1
Introduction
It is the mark of an instructed mind to rest satisfied with the degree of precision which the nature of the subject permits, and not to seek an exactness where only an approximation of the truth is possible.
—Aristotle
Ground water is an important natural resource throughout the world. In the United States, approximately 50 percent of the population and more than 90 percent of rural residents use ground water as their source of domestic drinking water (USGS 1990). Ground water is the source of about 34 percent of the irrigation waters in the United States. Other uses of ground water have grown dramatically; total use of ground water for 1985 was an estimated 73 billion gallons a day (USGS 1990), more than double the usage in 1950. In addition, ground water is the principal source of surface water during low flow periods. About 30 percent of river and stream flow comes from ground water, where it contributes to important ecological habitat as well as surface drinking water supplies (USEPA 1991a).
The importance of ground water has long been recognized, but the potential for ground water to become contaminated as a result of human activities at or near the land surface has only been recognized in recent years. Before about 1980 it was thought that soils served as filters, preventing harmful substances deposited at the surface from migrating downward into ground water. Today it is known that soils and other intervening layers have a finite capacity to filter and retard, and so protect ground water.
Over the past two decades, a large number of chemicals and wastes from human activities have been found in ground water throughout the United States. Ground water can be contaminated by localized releases from sources such as hazardous waste disposal sites, municipal landfills, surface impoundments, underground storage tanks, gas and oil pipelines,
back-siphoning of agricultural chemicals into wells, and injection wells. Ground water can also become contaminated by substances released at or near the soil surface in a more dispersed manner including pesticides, fertilizers, septic tank leachate, and contamination from other nonpoint sources.
Nitrates from fertilizers and animal wastes are the most pervasive type of ground water contamination. An estimated 20.5 million tons of fertilizers were applied to crops during 1988-1989 (USDA 1989). Between 1960 and 1985, agricultural use of nitrogen quadrupled, to 12 million tons (USDA 1987). Nitrate levels in ground water have increased concurrently with these rises in fertilizer application.
Pesticides also contribute significantly to ground water pollution. Each year about 661 million pounds of active pesticide ingredients are used in agriculture (OTA 1990, USEPA 1987). The first reported instances of ground water contamination by pesticides occurred in 1979 when dibromochloropropane (DBCP) was detected in California and aldicarb in New York. Subsequently, DBCP was detected in ground water in four additional states. By 1983, ethylene dibromide (EDB) had been found in wells in 16 counties of California, Florida, Georgia, and Hawaii (USEPA 1987). These findings prompted the suspension of EDB use in the United States. By 1988, pesticides had been detected in the ground water of more than 26 states (USEPA 1988). The largest monitoring study conducted in the United States, EPA's National Pesticide Survey (USEPA 1990), concluded that about 10.4 percent of wells in community water systems and 4.2 percent of rural domestic well water had detectable residues of one or more pesticides; fewer than 1 percent of all wells, however, were estimated to contain at least one pesticide in excess of established levels of health concern.
Once contaminated, ground water is very expensive to clean up; in many cases, cleanup may not be possible within a reasonable time (Mackay and Cherry 1989, Haley et al. 1991). In addition, ground water is the only source of drinking water for many rural areas (USGS 1990). The cost of replacing contaminated sources with bottled water or other alternatives is high relative to that of existing ground water resources (Abdalla 1990).
PROTECTING GROUND WATER FROM FUTURE CONTAMINATION
The seriousness and intractability of the problem of contaminated ground water has led resource managers to pursue a policy of prevention. Boxes 1.1 and 1.2 provide background information on the ground water protection programs of two federal agencies—the U.S. Department of Agriculture (USDA) and U.S. Environmental Protection Agency (EPA).
The factors that affect the ability of contaminants introduced at the land surface to reach ground water vary from place to place. Many extreme
|
Box 1.1 President's Water Quality Initiative The President's Water Quality Initiative was launched in 1989 in response to the widespread concern that agricultural activities contribute to the contamination of the Nation's ground waters. The goal of the initiative is to relate agricultural activities to ground water quality and to develop and implement farm management strategies that protect ground water. The USDA was directed to achieve this goal in a manner that maintains productivity and profitability, and minimizes regulation. Research, education, technical assistance, cost-sharing, and data collection programs have been implemented to achieve these objectives. The Initiative will extend through 1995; it is led by the USDA and involves eight principal USDA agencies, state agricultural experiment stations and cooperative extension services, the U.S. EPA, the U.S. Geological Survey, the National Oceanic and Atmospheric Administration, and state universities. As part of the initiative, the USDA developed a ground water vulnerability index for use in setting priorities in program management and to provide insight on the impact of policy development. A description of the USDA Ground Water Vulnerability Index for Pesticides and its applications is presented in the national level case study in Chapter 5. |
situations are relatively obvious. For example, ground water contamination is likely to occur in areas having shallow water tables and sandy soils with high recharge rates. Such relatively obvious situations, however, are found on land that comprises only a small fraction of the area of the United States. Efforts to protect against future contamination must focus on the much larger areas where relative vulnerability to contamination is more difficult to distinguish. Given this understanding, resource managers have sought to identify areas where contamination is more likely to occur than in other areas. Thus the concept of ground water vulnerability to contamination was developed.
Ground Water Vulnerability to Contamination
As illustrated in Box 1.3 the concept of ground water vulnerability to contamination has different meanings for different people. In its broadest context, ground water vulnerability refers to whether or not an underlying aquifer will become contaminated as a result of activities at the land surface. For the purposes of this report, ground water vulnerability to contamination is defined as:
|
Box 1.2 EPA's Pesticides and Ground Water Strategy Protecting the Nation's Ground Water: EPA's Strategy for the 1990s (USEPA 1991a) articulates the overall goal of EPA's ground water policy as: ''[T]o prevent adverse effects to human health and the environment and to protect the environmental integrity of the nation's ground-water resources; in determining appropriate prevention and protection strategies, EPA will also consider the use, value, and vulnerability of the resource, as well as social and economic values." The inclusion of vulnerability considerations in this policy objective recognizes that uniquely local hydrogeologic and land management practices are significant factors affecting the potential for contamination to occur and thus the need for different types of protection plans that are consistent with local needs and conditions. Based on the policy goals and principles outlined in this strategy, EPA developed a ground water protection strategy specific to the use of agricultural chemicals. The centerpiece of the Pesticides and Ground-Water Strategy (USEPA 1991b) "is the development and implementation of State Management Plans (SMPs) for specific pesticides of concern." An SMP is supposed to describe a state's approach to ground water protection for a specific pesticide based on local differences in ground water use, value, vulnerability, and sensitivity. Thus, as a part of their ground water protection responsibilities, states are strongly encouraged to conduct vulnerability assessments. EPA has taken a differential management approach to ground water protection. The major assumption underlying such an approach is that one can assess vulnerability well enough to reliably identify geographic areas that warrant separate treatment. This fundamental issue is addressed further in the following chapters. |
The tendency or likelihood for contaminants to reach a specified position in the ground water system after introduction at some location above the uppermost aquifer.
Note that this definition of ground water vulnerability refers to contamination resulting from nonpoint sources or areally distributed point sources of pollution and does not address individual point sources of pollution nor any situation where a pollutant is purposely placed in the ground water system. Sources such as landfills and underground storage tanks are not considered because they represent point sources even though they may degrade
|
Box 1.3 The Many Ways of Defining Ground Water Vulnerability Vulnerability means different things to different people. Some view it as an intrinsic characteristic of soils and other parts of the natural environment. Others find that vulnerability depends on the properties of individual contaminants or contaminant groups, but is independent of specific land-use or management practices (e.g., the amount of pesticide applied). Still others associate vulnerability with a specific set of human activities at the land surface. Some authors have attempted to avoid the term vulnerability altogether and have substituted terms such as sensitivity. The following quotes illustrate the diversity in terminology. Foster (1987) Aquifer Pollution Vulnerability - "the intrinsic characteristics which determine the sensitivity of various parts of an aquifer to being adversely affected by an imposed contaminant load." Ground Water Pollution Risk - "the interaction between (a) the natural vulnerability of the aquifer, and (b) the pollution loading that is, or will be, applied on the subsurface environment as a result of human activity." U.S. General Accounting Office (1991) Hydrogeologic Vulnerability - "a function of geologic factors such as soil texture and depth to ground water." Total Vulnerability - "a function of these hydrogeologic factors, as well as the pesticide use factors that influence the site's susceptibility." Total Risk - "This last approach is even broader, for it incorporates the size of the population at risk from potential pesticide contamination—that is, the number of people who obtain their drinking water from ground water in the area.'' Pettyjohn et al. (1991) Aquifer Vulnerability - "The geology of the physical system determines vulnerability." Aquifer Sensitivity - "Aquifer sensitivity is related to the potential for contamination. That is, aquifers that have a high degree of vulnerability and are in areas of high population density, are considered to be the most sensitive …" |
|
U.S. Environmental Protection Agency (1993) Aquifer Sensitivity - "The relative ease with which a contaminant (in this case a pesticide) applied on or near the land surface can migrate to the aquifer of interest. Aquifer sensitivity is a function of the intrinsic characteristics of the geologic materials of interest, any overlying saturated materials, and the overlying unsaturated zone. Sensitivity is not dependent on agronomic practices or pesticide characteristics." Ground Water Vulnerability - "The relative ease with which a contaminant (in this case a pesticide) applied on or near the land surface can migrate to the aquifer of interest under a given set of agronomic management practices, pesticide characteristics and hydrogeologic sensitivity conditions. |
the quality of the ground water over a region. Contamination resulting from brine injection wells, enhanced oil recovery wells, artificial recharge wells, and subsurface nuclear detonations are not considered because they represent purposeful placement of contaminants in the ground water system; it is obvious that any ground water system is vulnerable to such activity. The mobilization of naturally occurring trace elements and salt water intrusion into coastal aquifers as a result of pumping are also excluded. While in many places these sources and pathways may be the dominant cause of contamination, the concept of ground water vulnerability addresses only contaminants introduced by humans above the water table at or near the land surface. Other potential contamination must be addressed on a case-by-case basis using other means.
In certain circumstances, a large number of certain types of point sources—such as septic tank systems—distributed over a region could be considered a regional nonpoint source problem and are included in this definition. Also, cracks and fractures on a regional scale would be considered. In all cases considered under this definition, the contaminant must move at least partially through surficial material. Any mechanism that causes a complete bypassing of this material, such as back siphoning during chemigation, is not directly addressed by the methods examined in this study.
This conception of ground water vulnerability is bounded, as are any others, by a fundamental principle which is stated here as the First Law of Ground Water Vulnerability:
All ground water is vulnerable.
Vulnerability is not an absolute or measurable property, but an indication of the relative likelihood with which contamination will occur; no ground water
(with possible exceptions such as deep sedimentary basin brines) is invulnerable.
An important consequence of the First Law is that the time a potential contaminant would take to travel from the point of introduction to the specified position in the ground water system must be either an implicit or explicit part of any attempt to identify vulnerable areas. A long travel time by itself, however, does not guarantee that an aquifer has low vulnerability. Rather, a key issue is the extent to which processes such as dispersion, sorption, and biochemical transformations are likely to reduce concentrations of the contaminants of interest and/or transform the contaminants to benign products. Thus, it may be misleading to assign low vulnerability to a setting simply because the unsaturated zone is very thick. Dependent on the unsaturated zone materials, if the contaminants of interest are sufficiently persistent and mobile to reach ground water, then they will eventually reach the aquifer. For example, several investigators (e.g., Pratt et al. 1972) have shown that nitrates can take decades to reach ground water. By extension, pesticides that are persistent, but less mobile than nitrate due to sorption, could take even longer.
ASSESSING GROUND WATER VULNERABILITY
Ground water vulnerability is an amorphous concept, not a measurable property. It is a probability (i.e., "the tendency or likelihood") that contamination will occur, and thus must be inferred from surrogate information that is measurable. In this sense, a vulnerability assessment is a predictive statement much like a weather forecast, but for processes that take place underground and on much longer time scales.
An array of methods for predicting ground water vulnerability has been developed. Many of them are based on mathematical models using equations that approximate the behavior of substances in the subsurface environment. These methods are called process-based methods. Another set of methods combine physical characteristics that affect vulnerability in a weighted index or numerical score. A third approach uses statistical methods to draw associations with areas in which contamination is known to have occurred. Generally, the more complex and detailed methods require more complex and detailed knowledge of the system being assessed. Simpler methods incorporate more approximations and are less precise, but require less detailed information about the system being assessed. Although complex methods may describe transport mechanisms more precisely, the data required are often unavailable and must be approximated from limited existing information.
Uncertainty in the Assessment Process
Predicting ground water vulnerability is an imprecise exercise. Information about the subsurface is expensive to obtain, especially over large areas, and assessment methods can only approximate actual environmental processes or other associations. Thus one arrives at the Second Law of Ground Water Vulnerability:
Uncertainty is inherent in all vulnerability assessments.
All of these methods are based on abstractions of reality and are subject to uncertainty as a result of misspecification, misuse, and data errors. Uncertainty is inherent in vulnerability assessments because of limitations in knowledge of contaminant behavior in the subsurface, as well as significant limitations in the spatial databases used to make assessments. Most existing methods convey a misleading impression of the uncertainty of the vulnerability assessment. A consequence of the Second Law is that vulnerability should be expressed in probabilistic terms (i.e., likelihood) that provide information about the unreliability of the assessment.
Different approaches may give vulnerability ratings that do not agree with each other or with observations of ground water pollutants. The model evaluation problem for large areas, or even a field, is especially difficult because the results (i.e., vulnerability ratings) are not subject to experimental verification using normal scientific methods.
Elements of Vulnerability Assessment
It is impossible to formulate a universal technique for predicting vulnerability that considers all of the ways in which contamination occurs. Key elements to consider in a vulnerability assessment for a particular application include the reference location (e.g., the water table or a specified position within the ground water system), the degree of contaminant specificity, the contaminant pathways considered, and the time and spatial scales of the assessment.
Reference Location
Vulnerability may be assessed on the basis of the prediction of the arrival of a contaminant at the water table or at some location within the ground water system, such as a well or the interface between ground water and surface water. Although the water table is used as the reference location in many methods, the potential for contaminants to move elsewhere in an aquifer should also be considered. Important considerations include the locations of recharge zones (places where precipitation on the land surface
may infiltrate downward toward the water table) and discharge zones (places where ground water moves upward toward a stream or other discharge point). For example, the vulnerability assessed using the water table as the reference location may be greater at discharge zones than at recharge zones because the water table is shallower in discharge zones, whereas the potential for contaminants to migrate farther in the ground water system once they arrive at the water table may be significantly greater at the recharge zones. In some situations, water recharging the ground water system may move essentially horizontally along the water table gradient from high to low elevation and discharge at a surface water body or land surface depression. In other situations, the recharge can move substantially downward in the aquifer below the water table. In the former case, the potential for contamination is greatest near the water table; in the latter case, contaminants can spread through a large portion of the aquifer.
Specific and Intrinsic Vulnerability
Vulnerability assessments may or may not account for the different behavior of different contaminants in assessing vulnerability. In general, two types of vulnerability assessment can be defined. The first, specific vulnerability, is used when vulnerability is referenced to a specific contaminant, contaminant class, or human activity. A second term, intrinsic vulnerability, refers to vulnerability determined without consideration of the attributes and behavior of particular contaminants. In practice, a clear distinction between intrinsic and specific vulnerability cannot always be made. Many vulnerability assessment methods do not refer to specific contaminants (and hence are intrinsic); however, many of the parameters used in assessment methods (e.g., organic carbon content) will have different influences on different contaminants.
Contaminant Pathways
Contaminants can enter aquifers by several different means as illustrated in Figure 1.1. In general, vulnerability assessments consider only those types of contamination that begin as downward percolation from a surface source or from sources in the shallow subsurface. Thus, for example, direct entry of contaminants into wells resulting from a spill or back-siphoning during chemigation is not a pathway considered in vulnerability assessment.
Most measures of ground water vulnerability to contamination assume simple percolation from the land surface and ignore preferential flow paths, such as biochannels (root holes and worm holes) and cracks, joints, and solution channels in the vadose zone. These pathways, however, may give
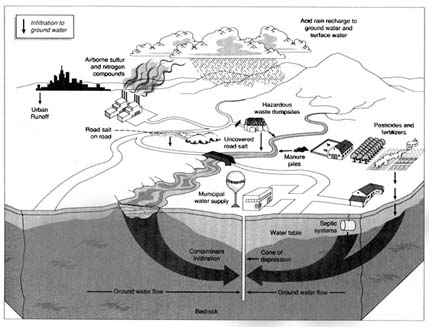
FIGURE 1.1 Pathways by which contaminants may reach ground water.
contaminants a more direct and rapid path to ground water than they would otherwise have. In some cases, considerable potential exists for water to move from contaminated shallow aquifers to deeper aquifers via existing or improperly sealed abandoned wells. Cross-contamination might take place in the wellbore or outside the well casing in an unsealed annulus. It is difficult to incorporate these types of contaminant pathways into quantitative measures of ground water vulnerability, yet they may be the primary control on the vulnerability of deeper aquifers to contamination. One approach is to overlay information on the potential for cross-contamination of deeper aquifers (e.g., sink holes or agricultural drainage areas) on traditional maps of shallow aquifer vulnerability as was done in Iowa (see case example in Chapter 5).
Vulnerability to contamination is commonly treated as a static property although ground water development can have a marked effect on vulnerability by changing the flow regime. Pumpage-induced movement of contaminated shallow ground water into deeper aquifers may be a significant consideration in some situations. Inclusion of these factors into a vulnerability assessment generally entails some level of computer simulation.
Spatial Scales
Often a key product of vulnerability assessment is a map delineating areas of different vulnerability. overall, the utility of different methods of assessment is highly dependent on the scale at which data are available, the scale used to display the results, and the spatial resolution of the mapping.
In general, vulnerability assessments are conducted at map scales that range from 1:12,000 to 1:250,000, although some multistate or larger area assessments might use map scales as small as 1:1,000,000 or 1:2,000,000. The spatial resolution of vulnerability maps depends on the resolution of the databases that are available for characterizing the region of interest. The situation is complicated because spatial databases tend to differ in their levels of detail and accuracy. Thus, it is difficult to make general statements about the resolution of vulnerability assessments. It is likely, however, that the resolution will be coarser than individual occurrences of contamination. Box 1.4 provides some additional information about maps and scales.
|
Box 1.4 Scale, Size, and Maps Vulnerability assessments are performed over areas ranging from the national level, through state, county and hydrologic unit levels, to the field level, where a field is as small as 2 or 3 acres. The degree of resolution required for a vulnerability assessment will depend on the purpose for which it is intended. In addition, factors such as the size of the area being assessed, the level at which information is available, and the capacity to handle information will affect the scale at which an assessment can be done. Table 1.1 shows the ranges of map scales at which different levels of assessment are appropriate. TABLE 1.1 Map Scales and the Corresponding Management Units
|
|
The usage of the cartographer's term "scale" can be confusing. Maps that provide high resolution, such as 1:12,000 and 1:24,000, are considered "large-scale." Maps having a lower level of resolution, such as 1:250,000 and 1:2,000,000, are termed "small-scale." As a point of reference, Figures 1.2a, b, and c show a 3-acre field plot depicted on a 1:100,000, 1:24,000, and 1:12,000 maps, respectively.  FIGURE 1.2a A 3-acre field plot is shown on each of the maps in Figure 1.2a, b, and c. The map in Figure 1.2a is drawn at 1:100,000; the 3-acre field plot appears in the upper right corner. Figure 1.2b is drawn at 1:24,000 and Figure 1.2c is drawn at 1:12,000. A comparison of these figures shows how resolution increases with map scale. |
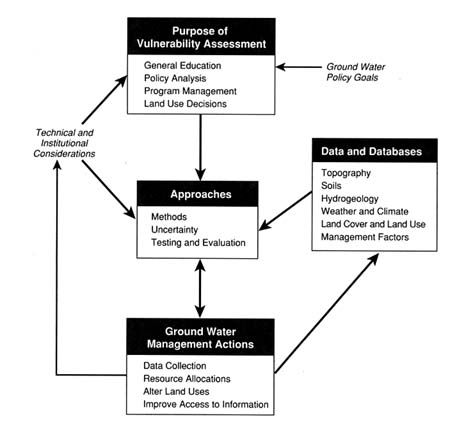
FIGURE 1.3 The vulnerability assessment process.
THE VULNERABILITY ASSESSMENT PROCESS
The flowchart in Figure 1.3 shows the major components of vulnerability assessment, which in general correspond to the chapters of this report. They include: determining the purpose of the assessment; selecting an assessment method, dealing with issues of uncertainty and evaluation; identifying the needs, availability, and quality of data; and eventually using the completed assessment in managing ground water resources.
As the flowchart shows, the approach used to assess ground water vulnerability is central to the process, but is also directly affected by inputs or considerations entailed by the purpose, data availability, and management use of the assessment. The selection and development of a method for vulnerability assessment is not simply a question of appropriate science, but also reflects concerns over the need for the assessment, the availability of suitable data, the level of uncertainty in the model or the data, and the
impact of this uncertainty on the management actions resulting from the assessment.
Ground water vulnerability assessment is a dynamic and iterative process that requires the cooperative efforts of regulatory policy makers, natural resource managers, and technical experts. In performing vulnerability assessments these three groups are united by a common goal: the protection of ground water by the development and implementation of different management practices or policies, based on vulnerability to contamination, that minimize or prevent contamination of ground water resources.
The first step in the process of vulnerability assessment is to identify the purpose of the assessment. As indicated in the flowchart, an assessment's purpose is influenced by a variety of factors including the organization's ground water policy goal, technical considerations (such as the form of the output and the cost of the assessment), and institutional issues (such as the time frame for the assessment and resource availability). Purposes of vulnerability assessments range from improving information and education through analyzing the impact of alternative ground water policies, providing a tool for allocating resources, and guiding the decisions of land users or land use managers. These issues are described in Chapter 2.
The next stage in the process is to select a suitable approach for conducting the assessment. Various methods are available. This stage of the assessment process includes choosing a model or technique for the assessment, identifying the uncertainties inherent in the model and the data needed for the assessment, and testing the model and its assumptions. Each of these issues is discussed in Chapter 3.
Highly related to the performance of an assessment are considerations surrounding the availability and quality of the data required. These data questions influence both the choice of technique for the assessment and the confidence of policy makers and regulators in making decisions based on the results. Issues of data availability and quality are addressed in Chapter 4.
Once an assessment is complete, various management actions may be taken to protect ground water quality or minimize contamination. Management actions could range from altering land use practices, targeting resource allocations, or disseminating vulnerability information through an educational program to collecting additional data on factors relating to vulnerability or ground water quality. Actions based on a vulnerability assessment should be tempered by the uncertainty of the assessment and the confidence of the technical experts in the assessment they have produced. Therefore, the flowchart indicates another iteration via feedback to the boxes concerning the approaches, the data, and technical and institutional considerations. Findings and recommendations on the use and improvement of vulnerability assessments and related research needs appear in Chapter 6.
Case Studies
Chapter 5 of this report presents six case studies, covering a broad spectrum of uses, assessment methods, and spatial scales of analysis. In each study, the selection of assessment methods seems to have been influenced by the availability of spatial databases, ease of implementation, and the perceived credibility or validity of the selected method.
In Iowa, the vulnerability assessments were conducted to acquire improved information that would help develop ground water protection strategies based on voluntary action, but not to support regulatory activities. In contrast, vulnerability assessments are being used in Florida and on Cape Cod to delineate land areas that will be targeted for differential management in order to protect the quality of ground water resources. The assessment conducted by the USDA has a national perspective and is designed to be used as a decision aid in program management and policy development regarding the impacts of agricultural chemicals on ground water quality.
California's approach to ground water protection reflects one end of the spectrum in the types of methods used for vulnerability assessment. The state relies completely on ground water monitoring for regulatory purposes in identifying Pesticide Management Zones. None of the extant vulnerability assessment methods was considered adequate or practical because their associated uncertainties were judged to be too large for use in California. Regulatory action is taken only after a pesticide has been detected in ground water, and pesticide use restrictions are imposed only within the land section where the contaminated well is located. Many of the states (e.g., Florida and Iowa) have adopted overlay and index methods because the required databases were readily available and because these methods could be easily implemented given the resources available. In other cases, (e.g., Hawaii), the use of one-dimensional simulation models that predict pesticide leaching to ground water are being explored as a tool in regional vulnerability assessments. On the other hand, sophisticated three-dimensional ground water flow models are being used to delineate the zones of contribution to public wells on Cape Cod. The USDA assessment technique represents a hybrid approach in that it employs a numerical index based on outputs from a simulation model that are being used as adequate predictors of likely outcomes under diverse conditions. Ground water monitoring networks are being established in many states (e.g., Florida) to track the impacts of land-use activities on regional ground water quality.
The spatial scales at which the vulnerability assessments have been conducted range from the national scale (e.g., USDA), to statewide assessments (e.g., Florida, Iowa, Hawaii), to county-scale evaluations (e.g., Cape Cod). Some of the assessments are based on spatial aggregation of outputs
from simulation models designed to represent field-scale processes (e.g., Hawaii, Cape Cod, USDA).
REFERENCES
Abdalla, C.W. 1990. Measuring economic losses from ground water contamination: An investigation of household avoidance costs. Water Resources Bulletin 26(3):451-463.
Foster, S.S.D. 1987. Fundamental concepts in aquifer vulnerability, pollution risk and protection strategy. Pp. 69-86 in Vulnerability of Soil and Ground water Pollutants, W. van Duijvenbooden and H.G. van Waegeningh, eds. The Hague, The Netherlands: TNO Committee on Hydrological Research Proceedings and Information No. 38.
Haley, J.L., B. Hanson, C. Enfield, and J. Glass. 1991. Evaluating the effectiveness of ground water extraction systems. Ground Water Monitoring Record Winter:119-124.
Mackay, D.M., and J.A. Cherry. 1989. Ground water contamination: Pump-and-treat remediation. Environmental Science and Technology 23(6):630-636.
Office of Technology Assessment (OTA). 1990. Beneath the Bottom Line: Agricultural Approaches to Reduce Agrichemical Contamination of Ground water. Washington, D.C.: U.S. Government Printing Office.
Pettyjohn, W.A., M. Savoca, and D. Self. 1991. Regional Assessment of Aquifer Vulnerability and Sensitivity in the Coterminous United States. Washington, D.C.: U.S. Environmental Protection Agency.
Pratt, P.F., W.W. Jones, and V.E. Hunsaker. 1972. Nitrate in deep soil profiles in relation to fertilizer rates and leaching volume. Journal of Environmental Quality 1(1):97-102.
U.S. Department of Agriculture (USDA). 1987. The Magnitude and Cost of Ground water Contamination from Agricultural Chemicals, A National Perspective. Staff Report AGES870318. Washington, D.C.: U.S. Department of Agriculture, Environmental Research Service. 54 pp.
U.S. Department of Agriculture (USDA). 1989. Agricultural Resources: Inputs, Situation and Outlook. Washington, D.C.: U.S. Department of Agriculture, Economic Research Service.
U.S. Environmental Protection Agency (USEPA). 1987. Agricultural Chemicals in Ground Water: Proposed Pesticide Strategy. Washington, D.C.: U.S. Environmental Protection Agency, Office of Pesticides and Toxic Substances .
U.S. Environmental Protection Agency (USEPA). 1988. Pesticides in Ground Water Data Base: Interim Report. Washington, D.C.: U.S. Environmental Protection Agency.
U.S. Environmental Protection Agency (USEPA). 1990. National Survey of Pesticides in Drinking Water Wells, Phase I Report. Washington, D.C.: U.S. Environmental Protection Agency, Offices of Water and Pesticides and Toxic Substances. EPA 5709-90-0-5.
U.S. Environmental Protection Agency (USEPA). 1991a. Protecting the Nation's Ground Water: EPA's Strategy for the 1990s. Washington, D.C.: U.S. Environmental Protection Agency, Office of the Administrator.
U.S. Environmental Protection Agency (USEPA). 1991b. Pesticides and Ground-Water Strategy. Washington, D.C.: U.S. Environmental Protection Agency, Offices of Pesticides and Toxic Substances.
U.S. Environmental Protection Agency (USEPA). 1993. A Review of Methods for Assessing Aquifer Sensitivity and Ground Water Vulnerability to Pesticide Contamination. Draft. Washington, D.C.: U.S. Environmental Protection Agency.
U.S. General Accounting Office (GAO). 1991. Ground water Protection: Measurement of Relative Vulnerability to Pesticide Contamination. Washington, D.C.: U.S. General Accounting Office. GAO/PEMD-92-8.
U.S. Geological Survey (USGS). 1990. National Water Summary 1987—Hydrologic Events and Water Supply and Use. U.S. Geological Survey Water-Supply Paper 2350. 553 pp.