4
Data and Databases
INTRODUCTION
Basic information on a variety of spatial and nonspatial attributes of the physiographic setting of the area to be evaluated is required to assess ground water vulnerability to contamination. Although the types of data required depend on the specific technique employed, some combination of information will be needed on natural factors, such as topography, soils, weather, hydrogeology, and land cover; and the human factors such as land use and management.
To date most vulnerability assessments have used existing data sources, and have rarely involved new data collection efforts in support of the vulnerability assessment. Since the data available for a particular region are often meager, the attributes of interest are often derived by some type of interpolation of information collected at sparsely distributed locations, sometimes from outside the region of interest, and frequently using data collected at a different spatial scale.
As discussed in Chapter 3, the reliability of an assessment depends on the validity of the approach for the particular application and the quality and currency of the data used. Thus, even if the vulnerability technique selected is valid, the use of poor quality data will introduce uncertainty into the results of the assessment. Uncertainties resulting from data quality problems can be reduced by insuring that the variability in the attributes (e.g., physical features and management practices) over the area is accurately
reflected in the interpolated values of the spatial and nonspatial attributes.
Dozier (1992) points out the synergism between model development—that is, for the purposes of this discussion, assessment techniques—and data collection efforts. He observes that ''Modeling and data collection each drive and direct each other. Better models illuminate the type and quantity of data that are required to test hypotheses. Better data, in turn, permit better and more complete models and new hypotheses." Most research efforts to date have been concerned primarily with the representation of environmental processes involved in contaminant transport and transformations. Considerable progress has been made in development of increasingly sophisticated simulation models. However, less attention has been paid to collection, entry, and management of the data required to estimate the model inputs at the appropriate spatial/temporal scales. The need for appropriate computing environments (i.e., integration of data bases, model computations, display of model outputs) needed in vulnerability assessments has also received little attention. These limitations have resulted in models (or techniques) that may describe relevant processes at a local scale (e.g., field plots), but are impractical to implement at larger spatial scales (e.g., watersheds, regional, national). On the other hand, paucity of data and a lack of understanding of the relevant processes at the requisite spatial and temporal resolution has led to development of models or techniques that may not be appropriate for larger scales at which vulnerability assessments are being conducted.
Since public funds are limited, many federal agencies currently are interested more in maintaining and improving the usefulness, accuracy, and availability of existing databases than in embarking on new programs of data collection. This chapter reviews the status of existing information, and describes several databases, their availability, and their use in ground water vulnerability assessments. The focus here is on federally developed and managed databases, with some reference to state and local databases. Although many state and local databases may be valuable in helping to assess the vulnerability of ground water to contamination for state, county, and watershed areas, no comprehensive listing of state geographic databases exists. The lack of this information makes it impractical for this committee to specifically cite or assess state and local databases. Appendix A contains a listing of sources of digital resource databases.
Federal Data Management Activities
Multiple federal agencies collect and use spatially-referenced attribute and nonattribute data required for vulnerability assessments. Over the past several decades, many scientists with diverse scientific backgrounds were
involved in collecting these data for a variety of intended uses. Integration of such diverse databases into an effective and compatible data and information management system is not a trivial task.
In 1982, the General Accounting Office reported concerns that federal agencies involved in digital cartographic data collection were collecting data without regard to the need for standards, were duplicating each others' efforts, and were not coordinating their efforts (GAO 1982). In 1983, the Office of Management and Budget (OMB) established the Federal Interagency Coordination Committee on Digital Cartography (FICCDC). The primary duties of the committee were to facilitate exchange of cartographic data, coordinate activities, develop data standards, determine requirements for data, and report to OMB annually.
Through the 1980s, the federal government's, as well as the nation's, use of geographic information systems and demand for other categories of digital spatial data grew. The OMB and FICCDC recognized this trend, and developed a revised OMB Circular A-16 (OMB 1990) to establish a process to foster the development of a national spatial framework for an information-based society. This framework will include the participation of federal, state, and local governments, and the private sector.
The circular established the Federal Geographic Data Committee (FGDC) to promote the coordinated development, use, sharing, and dissemination of surveying, mapping, and related spatial data. The FGDC's responsibilities include interagency coordination of data collection and sharing, and the establishment of federal standards for geographic data exchange, content, and quality. Fourteen departments and independent agencies are members of the FGDC, and additional agencies participate on FGDC subcommittees and working groups.
The circular also assigns government-wide coordination leadership responsibilities to federal departments for data categories. Agencies within the lead departments chair FGDC subcommittees that assist in coordination and development of national data standards with the participation of the communities interested in those data categories. The categories and lead agencies are listed in Table 4.1. Additional data categories will be added as the need and opportunity arise. In addition, the FGDC works with the Interagency Advisory Committee on Water Data for coordinate spatial water data issues.
The exchange of data between different computer systems is often difficult and sometimes impossible. Thus, the FICCDC and FGDC, in cooperation with the American Congress on Surveying and Mapping, developed a standard for exchange of geographic data (Mollering 1988), which has since been adopted as a federal information processing standard (FIPS 173) (NIST 1992). The Spatial Data Transfer Standard is described in Box 4.1.
Circular A-16 sets a long range objective of developing an integrated
TABLE 4.1 Federal Geographic Data Coordination Responsibilities (OMB 1990)
|
Geographic Data Category |
Lead Agency |
|
Base Cartographic |
U.S. Geological Survey, Department of the Interior |
|
Bathymetric |
Coast and Geodetic Survey, Department of Commerce |
|
Cadastral |
Bureau of Land Management, Department of the Interior |
|
Cultural and Demographic |
Census Bureau, Department of Commerce |
|
Elevation |
U.S. Geological Survey, Department of the Interior |
|
Geodetic |
National Oceanic and Atmospheric Administration, Department of Commerce |
|
Geologic |
U.S. Geological Survey, Department of the Interior |
|
Ground Transportation |
Federal Highway Administration, Department of Transportation |
|
International Boundaries |
Office of the Geographer, Department of State |
|
Soils |
Soil Conservation Service, Department of Agriculture |
|
Vegetation |
U.S. Forest Service, Department of Agriculture |
|
Wetlands |
U.S. Fish and Wildlife Service, Department of the Interior |
|
Box 4.1 The Spatial Data Transfer Standard The Spatial Data Transfer Standard (SDTS) (NIST 1992), also known as the Federal Information Processing Standard 173, is used to transfer spatial data and their attributes between two noncommunicating systems. The standard consists of three parts which together provide criteria for data exchange, including quality and content. Part I, logical specifications, provides the fundamental definition of digital spatial data, specifies the logical file structure for the data, and describes requirements for reporting data quality. The quality report requires five basic categories of information: data lineage (i.e., history and source of data, how they were compiled and digitized, etc.), positional accuracy, attribute accuracy, logical consistency, and completeness. Part II, spatial features, defines common geographic features, such as stream, road, aquifer, and their attributes. Currently, these definitions and their included terms define an initial set of entities found on topographic maps and hydrographic charts. The set will be expanded to include soils, wetlands, geology, and other data categories. Part III, ISO 8211 encoding, explains how to use the International Standards Organization (ISO) 8211 standard to implement Parts I and II. ISO 8211 is a specification for using a descriptive file technique which includes header information for each file being transferred. The standard is media independent, so that the SDTS can be used with any recording media. |
national spatial data infrastructure (NSDI), with the participation of state and local governments and the private sector. Several FGDC activities support the development of the NSDI. Town meetings and more direct contacts with groups representing different sectors of the spatial data community provide forums for making the public aware of federal geographic data and discussing roles and opportunities for participating in the NSDI. FGDC members are developing a data clearinghouse, including a draft standard for data documentation, or "metadata." The committee is encouraging the use of the SDTS to ease the problems of transferring and sharing geographic data, and is developing standards for the content of data sets for categories coordinated under Circular A-16. The committee also gathers requirements for geographic data and is forging partnerships for data production.
State and Local Data Management Activities
Many states have established strong programs for collecting, maintaining, analyzing, and distributing topographic, cartographic, natural resource, and attribute information. In several of these states, interagency committees have been created to coordinate data preparation and develop standards for these databases. These standards may, in fact, surpass federal standards owing to the scales and/or attributes required for state applications. In these cases, data tend to be of high quality and collected following a plan and standard.
Minnesota, for example, operates one of the oldest and most extensive state geographic information systems (GIS) in the country. The Minnesota Land Management Information System, established at the University of Minnesota in 1967, later became the Land Management Information Center (LMIC). The LMIC, together with the Department of Natural Resources, serves as the state's repository of geographic resource data and coordinates data collection and management activities within the state. A 1989 inventory identified more than 135 digital databases in Minnesota of which more than half were concerned with hydrology (Warnecke et al. 1992).
Other states have collected geographic information and made it available to users, but in a less organized fashion. In these areas, individual agencies have procured and developed automated systems and the data to support them on an as-needed basis. In many cases, the available digital database may be large, but not managed directly by any one group. Often state data centers act more as clearinghouses than as coordinating agencies, and the data tend to be fragmented, nonstandardized, and of unknown quality. Such data should be used with caution in conformance with standards, and within the sensitivity of the model to the data. Some of these states may have made some commitment to automating data collection and analysis
and may be in the process of formulating data requirements for various applications.
In the remaining states, little or no activity has occurred in the automation of geographic information and only limited geographic data are available. Generally, one or two agencies have begun to collect geographic data in digital form on an ad hoc basis. Many of these states are watching the development and maturation of information groups in other states before initiating their own process.
Local databases and their associated support systems also vary greatly in their degree of organization and sophistication. To data, cost of establishing digital database systems has been prohibitively large for all but the biggest municipalities. However, as costs decrease and the number of proven applications rises, local usage of these systems can be expected to grow dramatically, as will the amount of local-scale digital information. It is critical that some form of standardization be established early in the development of local systems to insure that adjacent jurisdictions can work cooperatively in the future and that data and applications can be transferred with minimum effort.
The availability and quality of state and local digital databases needed to support ground water vulnerability assessments depend on: (1) the presence of a jurisdictionwide coordination entity, (2) existing laws and mandates that require digital information, (3) multiagency or departmental use of the data, and (4) vision and financial support by senior management. Where these conditions are met, vulnerability assessments are likely to be better supported by data and personnel; where they are not, attempts at assessments will be difficult.
The State Geographic Information Systems Activities Compendium (Warnecke 1992) provides anecdotal information about digital database activities as well as a listing of contacts for those seeking additional information about state GIS activities.
TOPOGRAPHY
Topography affects ground water quality primarily through its influence on the hydrologic processes of runoff and infiltration. Slope, slope shape, and aspect information for use in determining runoff characteristics, snow melt patterns, and drainage basin delineation can be derived from raw elevation data. Elevation data can be combined with soil profile information, geophysical data, and well drilling records to produce three dimensional representations of the subsurface hydrogeologic features.
Characteristics and Availability of Data
Topography is represented on traditional paper maps in the form of elevation lines (contours) with the contour interval dependent on the scale of the map and the amount of topographic relief. Contour data can be represented in a digital database as vectors. However, digital elevation is usually maintained in a grid-cell (point samples) format called a digital elevation model (DEM).
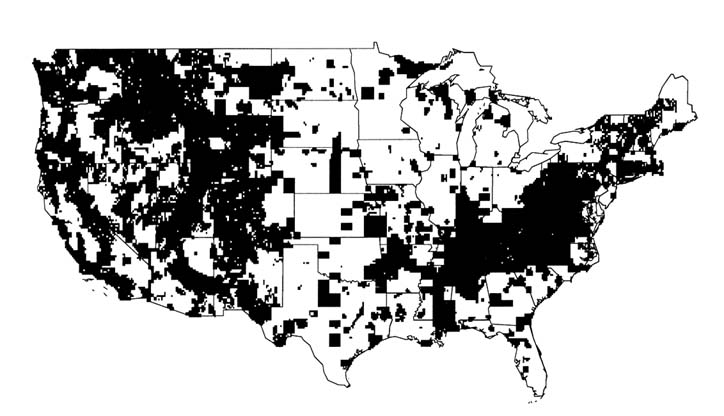
The U.S. Geological Survey (USGS) and the Defense Mapping Agency (DMA) have produced most of the topographic contour maps and subsequent DEMs for the United States. The USGS's National Mapping Division distributes DEM information at scales of 1:24,000 and 1:250,000. These two product lines differ in topographic detail and positional accuracies. The 1:250,000 scale DEMs are available nationwide, while the 1:24,000 scale DEMs are available for approximately 20 percent of the country, primarily in the western part. A status map of 1:24,000 scale DEM coverage is shown in Figure 4.1. Digital elevation data are distributed on nine-track tape and soon will be distributed on CD-ROM disks by the U.S. Geological Survey. Some additional digital elevation data are collected as part of operational programs or specialized research projects in other federal, state, and local agencies, and may be available from these sources.
Discussion
Digital terrain data, which might be used in regional or national ground water vulnerability assessments, are not currently accessible on a nationwide basis with uniform spatial and attribute characteristics. Data at map scales of 1:100,000 and 1:250,000 could be used for regional analysis. Because of the significant problems encountered in matching the boundaries of existing maps for adjoining subareas, often it is not possible to produce a seamless map of the larger area or region of interest. It is difficult to derive meaningful slope information from these data since the distance between sample points is orders of magnitude larger than the vertical component.
The 1:24,000 scale data provide high definition land surface information, however, complete elevation data are rarely available at this scale. Also, in certain instances, such as urban and forested areas, terrain data may be influenced by features above the actual terrain. Caution should be exercised when using such data for precise elevation analysis.
The utility of digital elevation data for ground water vulnerability studies would be enhanced by several actions:
-
Complete the 1:24,000 scale Digital Elevation Models series to provide continuous and uniform data.
-
Change the data preparation standards or develop algorithms to reduce the errors associated with nonterrain factors (e.g., trees, buildings) affecting elevation data.
-
Develop effective edge matching routines to eliminate errors along quadrangle boundaries at all scales.
-
Provide users with elevation point data sets rather than the rasterized averages in a DEM. Digital elevation data values are the average elevation of a number of sample points found in a resolution cell. Delivering the source point information would allow the user to sample or reclass the data in any fashion suitable for the application.
-
Develop new data collection methods for preparing digital elevation data. Stereo remote sensing, global positioning system technology, and other innovations may be useful in speeding up the data collection efforts and may perhaps result in a higher resolution product.
-
Develop standards for high resolution, large scale elevation models that are based on available technology and not on historic standards and procedures.
SOILS
Soil can be one of the most important factors affecting the transport of contaminants from the earth's surface to ground water. Various soil properties will affect the rates of contaminant transport, retardation, and sometimes degradation. Most vulnerability assessment techniques require soils information.
Characteristics and Availability of Data
The Soil Conservation Service (SCS) of the U.S. Department of Agriculture, through the National Cooperative Soil Survey (NCSS) program, is responsible for mapping the soils of the nation. Surveys have been completed for more than 75 percent of these soils, including most cropland. This mapping has been done on aerial photobases at scales of 1:15,840 to 1:31,680 and line maps at a scale of 1:250,000. SCS has established standards for creation of digital soil geographic databases and begun adding to these databases (Reybold and TeSelle 1989). Box 4.2 describes how soils are mapped.
Geographic Databases
Three digital geographic databases of different scales have been established for use in conjunction with other geographically referenced information: the Soil Survey Geographic Database (SSURGO), the State Soil Geographic
|
Box 4.2 Soil Mapping Soil is defined as the unconsolidated mineral and organic matter on the surface of the earth that has been subjected to and influenced by genetic and environmental factors: parent material, climate (including water and temperature effects), macro- and microorganisms, and topography, all acting over time and producing a product—soil—that differs from its parent material in many physical, chemical, biological, and morphological properties, and characteristics (SSSA 1987). Soils, within a landscape, are a continuum and hence are spatially variable. Most soil properties used for predicting the vulnerability of ground water to contamination vary in time and space (Wilding 1985), which allows the pedologist to partition the landscape into areas with greater homogeneity and to delineate and display these areas on maps as mapping units as shown in Figure 4.2. Mapping units are named for the dominant soil series within the mapped polygon (USDA 1975). Series are the lowest level of soil classification (Lytle and Mausbach 1991). Phases of series (e.g., eroded) constitute components within map units and allow for more precise definition. Once the mapping unit has been delineated, vertical and horizontal components are described, and physical, chemical, and biological properties recorded. These characterizations are based on corings and/or excavations at various points within the map unit, referred to as soil pedons. A pedon is the smallest sample—a minimum of one cubic meter in size—used for describing and classifying soils. This information and data are published collectively in a Soil Survey Report, usually on a county basis. |
Database (STATSGO), and the National Soil Geographic Database (NATSGO). The soil map unit boundaries in each geographic database are linked with soil attribute data to give the extent and properties of the dominant soil series phase in each mapping unit.
SSURGO is the digitized version of county soil surveys designed for farm, township, and county level resource planning and management. Soil map unit boundaries are delineated on orthophotographs or 7.5 minute quadrangles at scales ranging from 1:20,000 to 1:31,680 (Lytle and Mausbach 1991). In a typical soil survey (1:24,000), a map unit may vary from 1 to 5 hectares (2.5 to 12.5 acres) in size. These soil maps are digitized in vector format suitable for use in vector based GIS or conversion to raster format for raster analysis systems. SSURGO map units, such as that shown in Figure 4.2, contain one to three components (e.g., soil series, eroded phase) with up to 60 component/site properties (e.g., slope) and 1 to 28 layer
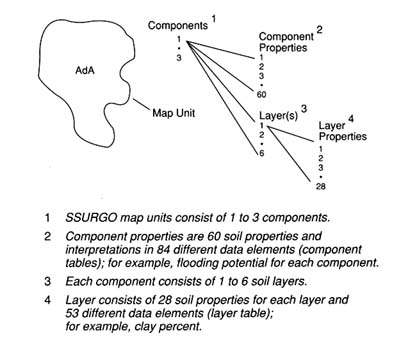
FIGURE 4.2 A conceptual diagram of a soil geographic database (SSURGO) map unit. (Adapted from Lytle and Mausbach 1991. Reprinted, with permission, from Proceedings: Resource Technology 90 copyright 1991, by the American Society for Photogrammetry and Remote Sensing: "Interpreting Soil Geographic Databases," D.J. Lytle and M.J. Mausbach, pp. 469-476.)
properties (e.g., percent organic matter). Attribute data for SSURGO are derived from the Map Unit Interpretation Record (MUIR) database.
The STATSGO database is designed for regional and statewide natural resource monitoring, planning, and management. It is an aggregation of SSURGO soil survey information at a scale of 1:250,000, using U.S. Geological Survey topographic quadrangle base maps. Since STATSGO map unit delineations, such as that shown in Figure 4.3, are generalized from SSURGO databases, each map unit can have up to 21 phases of soil series as components. For each STATSGO map unit, the area of each soil series phase present is recorded and can be associated with appropriate attribute data from MUIR for more precise analyses than would be suggested by the map scale (Bliss and Reybold 1989).
The NATSGO database is designed for multi-state and national resource assessment and planning. It is the digitized Major Land Resource Area (MLRA) map of the United States on a scale of 1:7,500,000 (USDA 1981).
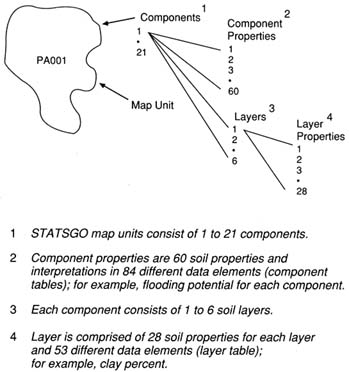
FIGURE 4.3 A conceptual diagram of a state soil geographic database (STATSGO) map unit. (Adapted from Lytle and Mausbach 1991. Reprinted, with permission, from Proceedings: Resource Technology 90 copyright 1991, by the American Society for Photogrammetry and Remote Sensing: ''Interpreting Soil Geographic Databases," D.J. Lytle and M.J. Mausbach, pp. 469-476.)
Map units, such as that shown in Figure 4.4, were developed from generalized state soil maps using land use, elevation, topography, climate, water, and natural vegetation information independent of state boundaries. Soil components in each map unit were determined by field investigations at three Primary Sampling Units (PSUs) selected by stratified random sampling procedures (Figure 4.5) as a part of the 1982 National Resource Inventory (USDA 1979). Soil properties for each of the soil series phases occurring in a NATSGO mapping unit are derived through a linkage with the Soil Interpretation Record database.
NATSGO coverage is complete for the country. The status of SSURGO and STATSGO mapping efforts is shown in Figures 4.6 and 4.7, respectively.
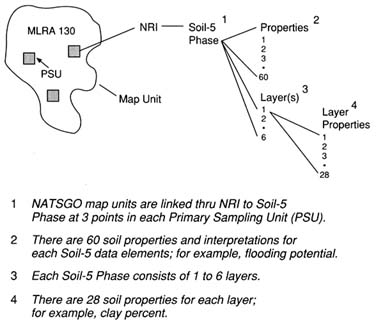
FIGURE 4.4 A conceptual diagram of a national soil geographic database (NATSGO) map unit (Adapted from Lytle and Mausbach 1991. Reprinted, with permission, from Proceedings: Resource Technology 90 copyright 1991, by the American Society for Photogrammetry and Remote Sensing: "Interpreting Soil Geographic Databases," D.J. Lytle and M.J. Mausbach, pp. 469-476.)
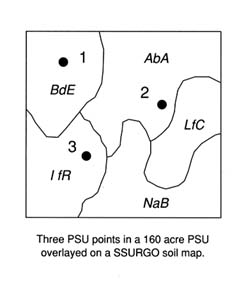
FIGURE 4.5 A conceptual diagram of a 1982 national resources inventory primary sampling unit (PSU) (Lytle and Mausbach 1991. Reprinted, with permission, from Proceedings: Resource Technology 90copyright 1991, by the American Society for Photogrammetry and Remote Sensing: "Interpreting Soil Geographic Databases," D.J. Lytle and M.J. Mausbach, pp. 469-476.)
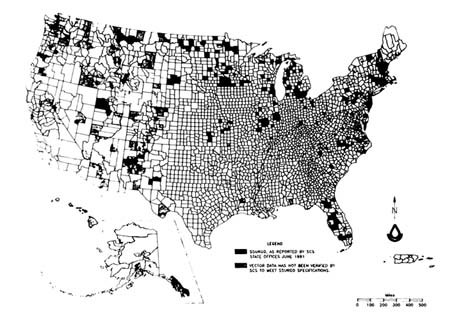
FIGURE 4.6 The June 1991 status map of the soil survey geographic databases (SSURGO) (USDA 1991a).
Attribute Databases
The Soil Interpretation Record (SIR or SOIL-5) database contains estimated values for more than 25 properties of more than 30,000 soil series and phases of soil series in the United States. These property or attribute values define the expected range of values for the site and major layer (horizon) of a soil series. The properties included are site characteristics including mean annual air temperature, precipitation, elevation, frost free days, and drainage; and horizon attributes including particle size distribution, bulk density, permeability, organic matter, available water capacity, soil reaction, salinity, cation exchange capacity, sodium absorption ratio, gypsum, and calcium carbonate equivalent. Estimates of flooding potential, water table depth, depth to bedrock, shrink-swell, and potential frost action characteristics are also listed.
Soil property data are recorded in SIR as an estimated range of values because soils in the landscape occur naturally in a continuum, not as discrete entities. Hence, all map units have inclusions of other soil series with similar and/or dissimilar properties. Soil survey guidelines (USDA 1983) specify that no more than 25 percent of a mapping unit should be comprised of dissimilar soils. Wilding (1988) and colleagues attempted to quantify the spatial variability of a number of soil properties within mapping units of
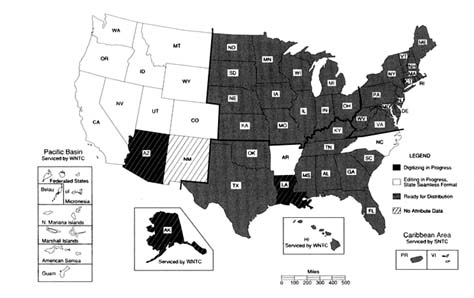
FIGURE 4.7 Status map of the state soil geographic database (STATSGO) (Map provided by the U.S. Department of Agriculture).
soil surveys. Their findings are recorded in Table 4.2 as the mean and range in coefficients of variation observed for various soil properties included in SIR. The section on uncertainty analysis in Chapter 3 contains information on other approaches to estimating uncertainty associated with soil properties.
A subset of SIR that contains most of the soil properties applicable for ground water vulnerability assessments is being compiled in ASCII formatted direct access files as the soil database used in the NLEAP model (Shaffer et al. 1991). Soil attributes have been depth weighted for the top 0.3 meter of soil (layer 1) and the rest of the profile (layer 2). This database contains a complete set of data for all soil series entries, and has been subjected to numerous internal checks of the data to assure consistency between various soil attributes, added missing data, and corrected erroneous entries. Significant attention was devoted to improved estimates for in situ permeability, water holding capacity, and water content at 15 kPa, including adjustments based on soil mineralogical composition as manifested through soil cation exchange capacity. The data are single valued and linked to SSURGO map units through the soil name and identification number of SIR. This database contains approximately 80 percent (most cropland) of SIR and all sand-textured soils exceeding 800 ha in area.
The Map Unit Use File (MUUF) database includes the name and symbol
TABLE 4.2 Relative Variability of Selected Soil Properties Sampled Within Mapping Units of Soil Series (Adapted from Wilding 1988)
|
 |
of each soil map unit in more than 2,600 soil survey areas. In addition, where available, acreage, percent composition of different taxonomic units, and SIR numbers to link SIR data with map unit components are included. When the MUUF database is combined with subsets of estimated soil properties from SIR, the resulting Map Unit Interpretation Record (MUIR) forms a database specific to phases of soil series in a given survey area. The Official Soil Series Description (OSED) database contains the narrative description of each soil series, while the Soil Classification File (SC) stores the taxonomic classification of the more than 18,000 soil series. Collectively, data in OSED, SC, and SIR define a soil series.
Site-Specific Databases
Site-specific or point data, often called hard data (Mausbach et al. 1989), are generated by field sampling of pedons for laboratory characterization and morphological description in support of soil surveys. These data are
used for definition of soil series in OSED and SIR databases. However, these data seldom represent the entire suite of properties embodied in the central concept of a soil series (Mausbach et al. 1989). Currently, a National Soil Characterization Database (NSCDB) is being designed to house pedon data collected by SCS at the national level and by cooperating land grant universities at the state level.
Discussion
Collectively, SSURGO, STATSGO, and NATSGO, and their associated databases can be useful in many methods available for assessing ground water vulnerability. SSURGO data are typically used at scales from the farm field level to multicounty level; STATSGO data may be useful at the multicounty to state level; and NATSGO data are intended for use at the multistate to national level. Primary limitations of these databases for vulnerability assessments can be characterized as follows: (1) soil attribute data in SIR are presented as ranges of soil properties rather than as measures of central tendency and associated variance, (2) SSURGO is not linked with digital elevation data, (3) contribution of macropores to water flow through the soil profile is difficult to evaluate, (4) location of appropriate sampling sites for characterization of a given soil parameter may not be related to soil taxonomy, and (5) the validity of transforming from field to state and national scale has not been demonstrated for either data or models.
Several efforts are currently under way to address some of these limitations. The NSCDB, which, in part, will replace SIR database, will incorporate site-specific, experimental data, including data means, variances, and associated uncertainties. The development of NSCDB will require the identification of the specific pedon that best describes the dominant soil series phase of each soil map unit. These data, compiled in NSCDB and linked to SSURGO, will represent the landscape more accurately and give planners and managers a better appraisal of the vulnerability of ground water to contamination in specific areas.
A listing of additional data needs would be endless if it reflected the needs of every potential assessment technique. However, particularly important soil parameters for assessing vulnerability are the in situ hydraulic properties of the soil profile and the soil organic carbon content. When these and other data are not available, empirical functions are used to approximate these properties based on other soil parameters (e.g., soil pH, bulk density). Inclusion of these properties in NSCDB will improve the reliability of assessments requiring these data.
The linkage of SSURGO to digital elevation data would allow for a better understanding of water movement across and into soil. This linkage would also enhance the accuracy of soil maps generated during field mapping. In addition, incorporation of the location, extent, and description of
inclusions within a given soil map unit in SSURGO would improve the utility of these data for vulnerability assessments. This task could be partially achieved by soil survey at a scale of 1:12,000. Vulnerability assessments at the field and watershed scale must consider land use and spatial and temporal variability of the land surface as they affect water movement across and into soil.
The development of digital soil geographic databases has not kept pace with demand. One major obstacle to automating the soil map, especially in the Midwest and the South, is that most current soil surveys were mapped and published on aerial photobases that do not meet National Map Accuracy Standards, now required by SCS. These maps must be meticulously recompiled to 7.5 minute topographic quadrangles or orthophotoquads before digitizing. This process must assure that line placement and data integrity are maintained. SCS has no active program to digitize detailed soil surveys for inclusion in SSURGO. Emphasis has been on digitizing ongoing surveys, with limited resources directed toward recompiling and digitizing published surveys, which are often the most critical for automated resource planning and analysis.
HYDROGEOLOGY
The properties of materials in the porous media below the soil zone, coupled with differences in the elevation of the water table, which is time-dependent, control movement of contaminants in the subsurface once they pass through the soil zone. Hydrogeologic databases incorporate details on water table configuration, subsurface geology, and hydraulic properties of saturated consolidated and unconsolidated geologic units. Often information in hydrogeologic databases is synthesized into a series of maps showing the areal and vertical extent of geologic units having similar hydraulic properties (e.g., hydraulic conductivity, porosity, and storage properties), the ability of geologic units to deliver water to wells, and directions of ground water flow.
Characteristics and Availability of Data
Currently, there is no national compilation of hydrogeologic data that can be used easily as a database or map. The U.S. Geological Survey, as part of its ongoing Regional Aquifer-System Analysis (RASA) program, produces maps showing basic hydrogeologic data at various scales. A Ground Water Atlas of the United States is being developed as part of the RASA program; the first of 13 planned multistate sections of the atlas has been published (Miller 1990). The Geological Society of America recently started to develop hydrostratigraphic (Maxey 1964) nomenclature for the United
States (Seaber 1988) at a regional scale that may have limited use in practice (NRC 1988). Several states, such as Minnesota and Wisconsin, have prepared statewide and larger scale hydrogeologic maps. A major product of most of these efforts is a generalized hydrogeologic map showing areal variability in aquifer material properties in the context of well yield or well capacity. Statewide hydrogeologic assessments of this type were used extensively by Pettyjohn et al. (1991) in their national assessment of ground water vulnerability and can be obtained by inquiries to individual state departments of natural resources or similar agencies.
Discussion
The establishment of a more useful hydrogeologic database at a national level is in its infancy, mostly because of the lack of good geologic mapping; the areal coverage of geologic maps at large map scales in the United States is scant at best (NRC 1988). Less than 20 percent of the continental United States has been mapped geologically at a standard scale of 1:24,000 or larger (NRC 1988)—one of the proportionally smallest national geological map bases in the developed world (Haney 1991). Although the U.S. Geological Survey and state geologic surveys are mandated to prepare geologic maps, these efforts have received low priority due to funding limitations. For example, USGS mapping in the 1980s was only a quarter of that done in the 1960s.
Geologic maps at sufficiently large scales provide the lithologic and structural data from which the information found in SCS soil maps can be placed in a larger context, particularly if lithologic facies are identified (e.g., Anderson 1989). Geologic and hydrogeologic maps, however, are only progress reports, whose accuracy depends on scale and the expertise of the scientist doing the mapping. State line and regional differences in nomenclature confound synthesis of some maps, whereas in some parts of the country (e.g., Canadian shield and glacial drift in parts of the midwestern United States), geologic units and surficial deposits are mapped as undifferentiated.
While the accessibility and national coverage of large scale geologic maps are poor, that of the national and state databases for basic hydrogeologic and subsurface information are even more scant, especially where there is no active mineral or hydrocarbon exploration history. Subsurface and hydraulic information must be compiled from individual well logs or soil boring data, usually found in state environmental agencies or geologic survey offices. The quality of these data and the extent to which such files are maintained are highly variable. Some states, such as Minnesota, require that all drillers submit to the state all well logs, measured water levels, and other hydraulic data, which are then digitized and stored as readily accessible
computer files. From a synthesis of these data and geologic maps, high quality large scale hydrogeologic maps are being prepared (e.g., Kanivetsky 1989a, b; Piaget 1989). In contrast, some states keep no systematic record of well logs, although subsurface data are available in consulting reports and published literature.
Finally, little attention has been paid to development of a national or regional effort to characterize the stratigraphic column between the upper 1.5 meters, which is investigated by soil scientists, and the water table. Although research in vadose zone hydrology is expanding, most studies are highly site-specific and no regional compilation of data has been made. In places like the Southwest, the vadose zone can be hundreds to thousands of meters thick, and its properties arguably will have a large effect on whether contaminants reach the water table.
WEATHER AND CLIMATE
Weather and climate can have significant influence on the transport of materials from the soil surface to the water table. Water from precipitation or irrigation is the main transport agent for most pollutants that affect ground water quality. Weather and climate elements important to water quality are: (1) precipitation, including intensities and timing of precipitation events, (2) solar radiation, (3) wind speed, (4) air temperature, (5) relative humidity, (6) potential evaporation, and (7) air quality variables.
Characteristics and Availability of Data
The National Weather Service (NWS) is the federal agency responsible for coordinating, collecting, maintaining, and distributing climate data. It operates a data collection network of some 8,000 weather stations producing the daily and monthly precipitation and temperature information that forms the backbone of our nation's climate database. This information was initially collected to evaluate climate in populated areas, and also used for weather prediction and flood warnings. Later, weather stations were placed in areas around airports to assist in aviation control. This arrangement has served the country well except in the less populated western third which has been sparsely covered with weather stations in mountain areas, which are natural water supply producing areas. As a result, several natural resource oriented agencies, such as the Forest Service, SCS, National Park Service, Bureau of Land Management, Bureau of Reclamation, and Bureau of Indian Affairs, and similar state government and university entities have developed climate data collection systems and databases to suit their own needs in their areas of jurisdiction. Also, agency coordination in climate data collection
and management has increased as a result of a more integrated approach to environmental and natural resource planning.
Existing climate databases are limited in terms of geographic coverage of climate data, data formats, data homogeneity, data quality, period of record, data record serial completeness, computerized availability, and/or timeliness. Many long term NWS data records in urban areas are largely unadjusted for the dramatic urban and industrial growth during this century. Of the 8,000 currently active U.S. weather stations, only 492 have been checked for instrument and location changes and adjusted for population (Hughes et al. 1991). Data from other stations are not representative of larger, more rural regions, complicating comprehensive spatial climate analysis. Urbanization has been most dramatic in affecting temperatures (particularly summer minimums) and to some extent precipitation, although urban effects on precipitation are more difficult to quantify.
Precipitation data have high spatial variability and are needed not just in daily increments but in hourly and 15 minute intervals to fully evaluate pollutant transport through the soil profile. Wintertime precipitation in cold regions of the country and particularly in the western U.S. in the form of ice or snow is very important in the evaluation of airborne dry or storm deposited pollutants. The mountain snowpack delays release of airborne pollutants accumulated in its layers until spring when the snowpack profiles become isothermal or otherwise have free water passing through. This situation creates significant short-term high concentrations of the pollutants (Sommerfeld et al. 1990). Since more than 70 percent of the water that flows in the West comes from melting mountain snows, this phenomenon is critical to subsequent water quality.
Solar radiation, relative humidity, and wind information are collected sparsely, mostly at aviation centers. For other areas this information requires considerable estimation and extrapolation for spatial analysis. Potential evaporation information also is collected sparsely, usually in areas where irrigation water management has required the data to guide water use and maximize crop production. Air quality data, except in populous areas, are scant, providing an inadequate database for spatial analysis.
Although not necessarily part of a climate database, soil moisture and soil temperature, important factors in chemical fate and transport, are sparsely observed nationwide. A 1991 SCS pilot project monitoring global climatic change identified more than 300 separate collection efforts for these two soil parameters. This information is in a variety of formats, specifications, and quality (USDA 1991b). However, much of this data collection is driven by irrigation water management needs, which do not necessarily match the data needs for ground water vulnerability assessments.
Several regional and national efforts are attempting to index climate information available from many sources for common use. A catalog of
215 U.S. Department of Commerce climate data sets has been prepared by the NWS (NOAA 1988), most of which are available either as microfiche or nine-track tape. The most extensive of these efforts is the Historical Climate Network (HCN) archived by the National Climatic Data Center (NCDC). It contains monthly values for precipitation and maximum/minimum temperature for 1,219 U.S. weather stations active in 1987 with at least 80 years of data record. The HCN contains both unadjusted and adjusted data, where the adjustments are for station moves and instrument or recording changes. An elaborate set of missing data and error codes are provided to aid in the interpretation and use of these data. The HCN is generally believed to be the most accurate database describing U.S. climate.
Several companies and government agencies have edited the NWS data and repackaged it for sale or their own use. EarthInfo Incorporated of Boulder, Colorado, has produced a CD-ROM version of Historical Climate Network which includes a user interface for the personal computer. WeatherDisc Associates of Seattle, Washington has produced a CD-ROM called World WeatherDisc which includes monthly average weather data for 5,511 NWS and cooperative stations from 1951 to 1980, as well as ten other climate data sets. IBM's Watson Research Laboratory (Wallis et al. 1991) has produced a CD-ROM containing the unadjusted daily and monthly values for 1,036 HCN sites from 1948 to 1988. This data set is serially complete, with missing data filled by correlation; obvious errors and missing values are flagged, and HCN codes and monthly differences from HCN values are recorded.
An on-line interactive operational database of all the snow survey data archived over the past 70 years for the western United States is available through the SCS. These data include snow depth, water equivalent, and associated precipitation and temperature.
During the 1980s, the NOAA National Climate Program established six Regional Climate Centers (RCCs) to provide services tailored to regional climate requirements. Many climate information providers collect climate data from RCC established networks or from agencies under RCC contract or data archiving services.
Three other major efforts are under way to develop better climate databases for the United States. The Climatic Data Access Facility (CDAF) was established by SCS in 1990 to assess, obtain, evaluate, manage, and disseminate climatic data and analyses needed to support the agency's water management and environmental modeling activities. One of the CDAF's goals is to provide error free, serially complete, spatially representative, and timely data through a network of climatic data liaisons to the nearly 3,000 SCS field offices nationwide. Currently the NCDC TD-3200 daily data set and SCS's Snow Telemetry (SNOTEL) data set are on-line and accessible through the CDAF's Centralized Database System (CDBS). The CDBS
now contains corrected daily temperature and precipitation data (Reek et al. 1992) and is expected to begin inclusion of spatial estimates of missing data to create serially complete data in 1993.
The U.S. Environmental Protection Agency (EPA) Global Change Database Program is producing a Global Ecosystem Data Set on a CD-ROM. The disc will contain locational data on soils, slope, aspect, elevation, vegetative cover, and climate, including monthly minimum and maximum temperature and precipitation. The data set has 10 minute resolution (approximately 13 by 18 km spacing), although the original resolution of some data was 0.5 degree.
The NWS's new Advanced Weather Information Processing System (AWIPS) uses state-of-the-art computer work stations to process information from Next Generation Radar (NEXRAD) sites and automated data networks. AWIPS will provide a highly sophisticated tool for weather forecasting as well as integrated spatial analysis and modeling of climatic data associated with specific storms. The system is expected to be a significant new source of computer derived spatial information for use in calibration of spatial data extrapolation models. Over the next decade AWIPS and NEXRAD will be implemented nationwide.
Discussion
Currently no U.S. climate database has adequate elevational and spatial coverage to define the great variability of climatic factors that exist, provides information consistent in format and quality, and makes it widely accessible to users by telecommunications and other means. However, this situation is receiving significant attention from the many agencies involved, and serious attempts are being made to improve data collection and archiving.
LAND USE AND LAND COVER
Land use and land cover (LULC) descriptions are used to provide insight on ground water vulnerability to contamination. LULC designations provide general descriptions of the natural and cultural activities taking place at the Earth's surface, and are broadly indicative of the kinds of contaminants likely to be available for leaching, including naturally occurring ones. For example, a cropland land use designation would indicate the potential for agrichemical use. An urban classification would suggest a different set of potential contaminants. The type of land cover affects how much precipitation and irrigation water infiltrates the ground, and how much water, nutrients, and other chemicals are taken up by plants.
Characteristics and Availability of Data
LULC data are usually represented as either mapped areas with associated attributes, or statistical indices for given areas such as a county or state. In both instances, data are collected using a standardized classification scheme. Most land use or land cover mapping projects manually interpret areas from remotely sensed imagery and then digitize class boundaries.
The classification scheme applied to LULC data is perhaps the most critical factor in determining the value of this information for ground water vulnerability assessment. For example, classes that are useful for forestry applications may not be appropriate for hydrologic investigations and vice versa. The spatial resolution of LULC data is also critical to use of these data. Large polygons generally will be more heterogeneous than smaller ones, and it is therefore more difficult to estimate meaningful average values for large polygons.
Land use and land cover are important data elements for many agencies of the federal government (USGS 1992). These data are used to evaluate current status, changing conditions, and resources over large areas in support of agency initiatives and planning operations. Many agencies have been digitizing existing and collecting new LULC data for their specific purposes, resulting in a mixture of data formats, LULC classification systems, and scales and accuracies.
The USGS is producing LULC maps and associated files for the entire United States. Most of the available files have been digitized using the Geographic Information Retrieval and Analysis System (GIRAS) format, and are available as either vector or raster files. The data are distributed in 1 degree of latitude by 2 degrees of longitude corresponding to the standard 1:250,000 topographic mapping series. The minimum resolution for GIRAS data is 4 hectares in urban and built-up lands and 16 hectares in other areas. The GIRAS digital data provide LULC information using the Level II Anderson classification (Anderson et al. 1976). Digital LULC data are distributed by the USGS/NMD on nine-track tape and will be distributed soon on CD-ROM disks.
Many other federal agencies, such as the Forest Service, Bureau of Land Management, Tennessee Valley Authority, and Fish and Wildlife Service, have collected their own LULC data or have modified existing GIRAS files. Many state and local government agencies also have extensive LULC data collection programs, primarily at the 1:24,000 scale.
Discussion
LULC data are by nature transitional—each file provides only a snapshot of the environment at one point in time. Vulnerability assessment
methods may require LULC information at discrete times to analyze the environment properly. Currently, the USGS has available comprehensive LULC data for the United States. As currently planned, future LULC data collection will be user driven and not collected on a routine repeat basis. In the past, USGS acquisition of LULC data has been slow, and the data for adjacent quadrangles may have been collected years apart and by differing interpreters using different collection techniques. In these circumstances, the resulting data are variable in their spatial accuracy and attribute quality. For these reasons, users of vulnerability assessment methods may need to seek additional sources of LULC data (e.g., interpretation of synoptic satellite data).
The Level II Anderson classification scheme used by the USGS is detailed enough for simple applications and provides the framework for more specific information where additional detail is needed. However, data requirements for more complex or comprehensive methods may quickly outdistance the attribute characteristics of this scheme. For example, Anderson Level II does not distinguish pasture land from cropland or irrigated from nonirrigated lands, yet these factors may affect vulnerability significantly.
The 1987 Agricultural Census and 1987 National Resources Inventory (NRI) are additional sources of land use information for state and national assessments. The data collection techniques and classification schemes differ between the Agricultural Census and the NRI, making comparisons of data difficult. The Agricultural Stabilization and Conservation Service (ASCS) and SCS land use and land cover data collected at the farm and ranch level are valuable because of their level of detail and currency, however, they lack a digital geographic reference.
The utility of digital LULC data for ground water vulnerability studies and other applications could be enhanced by the development of a standard LULC classification scheme to achieve consistency in data at the national scale. The development of such a classification scheme will require cooperation among scientists, other user groups, and image interpretation specialists. The scheme should include hydrologically significant land use classes developed to support vulnerability assessments and other ground water investigations.
In addition, much more thought should be given to mapping land cover as a mutually exclusive data category, with land use attributes added to the cover polygons as appropriate. The existing Anderson classification scheme intermixes land use and land cover categories so that a single land use or single land cover classification is not possible. Ancillary land use and land cover attributes would enhance the utility of the simple classification scheme now in use. Examples might include estimates of surface roughness, amount of impermeable surface, and type of cultural features present.
Since land use and land cover are dynamic attributes (agricultural cropping
practices change annually and seasonally), data collection programs should be completed quickly to create a database that is, ideally, specific to a given year.
MANAGEMENT FACTORS
Ideally, management factors such as plant growth, tillage and other soil disturbances with their associated ground cover conditions, irrigation, drainage, conservation practices, grazing, and agrichemical applications should be considered when conducting a ground water vulnerability assessment (USDA 1992). Not all these factors are described in national or regional databases; however, several databases are worthy of note because they address some of these factors, including the National Resources Inventory, the National Agricultural Census of 1987, the Irrigation Water Use Survey of 1988, and several pesticide databases.
Characteristics and Availability of Data
National Resources Inventory
The National Resources Inventory (NRI) is a multiresource inventory conducted at five-year intervals by the SCS. Data are collected at approximately 800,000 points on nonfederal lands and include information on soils, land cover, land use, cropping history, conservation practices, conservation treatment needs, potential cropland, prime farmland, highly erodible cropland, water and wind erosion, wetlands, wildlife habitat, vegetative cover conditions, irrigation, and flood susceptibility. In 1982 and 1992, sufficient sample information was collected to characterize major land resource areas (MLRAs). In 1987, however, fewer areas were sampled allowing for good characterization at the state level. For nonfederal lands, the NRI is one of the most comprehensive and consistent databases for national resource analysis and is one of the few that links soil type with management factors such as conservation practices, land use, land cover condition, and irrigation.
Agricultural Census of 1987
The Bureau of the Census conducts an agricultural census every five years. The 1987 census includes statistical information by county about farm numbers, farm value, farm size, market value of agricultural products, farm income, farm expenses, farm land use, farm irrigation, agricultural chemical use, livestock and poultry operations, crops and vegetables harvested, fruits, nuts, and berry production, and nursery and greenhouse crops.
Farm and Ranch Irrigation Survey
The 1987 Agricultural Census has been supplemented by a special survey of irrigators, which contains tabulations of irrigation data on U.S. farms and ranches in 1988. It provides county level data that relate water use to crops produced, sources of the water, and the technology used to apply irrigation water (USDC 1990).
Pesticide Databases
The EPA's Pesticides in Ground Water Database identifies the pesticides that have been looked for in ground water, the areas monitored, and the pesticides detected. The EPA is using this database to identify areas where pesticide use has been a problem in order to evaluate the need for restricted usage. This database may be made available in the future in electronic form from EPA's Pesticide Information Network.
An agrichemical use database compiled by Resources For The Future, Inc., is called the National Herbicide Use Database of 1989-90. It summarizes use of 96 herbicides on 84 crops on a county basis.
The USDA National Agricultural Statistics Service (NASS) has recently initiated a survey of the type and quantity of pesticides used on major crops. Initial data were gathered for pesticides on cotton in 1989. NASS has expanded the survey to corn, soybeans, sorghum, wheat, rice, peanuts, potatoes, vegetables, and fruits for 1990 and 1991.
The Pesticide Properties Database compiled by the SCS, Agricultural Research Service, and Extension Service (ES) describes the fate and transport characteristic of about 300 pesticides by crop and soil type. This database has been linked to the SCS soil databases to assist SCS and others in assessing pesticide leaching potential past the root zone.
Field Level Databases
Two agencies in the USDA, the Agriculture Stabilization and Conservation Service (ASCS) and the SCS, collect land information such as land cover and use, irrigation, drainage, crop history, crop yield, erosion rates, and conservation practices such as terracing and residue management for farmers and ranchers who participate in USDA farm programs. This information is collected on a farm field or ranch pasture basis and exists in digital tabular form for much of the country's private croplands. Field or pasture boundaries are drawn on aerial photographs at scales from 1:7,920 to 1:12,000, but are not available in digital form.
The extensive farm field and ranch pasture boundaries collected by ASCS and SCS need to be geo-referenced to be useful in a digital domain.
If this is done and a standard classification system is adopted, this database would no doubt be one of the most valuable available for ground water vulnerability assessment of private lands at the county, watershed, and field levels. An accurate photo-image base, such as an orthophotograph, would need to be used instead of an aerial photograph in order to meet national standards and permit effective sharing of these data with others.
CONCLUSION
Assessment of ground water vulnerability to contamination is a complex task requiring information contained in a variety of geographic databases maintained by federal, state, and local agencies. Early efforts in compiling spatially-referenced data resulted in analog outputs (i.e., paper maps), but more recent efforts have led increasingly to data stored in digital formats. Currently, such databases are used routinely in a wide range of applications, including vulnerability assessments, to produce thematic maps for policy makers and resource management. The production of thematic maps, and similar decision aids, requires retrieval, transfer, manipulation, interpretation, and analysis of the digital information.
Since these data and information have been collected and maintained by a number of entities and for differing purposes, a myriad of problems have been encountered in their use. The National Research Council's Mapping Science Committee (MSC) recently reported that lack of coordination has resulted in duplicative efforts among the federal agencies, at significant cost to the public, and that existing spatial data may not always be compatible or reliable (NRC 1993). On this basis, the MSC report argued for the development of the National Spatial Data Infrastructure (NSDI), which is defined as the ''total ensemble of geographic information at our disposal" as well as all the other resources required to use such information. The MSC concluded that "unless a vision for the National Spatial Data Infrastructure exists and the spatial data bases, policies, and standards are in place to facilitate the access and use of the spatial data on a national scale, opportunities in areas from environment to development will be lost."
The MSC report also recommends that federal efforts expand beyond the compilation of various types of spatial databases and development of standards for data exchange to include "more specific measures and standards of content, quality, currency, and performance of various components" of the proposed NSDI. It is not enough to have easy access to existing spatial data; it is important to know how good is the information contained in these databases. The MSC also recommends that base data (also referred to as minimum data sets in some modeling literature) required for small-, medium-, and large-scale applications of spatial data be identified. Base data requirements for vulnerability assessments are clearly needed.
Increasing use of thematic maps, and other decision aids, based on existing spatial databases has begun to point the need for additional data or for data of better quality. However, allocation of additional federal funds is unlikely for collection of new spatial databases, at least not for traditional approaches used in the past to collect the existing spatial databases. Thus, our attention must be focused on innovative, cost-effective techniques for gathering new spatial data. For example, Engman and Gurney (1991) and Dozier (1992) have reviewed the use of a broad spectrum of remote sensing techniques for gathering data required for describing hydrologic processes over a wide range of spatial and temporal scales. They discuss the more established remote sensing techniques based on earth-orbiting satellites, as well as the emerging remote sensing techniques (e.g., ground-penetrating radar and tomographic reconstruction) for the local-scale characterizations of subsurface hydrogeologic features. In addition, there exists a wealth of analog maps and photographs that could be converted to the more useful digital format.
The collection and synthesis of existing spatial databases has involved the extraordinary efforts of a large number of technical experts. The challenge is to meet the present and future spatial data needs without having to expend similarly tremendous efforts. Meeting this challenge will require close coordination among those who generate the spatial databases and those who use them for a variety of policy and management purposes.
REFERENCES
Anderson, M.P. 1989. Hydrogeologic facies models to delineate large-scale spacial trends in glacial and glaciofluvial sediments. Geological Society America Bulletin 101:501-511.
Anderson, J.R., E.E. Hardy, J.T. Roach, and R.E. Witmer. 1976. A Land Use and Land Cover Classification System for Use with Remote Sensor Data. Professional Paper 964. U.S. Geological Survey.
Bliss, N.B., and W.U. Reybold. 1989. Small-scale digital soil maps for interpreting natural resources. Journal of Soil Water Conservation 44:30-34.
Dozier, J. 1992. Opportunities to improve hydrologic data. Reviews of Geophysics 30(4):315-331.
Engman, E.T., and R.J. Gurney. 1991. Remote Sensing in Hydrology. London: Chapman and Hall.
Haney, D. 1991. Geologic Mapping—a National Issue. GSA Today, Geological Society of America, July, 1991, p. 143-1344.
Hughes, P.Y., E.H. Mason, T.R. Karl, and W.A. Brower. 1991. United States Historical Climatology Network Daily (HCN/D) Temperature and Precipitation Data. ORNL/CDIAC-50, NDP-042. Oak Ridge, Tennessee: Carbon Dioxide Information Analysis Center, Oak Ridge National Laboratory.
Kanivetsky, R. 1989a. Quaternary Hydrogeology. Geologic Atlas Hennepin County, Minnesota. N.H. Balaban, ed. County Atlas Series Atlas C-4. St. Paul: Minnesota Geological Survey.
Kanivetsky, R. 1989b. Bedrock Hydrogeology. Geologic Atlas Hennepin County, Minnesota.
N.H. Balaban, ed. County Atlas Series Atlas C-4. St. Paul: Minnesota Geological Survey.
Lytle, D.J., and M.J. Mausbach. 1991. Interpreting soil geographic databases. Pp. 469-476 in Proc. Resource Tech. 90, Second Intern. Sym. Adv. Tech. in Nat'l. Resource Manag., Washington, D.C., Nov. 12-15, 1990. Bethesda, Maryland: Amer. Soc. Photo. and Remote Sensing.
Mausbach, M.J., D.L. Anderson, and R.W. Arnold. 1989. Soil survey databases and their uses. Pp. 659-664 in Proc. Computer Simulation Conf., Austin, TX. July 24-27, 1989. San Diego, California: Soc. Computer Simul.
Maxey, G.B. 1964. Hydrostratigraphic units. Journal of Hydrology 2:124-129.
Miller, J.A. 1990. Ground Water Atlas of the United States: Segment 6—Alabama, Florida, Georgia, and South Carolina. Hydrologic Investigations Atlas 730-G. Reston, Virginia: U.S. Geological Survey.
Mollering, H., ed. 1988. Proposed standard for digital cartographic data. The American Cartographer 15(1):11-140.
National Research Council (NRC). 1988. Geologic Mapping: Future Needs. Washington D.C.: National Academy Press. 84 p.
National Research Council (NRC). 1993. Towards a Coordinated Spatial Data Infrastructure for the Nation. Washington, D.C.: National Academy Press.
National Institute of Standards and Technology (NIST). 1992. Federal Information Data Processing Standard 173. Gaithersburg, Maryland: National Institute of Standards and Technology.
National Oceanic and Atmospheric Administration (NOAA). 1988. Selective Guide to Climatic Data Sources. National Environmental Satellite and Data Information Service, National Climatic Data Center. Washington D.C.: U.S. Department of Commerce.
Office of Management and Budget (OMB). 1990. Circular A-16. Washington, D.C.: Office of Management and Budget.
Pettyjohn, W.A., M. Savoca, and D. Self. 1991. Regional Assessment of Aquifer Vulnerability and Sensitivity in the Conterminous United States. EPA-600/RSKERL-Ada-9141. Washington, D.C.: U.S. Environmental Protection Agency.
Piaget, J. 1989. Sensitivity of Ground-Water Systems to Pollution. Geologic Atlas Hennepin County, Minnesota. N.H. Balaban, ed. County Atlas Series Atlas C-4.
Reek, T., S. Doty, and T. Owen. 1992. A deterministic approach to validation of historical daily temperature and precipitation data from the cooperative network. Bulletin of the American Meteorological Society 73:753-762.
Reybold, W.U., and G.W. TeSelle. 1989. Soil geographic databases. Journal of Soil and Water Conservation 44:28-29.
Seaber, P.R. 1988. Hydrostratigraphic units. Pp. 9-14 (Chapter 2) in The Geology of North America, Vol. 0-2, W. Back, J.S. Rosensehein, and P.R. Seaber, eds. Boulder, Colorado: Geological Society of America.
Shaffer, M.J., A.D. Halvorson, and F.J. Pierce. 1991. Nitrate leaching and economic analysis package (NLEAP): Model description and application. Pp. 285-322 in Managing Nitrogen for Ground water Quality and Farm Profitability, R.F. Follett, D.R. Keeney, and R.M. Cruse, eds. Madison, Wisconsin: Soil Science Society America.
Soil Science Society of America (SSSA). 1987. Glossary of Soil Science Terms. Madison, Wisconsin: Soil Science Soc. Amer.
Sommerfeld, R.A., D.G. Fox, and R.C. Musselman. 1990. Snow in Mountain Watersheds: Connection to Climate and Ecosystem Health. Fort Collins, Colorado: Rocky Mountain Forest Experiment Station.
U.S. Department of Agriculture (USDA). 1975. Soil Taxonomy: A Basic System of Soil
Classification for Making and Interpreting Soil Surveys. Soil Conservation Service. Agric. Handbook No. 436. Washington, D.C.: U.S. Government Printing Office.
U.S. Department of Agriculture (USDA). 1979. National Resources Inventory Instructions. 1981-82. Washington, D.C.: USDA, Soil Conservation Service.
U.S. Department of Agriculture (USDA). 1981. Land Resource Regions and Major Land Resource Areas of the United States. Agriculture Handbook No. 296. Washington, D.C.: USDA, Soil Conservation Service.
U.S. Department of Agriculture (USDA). 1983. National Soils Handbook. Soil Conservation Service. Washington, D.C.: U.S. Government Printing Office.
U.S. Department of Agriculture (USDA). 1991a. Digital Soil Data. Washington, D.C.: USDA, Soil Conservation Service.
U.S. Department of Agriculture (USDA). 1991b. A National Inventory of Soil Moisture and Temperature Data Sets. USDA Soil Conservation Service Global Climate Change Pilot Project. Portland, Oregon: U.S. Department of Agriculture.
U.S. Department of Agriculture (USDA). 1992. Water Quality Modeling User Requirements. Draft 4.0 June 1992. Washington, D.C.: Agricultural Research Service, Extention Source, and Soil Conservation Service.
U.S. Department of Commerce (USDC). 1990. 1987 Census of Agriculture; Volume 3: Related Surveys; Part 1: Farm and Ranch Irrigation Survey (1988). Washington, D.C.: U.S. Department of Commerce.
U.S. General Accounting Office (GAO). 1982. Duplicative Federal Computer-Mapping Programs: A Growing Problem. GAO/RCED-83-19. Gaithersburg, Maryland: U.S. General Accounting Office.
U.S. Geological Survey (USGS). 1992. Forum on Land Use & Land Cover: Summary Report. Reston, Virginia: U.S. Geological Survey.
Wallis, J.R., D.P. Lettenmaier, and E.F. Wood. 1991. A daily hydroclimatological data set for the continental United States. Water Resources Research 27(7):1657-1663.
Warnecke, L., J.M. Johnson, K. Marshall, and R.S. Brown. 1992. State Geographic Information Systems Activities Compendium. Lexington, Kentucky: The Council of State Governments.
Wilding, L.P. 1985. Spatial variability: Its documentation, accommodation and implication to soil surveys. Pp. 166-167 in Soil Spatial Variability, D.R. Nielsen, and J. Bouma, eds. Wageningen, The Netherlands: Pudoc. Publishers.
Wilding, L.P. 1988. Improving our understanding of the composition of the soil landscape. Pp. 13-35 in Proceedings of the International Interactive Workshop on Soil Resources: Their Inventory, Analysis and Interpretation for Use in the 1990's, H.R. Finney, ed. St. Paul: Minn. Extension Service, Univ. of Minnesota.