Discussion of Selected Topics from the Restricted Report
USAF CAPABILITIES REQUIRING SECURE AND RELIABLE MICROELECTRONICS
The U.S. Air Force (USAF) focuses on five principal missions that are dependent on access to secure and reliable microelectronic components.
- Air and space superiority;
- Intelligence, surveillance, and reconnaissance (ISR);
- Mobility and lift;
- Global strike; and
- Command and control (C2).
 Reliable means microelectronics parts operate as designed in the operational environment.
Reliable means microelectronics parts operate as designed in the operational environment. Trusted means confidence that there is no malicious content.
Trusted means confidence that there is no malicious content. Assured means microelectronics parts have verified function with no extra functions.
Assured means microelectronics parts have verified function with no extra functions. Protected means microelectronics parts can prevent unauthorized functions as part of their design.
Protected means microelectronics parts can prevent unauthorized functions as part of their design.
It is not overstating the obvious that microelectronics are critical to the success of all five missions. Current USAF weapon systems utilize tens-of-thousands of different microelectronic part types (analog, mixed-signal, digital, radio frequency [RF], optical, etc.) fabricated using hundreds of different fabrication and packaging facilities
scattered across the globe.1 High-performance electronics are key to the USAF’s ability to deliver lethal effects at the time and location of need. This requires that weapon systems be designed not only to withstand the rigors of the battlefield but also to be able to perform the needed mission if subjected to electronic and/or cyberattack. Understanding both the operational environment and the inherent potential vulnerabilities introduced because of the global interconnectivity of the microelectronics supply chain is necessary to ensure mission success.
It is the combination of improvements in targeting, geolocation, and navigation precision that enables our militaries to not only hit the target on the first attempt, but to hit in the right spot. Today, a B-2A bomber uses the Global Positioning System (GPS), intelligence imagery systems, Milstar communications systems, and the precision GPS guided joint direct attack munitions weapons to provide the destructive power of an entire air wing in World War II. And, it does so in all weather conditions. Electronics are a major contributor to the net increase of 50,000 in targets per sortie from World War II to Operation Iraqi Freedom.”2
THREATS TO THE SUPPLY CHAIN OF MICROELECTRONICS IN USAF WEAPON SYSTEMS
Microelectronics components used in USAF weapons are an obvious target for malicious acts, especially when they are readily identified in program protection plans (PPPs) and critical parts lists (CPLs) as components critical to military or intelligence mission success. Examples include custom application-specific integrated circuits (ASICs), programmable logic devices—for example, Field Programmable Gate Arrays (FPGAs), microprocessors, and flash memories; however, as the complexity of systems increase, even “noncritical” components in the critical path of a component can create system vulnerabilities and the opportunity for an undetected threat vector. The scale of this challenge cannot be overstated. Each microelectronic component may contain as many as a billion transistors posing a challenge for the inspection process that, even if it could be accomplished, would be difficult, tedious, and error-prone, with the likelihood of finding even one tainted transistor unlikely. In principle, an electronic device containing multiple integrated circuits (ICs) could be undermined by a handful of rogue transistors.
___________________
1 National Academies of Sciences, Engineering, and Medicine, 2016, Optimizing the Air Force Acquisition Strategy of Secure and Reliable Electronic Components: Proceedings of a Workshop, The National Academies Press, Washington, DC.
2 U.S. Department of Defense (DoD), 2016, Joint U.S. Defense Science Board UK Defence Scientific Advisory Council Task Force on Defense Critical Technologies, Office of the Under Secretary of Defense for Acquisition, Technology, and Logistics, Washington, DC, March, http://www.dtic.mil/dtic/tr/fulltext/u2/a446196.pdf.
This explains why ICs have become an increasingly attractive target to attackers.3 In 2007, researchers at the University of Illinois, Urbana-Champaign, proved the feasibility of maliciously modifying hardware logic. They developed two general-purpose methods for designing malicious processors and, using these methods, created hardware Trojans to “implement attacks that stole passwords, escalated privileges, and enabled automatic logins to computers containing the ICs.”4 The nature of the modifications required involved the addition of a “relative handful of logic gates” to an otherwise clean baseline IC. According to a 2013 article, “the login attack that granted the researcher complete access to the targeted computer required the addition of only 1,341 logic gates to that computer’s IC—0.08 percent of the total 1,787,958 logic gates used in the IC.”5 In larger processors containing billions of gates, such a relatively tiny number of additions would be cost prohibitive to detect.
Automated test equipment can test millions of transistors per second for certain types of manufacturing fidelity. However, the design of this equipment is currently limited to detecting just the deviations from a narrow set of specifications. Any anomalies that involve aspects of the component that are not covered by the verification test such as cyber or electronic warfare (EW) attacks will go undetected. Hardware attackers can exploit the complexity of modern ICs to insert Trojan circuits. They can then use the special or unanticipated functions or events introduced by these Trojan circuits at run time to trigger the malicious logic buried deep in the circuit. Inspections of suspected counterfeit ICs6 are more realistic and begin with an analysis of the packaging and paperwork. This is followed up with several levels of inspection of the IC itself. These inspections include checking the circuit’s physical dimensions against known-genuine examples, and ensuring surface markings are permanent and not added by a secondary actor. However, third-party purchasers of ICs are rarely provisioned with the proper equipment to detect malicious or fraudulent circuits and often not trained enough to use such equipment to perform the more complicated inspection protocols.7
The intelligence community traditionally focuses on the adversary, assessing the presence and likelihood of a threat to U.S. national security. The defense community focuses on protection of national security by securing U.S. weapon systems,
___________________
3 K.M. Goertzel, 2013, Integrated circuit security threats and hardware assurance countermeasures, Crosstalk: The Journal of Defense Software Engineering 26(6):33-38.
4 Ibid., p. 34.
5 Ibid.
6 Counterfeit microelectronics cover a spectrum from parts that have been re-marked to disguise parts differing from those offered by the original part manufacturer, to defective parts scrapped by the original manufacturer and then salvaged and resold, to devices that have been refurbished and sold as new products.
7 K.M. Goertzel, 2013, p. 34.
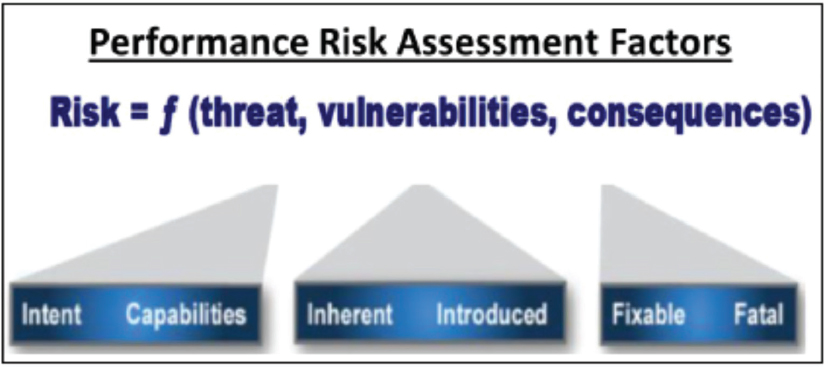
relying on the intelligence communities risk assessment to develop program protection and mitigation plans. A divergence in philosophies exists where the definitions of threat and vulnerability intersect. In the intelligence community, where protection of U.S. supply chains is concerned, the presence of a vulnerability does not necessarily introduce a threat, just the potential for one, just as the discovery of a threat may not indicate a high level of risk. This interpretation of risk is not widely understood within the Department of Defense (DoD). Figure 1 highlights how the IC defines risk as a function of threats, vulnerabilities, and consequences. For DoD systems, the program office must have an informed understanding of the threat as well as system vulnerabilities to fully understand risk.
The intelligence community can generate a comprehensive collection plan to identify threats to the weapon system only if the program office has accurately identified and prioritized vulnerabilities inherent to the programs under their responsibility. This relationship demands close integration of the defense and intelligence communities to synchronize the protection of U.S. supply chains.
SUPPLY CHAIN RISK MANAGEMENT POLICY
The defense community has several organizations focused on elements of supply chain risk management (SCRM), executing guidance through individual chains of command. In 2015, as a result of Section 937 of the National Defense Authorization Act (NDAA) for Fiscal Year 2014, Public Law 113-66, the DoD established the Joint Federated Assurance Center (JFAC), which reports to the Under Secretary of Defense for Research and Engineering (USDR&E). The role of the JFAC is to facilitate collaboration across science and technology (S&T), acquisition (ACQ), test
and evaluation (T&E), and sustainment efforts to ensure that software assurance (SwA) and hardware assurance (HwA) capabilities and investments were effectively planned, executed, and coordinated across the DoD. The charter of this organization is comprehensive—“the JFAC will develop, maintain, and offer software and hardware vulnerability detection, analysis, and remediation capabilities through a federation of internal, coordinated organizations and facilities from across the Military Departments, Defense Agencies, and other DoD organizations.” The JFAC:
- Supports program offices across the life cycle by identifying and facilitating access to department SwA and HwA expertise and capabilities, policies, guidance, requirements, best practices, contracting, training, and testing support;
- Ensures that requirements to innovate software vulnerability analysis, testing, and protecting tools are provided to inform DoD research and development (R&D) strategy development;
- Ensures that requirements to innovate hardware vulnerability analysis, testing, and protection tools are provided to inform DoD R&D strategy development; and
- Establishes and enables efficient and affordable acquisition and use of tools for SwA and HwA analysis and test.
Each Military Department is directed to support the JFAC by:
- Providing SwA and HwA capabilities and resources, and support for the JFAC and management construct;
- Assisting in the formulation of JFAC operational requirements;
- Developing R&D budget requirements in coordination with the JFAC;
- Nominating SwA and HwA capabilities and sustain inventory;
- Developing a communication plan to manage interactions between the JFAC support staff, members, and program offices; and
- Providing SwA and HwA capabilities to DoD programs and interact with program offices in accordance with each DoD components’ communication plan.
Furthermore, each service maintains a Damage Assessment Management Office (DAMO) that also reports to the USDR&E. Each DAMO is responsible for managing and tracking the review of potentially compromised defense information from a variety of sources. The DAMO is also critical to the integration efforts between the SCRM and intelligence communities during the maintenance and sustainment phase of the supply chain. The DAMO serves a key role as liaison to system pro-
gram managers, directly affecting protection efforts for fielded weapon systems.8 Program offices are key to the development of PPPs as well as the identification and dissemination of the information on critical technologies. Unfortunately, even with a centrally managed office like DAMO, or a collaboration organization like JFAC, coordination between the services and program protection has been a challenge. Special access program (SAP) restrictions and other classification issues are often roadblocks to interservice standardization of SCRM efforts. As an example, each service may view the same information, or technology, differently based on the weapon system it supports. In one case, although one USAF program may depend on a critical component for the survival of the weapon system and closely guards its program information, another program within the USAF may use the same technology for a system that is low risk, and therefore does not warrant the time and money required to conduct SCRM protection efforts. When this occurs, the efforts of one program may negate another program’s effort to protect supply chains and critical program information (CPI).
In an effort to assess and mitigate technical information losses, in 2016 the DoD established the Joint Acquisition Protection and Exploitation Cell (JAPEC) to address the critical gap in the integration of PPPs and threat reports supporting SCRM efforts. JAPEC’s draft guidance highlights the need to improve protection efforts early in the supply chain life cycle, particularly where there is a high likelihood of disclosing performance characteristics or manufacturing processes that are critical to defense efforts. Although threat reports should directly feed protection plans, many protection plans do not have a concurrent threat report. This report highlights the JAPEC as a best practice that the USAF might emulate as it develops a centralized Program Protection Office.
Recent assignment (ca. 2016) of SCRM concerns to the Office of the Assistant Secretary of the Air Force for Logistics and Product Support (SAF/AQD) have resulted in USAF working group efforts to address SCRM by USAF logistics organizations operating in the sustainment life cycle. Examples include the USAF SCRM Campaign Plan (Box 1), the new Supplier Assessment Working Group, and the USAF Supply Chain Risk Management Working Group, all headed by SAF/AQD. The USAF SCRM Campaign Plan in review includes 11 levels of effort (LOEs) that are aligned with NDAA Fiscal Year 2018, Section 807, of Public Law 115-91, summarized below. The effort is a multidisciplinary approach spanning numerous organizations within the USAF and is illustrative of the level of coordination that is required to effectively implement a SCRM strategy for the sustainment
___________________
8 DoD, 2015, “Guidance to Stakeholders for Implementing Defense Federal Acquisition Regulation Supplement Clause 252.204-7012 (Safeguarding Unclassified Controlled Technical Information) Version 2.0,” Office of the Deputy Assistant Secretary of Defense for Systems Engineering, August, https://www.acq.osd.mil/se/docs/DFARS-guide.pdf.
community—AFOSI,9 SAF/AA,10 SAF/AQ,11 SAF/CIO/A6,12 SAF/IA,13 AF/A2,14 AF/A4,15 AFMC,16 AFSPC,17 and other Major Commands (MAJCOMs). This effort is another example of a best practice already being implemented within the USAF acquisition community.
SUPPLY CHAIN VULNERABILITIES ARE A U.S. ACHILLES HEEL
Software and system developers take the quality of hardware for granted, never doubting that the logic of the integrated circuits (ICs) on which software runs and critical application data are stored will consistently function in a dependable (correct, predictable) and trustworthy (nonmalicious, nonexploitable) manner. This overconfidence in the security of the hardware supply chain is an Achilles heel. See Box 2.
___________________
9 Air Force Office of Special Investigations.
10 Administrative Assistant to the Secretary of the Air Force.
11 Office of the Assistant Secretary of the Air Force for Acquisition, Technology, and Logistics.
12 Office of the Air Force Chief Information Dominance and Chief Information Officer.
13 Office of the Deputy Under Secretary of the Air Force for International Affairs.
14 Office of the Air Force Deputy Chief of Staff for Intelligence, Surveillance, Reconnaissance, and Cyber Effects Operations.
15 Office of the Air Force Deputy Chief of Staff for Logistics, Engineering, and Force Protection.
16 Air Force Materiel Command.
17 Air Force Space Command.
On October 4, 2018, Bloomberg News claimed that Chinese operatives from a unit of the People’s Liberation Army inserted malicious microchips that allowed the malicious actors to create a secret opening into any network that included the affected machines. The article claimed that the hardware of numerous U.S. companies was affected, thereby potentially compromising the U.S. technology supply chain.18 Although the information has not been corroborated to date,19 and has been denied by those supposedly affected, the potential threat and its implications for the assured lethality of weapon systems should provide a wake-up call to the USAF leadership.20
Incorporation of counterfeit electronic components from untrustworthy sources for use in U.S. military equipment,21 the potential for sophisticated cyberattacks,22 and state-sponsored data exfiltration of U.S. military contractor networks23 publicly exacerbate the vulnerabilities within the USAF’s microelectronic supply chain. As an example, the owner of an Orange County-based seller of electronic components was arrested in May 2018 and charged with allegedly re-marking and selling old devices with altered date codes to deceive customers and end users into thinking the integrated circuits were new devices. The filing described how the owner acquired old, used, and/or discarded ICs from Chinese suppliers that had been repainted and re-marked with counterfeit logos. The devices were further re-marked with altered date codes, lot codes, or countries of origin to deceive customers and end users into thinking that the ICs were new. The counterfeit electronics were sold as new parts by manufactures such as Xilinx, Analog Devices, and Intel. One of the counts related to eight ICs that he (the owner) allegedly knew were counterfeit military goods, “the use, malfunction, and failure of which were likely to cause serious bodily injury and death, the disclosure of classified information, impairment of combat operations, and other significant harm
___________________
18Bloomberg, 2018, “The Big Hack: How China Used a Tiny Chip to Infiltrate U.S. Companies,” October ÂÂ4, https://www.bloomberg.com/news/features/2018-10-04/the-big-hack-how-china-used-a-tiny-chip-to-infiltrate-america-s-top-companies.
19CNBC, 2018, “FBI Director on Whether Apple and Amazon Servers Had Chinese Spy Chips: “Be Careful What You Read,” October 10, https://www.cnbc.com/2018/10/10/fbi-director-wray-on-super-micro-servers-be-careful-what-you-read.html.
20ExtremeTech, 2018, “Apple Denies Bloomberg Chinese Hacking Story to Congress,” October 8, https://www.extremetech.com/computing/278377-apple-denies-bloomberg-chinese-hacking-story-to-congress.
21 U.S. Department of Justice, 2015, “Massachusetts Man Sentenced to 37 Months in Prison for Trafficking Counterfeit Military Goods,” October 6, https://www.justice.gov/opa/pr/massachusetts-man-sentenced-37-months-prison-trafficking-counterfeit-military-goods-0.
22 DoD, 2017, Report of the Defense Science Board Task Force on Cyber Supply Chain, Office of the Under Secretary of Defense for Acquisition, Technology, and Logistics, Washington, DC, February.
23 H. Cooper, 2018, “Chinese Hackers Steal Unclassified Data from Navy Contractor,” New York Times, June 8, https://www.nytimes.com/2018/06/08/us/politics/china-hack-navy-contractor-.html.
to a combat operation, a member of the Armed Forces, and to national security.”24Table 1 provides a nonexhaustive list of reports that have documented counterfeits discovered in the DoD supply chain.
However, it is important that the USAF not limit its focus to just threats introduced through the deliberate insertion of vulnerabilities at some point in the supply chain. One case in point: nothing more than poor security practice resulted in malware negatively affecting the assembly lines at Taiwan Semiconductor Manufacturing Company (TSMC), causing significant delay to their system-on-a-chip (SoC)25 production. Although this primarily affected private companies, it serves as a cautionary warning to the USAF about the inherent vulnerability of the supply chain and how access to critical components is, in some cases, the main threat to maintaining USAF system lethality.26
___________________
24 U.S. Department of Justice, 2018,“Orange County Electronics Distributor Charged with Selling Counterfeit Integrated Circuits with Military and Commercial Uses,” Press Release 18-070, May 1, https://www.justice.gov/usao-cdca/pr/orange-county-electronics-distributor-charged-selling-counterfeit-integrated-circuits.
25 From a National Defense University, 2017 Industry Assessment paper: “One way to continue to increase the functionality of a chip without doubling its transistors, per Moore’s law, is to approach the chip architecture differently. The system-on-a-chip (SoC) concept has been one method to address this challenge, particularly in mobile devices. In SoCs, multilevel and multiarchitecture chips incorporate numerous central and dedicated processors (such as graphics processing units [or coprocessors]), communications (such as Wi-Fi and Universal Serial Bus [USB]), and memory, onto a single chip.”
26 G. Synek, 2018, “Malware Strikes Semiconductor Manufacturer TSMC Causing Assembly Line Shut Down,” TECHSPOT, August 4, https://www.techspot.com/news/75817-malware-strikes-semiconductor-manufacturer-tsmc-causing-assembly-line.html.
TABLE 1 Summary of Recent Reports Detailing Examples of Counterfeits and Malicious Insertion
| Year | Title | Summary |
|---|---|---|
| 2010 | NEPP Electronics Technology Workshop report on “Counterfeit Electronic Parts.”a | The report provided a detailed analysis of the problem of counterfeit chips. See Appendix G of this report for some examples of counterfeit chips. |
| 2012 | GAO reported on “DoD Supply Chain—Suspect Counterfeit Electronic Parts Can Be Found on Internet Purchasing Platforms.”b | A thorough report on GAO experiences. GAO advertised for replacement parts but received no legitimate parts in response. Instead, GAO received counterfeit parts, legitimate parts but with falsified post-production date codes, and fake parts. |
| 2012 | Senate report on “Inquiry into Counterfeit Electronic Parts in the Department of Defense Supply Chain.”c | The report found over 1,800 cases with over 1 million suspect chips. |
| 2013 | The Semiconductor Industry Association (SIA) reported on “Winning the Battle against Counterfeit Semiconductor Products.”d | The report provided another detailed analysis of the dangers of counterfeit chips. |
| 2015 | GAO testified before Congress regarding chips.e | GAO noted that by 2015, the trusted program had expanded to include over 60 trusted microelectronics suppliers, although DoD used only IBM (now GlobalFoundries) for fabrication of leading-edge trusted microelectronics. |
| 2015 | Testimony of Ms. Kristen Baldwin, Principal DASD(SE), before the House Committee on Armed Services Subcommittee on Oversight and Investigations regarding DoD microelectronics and the trusted and assured program.f | Overview and update on trusted and assured program. |
| 2016 | GAO released GAO 16-236, “Counterfeit Parts; DoD Needs to Improve Reporting and Oversight to Reduce Supply Chain Risk.”g | Recognized continuing need for supply chain improvement. |
| 2016 | Congressional Research Service (CRS), “U.S. Semiconductor Manufacturing: Industry Trends, Global Competition, Federal Policy,” June 27, 2016.h | Overview of industry; limited applicability to counterfeit chips and malicious insertion. |
| 2017 | President’s Council of Advisors on Science and Technology report on “Ensuring Long-Term U.S. Leadership in Semiconductors.”i | Interestingly, while the report offers recommendations on U.S. technology and China, among others, it does not even mention counterfeits or malicious insertion or trusted foundry, or how to deal with the problem. |
| Year | Title | Summary |
|---|---|---|
| 2017 | Defense Science Board Report on Cyber Supply Chain.j | 25 in-depth recommendations. No public examples of successful malicious insertion on DoD components. |
a Brian Hughitt, “Counterfeit Electronic Parts,” presentation at the NEPP Electronics Technology Workshop on June 22-24, 2010, https://nepp.nasa.gov/workshops/etw2010/talks/08_Hughitt_Counterfeit%20Electronics%20-%20All%20the%20World’s%20a%20Fake.pdf.
b U.S. Government Accountability Office (GAO), 2012, DoD Supply Chain—Suspect Counterfeit Electronic Parts Can Be Found on Internet Purchasing Platforms, Report to the Committee on Armed Services, U.S. Senate, GAO 12-375, Washington, DC, February.
c U.S. Senate, 2012, “Inquiry into Counterfeit Electronic Parts in the Department of Defense Supply Chain,” Report of the Committee on Armed Services, May 21, https://www.armed-services.senate.gov/imo/media/doc/Counterfeit-Electronic-Parts.pdf.
d Semiconductor Industry Association, 2013, Winning the Battle Against Counterfeit Semiconductor Products, Anti-Counterfeiting Task Force, August, https://www.semiconductors.org/.
e M.A. Mak, 2015, “Trusted Defense Microelectronics, Future Access and Capabilities Are Uncertain,” GAO 15-185T, Testimony Before the Subcommittee on Oversight and Investigations, Committee on Armed Services, U.S. House of Representatives, Washington, DC, October, p. 4.
f Andre Gudger, Kristen Baldwin, and Brett Hamilton, “Testimony Before the U.S. House of Representatives Committee on Armed Services Subcommittee on Oversight and Investigations,” October 28, 2015, http://docs.house.gov/meetings/AS/AS06/20151028/104057/HHRG-114-AS06-Wstate-BaldwinK-20151028.pdf.
g GAO, Counterfeit Parts: DoD Needs to Improve Reporting and Oversight to Reduce Supply Chain Risk, Washington, DC, p. 1.
h M.D. Platzer and J.F. Sargent, Jr., 2016, U.S. Semiconductor Manufacturing: Industry Trends, Global Competition, Federal Policy, R44544, Congressional Research Service, Washington, DC, June 27.
i President’s Council of Advisors on Science and Technology, 2017, Ensuring Long-Term U.S. Leadership in Semiconductors, Report to the President, January, https://obamawhitehouse.archives.gov/sites/default/files/microsites/ostp/PCAST/pcast_ensuring_long-term_us_leadership_in_semiconductors.pdf.
j U.S. Department of Defense, 2017, Report of the Defense Science Board Task Force on Cyber Supply Chain, February, https://www.acq.osd.mil/dsb/reports/2010s/1028953.pdf, p. 2.
In addition to state-of-the-art electronics, there will be a continued need for nearly every semiconductor technology from the last 30-40 years as existing platforms age. Many of these are no longer in commercial production and are increasingly difficult to locate in open markets, due to low non-DoD demand or transition to new manufacturing methods. Thus, DoD will need domestic sources for uninterruptible access to custom parts and means to deal with obsolescence replacement and modernization to avoid losing capabilities, especially in times of conflict and global supply disruption.27
___________________
27 DoD, 2018, Strategy for Ensuring Access to Assured Microelectronics, Response to National Defense Authorization Act for Fiscal Year 2017, Section 231, Under Secretary of Defense for Research and Engineering, Washington, DC, April.
THE ROLE OF CYBER
The complex and daunting challenges associated with ensuring that software in USAF weapon systems is both secure and reliable was not the focus of this report and is not explicitly addressed. Moreover, there are numerous other reports that provide a very detailed assessment of cyber vulnerabilities, threats, and potential risk mitigation strategies.28 However, as this report was being drafted, the U.S. Government Accountability Office (GAO) released its assessment of cybersecurity in DoD weapons systems.29 GAO was asked to review the state of DoD weapon systems cybersecurity (Figure 2).
The report addressed (1) factors that contribute to the current state of DoD weapon systems’ cybersecurity; (2) vulnerabilities in weapons that are under development; and (3) steps that DoD is taking to develop more cyber resilient weapon systems. The report offered a frank and sobering assessment on how well the acquisition community is doing in addressing the growing cybersecurity challenges in its weapon systems.30 Several of the observations in the GAO report are echoed by the findings of this report. Namely, the lack of a comprehensive test program to rigorously validate that the systems are performing as designed, with no additional

___________________
28 DoD, 2017, Report of the Defense Science Board Task Force on Cyber Supply Chain, Office of the Under Secretary of Defense for Acquisition, Technology, and Logistics Washington, DC, February.
29 U.S. Government Accountability Office (GAO), 2018, Weapons Systems Cybersecurity—DoD Just Beginning to Grapple with Scale of Vulnerabilities, GAO-19-128, Report to the Committee on Armed Services, U.S. Senate, Washington, DC, October.
30 Ibid.
functions and a lack of assessment tools for systems that have transitioned into sustainment programs to ensure that as hardware becomes obsolete, new components are designed with security and resiliency as key performance requirements. Last, the GAO report highlights the initiatives that each Service has developed that focus on cybersecurity. In 2015, the Navy established CYBERSAFE, which aims to ensure survivability and resiliency of critical warfighting information technology and system components and processes. In 2017, the Army conducted a deep-dive, Army-wide review to assess the service’s cyber needs, strengths, weaknesses, and assets. With this information, the Army plans to develop a holistic approach to address weapon systems and industrial control systems cybersecurity. In 2017, the Air Force established the Cyber Resiliency Office for Weapons Systems (CROWS), which focused on mission-level cyber risk analysis, integrating cyber info systems engineering, developing a cyber-savvy workforce, and increasing the integration of cyber intelligence. This organization aims to ingrain cyber resiliency into USAF culture in order to maintain mission-effective capability under adverse conditions. This office is dedicated to managing the execution of the USAF Cyber Campaign Plan (CCP) across the USAF enterprise and is a component within the USAF Life Cycle Management Center (AFLCMC/EN) organization. The goal of the CCP is to “bake in” cyber resiliency into new weapon systems and “mitigate” critical vulnerabilities in fielded weapon systems.31
Similar to the USAF SCRM Campaign Plan, the USAF CCP (Box 3) provides a good model for how the USAF might address the hardware vulnerabilities of the microelectronic components in its weapon systems. The CCP applies a “People, Processes, and Products” approach with seven lines of action (LOAs) that are intended to create a culture within the USAF acquisition community that understands that cyber resiliency is critical for mission assurance. Unfortunately, this plan lacks the LOAs intended to emphasize protection of program information—for example, LOE 4: Develop SCRM Education, Training, and Awareness; LOE 6: Periodic Review of Software and Services; or LOE 9: Enhance Contract Language, which are part of the sustainment SCRM Campaign Plan highlighted earlier.
Both of these campaign plans offer examples for creating a framework for how the USAF might adopt a similar approach for establishing a culture of “SystemSecure” to increase awareness across the USAF on the need for aggressive supply chain monitoring and remediation whenever risks are identified—both for hardware and software—across the entire acquisition life cycle. Ideally, the SystemSecure program should require certification with traceable and auditable provenance of the component
___________________
31 GAO, 2018, Weapons Systems Cybersecurity—DoD Just Beginning to Grapple with Scale of Vulnerabilities, GAO-19-128, Report to the Committee on Armed Services, U.S. Senate, Washington, DC, October, p. 33.
from design library to foundry, to packaging to the point of installation within a SystemSecure boundary across the entire life cycle of the weapons.
SUSTAINMENT—A SOFT TARGET OF OPPORTUNITY
Subsequently, in 2013, the Director of National Intelligence (DNI) issued guidance for SCRM in Intelligence Community Directive (ICD) 731. This directive established policy for supply chain protection through the identification, assessment, and mitigation of threats, addressing the intelligence community’s focus on activities of foreign intelligence entities and adversarial attempts to exploit vulnerabilities to a supply chain. ICD 731 specifically notes the importance of participation from subject matter experts outside the intelligence community, including acquisition, program offices, and other relevant functions to encompass a clear understanding of all stages of the defense supply chain. The directive also calls for the integration of security measures at all points in the supply chain where foreign intelligence entities could penetrate or compromise the process, requiring the establishment for a formal community to address SCRM matters.32
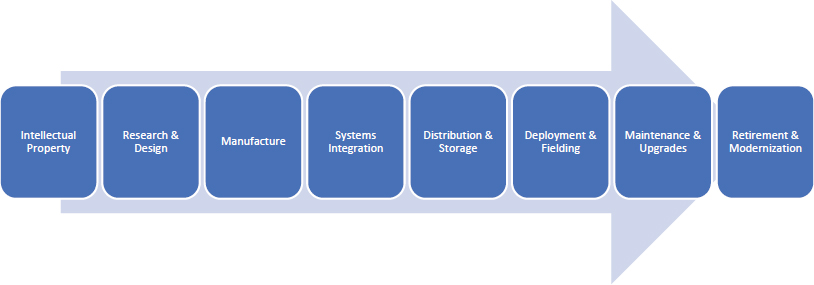
It is important to understand the nature of vulnerabilities that pose threats to the weapon system as a function of the particular stage in the supply chain life cycle. Figure 3 illustrates how the supply chain life cycle will be described throughout this report. The supply chain of an individual microelectronic component or system of components will be discussed in much greater detail in subsequent sections of this report and can be thought of as a subsystem of the overall supply chain life cycle.
The management of legacy weapon systems has evolved to include sophisticated upgrades that are required to keep pace with global advancements. Fre-
___________________
32 Office of the Director of National Intelligence (ODNI), 2013, Intelligence Community Directive (ICD) 731, “Supply Chain Risk Management,” December 7, https://www.dni.gov.
quent addition of next-generation components and systems are used to avoid the significant cost of retiring the legacy platform to make room for an even costlier acquisition of a new platform and its associated supply chain. In many cases, this exposes the legacy weapon system to a multitude of vulnerabilities, both during and after the upgrade. During the upgrade, the weapon system is managed either wholly or in coordination with maintenance support organizations comprised of personnel who are often unaccustomed to managing sensitive systems and may be unaware of the threats to the supply chain under their supervision.
A better knowledge of the factors affecting the operational capability of a fielded weapon system could enable analysts to identify vulnerabilities and limitations to the weapon system itself, while improving assessment of operational capability. This analysis, coupled with educated threat assessment, would produce an improved sight picture on the risk present in each phase of the supply chain. A more accurate risk assessment would give a better sight picture to inform the allocation of resources and collection efforts to a fielded weapon system, improving SCRM efforts for defense weapon systems.
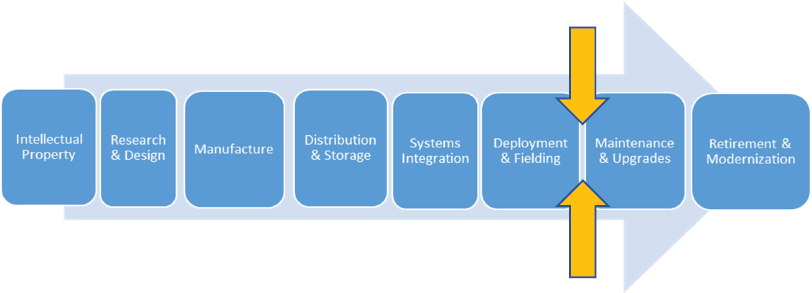
Figure 4 represents the transition point in the supply chain where there is a change in the nature of the threat and system vulnerabilities. Although hardware and embedded firmware are exposed to global threats up through the systems integration stage in the acquisition process, this is also the period of greatest scrutiny by the acquisition and intelligence communities. In contrast, once a system has been deployed and is part of the sustainment community, it is no longer subject to most of the PPPs developed in the early stages of acquisition. Effective implementation of the sustainment SCRM Campaign Plan highlighted earlier in this report could mitigate this gap.
The predominance of supply chain vulnerabilities after the fielding of a weapon system occur as operations conducted in cyberspace. Although cyber exposures can occur at earlier stages in the supply chain, these systems are maintained at higher
classification levels and undergo more scrutiny than they do in the maintenance phase. This additional scrutiny decreases the likelihood of successful malicious cyber infiltration prior to deployment and fielding of the weapon system. Additionally, firmware and software are designed independent of hardware production, and are often made to be changed or updated on a regular basis. This acquisition practice could introduce considerable vulnerabilities during operation of the weapon system, as software and firmware updates are routinely provided by maintenance staff over unclassified networks.33
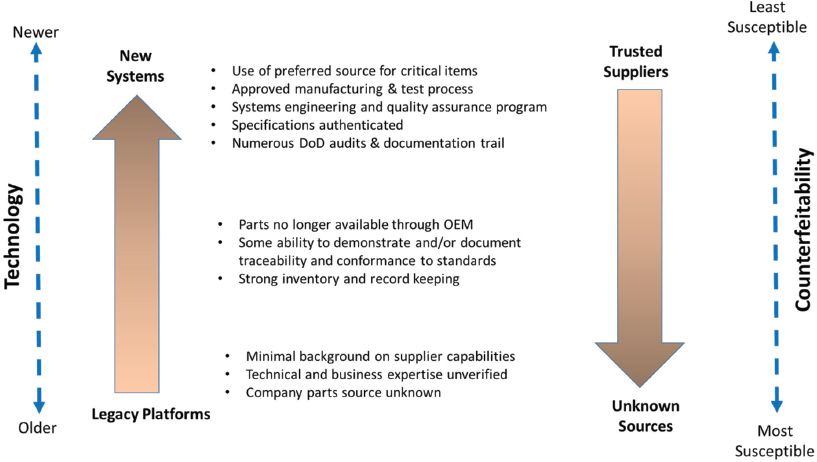
An increased emphasis on risk-based analysis in the supply chain of the sustainment community reveals a growing concern over counterfeits as carriers for a malicious cyber threat. A 2012 Senate Armed Services inquiry found overwhelming evidence that companies in China are the primary source of counterfeit electronic parts in the defense supply chain.34
Figure 5 illustrates the increased threat to legacy systems for counterfeit parts. Where next-generation weapon systems are closely managed by formal SCRM processes from the outset, legacy systems are viewed by field agencies as less sensitive, which is not usually the case for most platforms.35
The process for tracking counterfeit parts has been the study of at least one report.36 Reporting through the Government-Industry Data Exchange Program
___________________
33 DoD, 2015, Supply Chain Attack Patterns: Framework and Catalog, Office of the Deputy Assistant Secretary of Defense for Systems Engineering, Washington, DC, February 18.
34 U.S. Senate, 2012, Inquiry into Counterfeit Electronic Parts in the Department of Defense Supply Chain, Report 112-167, Report of the Committee on Armed Services, Washington, DC, May 21.
35 Slide developed by the committee based on a presentation by Robert S. Metzger, hosted by D.C. Microelectronics Group, “Supply Chain Security: Converging Threats and Coordinated Responses,” presentation on June 6, 2013.
36 Institute for Defense Analyses, 2014, State-of-the-Art Resources (SOAR) for Software Vulnerability Detection, Test, and Evaluation, Alexandria, VA, July 1.
(GIDEP) was identified as insufficient throughout DoD and industry partners by the Senate Armed Services Committee. GIDEP was created to allow DoD to track instances of counterfeit parts, which could assist the detection of threats to the supply chain. Even the Defense Logistics Agency (DLA), which relies on GIDEP information to identify suspect parts in its own inventory, rarely filed GIDEP reports for suspect parts it identified during the 2-year period of the Senate’s investigation. DLA’s practices have improved, but their reports represent only a small portion of the overall threat. Unless industry and field units develop better practices to report and track instances of counterfeit components, the threat will continue to grow. Moreover, even with robust GIDEP reporting, insufficient resources exist in the DoD to detect, validate, and distinguish malicious threats from counterfeits for profit. Furthermore, threat information is rarely shared with industry partners, who are in the best position to mitigate the risk.
Legacy aircraft present an easy target for adversary exploitation, as the DoD’s lengthy and bureaucratic acquisition system provides opportunities for a potential adversary to acquire CPI early that can be studied at leisure to find system vulnerabilities that can be readily exploited without more expensive or challenging hardware exploitations. In addition, legacy platforms are widespread throughout DoD, and when fielded to operational locations without experienced SCRM personnel, could be subject to exploitation during routine maintenance operations over unprotected networks. Exploitation of new weapon systems would be equally impactful, but it is less plausible due to the nature of the environment in which
they operate and the limited access provided to their maintenance and sustainment. Tanker operations, as an example, are foundational to the success of USAF aviation tactics; if an adversary is able to gain information on systems and capabilities that allow them to slow the refueling effort for a major engagement, operations could quickly degrade.
In summary, policy has solidified and synchronized the intelligence community and DoD SCRM processes, decreasing the likelihood of physical threats introduced in the initial design of the weapon system. However, once a weapon system is fielded, even though a physical threat is less common, a physical exploitation would be more difficult to detect and could persist for years before it was revealed as malicious. Vulnerability testing in the earlier stages of the acquisition process is robust and has the full attention of the acquisition and intelligence communities. However, in the sustainment community, field-level testing and reporting of malfunctioning parts lacks standardization and consistency across weapon systems. This creates a target of opportunity for adversaries to introduce counterfeit or tainted parts during the maintenance and sustainment phase of the supply chain.
MAINTENANCE AND SUSTAINMENT CONSIDERATIONS
Expanding Threat Vectors over the Next 5 Years
Understanding the threats facing USAF weapons systems over the next 5 years and beyond requires a very detailed understanding of the vulnerabilities of the components within the system. This is because a threat is predicated on the vulnerabilities of each component and its interdependencies to other components within the system, coupled with the capabilities of the adversary intent on exploiting the vulnerability for a specific purpose. Not all threats may be intended to be catastrophic and instead could be intended to erode confidence or assurance in the reliability of the system.
In spite of a deliberate effort to institute a robust program protection plan (PPP) for critical program information (CPI) across the life cycle of the weapon system, hostile cyberattacks and exfiltration of CPI are still occurring in USAF weapon systems.37,38 It is almost certain that potential nefarious actors have the capability to introduce malicious vulnerabilities through software, hardware, and/or system attack vectors.
___________________
37 U.S. Air Force, 2013, “Program Protection Planning for Life Cycle Management,” Air Force Pamphlet 63-113, October 17.
38 GAO, 2018, Weapons Systems Cybersecurity—DoD Just Beginning to Grapple with Scale of Vulnerabilities, GAO-19-128, Report to the Committee on Armed Services, U.S. Senate, Washington, DC, October.
Downstream lack of awareness of the inherent vulnerabilities to a weapon systems’ supply chain by some U.S. vendors is of concern, as is the potential for supply chain poisoning through the deliberate or inadvertent insertion of malicious code.39,40,41 Furthermore, continued engagement by U.S. forces in conflict zones such as Syria creates an environment ripe for foreign extraction of U.S. weaponry and reverse engineering of its electronic comp electronic components.42
Global Access and Pace of Innovation—Long Term Threats
In spite of the significant amount of national attention and Office of the Secretary of Defense (OSD) policy efforts aimed at increasing awareness of security and reliability of microelectronics in DoD systems, two issues will continue to challenge the USAF acquisition community for the foreseeable future: access and pace.
Access
The major threat to national security in the microelectronics industry is access to leading-edge components critical to future capabilities and access to components that are critical to legacy platforms that are no longer provided through the commercial market. The DoD market is a very small amount of the sales numbers of most major firms.43 DoD can no longer dictate the terms for cutting-edge designs, and the associated production runs, to industry. The commercial sector has outpaced DoD, and its demand for innovation and cutting-edge technologies has captured the market, making it insensitive to DoD-specific needs. In just the last several years, new market segments have emerged in support of cloud computing, autonomous vehicles and systems, advanced manufacturing robotics, wearable technologies, and the Internet of Things (IoT), just to name a few.44
___________________
39 U.S. Senate, 2012, Inquiry into Counterfeit Electronic Parts in the Department of Defense Supply Chain, Report 112-167, Report of the Committee on Armed Services, Washington, DC, May 21.
40 Semiconductor Engineering, 2018, “Security Gap Grows,” July 9, https://semiengineering.com/security-gap-grows/.
41 Federal Bureau of Investigation, 2011, Supply Chain Poisoning—A Threat to the Integrity of Trusted Software and Hardware, Washington, DC, June 27.
42Newsweek, 2018, “World: Russia Is Building Advanced Military Weapons Based on U.S. Missiles Used in Syria,” May 29, https://www.newsweek.com/russian-military-building-advanced-weapons-based-us-missiles-used-syria-947565.
43 D.J. Radack, 2016, Semiconductor Industrial Base Focus Study—Final Report, Institute for Defense Analyses, Alexandria, VA, p. 1-1.
44 Business Insider Intelligence, 2016, “10 Million Self-Driving Cars Will Be on the Road by 2020,” Business Insider, June 15, http://www.businessinsider.com/report-10-million-self-driving-cars-will-be-on-the-road-by-2020-2015-5-6.
As described in a recent report from the National Defense University,45 “National security applications must either work with small design houses and limited fabs that will do boutique designs and small volume runs, or piece together a system using commercially available designs and products. The impact of this reality in either case is less than ideal. First, National Security Systems will continue to have limited access for unique application design and fabrication. Second, if U.S. systems are built upon commercially available products, U.S. adversaries will have the same access and can fully reverse engineer and exploit the chips.”
Pace
Defense acquisition development timelines for both new weapon programs in development and modernization of legacy platforms will continue to remain an impediment to DoD in leveraging the emergence of the advanced-node commercial market. The slower pace required for test, mission assurance, training, and logistics support of national security system acquisition is incongruent with the rapid pace of the microelectronics industry. In some cases, highly capable systems can be designed and fielded without leading-edge technology and an acquisition strategy can be designed that is supportable in the future through lifetime buys of critical components or the use of “heritage process” fabrication capabilities such as that offered by the Defense Manufacturing Electronics Activity (DMEA). However, at some point in their operation, all USAF weapon systems are dependent on complex software-enabled microelectronic components (e.g., FPGAs), but at the same time, DoD has become a less influential buyer in a globalized supplier base for these critical components.46 This reliance on a global supply chain where access and trust cannot be assured is an unavoidable risk to USAF weapons systems that must be proactively managed throughout the life cycle of the weapon system. The need to understand the supply chain for every component (not just those that are labeled as critical) in each USAF weapon system is daunting but necessary before secure and reliable microelectronics can be realized.
TECHNOLOGY APPROACHES TO SECURE AND RELIABLE ELECTRONICS
Assessing the current and emerging threat landscape for microelectronics requires the evaluation of each segment of the industry separately but also noting the
___________________
45 National Defense University Industry Report, Electronics, 2017; The Dwight D. Eisenhower School for National Security and Resource Strategy; National Defense University, Fort McNair, Washington, DC.
46 DoD, 2017, Report of the Defense Science Board Task Force on Cyber Supply Chain, Office of the Under Secretary of Defense for Acquisition, Technology, and Logistics, Washington, DC, February.
criticality of each segment remaining synchronized with the others as technologies mature. A lag in one segment will drive repercussions and affects all other segments across the globe.47Box 4 illustrates this interdependence. Understanding the complexity and dynamism of the microelectronic supply chain requires systems-level expertise as well as subject matter experts from the microelectronics community, which is often beyond the capabilities resident in individual USAF program offices. Within the USAF, this important function appears to be addressed episodically and is disconnected and highly dependent on the individual efforts of staff within each program office.
Figure 6 outlines the high-level development life cycle of a modern microelectronic part from initial design, through fabrication, packaging, testing, and supply chain distribution. Each step along the life cycle path provides different
___________________
47 G. Synek, 2018, “Malware Strikes Semiconductor Manufacturer TSMC Causing Assembly Line Shut Down,” TECHSPOT, August 4, https://www.techspot.com/news/75817-malware-strikes-semiconductor-manufacturer-tsmc-causing-assembly-line.html.
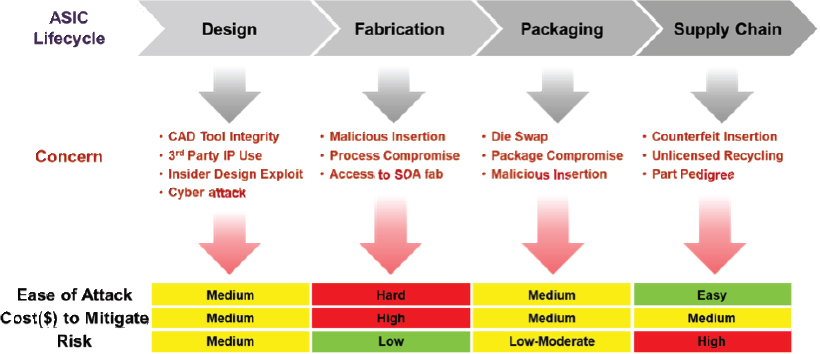
opportunities for an adversary to compromise the performance, functionality, and/or reliability of the electronic device.
Design Concerns
In the design phase, there are several areas of concern given the massive complexity of modern ASICs and FPGAs. The primary concerns are (1) the use of third-party intellectual property (IP); (2) protection of critical design information; and (3) the dependency on computer-aided design (CAD) tools.
- Third-party intellectual property (IP): Modern ICs can contain more than 10 billion transistors and can require hundreds of person-years to design. To handle this complexity and to reduce the design burden, IC designers make extensive use of already developed circuit blocks considered as IP by the designer (e.g., high-speed interface circuits, microcontrollers, and memory blocks). IP from a known or unknown source is often “locked”; the delivered product is encrypted to protect the source code, which means that the user must trust the provider. The opportunity exists for an adversary to compromise these IP circuit blocks for future exploit—for example, inserting circuit elements that do not alter the normal functioning of the device until triggered by some external command. Additionally, complex IP may have lifetime or other reliability limitations that are not known to the end user since not all design assumptions as stated in the delivered IP.
- Protection of critical design information: Another concern is design exposure. Modern microelectronic designs are extremely complex, requiring multiple design teams working together to generate the large digital design files (gigabytes) that describe the layout and functionality of the electronic part. It is in the design phase when microelectronics are in their easiest-to-understand form. Compromise at this stage can expose highly useful/descriptive CPI to the adversary. In addition to the possibility of malicious design compromise where the desired functionality of the part gets altered, the ability of the adversary to simply understand the inner workings of the electronic part (its strengths and vulnerabilities) exposes it to other forms of attack (e.g., cyber) that seek to exploit the weaknesses of the original design.48 Use of encryption throughout the design cycle is key, including encryption at rest and during design information transfers between team members. Product protection techniques can be applied through a number of design methods, including disaggregation of CPI across multiple devices ensuring that the information is not exposed to a single insider or fabrication facility. Cyber protection of CPI can be achieved through means such as Defense Advance Research Projects Agency (DARPA) System Security Integration Through Hardware and Firmware (SSITH), which enables the use of hardware roots of trust in an embedded electronics system. Additionally, microelectronics can be provided with unique identifiers to trace their provenance using built-in signature generators. Physically unclonable functions (PUFs) are one means of providing signatures and leverage the natural variations in the manufacturing process to encode this signature.
- CAD tools: Finally, microelectronic designers are dependent on computer-aided design (CAD) tools to lay out, simulate, and verify the proposed ASIC. There are just a few major suppliers of these tools. The initial computer-code originates from many different sources, including university research, acquired start-up companies, and contracted code writers from the international community. The pedigree of these CAD tools may not be fully known, and the software is frequently updated with new releases to fix known bugs and provide new features. The opportunity exists for a determined adversary to compromise these tools. However, the probability of a successful compromise of CAD
___________________
48 This coupling between the cyber and hardware domains is an area of growing concern and an extremely hard problem to solve or predict. Spectre and Meltdown are recent examples where cyber attackers tapped into hardware vulnerabilities in ICs that were considered highly secure when they were initially designed, allowing the attackers to gain access to sensitive data on the system. A part that may be considered secure today may not be so in the future. This is of particular concern for AF systems with their long operational life cycles, which provide the adversary the benefit of time to identify and exploit potential hardware weaknesses. More frequent refresh of the critical electronic hardware used in AF weapon systems would help to mitigate this risk.
tools is unlikely since there are many users of these software systems and any changes that could degrade their performance would ultimately be discovered.
An additional concern is the “insider threat,” which can affect any phase of the IC life cycle. It is in the design phase, where human contact is at a maximum, that the potential for tampering or changing the functionality of an IC is the highest. In a complex circuit where a “design team” approach is typically employed, there is the benefit of having multiple sets of eyes reviewing the final design. The likelihood of an intentional alteration of the circuit making it through the design team verification process is low unless the team is colluding together. However, the unlikelihood of a successful attack in the design phase does not preclude this vulnerability as a very real threat. Release of design information to adversaries who can at leisure study the design for inherent vulnerabilities to aid in subsequent attack vectors is a realistic threat.
Fabrication Concerns
This issue was brought to the forefront a few years ago by the sale of IBM’s microelectronic fabrication divisions in East Fishkill, New York, and Essex Junction, Vermont, that performed secure fabrication of semiconductor parts for the U.S. government under the Trusted Access Program Office (TAPO). IBM “sold”49 this division to GlobalFoundries (GF), which is owned by Mubadala Development Company, a state-owned holding company based in the United Arab Emirates.
This particular event emphasized the lack of a domestically owned foundry offering advanced node (e.g., 14 nm or beyond) capabilities.50 While the TAPO relationship was extended with GF at East Fishkill and Essex Junction for some process flows, the long-term viability of this agreement is uncertain. Many groups have examined this trusted fabrication issue. A general conclusion of these studies is that it will be cost prohibitive to stand up and maintain a government foundry at an advanced node, and that the government-trusted manufacturing community must find ways to utilize offshore, foreign-controlled manufacturing in a secure manner. The focus of several recent DARPA and Intelligence Advanced Research
___________________
49 IBM actually paid GlobalFoundries (GF) approximately $1.5 billion to take over their semiconductor fabrication operations; in exchange, GF agreed to supply the specialized IC’s used in IBM’s computer systems for some undisclosed number of years.
50 Intel fabricates at advanced nodes (e.g., 14 nm) but traditionally only as an integrated device manufacturer (IDM); it is venturing into the foundry marketspace but to date has not offered wide-scale foundry services; see Intel Corporation, “Intel Custom Foundry,” http://www.intel.com/content/www/us/en/foundry/overview.html. Samsung, Austin, Texas, and GlobalFoundries, Malta, New York, also operate 14-nm production lines, but these facilities are not U.S.-owned.
Projects Activity (IARPA) programs (TRUST, TIC, IRIS),51 have been designed to address this topic. These programs targeted enhanced verification and validation techniques for foreign fabricated microelectronics along with the development of design obfuscation techniques to “hide,” or make difficult to determine, an ASIC’s intended functionality. Adding to this view is that the level of automation and statistical process control, in a modern leading-edge fabrication facility, would make it extremely difficult for a single bad actor to reach into a production line and alter the functionality of a complex part without detection. There remain organizations within the government community requesting a dedicated fabrication facility, whether this be a government-specific annex attached to an existing domestic commercial fab or a dedicated government 300 mm back-end-of-the-line fabrication facility utilizing a split fab model (DMEA’s approach).52 There are classes of electronic devices, like those used in nuclear weapons and their associated command and control infrastructure, where security must be assured. However, these systems may not require the most advanced node electronic components and can most likely be met through existing trusted domestic fabrication sources. While these investments are an important step in building a U.S.-based manufacturing capacity, microelectronics needed for USAF weapon systems span a technology range well beyond what will be available through these programs. For example, RF receivers and other sensors require semiconductor processes that include high-power device technology such as gallium nitride (GaN) and very high-speed processing such as silicon germanium (SiGe). These technologies are not available in 300-mm wafers, and they require investments beyond what these programs will provide.
Until recently, the prior examinations of this problem have ignored the larger issue of future access to leading-edge microelectronics and the growing foreign control of semiconductor manufacturing, particularly in the Pacific region (e.g., China, Taiwan, and Korea). China’s fraction of world IC foundry production has grown significantly in recent years, with the Chinese government’s stated goal of developing a substantial domestic semiconductor fabrication capability. Supporting this intent, China has announced it will provide $150 billion over the next 5-10 years to subsidize growth in microelectronics manufacturing. To acquire needed technology for advanced node manufacturing, China has successfully negotiated with the Taiwanese Semiconductor Manufacturing Company (TSMC)—the world’s largest pure-play foundry, with 56 percent market share in 2017—to build
___________________
51 TRUST = Trusted Integrated Circuits; TIC = Trusted Integrated Chips; IRIS = Integrity and Reliability of Integrated Circuits.
52 The split fab model is where the front-end transistors are fabricated in an untrusted fabrication facility and the back-end wiring levels (which ultimately define the IC’s function) are performed in the trusted, government-owned back-end facility. The notion is that this can be performed in the lower-cost government facility than a complete fab performing both the front-end and back-end fabrication.
an advanced node semiconductor plant in Nanjing, China, and more recently has entered a joint venture with GF (current supplier of “DoD Trusted” electronics) to build a new semiconductor plant in Chengdu, China, slated to begin operation in late 2018.
When examined in this manner, the problem is immensely larger than the trust problem that has been the DoD focus to date, and the solution requires policy changes and investments well beyond what has been proposed to secure and maintain future access to advanced microelectronics. The scale of this issue will require a national-level initiative to correct. A logical goal would be to reverse the current trends and guide a large fraction of the nation’s advanced microelectronic fabrication facilities back onshore, and robustly invest in next-generation technology with the goal of maintaining a strong domestic hold of the resulting technology. The new $1.5 billion DARPA Electronics Resurgence Initiative (ERI) and OSD’s Microelectronics Innovation for National Security and Economic Competitiveness (MINSEC) are targeted in this area. U.S. dominance in future semiconductor fabrication technology, along with onshore facilities, could reduce the potential threat and offer a strong national strategic advantage.
Packaging Concerns
After an IC is fabricated, it is typically placed in a carrier (“package”), which protects the part from physical and environmental damage and serves as the electrical interface between the chip and the printed circuit board it is integrated onto. Just like with microelectronic fabrication, packaging technologies have continued to progress to accommodate the increasing pin count, higher performance, and high computational density of modern ICs. In the commercial product market, foreign companies dominate the high-volume packaging production. For these commercial off-the-shelf (COTS) parts, there are potential attack surfaces for a sophisticated adversary that need to be mitigated. However, in contrast to the limited number of deep-node complementary metal-oxide-semiconductor (CMOS) foundries, there are more available onshore companies that can provide packaging for DoD systems. There are presently 28 Trusted Packaging Suppliers that have been accredited by DMEA (as of July 26, 2018), and a vast number of original equipment manufacturer (OEM) providers.
With the presence of many capable packaging facilities in the United States, this is an area of opportunity where new technologies can be developed to improve performance and security of electronic parts for the DoD. DARPA has a long history of technology programs that have developed advanced packaging approaches for the high-density heterogeneous integration of electronics parts. The DARPA
CHIPS, JUMP, COSMOS, and DAHI programs53 are all examples. The commercial industry is also using similar approaches of integrating many individual IC die onto silicon interposers for state-of-the-art FPGAs and graphics processing units (GPUs).
In addition, DARPA has had several “packaging” programs targeted at ensuring the pedigree and trust of commercial components, and their supply chain, by leveraging advances in deeply scaled CMOS technology development and three-dimensional integration technology. In the DARPA SHIELD program, they developed an independent ~100 um × 100 um (size of a standard bond pad) dielet that can be integrated in the existing package of a commercial IC to provide inventory tracking, authentication, and telemetry. For example, if the part was exposed to high heat that is used in a soldering and desoldering process, the SHIELD dielet would record these events and subsequently report (through a proximity sensor) if the part has been recycled or tampered with. In other DARPA programs, advanced packaging approaches are being used to intimately integrate a secure trusted monitoring circuit with a commercial IC to ensure the overall functionality of the resulting microsystem.
Long-term threats to the USAF microelectronics supply chain include:
- Availability—Is there assured access to validated design IP, raw materials (reactants, substrates), trusted production capacity? Can an adversary throttle needed precursors? Are genuine legacy components that are no longer in production available through warehousing (lifetime buys) or vetted brokers?
- Gray Market/Counterfeit Components54—Is the USAF capable of reliably detecting genuine OEM parts being distributed outside the controlled supply chain distribution network; salvaged OEM parts that may have compromised reliability; counterfeit or different chips that have been remarked to masquerade as genuine legacy parts?
- Malicious Manipulation—Can USAF adequately monitor suppliers to reasonably ensure against “in-flow” of functionality through compromised design tools, insider threats, packaging adjuncts, or even new chips masquerading as gray-market legacy components?
___________________
53 CHIPS = Common Heterogeneous Integration and Intellectual Property Reuse Strategies; JUMP = Joint University Microelectronics Program; COSMOS = Compound Semiconductor Materials on Silicon; DAHI = Diverse Accessible Heterogeneous Integration.
54 “In typically long DoD acquisition processes, approximately 70 percent of electronics in a weapons system are obsolete or no longer in production prior to system fielding. The Department’s mechanisms for tracking inventory obsolescence and vulnerabilities in microelectronic parts are inadequate” (U.S. Department of Defense, 2017, Report of the Defense Science Board Task Force on Cyber Supply Chain, Office of the Under Secretary of Defense for Acquisition, Technology, and Logistics, Washington, DC, April).
THE SCRM CHALLENGE IN THE ACQUISITION LIFE CYCLE
The USAF acquisition community has been directed by DoDI 5000.02, DoDI 5200.44, and DoDI 8500.01 to apply SCRM methods throughout the acquisition life cycle of systems designated as “applicable systems” as part of a program protection strategy to mitigate threats emanating from the supply chain and address vulnerabilities existing within USAF acquisition programs. Several reports are available that discuss the evolution of the policy and instructions to implement SCRM and so this report will not provide a detailed analysis or critique of the policies. Appendixes C-F provide a nonexhaustive list of over four dozen current policies and guidance documents that USAF program management offices must follow to ensure compliance.
Instead, this section will summarize the historical and current approaches that have been “thrown at” the SCRM challenges listed in the previous sections of this report. Many of the current challenges facing the USAF acquisition community result from attempts to absorb uncontrolled complex technical and geo-economic advancements that are diametrically opposed to DoD and USAF basic requirements for system assurance into the current management structure of USAF programs. Assigning intelligence community threat assessment methodologies, along with concurrent development of vulnerability assessment and risk mitigation tools in the rapidly emerging technology landscape, to USAF program staff trained in traditional oversight focused roles and processes in the expectation that the workforce will recognize, self-organize, and adopt appropriate behaviors has proven unsuccessful.
Program management office personnel have the primary job of defining and managing programs and are often the front line in the interpretation of rules (FARS, DFARS).55 DoD guidelines, when combined with the platform-specific demands of the target system (power, performance, size, etc.), create the outlines of the program. Program staff are responsible for managing cost and schedule trade-offs from the inception of the program through to end-of-life. For this reason, it is very important that any costs (either to schedule or to budget) that are necessary to protect the system and/or to meet SCRM policy are fully understood. Whether personnel understand, at the time of budget creation, which components will require custom chips or a trusted supply chain will be an important factor in correctly predicting cost and schedule. The correct application of the definition of CPI by both the program office and prime contractor will decide which subsystems required a trusted flow.56
___________________
55 FARS = Federal Acquisition Regulations; DFARS = Defense Federal Acquisition Regulations Supplement.
56 National Defense Industry Association, The Guidebook on Trust, Version 17Q4.01, http://www.ndia.org/.
The primary objective of DoDI 5200.44 is to address prevention, detection, and mitigations of components that will adversely affect critical missions due to some form of integrity compromise. However, the selection of the component(s) and supplier(s) are often embedded within prime contractor internal policy and procedures. Government program managers are poorly positioned to pursue modifications to system requirements that exceed the scope of existing contracts. Unless SCRM-specific protections have been specified contractually, there is little chance they will be implemented by the outsourced product or service provider.
The primary concern to USAF acquisition programs regarding “secure and reliable microelectronics” is being able to trust that the procured components will function only as expected. The burden of providing assurances of trustworthiness has greatly increased over the traditional program protection approaches and developmental and operational testing methods. This gap in how DoD program protection programs have developed is, in part, because prior to SCRM and cybersecurity policies, program protection was basically a functional assignment within the “Security” group and focused upon operational security (OPSEC) practice issues. The skill sets of these government workers were not aligned with the challenges faced by SCRM and cybersecurity. Likewise, moving the assessment of technical threats to a systems engineering functional role was logical, but it failed to recognize security concerns during the initial concept and requirement development phases of the acquisition life cycle that left little recourse for recovery or control once the program requirements were “locked down” in the contract. Weapon systems design engineers assigned the new requirements for assessing threats, identifying vulnerabilities, and developing risk management protocols were provided procedures derived from an irrelevant information technology (IT) approach to network and information security. Consequently, many of the SCRM requirements have evolved into mandatory “checklists” instead of steps critical to the successful deployment of the weapon system. Program offices often cannot access the probability or likelihood of threat to their weapon system that would negate their ability to prosecute the mission. However, the imposition of SCRM processes potentially introduces schedule delays and cost increases that are viewed as immediate risks to mission success.
Based on an informal survey of six USAF program offices conducted during the early stages of this study, there is little doubt that USAF program offices are striving to be diligent in implementing an effective SCRM program. The committee gathered information on each programs’ definitions, processes, and procedures used to ensure that the microelectronics components used in their system were secure and reliable throughout the acquisition life cycle. The responses demonstrated little commonality across the programs—for example, the definition of the terms “secure” and “reliable” were often program-specific. Each program attempted to follow the DoDI 5200 guidance documents as well as they could within the limits
of the existing resources and staff expertise. There could be a potential opportunity to minimize duplication, share information, and enhance threat identification and risk mitigation efforts through the creation of a centralized process for enabling resources and experiences to be shared across programs. This might also help to mitigate some of the challenges experienced by DAMO and provide a better collaboration interface for the JFAC.
Each program interviewed was unique in how it followed the guidance from formal reference and inclusion of DFARS clauses at contract award to use of intelligence community assessments throughout the management of the contract. The programs with legacy components typically “inherited” the integrity of incoming electronics and did not conduct additional assessments. The level and frequency of the intelligence community threat assessments varied from a full-time intelligence officer to an ad hoc, threat report-driven cycle. The programs predominantly relied on the National Air and Space Intelligence Center (NASIC) for validation of the threat data instead of relying on the Defense Intelligence Agency Threat Analysis Center (DIA TAC) process, which has become slow and bureaucratic. The programs used their normal cost and schedule risk management and monitoring tools for supply chain threat and risk assessments. The programs also reported that contracting and finance policies did not hinder their ability to ensure reliability and/or confidence of their microelectronics except for modifications (not timely) and that the current policy of separating development and sustainment contracts imposed unnecessary risk to the system. Ironically, although it was lacking, the program offices reiterated that they believed that an aggressive security posture was needed throughout the life cycle. The programs relied heavily on existing DoD guidance and DFARS clauses to flow down requirements to the contractors but did not appear to have a way of validating compliance. Importantly, the committee specifically asked if waivers57 to SCRM requirements were requested, and if so, how often and at what level a waiver could be granted. The programs all reported that no waivers had been requested. However, each program expressed concerns over nondomestic component manufacturers, including configuration control, continuous availability, significant increases in program risk to meet the cybersecurity requirements, embedded software (no easy way to detect malware), and tampering and counterfeiting. Importantly, all of the programs reported that they did not have the necessary people with the appropriate expertise to ensure trust in the supply chain of their components.
USAF program offices are facing an overwhelming list of policies and guidance. Navigating through the volumes of documents generated by various oversight and policy groups is tedious, confusing, and often disjointed on how the program protection processes are interrelated. SCRM guidance and imposed activities often
___________________
57 Waivers are required if a nondomestic supplier is used for a critical component.
do not appear to have clear or achievable results. Verification of threats is lacking, and when a risk is identified and the threat confirmed, program offices in many instances do not have a recourse mechanism to deal with the threat. The time and effort expended on SCRM compliance is often not effective at ensuring that the weapon system is both secure and reliable.
As the DoD revises acquisition policies, USAF program offices will face even more challenges in implementing the guidance. Because SCRM is primarily concerned with the “integrity” component of the security objectives triad of “confidentiality-integrity-availability,” assurances that the integrity of mission-critical components are unchallenged as they travel through a global supply chain is not something that the program offices are equipped to validate. Current DoD policy specifies that all-source intelligence be used by program offices in making supply chain risk decisions. However, as our survey indicated, intelligence data are greatly lacking in specificity, the timeliness of reports, informal relationships, and contract decisions that occurred prior to the involvement of the program. There is little motivation to go beyond the minimal level of current SCRM compliance that focuses on identifying potential supply chain risks and then assessing if they might impact the performance of the weapon system. Replacing this approach with the ability to forecast risk based on a vulnerability analysis of the weapon system component would enable a reactive security approach, but it would almost certainly affect cost and schedule of the program. How to optimize this balance between a proactive vulnerability assessment with threat-informed risk analysis is likely beyond the scope of a single program office.
Moreover, the type of component integrity testing and verification needed to provide assurance that it is both secure and reliable requires specialized test equipment and expertise that is not readily available, is expensive, and is unrealistically time-consuming. As a result, specific evidence on the nature of the threat and the probability of risk to the system must be provided to the program offices to justify the cost and time to the program schedule to aggressively mitigate the risk.
In response to the 2017 NDAA that required DoD to develop a strategy to ensure that the DoD has assured access to trusted microelectronics, the DoD has recently published a comprehensive strategy—DoD Microelectronics Innovation for National Security and Economic Competitiveness (MINSEC)58—that builds on the existing trust and assurance activities within the DoD but provides emphasis on leveraging research and development (R&D) advances to deliver new capabilities to the warfighter and enhance security of the supply chain. The MINSEC strategy outlines a whole-of-government solution to align resources, policies, and incentives
___________________
58 U.S. Department of Defense (DoD), 2018, “Response to National Defense Authorization Act for Fiscal Year 2017, Section 231: Strategy for Ensuring Access to Assured Microelectronics,” Under Secretary of Defense for Research and Engineering, DOPSR Case #18-S-2455, Washington, DC, April.
in several areas that are in alignment with the findings and recommendations of this report—namely, proactive awareness and security that focus on subject matter expertise both within the acquisition community as systems are being conceived and acquired but also in the sustainment and modernization communities.
MINSEC specifically calls for proactive awareness and security, including supply chain tracking with proactive authorities, intelligence and counterintelligence, standards, and the implementation of new approaches like block chain. In addition, MINSEC is directing investments in disruptive R&D, rapid redesign of complex systems, along with new materials and electronic architectures to ensure U.S. leadership as a strategic advantage. The strategy aims to enable access and assurance to secure design, IP, electronic design automation (EDA) tools, fabrication tools, and prototype demonstrations. Finally, a renewed investment is needed in state-of-the-practice back-end technologies for assurance of existing components to complement existing investments in state-of-the-art processing for low-volume manufacturing of leading-edge components.
The MINSEC strategy focuses on maintaining innovation and enabling security through coordinated investments across an integrated circuit’s development life cycle, as illustrated in Figure 6 and discussed in the preceding section. The MINSEC strategy will also begin the hard task of aligning the existing policies to ensure uniformity and implementation of microelectronics protection measures. Finally, MINSEC will review the incentive structures and seek to lower barriers for the insertion of new technologies into weapon systems with the combined goal of providing advanced capability and greater assurance of security and reliability. As part of this strategy, MINSEC is advocating for 15 to 20 percent of the budget for a DoD program to be allocated for new capability insertion and demonstration projects every 1-2 years.
Achieving the goals of the MINSEC strategy will be technically and politically challenging, and it will take sustained leadership from the highest levels of government. Moreover, the uncertainties in long-term funding needed to implement MINSEC could significantly limit the effectiveness of the strategy. However, even if MINSEC is fully successful, the USAF will still need to establish its own in-house competence in SCRM to ensure end-to-end control of microelectronic components used in USAF systems, especially in the sustainment phase of the acquisition life cycle.
THE NEED FOR AN ENTERPRISE APPROACH WITHIN THE USAF
The massive amount of policy guidance and instructions (see Appendixes C-F) have been largely effective in transferring most SCRM functions from program security personnel to systems engineering staff. However, USAF acquisition programs appear to be mainly left on their own to figure out how to address SCRM within the limitations of their current staffing and budget levels. The approach offered through
MINSEC of “taxing” the program offices at 15-20 percent to incentivize the development and insertion of new capabilities will likely only exasperate these challenges.
Other reports have noted the challenges facing the program management offices. Most recently, the 2017 Defense Science Board (DSB) Cyber Supply Chain study noted, “Program management offices are responsible for creating Program Protection Plans. Currently, guidance, expertise, and support for this effort are insufficient, with limited engagement by the system engineering community and limited influence on system design. Program protection planning activities are uneven in quality and focus as some programs focus on protecting microelectronics availability whereas others emphasize protection of personnel or system security.” The study recommended that the JFAC should be used as a much-needed source of expertise in support of program managers to assist with life cycle program protection planning and system security engineering.”59
This report strongly supports the DSB recommendation but the committee believes that the USAF must also develop its own expertise at the enterprise level to better support the efforts of the JFAC. Currently, the USAF delegates SCRM to the program offices. However, delegating SCRM to the program offices results in costly duplication of effort and nonuniform implementation of policy and practices, and presents yet another threat vector.
For a supply chain risk management and threat assessment program to be effective, it must be authorized, implemented, and monitored from the highest levels of the USAF. As has been discussed throughout this report, threats to USAF microelectronic components spans the entire life cycle of the weapon system. Security and reliability start at the earliest stages of R&D, continue through acquisition of the system, and proceed into to sustainment and modernization of the platform. Currently, each phase of this life cycle is organizationally distributed across the USAF.
The USAF should establish a central office—the Air Force Program Protection Office—that should have the responsibility and authority for ensuring implementation of supply chain threat assessment and risk management tools across the weapon systems enterprise—from R&D through acquisition to sustainment and modernization. To be effective, this organization cannot simply be another oversight or coordination office. Instead, it must have unfettered access to program-office vulnerability information and mitigation plans, must be able to direct the use of red teams, must establish enforceable rules for weapon system OPSEC, and must have the authority to hold program managers accountable for implementation of threat mitigation actions. The AFOSI Program Protection Office is a critical component of this new office.
___________________
59 DoD, 2017, Report of the Defense Science Board Task Force on Cyber Supply Chain, 2017, Office of the Under Secretary of Defense for Acquisition, Technology, and Logistics, Washington, DC, April.
BEST PRACTICES WITHIN THE SUPPLY CHAIN RISK MANAGEMENT COMMUNITY
As part of this report, the study committee was requested to evaluate how other organizations implemented a SCRM approach. As an example of a best practice, the intelligence community manages SCRM at the enterprise level through the National Counterintelligence and Security Center (NCSC) Supply Chain Directorate, which reports to the Director of National Intelligence (DNI). The top priority is to identify and analyze threats to U.S. supply chains; develop standards for supply chain threat assessments to ensure analytic rigor; and promulgate rules of engagement for information sharing across government and industry partners supporting U.S. supply chains. In order to create useful frameworks to support the DNI’s SCRM policy, the NCSC published a series of Intelligence Community Standards (ICS) subordinate to ICD 731 that expand the vision for SCRM.60 In conjunction with the first ICS, released in October 2015, the Supply Chain Directorate released a white paper outlining their general framework for assessing risk to the supply chain.61 These two documents provide an excellent framework for the USAF to use in building its own SCRM community.
The NCSC framework draws its foundation from the business philosophy that risk is a function of cost, schedule, and performance. In this equation, a change to or influence on any of the three factors impacts the others. When the nature of the program does not allow for trade-offs in performance, the risk matrix must account for the integrity and security of the product itself. In this case, the supply chain and associated processes must be assessed separately to gauge risk to the supply chain as it relates to mission criticality. Figure 7 illustrates the assessment of risk as it relates to threat, vulnerability, and consequence to the performance of a system.62
The threat assessment requires an understanding of the adversary’s intentions and capabilities, and it includes an effort to discover specific and credible evidence that the system might be targeted by an adversary (Figure 8). It is also critical to distinguish inherent vulnerabilities from those introduced by an adversary, a task that can be difficult during certain phases of the supply chain, where inherent vulnerabilities are commonly observed and may present evidence similar to malicious vulnerabilities that were introduced to the supply chain. Finally, the consequence of a degradation in performance must be considered. If an adversary successfully exploits a mission-critical system, the outcome is categorized as either fixable or fatal.
___________________
60 Office of the Director of National Intelligence (ODNI), 2015, Intelligence Community Standard (ICS) 731-01, “Supply Chain Criticality Assessments,” October 2, https://www.dni.gov.
61 National Counterintelligence and Security Center, 2015, Supply Chain Risk Management: A Framework for Assessing Risk, Supply Chain Directorate, December 15.
62 Ibid.
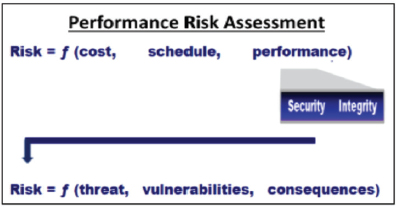
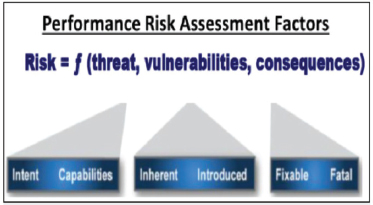
The framework, as described up to this point, does not change based on a particular stage of the supply chain life cycle. The life cycle itself becomes a significant factor when an adversary’s capabilities are applied. The level of a particular threat can fluctuate, as the adversary’s capabilities and intent align with the vulnerabilities inherent at, or introduced to, each stage of the supply chain. Considerable risk exists when the two factors are aligned, presenting an opportunity for an adversary during a specific phase. The supply chain’s dynamic risk environment presents opportunities to an adversary at every stage, requiring comprehensive protection efforts to match the adversary’s efforts.63
Once risk is determined, the NCSC framework informs the intelligence community’s protection efforts, directing the consideration and development of mitigation processes and countermeasures to address a specific threat or vulnerability revealed by their analysis. The nature of each factor drives a different response, or combination thereof, if multiple factors are in play. Figure 9 reflects the actions required to address each factor once the risk assessment is complete.
Figure 10 shows a basic representation of the risk-based analysis applied across SCRM activities. Its application is context-driven and can be adapted to assess current threats and vulnerabilities to the supply chain.
This framework for broad analysis ties the supply chain policies to the DNI’s strategic objectives and could be applied to the maintenance and sustainment
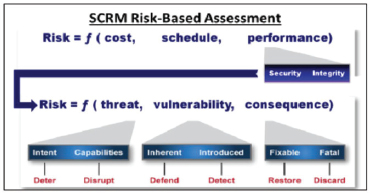
___________________
63 Ibid.
phases within the USAF acquisition community. As an example, published in 2015, ICS 731-01 provides guidance for the first step in the SCRM process—determining mission criticality.
Criticality assessment: An end-to-end functional review to identify critical functions and components based on an assessment of the potential harm caused by the probable loss, damage, or compromise of a product, material, or service to an organization’s operations or mission. The acquisition item is critical if its failure to perform as designed would result in a total mission failure, a significant and/or unacceptable level of degradation of the mission, or a mission compromise.64
The process begins with a detailed breakdown of mission functions along with the components associated with each mission function. ICS 731-01 also acknowledges higher risk in the maintenance and sustainment of a weapon system, whereby there may be poor standard operating procedures in place allowing a technician unsupervised access to critical technology and information. The directive highlights the fact that current processes promote reliance on others to make risk decisions about matters where they are not the risk owners, thus allowing residual risk to be passed to end users and enterprises. This detachment between the acquisition process and the fielded weapon system presents challenges to the criticality assessment process, which relies on the acquisition perspective to gauge vulnerability to a weapon system.65
Specific guidance for conducting threat assessments for acquisition items deemed mission critical was published in 2016. The guidance document, ICS 731-02, represents the second step in the SCRM process, and is defined as follows:
Threat assessment: The process of formally or systematically evaluating an adversary’s intentions and capabilities to compromise or exploit the supply chain. A threat assessment uses the latest available information to determine if there is specific and credible evidence that an acquisition item might be targeted by Foreign Intelligence Entities (FIEs) or other adversaries.”66
The intelligence community SCRM model is displayed as a flow of analytic processes illustrated in Figure 11.67 Unlike the SCRM process described above, the USAF acquisition community does not have the same level of oversight as the program offices. Furthermore, the lack of a central or enterprise level of oversight for SCRM makes it impossible to monitor threats or assess vulnerabilities for mission-critical capabilities across multiple program offices.
___________________
64 ODNI, 2015, ICS 731-01, “Supply Chain Criticality Assessments,” October 2, https://www.dni.gov.
65 Ibid.
66 ODNI, 2016, ICS 731-02, “Supply Chain Threat Assessments,” May 17, https://www.dni.gov.
67 Ibid.
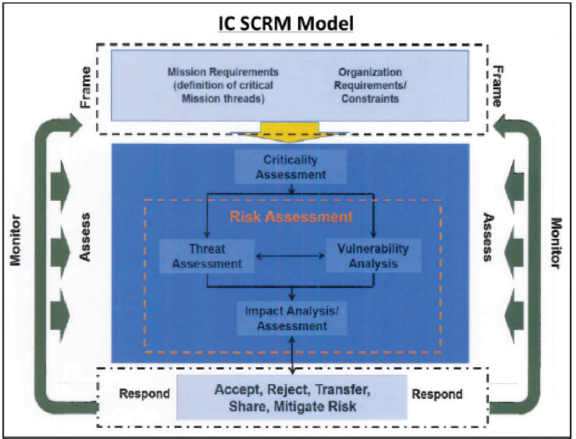
Commercial Fabless Chip Manufacturers—A Case Study of Supply Chain Risk Management and Monitoring
Many U.S. companies are centers for excellence when it comes to discovering and protecting technology that is of interest to U.S. adversaries. The same vulnerabilities that affect civilian industry are present in defense supply chains, creating a target of opportunity to share the SCRM burden with U.S. industry partners. Box 5 provides an illustrative case study.
Effective Acquisition Policy Requires Understanding the Threat
The USAF has no central organization responsible for SCRM, leaving each program office to negotiate its efforts in support of its own weapon systems. The USAF could greatly benefit from a clearer delineation of responsibility to integrate SCRM efforts and improve horizontal protection efforts between weapon systems. As described by the intelligence community SCRM model, an enterprise approach implemented across all USAF weapon program offices would provide a more effective mechanism for defining mission-critical risk assessments and would enable a more holistic approach to developing impact analyses to inform both modernization investment needs and workforce training requirements. The key to this approach is a robust threat assessment component informed by subject matter expertise. Fortunately, within the USAF, AFOSI has a forward-leaning approach to SCRM and is a key resource within the DoD SCRM community. Moreover, AFOSI is unique from other elements in the intelligence community in its outreach to U.S.
manufacturers for information sharing, and its combination of economic crime investigation with counterintelligence. Liaising directly with program managers to support USAF weapon systems, AFOSI has built close relationships with acquisition and program management experts as well as the industry supporting USAF supply chains. Unfortunately, at the time of this report AFOSI had fewer than 10 analysts supporting all of the USAF’s SCRM activities. Based on the scale of the threats facing the USAF supply chain, this is insufficient.
Culture of Security
As noted in earlier sections of this report, one of the easiest and most cost-effective ways to aid the adversary and weaken USAF mission effectiveness is to allow insight into U.S. capabilities and operations. This practice of advertising recent buys of microelectronic components is a very poor OPSEC practice and puts critical USAF electronics information at risk. As an example, a couple of years ago Lockheed Martin was awarded a DoD contract modification of over $104 million to procure and deliver over 80,000 Xilinx FPGAs required for building Joint Strike Fighter (F-35) aircraft.
Lockheed Martin Corp., Lockheed Martin Aeronautics Co., Fort Worth, Texas, is being awarded a $104,734,081 modification to a previously awarded firm-fixed-price contract (N00019-10-C-0002) for the procurement and delivery of 83,169 Xilinx field programmable gate arrays (FPGAs) for the U.S. Air Force (35,842); U.S. Marine Corps (10,517); U.S. Navy (9,517); and the governments of Italy (5,992); Turkey (6,370); Australia (5,952); Norway (4,905); United Kingdom (3,530); the Netherlands (61); and Denmark (483). These FPGAs are required for the manufacture of the low-rate initial production Lot VII through full rate production Lot III Joint Strike Fighter aircraft. Work will be performed in Fort Worth, Texas, and is expected to be completed in September 2014. Fiscal 2011 Aircraft Procurement, Navy; Fiscal 2011 Aircraft Procurement, Air Force; Fiscal 2013 Operations and Maintenance, Navy; Fiscal 2013 Operations and Maintenance, Air Force; and International Partner funding contract funds in the amount of $104,734,081 will be obligated at time of award of which $70,136,722 will expire at the end of the current fiscal year. This contract combines purchases for the U.S. Air Force ($46,384,611; 44.3 percent); U.S. Navy and U.S. Marine Corps ($23,752,211; 22.7 percent); and the governments of Italy ($8,107,089; 7.7 percent); Turkey ($7,593,019; 7.2 percent); Australia ($6,894,676; 6.6 percent); Norway ($6,640,664; 6.3 percent); United Kingdom ($5,132,732; 4.9 percent); the Netherlands ($115,809; 0.11 percent); and Denmark ($113,370; 0.10 percent). The Naval Air Systems Command, Patuxent River, Md., is the contracting activity.68
___________________
68 From Southern Maryland Online, “Local Navy Contract Awards,” posted June 12, 2013, https://somd.com/news/headlines/2013/16931.php; emphasis added.
FPGAs are used in several of the F-35’s systems, including radar, communication, and navigation systems, and are critical components.69 The current practice of providing specific details of critical microelectronic components in its contracting announcements such as the one published for the FPGAs in the F-35 is a poor practice.
Furthermore, undesirable practices like sharing PPP on unsecured networks, allowing electronics to be designed on Internet-connected computers, along with the open publication of critical weapon system parts lists and processes should be stopped. Many of these practices are intended to support contracting best practices such as full and open competition or to enable better communication between industry and the government. However, these practices enable the adversary to steal or exfiltrate CPI with little to no effort. Poor OPSEC is especially damaging because once the information is obtained, it then allows the adversary to expend as much time as needed to identify exploitable vulnerabilities—often before the weapon system has even been fielded. Existing OPSEC policies must be enforced, and when policy gaps are identified, new policies must be put in place to protect USAF weapon systems.
Other reports have documented the reality that program offices lack visibility into the complex supply chain of the microelectronic components used in the weapon systems. This report also finds this to be the case for the USAF. This lack of visibility impairs its ability to proactively monitor threats to the system, assess risks, and develop mitigation strategies to ensure security and resiliency of the system. Ironically, the lack of leadership’s understanding of potential vulnerabilities and liabilities leads organizations to address risks mainly from a technical perspective. However, this ignores the vulnerabilities that an untrained workforce represents, and as noted by the recent GAO report70 and other examples of poor OPSEC practices, there are significant opportunities to mitigate risks to the system by creating a culture of protecting program information across all parts of the enterprise as part of a SystemSecure approach to ensuring security and reliability of USAF systems.
___________________
69 J. Child, 2015, “FPGA processing boards push new performance barriers, Journal of Military Electronics and Computing, August, 8, http://intelligentsystemssource.com/fpga-processing-boards-push-new-performance-barriers/.
70 GAO, 2018, Weapons Systems Cybersecurity—DoD Just Beginning to Grapple with Scale of Vulnerabilities, GAO-19-128, Report to the Committee on Armed Services, U.S. Senate, Washington, DC, October.








































