A Decision Informatics Approach to Urban Emergency Management
James M. Tien
Rensselaer Polytechnic Institute
INTRODUCTION
Urban infrastructures are the focus of terrorist acts because, quite simply, they produce the most visible impact, if not casualties. From the September 11, 2001, attack on New York City’s World Trade Center to the more recent March 11, 2004, attack on Madrid’s commuter trains, it is obvious that urban centers are indeed vulnerable to such hideous acts. While terrorist acts are the most insidious and onerous of all disruptions, there are many similarities to the way one should deal with these willful acts—which would also include a malicious prankster releasing an electronic virus on the Internet—and those caused by natural and accidental incidents that have also resulted in adverse and severe consequences. However, there is one major and critical difference between terrorist acts and the other man-made but accidental disruptions: the terrorist acts are willful, and therefore also adaptive. Since terrorist and other willful acts (for example, electronic viruses, hacker attacks, and e-mail spam) are based on the most up-to-date intelligence or information, one must also counter these acts with the same, if not more sophisticated, willful, adaptive, and informed approach.
More specifically, the approach of real-time, information-based decision making, which Tien (2003) has called the decision informatics paradigm, is focused on decisions and based on multiple data sources, data fusion and analysis methods, timely information, stochastic decision models, and a systems engineering outlook. It should be emphatically stated that while the terms employed in describing the methodologies that underpin decision informatics are those belonging to decision analysis (emergency management, statistics, risk analysis,
and so forth), decision informatics is clearly multidisciplinary in nature and, depending on the problem being considered, could include experts from science (information, cognition, sociology, and so forth), engineering (telecommunications, biomedical, chemical, and so forth) and other disciplines (religion, terrorism, culture). It provides a systematic and consistent way to address real-time emergency issues, including those concerned with the preparation for a major disruption, the prediction of such a disruption, the prevention or mitigation of the disruption, the detection of the disruption, the response to the disruption, and the recovery steps that are necessary to adequately, if not fully, recuperate from the disruption. More importantly, one must approach an urban emergency management problem in a systemic or holistic manner, especially given the interdependencies of the underlying infrastructure systems.
Although the focus of this paper is primarily on terrorist disruptions, it is obvious that the decision informatics approach is likewise applicable to the preparation, prediction, prevention, detection, response, and recovery steps associated with the emergency management of any major urban disruption. The remaining sections of this paper deal with the types of disruption, the stages of or life cycle in a disruption, the decision informatics paradigm, and the combination of types, stages, and decisions in the efforts of the Department of Homeland Security (DHS) and its academically based Homeland Security Centers of Excellence, followed by some concluding remarks.
TYPES OF DISRUPTIONS
Modern society relies on the reliable operation of a set of human-built systems—each being a combination of people, processes, goods, services, physical structures, and institutions—to sustain people themselves, infrastructures, and commerce. In the United States, the constructed systems—most of which are privately owned and operated—are so essential that they have been called the nation’s lifelines. They are included in the broader set of critical infrastructures defined by the President’s Council on Critical Infrastructure Protection (PCCIP) (U.S. President, 2001) to be those physical and cyber-based systems essential to the minimum operations of both the economy and the government.
Historically, the nation’s critical infrastructures have been physically and logically separate systems that had little interdependence. However, as a result of advances in information technology and the necessity for improved efficiency and effectiveness, these infrastructures have become increasingly automated and interlinked. In fact, because the information technology revolution has changed the way business is transacted, government is operated, and national defense is conducted, the U.S. President (2001) singled it out as the most critical infrastructure to protect following September 11, 2001. Thus, while the United States is considered a superpower because of its military strength and economic prowess, nontraditional attacks on its interdependent and cyber-supported infrastructures could significantly harm both the nation’s military power and economy. Clearly,
infrastructures, especially the information infrastructure, are among the nation’s weakest links; they are vulnerable to willful acts of sabotage. The NRC Committee on the Role of Information Technology in Responding to Terrorism (2003) has made a number of recommendations to reduce vulnerabilities associated with the information infrastructure, including undertaking more research in authentication, detection, containment, and recovery.
The infrastructure interdependencies are most obvious when a disruption occurs. For example, interruptions in power and communications following the September 11, 2001, attack, in turn, forced the closing of the New York Stock Exchange, which is a critical part of the nation’s banking and finance infrastructure. As another example, the August 2003 electrical power outage on the East Coast caused the failure of wireless communications and affected the city of Cleveland’s water system. Clearly, there are innumerable interdependencies among the various infrastructure networks or systems that provide for a continual flow of goods and services essential to the defense and economic security of a nation. Indeed, for this reason, it is inappropriate to only categorize some infrastructure systems as being critical; they are all critical to the proper functioning of a nation or urban center; otherwise, the noncritical ones might well become the weakest links and thus vulnerable to attack and destruction. More importantly, the infrastructure interdependence problems should not be minimized, especially from a security and reliability perspective. In fact, contingency plans or backup systems should be developed and employed to mitigate these problems.
Sadly, the same advances that have enhanced interconnectedness have created new vulnerabilities, especially related to equipment failure, human error, weather, and other natural causes, and physical and cyberattacks. Thus electronic viruses, biological agents, and other toxic materials can turn a nation’s lifelines into deathlines, in that they can be used to facilitate the spread of these materials, whether by accident or by willful act. Even the Internet—with almost a billion users—has become a terrorist tool; jihad Web sites are recruiting members, soliciting funds, and promoting violence (for example, by showing the beheading of hostages). Also, as evidenced by the September 11, 2001, attack, components of an infrastructure system can be used as weapons of destruction.
As identified earlier, there are, in essence, three types of disruptions: natural incidents due to nature or natural forces, accidental incidents due to human errors or structural failures, and willful incidents due to human acts or destructive weapons. The who, what, when, and where of a number of well-known disruptions occurring in the latter half of the twentieth century are considered in Table 1.
The question remains: Are there differences between natural, accidental, and willful disruptions? The answer is an emphatic yes; indeed, these differences point to the need for a more adaptive, informed, and decision-oriented approach for dealing with willful acts than for reacting to natural and accidental disasters.
TABLE 1 Example Disruptions
|
Description |
Nature of Disruption |
|
Who? |
|
|
Natural |
|
|
1969 Hurricane Camille |
Hurricane Camille was a category 5 (out of a possible 5) hurricane. |
|
2002 SARS (Severe Acute Respiratory Syndrome) epidemic |
Employing DNA sequencing information, SARS was identified in 24 hours as a coronavirus strain from wild animals, including poultry. |
|
2004 South Asia Tsunami |
A magnitude 9.0 Indian Ocean earthquake caused tsunami tidal waves of up to 50 feet. |
|
Accidental |
|
|
1984 Bhopal Gas Tragedy |
Toxic methylisocyanate chemical vapor escaped from the Union Carbide plant due to safety valve malfunction. |
|
1986 Chernobyl Nuclear Disaster |
While testing Reactor 4 and ignoring safety procedures, a chain reaction caused explosion and release of highly radioactive material. |
|
1989 United 232 Explosion |
Failure of all three hydraulic flight control systems of Northwest’s DC-10 caused the crew to almost completely lose control of the aircraft. |
|
Willful |
|
|
1993 Oklahoma City Bombing |
Timothy McVeigh and others built bomb that was placed in a rented Ryder truck. |
|
1995 Tokyo Subway Sarin Attack |
Members of a terrorist group attacked five subway lines leading to the center city with toxic sarin nerve gas. |
|
September 11, 2001, Tragedy |
Nineteen terrorists hijacked four airliners, each loaded with thousands of gallons of jet fuel, and crashed them into highly visible U.S. targets. |
|
When? |
What? |
Where? |
|
August 17, 1969, 2 a.m. |
Regional: 255 killed; thousands evacuated; $4.2 billion in damages |
Makes landfall along Mississippi coastline |
|
November 2002–July 2003 |
Worldwide: 774 killed; 7,322 injured |
Began in South China, then Canada and Southeast Asia and a few cases in Europe and the United States |
|
December 26, 2004, 8 a.m. |
Regional: more than 160 thousand killed; thousands injured; millions displaced |
Affecting Indonesia, Sri Lanka, India, and Thailand |
|
December 2, 1984, 11 p.m. |
Regional: more than 10 thousand killed; more than 0.5 million injured |
Small town of Bhopal, India |
|
April 26, 1986, 1 a.m. |
Regional: 31 immediately killed; thousands injured and suffering disease; millions affected by remaining radiation |
Chernobyl nuclear power plant consisting of four reactors located in Ukraine |
|
July 19, 1989, 3 p.m. |
Local: 186 (of 300) crew and passengers killed; many injured |
Plane crash-lands on runway in Sioux City, Iowa |
|
April 19, 1993, 9 a.m |
Local: 168 killed; hundreds injured; building destroyed |
Oklahoma City Alfred P. Murrah Federal Building |
|
March 20, 1995, 8 a.m. |
Local: 12 killed; thousands injured |
Subway cars in Tokyo, Japan |
|
September 11, 2001, 8:47 a.m.–10:06 a.m. |
Local: 3,000 killed; billions of dollars of infrastructure and commercial damage |
American Airlines flight 11 crashes into World Trade Center (WTC) north tower; United Airlines flight 175 crashes into WTC south tower; American Airlines flight 77 crashes into Pentagon; United Airlines flight 93 crashes in field near Shanksville, Pennsylvania |
More specifically, Table 2 considers the different types of disruptions from four perspectives: cause, onset, target, and impact.
STAGES IN A DISRUPTION
The mission and overriding objective of the U.S. Federal Emergency Management Agency (FEMA), which is now a part of DHS (U.S. Congress, House, 2002), is to help the nation be ready to respond to disasters and disruptions of all kinds through a comprehensive, risk-based emergency preparedness program.
Traditionally, FEMA’s comprehensive emergency management system is composed of four stages: preparedness, mitigation, emergency response, and recovery. From a decision perspective, it is helpful to consider an expanded, six-stage process: preparation (corresponding to preparedness), prediction, prevention (corresponding to mitigation), detection, response (corresponding to emergency response), and recovery (corresponding to recovery). The additional prediction stage is necessary because it is beyond general preparation and helps focus prevention tactics; it requires a set of methodologies and technologies that is statistical in nature and risk-based in approach. The additional detection stage is also necessary; it follows prediction and precedes response and is very much dependent on data obtained from multiple data sources or sensors and the careful fusion and analysis of that data. Table 3 identifies the six stages of a disruption’s life cycle in terms of related decisions that must be considered at each stage.
DECISION INFORMATICS
In critically reviewing the disruption characteristics and related decisions identified in Tables 2 and 3, respectively, it is obvious that real-time, information-based decision making is needed for addressing major disruptions, especially terrorist acts, which are quite adaptive in reality. Alternately, what is needed is a decision informatics paradigm, as depicted in Figure 1. That is, the nature of the required real-time decision (in connection with each of the six stages of a disruption) determines, where appropriate and from a systems engineering perspective, the data to be collected (possibly, from multiple, nonhomogeneous sources) and the real-time fusion and analysis to be undertaken to obtain the needed information for input to the modeling effort, which in turn provides the knowledge to support a timely decision. The feedback loops in Figure 1 are within the context of systems engineering; they serve to refine the analysis and modeling steps.
Thus decision informatics concerns three related issues, that is, decisions, data, and information, and is underpinned by three multidisciplines, that is, data fusion and analysis, decision modeling, and systems engineering. In abbreviated form there are six steps in the decision informatics process: decisions, data,
TABLE 2 Disruption Characteristics
|
|
Characteristics |
Types of Disruption |
||
|
Natural |
Accidental |
Willful |
||
|
Cause |
Primary |
Nature |
Human Errors |
Human Acts |
|
|
Secondary |
Natural Forces |
Structural Failures |
Destructive Weapons |
|
Onset |
Period |
Hours/Days |
Hours |
Minutes |
|
|
Predictability |
High |
Medium |
Low |
|
|
Adaptability |
Low |
Low |
High |
|
Target |
Primary |
Infrastructures |
Infrastructures |
People |
|
|
Secondary |
Commerce/People |
Commerce/People |
Infrastructures/Commerce |
|
|
Vulnerability |
Indiscriminate |
Indiscriminate |
Weakest Link |
|
Impact |
Spatial |
Regional/Worldwide |
Local/Regional |
Local |
|
|
Temporal |
Years |
Months/Years |
Months/Years |
|
|
Damage |
Medium/Large |
Medium/Large |
Medium/Large |
TABLE 3 Life Cycle of a Disruption: Stages and Related Decisions
|
Stages |
Related Decisions |
|
Preparation |
How and where do terrorist groups form and recruit? How are targets picked and what motivates a willful act? How can potential terrorists be converted away from terrorism? How can one prepare for disruption without degrading quality of life and civil liberties? How can one integrate the help of industry and other private organizations? What type of resources (for example, protective gear) are available and at what locations? What integrated emergency command center needs to be established? How can one coordinate and standardize data, medical records, information systems, and communications? Is the preparation appropriate for both security and safety? How can one effectively assess preparedness? |
|
Prediction |
What precursor signals can be associated with natural, accidental, and willful incidents? What is the nature (for example, self-assembled, self-replicated) and scope of such attacks? What facilities, assets, and resources are most vulnerable to attack? In addition to direct threats, what are possible indirect or secondary threats (for example, zoonotic diseases, hurricane-related freshwater flooding)? How best can one pre-position resources for the most likely and most risky disruptions? How can one communicate accuracy of prediction? How can one provide education and simulated training for decision makers and responders? |
|
Prevention |
What identification (for example, biometric) technologies can be reliably employed to prevent unlawful entry? How can one prevent attacks, reduce vulnerability, minimize damage, and enhance recovery? How can one develop contingency plans or backup systems to mitigate interdependency problems? How can one warn the public (for example, color-coded alerts, terrorist threat index)? How and when is it possible to mitigate (for example, evacuate) before the disruption? How is it possible to mitigate problems of communications, traffic gridlock, and interjurisdictional issues? How is it possible to prevent problems associated with the roles and responsibilities of all involved? Are the prevention strategies sustainable and are they commensurate with the risk level? |
|
Stages |
Related Decisions |
|
Detection |
What sensors can be employed to detect a disruption? How is it possible to fuse and abstract valid and useful information from multiple data sources? What response preparation should be effected (for example, level of emergency)? How is it possible to validly identify the nature of an attack? What is the target (including people, infrastructures, and commerce) and scope (including time, space, and weapon used) of the attack? How is it possible to mitigate the potential impact of an attack? How is it possible to strengthen the public’s resilience to the disruption? |
|
Response |
Where should an emergency staging and medical triaging center be established? How is it possible to logistically inventory and disburse available resources, requested resources, and donated goods? How is it possible to coordinate and secure communications by computer, cellular, radio, and telephone lines? How is it possible to reposition resources for another attack or response to other incidents? How is it possible to coordinate and integrate workers and volunteers? How is it possible to coordinate within and between response levels (that is, local, regional, state, and federal)? How is it possible to communicate with the public, including dealing with the media? |
|
Recovery |
Which targets remain at risk and must be taken out of harm’s way? What can be done to recover from the resultant damages? How is it possible to store, protect, retrieve, and recover critical data? What state, federal, and commercial aid can be obtained to fund the recovery? What recovery goals, measures, and assessment procedures have been established? What projects, tasks, budget, and schedule are necessary for the recovery? What can be put in place to forestall or prepare for another disruption? |
analysis, information, models, and systems. These steps are summarized in Table 4.
Finally, it should be noted that decision informatics is, as a framework, generic and applicable to most, if not all, decision problems. Further, since any data analysis or modeling effort should only be undertaken for some purpose or decision, all analyses and modeling activities should be able to be viewed within the decision informatics framework. In short, decision informatics represents a decision-driven, information-based, adaptive, real-time, human-centered, inte-
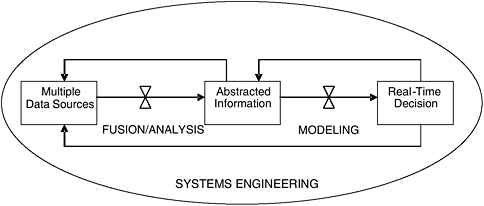
FIGURE 1 Decision informatics paradigm.
grated, and computationally intensive approach to intelligent decision making by humans or software agents. Consequently, it can be very appropriately employed to address decisions at the preparation, prediction, prevention, detection, response, and recovery stages of an urban disruption.
HOMELAND SECURITY
Following the September 11, 2001, attack on the U.S. homeland, the U.S. Homeland Security Act of 2002 (Public Law 107-296, see U.S. Congress, House, 2002) was immediately passed; it established DHS with a mission to “a) prevent terrorist attacks within the United States; b) reduce the vulnerability of the United States to terrorism; and c) minimize the damage, and assist in the recovery, from terrorist attacks that do occur within the United States.” Additionally a number of high-level reports have been published on how to make the homeland more secure from future acts of terrorism. The U.S. National Academies formed the Committee on Science and Technology for Countering Terrorism (2002); it strongly urged, among several other important recommendations, a risk- or decision-based approach to measuring and countering terrorism. It also helped define the Directorate of Science and Technology that is now a part of DHS. More recently, the National Commission on Terrorist Attacks Upon the United States (2004) is recommending the establishment of a National Counterterrorism Center—with a National Intelligence Director—to unify all counterterrorism intelligence and operations across the foreign-domestic divide in one organization. This and other commission recommendations are currently being addressed in Congress.
As stated in two related presidential directives (U.S. President, 2003a,b), the National Response Plan (NRP) (DHS, 2004) establishes a comprehensive all-hazards approach to enhance the ability of the nation to manage domestic inci-
TABLE 4 Decision Informatics Steps
|
Steps |
Considerations |
|
Decisions |
|
|
Disruptions |
Natural, Accidental, Willful |
|
Levels |
Operational, Tactical, Strategic, Systemic |
|
Targets |
People, Infrastructures, Commerce |
|
Data |
|
|
Attributes |
Measurability, Availability, Consistency, Validity, Reliability, Stability, Accuracy, Independence, Robustness, Completeness |
|
Sources |
Sensors Intelligence (SENSINT), Signals Intelligence (SIGINT), Imagery Intelligence (IMINT), Human Intelligence (HUMINT) |
|
Issues |
Standards, Compatibility, Interoperability, Scale |
|
Analysis |
|
|
Types |
Data Fusion, Data Analysis, Data Mining, Data Interpolation, Evolutionary Algorithms, Strengths, Weaknesses, Opportunities, Threats |
|
Disciplines |
Decision Analysis (Statistics, Risk Analysis, Operations Research, Economics), Science (Information, Cognition, Psychology, Sociology, Behavior, Organization, Computer, Agriculture, Livestock, Food, Ocean, Atmosphere), Engineering (Telecommunications, Human Factors, Biomedical, Chemical, Nuclear), Other (Religion, Terrorism, Culture) |
|
Information |
|
|
Attributes |
Same as Data Attributes |
|
Sources |
Same as Data Sources |
|
Types |
Threats, Vulnerabilities, Risks, Damages (Mortality, Morbidity, Physical, Environmental, Financial) |
|
Issues |
Same as Data Issues |
|
Characteristics |
Processed Data, Derivations, Groupings, Patterns |
|
Models |
|
|
Types |
Descriptive (System Dynamics, Simulation), Prescriptive (Mathematical Programming, Dynamic Programming), Adaptive (Evolutionary Models, Bayesian Networks) |
|
Disciplines |
Same as Analysis Disciplines |
|
Systems |
|
|
Attributes |
Intra-/Interdependent, Natural/Human-made, Physical/Conceptual, Static/Dynamic, Closed/Open |
|
Resources |
Law Enforcement, Firefighting, Public Works, Public Health, Emergency Medical, Private, Financial |
|
Networks |
Private (Organizations, Institutions), Public (Local, Regional, State, Federal), Cyber |
|
Issues |
Privacy, Civil Liberties, Quality of Life |
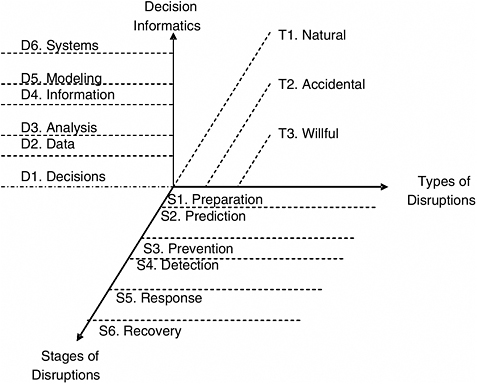
FIGURE 2 Urban disruptions: types, stages, and decisions.
dents. The NRP incorporates best practices and procedures from incident management disciplines—homeland security, emergency management, law enforcement, firefighting, public works, public health, responder and recovery worker health and safety, emergency medical services, and the private sector—and integrates them into a unified structure. It forms the basis of the federal government’s coordination with state, local, and tribal governments and the private sector during incidents. Further, to enhance the ability of the nation to manage domestic incidents, a single, comprehensive National Incident Management System (NIMS) is being established. The NRP is predicated on the NIMS. Together, the NRP and the NIMS provide a nationwide template for working together to prevent or respond to threats and incidents regardless of cause, size, or complexity.
DHS is organized into four major directorates: Border and Transportation Security (including sensors, signals, passenger profiling, and prevention tactics), Emergency Preparedness and Response (including preparation, prediction, prevention, detection, response, and recovery), Information Analysis and Infrastructure Protection (including data fusion and analysis, disruption modeling, performance versus cost analysis, vulnerability/risk assessment tools, and systems considerations), and Science and Technology (including biometric sys-
tems, weapons detection systems, and satellite image systems). DHS actually outsources many of its activities through contracts and grants—to federal laboratories, government agencies, and private organizations. In April 2004 the $130 million, 4.5-year Homeland Security Institute was established at Analytic Services, Inc., or ANSER, a systems engineering think tank modeled after the RAND Corporation.
Additionally, through the Office of University Programs within the Science and Technology Directorate, DHS is engaging the academic community to create learning and research environments in areas critical to homeland security. Labeled Homeland Security Centers of Excellence, it is helpful to consider them within the three-dimensional framework—types, stages, and decisions— discussed in the previous sections of this paper. As depicted in Figure 2, this framework identifies 3 by 6 by 6, or 108, possible foci for study consideration. Thus far, four Homeland Security Centers of Excellence have been established, while a fifth one is forthcoming; they are summarized in Table 5.
CONCLUDING REMARKS
Securing the homeland from damaging willful acts is a matter of trade-offs: between security and people, in particular, people’s privacy, civil liberties, and quality of life; between security and infrastructures, in particular, infrastructures that are highly interdependent; and between security and commerce, in particular, commerce that is dependent on highly efficient and nonredundant processes. In short, it is a trade-off between security and a free society.
Interestingly, the tools or technologies that underpin a modern society are likewise the weapons that can be used to undermine, if not destroy, society. Biological, chemical, and nuclear breakthroughs can also be considered to be weapons of mass destruction; the highly effective Internet provides a medium for cyberviruses, hackers, and spammers; and airplanes are employed as missiles against people, infrastructures, and commerce.
The decision informatics approach to urban emergency management can clearly address a number of vulnerabilities, including natural disasters, accidental tragedies, and willful acts. Several comments should be made about this approach. First, it is multidisciplinary in nature; obviously, depending on the problem being considered, it requires experts from many disciplines. Second, it is evolutionary in practice; as a problem becomes better understood, the approach could be better refined and made more expeditious. Third, it is systemic in scope; it seeks to consider a problem from different perspectives, in terms of, for example, efficiency and reliability, public and private goals, and domestic and international concerns.
The purpose of this paper, then, is to argue for the development of decision technologies that can be employed to prepare for a major disruption, if not predict and possibly prevent the disruption. Such technologies should also detect
TABLE 5 Homeland Security Centers of Excellence: Focus on Types, Stages, and Decisions
|
Established (3-Year Funding) |
Lead/Primary Partner Universities/Others |
Scope |
|
November 2003 ($12 million) |
Univ. of Southern California Univ. of Wisconsin, Madison New York Univ. North Carolina State Univ. Carnegie Mellon Univ. Others: Consultants, Academia |
Risk analysis related to economic consequences of terrorist threats and events |
|
April 2004 ($18 million) |
Texas A&M Univ. Univ. of Texas/Medical Branch Univ. of California, Davis Univ. of Southern California Univ. of Maryland Others: Industry, Government, Academia |
Potential threats to animal agriculture, including foot-and-mouth disease, Rift Valley fever, avian influenza, and brucellosis |
|
April 2004 ($15 million) |
Univ. of Minnesota Michigan State Univ. Univ. of Wisconsin, Madison North Dakota State Univ. Georgia Institute of Technology Others: Major Food Companies |
Agro-security issues related to postharvest food protection |
|
January 2005 ($12 million) |
Univ. of Maryland Univ. of California, Los Angeles Univ. of Colorado, Boulder Monterey Institute of International Studies Univ. of Pennsylvania Univ. of South Carolina, Columbia Others: Academia |
Applying social science to the understanding and prevention of terrorism |
|
Forthcoming ($15 million) |
To be determined. |
Ways to prepare for, respond to, and recover from major disasters |
|
Center Name |
Types |
Stages |
Decisions |
|
Homeland Security Center for Risk and Economics Analysis of Terrorism Events (CREATE) |
Willful |
Preparation Prediction Prevention Response |
Decisions Data Analysis Information Modeling Systems |
|
Homeland Security National Center for Foreign Animal and Zoonotic Disease Defense |
Natural Accidental Willful Detection |
Preparation Prediction Prevention Response |
Decisions Data Analysis Information Modeling Systems |
|
Homeland Security Center for Food Protection and Defense |
Accidental Willful |
Preparation Prediction Prevention Detection Response |
Decisions Data Analysis Information Modeling Systems |
|
Homeland Security Center of Excellence on Behavioral and Social Research on Terrorism and Counterterrorism |
Willful |
Preparation Prediction Prevention Recovery |
Decisions Data Analysis Information Modeling Systems |
|
Homeland Security Center for the Study of High Consequence Event Preparedness and Response |
Natural Accidental Willful |
Preparation Prediction Prevention Detection Response Recovery |
Decisions Data Analysis Information Modeling Systems |
the disruption, identify the responses required to deal with the resultant situation, and then, following the disruption, specify the recovery steps that are necessary to satisfactorily recuperate from the disruption.
REFERENCES
National Commission on Terrorist Attacks Upon the United States. 2004. The 9/11 Commission Report. Washington, D.C.: W. W. Norton and Company.
NRC Committee on Science and Technology for Countering Terrorism. 2002. Making The Nation Safer: The Role of Science and Technology in Countering Terrorism. Washington, D.C.: The National Academies Press.
NRC Committee on the Role of Information Technology in Responding to Terrorism. 2003. Information Technology for Counterterrorism: Immediate Actions and Future Possibilities. Washington, D.C.: The National Academies Press.
Tien, J. M. 2003. Towards a Decision Informatics Paradigm: A Real-Time, Information-based Approach to Decision Making. IEEE Transactions on Systems, Man, and Cybernetics, Special Issue, Part C, 33(1):102–113.
U.S. Department of Homeland Security (DHS). 2004. National Response Plan. Washington, D.C.: Department of Homeland Security.
U.S. Congress, House. 2002. Homeland Security Act of 2002. Public Law 107-296, as amended. H. R. 5005-8. 107th session.
U.S. President. 2001. Executive Order on Critical Infrastructure Protection. Washington, D.C.: The White House, October 16.
U.S. President. 2003a. Homeland Security Presidential Directive (HSPD) 5. Washington, D.C.: The White House, February 28.
U.S. President. 2003b. Homeland Security Presidential Directive (HSPD) 8. Washington, D.C.: The White House, December 17.
















