3
Privacy and Security Concerns Regarding Electronic Health Information
Concerns over the privacy and security of electronic health information fall into two general categories: (1) concerns about inappropriate releases of information from individual organizations and (2) concerns about the systemic flows of information throughout the health care and related industries. Inappropriate releases from organizations can result either from authorized users who intentionally or unintentionally access or disseminate information in violation of organizational policy or from outsiders who break into an organization's computer system. The second category—systemic concerns—refers to the open disclosure of patient-identifiable health information to parties that may act against the interests of the specific patient or may otherwise be perceived as invading a patient's privacy. These concerns arise from the many flows of data across the health care system, between and among providers, payers, and secondary users, with or without the patient's knowledge. These two categories of concerns are conceptually quite different and require different interventions or countermeasures.
Concerns Regarding Health Information Held By Individual Organizations
Electronic health records stored at individual organizations are vulnerable to internal or external agents that seek to violate directly the security and confidentiality policies of a specific organization (such agents are referred to as the "organizational threat" in this report). Internal
agents consist of authorized system users who abuse their privileges by accessing information for inappropriate reasons or uses, whether to view records of friends, neighbors, or coworkers or to leak information to the press. External agents consist of outsiders who are not authorized to use an information system or access its data, but who nevertheless attempt to access or manipulate data or to render the system inoperable. Health care organizations have long attempted to counter internal agents in their efforts to protect paper health records. They have less experience in protecting health information from technical attacks by outsiders because until recently, few health care organizations were connected to publicly accessible networks.
Scale of the Threat to Health Information Held by Individual Organizations
As yet, little evidence exists with which to gauge the vulnerability of electronic health information to outside attacks. The sites visited as part of this study reported no cases in which damaging intrusions by someone outside the site were detected,1 and no mechanisms exist in the health care industry for reporting incidents. Nevertheless, computer break-ins are known to have occurred in the health care industry. In one case, the so-called "414" group broke into a machine at the National Cancer Institute in 1982,2 although no damage was detected as a result of the intrusion.
Concerns over technical attacks by outsiders are rising in a number of other industry sectors and government. Commenting on a recent study by the Federal Bureau of Investigation and the Computer Security Institute (CSI), CSI Director Patrice Rapalus said, "The information age has already arrived, but most organizations are woefully unprepared . . . [making] it easier for perpetrators to steal, spy, or sabotage without being noticed and with little culpability if they are."3 As a result of sampling 400 sites, the study further stated that 42 percent of the sites had experienced an intrusion or unauthorized use over the past year, 20 percent of the respondents did not know if their sites had been invaded, only 17
percent of those suffering intrusions had notified authorities, and most respondents did not have a written policy for network intrusions. A recent estimate by the Defense Information Systems Agency indicated that Pentagon computers suffered 250,000 attacks by intruders in 1995; that this number is doubling each year; and that in about 65 percent of these attacks, intruders were able to gain entry to a computer network.4 A RAND Corporation study of information warfare scenarios in 19955 suggests that terrorists using hacker technologies could wreak havoc in computer-based systems underlying 911 emergency telephone services, electric power distribution networks, banking and securities systems, train services, pipeline systems, information broadcast channels, and other parts of our information infrastructure.
While not specifically describing threats to health care organizations, these reports indicate the growing vulnerability of information systems connected to public infrastructure such as the Internet. As such, they suggest that the drive for increased use of electronic health information (e.g., digital patient records) linked together by modern networking technologies could expose sensitive health information to a variety of threats that will need to be appropriately addressed.
General Taxonomy of Organizational Threats
Organizational threats assume many forms, from employees who access data even though they have no legitimate need to know, to outside attackers who infiltrate an organization's information systems in order to steal data or destroy the system. Each type of threat is characterized by different motives, resources, avenues of accessing information systems, and technical capability. They therefore pose different degrees of risk to an organization and can be addressed with differing types of controls.
Factors Accounting for Differences Among Threats
Motive. Both economic and noneconomic factors can motivate attacks on health information. Patient health records have economic value to insurers, employers, and journalists. Noneconomic motives can include curiosity about the health status of friends, potential romantic involvements,
coworkers, or celebrities; clandestine observation of employees; and the desire to search the health records of parties involved in contentious interpersonal situations such as divorce or the breakup of intimate relationships.
Resources. With respect to resources available to them, potential attackers can range from individuals with modest financial and computing resources to well-funded and determined intelligence agencies and organized crime. In between lie medium and large organizations that have an economic interest in gathering health data. To date, the threat posed by intelligence agencies and organized crime has not surfaced in the health care arena.6 The resources used in an attack against a health care organization are therefore those that would be available to an individual or a small group.
Initial Access. Initial access, the relationship of the attacker to the target data prior to the attacker's initiation of an assault on some stakeholder's system, has three elements:
-
1.
Site access. The attacker either does or does not have the ability (or inclination) to enter the facility where data are accessed on a regular basis.
-
2.
System authorization. The attacker either does or does not have authorization to use the information system in one way or another. System authorization is typically dependent on site access: a person without site access (either physical or electronic) is unlikely to have system authorization.
-
3.
Data authorization. The attacker either does or does not have authorization to access the desired data. Data authorization is dependent on system authorization: a person without system authorization is unlikely to have data authorization.
These three elements of initial access can be combined in various ways to characterize a potential attacker. For example, an individual may have system authorization by virtue of being a financial clerk, not have data authorization for patient records, and have site access because he or she has a badge that allows movement freely about a hospital or clinic (Table 3.1). Site access is an important element when countermeasures are being considered.
TABLE 3.1 Likely Combinations of Access Privileges in a Health Care Setting
|
Level of Access |
Example |
|
None |
Outside attacker |
|
Site only |
Maintenance worker |
|
Site and system |
Worker in the billing department who has access to information systems but not to clinical information |
|
Data and system |
Vendor or consultant with remote access privileges |
|
Site, system, and data |
Care provider such as doctor or nurse |
Technical Capability. The technical capability of an attacker is, in general, independent of the characteristics of access outlined above: an authorized user may be highly capable, and an unauthorized user may be computer illiterate. The technical capabilities of potential attackers can be characterized by three broad categories: aspiring attackers, script runners, and accomplished attackers.
Aspiring attackers are individuals with little or no computer expertise, but with ambitions and desires to learn more. They learn about attacks from popular literature, much of it published by organizations that cater to the survivalist and antiestablishment trade. The techniques they use are relatively unsophisticated and include the following:
- Researching the target site by reading open literature and scouting the location;
- Masquerading as an employee or other authorized individual to gain information or access;
- Guessing passwords, locating passwords written on calendars or elsewhere, or watching users enter their passwords;
- Searching trash bins for information on security practices and mechanisms; and
- Gaining entry to the desired location by gaining employment as a temporary employee, dressing as a custodial or professional staff member, or using some other method.
Script runners are an Internet phenomenon. These are individuals who obtain standard, scripted attacks and run them against information systems to which they desire entry. They generally have little or no
knowledge of how the attacks work, do not care about learning more, and are unable to proceed further if the scripts fail. The current inventory of scripts operates primarily in standard Internet environments; given the rush of other vendors (e.g., Microsoft and IBM) to make their products Internet compatible, this level of technical capability will soon be able to be directed against all products using the Internet.
Accomplished attackers are the most formidable threat: they understand system vulnerabilities and are capable of adapting to situations where scripted attacks fail. For a health care organization, the worst-case future scenario is an accomplished attacker gaining entry via the Internet to an information system that allows access to patient health information.
The technical capability of attackers at each level in this hierarchy is constantly evolving and improving. Techniques that just a few years ago were the exclusive purview of accomplished attackers have moved to the script runner stage and will shortly be available to aspiring attackers. Mechanisms for countering these threats must therefore also evolve and improve, which implies a continuing intellectual and financial investment in security technology.
Levels of Threat to Information in Health Care Organizations
During its site visits, the committee discerned a number of distinct types of organizational threats described by different combinations of motive, resources, access, and technical capability. They are categorized here by levels numbered one through five (with five being the most sophisticated).
- Threat 1: Insiders who make ''innocent" mistakes and cause accidental disclosures. Accidental disclosure of personal information—probably the most common source of breached privacy—happens in myriad ways, such as overheard conversations between care providers in the corridor or elevator, a laboratory technician's noticing test results for an acquaintance among laboratory tests being processed, information left on the screen of a computer in a nursing station so that a passerby can see it, misaddressed e-mail or fax messages, or misfiled and misclassified data.
- Threat 2: Insiders who abuse their record access privileges. Examples of this threat include individuals who have authorized access to health data (whether through on-site or off-site facilities) and who violate the trust associated with that access. Health care workers are subject to curiosity in accessing information they have neither the need nor the right to know. Although no overall statistics are available to indicate the scope of the problem, discussions with employees during site visits uncovered many cases in which health care workers have accessed information about the
- health of fellow employees or family members out of concern for their well-being. There are reports of health care workers accessing health records to determine the possibility of sexually transmitted diseases in colleagues with whom they were having a relationship—or in people with whom former spouses were having relationships. Potentially embarrassing health information (e.g., psychiatric care episodes, substance abuse, physical abuse, abortions, HIV status, and sexually transmitted diseases) about politicians, entertainers, sports figures, and other prominent people regularly finds its way into the media.
- Threat 3: Insiders who knowingly access information for spite or for profit. This type of threat arises when an attacker has authorization to some part of the system but not to the desired data and through technical or other means gains unauthorized access to that data. An example is a billing clerk who exploits a system vulnerability to obtain access to data on a patient's medical condition. For example, the London Sunday Times reported in November 1995 that the contents of anyone's (electronic) health record in Great Britain could be purchased on the street for about £150 (or about $230).7
- Threat 4: The unauthorized physical intruder. In this case, the attacker has physical entry to points of data access but has no authorization for system use or the desired data. An example of this threat is an individual who puts on a lab coat and a fake badge, walks into a facility, and starts using a workstation or asking employees for health information.
- Threat 5: Vengeful employees and outsiders, such as vindictive patients or intruders, who mount attacks to access unauthorized information, damage systems, and disrupt operations. This is the pure technical threat—an attacker with no authorization and no physical access. An example is the intruder who breaks into a system from an external network and extracts patient records. Threat 5 is truly dangerous only when patient records are accessed regularly through an external network. It is clear that most providers are moving toward the use of networking and distributed computing technologies as they move toward electronic medical records. Threat 5 is therefore a latent problem on the horizon. The current reliance on paper records and the preoccupation of system managers with internal systems make threat 5 low in perceived importance and, so far, low in reported incidence. This situation is unlikely to last past the point at which internal systems are connected to external networks.
Threat 5 also encompasses "denial-of-service" attacks conducted electronically by outsiders. Such attacks are intended to render the attacked
system useless for normal purposes. For example, an outside intruder may access a critical health information system not just to snoop on data but to insert a computer virus or Trojan horse that "crashes" the system at some later date or erases critical data files. Alternatively, an outsider could launch an e-mail attack in which a remote computer sends tens of thousands of e-mail messages in a very short time (e.g., an hour) to a given site, overwhelming the ability of the mail servers to process mail and rendering the system useless for ordinary e-mail purposes.
Countering Organizational Threats
There are two basic approaches to countering organizational threats to the privacy and security of electronic health information: deterrence and imposition of obstacles. Deterrence seeks to prevent violations of policy by imposing sanctions on violators; these sanctions may include dismissal, civil liability, or criminal prosecution. Obstacles are erected to prevent violations of policy by making them hard to achieve. Practical systems adopt a mixture of the two approaches; thus, in physical security one may install a reasonably strong lock (an obstacle) and an alarm system (representing deterrence, because apprehension in the act of breaking in carries criminal sanctions).
Deterrence assumes that individuals who constitute a threat can be identified and subjected to such sanctions. Technical support for deterrence centers on mechanisms for identifying users and auditing their actions. Obstacles are most often used in situations in which the threat cannot be identified or it is not practical to impose sanctions, such as in the protection of military or diplomatic information. Technical supports for imposition of obstacles include mechanisms for making a priori determinations of authorized use and then taking active steps to prevent unauthorized acts.
Three factors inhibit organizational adoption of obstacles: (1) the direct cost of the mechanisms, such as access control tokens, and cryptographic devices; (2) the indirect cost of decreased efficiency and morale (e.g., the "hassle factor" of an additional inconvenience); and (3) the possibility that an obstacle may prevent necessary, legitimate access or use of data (e.g., in an emergency or some other situation not anticipated by the mechanism's designer). Deterrence mechanisms also entail costs, but these costs tend to be more indirect (e.g., personnel costs in educating users about the existence of penalties for abusing access privileges).
Developing Appropriate Countermeasures
Specific countermeasures have to be developed for each of the five
threats outlined above. Health care organizations must therefore assess their information systems to determine the types of threats to which they are most vulnerable and must then implement the necessary organizational and technical mechanisms. Although the precise implementation will vary from one institution to another, some general rules of thumb apply across organizations (Table 3.2). Specific ways of implementing the types of mechanisms identified are outlined in Chapters 4 and 5.
Threat 1 can best be countered by organizational mechanisms that detect and deter abuses. More sophisticated technology per se can do little to prevent this kind of disclosure. Simple procedural measures appear to be most appropriate—for example, reminders about behavioral codes, confirmation of actions that might route or access information erroneously, or screen savers and automatic log-outs to prevent access to unattended displays. Chapter 4 examines the possibility of extending these procedures by maintaining patient anonymity through the use of coded patient identifiers (pseudonyms) in most of the care process.
The principal countermeasure for threat 2 is deterrence: appeals to ethics, education about what constitutes fair practice, and the imposition of sanctions after an incident occurs. Technology can also play a role in controlling inappropriate access to patient information. Strong user authentication, based on cryptographic techniques, can effectively control access to health information networks and computer systems-at least to the extent that system users protect their identifying data and make appropriate use of the information they are authorized to access. The use of encryption can place significant obstacles in the way of potential abusers, requiring them to obtain special data (keys) to make patient information legible. Properly analyzed audit records of accesses are another powerful tool to deter abuse.
A combination of obstacles and deterrence is necessary to counter threat 3. These include reasonable obstacles to prevent unauthorized access without interfering with authorized use and the deterrence steps used against threat 2. Audit trails are particularly effective at deterring this type of threat.
The countermeasures for threat 4 rely heavily on deterrence, supplemented with strong technical obstacles. Attackers run the risk of immediate identification and apprehension and have the potential of leaving physical evidence of intrusion (e.g., surveillance tapes) that can be used in prosecution. The obstacles that can be placed in the way of threat 4 include both technical security measures such as strong identification and authentication mechanisms and physical security measures such as requiring badges, and challenging strangers.
Countermeasures against threat 5 are based purely on the obstacle approach. In this case, the threat is not readily identifiable; its physical
TABLE 3.2 Types of Threat to Health Information Held by Health Care Organizations and Possible Countermeasures
|
Type |
System Authorization |
Data Authorization |
Site Access |
Threat |
Countermeasure |
|
1 |
Yes |
Yes |
Yes |
Mistakes |
Organizational and simple technical mechanisms |
|
2 |
Yes |
Yes |
n/a |
Improper use of access privileges |
Organizational and technical mechanisms such as authentication and auditing |
|
3 |
Yes |
No |
n/a |
Unauthorized use for spite or profit |
Organizational and technical mechanisms such as authentication and auditing |
|
4 |
No |
No |
Yes |
Unauthorized physical intrusion |
Physical security and technical mechanisms such as authentication and access controls |
|
5 |
No |
No |
No |
Technical break-in |
Technical mechanisms such as authentication, access controls, and cryptography |
location is not easily determined; and the threat may not be subject to any credible administrative, civil, or criminal sanctions (e.g., an intruder based overseas). Technological obstacles to intruders include the use of firewalls to isolate internal and external networks and strong encryption-based authentication and authorization technologies to prevent intruders from masquerading as legitimate users. However, the effectiveness of technological obstacles can be ensured only when network connections between the health information system and the outside world are restricted administratively to passing nonsensitive data (e.g., e-mail unrelated to patient care, access to the World Wide Web for research data). If external network connections are used for both sensitive and nonsensitive data, then the technical countermeasures required to guarantee security may well push the state of the art,8 to say nothing of exceeding the state of practice observed in the site visits. Furthermore, for some types of attack, there are no known obstacles at all; for example, denial-of-service attacks based on exhaustion of resources are very hard to defend against, especially when timeliness of response is an issue, although defenses against denial-of-service attacks can sometimes be created on an ad hoc basis. This is not to say that technical countermeasures are useless (indeed, the focus of Chapter 4 is on technical countermeasures that can be deployed to useful effect). Nevertheless, technical countermeasures cannot be viewed as a cure-all for security problems.
Observations on Countering Organizational Threats
Obstacles such as encryption and authentication are the only effective ways to counter organizational threats against systems that have an Internet interface because there are minimal, if any, accountability mechanisms in effect on the Internet. In addition, the Internet spans multiple legal and national jurisdictions. (The same holds true—to a lesser degree—for systems with any kind of "dial-in" interface.) As a consequence, extensive use of the Internet to access or transfer health record data will carry with it a significant and growing risk from organizational threats to the security and privacy of the data unless steps are taken to mitigate this risk; these steps are the focus of Chapter 4 and Chapter 6 . The largest portion of these risks will not be mitigated until ways are developed of holding Internet users accountable for their actions and agreements are in place across multiple legal and national jurisdictions to impose sanctions for violations of the security and privacy of health information.
Until these steps are taken, the use of the Internet for the access and
transfer of health information will have to be limited to those tasks that convenient obstacle-based security mechanisms can support; the culture of stakeholders will have to change to accommodate the extra load of mechanisms that are more difficult to use; or the aforementioned risks will have to be assumed by the health care system.
Provided that adequate obstacle-based security mechanisms exist at the Internet interface (e.g., by use of a firewall), a deterrence-based approach that allows relatively free internal access can be adopted without excessive risk. Countering organizational threats by erecting technical obstacles to access is not, in general, compatible with the efficient and effective operation of systems used by providers. The time pressures on providers do not permit the level of security-driven interaction that such mechanisms require, and the risk that an obstacle-based mechanism will deny legitimate access to data in an emergency (with the consequent liability) is inherent in such mechanisms. An important enabling mechanism for such an approach is an identification and authentication mechanism that has adequate strength and is acceptable to all classes of users.
Systemic Concerns About Health Information
Systemic concerns about the privacy of patient-specific health information are generally rooted in the use of such information in a manner that acts against the interests of the individual patient involved. These interests may involve specific identifiable adverse consequences such as increased difficulty in obtaining employment or insurance or less tangible ones such as personal embarrassment or discomfort. In order to understand how public concerns about such use arise, it is helpful first to examine the exchanges of health information throughout the health care system.
Uses and Flows of Health Information
Health information-both paper and electronic-is used for many purposes by a variety of individuals and organizations within and outside the health care industry (Table 3.3). Primary users include physicians, clinics, and hospitals that provide care to patients. Secondary users employ health information for a variety of societal, business, and government purposes other than providing care.9 They include organizations that pay for health care benefits, such as traditional insurance companies, managed care providers, or government programs like Medicare and
TABLE 3.3 Typical Users and Uses of Health Information
|
User |
Purpose |
Patient Identifiable? |
|
Patient |
|
Yes |
|
Primary care physician |
|
Yes |
|
Health insurance company |
|
Yes |
|
Clinical laboratory |
|
Yes |
|
Local retail pharmacy |
|
Yes |
|
Pharmacy benefits manager |
|
Yes |
|
User |
Purpose |
Patient Identifiable? |
|
Consulting physician |
|
Yes |
|
Local hospital |
|
Yes |
|
State bureau of vital statistics |
|
Yes; baby also identifiable |
|
Accrediting organization |
|
Yes |
|
Employer |
|
Possibly |
|
Life insurance company |
|
Yes |
|
User |
Purpose |
Patient Identifiable? |
|
|
|
|
|
Medical Information Bureau |
|
Yes |
|
Managed care company |
|
Yes |
|
Attorney |
|
No |
|
State public health and family physician |
|
Yes; baby also identifiable |
|
State agency collecting hospital discharge data |
|
Yes; baby also identifiable |
|
Medical researcher |
|
No |
Medicaid. As part of their management functions, these payer organizations also conduct analyses of the quality of health care delivered by provider organizations and its relative costs. Other secondary users include medical and social science researchers, rehabilitation and social welfare programs, public health services, pharmaceutical companies, marketing firms, the judicial system, and the media. They use health
information for purposes such as researching the costs and benefits of alternative treatment plans, determining eligibility for social programs, understanding state and local health needs, news reporting, and targeting possible markets for new or existing products. Marketing firms and vendors of health-related products also obtain health information that will help them target particular types of patients for direct marketing.10
The types of information collected by primary and secondary users vary greatly across individual organizations. Exchanges of data among these organizations are highly complex and dynamic. Rather than attempting to enumerate every possible flow, the discussion below traces the records of a hypothetical, but typical, patient named Alice. Alice's story is a representative, although by no means comprehensive, description of how health records are shared between organizations and individuals.
Alice's Medical Records
Alice is in her late twenties, married, and employed by a small company. Bob, her husband, is employed by a large firm. Bob's company offers its employees a choice of three health benefit plans: (1) a health maintenance organization (HMO) that operates its own clinics and pharmacies and permits referrals to outside physicians only under strict guidelines; (2) a preferred provider organization (PPO) that provides pharmacy benefits and reimburses charges from participating physicians at a higher rate than those from nonparticipating physicians, but allowing patients to choose physicians freely; and (3) a conventional indemnity insurance program in which all charges are reimbursed at the same rate after an annual deductible is met, with supplementary major health insurance to cover extraordinary expenses. Differences in the ways their health records may be stored and controlled are not outlined in the program descriptions, and Alice and Bob do not consider this factor in their decision. Hoping to save money but preserve choice of physicians, Bob and Alice choose the PPO option. Bob's employer is self-insured—an increasingly popular strategy for many large employers—though this fact is not stated openly during the enrollment process.
When they set up housekeeping in their current location, Alice and Bob consult friends, colleagues, and local sources of information to find
primary care providers. On her first visit to a prospective primary physician, who is a member of a small group practice, Alice is asked to fill out a medical history form and specify how she will pay for her care in the future. She indicates that she will use the health insurance benefits available to her through her husband's job. Since Alice specifies that some of her charges will be covered by a party other than herself, she is also given a form to sign that would authorize the physician's office to send information to the insurer for payment of claims. This release covers all future visits Alice makes to this practice.
Alice's initial visit is satisfactory, and she decides to use this physician as her primary care provider. Records for her initial examination are recorded on paper and held in the physician's office. Blood samples taken from her during the visit, however, are sent to an outside laboratory for analysis. Automated analysis equipment records the laboratory results and prints a paper copy that is returned to the physician; the laboratory bills Alice for the service. The laboratory also retains a record of the test and of Alice's identity. Through the third-party administrator used by Bob's firm to manage health care benefits, Bob's firm receives a claim from Alice for the office visit and the blood test, and approves payment.
The following year, Alice's annual checkup reveals hypertension, and blood tests show mild anemia. The physician prescribes two medications, and Alice fills the prescriptions at a local pharmacy. The pharmacy's charges are reimbursed through a pharmacy benefits program connected with the health insurance option selected by Bob. The pharmacy records Alice's name and address, reads her pharmacy benefits card, notifies the benefits program, and is reimbursed. Parts of Alice's health record now reside with the retail pharmacy and the pharmacy benefits provider, as well as her care provider.
When Alice becomes pregnant, she develops a condition that her primary care provider wishes to discuss with another physician outside the group. She requests Alice's permission to release information to the consulting physician, since Alice may wish a second opinion, and Alice will pay for part of the cost. Acting in accordance with the rules specified by Bob's firm, the third-party administrator approves both the consultation and part of the consultant's fee. The primary care provider trusts the consultant to keep information in Alice's record confidential.
The child is delivered at a local hospital used by the group practice. Prior to Alice's admission, she provides evidence of her ability to pay by showing her insurance card, and she signs a form authorizing the hospital to release to paying parties any data from this admission required for payment. The hospital performs a variety of tests and procedures during Alice's stay and creates a related set of records, some automated and
some on paper. The child's birth is recorded with the state, which also opens an immunization record for the child.
Subsequently, the hospital is visited by an accrediting body, which, as a routine part of its investigation, checks on the record-keeping procedures at the hospital. As it happens, Alice's records are among those reviewed, but the accreditors do not remove them from the hospital or make any copies. They simply check the records for accuracy and completeness and to ensure that they are stored in compliance with accrediting procedures.
Bob's company, feeling competitive pressures, considers ways to save money and increase productivity. Improving employees' health seems to be a positive step, since it may both decrease claims and improve performance. Since Bob's company is self-insuring, it asks the third-party administrator to provide it with claims information pertaining to its employees. Though reluctant to share patient-identifiable information because of concerns over privacy, the third-party administrator has no legal basis on which to refuse the request and, to maintain good relations with its client, provides the information to Bob's employer.11 Since her claims are paid by Bob's company, Alice's record, as well as Bob's, is also forwarded. Alice's company, under similar pressure, initiates a company clinic on-site and a ''wellness" program. Although she continues to be insured by Bob's company, Alice uses the clinic occasionally and, on her first visit, provides the clinic with her history, including a list of medications she is taking.
After the birth of their child, Bob and Alice realize that they need life insurance. Both of their companies provide some group coverage, but it is inadequate for their needs. Alice applies for coverage with a large, respected firm, which will provide the coverage she wants if she passes a physical examination. The life insurance company will pay for the examination, but she must sign a release permitting the results of the examination to be forwarded to the Medical Information Bureau (MIB). The life insurance company decides to accept the risk of insuring her but forwards the hypertension results to the MIB in accordance with the industry's practices because her hypertension, although under control, may potentially affect her longevity.
The group practice Alice uses is purchased by a managed care firm, which installs its automated records program. Results of Alice's office visits are now stored on a local computer system. The managed care firm, facing the same competitive pressures as Bob's company, periodically
reviews records from each of its many groups to ensure both the quality and the appropriateness of the care provided.
The managed care firm denies a request from another patient within the practice to consult a specialist for a condition similar to the one for which Alice was treated. The patient subsequently sues the practice, and her lawyers request disclosure of records from similar cases within the practice. The court grants a subpoena for the records involved, including Alice's, and the practice is compelled to provide copies of the records to lawyers. Alice's name is removed from the record.
A researcher wants to investigate the long-term effects of the hypertension medication Alice has been taking. He gets a federal grant to support the study and gains approval of his organization's institutional review board. He then writes to hospitals and physicians to request access to their records. Alice's physician contacts Alice and several other patients to ask if they are willing to participate in the study. Alice agrees and signs a consent form granting her physician permission to provide her records to the researcher for purposes of this study, but she insists that her identity not be revealed. The records are provided as requested, but with the name, address, and Social Security number fields scrambled in such a way as to allow Alice's records to be linked without divulging her identity.
At this point, parts of Alice's health record are held by a wide variety of organizations: her primary care physician's practice, a clinical laboratory, the local pharmacy, the pharmacy benefits provider, the practice of the consulting physician, the local hospital, the state bureau of vital statistics, the hospital accrediting agency, her husband's employer, her life insurance company, the Medical Information Bureau, the outcomes researcher, and various lawyers (Figure 3.1). Most of these organizations have information that specifically identifies Alice. She has explicitly consented to grant access to some of these holders; she is aware of others to whom she has not granted access; of others, she may be entirely unaware. If Alice and Bob had chosen a different health plan, the flows might differ. A comprehensive HMO, providing medical, hospital, and pharmacy service, might have more flows within it and fewer outside organizations, for example.
Government Collection of Health Data
If Alice were an impoverished single parent receiving government benefits, additional flows of data would involve state and federal social services agencies. The federal government collects data for reimbursement of care provided under Medicare and Medicaid, but states also collect large amounts of patient-identifiable information for their own pur-
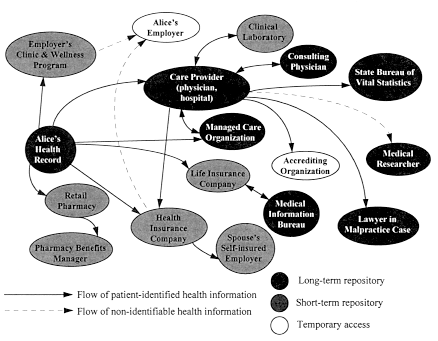
FIGURE 3.1
Flows of Alice's health information.
poses. State health agencies can provide services and collect identifiable data about patients just as providers in private health care entities would. Functioning as providers, they would release identifiable data with patient consent to insurers and other providers depending on the need to know. State health agencies collect data for the purposes of analyzing and disseminating information on health status, personal health problems, population groups at risk, availability and quality of services, and health resource availability.12 The categories of data collected are dependent on the services and functions each health department has within its authority. Environmental services, Medicaid, professional and facility licensing, and alcohol and drug abuse or mental health services are not located consistently in all state health departments across the country.
State health departments generally collect patient-identifiable data
related to health service utilization and costs, personal health status and risk (health surveillance data), alcohol and drug abuse services, and mental health services, among other categories. The types of data systems related to each of these categories can be extensive (Table 3.4).
Databases created for these purposes generally have a designated steward who is responsible for managing the protection and the uses of the data. These types of data are released in an identifiable form only in select situations: (1) research purposes for which there has been an approved human subjects review and a data-sharing agreement that outlines restrictions on the use of data, destruction of data at the end of research, and the penalties for violating the agreement; and (2) the investigation of a reportable disease or condition for the purposes of protecting the public's health. In the latter case, identifiable data are released to specially authorized public health investigators or private physicians who are responsible for care of the person believed to have a reportable condition or disease (e.g., measles, sexually transmitted disease, tuberculosis, birth defect, cancer). The steward of the database determines which staff members are allowed to access identifiable data for the purposes of analyzing them. Finally, state laws include penalties that prohibit improper release of data by a state government employee.
Risks Created by Systemic Flows of Health Information
As Alice's story shows, the types of organizations that collect, process, and store health information include not only other members of health care provider teams, such as referral providers, nurses, and laboratory technicians, but also groups such as insurance companies and third party payers, utilization and outcomes assessment groups, public health and disease registry groups, clinical research groups, and a growing health information services industry. These various organizations have historically developed separate policies with regard to the protection of information in these records. These separate policies reflect the different perceptions of individual stakeholders regarding the proper trade-off between Alice's privacy interests and their use of the data. Although these policies are not always formalized or documented, a consensus among the members of each stakeholder group can generally be discerned.
Such consensus typically does not exist between different groups of stakeholders (e.g., providers and insurers) or between managed care organizations and self-insured employers. A collection of health insurance executives is likely to agree regarding the bounds of legitimate access within their own business sector, as is a collection of physicians, but the two definitions of legitimate access are likely to differ significantly from one another. As a result, the movement of data around a network of
TABLE 3.4 Typical Health Information Collected by State Health Departments
|
Data Set |
Content |
|
Hospital discharge data |
Information on all patients discharged from acute care hospitals; systems track morbidity, hospital use and costs, and the distribution and utilization of services |
|
Clinic visit records |
Information on family planning services utilization |
|
Genetics clinics reports |
Summary statistics on services and volumes of contracted genetic counseling clinics |
|
Adult immunization survey |
Information on vaccination status of adults in schools and adults in health care facilities |
|
Child immunization tracking |
Information on individual childhood immunizations and rates |
|
AIDS reporting system |
Information on all reported Class IV AIDS cases; used for disease surveillance and trend analysis |
|
Behavioral risk factor surveillance system |
Yearly telephone survey on health-related behaviors of a sample of individuals 18 and older, used to develop statewide prevalence estimates to target preventive health services to counties, age groups, and so on |
|
Birth certificate file |
Information on all births occurring in a particular state; used to monitor trends in population fertility and maternal and child morbidity, to establish legal residence, and to assist in epidemiological analyses |
|
Birth events records file |
Linkage of records from the Hospital Abstract System |
|
Cancer registries |
Documentation of statewide incidences of cancer from hospital tumor registries and laboratory data |
|
Birth certificate file and infant file |
Information from studies on prenatal care and outcomes studies |
|
Death certificate file |
Information on all deaths occurring in a particular state; used to monitor trends in mortality, establish legal benefits, and assist in epidemiological analyses |
|
Data Set |
Content |
|
Fetal death file |
Information on all fetal deaths (gestation periods of 20 weeks or more) |
|
Newborn screening data |
Information on laboratory tests for hemoglobinopathies, which are performed on all newborns delivered in hospitals in the state; used for early identification and treatment of these disorders |
|
Long-term care facility influenza and pneumococcal survey data |
Information on immunization status for residents and staff of long-term care facility |
|
Rash data |
Information on new cases of measles and vaccination status of those cases |
|
Monitoring system for adverse events following immunization |
Tracking of suspected events following immunization; used to initiate follow-up action if needed |
|
Occupational mortality data |
Information on occupation-related mortality and effects of occupational exposures on natality |
|
Reportable diseases and conditions |
Information of occurrences of diseases (used for disease surveillance) and conditions |
|
Sexually transmitted disease morbidity and epidemiological reports |
Information on morbidity and epidemiological investigations and follow up actions for individuals or partners testing positive for sexually transmitted diseases |
|
Tuberculosis case registry and contacts |
Information on management of individual cases of persons with tuberculosis and individuals exposed to tuberculosis and their follow-up and treatment |
|
Women, infants and children information set |
Minimum information required by U.S. Department of Agriculture to certify clients for Women, Infants, and Children Supplemental Food Program |
|
Child abuse and neglect data |
Information on child abuse or neglect referrals, subsequent investigations, and responses to referrals and investigations |
|
SOURCE: Washington State Department of Health, 1996: personal communication (October). |
|
stakeholders (movement that often occurs without the consent that can be effectively withheld by the patient or primary provider) is not governed by any network-wide policy. Rather, data are treated in accordance with a variety of local policies that may or may not be consistent with the patient's understanding when signing a form that authorizes initial release of the information. Individual organizations often have strong business incentives to protect health information from other parties because they regard such information as having significant business value; nevertheless, almost all of the sites that the committee visited during the course of this study expressed serious concerns about potential harm to patient interests resulting from unrestrained use of patient information by organizations not involved in the provision of care.
Without industry-wide standards or regulations governing the uses of health information by primary and secondary users, the information can—and sometimes is—employed for purposes that violate patient privacy or are detrimental to the interests of the patient. One example of the kinds of harm that can befall patients is outlined in a recent case study13 that describes the results of a survey in which 206 respondents reported discrimination as a result of access to genetic information. Such discrimination resulted in loss of employment, loss of insurance coverage, or ineligibility for insurance. The cases were screened carefully to identify those in which discrimination was based on the future potential for disease rather than existing manifestations of a particular malady (i.e., the patients exhibited no phenotypic evidence of disease, only a predisposition to a future occurrence of treatable diseases such as hemochromatosis, phenylketonuria, muco-polysaccharidoses, and Huntington's disease).
A second example of harm is illustrated by the case of a pharmaceutical company that acquired a drug reimbursement service or pharmaceutical benefits manager (PBM). The PBM used information in its database in an attempt to convince physicians to prescribe drugs manufactured by the pharmaceutical company. In a March 1996 consent decree filed in Minnesota and joined by 17 other states,14 one such firm agreed to stop interfering in the prescription of medications from other manufacturers when it assessed patients' eligibility for coverage. Although no direct financial or physical harm befell patients in this case, their privacy interests were compromised when confidential information about them was
|
13 |
Geller, L.N., J.S. Alper, P.R. Billings, C.I. Barash, J. Beckwith, and M. Natowicz. 1996. "Individual, Family, and Societal Dimensions of Genetic Discrimination: A Case Study Analysis," Science and Engineering Ethics 2(1):71-88. |
|
14 |
PRNewswire. 1996. "Minnesota Takes the Lead on Agreement to Protect 41 Million Americans," October 25; available on-line at www.epic.org/privacy/medical/merck.txt. |
furnished to individuals (pharmacists) who were unconnected with the conduct or quality of their care.
These examples clearly suggest that the interests of patients may not be well served by wide dissemination of health care information. If Alice had developed an expensive, chronic condition as a complication of her pregnancy, Bob's self-insured employer could be made aware of that fact through its review of billing data (which contain detailed diagnostic codes) and could use such information to influence a decision about Bob's continued employment. Managers in Bob's company might well argue that Bob's high health insurance bills make him too expensive to keep on the payroll. In a recent survey of Fortune 500 corporations, 35 percent responded that they use individual health records in making employment-related decisions.15 One in ten companies does not inform employees of this practice. An earlier survey indicated that 50 percent of the companies used health records in making employment-related decisions and that 19 percent did not inform employees of such use.16 It is not clear from these studies how employers are using the data; there may be cases in which the information is used to benefit the employee,17 but it can be argued that such decisions should be made by the employee. Furthermore, no legal standard prevents Bob's old employer from discussing Alice's condition with a potential new employer or prevents some entrepreneur from establishing a clearinghouse of data on employees with high insurance costs.
Universal Patient Identifiers
Concerns about the systemic sharing of electronic health information are linked to efforts to establish a universal patient identifier for indexing patient records throughout the U.S. health care system. The Health Insurance Portability and Accountability Act of 1996 directs the Secretary of Health and Human Services to promulgate a standard for such an identifier by February 1998. The goals of this initiative are multiple and include improving the quality of care by allowing providers to more easily locate patient records, facilitating health services research, and simplifying the administrative aspects of managing and paying for care. Optimal health
care often depends on the availability of a complete medical record,18 and health outcomes research depends on the ability to undertake longitudinal studies on individuals (although not necessarily studies that are linked to the identities of these individuals). Detecting fraud may be possible only when abuse is revealed through unusual patterns of health care usage (linked through individual patient records).
Large, integrated delivery systems and managed care programs routinely assign patients identifiers for use within their health care systems without generating much controversy.19 What generates the largest amount of controversy is the prospect that a universal identifier will facilitate attempts to link information within and across much larger boundaries. For example, the idea of using the Social Security number (SSN) as a universal health identifier raises concerns not only that all medical data associated with a given individual can be linked, but also that an individual's medical data could be linked with financial data, purchasing habit data, family details, and other items of information—many of which are already indexed by the SSN—to create a personally identifiable, inter-linked record containing sensitive information. The use of any single number as a universal identifier could expand beyond its initial intent and become widespread in other domains, just as use of the SSN expanded well beyond the realm of identifying Social Security records.20
Adoption of a universal patient identifier would raise concerns about its use to link large numbers of personal data transactions in two distinct areas:
- Discrimination: Sensitive or adverse information may be used against an individual's economic interests in some way. For example, an employer may refuse to hire or promote an individual with a long and expensive history of medical claims (or with the prospect of expensive or chronic medical problems in the future based on genetics or family history).
- Loss of privacy: Many individuals have medical conditions that they might wish to keep private (e.g., a history of sexually transmitted diseases or treatment for depression). Even if an individual is not subject
- to economic discrimination as the result of such a past, he or she may well wish to limit the dissemination or availability of such information.
Mitigating the impact of such concerns is generally a matter of public policy. Health care enterprises and others with access to health care information can decide voluntarily to refrain from using a universal health identifier in particular ways, or mandatory mechanisms can be put in place by legislation. Legislative approaches might choose to prohibit discrimination in employment on the basis of patient information or prohibit the dissemination of patient information to employers. Nevertheless, it may be possible to design an identification and linking scheme that can satisfy the needs of the health care industry without jeopardizing patient privacy or that can help enforce any policy framework established for protecting privacy. For example, it may be possible to design a system that does not rely on a single number. Chapter 4 outlines some approaches for identifying and linking records. Chapter 6 contains the committee's judgments on these issues. The chapters include recommendations for extensive education of the public about threats to the privacy of health care information and criteria for ensuring that the development of any universal patient identifier explicitly recognizes its potential effects on privacy. They also include recommendations for the passage of legislation setting down the principles by which trustees of health care information are limited in its collection, use, and disposal and are responsible for disclosure of accesses to it. Finally, they include the development of technologies that control the integrity of, access to, and accountability for uses of health care information across all stakeholders.
Conclusions Regarding Systemic Concerns
Patient-identifiable health information has business value to organizations such as insurers, employers, providers, and drug companies. This value leads to organizational pressure to disseminate and use the data for purposes other than those for which they were collected. Individual patients are at a disadvantage in resisting this pressure because of the imbalance of power between them and these organizations.
Systemic concerns arise from deep differences among stakeholders as to what constitutes fair information practice. Every stakeholder that receives data about a patient has an argument to support its claims about a bona fide need for patient information. No consensus exists across society regarding the legitimacy of these needs and against which they can be independently assessed. Nor does consensus exist regarding the uses made of such information. This lack of consensus differentiates the security problem in the health care field from that of the military or financial
communities, for example, where a general consensus on information policy exists. As a consequence, security technology and practices from these other communities should be adopted only with great care.
Systemic concerns are exacerbated by technology, because computer networking permits rapid, large-scale, and unobserved access to data for uses never intended when the patient gave primary permission for the data to be recorded. To date, technological deterrents and obstacles play almost no role in controlling secondary use of patient information (i.e., use by nonprovider parties). Once the information leaves the hands of the health care provider, it is stored off-site with the secondary user, and access controls are at the discretion of that user site.
Systemic concerns will be reduced only by public policy decisions that influence the behavior of stakeholders regarding data privacy and security. These public policy decisions are necessary to rationalize the relationships among the various stakeholders (e.g., to spell out the acceptable uses of health care information by nonproviders and providers alike) and to reduce the incentives for wholesale release of patient information. Put differently, public policy must add up to a comprehensive whole that covers the entire network of use, including both primary and secondary uses of data. Because there is no consensus across society about what is acceptable, public policy in this area is difficult to make, but until such policy is in place, there is a progressive danger that care will be affected by patients' reluctance to confide in providers.
Systemic concerns are linked to development of a universal patient identifier, which, depending on its format, could facilitate the linking of patient-identifiable health information with other types of personal information. Although addressing this problem is largely a matter of public policy, judicious design of the method used to link patient records may help mitigate some privacy concerns and help enforce any policy framework established for protecting privacy.




























