4—
A Framework for Assessing Risk to Deployed Forces
The proposed framework for risk assessment of threats to deployed U.S. forces is intended to organize risk-assessment activities. It is divided into several components, providing places for various analyses, and organized to illustrate the role of each activity and how it contributes to an overall analysis of risks to deployed forces. The object is to foster a systematic approach to recognizing and cataloging potential hazards, founded on examination of the various activities and settings of deployment. Each recognized scenario or sequences of events that could lead to potentially hazardous exposures is divided into components for analysis, and these analyses can then be applied in judging the likelihood that potentially hazardous exposures will indeed be encountered and, if encountered, the probabilities that adverse outcomes will be engendered. This information can then be used to consider modifications of procedures, equipment, and actions to avoid or mitigate risks with the awareness that actions taken with respect to one risk might affect others and might need to be weighed against the needs of the military mission.
The framework puts great emphasis on recognition of potentially hazardous activities, including systematic processes to uncover previously unrecognized ones. It also emphasizes anticipatory analysis and contingency planning before actual deployment as a means for identifying preventive measures and allowing risks to be carefully analyzed before they actually arise. Finally, it provides for the collection of appropriate data before, during, and after actual deployments.
The framework is characterized by three major enterprises—ongoing strategic baseline preparation and planning, specific deployment activi-
ties, and post-deployment activities. These enterprises are characterized by separate modes of activity and analysis, but are connected to each other by their common application to achieving the goal of assessing risks to deployed forces and by their need to incorporate each other's results. The elements of the three enterprises are presented in Boxes 1, 2, and 3, and how these elements fit in the overall framework is illustrated in the form of a hierarchical tree diagram in Figures 1 to 6. Although a single tree encompasses the whole framework, owing to its complexity, it is necessary to represent the tree in a series of diagrams to indicate how the subparts are connected. Figure 1 presents the three major enterprises of the framework, Figures 2 to 4 depict the activities encompassed by the ongoing strategic planning enterprise, Figure 5 outlines activities to be undertaken during deployment, and Figure 6 illustrates the post-deployment enterprise. This chapter explains and elaborates upon each of the risk-assessment activities of the framework.
Ongoing Strategic Baseline Preparation and Planning
Ongoing strategic baseline planning comprises all of the activities and analyses concerned with preparation, through analysis, systematic investigation, risk-aware design of procedures and material, and contingency planning for threatening eventualities before they occur. As such it includes all activities concerned with recognizing potential threats, anticipating the circumstances under which they might arise, and assessing and characterizing each kind of threat qualitatively and quantitatively. The aim is to make a thorough examination of the processes, activities, and settings that might arise during deployment, to identify potential hazards (including previously unrecognized hazards), and to subject them to appropriate analyses. Although the present report does not explore risk management in depth, the ongoing preparations also include preventive measures such as setting exposure standards and modifying procedures to avoid or ameliorate risks. The activities are not tied to specific deployments, but represent the continuing development of information about potential deployment risks and exposures, organized through the framework so as to create an ever expanding and improving base of knowledge. This knowledge can be drawn on to increase the capability to avoid or mitigate risk and to refine doctrine and training so as to lead to safer deployments. That is, the first phase comprises ongoing, long-term activities aimed at increasing preparedness for risk mitigation issues in specific future deployments, since planning and preparation for specific deployments (which fall under a second, subsequent phase of activity, described below) must often be conducted at an accelerated pace.
|
BOX 1 Ongoing Strategic Baseline Preparation and Planning Activities
|
|
BOX 2 Specific-Development Activities
|
|
BOX 3 Post-Deployment Activities
|
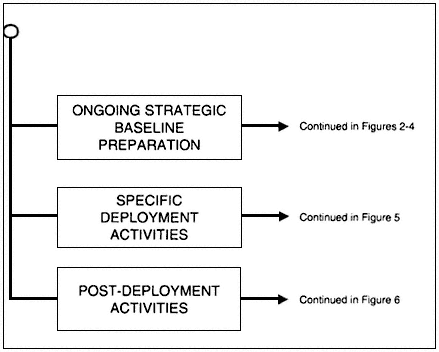
Figure 1.
The three enterprises of the proposed risk-assessment framework.

Figure 3.
Ongoing strategic baseline preparation (continued from Figure 2). The numbers correspond to the figures, which provide more detail about the activity.
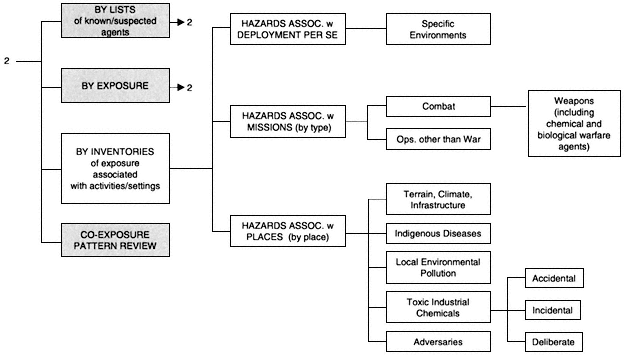
Figure 4.
Ongoing strategic baseline preparation (continued from Figure 2). The numbers correspond to the figures, which provide more detail about the activity.
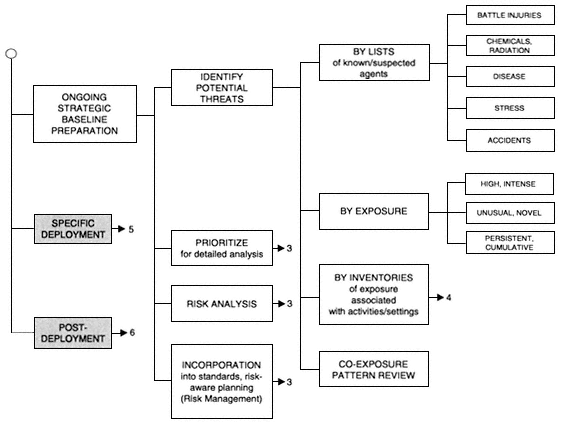
This phase of analysis is clearly large and complex, containing many distinct components of activity (Figures 2 to 4). It is divided into four major steps: (1) identify potential threats; (2) develop priorities for detailed analysis; (3) conduct a risk analysis; and (4) incorporate understanding of risk into standards and risk-aware planning (i.e., risk management).
Identify Potential Threats
The first step is to identify potential threats, both the agents of harm and the circumstances, activities, and settings that might cause potential threats to be realized. The aim is to systematically sort through activities to identify potential sources of hazard, including ones that might not have been recognized in this setting, or at all. Unrecognized threats could include agents not previously listed as hazards or new properties of recognized hazardous agents (such as chronic toxicity from ongoing low-level exposure). Clearly, the task of sorting through the whole universe of deployment-associated activities and settings is daunting, and the call to identify all potential hazards, including novel ones, is idealistic in view of the scarcity of data that usually prevails. In practice, a series of screening exercises, described below, can be pursued. The point of setting such a challenging goal is to go beyond a focus on agents already on standard lists of hazardous agents and activities, or on the most obvious properties of those agents.
This step is different from the traditional process of hazard identification, which focuses on marshaling and interpreting the evidence regarding the toxic potential of particular agents considered individually. It is also different from the usual process of identifying a list of potential agents of concern (as one might do in evaluating a toxic waste site), because it seeks to identify hazards rather than simply recognize potential exposure to a list of known hazards. Unlike a toxic waste site, where the exposures are there to be measured, the task here is to imagine potential exposure scenarios and the likelihood that they will occur during deployment. What needs to be examined is not just the agents and exposures, but the activities and settings that lead to exposures.
The practical means that is recommended for pursuing this search for hazards is to conduct several different screening exercises in parallel, each based on a somewhat different rationale. The intent is that by approaching the common question from several different angles simultaneously, one increases the probability that situations in which potentially harmful exposures might arise are recognized as such. Examples of such approaches are to screen (1) by lists of known or suspected hazardous agents; (2) by exposure considerations; (3) by inventories of exposures
associated with various activities or settings; and finally (4) by conducting a review of the hazards identified by the previous three methods. This last approach is used to identify likely patterns of co-exposure among agents that should be given special attention due to the possibility of accumulative or synergistic effects.
Lists of Known or Suspected Agents
Notwithstanding the advice not to rely solely on established lists of hazardous agents, it is wise to begin by consulting such lists for presence of agents associated with deployment tasks. Established sources of characterization of hazards could be consulted for several different kinds of threats, including battle injuries, chemicals and radiation, disease, physical and psychological stress, and accidents. A paper commissioned by the National Research Council (NRC) for this project (Rose 1999; abstracted in Appendix A), lists many infectious diseases that should be considered.
In addition to the Department of Defense's (DOD's) own existing lists, hazardous agents can be sought from such sources as the U.S. Environmental Protection Agency (EPA) Integrated Risk Information System and Acute Emergency Guideline Levels for Hazardous Substances, the Agency for Toxic Substances and Disease Registry Toxicological Profiles, the Hazardous Substance Data Base, the American Conference of Governmental Industrial Hygienists documentation, the International Agency for Research on Cancer monographs, EPA Health Effects Assessment Summary Tables, the National Toxicology Program Annual Report on Carcinogens, and the State of California Proposition 65 list.
The review of such lists should go beyond the properties that caused the agents to be listed, because listing might be prompted by the most sensitive among several toxicity end points or by a particularly prominent toxicity end point. The hazards that an agent might pose during deployment might be affected by likely exposure patterns that differ from those considered in the original listing. Similarly, the presence of an agent on some list of toxic compounds is not a substitute for full hazard identification. The object of this initial step is to recognize potential hazards for fuller consideration in the risk-analysis step.
Exposure
A second means of seeking potential hazards is to examine agents with notable exposure patterns. The aim of this process is to identify agents to which deployed troops are likely to be exposed, putting a premium on the need to understand their potential hazardousness. The thinking here is similar to that applied to the current discussion about
testing of high-production-volume chemicals (Environmental Defense Fund 1997). In this process, agents call attention to themselves through particularly high or intense exposures in the deployment setting; exposures that are unique to the deployment setting (or at least are unusual elsewhere); through exposures to new compounds (such as prophylatic medicines or combustion products of innovative materials); or through exposures to persistent compounds or those that might accumulate in the body. For agents with such exposure patterns, there is a high premium on DOD's ability to address the potential for toxicity, and if sufficient data are lacking, a high priority for appropriate testing is indicated. Although most agents that receive attention due to notable exposure patterns might end up not being particularly hazardous, establishing that this is the case is an important part of attending to the possibilities of threats to the health of deployed troops.
Inventories of Exposures Associated with Deployment Activities and Settings
Under this approach, the main focus is on examining activities and settings for the exposures and the potential risks they entail. As such, it represents the greatest departure from the usual approach of beginning with agents and exposures and then examining the activities where potential hazards arise. In this task, methods can be borrowed from the disciplines of life-cycle impact analysis and pollution prevention (Curran 1996; Barnthouse et al. 1997; Pojasek 1998; NAE 1998). The method entails systematic review of the activities that occur during deployment, and for each one, considering what exposures it entails, what materials it consumes, what waste products it emits, what products it produces, where the inputs will come from, where the outputs will go to, and the accidents and failures that might occur. The outputs of some processes might become the inputs of others. The point is not simply to scan or examine activities for known or obvious hazards, but to use the exercise to prompt consideration of what might be hazardous and what investigation is needed to understand its safety and risks.
This process serves several purposes. It constitutes an aid to recognizing potential hazards that might not otherwise be obvious. It highlights exposures to agents that are insufficiently understood and provides a basis for developing investigative priorities of such agents. It serves to link exposures to hazards directly to the activities that cause them, facilitating the development of risk-control measures, and it puts the development of such measures directly into consideration of the whole spectrum of threats that an activity could entail (and which might be affected by measures to control one of them). It also serves as a basis for linking
events into scenarios for quantitative analysis of the likelihood that potential hazards will indeed lead to adverse impacts.
The application of this approach in the military situation should be particularly fruitful because, in contrast to most organizations, the military has already put a lot of thought and analysis into how it conducts its tasks. To organize the task of examining activities and to enhance the utility of such an analysis in planning particular deployments, it is useful to break the process into parts that focus on (1) activities associated with deployment per se, (2) activities related to type of mission, and (3) hazards associated with particular places.
Activities associated with deployment per se are those entailed in most deployments as a result of needs for transportation and the provision of food, water, and shelter, as well as those associated with widely used equipment. These activities would include use of pesticides and insect repellants, standard vaccinations, waste disposal, exposure to exhaust fumes, and exposures associated with the operation and maintenance of military equipment. In short, they cover all of the potential hazardous exposures that deployed forces bring with them wherever they go on whatever mission. It might be useful to further segregate this category into subcategories describing deployments to different classes of environments, such as warm or cold, wet or dry, urban or rural.
Activities associated with missions include those specific to the type of mission the deployed forces are sent to accomplish. Clearly, combat has its own distinct set of activities and hazards, and this could usefully be broken up into a number of subcategories. Threats from the use of chemical and biological weapons (including the hazards associated with protective measures against those weapons) could form its own subcategory. The wide variety of missions for operations other than war could be classified into categories of efforts that entail distinct sets of activities and exposures to potential hazards.
Hazards associated with places, the third category, comprise those threats that are indigenous to the places where troops are deployed. The key here is to develop information about hazards that might be encountered in different locations around the globe so that this information will be available if ever needed. Information should be gathered on climate, terrain and infrastructure, on industrial facilities and the materials used, on the degree of contamination of local environments, and on the identity of the contaminants. Especially important is the question of local endemic diseases, because many of these may be unfamiliar and poorly studied.
Hazards associated with places can be subcategorized into those attributable to (1) local terrain, climate, and infrastructure (bridges, dams, flood-plains, and roadways); (2) indigenous diseases and vectors; (3) local envi-
ronmental pollution; (4) toxic industrial chemicals; and (5) various adversaries that U.S. forces might face. The threat from toxic industrial chemicals (as distinct from local pollution) comes from the possible release of stored chemicals or supplies at industrial or depot sites. Such releases might be entirely accidental, occur incidentally as an unintended consequence of other activities (e.g., a storage tank being hit by an errant missile), or be released deliberately by sabotage or terrorism. Assessment of the variations in threats associated with adversaries relies on judgments about potential opponents' military capabilities, weaponry, and tactics.
Dividing the inventory of activities associated with deployment into components allows the development of a base of information that can be used quickly when a new deployment is anticipated. This inventory generally can be combined with that appropriate to the specific mission and that to the specific location of the deployment to yield a deployment-specific catalog of threats. This inventory also gives opportunities to note the ways in which particular hazards might vary in their importance in different specific deployments, for example, if several agents with similar mechanisms of toxic action might be expected to be experienced together in certain combinations of mission and location.
Co-exposure Pattern Review
Co-exposure pattern review constitutes an evaluation of the results of the previously discussed examinations of hazards, notable exposures, and inventories of activities. The review is used to identify instances in which simultaneous exposures to agents might be a result of several different activities, possibly leading to greater effects than if the various exposures were experienced separately. It will also identify cases of simultaneous exposure to different agents that might be suspected of acting synergistically. Determining which combinations of agents have the potential to interact in this way is a difficult challenge. The matter is discussed in much more detail in a paper commissioned by the NRC for this project (Yang 1999, abstracted in Appendix A). Agents that affect one another's pharmacokinetics, that act on similar target organs, or act by similar mechanisms of action are prime targets for such considerations. The aim of this review step is to identify those situations that should be subject to deeper scrutiny and perhaps toxicological experimentation (see Yang 1999).
Develop Priorities for Detailed Analysis
The inventory created in the step that identifies potential threats might be quite large, and a clear view of potential hazards might in many cases be hampered by lack of data. An exercise to develop priorities is therefore
necessary to identify those situations most in need of further analysis and data collection. In addition, in cases in which the emergence of adverse effects follows from a complex chain of events, each of which requires analysis, it is necessary to decompose the scenario into its components, all the while assuring that all components in the chain receive sufficient attention so that the priority of the originating scenario is maintained. An example of an event in a complex chain that might require analysis would be a mechanical failure of a device leading to released chemicals in a wind-blown plume leading to contaminated vegetation through which troops may need to pass.
This step to develop priorities has similarities to the discipline of comparative risk analysis in that it seeks to compare a wide array of hazards and identify which ones have the greatest likelihood of occurring and the greatest potential impact, and therefore deserve priority attention. (It differs, however, in that one is developing priorities for potential hazards for further risk analysis rather than preparing risk estimates for regulatory attention.) There are several criteria that would suggest high priority:
- Likely to Occur. Those hazards most likely to be experienced in practice should be given high priority, all else being equal. Hazardous activities or events less likely to occur (but having consequences if they do) can receive lower priority, but need to be investigated in time, or else one runs the risk that the unlikely events transpire before an investigation has been done.
- Mission-critical. Hazards that could affect the chances of success of military missions must receive high priority for attention.
- Known Threat. If the potential impacts of a hazard are known, then scenarios involving exposure to that hazard, or unresolved questions about the circumstances that might lead to exposure, need to be investigated.
- Potential Impact. All else being equal, hazards with large potential impacts, including those that have effects beyond the immediate actual losses, should receive high priority. Low-probability, high-impact events can be given lower priority but should not be ignored simply because they are unlikely, because even the expected value of loss might be large. There is some obvious and unavoidable circularity in these criteria because one has to do some quantitative analysis of probabilities to know that a hazard is likely, critical, or large. The process of developing priorities must be based on extant or preliminary information, experience, and judgment. When priorities are sensitive to judgments or assumptions that might be questioned, obtaining information that can resolve such issues itself becomes a priority.
- Special DOD Responsibility. It is important to identify potential hazardous situations that DOD might be especially held responsible for investigating before allowing its troops to be exposed. It is difficult to define in general terms what those situations are, and attempting to do so is beyond the scope of this report, but instances can be recognized, mostly having to do with things that are not ''supposed to be" risky, but that in fact might be. These situations include exposures that are special to military situations and not experienced by civilians, and situations in which the military exposes troops to agents with unknown properties for its own military mission. DOD should consider how its special responsibilities might be construed and how to apply this understanding to the question of investigating hazards.
The object of developing priorities is not to sort those hazards that will be investigated from those that will not be. DOD ultimately has responsibility for investigating all of the potential hazards. The point of developing priorities is to provide the military with a rational sequence of hazards to assess.
Data Limitations
Risk analysis must always contend with the challenges of limited data. Guidelines for action in the face of harmful impacts will always be needed, while the information on which to base such decisions will always be limited, leaving some uncertainty about the existence and magnitude of risk. From case to case this uncertainty might vary but will always be present, and its impact should be judged against the urgency of the decision the analysis is meant to inform and the gains or losses to be experienced under alternative courses of action. Risk analysis does not require certainty about the hazards it attempts to characterize; indeed, as argued in Chapter 3, risk analysis might best be viewed as an investigation into our uncertainty about what potential impacts might befall the subjects of the analysis. This uncertainty comes not only from the contingency of outcomes on unknown future events, but also from our incomplete understanding of the applicable causes and effects.
The present framework urges a very comprehensive approach to investigating potential threats to deployed forces; it advocates consideration of the whole spectrum of potential threats from diverse sources and it calls for attention to all potential health effects of agents, not just those causing the most notable effects or those calling attention to the agent as a hazard in the first place. This approach is necessary if one is to be proactive about recognizing potential hazards, but the wider this net is cast, the
more data will be needed and the more instances will be encountered where attempts to characterize risks must be based on a very meager base of relevant information.
There are three areas in which data might be lacking. First, existing information might raise possibilities of adverse outcomes following exposure, but the data might be insufficient to provide robust answers about the magnitude or even the true existence of the risk in the population of interest. This leads to uncertainty in the characterization of tentatively recognized threats. Second, there might be insufficient data about actual levels of exposure or about the profiles of susceptibility of those exposed, leading to uncertain application of the understanding of the hazard in a particular instance of interest. Third, there might be adverse effects from an agent that are currently unrecognized because the agent has not been appropriately tested or because the existing tests are not sensitive enough or applicable to the human exposure settings of interest.
In facing the limitations of data, there are two pitfalls to be avoided. The first is to confine attention to those cases that are relatively data rich, on the grounds that more satisfactory, dependable answers can be obtained. This can result in overlooking important risks simply because they are have been overlooked previously. The second pitfall is to get bogged down in attempts to supply all the missing data, bringing all cases up to some ideal standard of information availability before seriously considering their risk analysis. Since resources are always limited, this quest can never be fulfilled.
Faced with many risks to consider, a paucity of data about them, and limited resources to gather new data and conduct the risk analyses, what is a responsible risk analyst to do? A two-pronged approach is necessary. First, risk analysis must be content to say what can be said and not only to acknowledge the inevitable remaining uncertainty, but to try to characterize that uncertainty so that appropriate perspectives on the meaning and robustness of the analysis are expressed. Historically, this approach has been stronger in some sub-fields of risk analysis than in others. It is an area of active methodological development, and DOD is advised to participate fully in this endeavor. Discussion of specific methods is beyond the scope of this report, but general accounts are available (Morgan and Henrion 1990). The general approach follows from the conception of risk articulated by Kaplan and Garrick, discussed in Chapter 3. The alternative possibilities for outcomes are laid out and their relative likelihoods are assessed in view of the data available—the better the data are able to narrow down the reasonable interpretations, the higher the likelihood associated with those outcomes and the lower the weight given to alternatives.
Characterization of uncertainty and the limitations of available data are important to all risk analysis, but they might play an especially impor-
tant role in the analysis of deployment threats, where high-consequence decisions might require taking one risk to avoid others. Risk management approaches exist to help make such decisions, but when the risks to be compared are quite uncertain, or uncertain to different degrees, good characterizations of the uncertainty is necessary in order to arrive at sound solutions.
In addition to such characterization of uncertainty, the second prong of the approach is to reduce the uncertainty by gathering more data. Given the limitation of resources, only a small amount of new data will be obtainable, and thus prioritization is necessary. Among competing needs, the relative priority for obtaining data should depend on (1) the costs of not having the data (such as losses due to suboptimal actions in the face of the uncertain risk, e.g., undergoing significant costs to avoid an exposure that actually poses little risk or failing to take easy measures against an unrecognized risk); (2) the costs of obtaining the data; and (3) the likelihood that the data, if obtained, will help settle the outstanding issues or result in a sufficient reduction in uncertainty that it was worth obtaining the data. Methods to employ these principles in determining the benefit of additional data on a risk question are codified in the established quantitative discipline of Value of Information Analysis (Clemen 1990; von Winterfeldt and Edwards 1986), which is further discussed in the companion report on exposure (NRC 1999a). The methods readily consider the costs involved with the delay entailed in waiting for data to be developed, an aspect that is useful in the deployment context, where issues arising during actual operations might need rapid responses on a timescale in which some information (such as exposure information) might be obtainable sufficiently quickly, while other information (such as toxicity information) might not be.
The criteria for developing priorities for detailed analysis of threats acknowledge that the risks in need of analysis are many, the applicable data are few, and the abilities to obtain additional data are limited. The criteria provide a guide to how pressing the need for analysis is in one threat relative to another. To the degree that a threat has high priority, it is important to consider obtaining the data necessary to understand it. That is, the priority gives a rough measure of the cost of not having data, referred to above, and the approach of Value of Information Analysis can be used to determine allocation of limited resources for obtaining further information.
Experience also provides important information about hazards, their impacts, and the circumstances that lead to manifestations of health and safety risks. As risk assessments are conducted, insight is gained into the nature of key questions, and data needs might be suggested, which should feed back into the prioritization of research. Tracking of the health expe-
rience of personnel during and after deployments provides important information that needs to be captured and fed back into the risk assessment process. These matters are more fully discussed later in this report and in an accompanying report (IOM 1999).
Risk Analysis
Once hazards and the circumstances under which they arise are identified, the tools of risk assessment can be applied to characterize hazards and exposures, and to conduct quantitative estimates of risk. These results can then be incorporated into decision making, such as planning, design of doctrine and standards procedures, and training. The risk-analysis step constitutes the core of the framework proposed here.
The hazards of concern vary a great deal in their nature, and their analysis varies greatly in the information available with which to characterize them and in the methods that have been developed to carry out that characterization. Risk projections might be based on actuarial data of past observations or incidence rates (e.g., the number of road accidents per vehicle-mile traveled), analogy with familiar risks, experimental data, or expert judgment. The confidence in the risk analysis will vary with the degree to which the setting for which estimates are made resembles the settings that are the basis for projection.
This section notes some commonalities among risk-assessment methods for different kinds of threats and calls attention to some special aspects of assessing risks for the purposes of protection of deployed forces. These matters may affect both the analytic methods and outcomes of risk assessments.
The general approach outlined in the NRC paradigm for risk assessment (NRC 1983) can be applied, not only for toxicity of chemical agents, but also for microbial and physical hazards. This paradigm facilitates focusing on the nature of the adverse impacts of concern, determining the measurable features of particular settings that affect the probability and/or severity of various adverse outcomes, and expressing the best estimate of the magnitude of risk as a function of those measures of exposure to the hazard.
In certain cases, the potential for exposure is more important to assessing overall risk than the potential response to the exposure (Rodricks 1999). For example, a high rate of casualties is expected among unprotected troops immediately downwind of a major release of a volatile nerve agent. The exact level of impact depends on the degree of exposure and the responses of the exposed troops, but the principal driver is the likelihood that such a release indeed happens. The real larger question is what is the risk to troops "exposed" in the sense that they are
present in a theater where weaponized nerve agent is present in the hands of an adversary. In this situation, the threat is not the nerve agent per se; instead, it is the course of events that leads to uptake of some small amount of the nerve agent. To address this larger risk question, one must assess the probability that the weapons are indeed used (contingent on the development of the conflict, assessed using military judgment and war-game simulations), the probability that they produce appreciable concentrations at the troops' location (contingent on winds and terrain and the locations of troops vis-à-vis the release point, assessed using fate and transport models), the probability that warning and protective measures fail (contingent on the performance of devices, equipment, and the troops themselves under duress, assessed using mechanical failure models, experiments, and training experience), and only finally (and least critical to the calculation, owing to its lack of case-by-case variation) the probability that an individual that takes up some agent succumbs to its toxic effects.
This view broadens the more typical exposure assessment procedures of exploring various modes of exposure and estimating variations in levels of uptake, by including the probabilities that the different exposure scenarios actually occur. The point here is that, for many situations of interest in protection of deployed troops, the likelihood that unfolding events might produce exposure might be of prime importance in assessing the overall magnitudes of risk.
The value of the Kaplan-Garrick definition of risk, discussed in Chapter 3, should be evident here. Beginning at a starting time and starting situation, one traces out the possible scenarios that describe the unfolding of future events, each scenario traced until its outcome of interest is reached. Because some scenarios require a chain of events to get to the outcome, the scenarios might represent compound events that might need to be broken up into a series of parts for analysis, each by appropriate methods. Often, it is useful to represent the unfolding of events in a tree diagram, with pathways of events splitting upon the occurrence of key events. The probability of each scenario transpiring (i.e., of each pathway down the tree) is estimated, and the probabilities for chains of events are estimated by finding the probabilities of their pieces, allowing for contingencies. The fact that the complex pathways are broken down into components for analysis does not alter the fact that the real risk questions are faced at the starting point of the analysis: What are the probabilities that the various end results will come to pass, and what impact will be suffered upon the arrival of each distinct possibility?
Structuring risk problems in this way is also valuable because it can clarify how risks change in actual situations as the events unfold, that is, as one proceeds down one branch of the event tree and not others. Con-
tinuing with the nerve agent example given above, once an agent-bearing shell explodes at a particular place, the issue of whether the weapon will be used is settled in the affirmative and the probability that a plume will move toward troops becomes highly case-specific, depending on the shell-burst site, the terrain, the troops' location, and the direction of the wind, all of which have the particular values for the current situation. This kind of analysis can be very valuable in planning responses to events, determining which properties of changing situations are key to the alteration of risks, and developing means to rapidly update generalized scenarios with situation-specific information. This information can then be plugged into the established analytical structure to give real-time risk information to commanders in the field.
Some of the key aspects to consider in risk analysis are the probability of release; the probability of exposure given release; the probability of a health effect given exposure; the probability of certain outcomes in specific deployment scenarios; and environmental consequences.
Probability of Release
The circumstances under which contained materials come to be released into the environment, and the likelihood of such releases, are frequently at issue. These are often approached using probabilistic fault-tree analysis to assess the chances of physical failures of the means of containment. The destructive forces of combat can greatly increase the probabilities of containment failures, even if the events are unintentional. To the extent that intentional human actions are involved in the releases (sabotage, terrorism, or use as weapons by adversaries), expert military judgment, experience, and the results of war games might have to be used.
Probability of Exposure Given Release
For agents that are released from specific places or at specific times, environmental fate modeling can be used to estimate the probability that releases lead to exposures of troops. Such modeling tends to be very dependent on local settings and conditions, however, because the various environmental components, the flows of media, and the impact of temperature, sunlight, and rainfall, can vary considerably. For agents that come to be well mixed into local air and water, or for local environmental pollution, the usual approaches for environmental contaminants can be used, in which the rates of consumption of air, food, and water are used to estimate ongoing intake rates of the contaminants they contain. The exposure factors that are used (inhalation rates, water consumption, body weights, exposure durations) should reflect the military situation, which
might be different from the exposure factors used in civilian environmental protection.
Probability of Health Effect Given Exposure
This is the central part of health risk assessment, and it entails the NRC paradigm (NRC 1983) components of hazard identification, dose-response analysis, and risk characterization.
Hazard Identification
Hazard identification is distinct from the earlier step of identification of potential threats in that the aim is to assess the weight of evidence as to an agent's toxicity in humans. For some toxicity end points, such as carcinogenicity, formal schemes for weight-of-evidence classification have been proposed, such as those used by the EPA (1996) and the International Agency for Research on Cancer (IARC 1987).
Dose-Response Analysis
Dose-response analysis for exposure to toxic agents describes how the probability of manifesting a toxic end point varies as a function of the magnitude of exposure. Extensive discussion of the methods for this type of analysis, and their pitfalls and interpretations, have occurred over the last two decades and have recently been summarized by Olin et al. (1995). Some issues of particular importance to the assessment of risks to deployed forces bear mentioning, however.
First, what is needed from a dose-response analysis is more than just a definition of exposure levels that can be considered "safe." In environmental or occupational health regulation, the intent is to eliminate unsafe exposures, but in the military setting, it might be especially necessary to consider possible impacts of exposures that are not classifiable as safe. The reason for this is that such exposures might be unavoidable or might be endured intentionally, and to not consider such exposures might engender a more consequential impact on the health of troops or the success of the military mission. Thus, definition of exposure levels that are expected to engender different levels or severities of toxic responses will be one of the ends to which the results of dose-response analysis will be put. This issue is further discussed by Rodricks (1999, abstracted in Appendix A).
Second, for similar reasons, the establishment of "conservative" estimates of dose-response relations, that is, those designed to err on the side of safety when faced with uncertainty about how to project expected human responses from available data, might not be appropriate for cer-
tain military uses. When risks cannot be avoided and decisions are made to accept some risks rather than others, or to bear some risk in furtherance of a more fundamental military objective, it is important to make these trade-off decisions with unbiased estimates of the impacts of various courses of action. In other applications, such as the setting of health-protective exposure standards for application in less severe circumstances, conservative estimates might be much more acceptable and indeed desirable. In essence, these are actually questions about the risk-management application of dose-response analysis. The important point here is that such analyses is conducted and its results presented, so that the different uses appropriate for different risk-management settings can be made.
Dose-response analysis for exposure to infectious agents is one that has developed rapidly in recent years. Advances in modeling strategies and the use of data on infection rates after different dose levels in human volunteers have led to descriptions of dose-response patterns for a number of important microbial agents. Currently, these models are better developed for description of infection rates than they are for describing the probabilities of appearance of disease symptoms among those who are infected. The challenge for the risk assessment of deployed forces will be to account for the fact that many microbial risk questions will be about agents that have not been well studied. Indeed, many disease organisms indigenous to various parts of the world have not been properly recognized and described. Attack rates on local inhabitants might be misleading as indicators of effects on American troops encountering the agents for the first time. The issues and challenges of microbial risk assessment in the context of protection of deployed forces is discussed in a paper commissioned by the NRC for this project (Rose 1999, abstracted in Appendix A).
Interactions. Another point to consider is that deployed troops might be exposed under conditions of physical or psychological stress. The effects of stress on the toxicity of agents is not well understood, but there are indications that stress might potentiate effects of other agents. There is the related issue of the effects expected from simultaneous exposure to several agents. In general, the degree to which the toxicities of different agents can be expected to interact is poorly understood and the matter of some controversy. Experimental approaches to this question can be considered, however, and particular attention needs to be paid to those combinations of agents that are identified as in need of scrutiny. The issues around these matters and experimental approaches that have been taken and can be considered are discussed more thoroughly in a paper commissioned by the NRC for this project (Yang 1999, abstracted in Appendix A). These issues are particularly critical for the program of health protection
for deployed troops in view of the controversies that have already arisen regarding the potential association of suites of symptoms in veterans of past conflicts with exposures to mixtures of agents that would not be expected to cause such effects individually.
Dose-Time Analysis. Still another critical question is that of duration of exposure and the importance of dose-rate effects. Many (although by no means all) exposures in environmental and occupational health regulation are chronic, low-level exposures that might be experienced at similar levels day after day, and the experimental approaches taken to test agents for toxic effects tend to reflect this in their consistent patterns of daily exposure. In cases of episodic exposure, however, it is not always clear how to apply assessments based on constant-dose rates. This is an ongoing issue in quantitative health risk assessment, but it applies particularly to troop deployment, where the durations of exposure might be indeterminate (depending on the length of deployment) and where transient episodes of high exposure might be encountered. The question is not simply about applying chronic exposure studies to estimation of risks from more acute exposures to troops—the opposite extrapolation is also of concern in cases in which the acute toxicity of agents might be well studied (such as agents in chemical weapons), but the effects of chronic, low-level exposures might not be. A consistent pitfall is the natural tendency to focus on obvious, known hazardous agents and their properties, such that other important effects may be overlooked.
Two basic approaches have been taken to address the question of duration and dose-rate. The more traditional approach is to consider toxicities appearing after dosing on different time scales as separate phenomena, with each time scale requiring testing and analysis of its own. In this approach, acute toxicity, subchronic toxicity, and chronic toxicity are separately characterized by experiments using single doses (or at least a very few doses repeated for at most a few days), doses repeated over several days to weeks, and doses repeated for a substantial portion of lifetime, respectively; separate assessments of dependence of response on dose level are made for each duration category. An application of this approach designed for the case of deployed forces risk assessment is presented by Rodricks (1999, abstracted in Appendix A). The approach also addresses the need mentioned above for determination of doses associated with different levels of adverse impact, not simply those deemed without undue impact. Rodricks proposes a matrix of dose levels that has the duration categories along one dimension and the levels of severity of toxic response along the other. The tabulated doses are those judged to be great enough that effects of the specified severity levels might begin to be expected to occur among people exposed for the various durations. This
kind of approach to the problem has the advantage of providing a straightforward, easily interpreted guide to what might be expected as consequences of roughly categorized patterns of exposure. This guide could be particularly useful for rapid decision-making in emergency situations or during deployments, when the information about an exposure is likely to be approximate regarding level and duration. The disadvantages are that the categories are necessarily rough, that intermediate cases are not easily handled, and that exposures that continue over time but are intermittent or vary in intensity are not really addressed, because it is not clear whether their similarities to acute exposures or chronic ones are most relevant.
An alternative approach to duration and dose-response is to attempt to address both the level and duration of exposure in the description of the dose-response relationship in a way that generalizes not only over dose levels but also over time. This is a more ambitious undertaking, and methods are under ongoing development. An analysis of how such an approach could work is presented by Rozman (1999, abstracted in Appendix A). Rozman notes that toxicity of ongoing exposures is a function of the balance between rates of biologic damage and repair. By observing how the rate of encounter with an agent, and the duration of that encounter, interacts with the time scales of the damage and repair processes, it is possible to generalize the description of the dose patterns necessary to generate a toxic response, and also to define conditions under which constant concentration-time products are expected to produce similar responses and those in which they are not. The advantage of this approach is that it makes use of toxicity data from experiments across a range of durations, integrating them into a single toxicological interpretation, and it provides an avenue to consider more complex patterns of variation in exposure level over time. The disadvantage is that many experiments as currently conducted do not provide good information on the role of time. Moreover, in a field situation, the eventual duration of an exposure might not be known when an agent is first encountered, and so duration categories might have to be rough approximations anyway, as in the first approach. Each approach has its advantages, and it is worthwhile pursuing both lines of analysis for application to assessment of risks to deployed forces.
Risk Characterization
Using the information gleaned from the hazard identification and dose-response analysis steps, quantitative estimates of risk can be generated to provide a general understanding of the type and magnitude of an adverse effect that could be caused under particular circumstances or scenarios. Characterization of the uncertainties associated with these estimates is also
an important part of this step. In cases where little quantitative data are available for analysis, qualitative characterizations can be made.
Recognition
As discussed earlier, a view of risk scenarios as trees of unfolding events over time helps to organize thinking about the complex chains of circumstances that lead to environmental releases, exposures, and possible adverse reactions. In this regard, the framework becomes a useful tool in noting which outcomes become more likely and which ones less so, thus guiding actions that might be taken to avoid or ameliorate looming risks. To take advantage of these opportunities, it is necessary to recognize any relevant changes in circumstances. Thus, part of the risk-analysis process should seek out opportunities to gather information for updating or altering the probabilities associated with different outcomes of uncertain processes. Practices to gather such key information can then be designed for use in actual deployment. Analysis of the components of complex risk scenarios to determine which are most responsible for overall uncertainty, and the resolution of which issues could most decrease that uncertainty, will contribute to this.
Environmental Consequences
Some agents released into the environment might persist for long periods, even if they do not pose an immediate threat to troops. This could affect deployed troops in the longer run, and it could become an issue if departing troops were seen as having left a contaminated environment behind. An analysis of environmental persistence of any emissions should therefore be part of the risk analysis.
Incorporation into Standards and Risk-Aware Planning
While defining a risk management program is beyond the scope of the present framework, which is aimed at identification and characterization of risks, it is important to provide a context in which the risk assessment results can be brought to bear on practical actions that may be taken to protect the health of deployed forces. The risk management tasks outlined below constitute the use and application of knowledge about threats to health and safety, and it is important to keep these ends in mind when characterizing risks so that the information obtained is appropriate and useful.
The final step of the ongoing strategic baseline preparation phase of the framework is the incorporation of the understanding of risks gener-
ated by the previous steps into planning, design of doctrine and standard procedures, and training. Incorporation involves the parts of risk management that can be conducted in the realm of generalized planning and preparation, by forging procedures, capabilities, and standards that will achieve reductions in threats to troops and establish appropriate decision-making practices that can be put to use in the eventuality of actual deployments. It uses the insights into risks posed by various activities and eventualities to plan how to conduct future operations with minimal unnecessary risk and to protect the health and safety of deployed forces to the maximum extent feasible.
Because the focus of the present framework is risk assessment rather than risk management, the treatment of this aspect will be brief, but it is clearly critical if the information developed about potential threats is to become useful in making changes to achieve improved protection of deployed forces.
Incorporation into Design and Doctrine
This large category of activities is meant to cover all of those opportunities to change and improve the military's means and modes of operation during deployment by taking advantage of the insights into risks and their sources identified in the previous steps. It includes the design of equipment, including protective equipment and detectors, means of transportation, logistical support, and weapons to achieve reductions in risks. An important part of this activity is examination of the hazards associated with operation and maintenance of military equipment as well as the use of pesticides and prophylatic agents, hazards that would fall into the category of those associated with deployment per se, discussed earlier. It also includes design of procedures, development of tactics, and reviews of the way that various missions can be carried out, all with the aim of achieving a low-risk environment during deployment, where exposures to hazards are avoided when possible and effectively defended against when necessary.
Also included is the design of practices and procedures for medical surveillance and the development of capabilities for prophylaxis and treatment regarding adverse health effects associated with deployment activities (see IOM 1999 for further discussion). Questions of personnel selection for deployment based on vulnerabilities to risks would also fall under this rubric. The development of detection and exposure measurement techniques and of protective equipment and procedures are also part of this incorporation step (see NRC 1999a,b for further discussion).
During deployment, as exposure probabilities and the likelihood of impacts of hazards change, many decisions will necessarily be based on
data immediately available and whatever store of knowledge and analysis has been assembled beforehand. Procedures for gathering and assembling appropriate information and archived analyses, and for using these to make sound decisions, need to be established as a part of preparedness. The Army's 1998 Risk Management Field Manual (FM 100-14) is an example of this kind of preparation.
Development of Standards
The foregoing design activities are aimed at optimizing ways to modify actions and material to avoid as much risk as is feasible, and to deal with the risk that cannot be avoided. Another risk-management approach is to define exposure standards that are deemed to achieve some specified degree of protection, and then to screen activities to assure that these standards are met. Although it is unwise to rely on standards alone as a means of controlling risks to military personnel, setting exposure standards is important in establishing a benchmark for protection of health against expected risks. It provides a straightforward means of defining health-protection goals, monitoring activities to assure that those goals are achieved, and allowing for a quick, relatively nontechnical evaluation of the risk potential of situations that have not received detailed analysis. For operational reasons, procedures for determining whether an activity meets exposure standards are desirable because they are relatively easy to formulate and to implement, and they can serve as guides in situations requiring quick decisions based on scarce information by nontechnical decision-makers. The military already uses exposure standards of various kinds a great deal to ensure safety of ongoing operations and to guide decision-making about the special, more-intensive exposures that might occur in emergencies, some deployments, and combat.
Different kinds of standards are appropriate for different settings. Broadly, it is appropriate to allow for different durations of exposure, because a level tolerable for a short time without ill effect might not be so for ongoing exposure. It is also useful to allow for standards that admit some degree of toxic response but protect against incapacitation or irreversible injury for use in guiding actions in emergencies or when important risk trade-off decisions must be made quickly, such as in combat.
By analogy with occupational standards in the civilian arena, military standards for emergencies and cumulative exposures (such as radiation exposure) are useful. The military's operational exposure standards are intended to allow for ongoing exposure of indefinite duration during the conduct of ''normal" operations without ill effect, where "normal" means having to do with usual ongoing duties and activities, including military occupational activities. One could imagine a special set of operational
exposure standards with assumptions appropriate to limited-term deployments or deployment-specific activities, but in practice the military's usual operational exposure limits fulfill the intent of this kind of standard.
The Short-Term Chemical Exposure Guidelines for Deployed Military Personnel (ACHPPM 1999) are aimed at defining higher exposure levels that can be tolerated in a deployment situation with low likelihood of marked response. They use some military-specific exposure factors but do not make any special consideration for the effect of stress or other deployment-specific factors that might modify sensitivity to agents. They are also aimed at specifying relatively safe levels.
The scheme for reporting risk-assessment results proposed by Rodricks (1999; abstracted in Appendix A) suggests an approach to defining standards that acknowledges that in some situations one must bear adverse effects from exposures to accomplish some other end. This approach is seen most clearly in the Emergency Exposure Guidance Levels (NRC 1986, 1993b, 1998), which estimate air concentrations of substances that might produce reversible effects but do not impair ability to respond to an emergency for a period of an hour. Other standards that provide for different levels of tolerance of some toxic effects for various lengths of exposure could be imagined and could prove useful in particular settings.
A caveat raised before is worth repeating here: standards tend to be set on the most obvious end points, but one must beware of overlooking subtle effects from low-level exposures that might accumulate with repeated episodes of exposure or might manifest themselves long after exposure, even though the exposure causes no detectable immediate harm and might be classified as "safe" with respect to the end point on which short-term limits are based. A recent GAO report was critical of existing DOD procedures and doctrine on this question (GAO 1998).
Contingency Plans
The generalized planning aimed at improving capabilities can be supplemented by contingency plans aimed at specific classes of deployments. These would provide insights into what might be expected in deployments in specific world regions under specific conditions and for specific purposes. They serve as templates, complete with bodies of analysis, ready to be consulted in the eventuality that particular deployments come to be considered, and into which the up-to-date, region-specific information can be plugged. This addresses the problem that complex analyses are difficult to carry out quickly and thoroughly, so the degree to which they can be prepared ahead of time increases preparedness.
Training
The effectiveness of efforts to design procedures and equipment to further the cause of risk prevention depends on the proper and efficient actions of the troops, and training can advance this end. Because a large number of reservists are often deployed, they should be included in such training.
Review
In any complex program in which there are many activities that must interact productively to reach the motivating goals, the military should conduct regular reviews of how well its risk-assessment process is working and how its goals are being fulfilled. It is all too easy to carry out the activities on a list of tasks without ever really bringing the results to bear in the way that motivated the efforts in the first place.
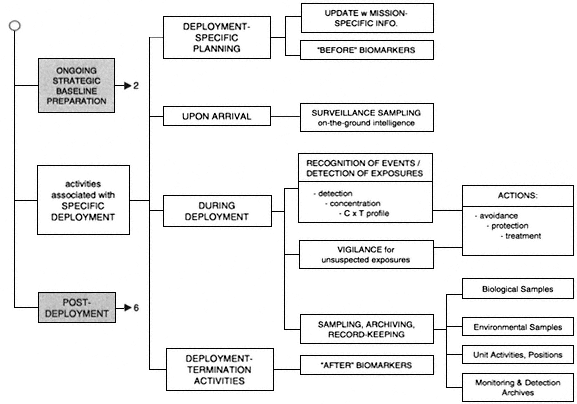
Specific Deployment Activities
The second major phase of the framework (Figure 5) addresses the use of these risk-assessment activities in actual, specific deployments. The key activities in this phase are to implement plans made in anticipation of deployment (ongoing strategic baseline preparations), update them with information specific to the deployment situation at hand, note the advent of threatening exposures when they actually occur, and activate the appropriate parts of the response plans accordingly. This phase must also include vigilance for exposures that, despite all the planning, were unanticipated. Finally, it must include collection and archiving of samples for future analysis.
Four subphases of activities associated with specific deployments are (1) deployment-specific planning, (2) activities upon arrival, (3) activities during deployment, and (4) deployment-termination activities.
Deployment-Specific Planning
Once a specific deployment is anticipated, but before it actually occurs, there is an opportunity to apply information specific to the location, mission, and current conditions, and to update and render specific the more generalized contingency plans that might have been developed in the first phase.
The kinds of information that can be applied include current meteorological conditions and forecasts for the immediate future, updates on the locations of hazardous materials, and current assessments of the capa-
bilities and inclinations of any adversaries that might be met. The ongoing strategic baseline analyses divided inventories of threats into those related to deployment per se, those specific to mission types, and those specific to places. The advantage of such a classification is that, when faced with a particular deployment, a situation-specific catalog of hazards can be created by taking all of the first list and adding those from the second and third lists that are appropriate to the particular mission and location. This situation-specific information can then be integrated into the earlier anticipatory analyses as part of the process of mission analysis and planning.
Biological specimens and health-status determinations are helpful tools in monitoring troops' exposures and health, and it is important to establish baseline levels among troops slated for deployment. Baseline information could be obtained by conducting annual health evaluations on reserve and active-duty personnel. Considerations for use of biological markers are discussed in much more detail in a paper commissioned for this project by the NRC (Lippmann 1999, abstracted in Appendix A). Lippmann argues that environmental and biological samples are a good deal less expensive to collect and archive than they are to analyze, and immediate analysis necessarily focuses on agents recognized at the time of collection as being of interest. It is therefore wise to archive most samples and to analyze them only once a specific hypothesis is formed that requires deeper investigation and specific analytical methods.
Activities Upon Arrival
The arrival of the deployed force might provide the first opportunity to collect on-the-ground intelligence. This should include obtaining local samples of soil, air, and water. Some of these should be archived to serve as baseline measures for future reference, but a subset should be analyzed to provide information on the extent and identity of local environmental pollution. Appropriate detection and meteorological instrumentation can be set up to provide the basis for feeding information into exposure models.
Activities during Deployment
This subphase also comprises the main part of the second phase of the risk-assessment framework. During the course of deployment, the key issue is detection of potential exposures and recognition of when situations and contexts occur for which useful prior analysis has been conducted. In the ongoing strategic baseline planning, hypothetical scenarios and schemes for the unfolding of possible threats, the consequences of each threat realized, and the likelihood that hazardous situations would be encountered.
Presumably, plans were formulated for appropriate responses to a range of various eventualities. During an actual deployment, the task is to discern which of the sets of contingent events imagined beforehand are actually transpiring and need a response. This is not merely the detection of agents of concern in the environment, it is the larger question of recognizing the determinants of the changing probabilities that various hazards will be encountered and will pose threats, and modifying actions accordingly.
Detection of Exposures
The detection of imminent exposures is an important aspect of during-deployment activity. (See NRC [1999a] for a discussion of detection methodology and capabilities.) The issue here is how such information can be used. A hierarchy of exposure information could be obtained. First is qualitative detection, which might be provided by a monitoring device that sounds an alarm when a concentration above a certain cutoff is detected. Such detection could trigger actions to employ protective equipment or to take evasive action, but it does not allow such actions to be modulated by the magnitude of the exposure. In many situations, this might not be a significant handicap, because the critical issue is the fact that exposure occurs at all. Next in the hierarchy is the measurement of a concentration (either instantaneously or averaged over some moderate interval). This kind of detection allows different actions depending on whether the concentration is high or low. There is no time component, however, so no allowance for the eventual duration of exposure or the particular concentration-time profile can be made, unless the time course can be guessed from the nature of the source of exposure. A yet more sophisticated detector might be able to keep track of the changing profile of concentration over time. Even if the time-concentration profile is critical to the toxic response engendered, information about the profile becomes complete only after the exposure is completed, and so such information might be of reduced value as a basis for modifying actions to avoid risk. If such profile information is recorded and saved, however, it might be valuable for dosimetry purposes in a retrospective analysis of the impacts of the exposure on the troops who experienced it.
Vigilance for Unsuspected Exposures
Detectors register the presence of those agents they are designed to detect, and prior analyses of threats address the situations that were anticipated, but necessarily exclude possible unexpected exposures. Detecting these in the short run is a challenge, because detection methods would have to be general enough to register whatever agents appear, yet not so
general as to react to ubiquitous innocuous compounds. Archived samples might be able to establish previously unsuspected exposures in retrospect. The issues involved in detecting unsuspected exposures, as well as other topics related to preparedness for health protection during deployment, are discussed in a report of the National Science and Technology Council (NSTC 1998).
Sampling, Archiving, and Record Keeping
It is important to take samples over the course of a deployment to document exposures. For practical reasons, the program of sample collection must be tailored to the force size, the nature and duration of the mission, and the type of activities the troops will be called upon to perform. Certain military occupational specialties with known high potential for exposures to particular hazards could be targeted for special attention in personal biological sampling and health surveillance. As noted, it is probably wisest to archive most of these samples until specific questions arise that require their analysis. It should be borne in mind that the surveillance methods have strengths and limitations, and appropriate, validated techniques are not always available. The considerations to be kept in mind when using biological markers are reviewed in a paper commissioned for this project (Lippmann 1999, abstracted in Appendix A). Samples are needed of (1) environmental samples to document initial levels and changes in concentrations over time; (2) information on unit activities and positions over time, so that these can be correlated with mapping of concentrations of agents; and (3) archives of the information gathered by monitors and detectors. Given that all of this information is of value chiefly in retrospect, the motivation to keep records and properly archive materials might be limited. It would appear wise to consider a moderate demand for such activity, but to act to ensure that that modest task is indeed carried out in a context of enormous pressure and demands for successful completion of the military mission. Medical surveillance and record keeping are discussed more fully in a companion report (IOM 1999).
Deployment-Termination Activities
DOD should consider the effectiveness and feasibility of collecting biological samples after deployment for comparison with baseline samples. Challenges in compliance are to be expected, given the troops' personal priorities upon returning home, so sufficiently rigorous enforcement of collection would be needed.
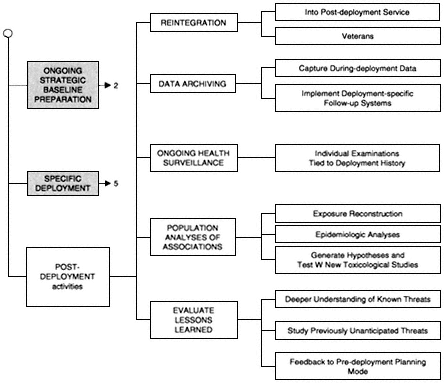
Post-Deployment Activities
The third and final phase of the overall risk-assessment framework (Figure 6) is the post-deployment phase. This includes the ongoing targeted medical surveillance of deployed veterans to identify late-appearing effects and analyze possible associations of exposure with later health experiences. These activities are discussed in more detail in IOM (1999). The focus here is on the gathering of information that can be fed back to ongoing research on the health and safety risks of deployment.
Enough information must be taken and carefully archived to facilitate reconstruction and tracking of troops' exposures over the course of deployment. The degree to which such exposure reconstruction can occur at the level of individuals or at the level of units depends on the amount of detail available in the records. Among the techniques that can be employed are to assess current exposures to groups that may be similarly exposed or exposed to agents with similar properties, to employ modeling of emissions and environmental fate to reconstruct environmental concentration estimates, and to estimate variation in exposure among individual troops through records of tasks and occupations they experienced during deployment together with estimates of typical exposure while conducting those activities. Exposure assessment approaches are discussed further in a companion report (NRC 1999a).
In a sense, all post-deployment activity is deployment-specific in that it focuses on examining the history and progress of veterans of particular actions. In another sense, however, it is not specific, in that it should be part of a program of following each person through his or her military career and beyond, maintaining job and exposure histories to track all of the factors that are thought likely to be relevant to health protection and the discovery of hazards. Each person will have been involved in a range of activities, and each person's health experience should be examined in the light of that whole history, integrated over specific episodes, including specific deployments. The issues involved with medical surveillance and record-keeping are further discussed in a companion report (IOM 1999).
It seems that possible environmental correlates of disease always bring out alarm-raisers and debunkers, whose public statements can raise public awareness of controversy about the analysis and interpretation of human experience. In view of the objectives of this framework to foster confidence in DOD's reputation as being diligent and responsible in its investigation of the potential causes of health complaints, DOD will have to think carefully about how it will conduct its own surveillance and retrospective analyses and how it will report on these matters to deployed veterans and to the public.
Several particular aspects of post-deployment activities are listed below.
- Immediate attention to the process of reintegrating troops returning from deployment into their normal military life, and reintegrating veterans into the civilian world, might help deal with some of the psychological strains that have proved to be issues in past deployments.
- Systematic processes for the collection and archiving of samples and data should be prepared before they are needed, and put into place promptly to receive data from new deployments. Constructing such mechanisms is really a part of ongoing strategic baseline planning, and setting up systems should not be done in an ad hoc way for each deployment case. It is important to establish a follow-up system, so the appropriate retrospective look at the deployment experience gets carried out systematically.
- Methods should be established to link the ongoing records of the health history of deployed veterans to the deployments that they participated in. Again, this should account for the total history of each person, rather than having records segregated by deployment. The methods should be established permanently rather than set up ad hoc for particular deployments.
- It is important that DOD take advantage of the data on human experiences with the hazards encountered during deployment and conduct ongoing studies. Unit activities data, archived monitoring data, and environmental and biological samples can be used to reconstruct estimates of doses, and these can be examined for association with disease patterns using epidemiological analyses. Hypotheses generated by these studies can then be examined with new tests and toxicological studies, as appropriate.
The points of the above exercises in surveillance and epidemiological analysis are, first, to maintain the ongoing responsibility of the military for the health of its personnel, and second, to learn from past experiences to provide better means for health and safety protection for future deployments. This pursuit can deepen understanding of known threats by adding data from actual experiences. It can in principle help to identify unanticipated threats and call attention to their need for further analysis. All of this information should be fed back to an ongoing process of recognizing and understanding the spectrum of potential threats to the health and safety of deployed U.S. forces. Responsibilities and policy for medical surveillance are given in the 1997 Deployment Medical Surveillance Directive 6490.2. Issues surrounding systematic approaches to post-deployment health surveillance, including the question of how to capture key information to feed back to characterization of incompletely understood health risks, are further discussed in NSTC (1998) and in a companion to the present report (IOM 1999).
Summary and Conclusions
Two general approaches could be used to organize a program to improve health protection from hazards that may be encountered in the military environment. One is to organize the risk analysis around hazards. When hazards are recognized, they are characterized and dose-response relationships determined, leading to definition of exposure levels that are deemed acceptable. These acceptable levels are expressed as standards, and activities that might lead to exposures and control measures to limit such exposures can be assessed as to whether they lead to the standards being exceeded, or the costs and effectiveness of various control strategies can be examined and the risks and benefits weighed. This mode of analysis is most appropriate when the nature and magnitude of exposures are well established and predictable, especially when exposures are ongoing.
A second approach is to organize the activities not around the hazards per se, but rather around the activities that one wants to conduct. This second broad approach is most appropriate when the activities can entail a number of different hazards, especially those that might or might not arise depending on the unknown future course of events. The activities are examined to improve understanding about the situations when hazards might manifest themselves and the likelihoods that those situations will arise. The exposures themselves are quite uncertain, and the risks of adverse outcomes are as much a product of the likelihood of the events leading to exposures as they are of the likelihood of adverse responses given that exposure occurs. A typical example of this approach is the fault-tree analysis of potential failures of a nuclear power plant, including a range of modes and amounts of releases that might follow different failure events, and the different environment fates of released materials depending on weather conditions at the unknown time of release. In such an analysis, the risk question is more about the probabilities of exposures of different numbers of people than about the health risk to a person given a certain exposure. Moreover, the whole spectrum of kinds of plant failure needs to be considered together, because adverse outcomes can arise in a number of ways.
Many of the hazards faced in deployment of U.S. forces are of this latter type, with the assessment of risks depending on the analysis of the uncertain events in exposure scenarios and the contingency on the course of events. Moreover, a key objective is to undertake a systematic evaluation of the sources of potential adverse effects, not simply a scanning of activities and scenarios for potential incidents of unacceptably high exposure to known hazards, and the chief challenge in this task is imagining the circumstances, activities, and agents, perhaps in combination, that
might lead to health and safety concerns and thus require further investigation and analysis.
The risk-assessment framework proposed in this chapter is a structured approach to gathering, organizing, and analyzing information in a way that encourages a comprehensive, integrated approach to the analysis of threats to deployed troops. As shown in Figures 1 to 6, the framework is characterized by a variety of component parts in which different types of risk-assessment activities are conducted. The organization scheme provides a rational structure for the overall risk-assessment process so that several things become clearer in the whole scheme: where each component activity falls, how each component contributes to the achievement of the ultimate goals, where each analysis takes its input information from, and where its results are used.
In general, the framework can be thought of as a scheme for how DOD can organize a comprehensive and integrated program. The framework is divided into three major categories—ongoing, during deployment, and post-deployment. The ongoing strategic baseline phase covers activities that should be done to prepare for possible future deployments. The first major step is to identify all of the major threats that deployed troops could encounter. The aim is to recognize the array of threats that require further analysis and set them in the context of the activities and settings that prompt them. Several parallel examinations—based on known hazards, notable exposures, and exposures associated with activities and settings directly—should be conducted, and from the combined results of these examinations, an inventory should be created of the agents and exposures and the relative needs for more detailed risk analysis.
After identifying potential hazards to deployed troops, the next step is to develop priorities for which hazards have the greatest likelihood of being encountered and pose the greatest threats to the military mission and to troop health. This task should be based on extant information, experience, and judgment to give the military a rough but rational sequence of hazards to assess.
When priorities have been set, the tools of risk assessment can be applied to quantitatively characterize the hazards, exposures, and outcomes. At this stage, the projected or estimated release, of exposure given release, of health effects given exposure, of certain scenarios unfolding, and of environmental consequences are all used to develop an overall scheme to identify realistic scenarios for given events. The practice of quantitative health risk assessment is best developed for questions concerning exposure to chemical agents and radiation, but can also be applied to microbial threats. For threats from accidents of various descriptions, actuarial data are the best guide, because a large body of documented experience is available and applicable to future settings. The results of these types of analyses can then
be incorporated into planning, design of doctrine and standard procedures, and training. The framework does not provide a useful way to estimate combat casualties, which must still be derived from experience, military judgment, and the analysis of war-game results.
The second major phase of activities occurs when a specific deployment is anticipated. At that stage, the generalized contingency plans developed on an ongoing basis can be refined and made more specific, based on the known location, the type of mission, and current conditions. Once deployment occurs, health and environmental data should be collected, monitored, and archived, if feasible. The data could be used for real-time risk decisions and later reconstruction of exposure scenarios. An important aspect of this step is the identification of exposures and outcomes that were not previously anticipated.
Post-deployment risk-assessment activities comprise the third major phase of the framework. In this phase, when troops and reserves are reintegrated back into their garrison or civilian lives, it is important to continue surveillance of veterans' health and to study any uncertain outcomes using exposure reconstruction and epidemiological analyses. Much of the information obtained during this phase can then be used to refine earlier risk analyses and to search for or study threats not previously considered.
It is presumed that the various component analyses of the framework will be executed in good faith and interpreted carefully, with full awareness of the possibilities and shortcomings of the available methods. The framework concentrates on how the results of all of these activities can come together, how they can be pursued systematically to ensure that important aspects are not overlooked, and how they become useful in addressing the overall objectives of the larger enterprise.
Although the degree to which current DOD activities and programs fulfill the approaches recommended here will be important in implementation of this framework, implementation would not be a simple exercise in checking off components on a list. What makes the framework relevant is not the execution of each of its elements, however competently done, but rather the systematic approach to the process of assessing threats to deployed troops and incorporating the results of each element of analysis into an integrated program that addresses the overall objectives of the troop health-protection program. Only by keeping these ends in mind and continually evaluating the collective effectiveness of the risk-analysis activities in meeting them will the individual component activities play their needed role in the overall program.