3
Government and Industry Best Practices
The objective of this chapter is to report on and discuss industry and government best practices addressing both evolutionary (deliberate) and revolutionary (rapid) technology development in areas correlated to the findings presented in Chapter 2. Case studies are discussed below, highlighting programs and procedures that have achieved positive outcomes for customers and users. Although every program and process could be further evaluated for failure modes and lessons learned that might be applied to future endeavors, the selected examples instead showcase the elements that clearly illustrate best practices.
BEST PRACTICES
Although creating a perfect technology development process for the United States Air Force may be too lofty a goal, the desired end state is enabling the “Three Rs”—(1) Requirements, (2) Resources, and (3) the Right People—that give process stakeholders the clear path that they need to work together successfully. Under the umbrella of these “Three Rs” are several critical factors, organized below as best practices. The Department of Defense (DoD) acquisition process is an intricate web of policies, organizations, processes, people, and priorities. Only when these forces are operating harmoniously can the process meet warfighter needs efficiently and effectively.
EXAMPLES OF GOVERNMENT BEST PRACTICES
The complexity of the DoD acquisition process can render the process slow and expensive. However, the work flow can be tailored to address situational requirements, as permitted by DoD Instruction 5000.02. In fact, the document’s outlined purpose includes a direct reference to the importance of a tailored approach, authorizing “Milestone Decision Authorities (MDAs) to tailor the regulatory information requirements and acquisition process procedures in this Instruction to achieve cost, schedule, and performance goals.”1 The instruction goes on to recommend areas in which a customized approach can be a critical success factor. In short, the DoD itself now recommends adapting the acquisition process, and success stories have arisen directly from this customized approach.
Joint Improvised Explosive Device Defeat Organization
Improvised explosive devices (IEDs) became an everyday danger to troops deployed in Iraq during 2003, with some DoD estimates of 20 attacks daily even during those early days of Operation Iraqi Freedom.2 This highly lethal and adaptive threat necessitated a more flexible acquisition model to neutralize an enemy with rapidly evolving tactics, techniques, and procedures. As the United States sought to counter this threat using add-on armor plates and other forms of protection on ground vehicles, insurgents became more creative in their emplacement methods as well as their technologies. For example, IEDs emerged with explosively formed penetrators (EFPs), which focus the explosive energy and projectile in a specific direction.3 The immediate need for more robust, powerful IED protection took center stage.
The Joint Improvised Explosive Device Defeat Organization (JIEDDO) was formally established by the Office of the Secretary of Defense (OSD) in 2006, having grown from the Army’s task force formed in 2003 to counter the IED threat in Iraq and Afghanistan.4 The organization’s stated mission is “to rapidly provide Counter
|
1 |
DoD. 2008. Department of Defense Instruction 5000.02. December 8. Available at http://www.dtic.mil/whs/directives/corres/pdf/500002p.pdf. Accessed on January 29, 2011. |
|
2 |
Donald P. Wright, Timothy R. Reese, and the Contemporary Operations Study Team. 2008. On Point II: Transition to the New Campaign, The United States Army in Operation Iraqi Freedom May 2003-January 2005. Fort Leavenworth, Tex.: Combat Studies Institute Press. Available at http://www.globalsecurity.org/military/library/report/2008/onpoint/index.html. Accessed August 6, 2010. |
|
3 |
Information on an explosively formed penetrator warhead is available at http://www.globalsecurity.org/military/systems/munitions/bullets2-shaped-charge.htm. Accessed August 6, 2010. |
|
4 |
More information on the Joint Improvised Explosive Device Defeat Organization is available at https://www.jieddo.dod.mil/about.aspx. Accessed September 2, 2010. |
Improvised Explosive Device capabilities in support of the Combatant Commanders and to enable the defeat of the IED as a weapon of strategic influence.”5
Part of JIEDDO’s success lies in its acquisition model, which is built on the premise that the organization must be as quick and agile as the enemy is. In this case, the enemy makes broad use of commercial, off-the-shelf technologies to rapidly bombard warfighters and civilians with new threats (e.g., IEDs triggered by cordless telephones and garage-door openers). Combining this urgent need with congressional relief on funding constraints enabled timely expenditures on research and development, procurement, and operations and maintenance, without the limitations commonly found in more routine technology development and acquisition. JIEDDO’s tailored procurement process allowed it to respond to joint urgent operational needs (thus bypassing the lengthy Joint Capability Integration and Development System [JCIDS] model), which significantly reduced response time.
JIEDDO also formalized its acquisition model, called the Joint IED Defeat Capability Approval and Acquisition Management Process (JCAAMP), in 2007. Shown in Figure 3-1, the JCAAMP is focused on rapidly delivering new capabilities to the field to defeat emergent technologies like the EFP.6 In addition, JIEDDO outlined a three-pronged approach to focus its efforts—attack the network, train the force, and defeat the device. JCAAMP characteristics include the following: support for flexible points of entry depending on maturity, effective testing and evaluation requirements, continued initiative assessment after initial delivery to warfighters, continuous enforcement of risk reduction, and formal oversight of acquisition during every phase.
Effective technology does not always require high levels of complexity. In 2006, JIEDDO zeroed in on the trigger mechanism for the EFP to reduce its accuracy, using a simple technological solution called Rhino, made of vehicle glow plugs and batteries housed in a munitions can. When extended in front of the lead vehicle in a convoy, this device causes passive infrared-triggered IEDs to detonate prior to the vehicle’s entering the kill zone. With the U.S. Army’s support, JIEDDO tested this capability in the continental United States, then competed the solution for production. By the end of 2008, more than 16,000 Rhino II systems had been produced and deployed under JIEDDO’s JCAAMP funding. Technology enhancements were delivered to the field later through upgrade kits, which included safety and performance improvements. Additional technological upgrades were made to adapt the system for the unique terrain requirements of Afghanistan (Rhino III), and
|
5 |
The mission statement for the Joint Improvised Explosive Device Defeat Organization is available at https://www.jieddo.dod.mil/index.aspx. Accessed August 6, 2010. |
|
6 |
DoD. 2009. Joint Improvised Explosive Device Defeat (JIEDD) Capability Approval and Acquisition Management Process. Joint Improvised Explosive Device Defeat Organization Instruction 5000.01. Washington, D.C.: Department of Defense. Available at https://www.jieddo.dod.mil/content/docs/20091106_JCAAMP_update.pdf. Accessed August 6, 2010. |
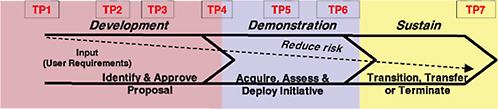
FIGURE 3-1
The Joint Improvised Explosive Device Defeat Organization’s (JIEDDO’s) Capability Approval and Acquisition Management Process acquisition model. NOTE: Pre-TP 1: Potential solutions to published operational or technology capability gaps received by way of the BAA Information Delivery System are adjusted for feasibility. S&T or proofs of concept supporting requirements are considered development efforts and are matured until eligible to proceed to successive TPs. TP 1: Gain approval from the vice director for the proposal to proceed. Complete evaluation of technology merit against operational capability gaps and readiness levels. TP 2: LOO Portfolio Manager approval to proceed to the JIEDDO Requirements, Resources, and Acquisition Board (JR2AB). TP 3: JR2AB recommendation to proceed to Joint Improvised Explosive Device Defeat (JIEDD) Integrated Process Team (JIPT). TP 4: JIPT endorsement and Decision Memorandum signed. TP 5: Decision by vice director to deploy an initiative for employment by operational units. TP 6: Decision to field a proven initiative. Decision to transition, transfer, or terminate (T3) initiative, as appropriate. TP 7: Complete transition or transfer of initiatives to services or agencies; or terminate. SOURCE: Department of Defense. 2009. Joint Improvised Explosive Device Defeat (JIEDD) Capability Approval and Acquisition Management Process. Joint Improvised Explosive Device Defeat Organization Instruction 5000.01. Washington, D.C.: Department of Defense. Available at https://www.jieddo.dod.mil/content/docs/20091106_JCAAMP_update.pdf. Accessed August 6, 2010.
Rhino was transitioned into a program of record.7 As demonstrated by JIEDDO’s successes against a difficult and tightly scoped mission, an institutionalized focus on the flexible, efficient acquisition of technology is critical to achieving results. JIEDDO’s tailored acquisition process allows the right people to provide the right solution at the right time, thus quickly responding to deadly threats.
Capabilities Development for Rapid Transition
As with the JIEDDO example, the U.S. Army’s Capabilities Development for Rapid Transition (CDRT) method is designed to get “capabilities to the Soldier quicker and with less fiscal and schedule risk than through the standard acquisition process.”8 The CDRT process identifies high-potential technologies being used
|
7 |
Joint Improvised Explosive Device Defeat Organization policy on “Defeat the Device” is available at https://www.jieddo.dod.mil/defeat.aspx. Accessed August 6, 2010. |
|
8 |
U.S. Army. 2008. Spiral Technology and Capabilities Development for Rapid Transition to the Army. 2008 U.S. Army Posture Statement. Available at http://www.army.mil/aps/08/information_papers/transform/Spiral_Technology_and_Capabilities.html. Accessed August 6, 2010. |
successfully in theater on a small scale, then assesses their broader applicability. The most promising are selected for recommendation to the Army, either as new programs of record or as accelerations into existing programs.9
With its emphasis on analyzing battlefield trends in order to identify emerging needs, the CRDT is one of three primary technology development approaches used by the Army for technology insertion and technology development. Another approach is in response to an operational needs assessment; through this approach, commanders in the field can identify specific requirements that are then verified and responded to by the Army. Finally, the more traditional approach of ongoing technology development is focused on continuous improvement of warfighter capabilities.10 As expressed by the Army:
The primary weakness of the current acquisition process is that it can take up to seven years to field a required capability…. CDRT significantly reduces the time required to get new technologies into the field, while ensuring critical capabilities are fully documented and supported over time.11
Thus, the CDRT is a critical element in the Army’s multipronged approach to procurement, which provides multiple options while working within the established organizational structure. Because the approach embraces customization from the onset, the Army can drive innovation at the appropriate pace.
Big Safari
Big Safari, an Air Force rapid-acquisition program in existence since the 1950s, is responsible for the rapid acquisition, modification, testing, fielding, and sustainment of selected capabilities as determined by the Assistant Secretary of the Air Force (Acquisition). In 2002, Big Safari took its own steps to rapidly transition critical unmanned aircraft intelligence, surveillance, and reconnaissance capability to warfighters by providing direct sensor data to troops on the ground.12 Big Safari’s success is directly tied to the ability to integrate off-the-shelf technologies in support of urgent operational needs.
|
9 |
Daniel Wolfe, CEO, Universal Solutions International, Inc. 2010. “Remarks to the National Research Council Air Force Preacquisition Technology Development Study Panel.” Presentation to the committee, June 7, 2010. |
|
10 |
U.S. Army. 2008. Spiral Technology and Capabilities Development for Rapid Transition to the Army. 2008 U.S. Army Posture Statement. Available at http://www.army.mil/aps/08/information_papers/transform/Spiral_Technology_and_Capabilities.html. Accessed August 6, 2010. |
|
11 |
Ibid. |
|
12 |
Chris Pocock. 2008. “L-3 Shows Latest, Handheld ROVER Terminal.” Aviation International News, July 14. Available at http://www.ainonline.com/news/single-news-page/article/l-3-shows-latest-handheld-rover-terminal-16649/. Accessed August 6, 2010. |
For example, in January 2002, the Big Safari program director was briefed on a concept that would provide ground troops the capability to receive video feeds from Predator unmanned aircraft in flight. By October, the Remotely Operated Video Enhanced Receiver (ROVER) working group was formed, including members of the U.S. Special Operations Command, the Army’s Special Forces Command, and other government agencies.
In order to meet full system specifications, Special Operations Tactical Video System (SOTVS) transmitters and receivers would have had to be installed on the Predator aircraft. Instead, the Big Safari team traded the fully integrated solution for an 80 percent capability. The team decided that decoupling a receiver from an aircraft would be the quickest way to deploy the system. The modified system with proven Technology Readiness Level (TRL) 7 maturity quickly established a one-way link from Predator aircraft to ground units. In fact, this decision enabled Big Safari to deliver a successful prototype of the ROVER system to the C Company, 3rd Special Forces Group (Airborne), within just 2 weeks.13
Today, this capability is present across the Army in L-3 Communications’ ROVER III, IV, V, and VI systems, as well as AAI Corporation’s One System® Remote Video Terminal and Sierra Nevada Corporation’s (SNC’s) Tacticomp™ sysem. In this case, the existence of an organization dedicated specifically to rapid technology development, and its key decision to incorporate proven and easy-to-integrate technologies to achieve an “80 percent solution,” enabled the team to meet its goals.
FINDING 3-1
Tailored processes can enable rapid technology insertion.
Future Naval Capabilities Process
The United States Navy (USN), including the Marine Corps, adopted the Future Naval Capabilities (FNC) process in 1999, shifting its investment focus from individual technology goals to the most vital future capabilities that can be fielded in 3 to 5 years. This forces the Navy’s near-term science and technology (S&T) efforts to center on delivering maturing technology to acquisition managers for timely incorporation into platforms, weapons, and sensors.14
|
13 |
“The Down Side of a Hack.” January 2010. Available at http://www.strategypage.com/htmw/htecm/articles/20100110.aspx. Accessed August 6, 2010. |
|
14 |
Office of Naval Research (ONR). 2008. ONR Selects 12 to Share $1.2 Million Research Funding Recipients Awarded Seed Money for Specific Promising and Innovative S&T Ideas. Office of Naval Research Press Release. Available at http://www.onr.navy.mil/en/Media-Center/Press-Releases/2008/12-Share-Funding-Award.aspx. Accessed August 6, 2010. |
FNC programs are administered through the Office of Naval Research (ONR), charged in the National Defense Authorization Act of 2001 (Public Law 106-398) with managing “the Navy’s basic, applied and advanced research to foster transition from science and technology to higher levels of research, development, test and evaluation.”15 This structure enables the ONR to fund and manage all phases of S&T development (6.1 through 6.4), and as a result, its experts can see programs through from beginning to end. The ONR executes FNC programs through a vast network of expertise, including hundreds of industry partners as well as numerous universities and nonprofit organizations.16 FNC activities account for roughly 30 percent of the Navy’s S&T budget, or approximately $500 million per year.17
The FNC program underwent restructuring in 2005 to align with leadership’s strategy for enabling capabilities that could be delivered within a 3- to 5-year period, closing known gaps experienced by the warfighter. To accomplish this objective, ONR bundles discrete but interrelated S&T products. Performance and maturity must be quantifiable and meet pre-negotiated exit criteria. Integrated Product Teams (IPTs) are composed of senior leaders, acquisition professionals, and technical personnel who are charged with directing technology development activities.18
The IPTs are overseen by the S&T Corporate Board, which includes the Vice Chief of Naval Operations, the Assistant Secretary of the Navy, and the Assistant Commandant of the Marine Corps. These four-star-level leaders ensure that the most important DoD and naval strategies are reflected in naval S&T priorities.19
This group is supported by the Technology Oversight Group, composed of several two-star Navy and Marine Corps leaders. The group is charged with oversight, integration, and investment decisions across FNC programs, as well as with approving individual FNC programs if they are found to close critical S&T gaps, rather than simply adding a new product into the mix.20 In addition, a Require-
|
15 |
Congressional Record, Senate. June 14, 2000. National Defense Authorization Act for Fiscal Year 2001, Amendment No. 3382. Congressional Record Online via GPO Access. Available at http://frwebgate2.access.gpo.gov/cgi-bin/TEXTgate.cgi?WAISdocID=Z7Q17N/2/1/0&WAISaction=retrieve. |
|
16 |
ONR. 2009. Innovation Newsletter. Arlington, Va.: ONR. Available at http://www.onr.navy.mil/Science-Technology/Directorates/office-innovation/~/media/AE5C1A7063244DFDABF807353421F3D0.ashx. Accessed August 6, 2010. |
|
17 |
USN. 2003. Naval Transformation Roadmap. Available at http://www.navy.mil/navydata/transformation/trans-pg92.html. Accessed September 2, 2010. |
|
18 |
NRC. 2004. 2003 Assessment of the Office of Naval Research’s Marine Corps Science and Technology Program. Washington, D.C.: The National Academies Press. |
|
19 |
Ibid. |
|
20 |
More information on FNC programs is available on the Navy Web site at http://www.navy.mil/navydata/transformation/trans-pg92.html. Accessed August 9, 2010. |
ments IPT, composed of two-star members from several functional disciplines, is responsible for transition resource programming, the preparation of required acquisition documentation, the prioritizing of new start proposals, and the coordination of sea trials.21 As illustrated in Figure 3-2, this robust organizational structure of checks and balances ensures that every program decision is built around cohesion with strategic needs, coordination of efforts, and emphasis on streamlined decision making.
Transition plans are required before an FNC program can be approved, but there exists the flexibility to progress if a project with high transformation potential is brought forward without a clear transitional picture.22 Once approved, TRL 6 maturity is expected within 5 years. Technology Transition Agreements are put in place before a program of record can be established or a specification can be written. These contracts, co-signed by the program manager, the developer, and the military sponsor, describe the FNC products, the level of technical risk, the TRL, the exit criteria, and the transition schedule, enabling the necessary budgeting for program transition and minimizing the risk that valuable technology will fail to mature and be applied (i.e., fall into the Valley of Death).
More so than in the Air Force, ONR S&T managers are held accountable and rewarded for the successful transition of programs from FNCs to full-fledged programs of record. This maintains focus and the motivation to ensure that the fleet’s requirements are understood, to develop enabling capabilities to address any gaps, and to reach the required goal of TRL 6 within 5 years. By way of example, all senior government employees with oversight or direct responsibility for an FNC are required, at their annual review, to declare the percentage of their programs that have transitioned. Their resulting bonuses are related to this success measure.
By strategically managing funding for all phases of S&T development, incorporating the right people at every stage of the process, and charting the course clearly with established time frames, milestones, requirements, and ties to warfighter needs, the Navy has created a culture of accountability and performance with its FNC process.
|
21 |
Available at http://www.onr.navy.mil/en/Science-Technology/Directorates/Transition/Future-Naval-Capabilities-FNC.aspx. Accessed August 9, 2010. |
|
22 |
See http://www.onr.navy.mil/en/Science-Technology/Directorates/Transition/Future-Naval-Capabilities-FNC.aspx. Accessed August 9, 2010. |
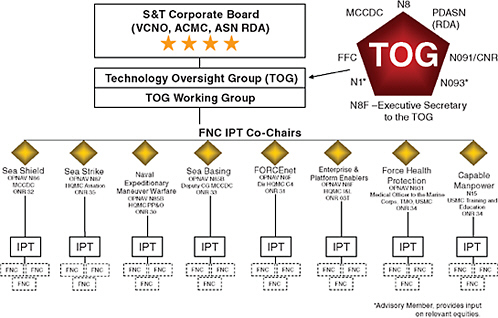
FIGURE 3-2
The organizational structure of Future Naval Capabilities (FNC). SOURCE: Lawrence Schuette, Director, Office of Innovation, Office of Naval Research.
Army S&T Objective Process
The Army also leverages a rigorous process to identify, select, and pursue S&T investments, which generally fall into the categories of basic research, applied research, and advanced technology development.23,24,25 Army Technology Offices (ATOs) are established on the basis of the areas that have been identified as critical
|
23 |
Mary Miller. 2009. Technology Transition—Lessons Learned. Report produced by the Director for Technology, Office of Deputy Assistant Secretary for Research and Technology/Chief Scientist. Washington, D.C.: Department of the Army. |
|
24 |
Department of the Army. 2007. Army Science and Technology Master Plan: Charting the Future of S&T for the Soldier. Report by the Office of Deputy Assistant Secretary of the Army for Research and Technology. Washington, D.C.: Department of the Army. Available at http://www.carlisle.army.mil/dime/documents/JPLD_AY08_Lsn%207_Reading%204_ASTMP.pdf. Accessed September 2, 2010. |
|
25 |
Thomas H. Killion, Deputy Assistant Secretary of the Army for Research and Technology/Chief Scientist. 2010. Army Science & Technology. Slides provided at the National Defense Industrial Association 11th Annual Science and Engineering Technology Conference, Charleston, S.C., April 13, 2010. Available at http://www.dtic.mil/ndia/2010SET/Killion.pdf. Accessed September 2, 2010. |
to outfitting the future force. There are three types of ATOs, each representing a unique S&T development process:
-
ATO-Demonstration (ATO-D)—a program focused on transitioning a specific technology to the warfighter within 2 to 4 years.
-
ATO-Research (ATO-R)—a research-focused activity intended to develop an immature technology further, possibly as a leading step toward a future ATO-D program.
-
ATO-Manufacturing Technology (ATO-M)—a program that centers on reducing cost through improved strategies for production.26,27
Although the three categories of ATO have differing scopes based on program goals and potential barriers to success, all three share a rigidly enforced structure. ATOs must have prescribed milestones and schedules, metrics that are agreed on by all participating parties, and established expectations for technology maturity by the program’s conclusion.28 Figure 3-3 illustrates that ATOs typically require a TRL of 6 or higher; this decreases risk during technology transition.29
Funding is only provided to those ATOs for which the expected results are generally concluded to be reachable within the program’s time frame.30 Because more than 60 percent of the Army’s advanced technology development efforts involve industry from their inception, established expectations provide valuable guidance and infrastructure for all involved parties.31 In addition, Figure 3-4 depicts Army leadership’s involvement with the S&T process to help establish priorities, to allocate funding based on those priorities, and thus to achieve program success.
Every year, the Army Training and Doctrine Command (TRADOC) and Head-
|
26 |
Department of the Army. 2007. Army Science and Technology Master Plan: Charting the Future of S&T for the Soldier. Report by the Office of Deputy Assistant Secretary of the Army for Research and Technology. Washington, D.C.: Department of the Army. Available at http://www.carlisle.army.mil/dime/documents/JPLD_AY08_Lsn%207_Reading%204_ASTMP.pdf. Accessed September 2, 2010. |
|
27 |
Mary Miller. 2009. Technology Transition—Lessons Learned. Report produced by the Director for Technology, Office of Deputy Assistant Secretary for Research and Technology/Chief Scientist. Washington, D.C.: Department of the Army. |
|
28 |
Ibid. |
|
29 |
Department of the Army. 2008. U.S. Army Weapons Systems 2009. New York, N.Y.: Skyhorse Publishing. |
|
30 |
Department of the Army. 2007. Army Science and Technology Master Plan: Charting the Future of S&T for the Soldier. Report by the Office of Deputy Assistant Secretary of the Army for Research and Technology. Washington, D.C.: Department of the Army. Available at http://www.carlisle.army.mil/dime/documents/JPLD_AY08_Lsn%207_Reading%204_ASTMP.pdf. Accessed September 2, 2010. |
|
31 |
Mary Miller. 2009. Technology Transition—Lessons Learned. Report produced by the Director for Technology, Office of Deputy Assistant Secretary for Research and Technology/Chief Scientist. Washington, D.C.: Department of the Army. |
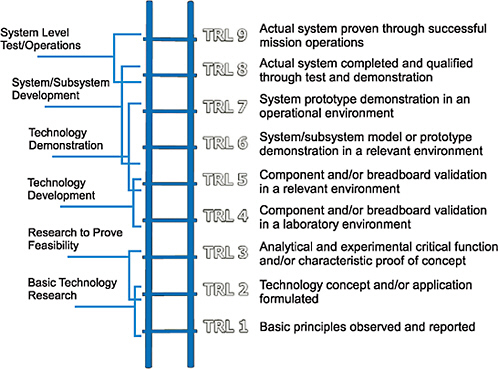
FIGURE 3-3
Department of Defense (DoD) hardware Technology Readiness Levels (TRLs). NOTE: Technology typically transitions out of science and technology and into an acquisition program after TRL 6. SOURCE: Based on information derived from the Department of Defense and the National Aeronautics and Space Administration.
quarters, Department of the Army, meet to review warfighter needs and establish priorities. That information is provided to a group of one-star general officers called the Warfighter Technical Council, which then submits its nominations for new ATOs, as well as revisions to existing ones. From there, nominations are reviewed by two-star general officers, all of whom have S&T oversight responsibilities. Finally, their recommendations are presented to a group of three-star and four-star General Officers called the Army Science and Technology Advisory Group, which ultimately signs off on or terminates the ATOs.32 With this alignment between senior Army leadership, S&T leadership, and the front-line staff responsible for
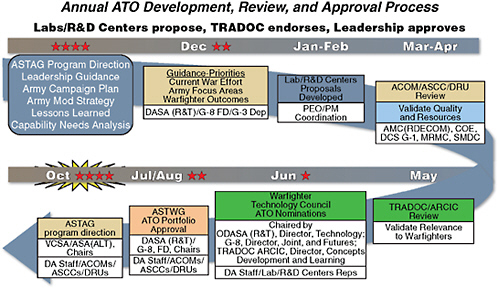
FIGURE 3-4
Army leadership involvement in the Army Technology Office (ATO) process. SOURCE: Mary Miller, Director for Technology, Office of Deputy Assistant Secretary, Department of the Army.
S&T development and transition, the ATO process has been successful, even when measured against the demands of a rapidly evolving battlespace.
FINDING 3-2
Successful technology transition is achieved by the participation of active senior service leadership, consistent priorities, and strong ties between commands responsible for science and technology, systems development and acquisition, and warfighting operations.
Dragon Eye
Responding to the U.S. Navy’s call for more rapid fielding of technologies in the late 1990s, the head of the Naval Research Laboratory’s (NRL’s) Vehicle Research Section recommended seeking out simpler, more mature systems for rapid fielding. Specifically, his approach called for government laboratories to take the lead on prototyping and nailing down specifications, then engaging industry initially for
build-to-print services, followed by spiral system upgrades to support continued capabilities growth.33
These principles were subsequently put into practice when the NRL was asked to provide an unmanned aircraft, dubbed Dragon Eye, with a smaller, less visible signature. Shown in Figure 3-5 is the hand-drawn sketch of the aircraft from an early meeting, outlining the required baseline configuration and proposed project plan.
Building on the fact that the NRL and similar organizations had been researching miniature unmanned air vehicle technologies for some time, Dragon Eye was scheduled in two phases: (1) a 12-month evaluation program including rigorous technical and operational evaluations, and (2) a 36-month development program to complete a comprehensive, mission-capable system design; to demonstrate aircraft prototypes; and to transition the aircraft to production by means of industry build-to-print services. Development was further partitioned to include an 18-month research and development phase including prototyping and the evaluation of industry best practices, followed by an 18-month period of refinement, system evaluation, and transition to production.34
Dragon Eye prototype evaluation began in 2001, and by 2004, production aircraft were deployed in both Iraq and Afghanistan. In its earliest configuration, the Dragon Eye aircraft offered man-portable, short-duration, “over-the-hill” surveillance capability. Incorporating proven, low-cost construction materials and commercially available sensors enabled the technology to be integrated, tested, and fielded expeditiously. This strategy also provided sufficient capabilities to address the user’s basic requirements: for example, adequate visibility in low-light and daylight conditions.
Incremental upgrades allowed additional technologies to be more thoroughly vetted prior to deployment on the aircraft, reducing both risk and cost. For example, enhancements for increased endurance and sensors for day or night operation were not mature enough for deployment at the time of the urgent need for Dragon Eye. Instead, these capabilities were incrementally retrofitted once proven mature. To date, a total of more than 1,300 Dragon Eye aircraft, designated RQ-14A, have been deployed, confirming the merits of this technology development and acquisition approach.35
In the case of Dragon Eye, the customer ensured that system performance requirements were fully defined and understood by all parties at the outset, and
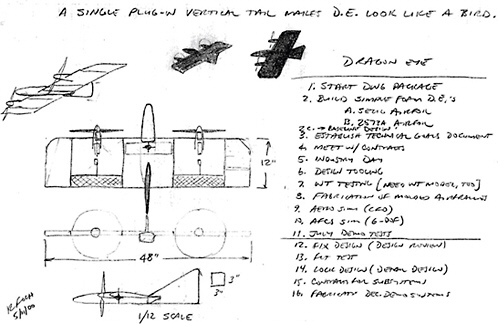
FIGURE 3-5
Original sketch of Dragon Eye. SOURCE: Francis Klemm, Superintendent, Tactical Electronic Warfare Division, Naval Research Laboratory. 2010. “Dragon Eye—A Small UAV: From a Paper Sketch to an Operational System in 30 Months.” Presentation to the committee, June 7, 2010.
ongoing research was leveraged to apply proven mature technology solutions to those requirements. Likewise, spiral technology development was planned to ensure adequate time for system development, prototyping, and testing, as well as to allow evolutionary enhancements to the system post-production. Dragon Eye succeeded because a small, self-contained team of experts matched available mature technology with an urgent operational need to deliver an entire system quickly.
FINDING 3-3
A full understanding of the capabilities and limitations of the technology prior to committing to an acquisition program reduces the inclination to adopt unrealistic requirements.
EXAMPLES OF JOINT GOVERNMENT AND INDUSTRY COOPERATION
The Rapid Reaction Technology Office and the VADER System
Combining the best practices and core capabilities of multiple organizations can contribute to a faster and more effective process. For example, the Rapid Reaction Technology Office (RRTO), the organizational structure of which is shown in Figure 3-6, was established in 2006 under the Director, Defense Research and Engineering (DDR&E), within OSD.36
According to a recent report from the National Research Council (NRC), the small and agile RRTO has a specific charter to explore technologies that meet urgent needs of the warfighter and can be matured within 6 to 18 months for rapid transition into the field.37 Table 3-1 details the RRTO’s goals, by division.
After a given technology is combat proven, the RRTO places the program with the most appropriate government agency for maturing or application, as appropriate. Among the keys to the RRTO’s success are experimentation, risk tolerance, and rigorous testing and prototyping.38
In 2009, the RRTO, in cooperation with the U.S. Department of Homeland Security, Customs and Border Protection, Northrop Grumman Corporation, and the Georgia Tech Research Institute, provided funding for a 5-night demonstration of the Vehicle and Dismount Exploitation Radar (VADER), a radar sensor.39
Integrated onto a Reaper unmanned aircraft owned by Customs and Border Protection, VADER was deployed along a 50-kilometer portion of the U.S. border with Mexico in Arizona.40,41 VADER sensors collected data during the flight and transmitted them to several locations. The collaborative demonstration was a great success: VADER successfully identified suspicious activities during 4 of the 5 nights, and following up on the transmitted data, authorities were able to seize persons
|
36 |
NRC. 2009. Experimentation and Rapid Prototyping in Support of Counterterrorism. Washington, D.C.: The National Academies Press. |
|
37 |
Ibid. |
|
38 |
Ibid. |
|
39 |
Benjamin Riley, Principal Deputy, Rapid Fielding Directorate, Office of the Under Secretary of Defense for Acquisition, Technology, and Logistics, Department of Defense. 2010. “Remarks to the National Research Council Air Force Preacquisition Technology Development Study Panel.” Presentation to the committee, June 8, 2010. |
|
40 |
WTAM News. 2010. “Unmanned Drones to Patrol U.S.-Mexico Border.” WTAM 1100 News, August 31. Available at http://www.wtam.com/cc-common/news/sections/newsarticle.html?feed=104668&article=7543084. Accessed September 3, 2010. |
|
41 |
Canwest News Service. 2009. “Predator Drones Patrolling Canada-U.S. Border.” National Post, June 24. Available at http://www.nationalpost.com/news/canada/toronto/story.html?id=1727873. Accessed September 3, 2010. |
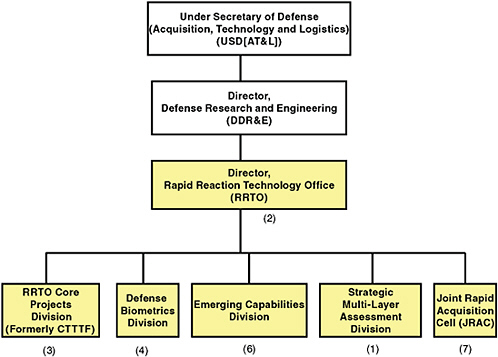
FIGURE 3-6
The organizational structure of the Rapid Reaction Technology Office (RRTO). SOURCE: Reprinted from Figure 2-1, National Research Council. 2009. Experimentation and Rapid Prototyping in Support of Counterterrorism. Washington, D.C.: The National Academies Press.
of interest as well as illegal narcotics.42 In February 2010, Northrop Grumman announced that it had completed additional flight testing of the VADER system. According to the company:
The VADER program is sponsored by the Joint Improvised Explosive Device Defeat Office (JIEDDO) and has been managed by both DARPA [Defense Advanced Research Projects Agency] and Defense Microelectronics Activity (DMEA) in conjunction with Army Intelligence and Information Warfare Directorate. DMEA awarded follow-on contracts to
|
42 |
OSD. 2010. “RDT&E Project Justification: PB 2011.” Available at http://www.dtic.mil/descriptivesum/Y2011/OSD/0605799D8Z_PB_2011.pdf. Accessed September 3, 2010. |
TABLE 3-1 Goals and Focus of the Rapid Reaction Technology Office (RRTO), by Division
|
Project Division |
Current Goals and Focus |
|
Core Projects Division |
Assumed responsibilities, functions, and projects from the RRTO’s predecessor, Combating Terrorism Technology Task Force. Manages ongoing projects from the current areas of emphasis, which include multiple initiatives. |
|
Defense Biometrics Division |
Development of a defense-wide biometric capability that supports identity management, tactical biometrics and forensic applications, and force protection. |
|
Emerging Capabilities Division |
Supports the Joint Capabilities Integration Development System and acquisition processes. Develops prototypes with military utility in targeted areas of technologies and engages in activities for advanced capabilities, leveraging interagency cooperation and coordination. |
|
Strategic Multi-Layer Assessment Division |
Provides planning support to combatant commanders and coordinates with the Joint Staff and Strategic Command to support global mission analysis. |
|
Joint Rapid Acquisition Cell (JRAC) |
Addresses the rapid resolution of Joint Urgent Operational Needs Statements (JUONSs) and immediate warfighter needs. The JRAC monitors the status of validated JUONSs and assists in the resolution of issues that could result in mission failure or casualties. |
|
SOURCE: Adapted from Table 2-1, National Research Council. 2009. Experimentation and Rapid Prototyping in Support of Counterterrorism. Washington, D.C.: The National Academies Press. |
|
Northrop Grumman in January 2009 to improve the capability and support testing by the Army.43
In this case, the resources, expertise, and solutions of multiple organizations, from government, industry, and academia, merged to form a rapid and successful demonstration of a key developing technology. Moreover, the proposed solution applies not only to the homeland security application for which it was initially demonstrated, but to many other missions, domestically and internationally. As the Northrop Grumman announcement notes, “When deployed, VADER will provide U.S. Army ground commanders with real-time accurate Ground Moving Target Indicator data and Synthetic Aperture Radar imagery.”44
DARPA’s Adaptive Execution Office
The leadership of the Defense Advanced Research Projects Agency (DARPA) has created a new office, the Adaptive Execution Office (AEO), which is applying a best practice of “transition ability of DARPA programs.” The AEO was modeled on both the Special Operations Command and Lockheed Martin Corporation’s Advanced Development Programs, where fielding capability rapidly, for exceptional
|
43 |
Northrop Grumman Corporation. 2010. “Northrop Grumman Successfully Demonstrates VADER Dismount Detection.” Northrop Grumman News Release, February 16. Available at http://www.irconnect.com/noc/press/pages/news_releases.html?d=184378. Accessed August 9, 2010. |
|
44 |
Ibid. |
needs, is the norm. The AEO director makes the point that “technology transition is not that hard but it takes passion.” DARPA actively searches for bright, capable people to be program managers, and it expects them to commit to a 4-year tenure. Technology transition needs to be a program strategy “sooner rather than later” and is formalized in a DARPA Program Authorization Document (PAD) addendum. There is no one-size-fits-all technology transition process, no “cookie-cutter” approach—hence the word “adaptive” in the process. The AEO conducts critical self-assessments starting with the underlying science and using measurable metrics. To facilitate technology transition, DARPA then brings in program managers from each service to be bridges to DARPA programs. DARPA becomes an adviser once a program reaches Milestone B. The Air Force can benefit in terms of fielding and cost sharing by participating with DARPA and industry partners to meet operational needs.45
Ground Robotics Consortium
The Ground Robotics Consortium was created by the Joint Ground Robotics Enterprise (JGRE) in the OSD’s office of Land Warfare and Munitions. The consortium provides a unique opportunity for nongovernmental organizations to participate in DoD research planning, producing a plan based on industry expert knowledge of evolving technology. It also allows the services to leverage companies’ independent research and development funding through insights gained as a result of this mutual planning process, and it benefits the services by lowering barriers for small innovative companies to enter into the government acquisition process.
Since its creation in 1998, the Ground Robotics Consortium has attracted 205 members from for-profit and not-for-profit companies and academia. The JGRE provides oversight and guidance, conducts planning and budgeting, manages the acquisition process, coordinates with other organizations, and conducts source selection. The consortium provides liaison among all the members and with the JGRE, participates in the development of plans, and supports the JGRE subcommittees. Significant advantages to the military services include improved technology readiness, increased interoperability, and, most importantly, the accelerated transition of robotic innovations from commercial uses to warfighting applications.46
|
45 |
Ellison Urban, Director, AEO, DARPA. 2010. Site visit by members of the committee, July 27, 2010, Washington, D.C. |
|
46 |
Ellen Purdy, Enterprise Director, Joint Ground Robotics, OUSD(ATL)/PSA/LW&M. 2008. “Ground Robotics. Industry/Academia Day. Government Technical Overview.” Available at www.jointrobotics.com/GRE%20Concept%20Final%20ver3.ppt. Accessed September 3, 2010. |
The National Small Arms Center
Established in 2004, the National Small Arms Center (NSAC) is managed by the Joint Services Small Arms Program Office at the Army’s Armament Research, Development, and Engineering Center (ARDEC) at Picatinny Arsenal in New Jersey. With membership including government laboratories, engineering test sites, firing ranges, production facilities, industry, and academia, the NSAC’s stated mission is “to mobilize the nation’s intellectual and industrial resources to provide the best small arms systems to the nation’s warfighters and law enforcement personnel.”47 As a hub to bring together these various stakeholders, the NSAC serves many roles. It is a center for research in the areas of small arms, providing consultation and training services to its members.48
Among these services are informational sessions, which enable government customers to outline their requirements before industry and academic members in order to set the thought process in motion before requests for proposals are issued. Likewise, industry and academia can meet to discuss customer priorities and explore how they might team to deliver the best ideas. In contrast, interested members can submit white papers on emerging technologies to assess interest by funding organizations in sponsoring additional research.
The NSAC utilizes the flexible Other Transactions Agreement (OTA) as its contracting vehicle for research and development, prototyping, and early production programs. OTAs, typically used for federal grants, are free of Federal Acquisition Regulation (FAR) clauses.49 This enables the organization to draw on the expertise and innovation of nontraditional defense contractors such as small contractors and academic institutions that typically are unable to qualify for FAR-based contracts. In practice, significant collaboration and teaming occur between experienced DoD contractors and these nontraditional members, resulting in shared innovation and technology advancement.
For example, AAI Corporation is an industry member of the NSAC, with a long record of small arms research, development, and production. Its current NSAC programs, launched in 2010 and resulting from proposals attuned to the group’s current interest in the areas of small arms lethality and fire control, include the following:
|
47 |
National Small Arms Center. 2005. Why Join National Small Arms Technology Consortium. Available at http://www.nationalsmallarmscenter.com/public_docs/why_join_EME.ppt. Accessed September 3, 2010. |
|
48 |
Ibid. |
|
49 |
National Small Arms Center. 2010. Public Documents Center. Other Transaction Agreements. Available at http://nationalsmallarmscenter.com/public-documents/C33/. Accessed September 3, 2010. |
-
A combined lethal/nonlethal projectile, which would enable forces to transition seamlessly from a nonlethal projectile for crowd control to a lethal projectile for direct threats;
-
An enhanced fragmentation warhead; and
-
Improved fire control and power management.
Members of the NSAC benefit from continuous information sharing among stakeholders, an emphasis on long-term thinking about warfighter needs and the enabling technologies of the future, and the more flexible OTA contracting vehicle that encourages teaming and creativity.
FINDING 3-4
Collaborative practices between government agencies and industry can lead to successful technology insertion.
Sierra Nevada Corporation and the Commercial Space Sector
Industry succeeds best when it leverages the best skills and expertise available from all sources to feed technology development. In February 2010, Sierra Nevada Corporation’s (SNC’s) Space Systems Group was selected to receive a portion of the $50 million Commercial Crew Development stimulus funding provided by the U.S. government through NASA. The focus of this initiative is incentivizing the private sector to develop and demonstrate human spaceflight capabilities. Scheduled to complete Phase I in December 2010, SNC is responsible for the following:
-
Delivering a program implementation plan for a fast-tracked, streamlined contract vehicle based on payment for performance. This approach is intended to reduce cost for all parties while allowing industry partners to contribute internal research and development dollars to the endeavor.
-
Completing a space vehicle review of its aeroshell tooling solution. This review comprised 40 subsectors, including both mechanical and computer models. SNC passed this review in early 2010.
-
Demonstrating the space vehicle prime motor’s functionality and capacity for reuse. To reduce risk, the contract stipulates that SNC will receive additional funding only if the motor operates as intended.
-
Completing a primary starter test to demonstrate that systems will operate according to program requirements in the unique environment of space.
SNC took several steps to ensure success in the space domain and, ultimately,
success of this program.50 It combined its own knowledge of government procurement with the specialized technical expertise of recent acquisitions to bring the best possible set of capabilities to the customer.51 SNC is also leveraging proven, mature technologies to reduce overall program risk. Its product development model was accepted by NASA and has not only reduced risk but also allowed SNC to meet the first milestones within budget and on time. In this manner, NASA has gained trust in SNC’s capabilities. This example underscores that technical skills, systems integration prowess, and knowledge of the acquisition process are all essential to delivering on customer requirements.52
The Naval Center for Space Technology
The NRL’s Naval Center for Space Technology achieves a synergy with acquisition and industry that could serve as a model for other technology developers. The Naval Center for Space Technology has built a 45-year record of successful space systems development, with a number of impressive accomplishments. Some notable examples of its successful technology development and/or prototyping include the following:
-
Payload Data Management System: A high-risk spacecraft avionics system developed in partnership with industry and subsequently transitioned.
-
TacSat-1 and -2: TacSat-1, a signals intelligence satellite, developed and launched in less than a year, and for less than $15 million.
-
Oceanographic and meteorological payloads.
Keys to the success of the Naval Center for Space Technology include the following:
-
The empowering of small and accountable development teams,
-
The augmenting of government laboratory expertise with industry capabilities, and
-
The sharing of the scientific and technology development resources of a
|
50 |
SNC. 2010. “SNC Receives Largest Award of NASA’s CCDev Competitive Contract.” Sierra Nevada Corporation Press Release. Available at http://www.sncorp.com/news/press/pr10/snc_ccdev_space-news.shtml. Accessed August 10, 2010. |
|
51 |
SNC. 2010. “Sierra Nevada Corporation Selected Under NASA’s Human Space Transportation Program: SNC Dream Chaser™ Space Program to Provide Commercial Crew Capability.” Sierra Nevada Corporation Press Release. Available at http://www.sncorp.com/news/press/pr10/snc_hstp.shtml. Accessed August 10, 2010. |
|
52 |
Mark Sirangelo, Corporate Vice President, Sierra Nevada Corporation, Space Systems Group. 2010. “SNC Space Systems.” Presentation to the committee, July 6, 2010. |
-
highly ranked laboratory—the Johns Hopkins University Applied Physics Laboratory (JHU/APL).
More recently, the Naval Center for Space Technology led the Integrated Government-Industry System Engineering Team (ISET) that developed TacSat-4. The spacecraft was built by the NRL and the JHU/APL, to standards developed collaboratively by the ISET. This collaborative approach represents a best practice for transitioning technology into operational application within tight constraints in terms of cost, schedule, and technical performance.
EXAMPLES OF INDUSTRY BEST PRACTICES
High Technological/Manufacturing/Integration Readiness Levels Pay Off: Ford, Jaguar, and Adaptive Cruise Control
The commercial automotive industry is akin to the defense industry in the sense that the former also must embrace the principles of speed to market and lean, affordable product development. Adaptive cruise control (ACC) was introduced in 1999 by the Ford Motor Company on the Jaguar automobile. ACC development began under the Program for European Traffic with Highest Efficiency and Unprecedented Safety (PROMETHEUS), which was intended to promote collaboration among vehicle manufacturers to garner improvements in traffic flow and safety.53 As the U.S. Department of Transportation’s Federal Highway Administration explains:
PROMETHEUS was started in 1986 and was initiated as part of the EUREKA program, a pan-European initiative aimed at improving the competitive strength of Europe by stimulating development in such areas as information technology, telecommunications, robotics, and transport technology. The project is led by 18 European automobile companies, state authorities, and over 40 research institutions. The budget for the project is over $800 million and the project is scheduled to last seven years. PROMETHEUS is a pre-competitive research project, with the output being a common technological platform to be used by the participating companies once the product development phase begins.54
With this initial development already complete, Ford undertook its own internal technology development program in 1993. By 1995, the team had achieved TRL 5 maturity. Just a year later, ACC was launched formally after being demonstrated
|
53 |
PR Newswire. 2010. “Jaguar Teams with Delphi to Introduce Adaptive Cruise Control.” Available at http://www.prnewswire.co.uk/cgi/news/release?id=24470. Accessed August 9, 2010. |
|
54 |
U.S. Department of Transportation, Federal Highway Administration. 2010. “European ATIS Projects/Systems.” Available at http://www.fhwa.dot.gov/tfhrc/safety/pubs/95153/sec5/body_sec5_01_04.html. Accessed August 10, 2010. |
at TRL 8. In 1999, the company successfully introduced ACC to the marketplace on its Jaguar luxury vehicle.55 In this example, the company harnessed a technology that already had been validated through extensive industry review and integrated with a larger system. The result was a successful product launch in a streamlined time frame.
FINDING 3-5
Decoupling technology maturation and system development has been proven to reduce overall risk dramatically.
There are instances in which the military services have sought to learn from industry in order to implement similar models. Today’s technology transition leaders invoke a collaborative, open atmosphere of innovation akin to the ideas of open-source technology architecture or free-market economics—namely, that free interplay among stakeholders results in a better outcome for all parties. For example, at the University of California, Berkeley, Dr. Henry Chesbrough pioneered the concept of “open innovation,” which encourages both the internal and external sharing of information and ideas as the true basis for success in innovation. The theory further contends that organizations which espouse “closed” innovation will miss crucial opportunities for success because ideas do not fall neatly into their established areas of operation.56
The Innovation Culture at 3M
The U.S. Army’s Tank Automotive Research, Development, and Engineering Center (TARDEC) adopted an exchange program with commercial industry pioneer 3M to identify and harness best practices for technology development and innovation.57
A case study by the William F. Achtmeyer Center for Global Leadership at the Tuck School of Business at Dartmouth describes the 3M culture of “intrapreneurship.” The study notes that nearly 35 percent of 3M’s total sales for the year 2000 came from products introduced within the previous 4 years, showing the organi-
|
55 |
Michael Sullivan, Director, Acquisition and Sourcing Management Team, U.S. Government Accountability Office (GAO). 2010. “Survey of GAO Studies and Findings.” Presentation to the committee, April 21, 2010. |
|
56 |
For additional information on open innovation, see http://openinnovation.haas.berkeley.edu/openinnovation.html. Accessed October 27, 2010. |
|
57 |
Thomas Gehring, Program Manager, 3M Industrial and Transportation Business. 2010. “3M Innovation Story.” Presentation to the committee, June 7, 2010. |
zation’s speed of innovation.58 The company employs a rigorous gate process as a data-driven tool for the mid-program assessment of technology maturity and to drive investment decisions. Figure 3-7 shows a variation of this process developed for the TARDEC.59
Other drivers of innovation include the company’s “15 percent option,” which enables employees to spend up to 15 percent of their work hours pursuing self-driven development projects.60 While the selection of these projects centers on the employee’s interests and technical specialty, they often venture into new technology areas or markets.
Additionally, as with other cases discussed previously in this study, 3M strives to ensure that technology development and product development are never done concurrently. That is, only after a new technology is developed to a high Technology Readiness Level and Manufacturing Readiness Level (MRL) does 3M consider it suitable for incorporation into new product development. For 3M, the simultaneous development of new technology and new products is considered unacceptable.61
The U.S. Army has adopted these lessons from 3M. The TARDEC’s Research Business Group independently benchmarked 3M’s technology roadmapping, project portfolio management, and stage-gate project management processes. These best practices were used to bolster TARDEC’s internal processes, and two pilot projects were selected for evaluation in 2010, with full implementation planned for 2011.62
The importance of evaluating the TRL, MRL, and Integration Readiness Level together as a measure of overall technology maturity was highlighted previously in this report. Indeed, recent changes in DoD Instruction 5000.02 substantially increase the emphasis on technology development and maturation. The pre-systems acquisition phase between Milestones A and B is now focused on reducing technology risk prior to contracting for Engineering and Manufacturing Development. This new direction, as set forth in the Weapon Systems Acquisition Reform Act of 2009 (Public Law 111-23) and in DoD Instruction 5000.02, is fully consistent with
|
58 |
William F. Achtmeyer Center for Global Leadership at the Tuck School of Business at Dartmouth. 2002. 3M Corporation. Available at http://mba.tuck.dartmouth.edu/cgl/downloads/20002_3M.pdf. Accessed August 10, 2010. |
|
59 |
Thomas Gehring, Program Manager, 3M Industrial and Transportation Business. 2010. “3M Innovation Story.” Presentation to the committee, June 7, 2010. |
|
60 |
William F. Achtmeyer Center for Global Leadership at the Tuck School of Business at Dartmouth. 2002. 3M Corporation. Available at http://mba.tuck.dartmouth.edu/cgl/downloads/20002_3M.pdf. Accessed August 10, 2010. |
|
61 |
Thomas Gehring, Program Manager, 3M Industrial and Transportation Business. 2010. “3M Innovation Story.” Presentation to the committee, June 7, 2010. |
|
62 |
Ibid. |
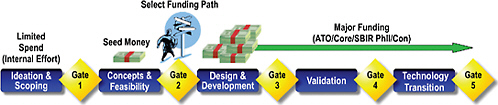
FIGURE 3-7
The stage-gate process of the U.S. Army’s Tank Automotive Research, Development, and Engineering Center (TARDEC). SOURCE: Thomas Gehring, Program Manager, 3M Industrial and Transportation Business; and Heather Molitoris, U.S. Army-TARDEC. 2010. “Technology Development and Innovation at 3M Company.” Presentation to the committee, June 7, 2010.
the best practices of industry innovation leaders like Ford/Jaguar and 3M. Their experience with the astute application of TRL assessment methods shows clearly that the TRL is of critical importance. Assessing readiness level in an objective and analytically rigorous manner is a start. Equally important, though, is maintaining the organizational discipline necessary to follow through on those assessments by not proceeding through decision gates until the required maturity is reached.
FINDING 3-6
Independent, rigorous, analytically based characterization of Technology, Manufacturing, and Integration Readiness Levels will lead to higher confidence and a greater likelihood of successful outcomes.
Technology Networks at Raytheon
Raytheon Company employs a system of technology networks to facilitate communication and collaboration across various locations, businesses, and engineering functional organizations. The technology networks are mandated and supported at the highest levels of the company. In fact, each network is led by one of the company’s senior technologists serving as the chairperson, supported by a council of technologists and a facilitator.
Five technology networks are built around Raytheon’s core technical competencies; these networks are further divided into numerous technology interest groups (TIGs), which can be formed at the initiative of employees, or chartered by the company to address strategic business objectives. Each TIG is supported by a core set of information-sharing tools that are provisioned at the corporate level.
Each technology network hosts an annual symposium offering several technical tracks and tutorials for the 200 to 500 attendees. These symposia bring together
colleagues from multiple locations to discuss common interests and issues, share solutions, and build relationships that facilitate future cooperation. Customers and suppliers are often invited to speak to and to interact with the participants. In addition, 1- to 3-day workshops are conducted with fewer attendees and a more focused technical scope, addressing a topic of strategic or competitive interest to a program, a product line, or the company as a whole. Workshops culminate with the development of recommendations for Raytheon’s approach to the selected topic. Each TIG hosts informative seminars to cover a spectrum of special-interest topics from new technologies and processes to new tools and supplier products, either available internally or elsewhere in industry.
Raytheon’s robust technology networking infrastructure provides a conduit for temporary alignment among people with diverse interests, roles, and responsibilities. When they return to their own locales and work areas, that information is redistributed even further among the workforce—speeding communication, increasing technology reuse, and ultimately delivering greater value to the customer. In addition, this example illustrates that technology can be conceptualized and advanced only to a certain point within one segment of an organization. Once it is opened to the larger organization for debate, evaluation, and validation through peer reviews or gate reviews, the technology is subject to even greater and more rapid opportunities for advancement, as well as successful implementation into a larger variety of applications.
A single example speaks to the power of this kind of networking in a large organization and the direct benefit that accrues to both the business and the customer. A particular product line was about to deliver a command-and-control facility to a customer; in the process of checking to see that all of the requirements had been met, it was discovered that a particular capability had not been certified, and the program chief engineer was uncertain how it should be done. An urgent e-mail was sent out to the appropriate technology network asking for domain experts in this particular topic area. Within 24 hours, six experts had been identified across the company, one of whom was located at the site in need of the help. The appropriate testing and certification were quickly completed, and the facility was delivered on time and in full compliance to a happy customer.
This communication and dissemination example, in which technology developers collaborate effectively to advance the organization’s objectives, would have applicability and value to the science and technology efforts of the Air Force.
CONCLUDING THOUGHTS
Several common threads run through the success stories outlined in this chapter. They include the following: the willingness to accept a good “80 percent solution” in months rather than a perfect answer years in the future; an objective
and accurate assessment of technology maturity; Integrated Product Teams that bring together the right people with best-of-breed technologies and processes; accountability for the forward trajectory of programs; and the dedication of adequate funding. In addition, the principles represented by the “Three Rs”—Requirements, Resources, and the Right People—are applicable to each best practice. Regardless of whether the procurement is evolutionary or revolutionary and regardless of whether it originates within the commercial or the DoD realm, all “Three Rs” continue to emerge as being critical to preacquisition technology development and maturity as well as to ultimate program success.



























