2
Understanding Violent Extremism
Many participants proposed that to better understand violent extremism, it is necessary to examine the shared characteristics of individuals who exhibit violent extremism. In this chapter, speakers discuss the origins of violent extremism and the challenges surrounding collecting empirical data about violent extremists. Several speakers noted that the progression to
radicalization is complex, often connected to personal as well as societal grievances, and that there is no single profile for a violent extremist. However, an expectation remains that if some shared characteristics of violent extremists can be identified, more preemptive steps can be taken to protect those individuals from progressing any further.
RADICALIZATION AND VIOLENT EXTREMISM: CHARACTERISTICS AND EMPIRICAL DATA
The Empirically Assessing Domestic Radicalization (EADR) Project
Michael Jensen, senior researcher at START, University of Maryland, provided a data-informed look at extremism in the United States. He emphasized that the best CVE policies should reflect an empirical understanding of the causes of radicalization and its consequences, but that representative, systematic data on those phenomena are currently lacking. This gap led to the development of the Empirical Assessment of Domestic Radicalization (EADR) project, a multiple-methods research project housed at START (see Box 2-1). Its quantitative cross-sectional dataset (Profiles of Individual Radicalization in the United States or PIRUS) contains information on a random representative sample of 1,473 individuals who radicalized, to either nonviolent extremist behaviors or violent extremist behaviors, in the United States. The qualitative component of the project is drawn from the life-course narratives of 110 individuals who became radicalized in the United States.
Jensen outlined the three objectives of the EADR project. First, it is designed to provide policy makers, CVE practitioners, intelligence analysts, law enforcement officers, researchers, and the public with representative data on extremism in the United States, including information on key radicalization mechanisms and processes. Second, it aims to provide analyses using rigorous methods that help to better understand how radicalization in the United States works, how it has changed over time, and how it may evolve in the future. Its third objective is to produce empirically derived policy recommendations for counterterrorism and CVE.
Jensen discussed five findings from the EADR project with relevance to CVE.
Extremism in the United States Spans Diverse Ideologies
Extremism in the United States is ideologically diverse, encompassing the far right (e.g., antigovernment, white supremacists), the far left (e.g., social justice, animal rights, environmental protection), single-issue ideolo-
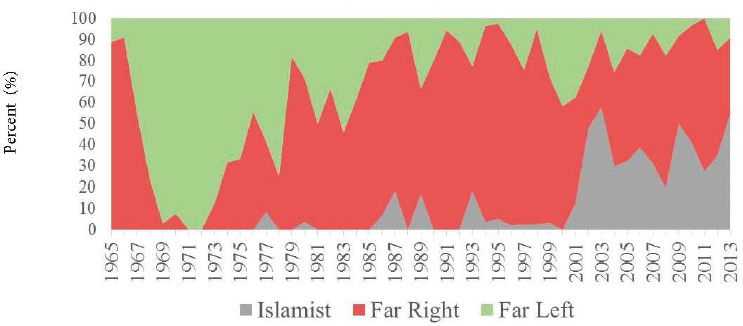
gies, and Islamist. Figure 2-1 represents exposure date by ideology over time between 1965 and 2013 in the United States.
Jensen explained that in the mid-1970s, there was a substantial upturn in the activity of extremists ascribing to far-right ideologies, and that group remains the majority in the present day. After the events of 9/11, there was a spike in the activity of Islamist extremists; however, the group still remains proportionally much smaller than far-right extremists. He noted that the ideological distribution in the PIRUS database also spans the spectrum of extremism:
- 43 percent far right
- 21 percent far left
- 21 percent single issue
- 15 percent Islamist
SOURCE: Jensen presentation, An Empirical Assessment of Domestic Radicalization, September 7, 2016.
Jensen contended that the problem faced today, despite what is portrayed in national media, is much broader than the issue of Islamist extremists, asserting: “So far our efforts in the CVE and counterterrorism realm have been disproportionately focused on one end of the spectrum, and there is a lot more going on that we need to pay attention to.” Warner Anderson, assistant professor in military and emergency medicine at the Uniformed Services University of the Health Sciences remarked that from a public health perspective, violent extremism should be considered in context of a national epidemic of violence. However, he expressed concern that interventions in the CVE space are drifting from where the evidence base recognizes the threat, which is in far-right wing and white supremacists’ groups, and into terrorism motivated by Islamic ideology.
Important Differences Across Ideologies
Jensen reported that there are important differences within and across the ideological spectrum that should inform the design of CVE programs and policies. For example, analysis of the database reveals broad variation along multiple demographic variables. Individuals on the far right (with an average age 38 years) are much older than individuals on the far left (28 years) as well as Islamists (30 years). Thus, intervention programs tailored toward young people may not be appropriate in all situations. Gender distribution in the database is also diverse. One-quarter of active individuals on the far left are women, while the percentages of women active on the far right and among Islamists are 5 percent and 4 percent, respectively.
Counter to the assumption that most individuals motivated to commit violent extremism come from economically disadvantaged backgrounds and have little education, Jensen reported that most individuals across ideologies in the database have at least some college experience (far right, 45 percent; far left, 75 percent; Islamists, 59 percent). Nearly 30 percent of those motivated by far-right ideology have military experience, compared with 11 percent of far-left cases and 10 percent of Islamist cases. Engagement in previous criminal activity prior to radicalizing is also common among all three groups, although it is more common on the far right, with 63 percent of cases having engaged in criminal behaviors before they adopted extreme views (compared with 51 percent of far-left cases and 40 percent of Islamist cases).
Jensen explained that the variable of radicalization duration captures the length of time from first evidence of exposure to radical beliefs to the time that an individual engages in extremist behaviors. He reported that individuals with far-right ideologies tend to have a longer window of 5 or more years, versus 1–5 years for both far-left and Islamist cases (both of the latter groups generally tend to skew closer to the 1-year window). Competition between extremist groups or cells is quite common on the far right, occurring in 50 percent of cases compared with 35 percent on the far left and 14 percent among Islamists.
Current Extremists Progression: Alone and Quick to Radicalize
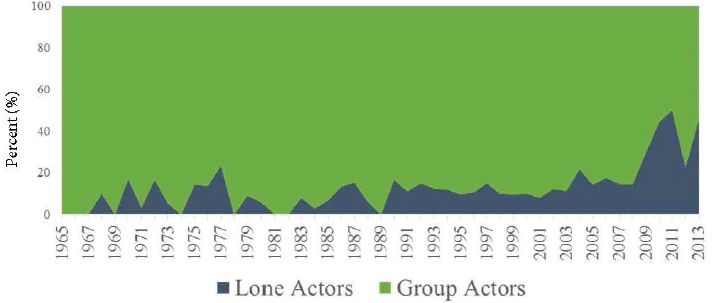
Jensen suggested that because of increased online activity, extremists are acting alone more frequently and becoming radicalized more quickly than they did in the past. He defined lone actors as individuals who are not affiliated with a formal extremist group or small cell; at most they might operate with just one other person. He reported that analysis of lone-actor behavior over time in the database reveals a sharp increase since about 2008. However, he emphasized that the label lone actor may be a misnomer. Although lone actors may be acting alone operationally, most are deeply embedded in strong social networks and thus are not alone in a practical sense. Online networks can mobilize behavior in a very real and expedited way, he explained, and true lone actors—those who have no interaction with anyone else with extreme views—are the outliers, not the norm (see Figure 2-2).
The analysis also evaluated radicalization duration and online activity for the subset of individuals who attempted to (or did) leave the United States to join foreign conflicts. Jensen reported a steep increase in those individuals’ use of social media and the Internet, coupled with a drop-off in radicalization duration from an average of around 16 months in the early 2000s to around 9 months by 2014. He suggested that windows of oppor-
SOURCE: Jensen presentation, An Empirical Assessment of Domestic Radicalization, September 7, 2016.
tunity for intervention do exist, but they are shrinking, so acting quickly to intervene is crucial.
Shared Characteristics of Individuals Who Commit Violent Extremism
Jensen explained that most individuals who hold extreme views do not engage in violence, but those who do often share a set of key characteristics. He reported that some of START’s data has generated a set of significant differences and strong predictors of the likelihood of engaging in an act of political violence. One of the strongest predictors, regardless of model and using different controls, was engagement in criminal activity prior to radicalizing, especially a history of juvenile criminal behaviors. Individuals with a criminal history were 1.5 times more likely to engage in violence after radicalizing than those without a history of criminal activity. Furthermore, individuals that adhered to far right or Islamist ideologies were 2–3 times more likely to be violent or attempt violence than those on the far left, or those that are motivated by idiosyncratic single issues. Individuals who were embedded in radical social networks were 2.5 times more likely to engage in politically violent acts based on database analysis.
Jensen added that individuals in the database with either a clinical diagnosis of mental illness or whose friends or family members believed them to suffer from mental illness were twice as likely to engage in political violence. Conversely, individuals in the database who had a stable employment history were two times less likely to engage in violence, which he flagged as a promising development. However, he noted that the relationship between
mental illness and violence is complex and confounded by multiple factors (such as substance abuse or trauma), so further research is needed to identify the primary drivers of violent behavior.
Radicalization Is Complex
Finally, Jensen emphasized that the pathway to radicalization is incredibly complex and unique: “There is no profile of an extremist; there is no set of three or five warning indicators that we can give to a law enforcement officer or to a school administrator.” To help disentangle some of those complexities, Jensen described an in-depth analysis of 56 people who radicalized in the United States. The analysis found that certain conditions seem to be particularly important or even necessary in the CVE space, said Jensen. First, almost every individual had a sense of community victimization, feeling deeply that they were members of communities being targeted and victimized. Secondly, most individuals underwent a fundamental radical shift in their cognitive frames: the way they perceive the world, the way they process information (especially disconfirming evidence), and how they process things that challenge their views. Furthermore, he suggested that many pathways to radicalization begin with emotional vulnerabilities that are often brought on by traumatic experience (e.g., the death of a loved one, childhood abuse). Because of the traumatizing event or events, the individual develops a need for identity that is fulfilled by extremist narratives or causes. Also very common were cognitive biases (groupthink, in-group/out-group bias, and perceptions of threat), especially among individuals embedded in radical social networks. Jensen observed that such isolated networks may serve as a breeding ground for further engraining those cognitive biases and making them increasingly difficult to overcome.
THE HYPOTHESIZED ROOT CAUSES OF VIOLENT EXTREMISM
Transforming Grievances into Violent Action
Multiple panelists explored the constellation of personal and societal factors that can drive an individual’s progression from personal grievances, to radicalization, and eventually to violent extremism.
Michael Downing, deputy chief of the Counter-Terrorism and Special Operations Bureau at the Los Angeles Police Department (LAPD), commented that from the law enforcement perspective, there is no “silver bullet” or profile of someone who will perpetrate violent extremism. However, he suggested that there are certain observable consistencies, including lack of identity, vulnerabilities, lack of attachment, and lack of societal inclusion. From the public health perspective, Arthur pointed to similar fac-
tors at play—oppression, discrimination, and disconnection—that seem to contribute to individuals around the world being radicalized toward other violent groups, such as gangs and cartels.
Stewart cited a study that examined the individual “pull” factors that increase susceptibility to recruitment to violent extremist groups, noting that the motivations tend to be extremely personal in nature: experiencing or witnessing torture, death of a relative or friend at the hands of the security forces or a foreign power, unfair trials, loss of property, humiliation, or even something as simple as refusal of a personal loan. She noted that these “pull” factors were connected to broad systemic forces: lack of socioeconomic opportunities, marginalization and discrimination, poor governance, violations of human rights and the rule of law, prolonged and unresolved conflicts, and radicalization in prisons.
Mark Stainbrook, assistant chief of the San Diego Harbor Police and senior fellow at the Potomac Institute, presented a list of 10 motivating factors for joining a gang or a terrorist group, derived from his academic research as well as his personal experience with individuals involved. He noted that, in most cases, no single element is the sole factor. Rather, it is typically the sum of several motivators that tips the scale. Nine of the motivators Stainbrook presented were shared between gang members and members of terrorist groups: camaraderie, identity, family or social network, family disruption, excitement or thrill, social pressure, protection, racism and discrimination, and satisfying material needs. He explained that the only motivating factor that seems exclusive to people who join terrorist groups, as opposed to those who join gangs, is ideological and/or religious justification. He stated,
The main difference is someone who has radicalized can now point to the ideological and/or religious justification for their participation in the group as it serves their vision of the greater good. This is extremely dangerous as it can justify high levels of violence, due to moral and theological imperatives.
Citing work by Hafez and Mullins (2015), Stainbrook called for a shift from thinking about radicalization as a linear process to thinking of it as a set of puzzle pieces that, taken together, provide a strong foundation for motivating homegrown violent extremism (see Figure 2-3).
Gender Violence and Childhood Trauma
Stewart’s group, Futures Without Violence, is a national nonprofit organization dedicated to preventing and ending violence against women, children, and youth, and it seeks to analyze violence through public health and social justice lenses. The group’s work around CVE arose out of its

SOURCES: Stainbrook presentation, September 7, 2016; radicalization model based on Hafez and Mullins, 2015.
efforts to address violence against women and girls internationally, which exposed linkages between violent extremism globally and its relationship to gender.1
Stewart cited work by Valerie Hudson (2012) that examined data from more than 100 countries, finding that after controlling all other factors (e.g., religiosity and poverty), the presence of gender-based violence was the best predictor of state instability. She suggested that domestic, gendered violence may be what attracts terrorists toward the Islamic State, because the Islamic State of Iraq and the Levant’s (ISIL’s)2 practices include sexual slavery and a fidelity to traditional gender norms, which can be used as
___________________
1 April 2016 Open Square Roundtable on CVE and Gender, https://www.futureswithoutviolence.org (accessed November 8, 2016).
2 To be consistent with the Director of National Intelligence all references to Daesh or ISIS have been changed to ISIL.
recruiting tools for young men, with reassertion of male control as a compelling narrative.3
She explained that domestic violence can be a red flag for violent extremism because it demonstrates that the person believes it is acceptable to use violence to exert control through instilling fear and is willing to do so. She emphasized this point using the examples of recent mass killers who had histories of domestic violence and grievances against women. Omar Mateen, for example, carried out the 2016 mass shooting at a gay nightclub in Orlando, Florida, killing 49 people and wounding 53. He had an extensive history of domestic violence, or as Stewart characterized it, domestic terrorism: taking his wife’s paychecks from her; confining her to the house; and beating her regularly for not living up to the standards of Islam. Mohamed Lahouaiej Bouhlel (who killed 80 people in Nice, France, in 2016) and Robert Lewis Dear (Colorado Planned Parenthood shooter in 2015) had similar histories of domestic violence and sexual assault.
Stewart reported that an analysis of Federal Bureau of Investigation (FBI) data on mass shootings from 2009 to 2015 found that in the majority of mass shootings, defined as killing four or more people, there were cases of domestic violence present in some form.4 While there is no proven explanation for this correlation, she suggested that there are striking parallels between the factors that drive the two phenomena: power and control through fear and violence.
Growing up as a witness to domestic violence is a major contributor to child trauma, which in turn is a major contributor to youth and adult violence, according to Stewart. She outlined some of the consistent drivers of violent behavior identified in the document on youth violence prevention in the United States released by the U.S. Centers for Disease Control and Prevention (CDC).5 On the individual level, she highlighted prior exposure to violence, in particular, as contributing to impulsiveness, substance abuse, and perpetration of violence, which in turn feeds the cycle of violence.
According to the Adverse Childhood Experiences Study on toxic stress,6 she explained, exposure to violence in childhood affects the architecture of the brain and body. The ability to react to life stressors becomes compromised, such that perceptions of threat and danger are heightened.
___________________
3 Sexual violence perpetrated against boys and young men is a taboo that also needs to be addressed, according to Stewart.
4 Such as an abuser who kills his wife or girlfriend, other family members, and/or neighbors or law enforcement officials attempting to help.
5 This document is available at http://www.cdc.gov/violenceprevention/youthviolence/opportunities-for-action.html (accessed November 8, 2016).
6 Through the work of Dr. Jack Shonkoff (director of the Center on the Developing Child at Harvard University) and many others. Data and resources available at http://www.cdc.gov/violenceprevention/acestudy/index.html (accessed November 8, 2016).
A person’s response to such stressors, whether it is walking away or drawing a gun, is also partially shaped by childhood exposures. From a policy standpoint, she suggested that because a person’s biology actually changes based on exposures to violence and trauma in childhood, more attention needs to be paid to childhood experiences of abuse and trauma, and more resources devoted to developing healthy coping.
Edward Pieczenik, licensed clinical social worker at the University of California, Davis, Extension Division, referred to additional research establishing that there are brain changes caused by exposure to violence. A type of hyperarousal can cause a person to cognitively misperceive the world, particularly in the presence of charismatic authority figures promoting propaganda. He suggested that there might be a direct—although not causal—association between such brain changes and violent or extremist behavior. He posited that emotional regulation and executive function deficits might make certain people more vulnerable in this regard.
Stewart reported that through life history interviews with violent white supremacist groups, the START research team found the following:
- Forty-five percent reported being the victim of childhood physical abuse.
- Twenty-one percent reported being the victim of childhood sexual abuse.
- Fifty-seven percent reported experiencing mental problems, as diagnosed by a medical practitioner, either preceding or during their extremist involvement.
- Seventy-two percent reported having problems with alcohol and/or illegal drugs.
While high levels of exposure to trauma in childhood may indeed be related to committing violence later in life, Heidi Ellis, director of the Refugee Trauma and Resilience Center and associate professor of psychology at Harvard Medical School, noted that there are many other potentially significant factors that contribute to the overall burden of adversity that some children face. In her experience with refugee youth and families, Ellis has observed a wide range of developmental trajectories among children who have experienced similar types of adversities. Some are resilient and emerge with good mental health and high levels of community engagement. Others struggle with mental illness, or become involved with gangs, and a small number engage in violent extremism or travel abroad to join foreign terrorist organizations. Her work within the refugee resettlement community focuses on finding the right levers to pull to help nudge someone toward a healthier trajectory. A common thread that has emerged is the importance
of social bonds. Feeling connected and a sense of belonging to one’s country of resettlement helps to mitigate violent extremist views.
Bob Griss, director of health care policy at the Institute of Social Medicine and Community Health, suggested that technology has made it easier for populations not to assimilate, particularly among refugee and immigrant communities who would have been less isolated and more connected to their physical communities in the past. Technology has made it possible to be part of any virtual community and adopt any value system, he noted, which can be problematic from a standard public health or community perspective. Yolanda Rondon, attorney with the American-Arab Anti-Discrimination Committee, pointed out that embracing one’s cultural heritage does not make one more or less prone to assimilating into American society, which is founded on a diversity of cultures. Rebecca Skellett, Strong Cities Network manager at the Institute for Strategic Dialogue, noted that given the increasing number of individuals who engage in extremist groups online, issues around policing and restriction of the Internet will be subject to debate among CVE practitioners, governments, and Internet service providers.












