Report of U.S.-Russian Working Group on Cyberterrorism Issues
Anita K. Jones, Igor Fedorov, Lewis M. Branscomb, Nikolay V. Medvedev, Yury K. Shiyan, Linton Wells III, Michael Wolin, A. Chelsea Sharber
The National Academies-Russian Academy of Sciences Working Group on Cyberterrorism Issues held discussions and consultations in Washington, D.C., on January 27 and 28, 2005. Experts from institutions in Moscow and the United States comprised the working group.
The working group visited the U.S. Department of Homeland Security (DHS) National Cyber Security Division (NCSD) and the D.C. Emergency Management Agency and received briefings from the CERT Coordination Center (CERT/CC) at Carnegie Mellon University and the National Academies Computer Science and Telecommunications Board. In addition, working group members made presentations on current and past activities in the United States and Russia on the contribution to security from work in the field of computer science. These activities include several National Academies reports, the 2003 Conference on Grand Challenges in Information Security and Assurance, the curriculum for the six-year program to train cybersecurity specialists at Bauman Moscow State Technical University, and advancements to incorporate cybersecurity into Russian government policy and legal framework.
SITE VISITS
U.S. Department of Homeland Security National Cyber Security Division (NCSD). The working group became acquainted with NCSD’s mandate, which is shared with U.S. Computer Emergency Readiness Team (U.S.-CERT) and described in the publications National Strategy for Homeland Security1 and
|
1 |
Office of Homeland Security. 2002. National Strategy for Homeland Security. Washington, D.C.: The White House. See http://www.whitehouse.gov/homeland/book/. |
The National Strategy to Secure Cyberspace.2 The working group also learned about NCSD’s priorities and mission—to secure cyberspace and U.S. cyberassets by implementing the strategy outlined in The National Strategy to Secure Cyberspace and priority protective measures to reduce the cybervulnerabilities of U.S. critical infrastructures. NCSD is divided into four organizational components: (1) U.S.-CERT operations, (2) outreach and awareness, (3) strategic initiatives, and (4) law enforcement and intelligence coordination.
NCSD’s international objectives include international cooperation with industry and critical infrastructure sectors; increased computer security incident response capabilities through training and technical assistance, adoption and implementation of principles described in OECD Guidelines for the Security of Information Systems and Networks: Toward a Culture of Security;3 and encouragement of other countries’ acceptance of the Council of Europe Convention on Cybercrime or individual laws at least as comprehensive (this becomes relevant when criminals are not physically within U.S. jurisdiction). Finally, the NCSD seeks a balance among government policy makers, law enforcement, and computer security incident response teams for international cooperation and collaboration.4
CERT Coordination Center. The CERT/CC connection to DHS was discussed, as well as trends in cybercrime. The malicious codes created to disturb the cyberenvironment are becoming more sophisticated. As a result, it is no longer possible to separate physical security and cybersecurity. Whether cyber or criminal threats are made, a better categorization than malicious activity in cyberspace needs to be created for them.5
D.C. Emergency Management Agency/Emergency Operations Center. The working group visited the Emergency Operations Center (EOC) of the D.C. Emergency Management Agency. Before September 11, 2001, the EOC was much smaller, with only 24 seats available for various response and critical infrastructure organizations. Not all of these seats had computers, and the computers that were in place were networked to one another but not outside the building. Since September 11, 2001, the EOC has been remodeled and can seat 50–60 representatives of the relevant response and critical infrastructure organi-
|
2 |
The Whitehouse. 2003. The National Strategy to Secure Cyberspace. Washington, D.C.: The White House. See http://www.whitehouse.gov/pcipb/cyberspace_strategy.pdf. |
|
3 |
Organisation for Economic Co-Operation and Development. 2002. OECD Guidelines for the Security of Information Systems and Networks: Toward a Culture of Security. Paris, France: OECD. |
|
4 |
Information taken from a presentation, National Cyber Security Division and U.S.-CERT— Overview, made by Liesyl Franz, Public Policy and International Affairs, National Cyber Security Division, U.S. Department of Homeland Security, on January 27, 2005 to the U.S.-Russian Working Group on Cyberterrorism Issues. |
|
5 |
Information taken from a presentation to the U.S.-Russian Working Group on Cyberterrorism Issues by Casey Dunlevy, CERT/CC, January 28, 2005. |
zations. It is connected to the D.C. power grid and has backup battery power, a backup generator, and analog telephones in case of power failure. Weekly tests are conducted on the generator. In addition, two backup sites and two mobile command vans are available. This remodeled site, however, will soon be replaced by a completely new EOC located at a new site in D.C.
In addition to housing and managing the EOC, the D.C. Emergency Management Agency works with the community to provide current information on emergency situations and current guidelines on action in an emergency. This includes the Alert D.C. Program, a voluntary program that allows D.C.-area residents and employees to receive emergency communications as text messages, voice alerts, or radio broadcasts, and publications such as It’s a Disaster! … and What Are YOU Gonna Do About It? A Disaster Preparedness, Prevention, and Basic First Aid Manual.6
PRIORITIES FOR THE FUTURE
The working group considered the following important priorities for future investigation.
Development of cooperative and complementary research programs to develop new principles, methods, and tools to design and construct more dependable systems; to quantify system attributes and risk (metrics); and to prevent, detect, and recover from cyberattacks. The working group believes that the rate of research progress to develop more dependable and robust systems is far short of what is needed. Further, without metrics to quantify both costs and benefits of reducing vulnerability to cyberattack, markets for those tools will continue to be weak.
Explore the most effective approach for developing national and international policy and law for cybercrime and cyberterrorism. In order to develop policy, it is important to examine the need for a common glossary of terms for international use in laws and regulations, jointly developed by legal and technical experts, and to explore how the academies can facilitate the solution of these problems.
Legal and regulatory structures for suppressing cyberattacks are fragmentary, inconsistent in terms and language used, and incompatible across national boundaries. Progress to rectify these shortcomings is urgent. A good place to start is a common set of terms for the methods of cyberattack, agreed to internationally by technical and legal experts.
Develop and exchange curricula for cybersecurity education and training. Cybersecurity education, based on a solid computer science foundation and including at least two postgraduate years of advanced and practical work, is essential to staff the vulnerable institutions and meet the need to develop better tools and methods. The main goals for specialist training include
-
developing a security policy based on international and national standards
-
using international standards to analyze information security risks
-
developing a network traffic security policy
-
applying techniques of information security identification and elimination of information security threats
-
implementing techniques of information security based on international and national standards
-
identifying information security risks
-
modeling attacks and protection technologies
-
auditing information security systems
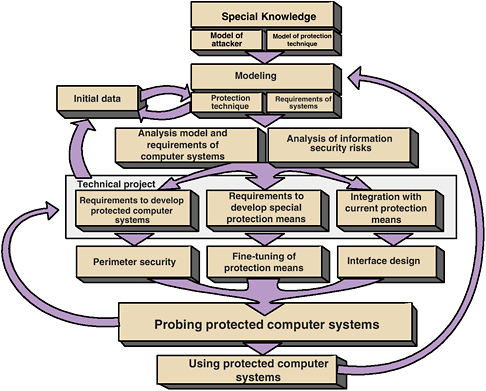
FIGURE 1 Skills for cybercrime prevention specialists at Bauman Moscow State Technical University.
The six-year program at Bauman Moscow State Technical University provides an interesting model for cybereducation and cybertraining. Figure 1 shows how different elements of education relate to each other.
Enable exchange visits of university scholars studying cybersecurity. The working group believes that academic exchanges are the best way to get experience with alternative curricula for cybersecurity. Summer internships and programs for students (graduate and undergraduate), instructors, and researchers are included in this possibility.





