2
Understanding the Threat Landscape
Several workshop sessions explored various facets of the threats facing the U.S. electric power system. Speakers examined the role and context of computing and communications technology in the electric grid; addressed the imperative to improve grid security from a national security perspective; and considered what constitutes grid resiliency and its cyber, physical, and human components. Panelists also addressed natural and man-made threats from electromagnetic pulse (EMP) and geomagnetic disturbance (GMD) events.
COMPUTING IN THE GRID
- Grid resiliency means providing trustworthy grid operations in hostile environments.
- The resiliency of the electric grid is highly dependent on the resiliency of cyber infrastructure.
- A holistic approach is needed to address the cyber, physical, and human components of grid resiliency.
William Sanders, Carnegie Mellon University, set the stage for the workshop with a broad overview of the issues surrounding security and resilience in the U.S. electric power system.
At the broadest level, Sanders said that the goal of grid resiliency is to provide trustworthy grid operations in hostile environments. To be trustworthy, a system should do what it is supposed to do, and nothing else.
In the context of electric power, this in part requires balancing and supporting goals for safety, confidentiality, integrity, and availability. It is also crucial to recognize that electric power systems operate in hostile environments beset by threats from accidental failures, design flaws, natural threats, and malicious attacks.
Advancing grid resiliency involves strengthening/enhancing cyber, physical, and human components. While there is much that can be learned from cyber resilience work in other fields, such as non-safety-critical business information technology (IT) systems security, the electric power system has important, unique attributes in terms of the systems, goals, and priorities involved. Existing reports, standards, and regulations in this area provide valuable guidance for resiliency protection protocols; examples include the Roadmap to Achieve Energy Delivery Systems Cybersecurity1 and requirements from the Federal Energy Regulatory Commission (FERC) and North American Electric Reliability Corporation (NERC). However, in order to best support true cyber security, Sanders urged that the subsector must transition from a culture of compliance to a culture of true security and resiliency.
Pointing to some recent examples of malware attacks involving energy cyberinfrastructure, Sanders emphasized that the threats are real, they are becoming more sophisticated, and they are increasingly targeting both the physical and cyber elements of our power grid. He described disruptive trends that raise new issues and potential vulnerabilities: the development of “smart” grid infrastructure, adoption of Internet of Things (IoT) devices and cloud services in grid operations, use of dynamic renewable energy sources, and increased electrification of transportation. Against this fast-evolving backdrop, Sanders said that it is critical to recognize that grid resiliency is highly dependent on the resiliency of cyber infrastructure via a complex, interdependent relationship that is not well understood. The picture is complicated even further by interdependencies with other infrastructures, such as telecommunications, transportation, and financial systems.
Sanders highlighted what he sees as key gaps in efforts to advance grid resiliency, including advanced sensing, analytics, and control functions; better detection and response capabilities for cyber and physical systems; well-defined resiliency metrics and assessments; and more attention to the social, cultural, and human factors at play. He urged a holistic view as the field works to close these gaps. “We have to move beyond
___________________
1 Energy Sector Control Systems Working Group, 2011, Roadmap to Achieve Energy Delivery Systems Cybersecurity, U.S. Department of Energy, Washington, D.C.
this current ‘piece-and-patch’ mentality,” he said. “We have to be ahead of the game.”
To ensure that resilience and security are enhanced (and not compromised) as the grid is modernized, Sanders emphasized that it is imperative for all players—industry, academia, and government—to collaborate to address both the near-term and the long-term challenges. While the challenges are substantial, he expressed hope in the field’s ability to meet them. “I think it’s critical that we act now,” Sanders said. “There has been a long set of basic work . . . and I think we have the basic understanding in place to allow us to make quick progress.”
CYBERSECURITY CHALLENGES
- There is wide heterogeneity in the cybersecurity challenges and capabilities of electric utilities across the United States.
- The threats facing the electric grid are heterogeneous, ranging from accidents, infrastructure failures, and natural events to malicious attacks from both outsiders and insiders.
- Existing tools, mechanisms, and partnerships offer promise, but significant progress has been stymied by a lack of research and development (R&D), implementation of existing solutions, or coordination.
Sanders introduced the first panel and moderated an open discussion following their remarks. The speakers were Brian Harrell, Cybersecurity and Infrastructure Agency (CISA) in the Department of Homeland Security (DHS); Michael Hyland, American Public Power Association (APPA); and Robert M. Lee, Dragos.
Brian Harrell, Cybersecurity and Infrastructure Agency
Brian Harrell, assistant secretary for infrastructure protection at CISA, focused on cyber-physical risk reduction. He highlighted risks posed to the grid’s key physical infrastructure in today’s multithreat landscape and described CISA’s perspective on the convergence between physical security and cybersecurity.
Harrell said that it is CISA’s view that the next major attack on critical infrastructure will likely have an insider component, whether from unintended information leaks or from radicalized personnel. An insider attack, by someone with “the keys to the kingdom,” could have devastating and cascading effects to U.S. power systems and other interdependent infrastructures. More worrisome still, existing systems may not be equipped to detect such breaches or recognize their severity when they occur, allowing insider threats to persist unchecked.
Industry standards have strengthened grid security, Harrell said, and the industry has a lot to be proud of. For example, mutual aid assistance agreements among 159 entities covering more than 80 percent of U.S. electricity customers enhance the cybersecurity coverage for those entities through intra-industry cooperation. Nevertheless, there remain reasons for concern and an imperative to act. First, Harrell urged that the industry create a culture of cybersecurity, akin to the culture of safety that was successfully established decades ago, and see that it is ingrained in the grid’s daily operations. Second, he argued that supporting career transitions between government and industry would help to transfer knowledge and practices between these sectors and create a workforce that is better equipped to understand and address the threats at hand.
Michael Hyland, American Public Power Association
APPA represents more than 2,000 municipal utilities, from large cities to small towns. Michael Hyland, senior vice president of engineering services, discussed APPA’s efforts to support cyber resiliency among its members.
Size and context affect each utility’s security needs, priorities, and capabilities. While APPA includes a number of large utilities such as those in Los Angeles, San Antonio, Memphis, and Orlando, most of its members are far smaller, and about half have fewer than 2,000 meters. When it comes to cyber activities and capabilities, Hyland pointed to three main groups of utilities. The first is very small utilities that essentially have no operational technology (OT) such as supervisory control and data acquisition (SCADA) systems or Advanced Metering Infrastructure. Some of these smaller utilities, he said, do not even have websites or use e-mail. The second group is comprised of large utilities that have a well-developed OT/IT interface and staff dedicated to cybersecurity, many of which fall under the NERC, FERC, and Critical Infrastructure Protection (CIP) standards. The third group falls between these two groups. These utilities may have some distributed OT elements with communications such as SCADA, but do not have a great deal of dedicated expertise and often have disconnects between OT and IT systems with respect to managing their cybersecurity.
Echoing other speakers, Hyland said that APPA is working to encourage a culture of cybersecurity across this broad spectrum of electric utilities, but cautioned that it will be a challenge. Due to resource constraints, some utilities struggle to fully adopt a culture of safety or a culture of reliability, and changing the way people think is never quick or easy. To offer tangible support to help utilities strengthen their recovery and resilience capabilities, APPA entered into two agreements with the Department
of Energy (DOE). The Infrastructure Security and Energy Restoration (ISER) cooperative agreement, based on physical mutual aid agreements, is intended to help protect and reinforce physical infrastructure, while the Cybersecurity for Energy Delivery Systems (CEDS) agreement is aimed at bolstering protections on the cyber side.
Robert M. Lee, Dragos
Robert M. Lee, chief executive officer of Dragos, described the current threat landscape along with his concerns about common security practices in the electric power industry.
Lee argued that the threats to the U.S. electric power system are often underappreciated, especially by those outside the industry. Many simply do not realize how active the threat landscape is, how many nation-state actors are involved, and the degree to which U.S. systems are being targeted. While his firm deals with 2-3 major incident response cases per month stemming from activities by approximately 10 different nation-state actors, most are not publicized as is normal practice among those doing incident response. There are likely many more intrusions than are not detected, and of those attacks that are recognized, many are misunderstood. For example, Lee noted that when Symantec analyzed the Dragonfly cyberespionage attack in 2014, its report2 focused on the electric industry impacts while largely overlooking impacts in other industries such as mining, transportation, and petrochemicals, which belied the scope of the attack.
Lee noted that our infrastructure is largely safe and reliable due to the significant investment our utilities have made. However, he characterized some of the practices that utilities must follow either due to regulation or “best practice” frameworks as “feel-good” security that wastes resources by focusing too much on ineffective preventative activities. As an example, a significant number of vulnerabilities introduce no risk to utilities yet necessitate a significant focus on vulnerability mitigation. As another example, utilities must deploy antivirus software; while this is not necessarily bad, it does not provide the same value in industrial and operations networks as it does in the context of enterprise networks. Lee said that many of the recommendations to utilities have been based on extending the enterprise security strategy instead of developing a unique and tailored strategy for the operations technology networks. While utilities are not to blame for this, as it was accepted practice for years, Lee argued
___________________
2 Symantec Security Response, 2014, “Dragonfly: Cyberespionage Attacks Against Energy Suppliers,” https://paper.seebug.org/papers/APT/APT_CyberCriminal_Campagin/2014/Dragonfly_Threat_Against_Western_Energy_Suppliers.pdf.
that practices should change now that the weaknesses of this approach are better known. On the positive side, however, Lee noted that effective defensive cybersecurity mechanisms are available and, when implemented properly, they work well.
Lee noted that, in contrast to decades past, security expertise today is concentrated in the private sector rather than in the government, a shift he attributed to cooperation and partnership between government, which was focused on cyber security earlier than industry, and the private sector over the years. When Congress and others seek to determine best practices and insights on the problem, Lee suggested that they should first look to the security practitioners at leading utilities now. While it is valuable to have this expertise within industry, it is important to note that industry is in the beginning phases of this transition and that today still too few companies undertake a root-cause analysis after an incident to determine if there was a cyber component to the issue or not. As a result, it can take too long to determine if a crisis is created by an attack or by a defect, giving the adversary a second chance to attack, as happened in the 2017 TRISIS/TRITON attack in Saudi Arabia. In that incident, the XENOTIME adversary purposefully tried to kill people by targeting a Safety Instrumented System; the attack was originally erroneously diagnosed as a maintenance issue.3
By contrast, root-cause analysis couples incident response with protections and practices that are implemented from the get-go. “We have to think about the response strategy first,” said Lee. “That response strategy is going to drive the detection strategy to get there, and that’s going to drive the collection and preventative strategy we want to put in place.”
Lee commended current efforts to address this need, including the CEDS agreement, the Roadmap to Achieve Energy Delivery Systems Cybersecurity, and the Neighborhood Keeper program,4 a collaboration between Dragos and DOE. Ultimately, to best protect our energy infrastructure, Lee asserted that it will be essential to simultaneously learn from the threats by adopting an intelligence-driven approach while also designing a better infrastructure that reduces the threat landscape and the attack surface, an approach being advanced by efforts such as the DOE Consequence-Driven Cyber-Informed Engineering program.
___________________
3 For more information on the TRISIS attack, see Dragos, TRISIS Malware: Analysis of Safety System Targeted Malware, https://dragos.com/wp-content/uploads/TRISIS-01.pdf, accessed February 20, 2020.
4 For more information on the Neighborhood Keeper program, see Dragos, “Neighborhood Keeper,” https://dragos.com/neighborhood-keeper/, accessed February 20, 2020.
Discussion
Participants discussed current vulnerabilities, the use of tools and models in this space, and the need for partnerships to address cybersecurity challenges.
Understanding Vulnerabilities
Granger Morgan, Carnegie Mellon University, asked panelists to comment on vulnerabilities posed by legacy infrastructure such as outdated operating systems and unprotected wireless networks. Lee answered that the risk posed by the ongoing use of legacy equipment has been somewhat overplayed, and what is more important is not what operating system is running, but whether utilities can accurately detect attacks and respond to them.
Gavin Donohue, Independent Power Producers of New York, Inc., asked if the cyber operations side has focused on being “prepared to fail” to the same degree that the electricity subsector in general has done. Hyland replied that more education and preparation is needed, and Harrell stressed that grid failure exercises including cyber threats are a valuable learning exercise for these efforts.
Tools and Models
Mark Lauby, NERC, asked about the status of efforts to build simulation tools, models, and risk assessments. Sanders pointed out that while researchers cannot model what is not understood, there are models available that could be scaled up, tested, and used for planning exercises. Hyland agreed, although he noted that while utilities are familiar with the impacts of weather, animals, and other everyday problems, more research is needed to characterize and model malicious attacks. Harrell added that vendors should play a more integral role in these modeling and planning efforts in order to better integrate security into systems.
Lee answered that despite the unknowns, good modeling exists for predictable scenarios and their secondary consequences. In the face of uncertainty as to the optimal amount to invest in cybersecurity, he emphasized that utilities should at a minimum be prepared to respond to known scenarios such as ransomware attacks and the events in Ukraine in 2015 and 2016. He added that there is a lack of a combined voice advocating for using these tools and stressed that a successful solution will rely on a combination of people, process, and technology.
Michael Howard, Electric Power Research Institute (EPRI), wondered if an artificial intelligence (AI)-based approach could be used to detect
and prevent insider threats in the future. Harrell noted that it is not possible to eliminate every threat, but a vigilant threat management program that includes human resources, operations, physical security, legal, and technological means—all of which exist today but are not fully implemented—could be the most successful at detecting suspicious internal activity.
The Need for Partnerships
Hyland emphasized the need for public-private partnerships (PPPs) that include R&D to create new technologies for the grid. Big or small, utilities cannot meet all of the needs alone, he argued. Lee agreed and pointed out that many of the technologies mentioned—such as detection capabilities and prevention strategies—already exist, while some that get advocated as a key to success, such as AI and blockchain, have not yet been shown to deliver value in security.
Jeffery Dagle, Pacific Northwest National Laboratory (PNNL), asked what, specifically, PPPs should be studying. Lee suggested that they deemphasize things that industry is good at, such as incident response, and focus instead on broader needs, such as supply chain security. Hyland praised the partnership that enabled APPA to create a scenario modeled on the attack on Ukraine’s electric grid, which municipalities can use to see exactly how much an outage would cost in relation to cybersecurity investments. Harrell added that PPPs also excel at pushing timely, accurate information during crises; as such, they could play a part in securely disseminating information to the right players within government and industry.
EMP AND GMD CHALLENGES
- Although less likely than cyberattacks, GMD and EMP events pose serious threats to grid infrastructure and operations.
- Existing standards, detection capabilities, and mitigation strategies provide some protection against these threats.
- Further research and implementation are needed to better understand the risks and increase resilience to catastrophic events.
Michael Howard, EPRI, set the stage for a panel on challenges related to EMP and GMD events, with a brief discussion of the nature of these events. An EMP is a man-made event resulting from a high-altitude nuclear blast. It has three components: E1 (an intense electromagnetic field occurring within nanoseconds of a nuclear blast), E2 (an intermediate duration pulse, lasting from about one microsecond to one second
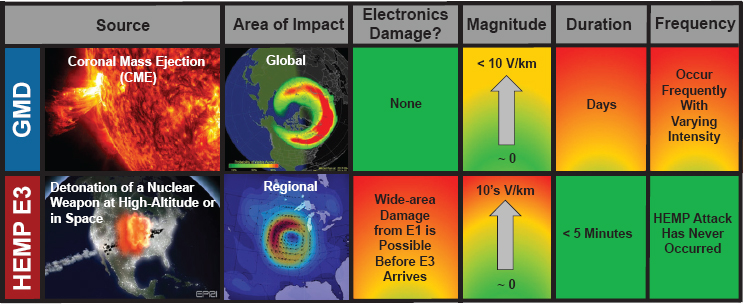
with an intensity similar to a lightning strike), and E3 (a pulse lasting tens to hundreds of seconds whose effects are similar, although not identical, to the effects of a GMD). A GMD is a natural event created by activity on the sun, specifically a coronal mass ejection (CME). While both types of events can have serious impacts on the electric grid, they differ in their spatial range, magnitude, duration, frequency, and impacts on electronics (Figure 2.1).
Howard introduced the speakers and moderated an open discussion following their remarks. Speakers included John Kappenman, Storm Analysis Consultants; Mark Lauby, NERC; and Randy Horton, EPRI.
John Kappenman, Storm Analysis Consultants
John Kappenman, founder of Storm Analysis Consultants, emphasized the vulnerability of today’s grid to GMD and E3-EMP events (E3-EMP, the slow pulse component of EMP, is similar to naturally occurring GMD events). The bulk transmission network has been growing more vulnerable to these threats for many decades for two important reasons, Kappenman said: The development and growth of extra-high-voltage networks, which allow larger geomagnetically induced current (GIC) flows, and the usage of single-phase transformers on these same networks that are more easily saturated by GIC flows. These combined design decisions have unintentionally increased the potential impacts of EMP and GMD events on grid infrastructure and have been unchecked by a rational design code that took this threat into consideration, Kappenman said.
Kappenman added that, for the fast pulse E1-EMP, the increased reliance on electronic-based controls and devices that have replaced older style electromagnetic relays and control systems in the electric grid has greatly increased vulnerability to this threat. The E1-EMP could disrupt operation and permanently damage distributed electronic control systems used in SCADA across the bulk transmission network, in distributed control systems in power plants, and even within critical end-user systems.
Kappenman noted that both severe GMD and EMP threats will have large geographic footprints of continental scale and could impact most of the bulk electric grids simultaneously across North America.
GMD threats are not purely theoretical: In 1989, a solar storm caused a grid collapse in Quebec, Canada, with intensities of about 400 nanotesla per minute,5 and scientists estimate storms could be 4-10 times more intense. Taken together, the design of today’s system combined with the likelihood of future GMD events creates the potential for widespread catastrophic failure involving unprecedented blackouts and permanent equipment damage affecting a large portion of the country. “Given sufficient time, the reoccurrence of a large storm event is a certainty—and it’s probably going to come with much more serious consequences than we’ve had in the past,” Kappenman said.
In regard to EMP, Kappenman emphasized that many critical state-of-the-art control systems utilized in power plants and SCADA are restricted from being exposed to electric fields from cell phones, which have an output in the range of 1-3 volts per meter (V/m). By comparison, the E1-EMP pulse field strength can be as high as 50,000 V/m, a level that would not only disrupt sensitive control system operation but that is also likely to cause widespread permanent damage to many of these electronic-based systems and hamper the ability to rapidly restore critical infrastructures necessary to sustain lifeline services to the population.
Due to the large geographic footprint of EMP events, even a regional EMP E1 event could expose thousands of substations and generating plants across the U.S. grid’s infrastructure at once. Unfortunately, this vulnerability both invites and rewards attacks. To reduce this vulnerability, Kappenman suggested targeting skeletal portions of the existing power grid that could provide at least limited lifeline support in a post-EMP attack scenario. For construction of new facilities, newly developed radio frequency-absorbing shielding concrete and new designs for protective control buildings could be used to encase and protect sensitive electronic infrastructure with minimal additional costs over previous designs, he said.
___________________
5 The tesla is a unit of measurement for magnetic fields. One nanotesla equals one billionth of a tesla; Earth’s magnetic field is in the range of 25,000-65,000 nanotesla.
Protecting our infrastructure will require balancing costs and efficiencies, but maintaining the capability to rapidly restore operations and support basic lifeline services in a worse-case scenario is essential, Kappenman concluded.
Mark Lauby, North American Electric Reliability Corporation
Mark Lauby, senior vice president and chief engineer at NERC, discussed NERC’s work on creating GMD and EMP protection standards.
NERC has mandatory GMD reliability standards, developed in partnership with government, industry, and academic experts. As zero risk is impossible, the goal instead is to minimize risk, Lauby said. The standards include mechanisms for understanding potential attacks, practicing risk assessments, and creating action plans for various scenarios.
NERC is also in the process of developing an EMP strategy, based on EPRI research. A task force is identifying vulnerabilities, reliability concerns, and resiliency methods. The next step is to seek input from government, industry, and researchers and incorporate ideas for response and recovery.
Randy Horton, Electric Power Research Institute
Randy Horton, senior program manager at EPRI, described a recently completed 3-year study6 that his team conducted on how to best respond to and mitigate a high-altitude EMP (HEMP) event. The project, a collaboration involving 63 U.S. utilities, DOE, the U.S. Department of Defense (DoD), and several national laboratories, sought to identify the impacts of a HEMP attack on transmission systems (switchyards, lines, and substations) and identify the most cost-efficient protections to implement.
While the team considered impacts of all three HEMP components (E1, E2, and E3), a significant portion of the research focused on E1 HEMP impacts. Team members developed computer models to estimate anticipated stress levels to compare against the strength of existing equipment; where data were not available, such as for digital protective relays, they conducted laboratory tests to fill knowledge gaps. Their findings indicated that some equipment, such as relays, were fairly resilient to a free field E1 HEMP pulse, but conducted surges—for example, the voltage and current surges that can be generated by the coupling of the E1 HEMP pulse into a control cable—pose a greater threat. Using low-voltage surge protection
___________________
6 Electric Power Research Institute, 2019, High-Altitude Electromagnetic Pulse and the Bulk Power System: Potential Impacts and Mitigation Strategies, EPRI Technical Report 3002014979, Palo Alto, Calif.
devices and filters, shielded control cables, and enhanced grounding and bonding practices could help mitigate this risk, Horton said. Improving the shielding of substation control houses is also recommended and can help mitigate any potential risk from free field E1 HEMP.
For the project’s second phase, the team is working with 19 U.S. utilities to develop tailored risk and impact assessments and then install and test mitigation solutions. They hope that this effort will not only benefit the involved utilities but also provide valuable data on costs and maintenance needs, Horton said. Noting that transmission impacts are only one part of the puzzle, Horton added that EPRI is also examining interactions and sharing information with other infrastructures, such as telecommunications, which could also be affected by a HEMP attack.
Discussion
Panelists and attendees discussed priority areas for further research into EMP and GDM events and opportunities to improve protection and response capabilities.
EMP Research Needs
Recognizing that it is impossible to fully defend against EMP attacks, Kappenman suggested that future work should focus on building better protective spaces, based on better design standards, that incorporate visionary approaches such as shielding concrete. Lauby stated that better EMP protection will come from more reliable wavefront information. He also suggested expanding the research scope beyond transmission systems into generation and distribution impacts, and even, Horton added, into interactions with other critical infrastructures. To support these efforts, Horton and Lauby agreed that industry and utilities need to have access to high-quality EMP-E1 assessment tools, as well as the expertise to use them.
GMD Research Needs
On the GMD side, Kappenman stated that better GIC measurements are needed to increase understanding of the complexities surrounding ground conductivity to depths of hundreds of kilometers. Participants pointed to research being advanced by the American Geophysical Union as relevant to improving knowledge in this area. Lauby, Kappenman, and Horton added that GMD research should also zero in on transformer thermal impacts, given their potential for catastrophic consequences, including to public health.
Improving Capabilities
Jeffery Dagle, PNNL, asked whether utilities have the capability to proactively take precautions when GMD events are approaching that exceed the magnitude their systems were designed to withstand. Lauby replied that every utility has an emergency operations plan to pre-position systems, and that includes restoration plans for unpredictable events. Kappenman added that while transformers have resiliency standards and ratings, many fall short of these standards in practice, making transformer failure a real possibility. In addition, he noted that there remain gaps in our understanding of how GMDs occur and how large and how long they can be, raising the troubling prospect that the true threats may go beyond what is captured in existing models. The more data that is uncovered, released, and studied, the better utilities can prepare, he said.
In response to a question by Mark Adamiak, Adamiak Consulting, panelists agreed that more solutions could evolve from available and emerging technologies, such as GIC blocking devices and other possible mitigation actions.
Cynthia Hsu, National Rural Electric Cooperative Association (NRECA), asked about the lifespan of existing GMD detection infrastructure in space and whether additional or replacement monitoring satellites are needed. Lauby agreed that better equipment for advanced detection was necessary, particularly to reduce false positives, but noted that existing equipment is tested on a regular basis. Horton stated that more descriptive measurements of the storm—estimating the electric field on the ground that determines the impacts, rather than only the K-index of the storm’s impact on Earth’s magnetic field—would be helpful. Kappenman added that satellites to measure GMD are single-point-of-failure machines, operating in the harsh space environment, and so are not fully reliable.
NATIONAL SECURITY IMPLICATIONS
- The electric power system is vital to U.S. national and economic security.
- The electricity subsector is enmeshed within an ecosystem of interdependent infrastructures.
- A holistic approach that accounts for the current and future threat landscape and the different roles and capabilities of government and industry could help improve the defensibility and resilience of the U.S. electric power system.
Morgan introduced a panel and moderated a discussion on national security implications of cybersecurity threats to the electric power system.
The speakers were Caitlin Durkovich, Toffler Associates; Paul Stockton, Sonecon, LLC; and David Batz, Edison Electric Institute.
Caitlin Durkovich, Toffler Associates
Caitlin Durkovich, director at Toffler Associates, discussed the importance of critical infrastructure to our national and economic security. Any disruption, from a weather event or a deliberate attack, could cascade across sectors and have significant consequences. Durkovich argued that the stakes have risen as infrastructures grow more interdependent and our adversaries look for opportunities to cause widescale disruption. “The security and resilience of our country is becoming more intertwined with critical infrastructure than ever before,” Durkovich said. “We also know that nation-states understand and continue to get better insight into the importance of our nation’s infrastructure to our national security and our economic security.”
To better protect our electric power grid and design systems that are secure, resilient, integrated, and modern, Durkovich outlined her vision for a central “belly button” in the federal government that would be responsible for establishing an overarching strategy and the corresponding policies, authorities, and regulations to achieve it. While the private sector owns and operates the assets within this critical infrastructure, she asserted that the federal government should have a role in creating a roadmap for a modern infrastructure system, and that public-private partnerships could be a valuable mechanism for building security and resilience into electric power infrastructure from the beginning.
This new vision, she stressed, must also account for the initiatives, processes, sensors, and technologies being deployed in the shift toward “smart” communities, both in the civilian and military context. While acknowledging that some important steps have been taken, Durkovich expressed her view that federal policy needs to further encourage and enable the shift to smart infrastructure. “Current federal policy is not incentivizing a shift to a modern infrastructure, especially in the energy sector, Durkovich said. “I think that we have to move quickly if we are going to get this right.”
America’s adversaries are adept at pushing the boundaries of engagement without generating a kinetic response from the United States, Durkovich said, and it is apparent that nation-state adversaries such as Russia have the potential to infiltrate U.S. infrastructure with malware and other technologies and “lie in wait,” ready to act when tensions escalate. China’s theft of U.S. intellectual property and its integral role in our supply chain further underscore the threats from abroad. To counter these threats, she reiterated the need to establish a centralized group
authorized to formulate and implement a smart infrastructure strategy and suggested updating and continuing the work already ongoing under Presidential Policy Directive 21.7 She urged a renewed focus on foreign interference, improving understanding of risks posed by new technologies, and expanding our capability to anticipate decades into the future, not years.
Paul Stockton, Sonecon, LLC
Paul Stockton, managing director of Sonecon, urged taking a holistic perspective on the future of the grid in a national security context. While he believes that today’s bulk power system entities and mandatory standards have kept pace with past threats reasonably well, he argued that further evolution is necessary given the severity of today’s threats, particularly those posed by Russia and China.
Beyond the infrastructure that comprises the actual electric grid, there are many interdependent sectors that enable and support the electricity subsector that are often overlooked and less well protected, making them susceptible to attack. For example, natural gas is a critical fuel source for power generation, and an attack on those pipelines could disrupt power generation—an indirect but effective way to compromise grid reliability. Stockton noted that former Director of National Intelligence Daniel Coates said in the Office of the Director of National Intelligence’s 2019 threat assessment8 that China has the ability to disrupt the flow of natural gas in a transmission pipeline for days to weeks.
To address these gaps, Stockton suggested establishing a design basis threat (DBT) for the oil and natural gas subsector. This would give grid owners and operators, as well as regional transmission organizations and independent system operators, a shared understanding of the threats to design resilience initiatives against. This understanding would include lessons learned from nuclear power plants and grid DBTs for physical security threats.
Stockton added that another often overlooked area of potential vulnerability is the nation’s ability to conduct blackstart power restoration—that is, to restart electricity generation from within a blacked-out area, rather than by importing power from outside the area to restart generation assets. Utilities responsible for blackstart must comply with rigorous
___________________
7 Office of the Press Secretary, 2013, Presidential Policy Directive 21—Critical Infrastructure Security and Resilience, The White House, Washington, D.C.
8 D.R. Coates, 2019, Worldwide Threat Assessment of the U.S. Intelligence Community. Statement for the Senate Select Committee on Intelligence, https://www.dni.gov/files/ODNI/documents/2019-ATA-SFR–SSCI.pdf, accessed February 20, 2020.
training and simulation requirements. However, it is impractical for them to test blackstart operations under fully realistic conditions (i.e., by intentionally turning off parts of the grid). In addition, because many blackstart generators run on natural gas, they could be vulnerable to a disruption of gas supplies. This vulnerability represents another example of the challenges presented by hidden interdependencies in our critical infrastructure.
Stockton noted in closing that similar cross-sector dependencies exist for many other infrastructure sectors, including communications systems and water utilities.
David Batz, Edison Electric Institute
David Batz, senior director of cyber and infrastructure security at the Edison Electric Institute, delineated the different roles for government and industry in increasing the resiliency of the nation’s electric power system, and how each can best operate within its own “swim lanes” to do this more effectively.
The vast majority of the U.S. grid is owned and operated by private entities. Their job, and their expertise, is not to anticipate the nation’s war-fighting capabilities, yet they find themselves on the front lines of defending their operations against nation-state and state-sponsored adversaries. The government, Batz suggested, can support infrastructure security by providing faster, better, and more scalable mechanisms for information sharing; creating incentives for defense-critical security installations; and detailing response plans for when adversaries probe systems.
Funding is also a challenge. Resilience mechanisms cost money, yet today’s rate-making structures are on the whole insufficient to support adequate defense and resilience against today’s threats, Batz argued. He added that rate structures fail to account for the relative importance of different electricity needs, giving equal weight, for example, to a recreational ice-skating rink and to a military base.
To move forward, Batz stressed the need to diversify fuel sources, vendors, and suppliers across the U.S. electricity subsector and in particular underscored the need to provide adequate funding for nuclear facilities. In addition, he stressed the need for collaboration as researchers seek to increase resiliency. As an example, he pointed to the 2006 Spare Transformer Equipment Program (STEP), in which utility owners and operators collaborated with FERC to create a transformer-sharing program for physical attack recovery. The program required incremental cost increases, which were absorbed into utility rates. Batz suggested that similar approaches could be implemented elsewhere where a relatively small investment could bring big payoffs in terms of resiliency.
“Let’s broaden the aperture and think about where else within our critical infrastructure we can invest toward resilience and not in all cases drive toward the lowest cost,” he said.
Discussion
Attendees and panelists discussed challenges related to funding and the supply chain and identified suggestions for improvement more broadly.
The Need for Funding
Providing adequate funding to address national security threats related to the electric power system is a difficult balance, Morgan said. While customers and business structures in this subsector have driven prices ever lower, government financing or incentives run the risk of overcompensating and leading utilities to “gold plate” infrastructure unnecessarily.
Durkovich added that customers demand low prices, not better security. A public education campaign may help, but she contended that little will change until people are willing to pay more for a secure and resilient infrastructure.
Stockton agreed that consumers rarely prioritize security over low prices, and added that certain basic needs, like water, should be kept inexpensive. It may be possible, instead, to make a compelling economic argument for the utilities to invest in security—for example, by assigning a dollar value to resilient power.
Securing the Supply Chain
Jeffery Dagle, PNNL, asked how cybersecurity supply chain vulnerabilities could be reduced. Batz answered that securing the supply chain will require a complete risk management overhaul, with multiple components that enable operators to understand the potential threats at every layer. While some cybersecurity components, transformers, and protective relays are made in North America or Europe, he noted that heavy equipment and consumer products are largely made in China, which creates vulnerabilities.
Suggestions for Improvement
Cynthia Hsu, NRECA, asked what responsibilities for national defense and cybersecurity are falling through the cracks between efforts and missions across federal agencies and the federal government.
Morgan pointed out that while bulk power is regulated by the federal government, public service commissions operate at the state level in a complicated regulatory environment. He and Durkovich noted that state- and local-level critical assets will shoulder a significant share of the burden when serious problems occur and would benefit from more exercises in order to build their capacity to respond effectively. Hsu agreed that local and smaller, state-level infrastructures would benefit from cybersecurity exercises to improve communication and response capabilities.
From a broader perspective, Durkovich suggested that the government should reassess security priorities and counterthreat mechanisms, perhaps creating regime similar to the 2002 SAFETY Act, which encourages anti-terrorism technological innovations, for the energy sector. She also noted that government and industry are both facing workplace talent challenges that will affect how we build, maintain, and secure our infrastructure.
Stockton pointed to information warfare as another important and often overlooked threat. For example, pairing a grid attack with disinformation to sow public distrust in leaders could be more damaging than a grid attack alone. Durkovich agreed, positing that while our enemies get ever more creative and capable in terms of manipulating perceptions, the U.S. government remains too focused on the current risk landscape, to the detriment of its ability to imagine and plan for future threats. “The thing that I am concerned about is that we are so focused on today—are we doing enough to think about tomorrow?” Durkovich asked, reiterating her suggestion that the government fund a new entity that considers the whole spectrum of critical infrastructure and looks decades into the future, creating a roadmap not only for new technologies but also for new threats.
John Kappenman, Storm Analysis Consultants, noted that the grid’s dependency on natural gas, especially for a blackstart, has fallen through the cracks, and emphasized the need to find a different fuel source or create a national policy regarding fuel reserves during a crisis. Batz agreed that such an investment would improve resilience, as would creating a fully realized catastrophe plan that ensures sufficient reserves and reduces utilities’ dependence on “just in time” inventory.
Stockton pointed out that system tests and crisis exercises would be more effective if they considered the impact of infrastructure interdependencies, instead of focusing on just one sector. Anjan Bose, Washington State University, noted that better modeling and simulation tools are also needed, and Michael Howard, EPRI, added that there is also a particular need for tools to better understand the interactions between the multiple infrastructures. Durkovich agreed that simulation tools are important, but emphasized that it is important to recognize that no simulation can fully re-create a true crisis. The human element is essential, she added, because in a real crisis, nothing will go as planned.


















