2
Workshop Discussions and Key Themes
Over the course of the 3-day workshop, there were numerous topics raised by speakers and brought up during related discussions. These topics and discussions are organized, roughly, according to the workshop terms of reference (provided in Appendix A). Finally, there are contained in each of the following sections certain key themes that arose during the workshop across multiple presentations and associated discussions, and these are highlighted below.
CURRENT TECHNOLOGICAL AND GOVERNMENT POLICY CHALLENGES
Current Department of Defense (DoD) policy guidance pertaining to secure and reliable microelectronic components is covered by DoD Instruction (DoDI) 5200.44 and DoDI 4140.67.
Establishes policy and assigns responsibilities to minimize the risk that DoD’s warfighting mission capability will be impaired due to vulnerabilities in system design or sabotage or subversion of a system’s mission critical functions or critical components by foreign intelligence, terrorists, or other hostile elements.1
Establishes policy and assigns responsibilities necessary to prevent the introduction of counterfeit materiel at any level of the DoD supply chain.2
The Defense MicroElectronics Activity (DMEA) is the sole manager of the Trusted Access Program Office (TAPO) that is responsible for ensuring that trusted microelectronics are available for U.S. national security systems.3 The speaker from DMEA noted that his organization is primarily interested in DoDI 5200.44—specifically, the requirement to use trusted foundries and suppliers for application-specific integrated circuits (ASICs). A participant from the Office of the Secretary of Defense noted that DoDI 5200.44 requires and promulgates acquisition programs to use only ASICs that have been designed, fabricated, and packaged by suppliers that have been “trust” accredited by DMEA. Importantly, however, one participant noted that the current government policies only cover ASICs and do not address other commercial-off-the-shelf (COTS) electronic components, which make up the majority of microelectronics used in DoD mission-critical systems. DoDI 5200.44 also authorizes the Air Force Office of Special Investigations (AFOSI) to investigate and provide threat reports upon request. These threat reports are created and disseminated through the Defense Intelligence Agency’s (DIA’s) Threat Assessment Center (TAC).4
______________________
1 Department of Defense, “Protection of Mission Critical Functions to Achieve Trusted Systems and Networks (TSN),” DoDI 5200.44, November 5, 2012. http://www.dtic.mil/whs/directives/corres/pdf/520044p.pdf.
2 Department of Defense, “DoD Counterfeit Prevention Policy,” DoDI 4140.67, April 26, 2013, http://www.dtic.mil/whs/directives/corres/pdf/414067p.pdf.
3 The TAPO was established in 2006 based on the recommendations of Defense Science Board, Task Force on High-Performance Microchip Supply, 2005, http://www.acq.osd.mil/dsb/reports/ADA435563.pdf.
4 According to the speaker from AFOSI, the Intelligence Community does not have a policy directive equivalent to DoDI 5200.44.
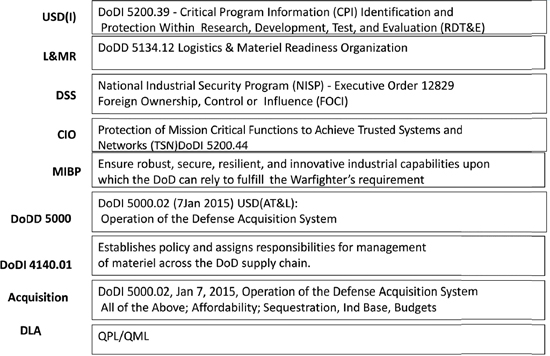
SOURCE. Dave Davis, Chief Engineer, Air Force Space and Missile Systems Center, presentation to the
workshop on March 17, 2016.
The chief engineer from the Air Force Space and Missile System Center (SMC) agreed and affirmed that SMC follows DoDI 5200.44 in the areas of getting DIA TAC reports for risk assessments, counterfeit prevention, and the use of DMEA-accredited ASICs. A DMEA representative noted that there is widespread knowledge of the DoDI 5200.44 policy, but not necessarily the definition of the policy. A speaker from the National Defense Industry Association (NDIA) confirmed this view by stating that there is a knowledge gap in government of the requirements of 5200.44 and that there is a need to educate the acquisition community on 5200.44.5 Finally, Figure 2-1 provides examples of the organizations and policies addressing the multiple missions and solutions required to address integrity assurance in microelectronic components used in DoD national security and weapons systems, according to multiple participants.
Finally, a key limitation with respect to government policies in the area of microelectronics is the time involved in drafting and implementing new DoD-wide policies—specifically, it can take up to 2 years to write and 2 years to implement new policies, according to a participant from the Office of the Secretary of Defense (OSD). At the same time, this participant agreed that more guidance in this area will help.
In addition to DoDI 4140.67 and DoDI 5200.44, DoDI 5000.02 requires government and industry program managers to employ system security engineering and prepare and maintain a program protection plan (PPP) throughout the acquisition life cycle of a weapon system.6 According to the speaker from OSD, a PPP requires the identification of critical components in a weapon system and associated risk assessment based on threats, vulnerabilities, and mission criticality. According to the speaker from SMC, they have been
______________________
5 The following section provides examples for better government and industry collaboration.
6 Department of Defense, “Operation of the Defense Acquisition System,” DoDI 5000.02, January 7, 2015, http://www.dtic.mil/whs/directives/corres/pdf/500002p.pdf.
performing rigorous program protection and countermeasures of the supply chain out of necessity for decades, due to the demands of space systems. Lessons learned from SMC’s approach to monitoring suppliers may be applicable to others, including the Joint Federated Assurance Center (JFAC). In response to recent releases where the DoD, NDIA, and the National Institute of Standards and Technology now specify that systems engineers are to provide program protection planning, the speaker noted that SMC’s systems engineers have historically performed this function. The speaker noted that requirements call for a security systems engineer (SSE) who performs the oversight of the program protection effort and is aligned with most of the activities currently being performed by SMC systems engineers.
Lastly, embedded systems were noted by multiple participants to be the next big policy issue in the area of secure and reliable microelectronics. The issue is that third-party providers who supply the embedded systems are not scrutinized by the DoD program protection policies being imposed on the discrete component providers. An example that was discussed during the presentation from AFOSI related that the provenance and design documentation, which is considered intellectual property (IP) by the owners of the embedded systems, is rarely provided. This results in components from suppliers that are unspecified to DoD being placed in systems to perform the most critical functions—for example, random number generators. In fact, the majority of microprocessor design products may be from third-party providers.7
______________________
7 Microprocessors are a security concern because of the impact they have on system operations, and the design complexity involved, which makes detection of hidden or unwanted functions to be extremely difficult. But there are many other complex devices vulnerable as well, such as FPGAs, ASICs, memory, and random number generators, which play a crucial role in intense computations, such as cryptographic functions.
Current Technology Capabilities to Detect Fraud and Counterfeits
Counterfeit and clone components are increasingly an issue that the DoD is facing with respect to secure and reliable microelectronics and were the main topics addressed by speakers from AFOSI and the Naval Surface Warfare Center (NSWC). According to presentations, the United States is losing critical IP due to globalization. Key issues the government is facing include (1) clones fabricated in unknown foundries that mimic the operation of authentic parts and (2) replications derived from stolen IP that instead are reverse-engineered with potentially altered function. A participant noted that the examples shown in the presentations were of older technologies and asked if counterfeiting is more of an issue with older technologies. The speaker from NSWC replied that counterfeiters are rapidly keeping up with advances in technology. Relatedly, the speaker from AFOSI noted that the Air Force is the largest consumer of old and obsolete technologies and that there are no parts that are beyond interest of counterfeiters. Upwards of 50 percent of Air Force sustainment parts originate in the grey market.
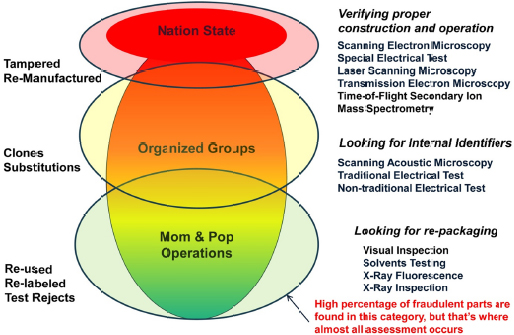
Pertaining to the issues raised in the NSWC presentation, there is inherent risk in looking for counterfeits due to false positive test results that have been observed in some test methods. Some participants noted that variations in chip measurements are criteria for binning of chips per performance measured (an accepted practice). However, these participants noted that measuring these variations is not a criteria for detection of counterfeits, making detection of real counterfeits difficult. The speaker from NSWC cited other methods that are more reliable indicators of counterfeits, such as principal component analysis and vector impedance measurements (see Figure 2-2).8 The participants from the Department of Energy’s Kansas City National Security Campus (KCNSC) stated that Sandia National Laboratories performs all of the testing for Nuclear Enterprise Assurance. One participant stated that establishing the trustworthiness of field-programmable gate arrays (FPGAs) presents multiple concerns, including the following: (1) threats due to malicious insertion, (2) vulnerabilities in programming, (3) complexity in detection methods, and (4) prominence of counterfeits. Another participant commented that a lot of the verification and evaluation tools used for space systems are classified and asked, How can we share these with the broader community and industry? A participant replied that DoD is working on a classification guide for the JFAC for how to share information on vulnerabilities.
Counterfeit parts are easier to make and sell because they do not necessarily have to work in the system under all conditions, as did the original part. They could also contain circuitry that has malicious content that can be activated at some point in the future. The speaker from NSWC noted that, while there are a large number of physical investigative techniques, ranging from simple visual inspection through destructive analysis using scanning electron microscopy, this is a slow and expensive process because it requires having knowledge of the intended design, the use of “golden units” for comparison, and extensive training. Having knowledge of the origin of parts is preferred because it provides legitimacy to the claim of authenticity. Program managers can avoid purchasing parts from after-market suppliers and distributors, however, with system lifetime buys of mission-critical parts at the outset of a program, which enables procurement from the original component manufacturers (OEMs) during production of those parts.
Many workshop participants were encouraged by the innovative and promising initiatives that the Defense Advanced Research Projects Agency (DARPA) either had under way or was starting to ensure the provenance of future integrated circuit parts. For example, the Supply Chain Hardware Integrity for Electronics Defense (SHIELD) program (a taggant) is intended to impose a cost and time asymmetry on the adversary.9 The taggant is embedded in the package material of the integrated circuit. These will work—as long as they are affixed to legitimate hardware—and are cost effective, but they do not solve the software side of the problem. Software integrity is a more immediate, and probably larger, problem
______________________
8Impedance is the effective resistance of an electric circuit or component to alternating current, arising from the combined effects of ohmic resistance and reactance (Oxford Dictionaries, http://www.oxforddictionaries.com/us/definition/american_english/impedance, accessed July 7, 2016).
9 A taggant is a unique signature found in an electronic component similar to strips found in currency notes to deter counterfeiters. For additional information on different forms of taggants, see Microtrace, “What is Taggant?,” http://www.microtracesolutions.com/taggant-technologies/, accessed June 27, 2016.
with weapons systems maintenance than the replacement of obsolete parts. The speaker from DARPA noted that technological solutions to ensure unchanged genuine parts and software are very possible and have the advantage of lower cost and significantly less supply-side disruption compared to bureaucratic policy solutions. In addition, DARPA noted that R&D costs are relatively inexpensive compared to added bureaucracy, and technological solutions are far easier and faster to implement. A key requirement of the DARPA SHIELD program is adoption of this taggant technique by the broader commercial industry. This is a necessary requirement to reach the cost targets and ultimate integration of this technology into the integrated circuit supply chain. Finally, one participant noted that software or hybrid software/hardware design features could help with making sure malware is not inserted in parts that are manufactured totally, or in part, in untrusted fabrication facilities; these same techniques could possibly help in the detection of clone or counterfeit parts. This “dual phenomenology” approach would make it more difficult to defeat techniques to improve trust in the supply chain.10
______________________
10 Although not specifically detailed during the workshop, the following related concepts were mentioned by the participant: (1) Released firmware and software can be checked for authenticity by cryptographic methods, such as “hash” verification, which would expose any unauthorized changes to the operational code. (2) The technique described above, coupled with on-board hardware logic that would be added, would work in tandem to monitor (each other’s) configuration; thus, if either the hardware, software, or firmware were modified, the combined verification check would fail. (3) Counterfeit parts would be exposed since they would not have access to, the pedigree of, or the capability to reproduce these functions.
CURRENT GOVERNMENT ACQUISITION CHALLENGES
One participant noted that the acquisition challenges for semiconductor technology can be separated into two divergent classes: (1) Class A, the acquisition of “bleeding edge” silicon technology and designs during its generation, literally at the limits of first-of-a-generation commercial availability and (2) Class B, acquisition of technology typically 3 to 4 generations behind the leading edge, such that the capital costs of obtaining such a fabricator would be a small fraction that of its original value. With these two options in consideration, this participant suggested evaluating the scenarios highlighted in Box 2-1.
A second challenge related to current acquisition processes for acquiring secure and reliable microelectronic components are relationships between government and industry program offices. One participant at the start of the workshop posed the following questions: How do we include and address rolling standards, metrics, and policies or processes, and How can any solutions be incorporated in Air Force acquisition? It was noted by some participants that the government does not necessarily know how to communicate SCRM requirements to industry, especially intelligence data on threats. A senior government leader at the workshop admitted that knowledge of SCRM requirements in government program offices is lacking and that there is a need for an integrated SCRM plan. An industry participant at the workshop strongly believed that discussions between government and industry need to occur before a contract starts and that it is critical to have engineers involved in the decision process, especially because the number of security-relevant SCRM requirements has greatly increased. (Getting these requirements into requests for proposals (RFPs) is critical.)
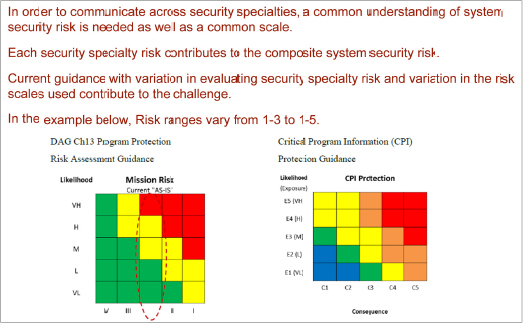
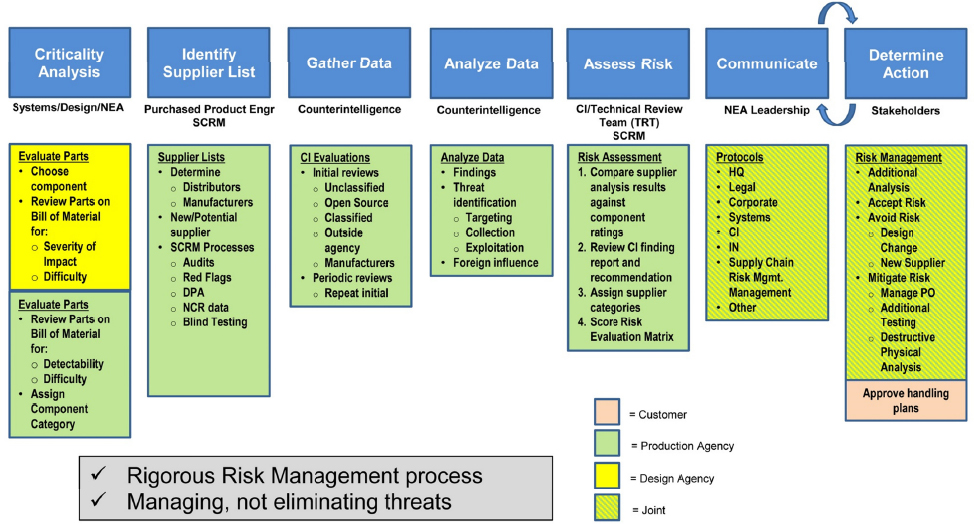
A participant noted that, traditionally, SCRM experts have come up through security fields, not engineering fields, and that the current thrust now is to push SCRM into systems engineering fields and acquisition fields. Another participant stated that the people who are writing the policies and acquisition RFPs also do not have these backgrounds. An industry representative stated that industry cannot do anything unless SCRM requirements are explicit in the contract—for example, common metrics for trust that are already being used by the anti-tamper community (see Figure 2-3).
One speaker on the last day of the workshop noted that, up until the 1990s, military microprocessor capabilities were superior to commercial products and that commercial products lifetimes have since been reduced dramatically. He stated that, once the trend to shorter lifetimes could begin to be observed, the government should have shifted the acquisition process to match the time-to-market shift to COTS products that were being used. A participant then posed a question, What evidence do you see of potential reforms to the acquisition system? The speaker replied that there has been some effort with respect to information systems; with respect to highly specialized defense systems, it is more difficult. A potential area to address a lot of the problems is reform of the acquisition system; although, as noted by another participant, it takes years to fight acquisition bureaucracy and to implement new practices.
A participant noted that policy and processes are needed by the acquisition workforce to ensure that contracts, parts procurement, and methods are put into practice to detect and prevent corrupted components and vulnerabilities from entering the systems’ life cycle—and one of the biggest problems is lax enforcement by government program offices of existing policies. The participant went on to specify that the acquisition process and workforce need to be more disciplined in performing program protection to assure system trustworthiness. This rigor needs to be applied to parts procurement guidelines, contracts (RFPs, statements of work, statements of objectives), design, and test. Finally, the participant stated that legacy systems and modernization programs are susceptible to bypassing recent program protection revisions to avoid extensive rework (i.e., cost) in requirements, documentation, and contracting efforts. This leads to perpetuating the fielding of vulnerable systems (which correspondingly have long operational life cycles).
Finally, another participant noted that there is far too much diversity in the rules for how DoD controls the acquisition and disposition of semiconductors and associated electronic assets. For example, in many, if not most, common systems in DoD usage today, there are system elements, such as FPGAs and graphic processing units (GPUs), that can be re-purposed after the fact. Similarly, analog circuitry has similar tuning capabilities. A critical aspect in both validating a system’s correct function, as well as maintaining it over time, is the quality and trust of one’s test equipment. This participant believed that it is important in any formal assessment of component acquisition that one include considerations as to the trust associated with the test equipment employed over the life of a given system and its components.
OPTIONS FOR POSSIBLE BUSINESS MODELS WITHIN THE NATIONAL SECURITY COMPLEX
At a strategic level, OSD explained the department’s planned long-term investment strategy for trusted microelectronics. The parallel components on this strategy include the following: (1) DoD identifying a commercial supplier of photomasks and building a trusted strategy to procure these; (2) transferring National Security Agency (NSA) TAPO roles and responsibilities to DMEA; (3) improving DoD microelectronics
evaluation (test and validation) capabilities; and (4) developing and demonstrating alternative approaches to the trusted foundry model.11 One participant noted that moving from a trusted hardware model to a trusted software model, which is where the department appears to be heading, is troubling—specifically, software can be made more assured, but not necessarily trusted.
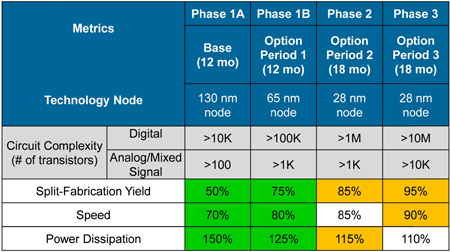
The concept of split manufacturing was raised by multiple speakers as an alternative business model to the current approach by DoD (see Figures 2-4 and 2-5). Split manufacturing involves doing the initial processing steps (front end of line, or FEOL) at one foundry and finishing the fabrication at another foundry (back end of line, or BEOL). One advantage of this approach is that a higher degree of security can be obtained by doing the split earlier in the process of manufacture. The chief engineer from SMC noted that split fabrication is being reviewed by SMC as a possible alternative to loss of the current trusted foundry model.
Another possible business model for acquiring secure and reliable microelectronic components is the approach taken by the KCNSC under the Department of Energy, as summarized in Figure 2-6. Unlike the many weapon systems and technologies that DoD is responsible for, the KCNSC is responsible for acquiring and inserting ASICs in nuclear weapon systems only. In a telling remark from the speaker from KCNSC, KCNSC has since borrowed heavily from DoDI 5200.44 while implementing a formal process for SCRM. A question that was asked by one of the participants, which went unanswered, is what DoD can learn from National Nuclear Safety Administration’s (NNSA’s) approach that is not cost-prohibitive.

______________________
11 Kristen Baldwin, Office of the Secretary of Defense, “Long-term Strategy for DoD Trusted Foundry Needs,” presentation to the workshop on March 16, 2016.
In a similar fashion, this question was also asked with regard to the NSA, the founder of the original TAPO program. The NSA established the TAPO program in 2004 to provide trusted access to components used in their systems rather than recapitalize their captive integrated circuit fabrication facility they operated at that time. The NSA is no longer involved in the TAPO program, having recently turned over the management role to DMEA. The question asked was, What is NSA’s current plan to ensure trusted microelectronics get used in their systems? A representative from OSD remarked that they plan to rely on their test and verification skills to validate the trust of their microelectronic components.
Other approaches for managing security and reliability risks include the following: (1) shortening the acquisition cycles, (2) aggregating microelectronics business, (3) planning for microelectronics technological change, (4) adopting commercial and industrial practices for security and reliability, (5) assessing security and reliability problems and then developing resiliency for missions and systems, and (6) developing a technological offset.12,13 In response, a participant noted that it would be difficult to aggregate U.S. microelectronics business because of the different needs of various government agencies, although one of the main functions of TAPO (beyond ensuring access to trusted state-of-the-art parts) is aggregation of DoD’s demand for trusted microelectronic components.
In the wrap-up discussions on the last day of the workshop, one participant noted that assured U.S. access to trusted microelectronic components is a pernicious problem. This participant stated that a new trusted foundry is not necessarily the answer and that there are two different, but complementary, issues—access to leading edge technology (foundries) and the issue of obsolete, counterfeit, or mimic parts. A second participant noted that the solution is not a dedicated government-run foundry and that the DoD requires many different types of electronic parts and a single foundry cannot support all these different needs (as noted above). This second participant also believed that the DARPA approach of figuring out how to build “trusted”
______________________
12 Brian Cohen, Institute for Defense Analyses, “Obtaining Assured Electronics in a Global Commercial Marketplace,” presentation to the workshop on March 18, 2016.
13 A technological offset is a means of addressing a military disadvantage against either a potential or real adversary. For example, the United States developed tens of thousands of nuclear weapons during the height of the Cold War to offset the numerical advantage the Soviet and Chinese military forces enjoyed relative to Western forces.
integrated circuits in an untrusted supply chain is the right one. The proposed DoD strategy of seeking to extend the existing contract with GlobalFoundries in the near term to buy time, while, in parallel, making investments in both test, evaluation, and validation capabilities and in alternative approaches to the trusted foundry model (e.g., DARPA’s approach) is a good one. Finally, as evidenced by the presentations from DARPA, the Intelligence Advanced Research Projects Activity, and industry, multiple new architectures and technologies exist that may provide solutions.












