Emerging Science and Technology Fields
Over the next 5-15 years, science, technology, engineering, and mathematics (STEM) resources—people and funding—will be needed by the Department of Defense (DOD) to fill at least four critical needs: (1) creating new capabilities, (2) identifying threats from new capabilities created by potential adversaries, (3) evaluating and advising decision makers on technology to best increase military readiness and functionality, and (4) providing the “intelligent customer,” a knowledgeable interface with industrial partners, to obtain the best technology at reasonable cost. The STEM skills required for these functions include the spectrum of capabilities from basic research to advanced engineering.
The sections below, which are not meant to be exhaustive, identify rapidly evolving areas of science and engineering with a potential for high impact on future DOD operations. STEM personnel will create, recognize, and exploit breakthrough discoveries, engineer prototypes and operational versions for military use, and integrate them into systems controlled by humans. Although it dos not minimize the requirement for continued advancement in traditional militarily important areas such as corrosion and structural fatigue, this chapter focuses on providing examples of a few rapidly expanding areas that can provide far-reaching and pervasive new technologies that will have implications for the STEM skills needed by DOD and the industrial base (Harris, 2011). The committee discusses five cutting-edge science and engineering technological systems that are likely to impact DOD capability, including (1) information technology, (2) autonomous systems, (3) systems biology, (4) innovative materials, and (5) efficient manufacturing. These interdisciplinary technologies require basic research expertise interwoven with engineering innovation to realize the potential for new DOD capabilities. For example, the section on innovative materials discusses applications of nanotechnology; the section on systems biology treats the human-machine interface; and the sections on autonomous systems and systems biology discuss energy.
Information technology is pervasive in DOD systems and has been the enabler of many military capabilities. The potential for increased innovation in capabilities is substantial. A few key areas highlight potential opportunities for advancing critical capabilities: data mining, cybersecurity, cloud computing, and communications technology.
The proliferation of data from sensors and intelligence gathering is overwhelming to humans. The computing activity known as data mining uses statistical and artificial intelligence techniques to extract useful information from databases of ever expanding size, where manual interpretation of data is impossible. The data mining task includes automatic or semiautomatic analysis of data for extraction of information found in operationally relevant patterns. Individuals engaged in data mining require knowledge of computer science, large database management, statistics, and relevant subject matter expertise. For instance, to extract useful associations out of telephone chatter from a foreign battlefield will require knowledge of language and local customs. Data mining has been extensively used in civilian environments, including market analysis, customer behavior, human genetics, spatial analysis of geophysical data, and even in high-energy physics experiments. While the field is expanding very rapidly, each use of machine learning must be grounded in deep understanding of the subject domain.
Network science, in particular dynamic link analysis, is a rapidly developing area related to data mining that is emerging as a distinct, multidisciplinary field. The combinatoric complexity of networks has led to alternative statistical approaches that go beyond static analysis. The Internet and more specialized communications systems are highly dynamic. Understanding the effects of those dynamics will be key to addresing significant problem areas such as needle-in-haystack issues, detection of anomalous behavior, and defending against cyber threats (and developing offensive cyber capabilities).
As the military, and society generally, have become dependent on information systems, communications, and computing, cybersecurity has become a critical capability. Even the cyber vulnerabilities of some civil infrastructure threaten assured operations outside military theaters. Military concerns about cybersecurity are not limited to military-owned infrastructure. It is in the interest of the military that the civilian STEM workforce be knowledgeable about the best information assurance techniques.
Cybersecurity research challenges include ensuring the integrity of data, controlling access to sensitive information, making data accessible when needed, protecting privacy, preventing intrusion, preventing access to data that is unencrypted while it is being processed, and managing degraded information systems to effectively serve priority mission needs. In addition, it is a challenge to know whether combining multiple sources of data increases the sensitivity of the merged data, when, for example, personal identity associated with a record might be inferred.
The cybersecurity STEM workforce will need to apply new approaches in algorithms, hardware and software architectures, and the design and engineering of complex, secure systems. This is particularly complicated by the fact that education and training programs outside the intelligence and military communities address only defensive cybersecurity. It is incumbent on the intelligence community to continue to explore ways to partner with industry and with educational institutions to provide the STEM workforce a strong background in effective approaches to cybersecurity.
A recent development in computing technology is the centralization of storage and heavy-duty computing capabilities in locations separate from the user’s PC. In many ways, this development is reminiscent of the early days of computing, when a user’s desk had only a terminal and all the storage and computing were executed on a mainframe computer located somewhere else in the building. The difference between the old and the new is the communication protocols and bandwidth that are available. Cloud computing, as opposed to using a large central mainframe, relies on sharing common hardware resources such as memory and CPU that are accessed via the Internet.
The driver for cloud computing is the need to get users’ applications loaded and running faster at considerably lower cost, reduced local maintenance, and higher reliability of resources including servers, storage, and networks. With the availability of handheld devices such as smart phones and notepad computers, cloud computing is a grow-
ing part of the IT infrastructure. Cloud computing provides a cost-effective alternative to the existing paradigm of relying on local computing capability.
Both the intelligence community and the military are rapidly adopting cloud infrastructures because of their efficiency, flexibility (especially when scaling compute activities), and more centralized administration. Clouds provide a centralized information infrastructure that offers distributed access, making assured cyber protection even more vital.
Security issues include controlling access to sensitive data, segregating data, insuring privacy and data integrity (including during data processing), and preventing intrusion. The inherent efficiency and flexibility afforded by cloud computing have already resulted in its rapid acceptance in the commercial arena, and the DOD is exploring potential applications.1
Current and future military communications systems rely heavily on mobile communications systems. These systems can integrate individuals, autonomous units, and command nodes. Essential elements are throughput capacity and security. New advances in optical communications are also creating faster logic elements and broad bandwidth communications with reduced power for both fixed and mobile systems. One essential characteristic for national security is that the networks should be fail-safe or fail-soft. To meet this requirement, the networks reconfigure or reassemble autonomously to compensate for a failure in part of the system.
One application of IT is training warfighters in new skills and doctrine. Uncertainty about the types of military engagements the United States is likely to face in the next decade creates an urgent requirement for “anywhere, anytime” training. The readiness of U.S. military and diplomatic establishments to engage in situations that range from major confrontations in the Pacific, to terrorist attacks on the United States or our allies by non-state groups, to missile attacks or dirty bomb assaults on U.S. population centers, requires continuous training of combatant commands and continental United States forces. With the rapid development of worldwide satellite and cellular communications and networks, the infrastructure exists to integrate these assets into a true “anywhere, anytime” training capability.
The appearance and the acceptance of robots on the battlefield and unmanned aerial systems (UASs) in the airspace have engendered new tactical capabilities during the current Middle East conflicts (Economist, 2011). Steady improvements in computing, sensing, networking, and system-integration technologies have offered new capabilities for leveraging human functions with machine functions.
The emergence of autonomous systems as a key component of U.S. military power is another catalyst for integration of technical disciplines, including computing, sensing, communications, materials, and mechanical engineering. To date, however, few fully autonomous systems have become “field ready”; most deployed “autonomous systems” are actually semiautonomous, requiring an operator in the loop.
Most autonomous systems will rely on an interoperable network of manned and unmanned platforms, command and control assets, data analysis, and support functions. However, the current logistical burden associated with deployment must be significantly reduced. The trend toward smaller autonomous systems is in part driven by the potential advantage of their reduced support demands for operation and maintenance.
Autonomous systems benefit from advances in conventional air, sea, ground, and space platforms and related technologies, including propulsion and advanced materials. DOD should maintain continued focus and investment
1 The Defense Advanced Research Projects Agency issued a solicitation in June 2011 on mission-oriented resilient clouds.
in these areas, because they are critical to supporting its missions. This section does not cover advances in those traditional disciplines. Instead, new challenges and opportunities in four areas are presented to advance autonomous systems: (1) modeling and simulation, (2) operational applications, (3) sensor integration, and (4) energy and power.
Modeling and simulation are critical enablers for the design and operation of complex autonomous systems. Multidisciplinary optimization of vehicle, sensor, and network performance in the system-design phase relies on high-fidelity models of the system and its components. Optimization using simulations provides the means to maximize capability and flexibility relative to cost and other constraints; operational employment provides opportunity for innovative applications in a battlefield environment.
Operating autonomous systems on the battlefield in cooperation with manned assets and unpredictable enemy forces would benefit from a clear understanding of the adversary’s behavior. Autonomous systems today typically operate with limited human intervention during operation. Programmed decision-making processes in the autonomous system are constrained in principle, but sensor malfunctions or disruptions to communications links can result in unpredicted responses. Mission-level modeling and simulation of the entire battle space is required to operate safely and consistently for combined manned and unmanned forces.
The range of capabilities of remotely controlled robots and UASs has expanded rapidly in the last few years. These technological advances were often made in response to joint urgent operational needs2 identified by the field commanders. The Navy is developing airborne, surface, and undersea autonomous systems for sensing and surveillance, while the Army is developing land-based robots for explosives countermeasures and materiel transport. A major factor accompanying this progress has been the recognition that many battlefield assignments can be performed more effectively, safely, and often at less cost using robots and UASs.
To date, autonomous systems such as Global Hawk and Predator have demonstrated their effectiveness on today’s battlefield. As future doctrine evolves, autonomous systems will provide innovative capabilities for both the military and homeland security. The next generation of micro UASs, reconnaissance and attack UASs, soldier augmentation robots, and unmanned logistics vehicles will employ sophisticated multispectral sensors, self-organizing networks, swarming technologies, and many other bandwidth-intensive and computationally intensive technologies.
With these new capabilities, the military will likely use unmanned systems more widely in future combat as they demonstrate increasing combat effectiveness. Unmanned platforms may accompany strategic, penetrating, manned attack aircraft. Even air-to-air combat between unmanned fighters is not far beyond the reach of currently available technology. In conjunction with the growing technical capabilities of autonomous systems, DOD will develop new doctrines and concepts of operations as these systems become fully integrated into future missions.
One of the main missions of autonomous vehicles currently deployed is to carry sensors into access-denied or hard-to-reach places. To date, the primary application of sensor suites has been for intelligence, surveillance, and reconnaissance (ISR). Remotely piloted aircraft can patrol a designated airspace continuously for 24 hours or more, taking imagery and other data to identify threats and protect forces. Such ISR support will continue to be a major mission in future conflicts; this particular application will be facilitated by improved data mining technology.
2 DOD maintains a Joint Urgent Operational Needs Fund (JUONF), which “provides resources for urgent and compelling requirements that will prevent critical mission failure or casualties.” See http://comptroller.defense.gov/defbudget/fy2012/budget_justification/pdfs/02_Procurement/JUONF_PB12_PDW_Final.pdf.
Integrating sensors on autonomous systems to support ISR tasks requires a precise understanding of the vehicle’s capabilities and operational needs. Equipping a remotely piloted vehicle (RPV) or unmanned ground vehicle (UGV) with sensor suites that might include cameras or spectrometers, antennas for signal collection and data transmission, GPS, and radar requires building many sensitive systems into a vehicle while ensuring that all of them receive adequate power and cooling and do not interfere with each other. The challenge becomes even greater with emerging micro-RPVs and small ground-based robots. Early examples are already being tested for operations, including ISR, in urban areas.
The skills required to address these ISR, power, and structure challenges fall within existing disciplines. Autonomous systems, however, pack an unusual number of disparate, highly integrated systems into each vehicle. Fully autonomous operation of these vehicles also includes integrating machine logic and smart sensors with an understanding of the physics of the vehicle and its surroundings in order to “see” and navigate through the world. Providing this limited “cognitive” ability to next-generation autonomous systems while continuing to collecting operational sensor data frees system operators from mundane supervision tasks and allows the warfighter to focus on the mission, not on operating the vehicle.
One key advantage of autonomous systems is their long-duration operation, far beyond human endurance. Remotely piloted aircraft can provide a steady watch for a day or more, while small, unmanned ocean “gliders” have operated for weeks at a time. The unblinking pictures of the battlefield provided by these vehicles can offer insights into the operations and tactics of adversaries. Nevertheless, the operational time may be limited by the onboard energy supply, and this problem becomes more acute with decreasing platform size.
Enhancing the duration of continuous autonomous systems requires advances in energy storage and power generation, from higher-capacity batteries to more efficient combustion engines. Commercial industry is pushing for many similar advances. Demand for energy and power solutions will generate innovative solutions. One such area is the move toward a modern electric transmission and distribution system or “smart grid” that is secure, is self-healing, and optimizes assets and operates efficiently (National Research Council, 2009a). The DOD will need a STEM workforce capable of understanding and assessing a range of technologies from multiple fields if it is to remain a smart buyer and integrator.
Improvements in traditional engines, turbines, and other propulsion systems will provide one avenue to increase the duration and mission utility of autonomous systems. Coupled with smart vehicle design, internal combustion engines and turbines are likely to provide power for many of tomorrow’s systems. The use of standard ground and aviation fuels will help autonomous systems integrate into existing logistics chains. For smaller systems, solar cells, fuel cells (including those specified for biofuels), and advanced batteries may provide sufficient power.
Recent efforts in autonomous systems, like DARPA’s ISIS (Figure 2-1) and Vulture programs, seek multi-year endurance (Defense Industry Daily, 2010; Eaton, 2010). Independent operation for years at a time has traditionally been the province of satellites and space probes. Creating aircraft capable of this feat requires self-contained energy systems that can generate enough power from the environment to sustain flight and maneuverability. Multi-year-endurance autonomous systems must harvest and store energy from the environment with systems designed to operate without maintenance or downtime.
Achieving long-duration operation in autonomous systems may also rely on unique propulsion mechanisms and operational concepts. Ocean gliders, for example, ride on currents and vary their buoyancy to achieve controlled forward motion (National Oceanic and Atmospheric Administration, 2009). Rather than simply harvesting energy from the environment to generate electricity, designers can choose to create a vehicle that relies on the unique features of its operating environment for high-efficiency propulsion. Both aerial gliders and airships utilize air currents for propulsion. Hybrid autonomous vehicles that combine mechanical propulsion and gliding are also under development.
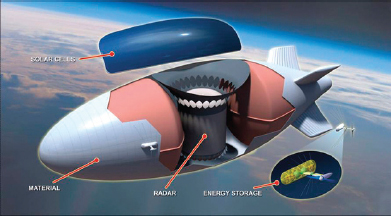
FIGURE 2-1 DARPA ISIS blimp.
SOURCE: DARPA; see http://www.darpa.mil/Our_Work/STO/Programs/Integrated_Sensor_is_Structure_(ISIS).aspx).
Systems biology identifies the interactions among the components of a biological system that give rise to the function and behavior of the system. As a paradigm, systems biology focuses on “how system properties emerge … the pluralism of causes and effects … by observing, through quantitative measures, multiple components simultaneously and by rigorous data integration with mathematical models” (Sauer et al., 2007). The development of a computational model to explain the interactions among many components and to predict the result of changing one or more of the components is critical for predicting the functional consequences. Currently, such models exist but have limited scope and so can be both predictive and verifiable only in the short term; longer-term predictions are difficult to verify and thus engender limited trust. Practically, the field of systems biology uses data from diverse experimental sources and interdisciplinary tools and personnel for characterizing the integration of complex interactions in biological systems.
Among the important consequences of the human genome project was the realization that the function of a living organism could not be explained solely by the genes involved. Other components such as proteins and metabolites are critical in the complex pathways that determine a response at the cell or organism level. Systems biology has particular promise for delivering future technology and solving real problems because of the following underlying assumptions: (1) if we can understand how complex natural systems work, we can learn how to alter specific functions (e.g., pathogenicity, human performance, bioremediation) and (2) if we can learn to alter natural systems, we can create desired functions (biofuel production, biosensing, biomanufacturing/bioprocessing).
For evaluating the potential of systems biology to advance DOD capabilities, the discussion below is presented in three parts: (1) understanding natural systems; (2) modification of natural systems to impart particular capabilities; and (3) utilizing modified natural systems.
Many of the models created to understand the molecular interplay within living organisms have been developed using bacteria because they are single-cell organisms comparatively easily manipulated in the laboratory. An important nonmedical application of systems biology using selected naturally occurring organisms is bioremediation, which uses biological agents, such as bacteria or plants, to remove or neutralize contaminants in polluted
soil or water. Bioremediation, in which biological agents use contaminants as a source of food and energy, often requires enriching the soil and controlling temperature and pH. Many companies have adapted microorganisms for specific soil contaminants. Similar approaches are feasible to produce bacteria that degrade contaminants of military concern, such as explosives, chemical agents, and bio-threat agents.
The tools developed for understanding microorganisms are employed to understand cell-cell interactions and the role of such interactions in much larger multicellular organisms, such as humans. For example, understanding interactions between bacterial cells is critical if we want to regulate the formation of biofilms during marine corrosion or development of dental decay. Naturally evolved cells are used in the open environment to expedite degradation of pollutants or to produce large quantities of enzymes that function at elevated temperatures or in highly acidic conditions. Understanding mammalian cell-cell interactions is critical to increasing the host response to cancer. Increasingly complex models are being developed to explain the biochemistry of inter-species interactions, such as man-bacteria, in order to understand infection and intoxication. Such studies spark hope for new approaches to medical diagnostics based on host response and to therapeutics based on new vaccines or therapeutic blockades of the biochemical cascades triggered by infection. Such knowledge is important for DOD to protect warfighters operating in areas of endemic disease as well as those exposed to biological warfare agents.
As understanding of the interplay between biological processes at the cellular level and function at the organ and whole-animal level increase, we should also be able to improve the evaluation, treatment, and prevention of problems such as traumatic brain injury, post-traumatic stress disorder, and even fatigue. Improved understanding of cognition itself is a systems biology problem amenable to molecular-level understanding. Simulation on a multi-length scale should provide new tools for improving cognition, stress management, decision making, and learning.
Systems biology at the level of the individual human has numerous other implications. In particular, understanding the cognitive process is leading to more effective training, new technologies for the man-machine interface that will be critical for utilizing robots and autonomous systems, improved information processing and decision making, and the possibility of human performance enhancement. Human-systems engineering is an evolving field that optimizes the interface between the human and his or her environment or work processes.
Already, investigators with a systems biology understanding are moving into scales larger than a single human being. Population issues such as obesity, drug addiction, violence, and mental health have a major impact on military recruiting (Burke, 2011). Interactions within populations can be modeled in much the same way as molecules within cells and used to understand phenomena such as pandemics and human health behaviors. Eventually, it may be possible to develop better models for detection of deception and for assessing intent, though models of human behavior must advance substantially before this can be realized.
Modification of Natural Systems to Impart Particular Capabilities
To date, a major impediment to successful genetic modification of organisms has been the fear, if not the realization, of unintended consequences. Cells have complex pathways that can provide alternative mechanisms to help ensure their survival if one function is changed. Systems biology provides a roadmap that identifies a multitude of molecular consequences from a single genetic change, and the tools from a subfield known as synthetic biology allow design of modified cells for a wide range of applications ranging from detection to biomanufacturing to biofuel production.
New motifs for molecular recognition are engineered into cells, enabling recognition of targets as diverse as explosives, chemical agents, pathogens, or metals. In addition, as a consequence of target binding, cells can recognize a vanishingly small amount of the target and generate an easily measurable signal (e.g., color formation). Such cells can be used over extended periods for monitoring the environment or for self-replication to provide a continuous source of miniature sensors.
As an alternative to using intact cells as sensors, cells can be designed to secrete recognition molecules that have been modified to exhibit desirable properties such as high affinity for binding to a target, anchors for incorporation on an optoelectronic surface, storage stability, or intrinsic signal-generating properties. Not only is an understanding of the possibilities for changing the systems biology of the cell required to produce the most useful
molecules, but also a systems engineering understanding of the sensor as a whole and its application is necessary for the design of useful molecules.
Utilization of Modified Natural Systems as Production or Processing Facilities
For centuries, specially selected cells have been used to make beer, bread, and cheese in large quantities. Today, genetically modified cells are used for bioproduction of hormones and other therapeutics. Cells are engineered to produce the particular molecule or function of interest with high efficiency and under the required manufacturing specifications. In addition to food and pharmaceuticals, the cellular production of plastics, oils, and specialty chemicals has already been demonstrated. Neither the cellular production machinery nor the equipment for large-scale operation is as yet cost-effective for most applications.
Bioproduction is among the most important areas for biofuel development. Biofuel technology has been following the rapid advances in basic knowledge of the life sciences. This knowledge is a key to obtaining sustainable and renewable energy sources from domestic resources.
The economics and net energy balance of the ethanol fuel cycle are well understood (National Research Council, 2009b). Multiple strategies are under development to generate ethanol from the fermentation of a broad variety of cellulosic materials. Exciting work shows that altering the genome of carbon-dioxide-fixing algae makes them more efficient in the production of hydrocarbon molecules. A major task for the production of any biofuel is engineering the scale-up of successful laboratory experiments to full-scale production. Economic assessment of resource management, chemical engineering, and life-cycle costs are required at the pilot-plant stage to make reasoned decisions about the technology path to pursue.
Materials science and engineering underpins many technologies critical to DOD. Emerging innovations in materials technologies are interdisciplinary, crossing boundaries between materials science, nanotechnology, biology, chemistry, and physics. This section provides a few examples of materials for energy storage, weapons systems, lightweight structures, photonics, and electronics that have application in expanding military capabilities.
The development of energy-efficient systems and devices for transportation, sensors, and platforms has had, and will continue to have, a broad impact on DOD operational capabilities. Next-generation batteries and fuel cells, for example, will enable remote operational capabilities for longer periods at lower costs and will increase portability, while reducing reliance on petroleum-based fuels (National Research Council, 2003b).
Nanotechnology has created new possibilities for engineering energy-related materials with desirable properties and novel functionalities. Examples include nanowire-based batteries and electrochemical cells exhibiting higher energy densities and improved cycling without degradation; nanoscale materials for catalysis; next-generation thermoelectric materials taking advantage of modifications in phonon transport at the nanoscale; and photovoltaic materials in which the optical and electronic properties of materials and devices better overlap with the solar spectrum to increase efficiency (Atwater and Polman, 2010; Chan et al., 2008; Li and Somorjai, 2010).
The properties of materials at high energy densities are important for high-performance weaponry, propulsion systems, ammunition, and explosives. The design of these systems and their optimization rely on understanding fundamental aspects of materials at high temperature and high pressure and shock, at length scales from atomic to bulk, and at timescales from femtoseconds to seconds. Nanostructures play an important role in these energetic materials as well, for example, through enhancing energy release by increased activation at interfaces. Nanocomposites can similarly provide enhanced reaction rates and mixing on nanometer scales for next-generation propellants and combustion devices at high energy densities with tailored release rates. Examples include nanothermite reactions in metastable intermolecular composites and in nanoscale sol-gels (National Research Council, 2003a).
Advanced structural materials research has focused on the development of high-strength, lightweight materials with many applications to DOD systems. Ductile materials include multifunctional and self-healing materials that can respond or adapt to external conditions and repair local damage such as crack formation without intervention. Other examples of advanced materials include anti-corrosive coatings for thermal protection systems or turbine
engines, nanorobotic self-healing applications (sometimes bioinspired by nature), and nanomaterials for uniforms and textiles capable of shielding soldiers from harsh environmental conditions, including those associated with chemical and biological warfare. Continued R&D is required for advanced synthesis and materials processing, first-principles simulations, and the atomic/nanoscale probing of the first steps in damage/crack/defect formation and of processes at interfaces.
Studies of the interactions between light and materials are relevant to technological applications ranging from information storage and communications technology to directed-energy weapons and advanced imaging. The optical properties of materials figure critically in the development of stealth technology, and meta-materials offer new opportunities for channeling the flow of light, e.g., for cloaking applications across the entire electromagnetic spectrum. Plasmonics similarly enables control of light propagation in materials with applications to guiding light through optoelectronic chips, nanoscale lasing on chips, and high-speed computing with light, exploiting synergies between photonics, plasmonics, and electronics. Directed-energy systems based on next-generation lasers require the development of novel materials with control of the optical, thermodynamic, and electronic properties, enabling development of ultra-low-threshold and ultra-high-intensity systems.
The United States is becoming increasingly dependent on overseas manufacturing for both civilian and military goods. Lower labor costs overseas and the economies of scale achievable through global production and sales provide a substantial cost advantage to manufacturers outside the United States. Following the movement of factories, global companies are increasingly investing in research and development facilities overseas to take advantage of the proximity to their production facilities (Figure 2-2).
For national security reasons, defense production will never move overseas fully; however, at the subsystem and component levels there is already considerable foreign content in most U.S. systems. Overseas manufacturing can introduce two critical risks: (1) hardware vulnerabilities (whether malicious or unintended) can be introduced into the production process; and (2) other countries can limit access to critical products by cutting off supplies.
Economies of scale captured by commercial firms using large overseas manufacturers are of limited value to DOD and industry because defense goods are typically manufactured in small numbers. For example, the annual output of a modest commercial truck factory exceeds the total number of Humvees (i.e., the high mobility multipurpose wheeled vehicle) in the U.S. Army inventory. These small product outputs do not support large capital investments in factories using current automation technology.
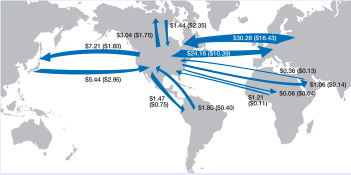
FIGURE 2-2 R&D performed in the United States by U.S. affiliates of foreign companies, by investing region, and R&D performed abroad by foreign affiliates of U.S. multinational corporations, by host region, 1998 and 2008.
NOTE: Figures in billions of current dollars. Figures in parentheses are for 1998.
SOURCE: National Science Board (2012), Figure O-6.
The DOD needs to look to other sources of innovation to improve manufacturing efficiency. Several new technologies offer that opportunity, including (1) direct manufacturing, (2) micromanufacturing, and (3) flexible robotics. A common trend that underlies advances in these three areas is the increasing use of continuous “digital threads” through design, production, and sustainment. For decades, computer-aided design has been the starting point for hardware production. Increasing automation on the production line allows the digital files generated by designers to transfer intact and electronically to manufacturing, ensuring a close agreement between as-designed and as-built products. The expansion and unification of IT systems in defense companies extends this digital thread throughout the product’s life cycle. Designers, production workers, and maintainers can now use a single copy of specifications and plans, preventing discrepancies and eliminating waste associated with creating and archiving numerous copies of the same basic information.
One of the central challenges to building a STEM workforce that can continue to develop and incorporate these advances is the decline in U.S. manufacturing employment. While manufacturing advances may ultimately bring production facilities back to the United States, it is reasonable to expect that future manufacturing innovations will come from overseas universities and businesses that are closer to factories. The DOD will need to demonstrate a commitment to the U.S. industrial base and to education in manufacturing and industrial engineering to develop a workforce capable of realizing the value of these innovations.
Rapid direct manufacturing processes enable the production of parts from the ground up, adding new material from scratch in a step-by-step process instead of starting with a solid block and machining some of the material away. This technology, also called 3-D printing, has been used since the 1980s to produce prototype parts with accurate shapes but without durability owing to the plastic materials utilized. Based on recent advances, direct manufacturing processes can now use a dramatically expanded palette of materials. Production parts for aircraft and other complex systems, not just prototypes, are being made today with such processes. Metals and ceramics in addition to the traditional plastics offer an expaned range of material options.
Making parts directly reduces the waste associated with cutting and machining and avoids the long lead times required for cast metal parts. In addition, direct manufacturing increases the efficiency of small production facilities because it requires much less investment in tooling. For DOD systems with low production volumes, direct manufacturing offers a significant change in production efficiency and cost reduction.
The advent of microelectromechanical systems (MEMS) in the 1980s has resulted in diverse defense applications, from accelerometers to radio-frequency (RF) electronics, cameras, and communication devices. MEMS components reduce size, weight, and power requirements. MEMS are produced using process technologies developed for the semiconductor industry. As a result, unit prices can be low despite the complexity of the systems because the cost of the production facility is shared by other, high-volume electronic components.
MEMS and similar emerging devices at the nanoscale offer a unique opportunity for DOD (Pomrenke, 1998). Realizing needed functionality in a microdevice can often be cheaper than producing it from discrete components because all of the manufacturing steps are automated. Even for relatively low-volume parts, DOD is taking advantage of fully capitalized commercial production facilities and continued advances in manufacturing efficiency and quality, driven by the needs of the global semiconductor industry.
Traditional industrial robots are a feature of highly automated, large-scale factories around the world today. Such robots perform highly specialized tasks. At best, changing the robotic task requires substantial reprogramming and testing. At worst, changing the task requires scrapping the entire robot.
Such conventional robotic solutions are unsuitable for most defense manufacturing, in which production vol-
umes are not large enough to justify the investment. Advances in machine vision, control systems, actuators, and the man-machine interface offer the capability to create flexible industrial robots that perform a variety of tasks. Rather than relying on parts coming down an assembly line in exactly the same place each time, an advanced, flexible robot would sense the incoming part and assess what to do with it. Flexible robots are readily reprogrammed to accommodate design or product changes, and to work alongside humans in the same way that autonomous systems operate with manned platforms on the battlefield.
Flexible robotics is on the horizon and is poised to change the design of factories. A one-time investment in advanced robots would be recouped over generations of products, bringing automated production to complex, low-volume defense hardware. DOD investments in manufacturing technology can drive this field, and an educated workforce will bring it to fruition.
STEM SKILLS RELEVANT TO THE FIVE AREAS
A requirement for expertise in information technology permeates all of the cutting-edge technology examples discussed in this chapter. Much of the innovation in information technology is occurring outside the national security community. In areas such as cloud computing and communication technologies, a particular focus on cybersecurity is necessary. The U.S. educational system is training individuals capable of creating new communications and computing strategies; however, the demand from the civilian economy is quite large, and it is not clear that DOD has the financial flexibility to compete for the highest-quality individuals in this area.
In addressing DOD skill needs for other information technology areas, both the DOD and defense contractors require teams of scientists and engineers with advanced knowledge in a range of fields plus the ability to integrate new information from those fields. For instance, applications of data mining may require individuals who are trained in computer science, data mining, linguistics, statistical analysis, cultural anthropology, and optical physics. Machine-assisted decision making is especially critical for DOD operations; critical skills required here are found in computer science, programming languages, and linguistics. Machine translation of languages requires not only expertise in software and linguistics, but also sophisticated cognizance of the current culture, and likely subculture, of those communicating in the language.
Shortages of specialists in cybersecurity have been noted by other analyses, which have estimated that thousands more offensive cyber warfare professionals may be needed, starting from a base level today of roughly 1,000 nationwide (Center for Strategic and International Studies, 2010). Further, US CYBERCOM notes it would take 18 months to train any new hires to the required level of competency. Citing concerns about offensive cyber capability in particular, Congress has recommended that DOD reorganize its current network structure to free up professionals who are otherwise serving as administrators of the numerous networks and 15,000 subnetworks (Brannen and Fryer-Biggs, 2012; Senate Committee on Armed Services, 2012).
The employment of autonomous systems by DOD will require a wide range of STEM skills. Universities today are well equipped to teach computer science, physics, mathematics, and other skills necessary for the continued development of modeling and simulation expertise. The film and video game industries are ensuring both a steady supply of students and robust competition for their talents; well-trained, talented individuals can also be attracted to work on DOD problems.
Ensuring robust communications links to control and supervise autonomous systems, providing sufficient bandwidth for desired utilization of the data they generate, and making available the computing power needed to utilize the systems’ capabilities require significant advances in technology. The challenges cut across traditional disciplines, from electrical engineering and computer science to materials and optics, and even to biology for the design of control systems and models for efficient movement. The growth of bioengineering and research departments devoted to biologically inspired systems has spurred the development of computing and control systems that can manage large swarms of vehicles: the robotic equivalent of ants and bees. DOD support can encourage the growth of these and other similar initiatives to develop a robust, multidisciplinary STEM workforce to support command, control, communications, and computing (C4).
STEM education in traditional aerospace, mechanical, and electrical engineering disciplines will have to evolve to prepare students for developing multidisciplinary systems. The skills needed to address the critical problem of
controlling autonomous vehicles lie at the intersection of physics, biology, information, engineering, systems, and human factors. Vehicle navigation competitions like DARPA’s Grand Challenge have inspired the formation of multi-disciplinary teams to tackle these challenges (Markoff, 2007). Making autonomous vehicles energy efficient requires a multidisciplinary STEM workforce that can integrate oceanography, atmospheric science, biology, and other fields into vehicle design.
The STEM disciplines that would be central to systems biology applications such as biofuels production and bioremediation are chemical, mechanical and bioengineering; chemistry; and the biological sciences. Most of the effort in these areas will be cross-disciplinary. There does not appear to be an urgent requirement in DOD to address site remediation, but many government installations require long-term remediation of their environmentally impacted facilities. The broader application of approaches pioneered in systems biology to model and predict the responses of natural systems, including human cultures, progression of epidemics, and impact of infrastructure changes, requires teaming of information technologists, economists, and social scientists along with life scientists and engineers.
Manufacturing approaches that meet DOD requirements also require cross-disciplinary STEM talents. General needs can be fulfilled by traditional education in mechanical engineering, MEMS, 3-D printing, automated design, and materials. Cross-disciplinary improvements will address economic analyses (such as life-cycle cost projections), energy minimization, robotics, man-machine interfaces, and, almost certainly, systems engineering for both the potential products and the manufacturing systems.
Previous studies have stressed the importance of systems engineers with domain-specific knowledge who are capable of comprehending and managing all of a system’s components and their interactions, and who are responsible for the design, manufacture, and operation of complex systems. Until the 1990s, government teams were involved in the front-end part of the total systems engineering process (i.e., the preplanning process); for example, the Air Force Systems Command included a structured organization with this function. Since that time, however, there has been an erosion of this embedded capability (National Research Council, 2008).
Other declines in organic STEM capacity have been documented at DOD. Following the so-called peace dividend of the 1990s, the size of the acquisition workforce declined in tandem with the procurement budget. However, when the latter increased sharply in the early 2000s, there was not a concomitant increase in the number of acquisition workers. One side effect of this decline has been that responsibility for systems engineering and integration has moved to industry, with at least one report calling for an increase in the quality of the DOD acquisition workforce (Defense Science Board, 2009). A further example: until 1998, the DOD budget included category 6.3B for systems advanced development that supported rapid prototyping programs (National Research Council, 2001).
STEM personnel are required for a wide variety of DOD R&D, acquisition, and operations. Advances in DOD capabilities in information technology, microelectronics, nanomaterials, systems biology, and direct manufacturing are critical to creating effective and affordable military systems. The potential for autonomous systems, micro-scale systems, efficient energy supplies, and improved human performance will demand input from a variety of STEM disciplines.
Finding 2-1. Advances in the technology areas relevant for future DOD capabilities, such as those described above, require knowledge from multiple disciplines. Most overlap with the commercial sphere, making DOD simply another competitor to attract high-tech talent. Teams of dedicated individuals with different knowledge bases should work together to apply cutting-edge science and engineering to solve DOD problems.
Recommendation 2-1. The STEM workforce needs training for cross-disciplinary teamwork. DOD should encourage interdisciplinary collaborations at all career stages in both academic and government laboratories through support of interdisciplinary projects, academic and on-the-job learning opportunities, and career rewards for interdisciplinary endeavors.
Finding 2-2. Transition of laboratory science and technology to deployment in DOD operations requires competent systems engineering as well as expertise in component engineering. The expected progression from graduate scientist or engineer to system engineer usually takes several years of increasing exposure to simulation and modeling, materials optimization, control and communications software development, and field testing. Today, universities often provide opportunities for undergraduate research, interdisciplinary problem solving, prototyping projects, and formal courses on system engineering. As a result, STEM graduates from many universities have some hands-on experience in cross-disciplinary projects and course work in system engineering. However, systems engineering at the scale required is performed entirely by DOD and its contractors. This understanding of systems engineering is particularly important for efficient military acquisition and preparedness for both DOD contracting and the industry responding to the government requirements.
Recommendation 2-2. The DOD should reassemble government teams to do preliminary system engineering— including affordability, capability, and sustainability—and program structuring so that the government focus is on relevant requirements when interacting with the defense industry. The industry teams also require system engineering and integration teams that can efficiently respond to the government’s requirements.
Finding 2-3. Uncertainty as to the types of military engagements the United States is likely to face in the next decade creates an urgent requirement for “anywhere, anytime” training. With the rapid development of worldwide satellite and cellular communication networks, ISR (intelligence, surveillance, reconnaissance) capabilities, and modeling and simulation, the infrastructure exists to integrate these assets into a true “anywhere, anytime” training capability.
Recommendation 2-3. The DOD should initiate a major program to secure the necessary STEM-qualified government teams to deliver effective, worldwide training and to leverage information technology and ISR infrastructure to meet a mandate of “anywhere, anytime” training.
Finding 2-4. Innovative materials broadly underlie critical technology for the DOD and are essential for maintaining a technological edge. The most recent innovations in materials science are cross-disciplinary and range from fundamental science to use-inspired research and development. An emphasis by DOD on STEM education in materials science and related areas (e.g., nanotechnology, systems biology, energetics, photonics) can seed the development of new capabilities as well as new solutions to old problems.
Recommendation 2-4. The DOD should maintain expertise in materials science as broadly defined. This can be achieved in part by leveraging existing programs within DOD labs as well as at universities, and by increasing the interaction between the two. Making DOD careers attractive to the STEM workforce requires emphasis and placement of DOD resources in the entire pipeline from basic research and discovery science to applied research and product development.
Finding 2-5. The United States increasingly relies on information technologies to support its warfighters. The support provided by information technology improves the capability to respond effectively to the changing mix of challenges. Data collection, data translation, data mining, cybersecurity, and data manipulation for correct interpretation of increasing amounts of information require expertise not only in the understanding of physical sensors and advanced computing software and platforms but also expertise in linguistics and a deep understanding of local cultural nuances. Consistent with the most recent national security policy documents, the United States especially needs to increase its ability to operate in the Asian/Pacific theater. There is evidence, however, of a nationwide shortage of cybersecurity professionals with appropriate security clearances.
Recommendation 2-5. The DOD should pay special attention to the need for multidisciplinary STEM personnel to support the information technology infrastructure for defense. While individuals are being trained at universities
in various specific disciplines, few individuals are trained with multidisciplinary capabilities. DOD should explore the possibility of developing multidisciplinary training in-house or in targeted university programs.
Finding 2-6. Areas of near-term technological focus with relevance to DOD’s mission include the following: advanced robotics and autonomous systems; intelligence collection; cyber warfare (defensive and offensive); human-machine interactions on human terms; means to detect and neutralize biothreats; military applications of the biosciences (systems biology, biosensors, etc.); military applications of the information sciences; and nanotechnology (for innovative materials and other applications).
Atwater, H.A., and A. Polman. 2010. Plasmonics for improved photovoltaic devices. Nature Materials 9(3):205-213.
Brannen, K., and Z. Fryer-Biggs. 2012. U.S. short on offensive cyber experts. Defense News, July 2.
Burke, D. 2011. Emerging Science and Technology in the Life Sciences. Presentation to the Workshop on STEM Workforce Needs for the U.S. DOD and the U.S. Defense Industrial Base, August 1, Rosslyn, Va.
Center for Strategic and International Studies (CSIS). 2010. A Human Capital Crisis in Cybersecurity. Washington, D.C.: CSIS.
Chan, C.K., H.L. Peng, G. Liu, K. McIlwrath, X.F. Zhang, R.A. Huggins, and Y. Cui. 2008. High-performance lithium battery anodes using silicon nanowires. Nature Nanotechnology 3(1):31-35.
Defense Industry Daily. 2010. DARPA’s Vulture: What goes up, needn’t come down. Defense Industry Daily. Available at http://www.defenseindustrydaily.com/DARPAs-Vulture-What-Goes-Up-Neednt-Come-Down-04852 (accessed June 6, 2012).
Defense Science Board. 2009. Creating an Effective National Security Industrial Base for the 21st Century: An Action Plan to Address the Coming Crisis. Arlington, Va.: U.S. Department of Defense.
Eaton, K. 2010. DARPA’s Smart Blimp: Mysterious, Hovering Future of Battlefield Surveillance. Available at http://www.fastcompany.com/1589776/isis-airborne-radar-defense-surveillance-unmanned-airship-blimp (accessed June 6, 2012).
Economist, The. 2011. Flight of the drones. The Economist, October 8.
Harris, W. 2011. Presentation to the Workshop on STEM Needs for the U.S. Department of Defense and the U.S. Defense Industrial Base, August 2, Rosslyn, Va.
Li, Y.M., and G.A. Somorjai. 2010. Nanoscale advances in catalysis and energy applications. Nano Letters 10(7):2289-2295.
Markoff, J. 2007. Crashes and traffic jams in military test of robotic vehicles. New York Times, November 5.
National Oceanic and Atmospheric Administration. 2009. Ocean Glider Set to Attempt Atlantic Crossing. Available at http://oceanservice.noaa.gov/news/weeklynews/apr09/glider.html (accessed February 2, 2012).
National Research Council. 2001. Review of the U.S. Department of Defense Air, Space, and Supporting Information Systems Science and Technology Program. Washington, D.C.: National Academy Press.
National Research Council. 2003a. Frontiers in High-Energy-Density Physics: The X-Games of Contemporary Science. Washington, D.C.: The National Academies Press.
National Research Council. 2003b. Meeting the Energy Needs of Future Warriors. Washington, D.C.: The National Academies Press.
National Research Council. 2008. Pre-Milestone A and Early Phase Systems Engineering. Washington, D.C.: The National Academies Press.
National Research Council. 2009a. America’s Energy Future: Technology and Transformation. Washington, D.C.: The National Academies Press.
National Research Council. 2009b. Liquid Transportation Fuels from Coal and Biomass. Washington, D.C.: The National Academies Press.
National Science Board. 2012. Science and Engineering Indicators. Arlington, Va.: National Science Foundation.
Pomrenke, G. 1998. Defense Advanced Research Projects Agency Ultra Electronics: Ultra Dense, Ultra Fast Computing Components. Available at http://www.wtec.org/loyola/nano/us_r_n_d/03_24.htm (accessed June 6, 2006).
Sauer, U., M. Heinemann, and N. Zamboni. 2007. Genetics—Getting closer to the whole picture. Science 316(5824):550-551.
Senate Committee on Armed Services. 2012. Report to Accompany S. 2354: National Defense Authorization Act for Fiscal Year 2013 (Report 112-173). Washington, D.C.: U.S. Government Printing Office.














