2
Making Technology Work: Individual and Organized End Users
This chapter focuses on end users and the technology foundations they need in order to gain the benefits of the national information infrastructure (NII) in their everyday lives. Additionally, it describes how the absence of definitive information regarding end-user preferences is a major source of uncertainty that infrastructure providers must factor into their deployment decisions. As a starting point for analysis, it addresses these questions: How is demand for access evolving? How does the end user access what he or she wants? What equipment and systems compose the end user's means of access? How does private industry translate what it knows about the above into decisions regarding technology deployment generally?
Who Is The End User?
The end user of the NII is potentially every man, woman, and child. The end user may be the person at work using a networked computer environment; the person at home doing on-line shopping, sharing ideas with fellow hobbyists, or collaborating on a work project with remotely located colleagues; a child accessing material in a library, sending homework to a teacher, or playing a game; a traveler changing an airline reservation; the household that has an energy conservation system; or the realtor who relays facts, pictures, and bid and contract details for a house to prospective buyers. Box 2.1 lists some of the categories of usage. User applications range from the critical to the trivial. As the January work-
|
BOX 2.1 What Do Information Infrastructure End Users Do?
|
||||||||||||||
shop and May forum made clear, there is no consensus on precisely how or to what extent end users will make use of evolving information technology capabilities—no consensus on demand. Nor, in the absence of expressed demand, is there a consensus on how large a fraction of U.S. households currently can access desired levels of services. Ross Glatzer, past president of Prodigy, noted that experience with on-line services emphasizes the role of communications as the foundation for how services are used, with information offerings and on-line transactions tightly integrated. He cautioned against overemphasizing any one type of activity or assuming that delivery of information and content will dominate.
While this view projects a continuum of uses for the NII, one particular issue shapes many of the specific considerations in this report—the distinction between the worker in the corporate setting or large institution and the end user in the small business or in the home. This distinction seems to have polarized the planning of many business sectors, including that of some of the facilities providers. In the near term, there will continue to be differences in the equipment and support available to different broad sets of users: large and small business users in the office or home will use computers and telephones, not television sets; they may use laptops or other computer equipment purchased by their employer, as well as business software or specialized systems to support remote work.1 As discussed below, they have very different needs for their communications infrastructure, requiring such features as more accessible bandwidth to and especially from the home, continuous access with multiple ongoing connections at once, and different sorts of communications security. Over the long term, the distinction between home and small business users and users in large businesses and institutions will disappear as people work increasingly from the home. The trend toward self-employment, typically home-based, is strong, and the very small business and the home are similar in terms of expertise, purchasing power, space, and other attributes.2
In some instances, there are signs of overlapping uses of information technology for business purposes across home and office. For example, Stuart Wecker of Symmetrix Incorporated observed that ''it is hard for me to tell what is a business user," noting that people now install second lines in residences at higher than expected rates. Moreover, the increasing exposure to computing and networking in work, study, and other institutional contexts will both broaden the customer base and lead to the use of tools mastered at work or in school for other than business-related tasks.8 The explosive growth of experimentation, particularly in the context of the Internet, underscores how the simple pattern of an end user at home performing the same work-related tasks as otherwise would be done at a
place of employment does not capture the full range of transference of information technology-enabled capabilities.
Why The NII Must Reach The Home
Particularly in plans for technology deployment to and network access for the end user in the home, the steering committee found areas of uncertainty and confusion. In one view, advanced network services will penetrate into the home because some one application is so important and desirable that it alone can drive the economics of deployment. This "killer app" economic model has, for residential networking, most commonly anticipated entertainment services as the dominant driver. But the problem with the "killer app" metaphor is the expectation that one activity will saturate the market.3 Communications and content providers contributing to the NII 2000 project did not quantify the analysis, but their comments suggested that an application need only capture a significant percentage (even 10 percent) of the national market for telecommunications to justify the necessary facilities investments.4
Entertainment has appeal as a "killer app" for residential use for several reasons, including the obvious one that broadcast and cable are in the entertainment business already and understand it.5 As a result of their efforts, the principal application of communications technology for the nonworking home consumer has been television entertainment. Even for sectors such as telephony that are only contemplating entering the entertainment business, there is a proven market that can at least justify financial speculation. Home entertainment is an important segment of the U.S. communications industry (see Figure 2.1)6 and will continue to grow with the transition to digital technology. As a set of businesses, however, home entertainment represents only a small percentage of the U.S. economy. One reason is that strictly personal use of information infrastructure for entertainment is a function of disposable personal income (including competing demands on household resources) and discretionary time.7 By contrast, business-related use depends on the shift of activities to the home that traditionally or otherwise require a person to be at a different and specific location—literally, a place of business.
The perceived inability of providers to construct a business case for investing in residential information infrastructure in the absence of a "killer app" was a basis for frustration expressed by representatives of various business domains. As examined in Chapter 3, comments from infrastructure builders (excluding cable and terrestrial broadcast television providers) indicate that they are slowing their investments for fear
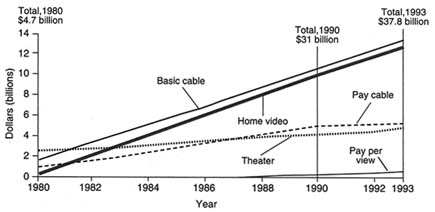
FIGURE 2.1 Consumer spending on entertainment, 1980 to 1993. SOURCE: "The NII in the Home: A Consumer Service," a white paper contributed to the NII 2000 project by Vito Brugliera, James A. Chiddix, D. Joseph Donahue, Joseph A. Flaherty, Richard R. Green, James C. McKinney, Richard E. Ottinger, and Rupert Stow. Data from P. Kagan.
that home entertainment may not yield a sufficient return after all (Mills, 1995c). Pessimistic about consumer market prospects, Paul Green of IBM's T.J. Watson Research Center concluded that "the only way that I see that we are ever going to be able to get fiber to the home, barring some discovery of the 'killer app,' is via smaller and smaller businesses installing their own private fiber or renting it from the telephone company. Eventually it will just become slowly democratized." For user domain representatives, it was one matter to hear about infrastructure being built for what they felt was the wrong "killer app"; it was quite another for them to hear that it might not be built for many decades, given that the speculative "killer app" might be dead on arrival.
Evidence of growth in the amount of business that will be conducted to and from the home supports the conclusion that the vast majority of information infrastructure use will involve interaction with industries and government: finance and banking, health care, government services (benefits, information, taxation), manufacturing, and dozens of other domains, each of which has, to varying degrees, been assimilating networked infrastructure into a variety of business processes. Inputs from these sectors indicated that business uses in the home, and not leisure uses, should be driving the plans for deployment of bandwidth to the home. This insight is consistent with the slow rollout of fiber reflecting expectations for communications traffic based primarily on conventional use of
telephony (see Chapters 3 and 5). It is not clear, however, whether slow deployment of non-television bandwidth reflects anticipation of gradual growth in the market for miscellaneous business uses, or instead reflects lack of recognition of the eventual market role of these uses. The small body of current knowledge about deployment of application services compounds the uncertainty. Over the long term, however, business-use financing (treating infrastructure as a cost of doing business) should be at least as important as consumer financing in driving deployment (see "Economic Models" in Chapter 3). Overall, business uses will drive the deployment of information infrastructure because they give rise to interactions that will take place in large institutional settings, small business settings that resemble homes in terms of resources, and homes.
Together, inputs from infrastructure suppliers and users suggest that no one application domain is expected to drive more than a small percentage of the activity on the NII. Further, the evolution of different product and service elements—such as voice telephony, electronic mail, and various forms of video distribution—is too uncertain to allow reliable predictions about which, if any, might dominate. It is the steering committee's view that NII technology deployment will be driven by the collective needs and aggregate economics of many domains. In other words, the search for a holy grail of information infrastructure does not lead anywhere, but everywhere.
Evolving Demand For NII Capabilities
User familiarity with information technology and user demand for NII capabilities will co-evolve, a process that will take time and that may also yield unanticipated results.
8 9 The beginning of such a co-evolution is evident in people's increasing willingness and ability to talk about the Internet, as well as in other indicators that user involvement is greater today than a year ago and still growing:10 more people using information technology at work, school, and at home; more advertisements, articles, and business cards including links to a network or World Wide Web (Web) address; and more movies, popular books, and other mainstream media with computer and networking themes.
Yet making the transition from interest in and acquaintance with information technology to fuller acceptance, implementation, and use is not necessarily a natural process. In many instances, end users do not quite know what they want,11 and their perceptions often differ by age. Further, it is difficult to make full use of technologies whose potential end users cannot imagine when they are still unfamiliar with the technology.12 Additional barriers to widespread implementation are both technical—how to incorporate legacy systems, how to ensure interoperabil-
|
BOX 2.2 Electronic Commerce and Legacy Systems The electronic commerce domain has a large quantity of legacy systems which it needs to interface to, and ultimately phase-out of as it evolves to more modern systems, applications, and processes. These legacy systems and processes (e.g., paper checks, mainframe-based settlement and payment systems, and electronic data interchange value-added networks) will not go away overnight, and a successful electronic commerce infrastructure must allow the user to easily and transparently transfer between and switch back and forth between the new all-electronic and the older, hybrid legacy systems and processes. —Daniel Schutzer, "Electronic Commerce" |
ity—and cultural. Daniel Schutzer (in a white paper) and others underscored the difficulty of accommodating legacy systems in the near term to facilitate communication among different domains (Box 2.2) as the information infrastructure evolves. White papers by Thomas Rochow et al. and by Robert Mason et al., for example, commented on difficulties with introducing use of information technology in manufacturing that are also applicable across the board to the several user domains examined during the course of the NII 2000 project (see Box 2.3).
A majority of user domain representatives at the workshop and forum indicated that the primary issues inhibiting greater NII use were not infrastructure-specific. In fact, several of the speakers commented on their satisfaction with current communication services, and it is also the case that networking in at least some form is being used increasingly in essentially all industries and sectors (see Box 2.4 and Chapter 5 for observations on business networking trends). Enormous opportunities for savings have long been part of the appeal of business networking applications such as electronic data interchange (EDI) and also underlie, for example, power-utility investment in energy demand management systems as discussed in the white paper by John Cavallini et al. Widespread implementation and use of information technology, however, are complicated by ongoing fundamental changes in nearly every user domain that have as much to do with the information itself as with how it is communicated. In the 1980s, for example, EDI attracted attention as an advance beyond internal corporate networking to support interenterprise communication using standardized trade-related documents. In the 1990s, discussions of electronic commerce have reflected extensive changes in activity within and among enterprises and individuals that now have greater flexibility in exchanging information. Current accounts of indus-
|
BOX 2.3 Adaptation to the Use of Information Technology in Manufacturing Nothing is harder to facilitate than the change of a work process. This is cultural change, often a change from what has been a successful process in the past. Human beings, perhaps as a result of a built-in predisposition to protect the species from the unknown, are strongly resistant to change. —Thomas C. Rochow, George E. Scarborough, and Frank David Utterback, "Electronic Integrated Product Development as Enabled by a Global Information Environment: A Requirement for Success in the Twenty-first Century" … [T]here is concern that the learning cycle for small manufacturing enterprises (SMEs) … to implement information technology is too long and too costly for them to effectively make the transition to the NII environment. The solution to the problem is not simply one of assuring that every SME can purchase and install a new information system. Instead, the solution requires an understanding of how a complex combination of structural, technical, managerial, and economic factors affects the diffusion of information technology in SMEs and puts at risk a significant component of the nation's manufacturing base. —Robert M. Mason, Chester Bowling, and Robert J. Niemi, "Small Manufacturing Enterprises and the National Information Infrastructure" |
try and sector-specific problems concern how different industries conduct business and/or evolve, both in terms of overall structure and business processes and in terms of the assimilation of all kinds of information technology into those processes.13 14
Within each domain the barriers differ, but contributors to this project delineated some broad themes. Data formatting standards and legacy systems are pervasive concerns. Difficulties have surfaced in the context of EDI, collaborative databases, and other applications that involve document handling and exchange, and the white paper by Stephen Zilles and Richard Cohn speaks, for example, of the need for standards to support all steps of document use—production, viewing, reading, reusing, annotating—and links standards to architectures. Another cross-cutting concern is labeling and identifying people, places, and organizations, as Ed Hammond points out in a white paper. Yet another related concern is lack of cohesiveness within industries and organizations themselves. Richard Sharpe of the Hartford Foundation explained at the January workshop that health care "information is totally fragmented. The business is
|
BOX 2.4 Demand for Networking in the Business Domain
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
not a system. It is a cottage industry, with each cottage having a different approach to the netware."
In addition, the cultural metamorphosis required in the transition to use of information technology within each of the several user domains is a reality that telecommunications providers must factor into their deployment decisions, according to project participants. Several speakers at the
forum noted that infrastructure providers' involvement in helping end users to accept advanced communications capabilities and use them in new ways might accelerate the demand for services. As Thomas Rochow of the McDonnell Douglas Corporation pointed out with regard to manufacturing, "We are talking about a sector of our economy that really has to learn how to crawl before we can walk and then run. If you help us do that, you might be surprised that we can help you co-evolve with us for our mutual benefit." Fostering the adoption of information technology is arguably a task for both the user domains and the facilities providers, given that infrastructure providers have a business interest in being responsive to customers' needs. From the providers' perspective, each application domain has its own language, perspective on its problems, and need for a somewhat tailored approach—all factors that can slow progress.
Whether or how well assimilation proceeds, it may also pace the rate of market growth, inasmuch as it speaks to the problem of market penetration in a given domain. In their white paper, Mason et al. note that smaller manufacturing enterprises that may be only at the beginning of the so-called "learning curve" are responsible for up to nearly 40 percent of the nation's manufacturing employment. Richard Sharpe remarked, "Health care is a sleeping giant. This is a major sector, a trillion-dollar business opportunity for you folks who are selling your wares."
Variations in requirements imply, in particular, that there is no coherent voice through which users can express their needs up front. It also implies that no one domain may have sufficient clout to sway investment choices one way or another to meet its needs. Thus, when infrastructure builders aim for a constituency that represents a common denominator or compromise among different flavors of demand, it is easy for users in any domain to feel that "they're not talking to us."
The lack of specific requirements or variation in perceived requirements could be a problem for those who must decide what infrastructure to build through processes involving up-front commitments to long-lived facilities characterized by economies of scale that are paid back through volume use. As David Messerschmitt of the University of California at Berkeley observed at the forum:
Do the needs of various user groups, such as doctors and hospitals and Joe Six Pack, differ radically? If so, we need to think of perhaps different network solutions that are somehow "gatewayed" for these different communities. Or are their needs actually very similar, and not different enough to justify that segmentation, so that we can benefit from the economies of scale of defining a more homogeneous NII network infrastructure?
The discussion here (see Chapters 3 and 4) does not conclude that separate networks are required.
The End User As Consumer
In the effort to stimulate consumer demand for information technology, affordability, ease of use, and interoperability of available devices stand out as basic considerations. Affordability is a concept that applies to a product's entire life cycle; it includes both the initial purchase price and other costs incurred over a relatively long expected period of use (consumers generally cannot recover the costs of their durable goods in the same way that businesses can recover the capital of past investments and invest it for modernization15). Joseph Flaherty of CBS Incorporated summed up the situation as follows: "So while the network questions might be bandwidth, bandwidth, bandwidth and access, access, access, the consumer questions are cost, cost, cost and life, life, life of the facility."
Project contributors associated with television manufacturing and services emphasized the consumer experience with electronics: relatively low price points, long-lived products (especially in the case of the more expensive items), and compatibility. In contrast, contributors associated with the computer industry observed that consumers are investing in personal computer (PC) equipment even though it costs more than entertainment devices, although given the relatively high initial costs, customers are unlikely to upgrade regularly.
Costs for equipment are only part of the challenge in increasing consumer demand. Another is the price of service. While broadcast television involves no service charge, Brugliera et al. note in their white paper that basic cable service averages about $300 per year and premium channels an additional $100 per year each, levels that consumers are aware of and can factor into their expectations. Average monthly rates for basic telephone service, according to Federal Communications Commission (FCC) statistics, are about $11 for residential customers and about $43 for single-line business customers (FCC, 1994, pp. 304-305).16 In contrast, online service pricing has been volatile, currently averaging around $10 per month for about 10 hours of "basic" service. Price levels affect willingness to move from one pattern of consumption to another (e.g., from videocassette rental to use of video on demand) and to use new kinds of products.
In addition to the issue of overall cost are the issues of predictable cost and easy payment for services, as emphasized by Leonard Kleinrock of the University of California at Los Angeles in the context of nomadic computing needs, which combine portable and alternative computing and communications arrangements (see Box 2.5). The features sought by
|
BOX 2.5 Predictable and Easy Payment I do not want to make a query out over the network and have a 15-megabyte videoclip downloaded to me on my 14-kilobit modem. I want to be warned about the cost in time, delay, dollars, and storage and maybe get some approximate picture, maybe just the title of the picture, or fuzzy image, or a slower frame rate. In order to create this, we need a variety of capabilities. We need the ability to handle replication services, file synchronization, predictive caching, adaptive database management, location services, tracking of people, devices, resource discovery, and profile discovery. In order for me to use [the telephone system] anywhere, all I need is coin of the realm and an empty telephone booth. I do not have to identify myself, register ahead of time, or pay for it ahead of time; I just go and use it. —Leonard Kleinrock, University of California at Los Angeles |
Kleinrock imply corresponding accounting mechanisms—well established for telephony and various subscription television services but currently in flux for computer-based services.
Growth in consumer acquisition and use of PCs provides evidence that at least more of those who can afford to purchase PCs are opting to do so. At the January workshop, Tora Bikson of the RAND Corporation cited research showing that the proportion of income spent on access to PCs or access to network services has increased (Anderson et al., 1995). Similarly, the growth of cellular telephony suggests a willingness to alter household budgets to cover the cost of a valued service. The cellular pricing structure, which makes handsets very cheap and calls quite expensive (though prices are beginning to fall), gives people the opportunity to experiment with using the service. Growth in volume suggests that many find it more useful than they expected, fueling the transfer of this technology from business-financed use to more personal use.
In addition to cost, ease of use was described by project contributors as a primary consideration in consumers' willingness to use information technology. The white paper by Oscar Garcia discusses the issue. The user interface is clearly a crucial component in information technology use and one for which research could bring needed improvements (see Chapter 6 for a discussion of research needs). Experience with telephones and televisions, which are generally recognized as easy to use, illustrates that user interfaces can be tailored to a single use. Similarly, the common wisdom on fax is that it was accepted because it had a single-use interface and worked over telephone lines. In contrast, tasks associated with more
complex and emerging service objectives such as accessing and using the Internet are still perceived as complicated, with more variables and harder-to-use interfaces.17
Although technology advances have enabled dramatic improvements over the last several years, the general-purpose PC is not yet as easy to use as either the television or the telephone, largely because many of the tasks to be performed with the PC are intrinsically more complex. This is a significant barrier for many, and is likely to be one for many years to come.
Some of the difficulty in learning to use new technology is being offset by the emergence of new service businesses that offer, for example, the capability of hosting Web pages for customers who do not want to configure and operate their own Web server. Such businesses provide the storage for Web pages, as well as the service that translates the names for the Web pages (the universal resource locators) into the appropriate address on the network. Customers pay monthly fees for such services. Other service providers intend to sell a turn-key capability that a client can install to operate a Web server.
Despite the need for continued improvement in ease of use, it is important to emphasize that expectations for user friendliness should not be unrealistic. A local, consumer market assumes that people will know what to do with the capabilities available. The basic user will be able to accomplish a great deal with navigation tools built into current and future television services, for example, but skillful use of interactive environments, beyond entertainment applications, will require training—which is already taking place in the corporate setting, in social groups for adults, and in the schools, especially for the next generation of users.
Elaborating on Paul Green's characterization of the popular desire for ease of use as a point-click-results capability, Irene Greif of the Lotus Development Corporation suggested the need to prepare for a greater level of sophistication by building systems that accommodate the sophisticated as well as the limited:
We do not want to build user interfaces so simple that the user who needs to undertake a more complex task, for example to issue a sequence of requests—some of which depend on the outcome of previous requests—cannot do so at all. A simple point-and-click interface cannot easily express these more complex objectives.
Another issue for providers is responding to the need for access to the same information from different user interfaces. People have different sets of skills for finding and visualizing information, and they need different user interfaces to allow them to make the best use of those skills. Group systems that take into account users' varying capabilities can be
very valuable in making teams more productive and smoothing out the problems inherent in people seeing things differently.18 Different kinds of interfaces may also be needed to support access by people with certain physical limitations. Of particular concern are the vision-impaired, whose needs are not addressed by the many activities aimed at producing a more visually rich interface, whether via television or PC.
Access Devices
In homes, the three main access devices deployed at this time are the telephone, the television (TV), and the PC. Ninety-four percent of U.S. households have a telephone (FCC, 1994, Table 8.1), about 97 percent have a TV (McConville, 1995; Veronis, Suhler, 1995, p. 313), and 32 percent have a PC (Veronis, Suhler, 1995, p. 313). At work, the access devices are telephones and PCs. On the road, it is again the telephone (perhaps wireless) and the portable PC, with TVs ubiquitous in temporary accommodations. Communication occurs over public and private networks. It is logical to start with this installed base to understand how people will access future information infrastructures, even though current devices will evolve over time.
The ''inevitable" merging of the various access devices into one, either the TV or PC, has been forecast. Notable in the January workshop, however, was the expectation among participants from the computer, television, and telephone industries that these access devices would coexist, albeit with an increasingly powerful and flexible set of capabilities. Despite interest in speculating about futuristic consumer devices, the roles of the principal access devices are not likely to change for at least several years. The PC-TV combinations now coming onto the market appear to be basically a PC with augmented capabilities for television reception. The television is not becoming a PC, although the PC may be used as a television (and also as a telephone).
Given the enormous installed base and the substantial volumes of existing devices that will be delivered in the next several years, it is likely that televisions, PCs, and also telephones will remain the only access devices deployed in enough quantity to qualify as consumer items. Changes will take place, but, as has been seen before, a new service will not completely supplant an established one: as television service emerged, for instance, radio service did not die, because it had a well-defined set of user modalities that continued to provide value; as television emerged, movies did not disappear. The PC is a new medium whose capabilities can be exploited to provide new services, such as those associated with the Internet, as well as mature services whose operators understand and know how to capitalize on PC capabilities.
The Personal Computer
Given the various uses anticipated for the NII—including work, learning, business and commercial transactions, and entertainment—the PC's role as an access device will become increasingly important (see Box 2.6).19 Close to 60 million PCs were deployed in the U.S. workplace at the end of 1994, with close to 80 percent of them connected to a network (IDC, 1995f). About 32 million were deployed in the home. 20 Millions of portable PCs are used by mobile workers. The most rapidly growing industry segment is the installation of PCs in the home (Business Week, 1995).
The PC's importance for access to current and future information infrastructure raises concerns particularly about cost and ease of use. Consumers now pay about $2,000 for a new computer, a price that has increased slightly over the last several years—as has the volume of PCs purchased. Current industry trends are to keep prices relatively constant while delivering increasing power and capability in the machine. Improvements in processor design and integrated circuit manufacturing techniques have consistently lowered the cost for a given amount of memory or processing power,21 a trend likely to continue. These added capabilities are important both in improving ease of use (graphical user interfaces, for example, require substantial processing power and memory) and in delivering multimedia capabilities.
Although the PC thus provides the greatest and most general capability among the common access devices, as an access device it is relatively expensive. Consequently, the computer industry continuously asks the question, Can we create a useful, under-$500 access device? Such a "Model T" or "Yugo" could boost the household penetration rate of PCs closer to 80 percent. To date, no such device has proved popular, in part because the compromises required in features and capabilities would be severe, but companies are experimenting with limited-feature, low-price devices, and their experiences will help calibrate the market.22 The improvement in features at an approximately constant real cost will likely pace the replacement (or augmentation) rate. Compounding the costs for equipment and software purchase are other costs relating to network access and support, which may raise the effective cost of a networked PC to several thousand dollars, or in large institutions, tens of thousands of dollars.
Given the expectation that PC costs will remain relatively constant at about $2,000 per system, what steps can be taken to ensure that the widest possible cross section of society benefits from this technology? 23 What is likely to happen has an analogy in how needs for transportation are satisfied: while not everyone owns an automobile, most have access to transportation. Similarly, electronic access to information is being made avail-
|
BOX 2.6 The Growing Role for the Personal Computer
|
||||||||||||
able increasingly in libraries, schools, business establishments, and other public centers where PCs can be utilized by many. Kiosks provide a means for access in public places, although usually for a specified set of services accessed through specialized interfaces (and with less privacy than is possible in the home or individual office).
The Television
About 97 percent of all U.S. households have a television, and about 62 percent out of those have cable service (McConville, 1995). Television is clearly a ubiquitous access device, one that provides communication services for substantial periods of time. It is part of our culture; much of our entertainment and information comes from watching television. With the widespread use of cable services, there is also an existing infrastructure to manage the interaction between users and service providers. Consumers can purchase premium services, either on a monthly basis or on impulse, via the set-top converter, which is the gateway between the television and the cable service providers.
Terrestrial broadcast television uses wide bandwidth that potentially could help to enable other services, via broader access to the bandwidth. The greatest source of bandwidth to the home is terrestrial TV, but its 6-MHz channels provide 20 Mbps only for one-way communication into the home, supporting only a fraction of the activities that can leverage the NII. Broadening of access is more evident in cable television. As digital video transmission is deployed, cable service providers will be able to increase the capacity of their networks and will also be able to offer additional, including interactive, services. In such an environment, a customer would be able to access (purchase) content—such as video programming—more or less on demand from a server. The set-top box will play an increasingly important role and will likely go through rapid technological evolution over the next several years.
The likely first step in migrating toward such an environment is the evolution of existing cable systems to hybrid fiber coaxial cable (hybrid fiber coax; HFC) systems, as discussed in Chapter 4. The use of HFC will allow the coexistence of digital and analog signals and will enable two-way, asymmetric transmission of digital data (NIST, 1994c; Hodge, 1994). This is a basic infrastructuren capability that, if properly deployed, will allow the network to connect a number of access devices: television (via set-top box), the PC, and the telephone. While some in the industry would like to see a quick migration to an all-digital delivery paradigm, the television community is concerned about the migration path from analog to digital transmission, combined with the rise of interactivity. In a white paper, Allen Ecker and Graham Mobley voice the expectation that digital set-top boxes will "also have analog tuning capability because you do not want to do away with the analog services that are currently providing most of the revenues that cable systems enjoy, and most of the consumer demand at the current time." Advanced analog set-top boxes have the capability of sending digital applications such as on-screen displays of program guides, virtual channel information, and other digital
data along with the analog video and audio. This capability allows an analog set-top box to bridge the gap between analog and digital services that will evolve in the future.
As the television industry moves forward, costs will increase. Television equipment will continue to become "smarter," requiring processing power, memory, and software. Furthermore, modulation techniques to support digital video transmission require high-performance and complex integrated circuits. The cost of such equipment is several times the cost of current set-top boxes. It will take many years before cost goals acceptable in the consumer market will be realized. In the meantime, modest steps are possible such as expanding the channel capacity by the addition of digital delivery to the current analog service.
In summary, an upgrade of the cable plants to HFC, coupled with the development of advanced consumer systems, should allow for advanced television services and an expanded use of broadband networks reaching the home. While this will provide added business opportunities for the service providers, it is highly likely that the role of the television will continue to be what it is today: an entertainment device (CSTB, 1995c).
Advanced Television
Digital television channels provide more broadcast capacity as well as increased data bandwidth in the available spectrum. They make use of compression techniques to allow up to four times the usual number of program streams to be transmitted within a single broadcast channel bandwidth. In addition, efficient channel utilization is likely to link digital high-definition television (HDTV) transmission with unused data stream capacity that could be used for transmission of additional programming or a data service.
HDTV has been the subject of significant levels of corporate and research investment in recent years. It is also the subject of FCC activities in terms of both standards setting and spectrum allocation. Experts are divided about the future of HDTV per se, with some believing that it will provide a very attractive human interface and set of capabilities and others foreseeing a much less significant role. The steering committee generally discounted the impact of HDTV as a force shaping communications and information-related behavior and markets for the next 5 to 7 years, given HDTV's high initial prices and very limited sales, and believes that it will be even longer before a significant amount of HDTV-compatible programming will be available.24 Even then, the steering committee considered the availability of new spectrum for other uses to be more important than the availability of a higher-fidelity television viewing experi-
ence, In the meantime, TV programming displays on PCs are growing, presenting prospects for enhancing and otherwise using those images.
The Telephone and Other Access Devices
With about 94 percent of all U.S. households having telephone service, telephones rival televisions as the most widely used device for gaining access to the NII and will continue in that capacity for the foreseeable future. Although the functionality of a telephone can be found increasingly in PCs and its eventual integration into television and set-top box installations has been variously proposed, it is unlikely that such developments will affect the widespread installation of telephones. The telephone is an inexpensive and highly versatile consumer device that has become an integral part of our lifestyle, and the ongoing introduction of a variety of telephone-based services further increases its functionality.25
Cellular and personal communication service (PCS) telephones now provide increasing communications mobility to a broadening slice of society.26 Initially expensive business tools for senior executives, real estate agents, and other business managers who must operate untethered to landlines, cellular telephones are now becoming commodity items for the general consumer; PCS "telephones" are expected to follow suit. Over time, these telephones, too, are becoming "smarter," linking into computer networks for data access or for basic telephony over broad regions of the world that have central billing.
Combining a range of computing and communications features in a highly portable package, personal digital assistants (PDAs) promise to provide "anytime, anywhere" communication capabilities of a broader nature than can be found in pagers or telephones or a hybrid of the two.27 If that promise can be realized, then PDAs may constitute a cheap ($200) PC with communications capability. Greater support for wireless, mobile systems may spur development and use of such small systems, although their impact may be limited in this decade.28
Toward a Fully Integrated Home System
An important question is how the three separate classes of access device—the telephone, the television, and the PC—will interconnect and interoperate with the various networks coming into the home. Currently, there is no clear or consistent model for how (or even whether) to achieve interconnections): the consumer must obtain a separate interface unit for each access device being connected to each type of network. A PC requires a stand-alone device (a voice modem, an integrated services digital network (ISDN) interface, or (now emerging) a modem for the cable net-
work); a television requires a leased or purchased set-top box, satellite decoder box, or simple antenna to receive television signals. The consumer must hook all these pieces together correctly. This task is, at present, a significant source of user frustration that is often compounded by the failure of the various parts to work well together. For example, televisions cannot offer advanced features such as "picture inside the picture" through many set-top boxes.29
Any business sector that provides infrastructure components must work to ensure that there are suitable standards and interconnection interfaces in place so that the consumer can assemble a system from parts or pay an expert to provide the assembly service. Failure to provide and implement such standards is perceived as a barrier to market penetration (see Box 2.7), yet premature standardization also remains a concern. Some industry players see the set-top box as evolving to serve as a central point of interconnection for all networks and applications. This capability would require that the set-top box (which might at that point be too large to actually sit on top of a television set) have some internal modularity so that interfaces to different networks could be plugged into it, much as network interface cards today are plugged into a PC. See Box 2.8. Other project contributors cautioned against projecting the characteristics of today's set-top boxes into the future. General Instrument's Quincy Rodgers noted that set-top boxes divert attention from "the real issue, which is where different functionality is to be performed in a network." Additionally, Robert Aiken of Lawrence Livermore National Laboratory questioned whether "what gets deployed [in the home] becomes a separate choice from what gets deployed in the access network."
A well-elaborated concept for staged evolution toward home-based integration is offered in the white paper by Ecker and Mobley. They describe the potential for a two-part home communications terminal (HCT)—one part specific to the particular network (network interface module) that could be rented and one general part that could be purchased with features to meet the needs of the consumer (see Figure 2.2). 30 In the forum, Mobley explained that a network interface module would be necessary "in order to come up with a box that a consumer can buy and know would be compatible in the future." The final phase of integration would be a fully integrated home unit or home set of equipment that would connect broadband PC modems to the cable system, provide for power consumption monitoring, support telephony, and provide access to digital interactive entertainment. According to Ecker and Mobley, the rate at which full integration occurs will be governed by a number of factors, including migration to digital transmission, development of multimedia operating systems and user interfaces to support multiple applications, design for "full interoperability at critical interfaces and [to] oper-
|
BOX 2.7 The Need for Consumer Interface Standards Consumers have a very interesting habit. If the industry is confused, think about how confused consumers are. They simply sit on their wallets. If we want to make the NII useful, we have got to deal with standards. —Vito Brugliera, Zenith Electronics Corporation There will be opportunities for communication of applications between appliances within the home. That means that whatever we design in terms of a network has to comprehend access into the home, out of the home, and within the home within the architecture. [There is a need to develop] something I would call the moral equivalent of the RJ-11 for broadband. By that I mean a lot more than just the physical connector. What the RJ-11 has done symbolically for the telephony industry is turn on a very large set of creative applications of telephony, ranging from modem applications in the data space to all sorts of remote voice mail with touch-tone entry, and all sorts of answering machines. … [T]here is a national market in which a consumer can go down to … the local supplier, buy equipment, and know that it will plug in and work not just in his current home, but also in whatever home he moves to. We need to achieve something like that for the broadband world. We need an architecture that will generate a standard consumer way of interfacing with the broadband network, which is independent of all of the choices we know we are going to have to make in the access network. We have heard arguments about the differences between various hybrid fiber coaxial cable-type deployments, between that and fiber to the curb, asymmetric digital subscriber line, and various wireless technologies for reaching the home. Ultimately, I think the consumer is not going to care a lot about the access technology. What he is going to want to be able to do is have his PC or his other information appliance capable of plugging into the NII In a standardized way. That is going to require the definition of a standard for connectivity both at a physical level and at an electrical level, and a protocol level that is common across at least a national market, perhaps a worldwide market. —Kevin Kahn, Intel Corporation If you believe the PC is the device, then the answer is a 10-base T Ethernet plug: it is an RJ-45. It is the logical successor to an RJ-11. The wireless modems have that plug on the back, the ISDN modems have that plug on the back, and the T-1 modems and the RF modems. Guess what? PCs already come with Ethernet plugs on the back and you plug them together and you are done. They are in fact routers. The set-top box should be a router; it is a media converter. That is what it is. We are done. It is Ethernet. —David Clark, Massachusetts Institute of Technology |
|
BOX 2.8 Computer-based Set-Top Boxes and Multisignal Conversion Given the several digital data delivery media entering the home including cellular, broadcast, cable, telephone, and direct broadcast satellite, practicality, economy, and convenience demand a single "set-top box" for the description, decoding, and processing of the signals for display. Further, the increasing need for interactive upstream communication suggests that, if it should ever achieve universal penetration, the computer, with its associated telephone modem, is the most efficient location for the multisignal converter functions. The convenience of the armchair remote control facing the television display will remain for the viewer of entertainment programs, but some of the switching functions it originates would be performed in the computer-based signal converter. In this concept, the leads from the terrestrial antenna, the satellite dish, and the cable feed would all terminate at the computer box where appropriate circuits would process the signals for display at, in many cases, multiple viewing locations in the home, each requiring different signals for display. This aspect of convergence will minimize the cost of equipment to be acquired by the consumer. —Vito Brugliera, James A. Chiddix, D. Joseph Donahue, Joseph A. Flaherty, Richard R. Green, James C. McKinney, Richard E. Ottinger, and Rupert Stow, "The NII in the Home: A Consumer Service" |
ate efficiently within the regulatory environment," and in particular the cost of the fully interactive HCT. Currently such units do exist, but they are quite expensive, in part because of the high-density integrated circuits needed to handle the "complex digital and analog signal processing inherent in any interactive terminal."31
What Increasing Use Of General-Access Devices Implies For Networking Technology Deployment
The increasing use of general-access devices such as PCs has implications for architecture, facilities, and service offerings (see Box 2.9). Also important are basic expectations about how access devices will be used and by whom, including the degree of end-user control over bandwidth and content selection.
What technical capabilities should an advanced information infrastructure have to support expected end-user needs? Chapter 4 discusses options for residential network access that are now under consideration or are currently being deployed. In this section, the steering committee identifies several essential service features for an NII:
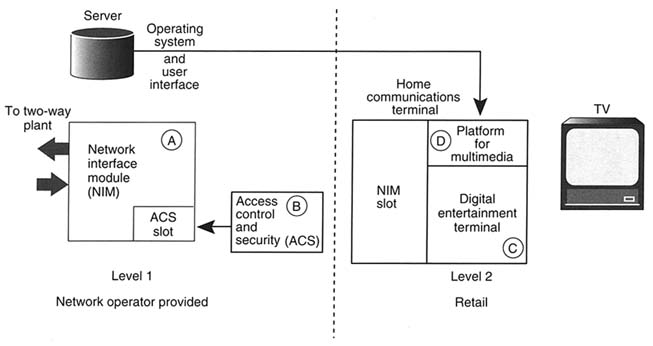
FIGURE 2.2 Proposed two-part broadband digital home communications terminal.
Architecture to resolve interoperability and retail sales issues. SOURCE: "The Evolution of the Analog Set-Top Terminal to a Digital Interactive Home Communications Terminal," a white paper contributed to the NII 2000 project by H. Allen Ecker and J. Graham Mobley.
|
BOX 2.9 User Behavior and Architectural Support If I really wanted to be interactive, I would talk to my wife instead of watching television. Most people watch TV. We've had (since 1950) 45 years that have demonstrated pretty conclusively that a lot of people want to have a fair amount of passive entertainment. And I don't think it's necessarily because there is an unavailable interactive alternative. In fact it may be due to the availability of the interactive alternative that you want that passivity. We may be bumping up against a basic constraint on human demand. —Steven Wildman, Northwestern University But the Web is based on a different model where the people of the world are creating the content. It makes a great deal of difference in the architectures of the national information infrastructure as we move forward as to where you assume the content is coming from. If it really comes from people everywhere, then you need a two-way, broadband infrastructure. … However, if the content is primarily provided by Hollywood and the likes of the current content providers, if the primary market is pay per view, then you can have servers that broadcast essentially to the people. —Robert Lucky, Bell Communications Research [There is] value out of being able to present views, present them to one or many specific others, and to communicate as a participant in varied interactions. … [T]his implies an architecture quite different from the kind that would mainly support downloaded entertainment. It also implies a set of addressing mechanisms that we do not necessarily get with other kinds of connectivity. —Tora Bikson, RAND Corporation In the future you will see much more sophisticated things of that nature, where the content is created on the fly by the user in a collaborative sort of an application, collaborative design, or whatever, where you are mixing graphics and simulation with voice and video, and so on. So I would actually characterize it as three generic kinds of applications. I think that you are either going to have three separate networks for those purposes, or you are going to have a single network that accommodates them all in a relatively cost-efficient way. —David Messerschmitt, University of California at Berkeley It all depends upon who gets clicked. If I am at home and I get clicked [by a distant Web user], I need bandwidth back into the network to respond to that click. —Leonard Kleinrock, University of California at Los Angeles |
- High data rates to the end-point,
- Adequate bandwidth in both directions,
- Multiple-session capability,
- Continuous availability of service,
- Real-time, multimedia communication,
- Nomadicity, and
- Security.
Associated with these service features, to make them viable in the market, are ease of attachment and low cost. None of these capabilities are static; they will evolve with the technology and its uses. There are strong ties among the various components: the applications, the computing capability at the end point, and the network capability.
High Data Rates to the End Point
The network connection, or ''last mile," must be able to support high data rates (high bandwidth) in order to allow the use of rich, multimedia data types. In the corporate setting, this level of access via local area networks is taken for granted. However, to the home, most users currently use conventional telephony-rate data communications, with current data rates at or below 28.8 kbps. Enhancements to cable TV systems offer the potential of receiving data at 20 Mbps, but that bandwidth is not available to subscribers to transmit with. The capabilities of the video delivery systems are being further expanded. For example, inherent extra capacity in the television vertical blanking interval is now being used by service providers to carry content other than conventional broadcasting, from program-guide information to Web pages linked to broadcasts through the Intercast technology. Yet even with Intercast, a telephone return path is needed for interactive applications.32
Many contributors identified ISDN, which offers a data rate of 128 kbps, as the next obvious step in upgrading link speed to the home. ISDN is the cheapest way to gain a factor of 5 to 10 in bandwidth without having to rewire the home; it allows reuse of the existing infrastructure at a relatively small incremental cost.
While these speeds are applicable for tasks such as exploring the Web or exchanging mail, they can constrain more advanced jobs involving access to higher-resolution images or video. These services are better served by data rates similar to those for today's local area networks, with peak transmission speeds between 1 and 10 Mbps. The steering committee concluded that residential bandwidths in this range would be very desirable to serve emerging applications needs.33
Adequate Bandwidth in Both Directions
In a typical corporate network environment the end user is able to receive and send data at the same rate. This symmetry is also present at lower speeds when a PC is connected to a network via a modem through conventional telephony or ISDN circuits. However, because of the features of some advanced technologies such as those used by the cable industry, the service that cable providers are anticipated to provide is typically highly asymmetric: users are able to receive data at a higher rate than they can send data. Chapter 4 gives more details on the performance to be expected. Although this upstream or reverse-channel speed is adequate for many applications, many believe that it may become an increasingly limiting factor in achieving the promise of an advanced NII.34 It is important that network architectures take such potential limitations into consideration and allow for future upgrades to assure that demand for ever-increasing bandwidth can be satisfied economically.
Multiple-Session Capability
Network access must be able to support multiple sessions simultaneously. Corporate networks are able to provide this capability today. For such a capability to be available to the home, some sort of packet switching is required. Packet switching allows a user with a single telephone connection to communicate with multiple remote sites. Inexpensive packet switches are now being marketed for the home or small business that will allow multiple individuals (workers or family members) to have network access simultaneously without having to sign up for multiple service connections. Increasingly, ISDN and conventional telephony modems are being used from the home to carry data packets exactly for this purpose. Current data modems for cable now being evaluated also use the packet mode of transmission to support this objective.
Continuous Availability of Service
Continuously available service is important because it saves having to dial up to be able to receive information. For example, a user can be notified of received mail as it arrives, not just when the user thinks to check for it (the assumption is that the user is not billed for passive connect time). When availability is continuous the user can offer a service on demand—the user can become a provider. Continuous availability of service is often found in large business or institutional settings. In the home today it is most evident in televisions left on for long periods of time.
Real-time, Multimedia Communication
The network must be able to support advanced, real-time, multimedia communication capabilities. Audio and video will become increasingly useful modes of information delivery. Consider, for example, video clips as a part of a Web page advertising some product or a component in an electronic mail message. Another important application area is teleconferencing, especially video conferencing, which many think will be a key facilitator of "telework." The requirement for multimedia, real-time communication implies a need for adequate bandwidth (ISDN may not be enough), bidirectional bandwidth (the teleworker will both send and receive a teleconference), and specific tools for bandwidth management. Improvement of compression is allowing better and better video to be supported on comparatively narrow bandwidths. Video conferencing on 128 kbps looks much better and is much cheaper today than a few short years ago.
Nomadicity
Network access must be available from multiple points—at work, from the home, on the road—whether tethered to a wireline system or through wireless capabilities. Different mechanisms for access will most likely have different characteristics, both in the physical and logical connection, but the applications must be able to scale with available resources. Nomadicity (any time, anywhere access) is a critical capability for an advanced information infrastructure (see Katz, 1995). It bears on lower physical and services levels of the architecture as well as middleware and application levels. The challenges of providing for nomadicity were outlined in forum comments and in a white paper by Leonard Kleinrock; see Box 2.10. Nomadic users must adapt to differing bandwidth levels from different locations and increasingly will embrace wireless and wireline transmission at different times and locations .35 Supporting them places a premium on interoperability and accommodation of differences in the nature of the error rate, fading behavior, interference levels, and so on between wireless and wireline networks as well as accommodation of multiple wireless architectures that may or may not involve base stations.
Security
Security considerations will be increasingly important. Although the need for security is currently appreciated more in businesses than in homes, even in businesses there is limited awareness. The topic of security is well beyond the scope of this project, but contributors clearly noted
|
BOX 2.10 Nomadicity The kinds parameters we have to worry about are the usual ones: bandwidth, latency, reliability, error rate, delay, storage, processing power, interference, interoperability—and, in addition, size, weight, and battery power, another set of key concerns in the things we carry around with us. … We have to deal with the unpredictability of the user, of the network, of the platform. We have to deal with graceful degradation. We have to scale with respect to everything: number, size, quality of service, and so on. —Leonard Kleinrock, University of California at Los Angeles |
the need for capabilities that allow for the protection of individual privacy, the security of funds transfer and protections for intellectual property, and the integrity of material transmitted. Several contributors commented on how this issue is being tackled within industry domains (e.g., banking and finance, manufacturing), including attempts to use the Internet more securely; deployment issues relate to securing of infrastructure links and end-to-end applications and therefore affect all levels of the architecture and all players, including users themselves.
Dependence on networking activities in more and more social and economic activity will broaden concerns about security. Irene Greif described this process at the forum:
Once your community is all hooked up so that everybody can talk to everyone else, if you volunteer to organize a PTA committee to do a surprise party for the teachers, you are going to have to figure out whether the discussion bulletin board that you have put in place for that process can be read by all of the teachers, the principal, some of the students, all of the parents. You will be doing access control and database design, and building a whole application. That is not easy. We have had quite a bit of success in the business world with groupware products, getting some of those kind of capabilities out of the hands of the skilled programmers, MIS [management information systems] departments, and into the hands of office workers. But that is still very far from what home users will want.
Concluding Observations
As outlined above and based on many inputs, the steering committee concluded that the following capabilities are essential service features of an information infrastructure evolving to meet end users' varied and in-
creasingly general-purpose needs: high data rates to the end point, adequate bandwidth in both directions, multiple-session capability, continuous availability of service, real-time and multimedia access, nomadicity, and security. Together, they compose a very different set than is currently available.
Comments by representatives of various user domains suggested concern about two alternative and undesirable prospects. On the one hand, decisions regarding financing, timing, bandwidth, symmetry, standards, services, and virtually every other aspect of residential and small-business access appear to many to be driven today by the presumption that home entertainment is the residential "killer app." Industry and government service representatives, concerned about their business or functional needs, are unsure what will result under this scenario. Would the infrastructure deployed as a result be of sufficiently low generality to lock out either some currently viable applications or deployments, or some future ones? Or would deployment of any sort be slowed because of uncertainty about the viability of this business model?
On the other hand, responses by different infrastructure providers to varying business pressures might result in an NII characterized by heterogeneous technologies and architectures, interoperating poorly, if at all. Investment in the reengineering of access facilities to the home will be slowed by the difficulty of making an integrated business case for infrastructure deployment, because the potential uses for infrastructure appear in a number of business sectors and are difficult to evaluate. At the same time, development of multiple delivery systems can foster innovation in technology and businesses and can provide more choices to meet diverse user needs and wants. Will citizens and sectors of the economy, as they become sufficiently sophisticated in their use of a range of applications, recognize the implicit cross-application demand for general-purpose capabilities too late to motivate timely provision of such capabilities?
The disconnect between users and infrastucture providers must be resolved largely by the user and application domains better articulating their needs and making clear the importance of enabling broad infrastructure use. This is something the user domains have not done well. A second approach to bridging the gap is to bring the infrastructure builders into the industry or sector planning and implementation processes so that the two can deal jointly with the technical and financial models required to serve both. A good example of this approach is represented by the North Carolina Health Information and Communications Alliance established by the state legislature but funded almost entirely by private industry. This project, truly a joint effort of state government, health industry professionals, health industry information vendors, and infra-
structure providers, illustrates that installing infrastructure can be handled more quickly and easily than can working through the political, social, and high-level barriers to use—problems that are expected to take several years to resolve.
Despite real concerns and choices, the near-term barriers to end-user access are not the technical features of the access infrastructure. A modern modem and Internet access from a Macintosh or "Windows" PC constitute a sufficient baseline for the next stage in widening access to general-purpose information infrastructure. Users today have concluded that they can experience the World Wide Web quite successfully from a home or a school over telephone lines. One possible path forward involves encouraging further use so that people can learn how to benefit more fully from the information technology. Rather than emphasizing the need for more bandwidth as a minimum, users should perhaps focus on minimizing barriers related to cost, ease of use, a natural process of familiarization and acceptance, and maturation of standards and interfaces, so that the consumer is better able to purchase and integrate the needed components.
The enduring issue of standards and interfaces for consumer equipment has ramifications that range to the competitive position of U.S. companies, given the international nature of information infrastructure goods and services. For data access, the steering committee sees a trend toward an Ethernet interface, the so called 10Base-T standard, as the connector for consumer data devices.36 In the television industry, the organization of the next generation of product (e.g., the eventual role of the set-top box and the television) is not currently clear. A number of developments point to progress in the area: the Advanced Television Systems proceeding at the FCC is likely to settle on a wide range of characteristics of digital systems for broadcast television, 37 the preponderance of which will apply to all methods of network distribution; MPEG-2, while not a complete system, has standardized a wide range of digital video characteristics, and the Advanced Television standard is expected to be consistent with MPEG-2; telephone companies have begun the process of procuring video equipment, several settling on an architectural structure consistent with that described in the white paper by Ecker and Mobley and based on a separation of security and network functionality into two parts—network equipment (a network interface module) and other features in consumer equipment (a digital entertainment terminal); and standards bodies (such as the Digital Audio Visual Council) are currently working toward standardizing digital video over cable television systems. It should be noted, however, that there are advocates both for the marketplace setting the standards or for technologists seeking to do the
same by setting standards prior to the introduction of a given technology. Both approaches have advantages and disadvantages.
Notes
-
6.
Terrestrial television broadcasting revenues are derived overwhelmingly from advertising and size the industry at about $30 billion annually (Veronis, Suhler, 1995, p. 104).
-
8.
Kraut's Home Net project shows that the methodologies developed in workplaces are being taken into homes as well (Kraut et al., 1996).
-
10.
The rise of the magazine Wired may be emblematic: it "has become the totem of a major cultural movement" (Keegan, 1995).
-
design tools also come into play in fairly short order, as end users realize that their group needs something slightly different than other groups.
-
driving IS [information systems] policy, and that's bizarre." As a result, some companies are quietly expensing their computer hardware, while others are exploring leasing options. See Halper (1995).
-
16.
Affordability is a concern for small businesses as well as residences.
-
20.
See Veronis, Suhler & Associates (1995), p. 313. Some sources offer a higher estimate, up to 35 percent; see, for example, Maresca (1995).
-
24.
Each week, 50 hours of HDTV-compatible programming is available now in the form of 35-mm film used in most prime-time productions.
-
25.
Voice messaging, call forwarding, caller identification, and other services are obvious examples.
-
26.
The white papers by Robert Roche and Mary Madigan give details.
-
28.
Philips Electronics recently announced plans for a video telephone that could be worn on the wrist and offer Internet access (Bloomberg Business News, 1995).
-
32.
Eventually, technology (e.g., plug-in boards) may support consumer access to the vertical blanking interval, thus facilitating more direct interactivity (Intercast, 1995).
-
33.
As discussed in Chapter 4, there are a number of options for more advanced transmission services to the home. In addition to copper wire, 60 percent of U.S. homes have cable television service. Since 93 percent of homes are passed by cable service, further deployment of coax access, as for HFC, is relatively easy in these neighborhoods. The evolution of traditional cable systems to hybrid fiber coaxial cable increases the potential for provision of advanced network services with higher bandwidths.
Broadcast is another path to the home. There is today limited ability to carry data in the unused portions of the video signal (e.g., the vertical blanking interval), and the anticipated move to digital video broadcast will provide much greater capacity. The rapid emergence of direct broadcast satellite is another path to the home, with similar opportunities for general information delivery. Interactivity for these two paths is hampered by the fact that the telephone is the most likely back channel for the foreseeable future.
Cellular, and eventually PCS, telephones are also points of access from the home. However, they are low-bandwidth connections and are likely to be used for data access only when alternative wire services are not available.
-
34.
ISDN is used to support video and data conferencing, for example, but it is difficult to upload a great amount of data.
-
35.
Meanwhile, software to support nomadic users is providing options for conserving on bandwidth (e.g., through compressed file transfer and transmission
-
of only changed portions rather than the entirety of files) as well as remote control of network nodes (e.g., printers) and security (Watt, 1995).
-
37.
The FCC will be building on voluntary standards setting that is ongoing in industry.




































