aircraft carrying large fuel loads could produce fires that would greatly complicate rescue and recovery efforts.
Previous studies on aircraft crash impacts (Droste et at., 2002; Lange et al., 2002; HSK, 2003; RBR Consultants, 2003; Thomauske, 2003) suggest that the consequences of a heavy aircraft crash on a nuclear installation depend on factors such as the following:
-
Type and design of the aircraft.
-
Speed of the aircraft.
-
Fuel loading of the aircraft and total weight at impact.
-
Angle-of-attack and point-of-impact on the facility.
-
Construction of the facility.
-
Location of the target with respect to ground level (i.e., below or above grade).10
-
The presence of surrounding buildings and other obstacles (e.g., hills, transmission lines) that might block certain potential flight paths into the facility.
In other words, the consequences of such attacks are scenario- and plant-design specific. It is not possible to make any general statements about spent fuel storage facility vulnerabilities to air attacks that would apply to all U.S. commercial nuclear power plants
U.S. commercial nuclear power plants are not required by the Nuclear Regulatory Commission to defend against air attacks. The Commission believes that it is the responsibility of the U.S. government to implement security measures to prevent such attacks. The commercial nuclear industry shares this view. The Nuclear Regulatory Commission staff informed the committee that the Commission has directed power plant operators to take steps to reduce the likelihood of serious consequences should such attacks occur. The staff also informed the committee that the Commission may issue additional directives once the vulnerability analyses it is sponsoring at Sandia National Laboratories are completed. These analyses are described in the committee’s classified report (see also Chapters 3 and 4 in this report).
2.2.2 Ground Attacks
Ground attacks on a nuclear facility could take three forms: (1) a direct assault on the facility by armed groups, (2) a stand-off attack using appropriate weapons, or (3) an assault having both air and ground components. The direct assault would likely be carried out by a group of well-armed and trained attackers, perhaps working with the assistance of an insider. The objective of such an attack would likely be to gain entry to protected and vital areas of the plant (FIGURE 2.1) to carry out radiological sabotage. The attackers would need to have knowledge of the design, location, and operation of the spent fuel facility to carry out such an attack successfully.
Commercial nuclear power plants are required by the Nuclear Regulatory Commission to maintain a professional guard force at each plant to defend against a Commission-developed design basis threat (DBT), which includes a ground assault. The protective force is a critical part of a nuclear power plant’s security system for deterring,
|
10 |
All current dry cask storage facilities in the United States are constructed at ground level, whereas spent fuel pools can be located above or below grade, depending on plant design (see Chapter 3). |
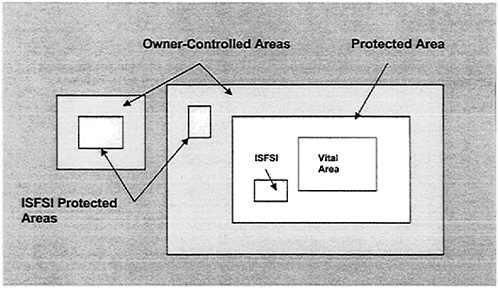
FIGURE 2.1 Commercial nuclear power plant sites are demarcated as shown for security purposes. The part of the power plant site over which the plant operator exercises control is referred to as the owner-controlled area. This usually corresponds to the boundary of the site. Located within this area are one or more protected areas to which access is restricted using guards, fences, and other barriers. Dry cask storage facilities, formally referred to as independent Spent Fuel Storage Installations (ISFSIs), are located within these areas. The vital area of the plant contains the reactor core, support buildings, and the spent fuel pool. It is the most carefully controlled and guarded part of the plant site. SOURCE: Modified from Nuclear Regulatory Commission briefing materials (2004).
detecting, thwarting, or impeding attacks. The Commission staff declined to provide a formal briefing to the committee on the DBT for radiological sabotage, asserting that the committee did not have a need to know this information. Nevertheless, the committee was able to discern the details of the DBT from a series of presentations made by Nuclear Regulatory Commission staff. Commission staff also provided a fact check of this information as the classified report was being finalized.
Power plant operators are required to demonstrate to the Commission’s satisfaction that there is “high assurance” that their guard forces can thwart the Commission-defined DBT assault. This guard force also must be able to provide deterrence against a beyond-DBT attack depending on the adversarial force. Reinforcing forces would be provided by local and state law enforcement as well as federal forces. The Commission staff also informed the committee that since the September 11, 2001, attacks, the Commission has been working with DHS to improve coordination procedures with federal, state, and local agencies to improve their response capabilities in the event of an attack. DHS also is making grants to local law enforcement agencies around power plant sites to raise their capabilities to respond to requests for assistance.


