E
Tactical Information Networks
This appendix adds detail to the treatment of tactical information networks in the main body of the report. Considering the general aspects of network design, it shows that there are significant inadequacies in the Navy’s current design for tactical information networks and the planned communications links may not be a good match for the information networking demands placed on them. It points out ways in which commercial networking technology could be used within the Navy’s tactical networks and those areas in which commercial technology will probably need to be augmented with military-specific technology. The committee does not pretend to design the Navy’s tactical information networks. That will require a great deal of architectural design and system engineering work. However, this appendix does show that a comprehensive, unified approach to the design of tactical information networks is missing in the Navy’s planning. Such an approach is a necessary ingredient for network-centric operations.
E.1 CHARACTERISTICS OF TACTICAL TRAFFIC
It is often said that, to a network, “bits are just bits”—but that is not entirely true. Although it is not the job of a network to interpret the contents of the bits that pass through it, the network must provide the services that its traffic requires. In general, each traffic type within a network has somewhat different requirements. In the specific case of tactical networks, the different types of traffic have quite widely varying needs. Hence, different types of traffic must be marked as such and the network must handle each traffic flow according to the rules established for that type of traffic. In the most extreme cases, entirely separate net-
works (“stovepipes”) may need to be set up for some types of traffic to ensure that their service requirements can be met.
E.1.1 Varying Types of Tactical Traffic
Earlier sections of this report describe current and planned tactical information network use in some detail. This section briefly recapitulates and then proceeds to translate these traffic considerations into more general architectural demands on the tactical network.
-
Sensor feeds. A wide range of sensor data flows into a tactical network. These feeds range from such heavy flows as imagery and synthetic aperture radar (SAR) from airborne platforms, through lesser flows such as moving-target indicators (MTIs), and down to sporadic and light traffic from cues such as unattended ground sensors or underwater sensors. Most types of imagery do not need particularly accurate transmission; they can withstand fairly high bit error rates. But more highly processed information, such as MTI tracks, require quite reliable delivery.
-
Weapons control. Real-time control of weaponry can range from the exceedingly time-critical “in-the-loop” applications, such as shooting down incoming missiles in the cooperative engagement capability (CEC) system, to relatively undemanding “update” applications for tracking a slowly moving target. Traffic delivery deadlines can thus range from milliseconds, in the most demanding cases, to tens of seconds in the least demanding. In either case, however, extremely high reliability is required in the delivery of control commands to an in-flight weapon.
-
Common tactical picture. The common tactical picture is a human-visible representation of the current situation, delivered with the appropriate level of detail so that the operations personnel can understand those aspects of the situation relevant for them and make decisions accordingly. This type of application can be implemented in a number of different ways, and each will impose different types of requirements on the tactical network. As an example, the U.S. Army’s Force XXI Battle Command Brigade and Below (FBCB2) program uses a hierarchical reporting mechanism in which each moving platform reports its position to a server, at a rate depending on how fast it is moving. The entire picture is then periodically distributed to everyone and filtered down to its relevant details at each receiver. This particular implementation imposes a fairly heavy “background hum” of position (and related) information on the network, with short messages and required latencies on the order of 1 s. However, high reliability is not required because messages are constantly being resent. If one is lost, the next will probably get through.
-
Tactical command and control (C2). Many tactical commands will be given by voice. Some fraction, however, will be delivered as data messages.
TABLE E.1 Notional Summary of Tactical Traffic Requirements
|
Traffic Type |
Distribution |
Acceptable Delay |
Reliability |
Bandwidth |
|
Imagery |
Few platforms |
High |
Moderate |
High |
|
Cooperative engagement capability |
Few platforms |
Very low |
Very high |
High |
|
Weapon control |
Single weapon |
Low |
Very high |
Low |
|
Common tactical picture |
All/most platforms |
Moderate |
Moderate |
Moderate |
|
Command and control |
Few platforms |
High |
High |
Low |
-
These messages may be created and interpreted by people—for example, typed on a keyboard and later printed and read on paper. Alternatively, they may be created and interpreted entirely by machine. For instance, platforms may automatically report fuel consumption to logistics databases. Different types of messages can have radically different kinds of service requirements: some (such as a call for fire) are urgent and must be reliably delivered; others are more routine or could be dropped if necessary.
-
Notional summary of traffic types. Table E.1 is not meant to be precise or encyclopedic, but marshals the requirements sketched above into a tabular format to show the degree to which tactical traffic flows differ.
E.1.2 Conclusions Drawn from the Traffic Requirements
This section draws some conclusions based on the tactical traffic mix discussed above. These conclusions help guide the critique here of the Navy’s current plans for tactical networks; the committee makes its recommendations in Chapter 4.
E.1.2.1 A Mixture of Predictable and Unpredictable
The first conclusion is that a significant portion of tactical traffic is unpredictable. It can be very “bursty,” surging one moment and dying away the next, in response to ever-changing and unforeseeable operational needs.
CEC radar tracks are, for instance, highly predictable. There will be a known number of CEC-enabled ships within a tactical arena, and once the network has formed, the traffic within the CEC’s Data Distribution System defined below is quite predictable. The presence of incoming missiles is not easy to predict, but the CEC system is designed so that its traffic load does not change much as it transitions from an inactive state to a fully engaged state.
The flow of imagery also seems at first relatively predictable. There are only so many sources of imagery and they can only be tasked at such a rate, and so the
flow of images seems predictable. This sense of predictability may, however, change as smaller unmanned aerial vehicle (UAV) sensors are introduced. One can imagine that sensors would be deployed at relatively short notice; one day there might be only one or two UAVs capturing imagery and the next day, there might be quite a few. In addition, individual imagery streams might turn on and off abruptly as sensors maneuver over target areas, detect activity, and so forth. Finally, variable efficiency compression (e.g., in a JPEG file) can change the traffic load unpredictably.
Distribution of the common tactical picture also seems, initially, to be reasonably predictable. In its simplest form, every platform could report information about itself at regular intervals, and the summary could be redistributed (if necessary) at equally regular intervals. In practice, however, platforms could well adjust the rate at which they sent updates to best match their current mobility, and the number of platforms in an area would be likely to change fairly dramatically over time; indeed the indications of enemy activity would likely change unpredictably.
In summary, a noticeable percentage of the traffic flowing through tactical networks is likely to be unpredictable and/or bursty. Such traffic surges, then dwindles, then surges again, changing from moment to moment. Since tactical networks have very finite capacities, this gives strong motivation to design a network that can take advantage of statistical multiplexing—to let one type of traffic surge fill the bandwidth that is momentarily being left unused by another traffic type.
E.1.2.2 Delay, Priorities, and Reliability Requirements
The next conclusion is that a tactical network must be able to accommodate varying delay requirements, priorities, and reliability requirements. When translated to information-networking mechanisms, these requirements generally devolve into two distinct kinds of priority—delay priority, which measures degrees of time-sensitivity, and reliability, which defines which messages should be accorded extra error correction when transmitted across radio frequency (RF) links and preferentially retained in memory during overload conditions. With such prioritization, it is inevitably the case that there must be some administrative mechanism for deciding on the relative priorities of traffic and establishing these policies.
E.1.2.2.1 Delay Priorities
Each host is responsible for marking each message, i.e., datagram, with the appropriate delay priority. Each node along the forwarding path must maintain sufficient queuing and forwarding discipline so that it forwards all packets with more stringent requirements before those with less stringent requirements. Pos-
sibly datagrams must be marked with expiration times, and routers must delete expired packets from the system; this would help during overload conditions. Possibly the network should implement flow control and not accept packets that it could not deliver in time. Stringent delay requirements will also strongly influence design of radio waveforms. In particular, they affect the way in which the channel is accessed (in multiaccess channels) and the maximum size of a frame that is transmitted in one contiguous piece. In particular, such requirements often lead to waveforms with short frames and bounded-delay channel access schemes.
E.1.2.2.2 Reliability
Each host is also responsible for marking each datagram with its relative requirements for reliability. This translates into how reliably the datagram must be delivered across an RF link, and hence can alter the error-control strategy (e.g., optional fast Ethernet channel (FEC) and/or automatic retransmission queue (ARQ)) for transmission across that link. It also affects how queues are managed within network nodes (primarily routers) when memory is running low: messages with the lowest priority tags are dropped first. Note that queues often fill up in routers—this is a normal, rather than exceptional, case. The simplest case is when a fast link leads into a router, but a slow link leads out; for example, a flood of traffic arrives very quickly on an Ethernet but must then be forwarded over a slow radio link. Queue overflows, and thus packet discards, are normal and inevitable in such cases. Important traffic can be protected, however, by assigning it a higher reliability than other traffic.
Stepping back from this detailed discussion, it is apparent that a rather large administrative burden is looming in the background. If indeed traffic is to be prioritized, someone must make all the administrative decisions as to those priorities. Since this involves deciding whose traffic is more important than whose, such decisions have often proved rather difficult to make and enforce. Such problems will not magically disappear as tactical networks become widespread.
E.1.2.3 Future Types of Tactical Traffic
The final conclusion that can be drawn is this: There is currently no “strong family resemblance” among the different traffic types in the network, and hence future traffic added to the network will probably look rather different from the traffic types that are well understood today. This should translate to a relatively heavy emphasis on designing a network that is flexible, open ended, and very easy to modify. Unfortunately, this conflicts with the equally admirable goal of efficiency. If the current set of traffic were going to remain unchanged for decades, it would make excellent sense to optimize every detail of the network and RF waveforms to support this traffic mix. But such is not likely to be the
case. It is very difficult to predict exactly what new traffic will be flowing through tactical networks in the coming two or three decades, but very easy to predict that there will be something new—and quite a bit of it, most likely. Hence now is not the time to optimize; now is the time to be flexible.
E.2 CURRENT PLANS FOR TACTICAL COMMUNICATIONS—“HOW IT IS”
The Navy is currently deploying, or planning to deploy, several different types of data communications subsystems on its tactical platforms. This section briefly reviews the most important of these current or planned tactical data links, with an eye to those technical details that make the data links more or less suited to smooth integration into an overall tactical network architecture. It is interesting to note that the Navy’s “canonical view” of the emerging architecture for network-centric warfare is not much more than a relabeling of two of its deployed systems and that a number of other tactically significant naval systems—now being planned or envisioned—simply do not fit into this canonical view.1
E.2.1 The Canonical View
The canonical “architecture” for network-centric operations consists of three layers. Two of these, the Joint Composite Tracking Network (JCTN) and the Joint Data Network (JDN), are meant to carry tactical traffic. The third layer, the Joint Planning Network (JPN), is presumed to be too slow to carry tactical traffic, although in some futuristic concepts it does appear as part of the tactical infrastructure, e.g., to perform reachback from forward sensors to a Global Broadcast System (GBS) or even a Global Positioning System (GPS) uplink so that the sensor information can be distributed for tactical purposes by satellite.
The Joint Composite Tracking Network is in fact synonymous with the cooperative engagement capability (CEC), and so these terms are used interchangeably here. The CEC is a tightly integrated set of distributed radar systems, each of which is mounted on a different platform. Its internal radio networking system is the data distribution system, which is perhaps best thought of as a specialized set of highly reliable, time-critical protocols that provide a distributed “radar backplane.” The Joint Data Network, similarly, is another name for the Joint Tactical Information Distribution System (JTIDS). JTIDS radios are installed on a range of platforms and organized into “nets.” Every platform within a given net can share data with all other platforms in the same net. Table E.2
TABLE E.2 Data-carrying Characteristics of the Joint Tactical Information Distribution System (JTIDS) and Cooperative Engagement Capability (CEC) Radio Systems
|
|
Intended Uses |
Type |
Raw Speed |
Open? |
|
JTIDS |
Force control messages, common tactical picture, and so on |
Time division multiple access |
Up to 115 kbps |
No |
|
CEC Data Distribution System |
Internal distribution of CEC tracks and coordination |
Special reliable flood |
Classified |
No |
provides a thumbnail sketch of the data-carrying characteristics of these two radio systems.
E.2.2 Tactical Links Outside the Canonical View
As mentioned above, the “canonical architecture” for networked operations defines exactly two tactical communications subsystems for the Navy, namely CEC and JTIDS. By implication, it would seem these two subsystems are expected to carry all tactical data traffic. In practice, however, several other radio subsystems are also employed, or being seriously considered, and indeed carry rather different types of tactical traffic than those carried via CEC or JTIDS. Table E.3 summarizes each of these noncanonical links. Thumbnail descriptions of some canonical and noncanonical links are given in the following sections.
E.2.3 Joint Tactical Information Distribution System
The Joint Tactical Information Distribution System, also known by the related but not interchangeable terms Management Information and Data System (MIDS), Link 16, or TADIL-J, is the Navy’s chosen radio subsystem for distributing “force control” messages within the tactical arena. These messages include surveillance tracks, weapons coordination, air control, target information, precise position location and identification, and even digitized voice networks.2 JTIDS
|
2 |
All information on JTIDS has been derived from two sources: Welch, LCDR David, USN. 1999. “Overview of Links 4, 11, 16, and 22,” Office of the Chief of Naval Operations, N62G, Washington, D.C., February 17; and Program Executive Office (Air and Missile Defense), U.S. Army and Army Aviation and Missile Command, Life Cycle Software Engineering Center, and Missile Research, Development and Engineering Center, U.S. Army. 1999. Introduction of JTIDS (U). Available online at <http://jtids.redstone.army.mil/JTIDS_101/sld001.htm>. |
TABLE E.3 Summary of Noncanonical Tactical Links
|
Link |
Intended Uses |
Type |
Raw Speed |
Open? |
|
Common data link |
Imagery and synthetic aperture radar (SAR) collection |
Point to point |
200 kbps up, up to 274 Mbps down |
Yes |
|
Tactical common data link |
Imagery and SAR collection |
Point to point |
200 kbps up, 10 Mbps down |
Yes |
|
Global Positioning System |
Weapon target location updates |
Broadcast |
Unknown |
No |
|
Vehicular radio communication-99 |
Command and control, video conferencing for the Marines |
Multihop network |
Unknown |
Yes |
radios—or their MIDS variants—will be installed on a variety of aircraft, surface ships, and submarines over the next 7 years, as well as in Patriot and theater high-altitude area defense (THAAD) forces. Table E.4 lists JTIDS (Link 16) characteristics.
Certain technical characteristics of the JTIDS waveform have important effects on the types of networks that can be built with JTIDS radios, and so such characteristics are briefly described in the following sections.
E.2.3.1 Waveform
JTIDS operates in the L-band. It divides the spectrum into 51 channels between 969 MHz and 1,209 MHz, with a channel spacing of 3 MHz. Certain portions of this spectrum are also used for identification friend or foe (IFF), tactical air navigation (TACAN), distance measuring equipment (DME), and Mode S, which excludes two subbands and imposes some restrictions on exactly how JTIDS can be used in noncombat situations. In particular, time slot duty cycles for JTIDS must be restricted to no more than 20 percent under “normal” conditions. Exercise conditions do not have duty cycle restrictions, and full combat conditions have no restrictions.
JTIDS uses a time division multiple access (TDMA) waveform. Every 24-hour day is divided, in the JTIDS waveform, into 112.5 epochs. Each epoch lasts 12.8 minutes and is subdivided into 64 frames of 12 seconds apiece. Each frame is further subdivided into 1,536 time slots. Each time slot is thus 7.8125 ms long. Time slots within frames are organized into three distinct sets, labeled A, B, and
TABLE E.4 JTIDS (Link 16) Characteristics and Those of Other Tactical Digital Information Links (TADILs)
|
|
TADIL A Link 11 |
TADIL C Link 4A |
TADIL J Link 16 |
TADIL J Link 22 |
|
Anti-jam |
No |
No |
Yes |
No |
|
Crypto secure |
Yes |
No |
Yes |
Yes |
|
Data rate (kbps) |
1.3 to 2.25 |
5.0 |
28.8 to 115.2 |
2.4 |
|
Message standard |
M series |
V/R series |
J series |
J series |
|
Participants |
20 |
4-8 |
128+ |
40 |
|
Critical nodes |
Yes |
Yes |
No |
No |
|
Voice circuits |
No |
No |
2 |
No |
|
Architecture |
Radio broadcast |
Radio point-to-point |
TDMAa |
TDMAa |
|
Frequencyb |
HF/UHF |
UHF |
UHF/spread |
HF/UHF spread |
|
aTDMA, time division multiple access. bHF, high frequency; UHF, ultrahigh frequency. |
||||
C. Time slots within a frame are identified as A-0, B-0, C-0, A-1, B-1, C-1, …, A-511, B-511, C-511. A given radio (“terminal”) may have up to 64 blocks of time slots assigned to it. Each time slot block (TSB) is defined by a triplet: set (A, B, or C); index (0 to 511); recurrence rate (0 to 15). Each assignment for a given terminal is designated as transmit, receive, or relay.
A JTIDS net is a group of terminals that exchange messages among themselves. In other words, it is a group of terminals whose time slots have been defined so that when one member of a net is transmitting, every other member of the net is receiving. Obviously this requires careful planning to ensure that indeed all the other members are receiving at that time, that only a single radio is granted a “transmit” time slot at a given time, and so forth. The JTIDS architecture allows 127 different nets (numbered 0 through 126) to be active simultaneously within the same RF spectrum. Since JTIDS is a frequency-hopping radio, each net is made mutually exclusive by assigning a unique frequency-hopping pattern for transmissions.
E.2.3.2 Access Modes
As defined, JTIDS provides three distinct access modes for a terminal that needs to transmit: dedicated access, contention access, and time slot reallocation (TSR) access.
-
Dedicated access is the mode described above. In this mode, the network planners ensure—by preparing the corresponding time slot plan for a given net-
-
work—that a given JTIDS terminal has exclusive use of an assigned TSB. This has the advantage that the terminal is guaranteed access to the network at regular intervals, but it also has the corresponding disadvantage that the time slot goes wasted if the terminal has nothing to say at a given moment.
-
Contention access is quite different. In this mode, a given net provides a pool of time slots available for any terminal’s use. Any terminal that needs to transmit will randomly select a time slot from this pool and transmit in that time slot. This scheme has a number of advantages: it is easy to plan, makes it quite simple for terminals to enter or leave the net while the net is in operation, and provides some of the traffic efficiencies of statistical multiplexing for traffic that is bursty or hard to predict in advance. Its main disadvantage is that multiple terminals may transmit during the same time slot, which can result in lost messages and/or some terminals hearing one transmitter while others hear a different one.
-
Time slot reallocation access is the most complex mode. As with contention access, all terminals share a single pool of time slots. Rather than transmit at will, however, the terminals perform a distributed algorithm to apportion the time slots. Each terminal transmits its bandwidth needs periodically, and every terminal performs identical algorithms to ensure that the pooled time slots are apportioned as per the needs. It is unknown whether this access scheme has been implemented in practice.
E.2.3.3 JTIDS Data Rates
Each JTIDS time slot has the following components. The time slot begins with a variable start jitter delay, then synchronization and time-refinement patterns, the payload (message header and data), and finally dead time to allow for RF propagation. This discussion concentrates only on the message data portion of a time slot. Each data portion can contain 3, 6, or 12 75-bit words, depending on the exact encoding of the message. Thus each time slot can carry anywhere from 225 to 900 bits of data payload, giving an aggregate data rate for a given JTIDS net of between 28,800 and 115,200 bps. Some of this “raw” capacity is used for housekeeping and so is not available for tactical traffic, but these numbers give a useful yardstick for the approximate capacity of a JTIDS net.
By comparison, current commercial phone-line modems run at roughly 53,000 bps in the downstream direction. Thus one JTIDS net has a raw capacity ranging between roughly one-half and two times that of a phone-line modem. Since JTIDS divides its available L-band spectrum up into 51 channels, the extreme upper bound on the number of bits per second that can be transmitted simultaneously from all JTIDS terminals in a tactical arena is thus 51 × 115,200 = 5,875,200 bps. (This assumes that all available spectrum is devoted to JTIDS, that all terminals use the maximum possible data rate, and that all time slots in all channels are used for transmission and ignores the overhead of housekeeping
bits.) Working from the previous calculation, JTIDS achieves 5,875,200 bps in 51 × 3 MHz of RF spectrum, for an aggregate spectral efficiency of 0.0384 bps/ Hz. Partly, of course, this is driven by the tactical need for very robust anti-jam features. To a noticeable extent, though, it is driven by the basic short-frame TDMA structure of the JTIDS waveform where rather short payloads are surrounded by the dead times of synchronization patterns and propagation allowances.
E.2.4 Common Data Link and Its Variants
The common data link (CDL) is a family of radios that provides standardized, wide-band, line-of-sight (LOS) communications between airborne reconnaissance sensors and their users.3 The common data link has been mandated by the Assistant Secretary of Defense (Command, Control, Communications, and Intelligence) (ASN (C3I)) as the data link for all imagery and signals collection systems. The Navy is currently acquiring ship-mounted CDL terminals, under the name common high-bandwidth data link (CHBDL).
At the RF level, CDL has both X- and Ku-band options. In the X-band, the command link (up) is 9.750 to 9.950 GHz, and the return link (down) is 10.150 to 10.425 GHz. In the Ku-band, the command link is 15.15 to 15.35 GHz, and the return link is 14.40 to 14.83 GHz. The tuning increment is 5 MHz in both bands. Typical airborne antennas are 7- or 9-inch directional dishes, though some applications use omnidirectional antennas. Typical surface antennas are 1 m or 6 ft dishes.
The CDL command link runs at 200 kbps. It employs binary phase shift key modulation, Viterbi convolutional encoding (rate 1/2, constraint length 7), interleaving, and pseudo-noise spreading. The command link uses a 40-bit frame to structure a sync channel, link command and control channel, audio channel, and from 1 to 10 subchannels for Prime Mission Executive Command. The CDL return link runs at a selectable data rate: 10.71 Mbps, 137 Mbps, or 274 Mbps. It employs offset quadrature phase shift key modulation, Viterbi convolutional encoding (rate 1/2, constraint length 7), and interleaving. The return link multiplexes a number of data channels, each running at a fixed rate, onto the overall link.
TCDL is a Defense Advanced Research Projects Agency (DARPA) program that will develop multiple qualified sources for a lightweight, low-cost, CDL-
interoperable data link for small UAVs. TCDL systems will be less capable than full CDL systems; in particular, they will only implement a slower return link.
At least one manufacturer provides a CDL variant with asynchronous transfer mode (ATM) interfaces. This allows transmission of arbitrary ATM data between aircraft and the surface ship. Since the Internet Protocol (IP) can be deployed over ATM links, it also allows tying the aircraft into a wider-area military internet at the appropriate security level.
E.2.5 Networks for the Land Forces (Marines, Army)
In the near future, the U.S. Navy will need to connect its networks with a number of tactical land-based networks. In particular, Marine Corps and Army forces will be important partners in tactical networks, and the Navy’s networks must be designed to integrate smoothly with the networks that will be provided by these two Services. In the longer term, the U.S. Navy must also interoperate with an ally’s networks; but this whole area is sufficiently ill-defined that it is not discussed here. It is only noted in passing that the armies of two important allies (Canada and the United Kingdom) have both determined that their tactical networks will employ Internet technologies, which does provide a clear path toward interworking with the Army and the Marine Corps.
The Marine Corps is experimenting heavily as it moves toward using tactical networks. Two efforts deserve particular note. The first is their acquisition of the new Tactical Data Network (TDN). The other is the recent advanced concept technology demonstration (ACTD), Extending the Littoral Battlefield (ELB). Each is discussed in turn.
The TDN is built from standard Internet technology, using ruggedized Ethernet hubs, conventional servers for e-mail, (commercial) routers, and standard network management tools. Networks are linked together using the Internet protocols running over standard line-of-sight trunk radios (AN/MRC-142) or satellite transponders.
The ELB demonstration aimed to show how the Marines would fight in the future. Dispersed forces ashore went beyond line of sight and called back (via voice and data networks) for fire. A number of different types of communications technology were employed on an experimental basis.4 Most interestingly, the Marines created a wide-area, mobile ad hoc network using a combination of VRC-99 packet radios with commercial 802.11 WaveLAN radios. The entire network was based on Internet technologies. Radios were deployed at sea, aloft,
and on the ground to form the network links. The VRC-99 radios provided a self-organizing radio network that acted as a long-range “backbone” for data communications. Local wireless communication tied into this backbone via the commercial WaveLAN radios. Although the demonstration encountered a number of technical problems, it was the first real instantiation of the Marines’ vision for how they will use networking.
The U.S. Army’s tactical networks can be divided into a few basic categories: far-forward, highly mobile networks (the Tactical Internet); movable command centers (Tactical Operations Centers); and rear, relatively fixed networks (Warfighter’s Internet—Terrestrial). The first two have clearly fixed upon the Internet architecture. The devices in these networks are standard PCs or UNIX computers connected to the network via standard serial lines or Ethernets. Routing is performed by a mixture of commercial routers and specialized military routers. The Warfighter’s Internet has not yet been completely defined, but it clearly will interoperate with the other Internet-based Army networks as well as the more fixed strategic networks (SIPRNET).
E.2.6 Future Tactical Communications Systems
A number of other tactically significant communications subsystems are currently in the planning or ideation stages. These subsystems are not discussed here, but it is important to recognize that they are on the drawing boards and may within a decade become real components of the Navy’s tactical networks. These systems range all the way from Discoverer II, envisioned as a low-Earth-orbiting (LEO) constellation of radar-imaging satellites that provides near-real-time imaging to forward-deployed forces, down to acoustic communications links between ships and submerged submarines. One can also imagine commercial networks as part of this overall blend, e.g., transporting tactical data via Iridium or GlobalStar satellite phones. The associated link speeds range across many orders of magnitude, and the types of traffic expected across these links do not fit well into the Navy’s canonical view of its “emerging architecture.”
E.3 THE VISION—HOW IT SHOULD BE
The network-centric vision depends strongly on one’s vantage point. At the highest level, it encompasses such operational benefits as self-synchronization of distributed forces. At the application level, it encompasses concepts such as distributed radar systems, real-time targeting of weapons in flight, and the like. The vision as seen at the networking level is noticeably more prosaic but, the committee argues, equally important. This section explores the network-centric vision from the perspective of Layer 3 of the Open Systems Interconnection (OSI) model, i.e., in terms of networking architecture and technology.
E.3.1 Network Services That Are Medium-Independent
The medium is not the message. Any type of traffic should be able to flow across any kind of communications link, and all decisions about which types of data should flow across which radio networks should be policy decisions rather than cast-in-concrete engineering design decisions. If there is some reason that imagery should flow across JTIDS nets, it should require nothing more than changing a few policy rules. And one should not need to upgrade JTIDS radios in order to carry new types of messages, any more than one upgrades one’s Ethernet transceiver in order to receive new types of Internet traffic.
E.3.2 Seamless Connectivity Across Joint Forces
All types of application traffic should be able to flow smoothly across the tactical, and indeed strategic, networks of the joint forces. The Navy afloat should be able to exchange imagery, tracks, and the common tactical picture with the Marines and Army on the ground, with the Air Force, and indeed with allies and coalition forces. It should not matter that the forces use different types of radios; the messaging should be independent of such lower level details. Connecting one Service to another should be a “plug-and-play” operation, with all addressing and routing taking place automatically, rather than a laborious, time-consuming process that relies on specialized gateways. At the strategic level, each Service’s network connects in a simple, straightforward way. There is no “protocol translation gateway” needed at a special connection point in order for the Army to access the Navy’s Web sites. Common protocols and a common addressing plan obviate this need. The same should be true for each Service’s tactical network.
E.3.3 Greatly Reduced Planning and Management
To the largest extent possible, tactical networks should be plug and play. Extensive planning and finicky configuration are a bad match for the chaotic, fluid tactical environment. Commanders-in-chief (CINCs) should be able to compose forces in ways that make operational sense without being constrained by artifacts of the communications systems. The networks should gracefully adapt to the offered traffic load as it changes from minute to minute, switching automatically from handling heavy imagery flows across its RF links at one moment to handling radar tracks and location information the next.
E.3.4 Network Security
Tactical networks must be secure against intruders, disruption, and eavesdropping. Loss or compromise of network nodes must not imperil the remainder
of the network. Intruders should not be able to insert false data into the networked information systems, nor should they be able to deny service to network participants.
E.3.5 Open Systems That Take Advantage of Commercial Standards
Finally, insofar as it is feasible, the Navy’s tactical networks should employ open systems based on commercial standards. These days, military networking technology cannot begin to compare with its commercial counterparts, and the gap is growing wider month by month. The Navy cannot afford to design and build all its own network technology; and even if it could, the military technology would be obsolete long before it was deployed.
E.4 DEFICIENCIES IN THE NAVY’S TACTICAL NETWORKING PLANS
The communications links that the Navy plans to acquire do not add up to a coherent network architecture. They remain instead a compendium of discrete, separately purchased radio systems. Although the Navy often portrays these systems as an emerging architecture, there is in fact no underlying system architecture for these links and, hence, no actual network. And since the systems fail to leverage commercial networking technology, they have already fallen far behind commercial standards in networking.
E.4.1 Stovepipes
Military stovepipe systems have been decried for years, so this discussion is brief. Each naval RF data subsystem has been bought and engineered as a stand-alone solution to some unique problem. Each is a point solution. To a large extent, a given type of service equals the corresponding radio equipment. The overall result is that each RF data system is rigidly structured to provide a specialized set of services. Thus the JTIDS radio provides target information, the CEC radio (DDS) provides radar track distribution, and so forth. Conversely, if a user wants target information, he or she must install a JTIDS box.
Until a few years ago, wireless services in the commercial world were similarly fragmented. One type of radio was used for paging, another for cellular telephony, various others for specialized data services, and so forth. But these distinctions have rapidly blurred as service providers move to converge on only two networking schemes that are deployed across a very wide variety of radio technologies: telephony-compatible voice services (across standard waveforms such as the Global System for Mobile Communications (GSMC), code division multiple access (CDMA), or proprietary waveforms), and Internet-compatible data services (via General Packet Radio Service (GPRS), IS-95B, or proprietary
solutions). The Navy should understand these trends and draw the appropriate lessons for its own networks.
E.4.2 Closed, Proprietary Systems
A further problem is that these stovepipe systems are built as closed, and generally proprietary, solutions. In standard networking terms, this means the following:
-
The networking protocols are not open. As opposed to most commercial networking protocols, there are relatively high barriers to entry for new companies that wish to provide compatible, interoperable technology for naval RF systems.
-
The networking protocols are not layered. Modern networks are built of layered protocols, where each protocol is carefully isolated from the layers below and above it in the protocol stack. This layering is generally described in terms of the OSI reference model, although existing network technology does not exactly match the layers used in this descriptive model. Naval RF systems generally do not make sharp distinctions between the layers, with the result, for instance, that it requires major effort to ensure that a JTIDS radio can convey a new type of message. Contrast this with the Internet, where new forms of messaging and communications are freely invented and can be carried across the existing network structure with no modification to the network’s routers.
-
These systems employ little or no commercial networking technology. As such, they fail to leverage what is possibly the fastest-developing technology of the current era. By contemporary standards, “networks” such as JTIDS already seem archaic. Since they are missing out on the extraordinarily rapid development of networking at the current time, it is hard to imagine how out-of-date these naval systems will be when they are fully deployed. The Navy long ago stopped designing and building its own computers; now it is time to stop designing and building its own network technologies.
E.4.3 Lack of Flexibility
A further characteristic of naval RF systems is that they require a great deal of advanced planning before they can be deployed. A certain amount of planning is inevitable—frequencies must be allocated, keys must be distributed, and network names and addresses must be assigned. Systems such as JTIDS, however, introduce a level of planning complexity that makes it difficult to freely “mix and match” tactical forces in the field. JTIDS frequency and TDMA slot planning is complex enough so that they take days or weeks to complete. A task force sets under way with (say) five JTIDS plans. If a contingency arises that cannot be accommodated by one of these preset plans, improvisation is difficult.
Certain aspects of this planning problem could have relatively straightforward technical solutions. For instance, organizing the RF links into a small set of broadband links—rather than a large set of narrowband links—would help reduce the frequency planning problem. Switching from TDMA channel access to prioritized carrier sense multiple access/collision avoidance (CSMA/CA) channel access, or a hybrid TDMA plus CSMA/CA scheme, would eliminate or reduce the slot-planning problem. This is certainly quite different from the current types of radio technology being deployed by the Navy, but technically quite feasible. In fact, such schemes are widely used in the commercial world, e.g., in wireless local area networks (LANs).
Other aspects of the planning problem are much harder to solve. In fact, current commercial networking technology actually introduces new planning problems. Conventional data networks typically involve a good deal of planning (of addresses, names, and so on); and since such networks generally change rather slowly, there is little commercial emphasis on plug-and-play networks or on good tools to help with network planning.
E.4.4 No Good “Data Haulers”
Compared with the commercial world, the Navy will be very bandwidth-poor. This is partly inevitable, given the exigencies of the tactical environment. To some extent, however, the scarcity is avoidable. The Navy is simply not planning to buy many high-capacity tactical radios.
Calculating the relative bandwidths of tactical radios and commercial data radios makes this point quite apparent. Commercial wireless networking distinguishes between “access” networks such as wireless LANs, and “backbone” networks that are typically point-to-point links. Current wireless LANs run over small omnidirectional antennas at a maximum speed of about 10 Mbps, although they often fall back to much slower speeds (e.g., 1 Mbps) due to interference, multipath, and the like.5 Current point-to-point links run over directional antennas at speeds between about 10 Mbps and 155 Mbps. The Navy’s plans for the CDL and DDS radios are sufficiently specialized that it is probably unrealistic to think of these radios as generic “data haulers” for naval tactical networking. This leaves JTIDS as the only plausible radio for transporting generic data across the battlespace. A JTIDS terminal’s maximum throughput of roughly 115 kbps thus provides only 11 percent of the bandwidth of a slow wireless LAN (1 Mbps), only 1 percent of the capacity of a fast wireless LAN (10 Mbps), and less than 1/10 of a percent of the capacity of a high-speed (155 Mbps) commercial RF link.
Thus one can summarize by stating that the Navy’s tactical data radios will
provide bandwidth that is somewhere between one and three orders of magnitude less than those used in the commercial world. It is true that low-probability-of-interception/low-probability-of-detection (LPI/LPD) and anti-jamming (AJ) features of the waveform account for some of this difference. The bottom line remains, however, that the Navy will not—with current plans—have a great deal of bandwidth for its tactical networks.
E.4.5 No Coherent Plans for Information Network
The problems outlined in previous paragraphs are symptomatic of a much larger issue: the Navy has no overall plans for its tactical information network. Such plans would include the following:
-
A unified addressing and naming plan for nodes in the network;
-
An overall list of the types of tactical traffic that flow across the battlespace, the sources and destinations of this traffic, and their required service characteristics;
-
A routing plan for the network;
-
Designs for how the tactical network fits into the larger picture of each other Service’s tactical network, the Joint Planning Network, and so forth; and
-
Engineering of RF links and spectrum to meet network needs.
E.4.6 No Overall Plan for Network Security
The Navy has no overall plan for security in its tactical networks. Security is part of the foundation of an information network architecture—it is extremely difficult to add after the fact. Years of work have gone into adding security to the Internet after the fact, but the results are still far from satisfactory. Web sites continue to be hacked, and intruders continue to gain access to poorly protected computers. The Navy should take care that its tactical networks are at least as secure as those provided by commercial vendors.
The key point here is that networked naval warfare introduces new vulnerabilities. Enemy capture of a network node means that the enemy is now inside the Navy’s network. If this seems a remote possibility, remember that the naval tactical networks will be closely linked into ground networks for the Marines and the Army. Overrun of a tactical node can be something as simple as capture of a single wheeled vehicle. Once an enemy has captured a functioning network node, it can take some time before anyone notices and excises that enemy from the network. During this time, an enemy can cause a great deal of damage; some of it may last far longer than the node itself. For instance, they may spoof the common tactical picture, adding fictitious elements to it. They can also engage in various types of network denial-of-service attacks.
Link encryption plus over-the-air rekeying is not a sufficient answer to this
problem. Full-scale network protection requires a number of additional technologies, including firewalls, intruder detection, layered defenses, and so forth. Commercial technology provides limited help in this area. It can supply firewalls, an infrastructure for public-key management, key exchange protocols, authenticated routing protocols, and so forth. But at present no commercial technology can adequately deal with the “enemy capture” problem. DARPA is tackling a wide range of issues with its Information Assurance program, but even so, it is unlikely that tactical networks will be sufficiently well protected in the near to mid term. This should be of major concern to the Navy.
E.5 HOW TO ACHIEVE THE VISION
This section provides a series of high-level observations on how the Navy might proceed as it develops its overall tactical network architecture. There are no startling insights here; rather, these observations elaborate on the usual steps of systematic network design. However, the committee has seen no signs that the Navy has yet gone through these steps, and so encourages the Navy to do so before beginning to design or roll out the operational subsystems. In particular the committee makes note of the following:
-
The Navy should recognize that every network needs an architecture and immediately establish an overall tactical network architecture that includes published (and enforced) architectural standards documents and layered protocol stacks. This architecture should recognize that the tactical network is a “network of networks” and explicitly plan for independent upgrade paths of all components and communications subsystems within this overall network.
-
The Navy should explicitly determine which points on the stovepiped-open continuum are suitable for interconnecting its various communications subsystems, with justifications as to why those points are the best design choices.
-
The Navy should explicitly determine the best blend of commercial and military networking technology for its tactical networks, with detailed justifications for why military technology is required for any given part of the design. The committee believes that the commercial Internet Protocol should be the basis for this design.
-
The Navy should provide open, commercial-compatible interfaces to certain of its tactical communications systems (JTIDS, CDL) so that standard networking technologies can be used in conjunction with these subsystems.
The committee has not found any definitive, Navy-wide list of arguments against using commercial technology in tactical networking. However, a number of arguments seem reasonably widespread, such as: Tactical links require antijam protection and Type 1 encryption, tactical traffic is life-critical and delays must be guaranteed bounded, and tactical RF links do not have enough capacity
to carry conventional networking traffic. These issues are important and deserve serious attention. However, it is by no means evident that they rule out commercial technology. Accordingly, the next section presents the committee’s view on the blend of commercial and military technology. After that, two further matters pertinent to achieving the overall vision are discussed—opening radio architectures and areas of needed research.
E.5.1 Blend of Commercial and Military Technology
E.5.1.1 Lower Layers (Radios)
The Navy, which employs a wide variety of radios (OSI layers 1 and 2) in its tactical networks, needs lower layers (radios) of the following broad classes:
-
Multiple-access (shared-channel);
-
High-capacity, point-to-point; and
-
Satellite links.
At the very least, the Navy needs anti-jam protection for most of its tactical links. In many cases, it is also desirable that its radios have LPI and LPD. None of these features is likely to be implemented to any significant degree in commercial radios, and so it is likely that the lower layers (radios) in the Navy’s tactical network will be predominantly military. Some links, however, may be implemented via commercial radios, and even in military-specific radios, many of the component technologies may be commercial.
E.5.1.2 Upper Layers (Applications)
Layers 4 and above of the protocol stack, i.e., the applications and the protocols that they use, will likely be a mix of commercial and military. Some of the tactical applications are really indistinguishable from normal commercial uses, for example, transfer of large imagery files. There is very little justification for creating specialized military applications or protocols for such purposes. Other tactical applications have no commercial analog. A good example is distribution of the common tactical picture. This will require a highly specialized application program and indeed most likely a specialized protocol to distribute the necessary data; so this application and protocol will likely be military specific. Many other applications will involve a blend of commercial and military networking technologies.
E.5.1.3 Middle Layers—The Missing Piece
The lower layers will be predominantly military; the upper layers will be commercial mixed with military. What about the “networking” layer, i.e., Layer 3 of the OSI stack? Chapter 4 recommends using the IP for all links where feasible and specialized military protocols for the rest. Hence, here both its strengths and its weaknesses are discussed briefly in this context.
E.5.1.3.1 Strengths of the Internet Architecture
The main strengths of IP as a standard “bearer” protocol are that it is ubiquitous, cheap, and very rapidly developing in the commercial world. Since virtually everyone is now aware of the astonishing growth of the Internet, this point is not belabored here. But it is a very real advantage.
Furthermore, an IP-based tactical network architecture will connect seamlessly with the Navy’s IT-21 network, the Marine’s TDN, and all of the Army’s forward area networks, as well as the networks being deployed by the UK and Canadian armies. These networks are all Internet-based and so, given the appropriate policies and attachment points, traffic should be able to be freely exchanged across all these networks (or restricted or even forbidden, if the policy so dictates).
The Internet architecture also offers excellent network security tools. Its IPSec protocols provide a highly extensible framework for performing end-to-end security with a variety of authentication and privacy features. Internet firewalls are commodity items. New security techniques, including developments in DARPA’s Information Assurance program, are geared toward the Internet. No other networking technology has anything near this range or depth of security apparatus.
Finally, training would be simplified if the Internet architecture were adopted for the Navy’s tactical networks. Since Internet technology is a commodity item, books, videotapes, and training courses abound. The Navy would not need to develop special training materials to teach its staff how to configure, manage, or troubleshoot its tactical networks.
E.5.1.3.2 Weaknesses of the Internet Architecture
The Internet architecture does have weaknesses, however, ones that are highlighted in the tactical networking environment. The key weaknesses of IP for tactical environments are as follows:
-
IP header overhead. A “bare” IP datagram requires 20 bytes of header information; to this, the User Datagram Protocol upper layer adds 8 bytes, or the Transmission Control Protocol (TCP) adds 20 bytes. If the IP packet’s payload is
-
very short, this header overhead can be significant. However, this problem can be greatly reduced by employing some variant of the standard IP header compression protocols. On average, such protocols can reduce the IP header to a few bytes.
-
Poor transmission control protocol performance on tactical RF links. The TCP is sensitive to dropped packets and large degrees of jitter in packet arrival times; in particular, it treats such events as if they were caused by network congestion and responds by sharply reducing its throughput. This gives rise to poor TCP performance over many types of low-speed (e.g., 10 kbps or lower) radio links, including commercial cellular phone systems and tactical radios. Although some engineering can help to lessen these problems, the wisest course might be to add sufficient forward error correction to higher bandwidth links to make packet loss fairly rare, and to forgo using TCP across low-bandwidth tactical links.
-
Problems with mobility. The Internet Protocol suite implicitly assumes that a computer does not move very often from one network to another. When this assumption is violated, a number of protocol problems occur. For instance, operating systems may need to be power cycled to obtain new IP address information, existing data sessions may need to be torn down and restarted, name to address mappings may become obsolete, and so forth. This problem is too complex to discuss here, and there are some efforts to revise the Internet protocols to lessen or eliminate this problem (IP mobility). However, issues still exist and it is unclear whether IP mobility will in fact become widely adopted. This area should be noted as a concern for those tactical platforms that move from one network to another.
-
Configuration. Typical Internets require a great deal of “behind the scenes” configuration to make them work. A wide variety of servers and routers need separate, but consistent configuration. Network addresses and masks must be consistently assigned, dynamic host configuration protocol (DHCP) and domain name service (DNS) servers must be properly set up, management terminals must be correctly identified for all the manageable elements of the system, a wide variety of options must be set on commercial routers, and so forth. Misconfigured computers and routers are relatively common in the commercial world and would likely be even more common in tactical environments. This area would need serious, sustained effort to ensure that the administrative burden is not excessive. (On the other hand, most types of networking introduce a comparable set of configuration and administration issues.)
E.5.2 Potential for “Opening” Existing/Planned Radios
Previous sections point out that the Navy’s current radio links are in essence stovepipe systems and that at present these links tightly couple the RF technology with the types of messages that can be transported across the links. These sec-
tions then go on to note the advantages of using a modern, layered network architecture, and the desirability (where possible) of employing a single, universal bearer protocol such as IP across all the RF links.
What would it take to “open up” the Navy’s existing and planned data radios so that they could carry any type of message? The internal details of these radios are not known, and so the committee cannot give a detailed answer to this question. However, the committee has had experience with a similar task for various other kinds of radios, and in general, it has been technically feasible and not extensively costly. It is a question that the Navy should be posing to its contractors.
Table E.5 summarizes the committee’s views about opening the Navy’s three major tactical data radios.
TABLE E.5 Opening the Navy’s Major Tactical Data Radio Systems
|
|
Joint Tactical Information Distribution System |
Common Data Link, Tactical Common Data Link, etc. |
Data Distribution System |
|
Current use |
Track distribution |
Intel sensors (imagery, synthetic aperture radar, …) |
Cooperative engagement capability “backplane” |
|
What is required to make radio open |
New Internet Protocol message format, standard interface |
Contractor already has assisted transfer mode, Ethernet interfaces |
New IP message format, standard interface, very fast/reliable cutover to radar |
|
Good points |
Most widespread data radio (sea, air) |
High-bandwidth surface/air link; good for relaying communications |
High-bandwidth link among some ships and planes; excellent anti-jamming |
|
Bad points |
Spectrum issues; Time division multiple access channel access |
No reliable anti-jamming? Lacks encryption? |
Development costs? High nonrecurring expense test costs; spectrum issues |
|
Should it be opened?a |
Yes |
Yes |
Unclear |
|
aResponse summarizes committee’s views. |
|||
E.5.3 Research Opportunities
Most of the transition to a tactical network suitable for network-centric operations can be accomplished with a solid network architecture and sound systems engineering, followed by intensive development work on the various communications subsystems. Such work is hard, but it is not rocket science. Some new tactical networking technology is desirable, though, and will require an R&D effort as it will most likely not be developed in the commercial sphere.
E.5.3.1 Better Channel Access for JTIDS
The JTIDS waveform defines several channel access mechanisms. None is very close to the current commercial practice, e.g., as embodied in the Institute of Electrical and Electronics Engineers (IEEE) 802.11 wireless LAN standard. The 802.11 waveform conducts a transmission via four discrete steps: (1) the transmitter sends a request to send (RTS); (2) the receiver sends a clear to send (CTS); (3) the transmitter sends a variable-length data frame; (4) the receiver sends an acknowledgment. This waveform, together with its associated state transition diagrams, gives a reasonable CSMA/CA channel access protocol that guards against the classic hidden terminal problem. Research and experimentation with similar waveforms could bring significant benefits to the JTIDS waveforms in terms of allowing JTIDS to carry higher levels of bursty traffic than they can now successfully transport.
E.5.3.2 Potential Bandwidth Increases
Bandwidth is always a scarce commodity in the tactical world, but it is likely that the Navy will encounter quite severe bandwidth shortfalls in the future. There are a number of technical approaches that could help, and research in this area could prove very useful. Current naval plans for tactical networking expect that the data radios will be running at quite high power to ensure that the receiver is within earshot of the transmitter. This is an effective technique but leads to inefficient use of the RF spectrum. In particular, it does not encourage local spatial reuse, i.e., the reuse of the same RF spectrum at geographically separated regions. The Navy’s plans are perhaps most clearly highlighted by contrast with commercial cellular systems, which impose tight power controls on their transmissions in order to reuse the same frequencies multiple times within a metropolitan region. If the cellular systems worked like Navy radios, they would support only a few dozen simultaneous phone calls over an entire city. In addition, JTIDS’ overall capacity as a data hauler is quite low; a different waveform designed for wideband, packetized communications could likely do better and still have the requisite anti-jam properties.
E.5.3.3 Ad Hoc Networking
Ideally, Navy tactical networks would form automatically to include all nodes in a given area. In addition, nodes would automatically begin to act as relays when needed to forward traffic on to further nodes that are outside radio range of the original transmitters. Such networks are termed ad hoc networks or sometimes mobile ad hoc networks (MANETs). There has been little commercial interest in such networks, as commercial service providers can usually arrange to carefully plan their RF base stations, bring wireline connectivity to the base stations, and so forth. This obviates the commercial need for such ad hoc networking technology. DARPA and other military agencies, on the other hand, have been funding research into ad hoc networks for some years, and the first or second generation of workable ad hoc networks is now up and running. These networks include near-term digital radio (NTDR), VRC-99, Global Mobile Information Systems, and others. These networks appear to work reasonably well; indeed, the NTDR has even been adopted for use in the Army’s First Digitized Division. The technology is far from mature, however, and R&D would likely have very useful payoffs.
ANNEXES TO APPENDIX E
Annex 1 Imagery and SIGINT Dissemination Characteristics
This annex presents reference information on direct dissemination from imagery and SIGINT platforms (Table E.A.1) and indirect imagery dissemination systems (Table E.A.2).
TABLE E.A.1 Imagery/SIGINT Platform Characteristics (Direct)
|
Platform |
Sensor |
Data Link |
Link Data Rate |
Mode |
|
U-2 |
SAR |
CDL |
274 Mbps |
LOS |
|
EO/IR |
CDL |
274 Mbps |
LOS |
|
|
Other |
CDL |
274 Mbps |
LOS |
|
|
SAR |
ETP |
274 Mbps |
Sat |
|
|
Global Hawk (HAE UAV) |
SAR, EO/IR, MTI |
CDL |
274 Mbps |
LOS |
|
|
SAR, EO/IR, MTI |
Ku |
50 Mbps |
Sat |
|
F-14 |
EO (TARPS) |
CDL |
137 Mbps |
LOS |
|
F/A-18 |
SAR (APG-73) |
CDL |
137 Mbps |
LOS |
|
|
EO/IR (ATARS-USMC) |
CDL |
137 Mbps |
LOS |
|
|
EO/IR (SHARP-USN) |
CDL |
274 Mbps |
LOS |
|
Predator (MAE UAV) |
Video (EO/IR) |
Legacy |
Analog, ~1.5 Mbps |
LOS |
|
|
SAR |
Legacy |
3.0 Mbps |
LOS |
|
|
Video (EO/IR) |
Legacy |
3.0 Mbps |
Sat |
|
|
SAR |
Legacy |
3.0 Mbps |
Sat |
|
Pioneer (TUAV)—USN |
EO/IR/Video |
Legacy |
Analog, ~512 kbps |
LOS |
|
Pioneer (TUAV)—USMC |
Video |
Legacy |
Analog; currently tape only |
LOS |
|
Surface Terminal |
Data Link Receiver |
Processor |
Remarks |
|
JSIPS-N/TEG |
CDL-Navy-ST/TIGDL |
CIP |
|
|
JSIPS-N/TEG |
CDL-Navy-ST/TIGDL |
CIP |
|
|
BGPHES-ST |
CDL-Navy-ST/TIGDL |
BGPHES |
|
|
CONUS |
Unique |
|
Indirect only via NIS/CA |
|
MCE/JSIPS-N/ TEG |
CDL-Navy-ST/TIGDL |
CIP |
GH now limited to 50 Mbps rate |
|
Satellite receiver (ashore) |
TIGDL |
CIP |
Satellite relay—actual data rate function of satellite transponder power |
|
NAVIS/JSIPS-N |
CDL-Navy-ST/TIGDL |
CIP |
Some TARPS sensors still film based; not all TARPS have data link; TARPS sensor to be replaced by SHARP |
|
JSIPS-N/TEG |
CDL-Navy-ST/TIGDL |
CIP |
|
|
JSIPS-N/TEG |
CDL-Navy-ST/TIGDL |
CIP |
Includes medium-altitude electro-optical and low-altitude electro-optical and infrared line scanner sensors |
|
JSIPS-N/TEG |
CDL-Navy-ST/TIGDL |
CIP |
CIP upgrade for SHARP planned |
|
Legacy |
Legacy |
N/A |
Data link upgrade planned (TCDL) |
|
Legacy |
Legacy |
OBP |
Data link upgrade planned (TCDL) |
|
Legacy |
Legacy |
N/A |
Data link upgrade planned (TCDL) |
|
Legacy |
Legacy |
OBP |
Data link upgrade planned (TCDL) |
|
Legacy |
Legacy |
N/A |
Pioneer, a legacy system, to be phased out when VTUAV becomes operational |
|
USMC G/S (control link) |
Legacy |
N/A |
Analog 512 kbps data link currently not used; Pioneer, a legacy system, to be phased out when VTUAV becomes operational |
|
Surface Terminal |
Data Link Receiver |
Processor |
Remarks |
|
TCS/JSIPS-N/TEG |
TCDL |
N/A |
Pioneer replacement; under development |
|
Legacy |
Legacy |
N/A |
Data link upgrade planned (TCDL) |
|
Legacy |
Legacy |
N/A |
|
|
CGSM/afloat |
SCDL |
N/A |
USN planning for JSTARS transitioning SCDL to TCDL |
|
CGSM/afloat |
SCDL |
N/A |
|
|
CTT |
TADIL |
N/A |
CTT being replaced by JIT |
|
LOS, line of sight MAE UAV, medium-altitude endurance UAV, Predator MCE, mission control element; HAE UAV ground station for advanced concept technology demonstration (ACTD) activities NIS, National input segment OBP, on-board processor SHARP, Shared Reconnaissance Pod; previously Super Hornet Airborne Reconnaissance Pod TARPS, Tactical Airborne Reconnaissance Pod System TCDL, tactical common data link TCS, Tactical Control System; tactical UAV ground station; may merge into both JSIPS-N and TEG in future TEG, Tactical Exploitation Group; USMC ground station; 3 funded TGIF, Tactical Ground Intercept Facility TIGDL, tactical interoperable ground data link TIS, tactical input segment; part of JSIPS-N; TIS = CDL-Navy-ST and CIP and screener workstation and support equipment TUAV, tactical UAV VTOL, vertical takeoff and landing SOURCE: Compiled from data courtesy of National Imagery and Mapping Agency, Bethesda, Md., 1999. |
|||
TABLE E.A.2 Imagery Dissemination Systems (Indirect)
|
Number of Receivers: Current |
Total Number of Receivers in POM |
Capability |
Imagery Use |
Remarks |
|
~9 |
~10 |
1.5-45 Mbps |
1.5-45 Mbps |
DDS to ships via JCA |
|
~50 |
~300 |
1.5-24 Mbps |
0.768-6 Mbps |
|
|
All ships |
All ships |
64 kbps |
Small |
|
|
All fixed and garrison sites |
All fixed and garrison sites |
0.128-45 Mbps |
0.128-45 Mbps |
|
|
3 |
3 |
1.5 Mbps |
128+ kbps |
|
|
All fixed and garrison sites |
All fixed and garrison sites |
0.128-45 Mbps |
0.128-45 Mbps |
|
|
16 |
20 |
1.5 Mbps |
768 kbps |
Data rate can vary from 384 to 1544 kbps;normally 768 kbps |
|
~50 |
~300 |
1.5-24 Mbps |
0.768-6 Mbps |
|
|
STEP sites |
STEP sites |
768 kbps |
128 kbps |
|
|
13 |
44 |
1.544 Mbps |
Varies |
CV/CVN, LHA/ LHD, CG, LSD-41, LPD-17 |
|
JCA, Joint Services Imagery Processing System-Navy (JSIPS-N) Concentrator Architecture; USN future imagery dissemination “system”; will utilize both GBS and CA II communications system and will replace DDS for the USN. NIMA will send all imagery to USN JCA in Suitland, Maryland; JCA will then disseminate it to individual ships and user sites. MTACS, Maritime Tactical Communications System; Service-maintained, networked communication infrastructure supporting the USMC and interfaces with the USN; provides a user connection to the DISN and a communications link between command component afloat and ground component ashore POM, program objective memorandum POS, point of service; connection between local networks and DISN, could be SATCOM ground terminals like T-MET, Tri-band, or STEP, or fiber-optic land line STEP, standard tactical entry point; provides tactical communications entry into the DISN via the DSCS; to be upgraded to teleport concept, which also will include expanded capacities, protocol interfaces, and commercial connectivity TS II, Trojan Spirit II; U.S. Army deployable SATCOM terminal system; USMC also owns and operates several terminals SOURCE: Compiled from data courtesy of National Imagery and Mapping Agency, Bethesda, Md., 1999. |
||||
Annex 2 JPN, JDN, and JCTN Network Components
This annex provides a schematic diagram (Figure E.A.1) of the networks composing the Joint Planning Network, the Joint Data Network, and the Joint Composite Tracking Network.
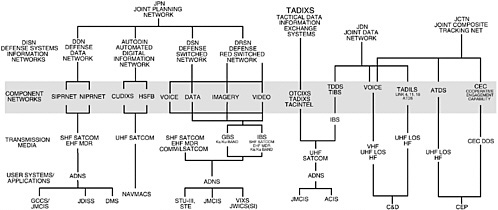
FIGURE E.A.1 Joint Planning Network, Joint Data Network, and Joint Composite Tracking Network network components. SOURCE: Modified from “Figure 3-1 TAD Communication Networks” in Bragg, Rick, PMW176-2, 1997, AADC Afloat Communications Requirements Analysis, Program Executive Office Theater Air Defense, Space and Naval Warfare Systems Command, San Diego, Calif., May 30, p. 3-2.

































