the industry. Traditional external entities like suppliers, consumers, regulators, and even competitors now must have access to segments of the network. The definition of the network must be expanded to include the external wide-area network connections for these external entities. This greatly increases the security risk to other functional segments of the internal network that must be protected from external connections. This is true whether a private network or the Internet is used to support the external wide-area network.
The external entities already have connections to the Internet, and as such the Internet can provide the backbone for the external wide-area network. Duplicating this backbone to create a private network requires not only large startup costs but also ongoing maintenance costs and potentially higher individual transaction costs than using the Internet. Nearly all control centers have multiple communication links. To understand the data security issues in the communication routes into the centers, more effort is required to determine how key data are routed before it gets to the center and where vulnerabilities exist (see Box 4.1).
In addition, standards for future solutions are being developed in several arenas, including, but not limited to, the International Electrotechnical Commission, the Instrumentation, Systems, and Automation Society, and, of course, the IEEE and ASME.
To address known vulnerabilities, the industry has worked diligently for the last 5 years to develop mandatory cyber standards through the NERC standards process. These mandatory standards will require a variety of preventive actions by all firms operating electric power facilities connected to the electric grids in North America. It is important to note that to effectively address the evolving spectrum of cyber threats, cyber standards should allow new technology solutions to be rapidly implemented and integrated to keep pace with these dynamic threats. Appendix E summarizes these new standards, which should be fully adopted within 3 to 5 years.
In summary, given the dynamic nature of cyber and communication threats, the long-term issue of cyber security and the hardening of the communications networks that provide mission-critical information to the energy control centers will require more investigation to enable dealing effectively with the threat.
• Minimizing penetration pathways to critical cyber systems is essential. The use of information/cyber systems makes more complex operation possible but also introduces new vulnerabilities. Any interconnection of the control systems with various corporate business systems, and thus to public networks, adds to the system vulnerability. Stand-alone autonomous systems are ultimately the most secure. Isolation of the critical systems must be the basic principle of cyber security for the power grid.
• Judicious interconnection is unavoidable. Although interconnection with public communication networks should always be avoided, control systems do need data from other systems, and vice versa. For example, energy management systems (EMSs) often need data from neighboring control centers or from market computers. Similarly, some engineering systems need data from the SCADA system or the EMS or from substation control or monitoring equipment. Such interconnections represent security risks and should be designed with care using high-quality security tools and the best available management practices. Firewalls with proper authentication and verification procedures, together with the use of unidirectional data transfer when appropriate, should be utilized.
• Best practices for security provisions always apply. Cybersecurity is part of FERC/ERO mandatory reliability standards. “Basic” security protocols and architecture must be standardized and adopted. SCADA/control system protocols should include elements to assure authentication and integrity. The
BOX 4.1 Addressing Control System Vulnerabilities
An article by Welander (2007) summarizes recent progress and work led by the North American Electric Reliability Council (NERC) in addressing 10 control system vulnerabilities highlighted in 2006 by the Control Systems Security Working Group of NERC (NERC, 2006). The article quotes a NERC official as stating that the 2006 version “’has grown from a simple listing of vulnerabilities in 2004, to include three levels of mitigations for each of the documented vulnerabilities’” (Welander, 2007, p. 38). Excerpts regarding 3 of the 10 listed vulnerabilities are given below:
• Inadequately secured wireless communication (including microwave technologies)
Before installing wireless, it’s important to do a complete assessment to identify the best areas for wireless use and ensure that leakage out of the plant is minimized. Wireless leakage occurs when you have transmitters or wireless-enabled workers walking around with tablet PCs or handheld devices. Those devices may be transmitting in an area outside a plant. (Welander, 2007, p. 42)
On the wireless network side, technologies such as 802.11 b and g are often in place, operating in the 2.4 GHz spectrum. Often they have been deployed without a suitable site survey to determine if coverage is adequate and to evaluate if spurious emissions are limited so that people external to the facility must work hard to find these networks. (Welander, 2007, p. 42)
• Use of a nondedicated communications channel for command and control
[An example of this] would be the case with Internet-based SCADA. This vulnerability also could include inappropriate use of control system network bandwidth for non-control purposes, such as VoIP (voice over Internet Protocol)…. IT [information technology] professionals typically look at application performance, and near real time for control is a foreign concept. Taking 300-500 ms extra to receive e-mail or a Webpage is largely unnoticeable; 300-500 milliseconds for control messages or safety messages could be disastrous. Often, what is an acceptable level of saturation or utilization from an IT perspective can spell disaster for controls. (Welander, 2007, p. 42)
• Unauthenticated command and control data
Not all controllers out there today authenticate who’s making the change and authorize that the change is allowed for that user through the controller. This security step on most control systems is performed at a layer in the control system above the controllers. This leaves the controllers vulnerable, and that’s why defense-in-depth is absolutely required. You’ve got to make sure the controllers are deep down in the security infrastructure, with multiple layers of defense above them. If you’re not doing that, then your controllers are basically wide open on the Web. (Welander, 2007, p. 44)
Mitigation strategies for all 10 of the vulnerabilities range from using software packages to changing corporate culture. The online version of Welander’s article (at http://www.controleng.com/article/CA6433393.html?text=welander) includes the full text of the NERC document (NERC, 2006) with three-tiered strategies for addressing each vulnerability.
process of developing, testing, and applying software security patches, and related upgrades, should be accelerated and requires careful and continuing management attention.
• Substation cyber security requires defense at several levels. Assuring security of communication between a growing multitude of microprocessor-based devices at substations and other distributed systems is a challenge that must be met with various levels of defense. All modern relays and other monitoring equipment have processors, and data capture and communications interfaces, which need to be connected, but this must be done with security as a strict requirement. Minimizing connectivity, requiring/ensuring strict authentication, and conducting regular testing are all important. Although wireless communication usage is increasing for various applications within substations, wireless links should not be used to implement critical control functions.
• Protection against human error is critical. Many controls are still manual and even the automatic control systems require manual testing and maintenance, thus allowing many human interfaces. In addition to limiting access and requiring strict authentication to screen out unauthorized personnel, systems should be hardened against human error. For example, testing equipment (laptops) has been known to have introduced viruses into substation equipment. Hardening
against human error automatically raises the barrier against malicious attack.
• Investment in process and personnel must be a priority. There has been a serious lack of investment in power system infrastructure in recent years, and market-based priorities are unlikely to support strategically increasing security in power systems. Cyber security, like the reliability of the grid, probably has to be mandated by the FERC/ERO process, which usually means that the mandatory standard (i.e., the minimum required) will lag behind best practices. Because cyber security weaknesses tend to provide highly opportunistic windows for would-be attackers, and mandatory standards processes tend to be slow, the industry must continue to look for ways to facilitate rapid and the reliable implementation of security upgrades and patches and to ensure that its personnel are well trained and applying best practices. Simply conforming to the last round of standards will often not be sufficient to provide adequate protection.
AGA (American Gas Association). AGA-12 Cryptographic Protection of SCADA Communications. Available at http://www.gtiservices.org/secu-rity/aga12_wkgdoc_homepg.shtml. Accessed August 2007.
Amin, M. 2000. “Toward Self-Healing Infrastructure Systems.” IEEE Computer Magazine 33(8): 44-53.
Amin, M. 2001. “Toward Self-Healing Energy Infrastructure Systems.” IEEE Computer Applications in Power Magazine 14(1): 20-28.
Amin, M. 2001 and 2002. Special issues on control of complex networks. IEEE Control Systems Magazine 21(6) and 22(1).
Amin, M. 2002. “Security Challenges for the Electricity Infrastructure.” IEEE Computer Magazine 35(4)(Part Supplement): 8-10.
Amin, M. 2003. “North America’s Electricity Infrastructure: Are We Ready for More Perfect Storms?” IEEE Security and Privacy Magazine 1(5): 19-25.
Amin, M. 2004a. “Balancing Market Priorities with Security Issues: Interconnected System Operations and Control Under the Restructured Electricity Enterprise.” IEEE Power and Energy Magazine 2(4): 30-38.
Amin, M. 2004b. “Electricity.” Pp. 116-140 in Digital Infrastructures: Enabling Civil and Environmental Systems Through Information Technology, R. Zimmerman and T.A. Horan, eds. London, U.K.: Routledge.
Amin, M. 2004c. “North American Electricity Infrastructure: System Security, Quality, Reliability, Availability, and Efficiency Challenges and their Societal Impacts.” chapter 2 in National Science Foundation (NSF), Continuing Crises in National Transmission Infrastructure: Impacts and Options for Modernization. Arlington, Va.: NSF.
Amin, M. 2005a. “Energy Infrastructure Defense Systems.” Proceedings of the IEEE 93(5): 861-875.
Amin, M. 2005b. “Scanning the Issue.” Proceedings of the IEEE 93(5): 855-860.
Amin, M. 2005c. Special issue on energy infrastructure defense systems. Proceedings of the IEEE. May.
Amin, M., and C.W. Gellings. 2006. “The North American Power Delivery System: Balancing Market Restructuring and Environmental Economics with Infrastructure Security.” Energy 31(6-7): 967-999.
DHS (U.S. Department of Homeland Security). 2006. “National Infrastructure Protection Plan.” June. Available at http://www.dhs.gov/nipp. Accessed August 2007.
DOE (U.S. Department of Energy). 2002. “National Transmission Grid Study.” Available at http://www.pi.energy.gov/documents/Transmission-Grid.pdf. Accessed August 2007.
DOE. 2003. “Annual Energy Outlook 2003.” Energy Information Administration.
Dy Liacco, T.E. 1967. “The Adaptive Reliability Control System.” IEEE Transactions on Power Apparatus and Systems 86(5): 517-531.
Eisenhauer, J., P. Donnelly, M. Ellis, and M. O’Brien. 2006. “Roadmap to Secure Control Systems in the Energy Sector.” Report prepared by Energetics Incorporated, Columbia, Md., sponsored by the U.S. Department of Energy and the U.S. Department of Homeland Security in collaboration with Natural Resources Canada, January. Available at http://www.controlsystemsroadmap.net/.
EPRI (Electric Power Research Institute). 1999. Electricity Technology Roadmap: 1999 Summary and Synthesis. Technical Report CI-112677-V1. 160 pp. Palo Alto, Calif.: EPRI.
EPRI. 2000. Communication Security Assessment for the United States Electric Utility Infrastructure. EPRI Report 1001174. Palo Alto, Calif.: EPRI.
EPRI. 2001. Electricity Infrastructure Security Assessment. Vol. I-II. Palo Alto, Calif.: EPRI.
EPRI. 2003a. Complex Interactive Networks/Systems Initiative: Final Summary Report—Overview and Summary Final Report for Joint EPRI and U.S. Department of Defense University Research Initiative. Palo Alto, Calif.: EPRI, 155 pp.
EPRI. 2003b. Electricity Technology Roadmap: Synthesis Module on Power Delivery System and Electricity Markets of the Future. Palo Alto, Calif.: EPRI.
EPRI. 2004. Supervisory Control and Data Acquisition (SCADA) Systems Security Guide. EPRI Report 1002604. Palo Alto, Calif.: EPRI. Available at http://www.epri.com.
EPRI. 2005a. Guideline for Securing Control System and Corporate Network Interfaces. EPRI Report 1010714. Palo Alto, Calif.: EPRI. Available at http://www.epri.com.
EPRI. 2005b. “Strategic Insights into Security, Quality, Reliability, and Availability” (co-authors: M. Amin et al.). Report 1008566. Palo Alto, Calif.: EPRI, 128 pp.
Fink, L.H., and K. Carlsen. 1978. “Operating Under Stress and Strain.” IEEE Spectrum 15(March): 48-53.
Gellings, C.W., and K.E. Yeager. 2004. “Transforming the Electric Infrastructure.” Physics Today 57(12): 45-52.
Hauer, F.F., and J.E. Dagle. 1999. Review of Recent Reliability Issues and System Events. Consortium for Electric Reliability Technology Solutions, Transmission Reliability Program, Office of Power Technologies, U.S. DOE, August 30.
House Committee on Energy and Commerce. 2003. Blackout 2003: How Did It Happen and Why? Committee hearing September 3-4, 2003. Available at http://energycommerce.house.gov/reparchives/108/Hearings/09032003hearing1061/print.htm. Accessed August 2007.
Kropp, T. 2006. “System Threats and Vulnerabilities: An EMS and SCADA Security Overview.” IEEE Power and Energy Magazine 4(2): 46-50.
Kundur, P. 1994. Power System Stability and Control. EPRI Power System Engineering Series. New York: McGraw-Hill.
Marburger, J. 2002. Testimony before the House Committee on Science, June 14.
National Science Foundation, Division of Science Resources Statistics. 2003. Research and Development in Industry: 2000. NSF 03-318. Available at http://www.nsf.gov/statistics/nsf03318/pdf/taba19.pdf. Accessed August 2007.
NERC (North American Electric Reliability Council). Undated. Disturbance Analysis Working Group database. Available at http://www.nerc.com/~dawg/. Accessed November 2007.
NERC. 2002. “NERC Security Guidelines for the Electricity Sector.” Available at http://www.esisac.com/library-guidelines.htm. Accessed August 2007.
NERC. 2006. “Top 10 Vulnerabilities of Control Systems and Their Associated Mitigations—2006.” North American Electric Reliability Council, Control Systems Security Working Group, U.S. Department of Energy, National SCADA Test Bed Program, March 16, 8 pp.
President’s Commission. 1997. Critical Foundations: Protecting America’s Infrastructures. Report of the President’s Commission on Critical Infrastructure Protection. Washington, D.C., October.
Samotyj, M., C. Gellings, and M. Amin. 2003. “Power System Infrastructure for a Digital Society: Creating the New Frontiers.” Keynote address. Pp. 1-10 in Proceedings of the CIGRE/IEEE PES International Symposium on Quality and Security of Electric Power Delivery, Montreal, October 7-10.
SNL (Sandia National Laboratories). 2005a. A Reference Model for Control and Automation Systems in Electric Power. SAND2005-1001C. Albuquerque, N.Mex.: Sandia National Laboratories. Available at http://www.sandia.gov/scada/documents/NSTB_Ref_Model_V1_2.pdf. Accessed August 2007.
SNL. 2005b. Framework for SCADA Security Policy. SAND2005-1002. Available at http://www.sandia.gov/scada/documents/sand_2005_1002C.pdf. Accessed August 2007.
US-CERT. 2005. “Control Systems Cyber Security Awareness.” Pittsburgh, Pa.: Carnegie Mellon University, Software Engineering Institute, July 7, 7 pp.
Weiss, Joseph. 2004. “Control Systems Cyber Security—Maintaining the Reliability of the Critical Infrastructure.” Testimony before the House Government Reform Committee’s Subcommittee on Technology, Information Policy, Intergovernmental Relations, and the Census, March 30.
Welander, P. 2007. “10 Control System Security Threats.” Control Engineering 54(4): 38-44. Available at http://www.controleng.com/article/CA6433393.html?text=welander.










