In order to provide more reliable and efficient service, the electric power delivery system is incorporating an ever increasing amount of data transfer, with communications occurring over a wide array of systems. Massoud Amin, University of Minnesota, noted that the systems have become so intertwined that operators may forget where the data is coming from, citing an anecdote of a power plant operator who was receiving all of his commands over the internet. Granger Morgan, CMU, pointed out that while adding more points of intelligent control can add capacity, stability, and flexibility, it also adds more entry points for cyberattack. Paul Nielsen, Software Engineering Institute, CMU, asked a question about the conundrum facing utilities today: What risk are you willing to accept for capability?
While the sophistication of cyberattacks is increasing, the level of technical knowledge necessary for the attack is decreasing according to both Dr. Nielsen and Patricia Hoffman, DOE (Figure 3-1). Joseph McClelland, FERC, noted that the power sector is an increasing target for cyberattacks, both in the United States and abroad. Stressing the ubiquitous nature of cyberattacks, Terry Boston, PJM Interconnection, recalled a common saying: “There are two types of people: those who’ve been attacked, and those who don’t know they’ve been attacked.” With such attacks becoming commonplace, it is crucial to understand where the underlying vulnerabilities lie in the electric power delivery system.
Galen Rasche, Electric Power Research Institute (EPRI), described the new world that is emerging—just as critical infrastructure has become increasingly integrated with the electric power system, so too has the grid become more reliant upon the communications network (Figure 3-2). An increasing number of sensors applied to the grid allows for both improved flexibility and increasing automation. However, Mr. McClelland noted that such an increase in automation increases the number of on-ramps for cyberattacks. And as Mr. Rasche pointed out, this increased integration with the communications infrastructure can leave the grid vulnerable, as layer upon layer of connectedness results in an increasing amount of trust placed in suppliers.
The legacy systems common in transmission and distribution systems often communicate via insecure protocols, according to Mr. Rasche. One of the biggest challenges in securing this legacy hardware is the fact that these very protocols are created through standards organizations, and such processes are, by design, very slow to change. Therefore, more robust network, system, and security management protocols are necessary for transmission and distribution systems to identify the types of security faults common to antiquated hardware.
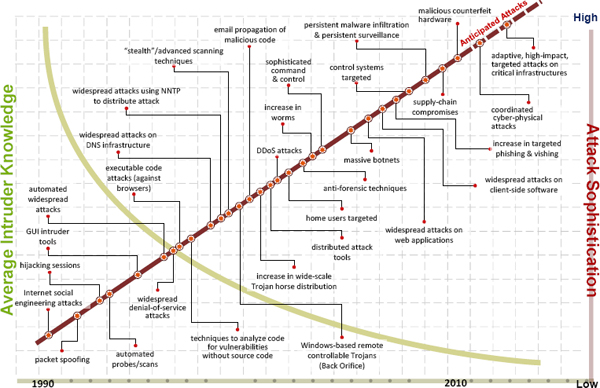
FIGURE 3-1 Average intruder knowledge and attack sophistication as a function of time. SOURCE: Presented at the workshop by Patricia Hoffman, Department of Energy, February 27, 2013; from Howard Lipson, Carnegie Mellon University (CMU) Software Engineering Institute CERT®. Copyright 1998-2011. This CMU and Software Engineering Institute material is furnished on an “as-is” basis. CMU makes no warranties of any kind, either expressed or implied, as to any matter including, but not limited to, warranty of fitness for purpose or merchantability, exclusivity, or results obtained from use of the material. CMU does not make any warranty of any kind with respect to freedom from patent, trademark, or copyright infringement.
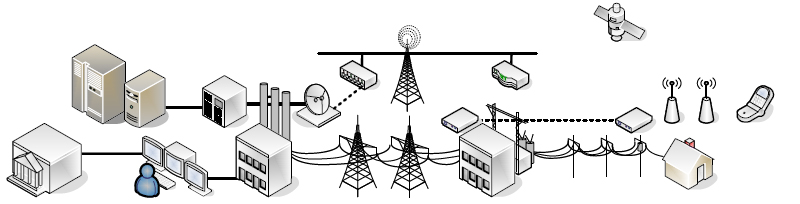
FIGURE 3-2 The communications network (top) and electric grid infrastructure (bottom) merged, with smart metering being deployed in homes, sensors being deployed at the distribution infrastructure, and all of this being communicated to users at central control facilities. SOURCE: Galen Rasche, EPRI, workshop presentation, February 27, 2013.
Modernized hardware and software do not necessarily offer increased protection, however. As Fred Hintermeister, North American Electricity Reliability Corporation (NERC), pointed out, supply chain security is critical to ensuring that a particular subsystem is secure, regardless of the system or vendor. Dr. Nielsen agreed, expanding on the necessity of knowing who wrote the software for every component of all of your partners’ systems. While this may seem a
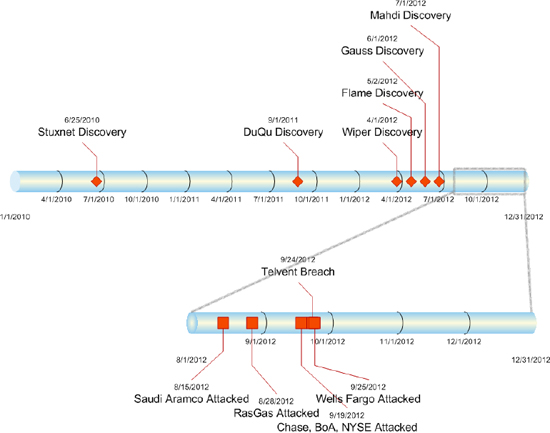
FIGURE 3-3 High-profile cyberattacks (2010-2012), with magnification of August through December, 2012. SOURCE: Fred Hintermeister, NERC, workshop presentation, February 27, 2013.
daunting task, the increasing number of attacks is pushing hard on utilities and their partners to ensure that their systems are secure at every level. NERC is working with a global network of governmental intelligence sources, vulnerability researchers, and others to develop products that specifically address emergent issues, particularly in the area of cybersecurity. A system is only as secure as its weakest link, and it is a crucial part of established NERC procedure to push mitigation measures out to the relevant bulk power system entities in a timely manner so that they may address the full chain of operations.
Risk Assessment and Cybersecurity
Given the prevalence of attacks (Figure 3-3), it is crucial to evaluate how best to maintain system integrity with minimal risk. Dr. Nielsen suggested that appropriate choice of architecture can help make these trades in design by linking the business goals to system goals. Dr. Morgan noted that that separate risk assessments could be needed for natural disasters and intelligent agents. While it would be possible to evaluate which architecture is more vulnerable
than another to a given susceptibility, the probability of attack relevant to making an analytical choice in system architecture will be substantially different for a natural disaster than for a terrorist threat.
Making such a risk assessment is difficult, according to Mr. Rasche. Because cybersecurity involves the meshing of two networks based on completely different expertise, it is difficult to adopt common protocols for risk analysis. Narain Hingorani, Consultant and National Academy of Engineering member, and Anjan Bose, Washington State University, agreed that cross-expertise and operator training are both significant issues at this interface. Mr. Hintermeister mentioned ongoing work in this area: The NERC Information Sharing and Analysis Center maintains a near-real-time, grid-common operational picture to inform risk assessment and mitigation development and delivery.
Diane Munns, MidAmerican Energy Company, noted that the regulatory bodies are at a particular disadvantage when it comes to both expertise and authority. On top of this, the regulatory process itself is not well designed for cybersecurity, according to Mr. McClelland. NERC can develop standards for reliability and cybersecurity and submit them to FERC, but because the process is both slow and open, it is not adequate for national security purposes—in effect, both the threat and the mitigation strategy are announced through the regulatory process.
Given the nature of the cyberthreat, there was significant discussion over the potential for catastrophic damage, particularly for causing damage to the physical infrastructure. Dr. Morgan cited recent work at Carnegie Mellon indicating a low probability that a hacker could destabilize the bulk power grid by toggling customer loads via hacked smart meters.1 However, Mr. McClelland cited both the Aurora test at Idaho National Laboratory 2 and a collaborative project with Lawrence Berkeley National Laboratory to identify critical frequency vulnerabilities for customer load shedding as evidence of the sensitivity of certain aspects of the physical infrastructure to cyberattack.3 Dr. Amin also suggested such potential vulnerability, though other participants commented that the Aurora experiment in particular was not indicative of a typical utility control system. Regardless of the disagreement over a potential causal link, however, participants from both perspectives agreed that a cyberattack combined with a damaged physical infrastructure would magnify the effectiveness of a terrorist threat, particularly in the event of a coordinated attack on multiple fronts.
There are many cybersecurity actions that can be taken to reduce vulnerability to a cyberattack. Most obviously, according to Dr. Amin, wireless and public internet access should
___________________________
1 A. Narayanan, 2012, The emerging smart grid: Opportunities for increased system reliability and potential security risks, Dissertations, Paper 138, available at http://repository.cmu.edu/dissertations/138.
2 Video available at http://www.youtube.com/watch?v=fJyWngDco3g.
3 J. H. Eto, J. Undrill, P. Mackin, R. Daschmans, B. Williams, B. Haney, R. Hunt, J. Ellis, H. Illian, C. Martinez, M. O’Malley, K. Coughlin, and K. Hamachi-LaCommare, 2010, Use of frequency response metrics to assess the planning and operating requirements for reliable integration of variable renewable generation, LBNL-4142E, December, available at http://certs.lbl.gov/pdf/lbnl-4142e.pdf.
be avoided at all costs. Mr. Boston suggested building the system like a nuclear secure lab, where communication is handled as an information diode that does not “shake hands” with the computer, so that information transfer is one-way.
According to Dr. Amin, the vulnerabilities of centralized control seem to demand smaller, local system configurations. Thus, resilience may depend upon the ability to bridge top-down and bottom-up decision making in real time. This highlights the need for building secure sensing, fast reconfiguration, and self-healing into the infrastructure. Mr. Rasche also recognized the importance of real-time analytics and integrity checking, because these systems cannot simply be taken off-line. Mr. McClelland highlighted the ongoing efforts by FERC to anticipate attacks through pattern recognition as one particular example of real-time analytics that can increase cybersecurity in the power system. Ms. Hoffman also acknowledged the importance of situational awareness: Aggregating monitoring information to develop a “common operating picture” enables real-time prevention and can boost the effectiveness of training exercises. Such an approach should be risk-oriented and data-driven, with the data being linked to actionable knowledge, according to Mr. Hintermeister.
Tabletop exercises on the impact of cyberattacks offer an opportunity for close coordination between information technology experts and power system experts, according to Mr. Rasche. Such penetration testing would be significantly improved through a common metric for cyberresilience. Assessing the vulnerability of a system is difficult, particularly in the case of a zero-day, or previously unknown, vulnerability. How can one measure resilience to an unanticipated event?
Because most utilities do not have an integrated security system, according to Mr. Rasche, devices tend to be upgraded in silos. A more systematic approach would allow correlating events across distributed power systems with the data being collected, as suggested above. Dr. Amin suggested that the industry should facilitate and encourage design of security at the start and look to include it in standards where appropriate. The certification of vendor products for cyberreadiness would essentially allow for security by default. Mr. Hintermeister pointed out the use of NERC’s HYDRA network of subject matter experts for the technology vendor supply chain. Because reliable operation necessitates security throughout the entire supply chain, it is crucial to approach the problem at both the hardware and software level.

Mr. Boston pointed out that collaboration is key. It is important to leverage industry relationships to share best practices and coordinate response plans. He pointed to the benefits of PJM Interconnections partnerships with DHS, the University of Maryland, Boeing, and the Pacific Northwest National Laboratory as evidence of the way in which shared expertise can benefit the industry. While Mr. Hintermeister agreed on the need to embrace partnerships, he stressed that it is important to have empathy for the partners. Everyone has a different role and different concerns, and one must be aware of those additional requirements.





