6
Workshop Three, Part Two
OPENING REMARKS
Workshop series co-chair Ms. Deborah Westphal, chairman of the board, Toffler Associates, welcomed participants to the final day of the workshop series and provided an overview of themes that emerged in the previous day’s discussions. She described her observations about the many hidden risks and gaps in the Air Force’s digitization effort, including those related to the Air Force’s need to
- Consider energy at the tactical edge and an overall strategy for energy;
- Develop a strategy for semiconductors to leverage artificial intelligence (ai) and machine learning;
- Understand china’s digitization strategy, which includes data collection on citizens;
- Emphasize privacy, transparency, security, accessibility, and usability of data;
- Avoid using doctrine only to document past successes;
- Recognize risk without limiting future possibilities;
- Train and retain personnel;
- Fund the future instead of pay for the past;
- Address both the time to transition and the clash with old ways;
- Embrace partnerships in a contested environment;
- Determine who has decision-making authorities and how to speed up those decisions;
- Differentiate between enterprise strategies and operational strategies; and
- “Thaw the frozen middle” so that bottom-up innovations can flourish.
Dr. Marv Langston (USN, ret.), independent consultant, suggested that the Air Force adopt Andrew Stricker’s Digital Transformation Cycle to highlight gaps and opportunities. Mr. Alden Munson, senior fellow and member, Board of Regents, Potomac Institute for Policy Studies, expressed continued concern
about the Air Force’s cybersecurity challenges. Although the ideal system would have all of the data necessary to support Air Force operations catalogued in a digital archive with ready access, if it is not possible to implement capable cyber defenses, that type of architecture may not be feasible. Instead, the data may need to be partitioned with a firewall, behind which it is not possible to access the entire data set. Mr. Jay Santee (USAF, ret.), vice president, Strategic Space Operations, Defense Systems Group, The Aerospace Corporation, stressed that although the cybersecurity issue is important, it cannot be an excuse for inaction. The United States cannot afford to lose its ability to compete with the adversaries. Because much work is involved in securing and maintaining the desired infrastructure, he suggested that the Air Force hire contractors to govern and maintain the architecture. He underscored that the digital transformation is about process reform: processes have to collapse and change in the transition from document artifacts to digital artifacts. It is crucial to provide access to higher-quality information to make better decisions. To be successful, he continued, the Air Force cannot simply issue tools; it should let people create them. Gen. James (Mike) Holmes (USAF, ret.), senior advisor, The Roosevelt Group, explained that decentralized action is essential in a world where communications will be continually attacked; instead of having 1,000 people in an air operations center planning and executing operations, it is important to bring the data to the people at the edge and allow them to make decisions. This cultural shift is a massive piece of the transformation effort. Mr. Santee agreed with Gen. Holmes that the governance of who can make decisions at what level will be critical.
FUTURE CYBER AND ELECTROMAGNETIC SPECTRUM ISSUES: A PANEL PRESENTATION
Col. Lisle Babcock, former LeMay Center Commander, emphasized that if the Air Force focuses only on digitizing cyber capabilities, it could miss an important opportunity to use electromagnetic spectrum (EMS) capabilities to gain superiority.
He explained that in 2019, the LeMay Center was tasked with writing doctrine for joint all-domain operations, which was the first time the Air Force adopted a forward-looking perspective for doctrine. The goal of this effort was to consider how the force could be deployed 3 to 5 years into the future, and to look across all domains to find a way to converge and bring kinetic and non-kinetic effects to bear at the edge of the fight. The next step was to consider the expected loss of communications in a contested environment with a peer adversary and how AI and mesh networks could be used to bring available data to the right people at the forward edge to execute commander’s intent. He referenced Gen. Charles Brown’s intent to use doctrine to change the culture of the Air Force—breaking the paradigms of centralized control and centralized command; expanding pipelines of communications for cyber capabilities; and training flight, group, squad, and wing commanders to make decisions without additional command and control communications and based on the risks to force and mission and available data. Delegating control of both assets and authorities is key to success in a contested environment. He said that Gen. Brown also stressed that recording ideas on paper is insufficient; people have to be trained differently.
Col. Babcock remarked that a true digital culture promotes external versus internal orientation, comprises delegation of control, encourages boldness over caution, emphasizes more action and less planning, and values collaboration over individual effort. These five elements tie into the joint all-domain operations doctrine as well as to Air Force Doctrine Publication 1, which discusses mission command, centralized planning, and decentralized execution of capabilities. A culture change is also needed in teaching, executing, and exercising capabilities within the Air Force, he continued, so that airmen are prepared to fight in a contested environment.
Col. Babcock asserted that accessing exquisite information and delegating control for decision making requires using the full spectrum of the EMS to revive data and relay them between the Air Operations Center (AOC) and the forward edge. He reiterated that the Air Force will lose the fight if it focuses only on networks and frequency ranges for cyber capabilities, without consideration for the entire EMS as a capability. In 2019, HAF A5L was stood up to serve as the EMS Superiority Directorate within HAF A5.
This group is considering how to build a software-defined radio capability that would “plug-and-play” with all current systems. This digital radio would link to major communications and provide data in real time, and enable a quick hop rate through multiple frequencies to avoid jamming or exploitation by the enemy.
Ms. Westphal asked how Air Force Futures could provide more value in the 10- to 15-year time frame. Col. Babcock described a symbiotic relationship between the LeMay Center and Air Force Futures. Because the LeMay Center tends to focus on a 3- to 5-year outlook and Air Force Futures focuses on the 5- to 20-year outlook, Air Force Futures is reviewing the LeMay Center’s lessons learned. Rear Adm. David Simpson (USN, ret.), chief executive officer, Pelorus Consulting; partner, Deep Water Point; and professor, Virginia Tech, pointed out that with the increased use of AI and airpower to respond to threats at machine speed, human-impacting decision operations will shift, with the human contribution to the OODA (observe, orient, decide, act) loop occurring weeks, months, or years in advance. He proposed that senior leaders shift similarly and focus on the data collection plan, the inference bias being generated, whether new threat observations from the adversary have been employed to adjust algorithms, and whether the AOC is responding to the trend to have more unmanned aviation in the battlespace (for which the algorithm will predetermine a response). Col. Babcock replied that expert adjudicators in the LeMay Center’s Wargames Center discuss what war could look like in 2035. The vision for the OODA loop is transitioning from human-in-the-loop to human-on-the-loop, to ensure quality and accuracy of algorithms. This new vision can only be achieved, however, if people trust machine learning; this will lead to buy-in from warfighters on the forward edge, and then the “human on the loop” could eventually reduce involvement further. He anticipated that the AOC will serve as a “fuser” for all of the individual operating areas and as a manager for the battlespaces. He noted that the forward edge leader should be able to assess risk, make a decision, and continue to operate until told otherwise. However, senior leaders have to be trained to be comfortable with empowering subordinates, as this is a substantial cultural shift for the Air Force.
Brig. Gen. Greg Touhill (USAF, ret.), director, Software Engineering Institute (SEI) Cybersecurity Division, underscored the value of the warfighter’s perspective in digital transformation. Encryption and cryptography are becoming more important, and quantum computing continues to show promise for the future. However, the Air Force’s current encryption and cryptography capabilities are “elderly” from an Internet-age time frame. He stressed that the Air Force needs to increase its investments in encryption and cryptography to improve its cybersecurity posture.
He described rapid advancements in AI and machine learning—for example, robotic process automation (RPA) is being implemented across business functions that underpin the warfighting capability in the Air Force, and throughout the government and industry more broadly. There have also been developments in robotic coding. As a result, SEI is focused on “fuzzing”: checking the code that is developed by machines for error and correction using AI capabilities. He cautioned that adversaries are using the same AI capabilities for automated polymorphic malware development. There has also been an increase in the employment of robo-hackers in the commercial sector, and he expressed concern that this technology could be used lethally by adversaries on the battlefield to interfere with operations. However, the U.S. military has experienced substantial advances in autonomous systems that could be useful in contested environments, and those systems will continue to evolve. Other nation states and commercial enterprises are also investing in autonomous systems.
Brig. Gen. Touhill also expressed concern about the “suspect supply chain” (e.g., What is in your code, who is in your code, and where did your code come from?), and he noted that the U.S. government does not have a firm understanding of the provenance of its code. There has been a significant amount of software reuse among commercial products over the course of decades. Although difficult to create, he advocated for a software bill of materials. Because the risk surface is so vast (e.g., firmware, operational technology, Internet of Things devices, weapon systems, embedded systems), the Air Force needs to increase its aperture as cyber risk is assessed with the supply chain of software. Another area of concern is cloud security. Migration into cyber clouds is drastically increasing and has essentially become a business imperative throughout the defense industrial base, industry, and the military. Thus, he continued, it is critical to ask the following questions about cloud security: Who is on the virtual machine next to me? Who is on the container next to me?
Dr. Langston questioned why the Air Force is not taking advantage of quantum technologies. Brig. Gen. Touhill said that although there is movement toward practical applications for quantum, it is still in the very early stages. A higher level of maturity in the technical stack is needed to build reliable applications. However, because the curve is accelerating quickly, he suggested that the Air Force invest in the technologies and be aware of how adversaries are investing in them.
Brig. Gen. Touhill turned to a discussion of zero trust, which he defined as a security strategy, not a product. Zero trust is a starting point in which breaches are assumed and trust has to be earned; a person only has access to particular content based on specific authorization. Using the Office of Personnel Management (OPM) hack as an example, he explained that organizations often fail to understand their own data. Unclassified OPM data were deemed unimportant, without consideration for the sensitivity of those data. OPM did not understand who owned the data, how the data were hosted, or who could access the data; and rules about who should see the data were not defined. He described this as an ongoing challenge across the military. As Air Combat Command leads a zero-trust initiative for the Air Force, it is important to understand the data: where they are, who owns them, who should access them under what conditions, and how they are managed. He asserted that zero trust is a critical component of national security and prosperity as the Air Force moves forward.
Ms. Westphal pointed out that understanding data requires insight about supply chains. Brig. Gen. Touhill replied that the scope and scale of the products, hardware, goods, and services create a difficult problem, but random sampling remains one of the best practices. Additionally, when companies ask third-party providers for data feeds from robotic process lines, it is possible to plug-in to some of the AI capabilities to evaluate the consistency and quality control of some of the product lines. He said that this use of machines to check machines will likely become more prevalent. Mr. Munson added that in the case of SolarWinds, penetration of a small company represented a major compromise for the nation. He asked if the supply chain problem should be treated as a major threat to national security. Brig. Gen. Touhill responded that the supply chain is a whole-of-government issue, and a government-private sector partnership could begin to address the problem.
Brig. Gen. Touhill’s final topic of discussion was the value of the EMS. He explained that the “untethered world” of mobility and various devices has provided excellent capabilities but has also presented extreme risk. The U.S. military’s outdated cryptography and encryption technologies continue to be employed throughout the fielded forces because there is a misplaced perception of legacy system security. He added that cyberattacks are under way, but the Air Force does not have methods to address an adversary attacking the EMS. He emphasized that as space-based intelligence, surveillance, and reconnaissance and communications platforms become critical elements of the warfighting capability, it is important to pay attention to how cyber and the EMS are connected, and to allocate resources to protect the EMS.
Dr. Langston wondered why there are no “hide-in-plain-sight” efforts for software-defined networking. Brig. Gen. Touhill said that networks are now at the level of people and their devices. A challenge for the future is to leverage technologies (e.g., software-defined perimeter) to burn through the contested cyber environment while maintaining a measure of mission effectiveness. Dr. Langston suggested applying resources that are being wasted on outdated technology. Brig. Gen. Touhill noted that although the interrelated mesh is very capable, there are still ways to take it down. It is important to maintain some independence as well as a dedicated communications capability with multiple layers that is resilient by design.
Mr. Steven Hernandez, Chief Information Security Officer, U.S. Department of Education, opened his presentation with a discussion of the threat scape in the federal civilian space. He explained that the adversary continues to be impressive in its ability to automate, orchestrate, and defeat U.S. defenses. When building these defenses, every “brick” in the “wall” has to be placed correctly; an adversary only needs to find a single gap in the construct to gain access. Compliance with security standards is also critical. While there is an increased demand for red teaming exercises, he pointed out that these efforts are only as effective as the expertise involved. Even though a red team may clear a system, it does not mean the system is completely safe; it just means that a particular aspect of expert knowledge has been exhausted. To address
this issue, he rotates his red teams every year or every quarter. He reiterated that the threat fully understands that only one weakness needs to be identified to establish a presence. With the increasingly blurred line between the personal and the professional lives of warfighters, there has been an increase in the number of attacks that leverage warfighters’ personal information for use against the government. He asserted that as a result, an identity management framework is needed to help warfighters understand the role of identity and its relationship to ensuring the protection of U.S. systems and missions.
Mr. Hernandez noted that disruption is the new currency for attackers, most often emerging via ransomware. He discussed a devolution of communication—for example, soldiers who have to buy local cell phones and download What’s App just to complete a mission. He emphasized that warfighters should have secure and assured services when and where they need them. However, when this is not the case, it is essential to have a mechanism to secure communications on commercial civilian technology. He also described today’s secure, encrypted traffic as the “decrypted fodder” for tomorrow’s quantum computers. It is important to think about the type of information being sent, the type of encryption being used, and what quantum means in terms of risk when it becomes powerful enough to break modern encryption technologies.
Mr. Hernandez turned to a discussion of federal initiatives to build more resilient defenses, noting a disconnect between vendors’ proposed security and the reality. For example, although 5G has security capabilities, because they are rudimentary and do not integrate well with other security technologies, 5G remains an untrusted network. He remarked that having access to high quality data is important. Although data do not need to be located in one place, visibility of the data across the data ecosystem is key to decision making. The Office of Management and Budget (OMB) Memorandum 21-31 creates a foundation—fidelity, robustness, and visibility requirements—for data logging. After the SolarWinds breach, OMB Memorandum 21-30 was released to ensure that it is possible to identify critical software assets throughout an enterprise as well as who has enterprise-level visibility.
Mr. Hernandez explained that the current federal civilian estimate for funding shortfall in cybersecurity is approximately $9 billion. In the Technology Modernization Funding for 2021, Congress allocated $1 billion, for which the agencies can compete. This funding approach helps determine how to release legacy infrastructure constructs because it provides an infusion of cash for acceleration of IT modernization, especially for those projects that push toward new security architectures and better civilian-facing services. For instance, his department is 100 percent cloud-based, and many other federal agencies are moving in that direction. The Cybersecurity Infrastructure and Security Agency (CISA) recently released a draft secure cloud migration document that will be used by federal agencies in an effort to establish trust. CISA has also released a maturity model for zero trust, with different capabilities at various levels. It can take decades to achieve a mature digital trust architecture: zero trust is a lifestyle and a journey, not a destination. Organizations with a strong credential access management approach and a strong data approach are now focusing on the control plane with Secure Access Service Edge as an intermediary step (i.e., agile, flexible edge in the cloud through which services are accessed; and always-on encryption) and with Security Orchestration, Automation, and Response (i.e., robotic processes, automation, algorithms, and rules are taking immediate action based on real-time observations by redefining a software-defined network, establishing a new perimeter, or moving traffic to a honeypot). In closing, he highlighted areas in which the Air Force is succeeding: the foundation for a zero-trust architecture has emerged but will continue to evolve, and Platform One has helped build foundational capabilities for DevSecOps. He encouraged the Air Force to continue to expand those efforts.
Open Discussion
Dr. Langston suggested the use of automated penetration testing, and Mr. Hernandez noted a distinction between automated vulnerability discovery and penetration testing, which would rise to the next level of exploitation. He commented that automated penetration testing is effective in that it serves as a stop gap
and in some cases has a human element, in which discovered vulnerabilities are passed to researchers. However, a significant amount of trust in the vendor is needed for this approach.
Mr. Munson observed a vulnerability around the Air Force’s commitment to encouraging small companies to offer products. Often, the cyber defenses of these small companies are limited owing to scarce financial resources. He wondered how to continue to encourage these companies without accepting the cyber vulnerabilities that might accompany them. Mr. Hernandez responded that if the government wants high-assurance systems and platforms, it has to be willing to invest in those spaces when they are critical to the mission.
Dr. Rama Chellappa, Bloomberg Distinguished Professor of electrical and computer engineering and biomedical engineering, Johns Hopkins University, said that the cybersecurity community is already worried about the potential vulnerability of a deep learning system that has not been implemented on a wide scale. Mr. Hernandez remarked that deep learning is siloed for the federal government. He added that it is not the concept of deep learning that is challenging; it is the capabilities of the vendors and how they can be applied across the enterprise. The important challenge now is to work on high-assurance data and data visibility so that deep learning has something to view. Brig Gen. Touhill explained that among the many types of data (structured data, unstructured data, semi-structured data, and metadata) throughout the life cycle, the three key foci are (1) data integrity (accuracy and completeness), (2) data quality (readable and compliant with organizational requirements), and (3) data security (unaltered). These three components are especially important in deep learning environments. He asserted that “Grade A” data and a “Grade A” process leads to “Grade A” conclusions.
Ms. Westphal asked if the EMS is an area of future conflict and whether technology development is enabling its more efficient use. Brig Gen. Touhill emphasized that the EMS is already a contested space: there is much congestion and demand for bandwidth, and there is a drive for competitive advantage, ongoing espionage, and leverage of the EMS for collection and gathering. Col. Babcock explained that China and Russia are leveraging ultra-high frequency technologies. However, ultra-wideband technology, which has been in existence for two decades, is used infrequently even though it enables the use of a larger portion of the spectrum at a lower threshold. Some technologies will require additional support from the commercial sector, but it is important to use and leverage existing technology to create a standard baseline across all capabilities. He underscored the need to change the culture of the administration, of capability development, and of the acquisition process, which has to become more streamlined and expeditious. Mr. Hernandez noted that the EMS will be available in the future in new forms. Starlink, for example, will likely become the premier data fabric for EMS. However, it is important to develop the right assurance and technology to leverage such a capability. Secure hardware development is also an important part of this discussion.
CREATING A SUSTAINABLE CAPABILITY FOR THE FUTURE: A PANEL PRESENTATION
Dr. Jake Sotiriadis, director of Operations and Engagement, Collaboration Laboratory and Research Faculty, National Intelligence University, said that the first part of digital transformation should be to determine whether the right questions are being asked and whether the entire range of possibilities is being considered. For example, even though the world is three- dimensional, senior leaders are still being given one-dimensional products to conceptualize complex issues. Another approach has been for everyone to coalesce around one vision of the future, which raises questions about an organization’s ability to move forward. To build new concepts and develop new strategies for digital transformation, he emphasized the need to become comfortable with being uncomfortable. He noted how difficult it is to predict the future: history demonstrates that most assumptions about the future have been consistently wrong. Therefore, he stressed that it is critical to think about alternative future scenarios and to question assumptions as part of a “cognitive operating system,” which is the systems-based approach to understanding interconnectivity and embracing analytic complexity in thought processes.
Dr. Sotiriadis posited that most people understand that digital transformation is a necessity to link antiquated platforms, make information ubiquitous, and overwhelm the adversary with thousands of kill
chains. He pointed out that the Air Force has to begin “trading in the currency of uncertainty” because it cannot operate with definitive conclusions. It is important to begin to ask how alternative futures defy accepted probabilities to affect baseline assumptions. Although it is clear that all systems have to be networked (e.g., the Advanced Battle Management System and joint all-domain command and control [JADC2]) to overcome the digital connection deficit, the cognitive operating system plays just as important of a role. He explained that using the processes of strategic foresight and future studies allows for anticipatory thinking, rather than reactive action. Many countries in Europe and Asia are mandating that policies that impact digital transformation and human capital investments go through a process of “future proofing” (i.e., considering alternative future possibilities in terms of potential response and investments or divestments). This approach requires harnessing weak signals and emerging trends in the current strategic environment without being hindered by bureaucracy. For example, he asserted that the OODA loop, which is an inherently tactical approach that informs operational culture, does not lend itself well to the great power competition or to macro-level problems. Given the difficulty that private sector organizations have in anticipating change and crafting preferred futures, a hierarchical and bureaucratic organization with short-term budget cycles such as the Department of Defense (DoD) will face even greater challenges.
He underscored the value of considering the costs of inaction: a digitally connected, networked lethal force would be cognitively irrelevant if this new type of thinking is not embraced. If the focus on the future continues to revolve only around technology, strategic opportunities could be missed. The organizations best postured to dominate in a world of disruptive change are those that can adapt, learn, and anticipate. He emphasized that the most useful statements about the future should initially appear to be absurd. Part of embracing the notion of strategic foresight in planning includes tapping into virtual and augmented realities for training and helping decision makers better understand and consider potential responses to alternative future scenarios. Once this type of thinking becomes the norm instead of the exception, a cognitive operating system emerges at the enterprise level. In the past, these types of “futures” initiatives have been designated to a single office; instead, a more comprehensive approach would be beneficial, including the position of chief futurist to coordinate efforts across defense, academia, intelligence, and the private sector. In closing, he stated that more intellectual diversity is needed in the Air Force, as well as an acceptance that a national security metaverse is imminent.
Ms. Westphal asked if the Air Force should focus on addressing its lack of diverse thinkers before building the futures capability. Dr. Sotiriadis replied that both avenues could be pursued in parallel. Having the futures capability established as well as having a champion for futures thinking at the enterprise level will attract external voices. And then having the right people in the right positions evolving the capability will attract additional diverse thinkers.
Dr. Eneken Tikk, executive producer at Finland’s Cyber Policy Institute, remarked that it has become costly economically, societally, and politically to be simultaneously a democratic society and an information society. She shared perspectives on cyber diplomacy and cybersecurity from different regions and countries.
First, she examined the perspective of the European Union, mentioning that even close allies have varied approaches to cyber operations. Europe has almost 100 percent connectivity, similar to North America. The Nordic countries, in particular, have very advanced information societies and have achieved a balance of dependence and resilience. However, these countries still confront challenges, in which parts of the population are so vulnerable that it becomes impossible for the government or military to defend them from threats. She noted that Europe does not perceive itself as a primary cyber operator or recipient of the use of military cyber capabilities. Europe has a high demand of administrative accountability for the development and use of information and communication technologies, and there are expectations of digital welfare states. There is also an expectation that the state guarantees that these services and solutions are reliable, trusted, and available. She explained that Europe has extraordinary privacy and transparency agreements, along with rigorous checks and balances, which limits the U.S./EU privacy shield. There are still conflicting attitudes across European countries toward more centralized cyber operations and the roles of cyber commands. There is also a strong pressure in Europe for the rule of law and for strict limitations
on cyber operations. This law-centric thinking, she continued, makes it difficult to justify policy-driven agendas.
Second, Dr. Tikk remarked, Russia is a very moderate information society; it is far from 100 percent connected and does not aspire to become an advanced information society. Yet, it has been successful in destabilizing the Western narrative that information and communication technologies drive societal and economic benefits. Russia has successfully demonstrated the vulnerability of democratic processes as ideal landscapes for international cyber insecurity. However, Russia has for the most part been protected from Western cyber operations and is less exposed to inquiries of accountability than Western nations. She said that every Western cyber operation reinforces Russia’s pursuit to convince the world that increased digital sovereignty and control over the national information space is needed.
Third, she shared the perspective of “Country N,” which encompasses the outlooks of several countries. She explained that the average level of Internet penetration across the world is only ~60 percent, but there are many countries with 90 percent and many others with far less. “Country N” has an understanding of potential vulnerabilities and costs related to technological capabilities, but connectivity and technology dependence remain important issues. There is little international law on “Country N’s” issues (e.g., capacity) and limited resources to deal with the issue independently. “Country N” is exposed to two different narratives—the Western narrative (the European Union and the United States) and the Russian narrative—and is pressured to choose between them. The Western problems of advanced capabilities and freedom of use are not well understood by “Country N.” However, “Country N” is relatively untouched by advanced capabilities and is open to less advanced capabilities.
Based on these three perspectives, Dr. Tikk asserted that the future of military cyber capabilities and the limitations of their use remains unresolved; the most advanced countries are often at a disadvantage, and the United Nations charter does not divide the world into “good states” (democracies) and “bad states” (authoritarian regimes). There is a high risk associated with advanced capabilities to prompt international or bilateral control, and questions remain about return on and direction of investment. In closing, she noted that the world’s technological capabilities are far less than those of Western societies, and the international community at large is increasingly becoming disconnected from these privileged countries. Thus, it is critical to consider both economic and political costs in discussions of digital transformation.
Dr. Julie Ryan, chief executive officer, Wyndrose Technical Group, asked how a country could identify a path forward in this situation. Dr. Tikk emphasized that the solution is different for every country. She cautioned against assuming that the most important agenda for one country would be the same for others. Western governments are increasingly disconnected from their own populations, which is especially problematic. Ms. Westphal wondered about the role of partnerships, especially in a contested environment, and Dr. Tikk stressed the value of alliances and cooperation but reiterated the need to think about cost. For example, a political tension has arisen because the United States and Europe have such different perspectives on privacy guarantees for individuals. However, political arrangements alone may not determine an outcome because there are still legal procedures to consider. The legal environment that may impose countermeasures to operations is no longer just an international issue; it is increasingly domestic. The more this affects populations, she continued, the more it affects industry or corporate actors, who can take action against U.S. policies or operations through domestic processes.
Mr. Patrick Sack, vice president and chief technologist, Oracle National Security Group, explained that Oracle supports organizations with the best and most trusted data to gain decision advantage. He said that with the evolution of cloud (which is replacing the need for organizations to have data centers behind their own firewalls and within their own perimeters), security is being taken seriously in commercial spaces for the first time.
He described cybersecurity as “asymmetric” because the attacker only has to be right once, while the defender has to be right always. With billions of dollars invested in cloud infrastructure and IT, and trillions of dollars invested in the sensitive content and intellectual property of cloud users, cloud providers have to think carefully about security. Therefore, cloud providers have many of the same concerns that the Air Force has about supply chains, security models, connectivity, insider threats, and trust. For example, because clouds are global and interconnected, disrupted communications on such a large network could be
catastrophic. He pointed out that cloud providers have a responsibility for this critical infrastructure, including the money, lives, and jobs at stake.
Mr. Sack noted that data centers are interconnected with compute and storage and with redundant high-speed communications all over the world. Although Oracle and Microsoft Azure are competitors, they have connected their data centers to prevent increased threats that could emerge when data migrating among multiple clouds traverse other customer networks. Having these dedicated pipelines that can be monitored provides more confidence for data security.
He observed that customers seek a simple way to install software, without the responsibility of needing to patch or secure it. Customers request high levels of isolation and data protection for their systems. Although customers desire the highest level of security, they also want to delegate some of the most critical parts of security to the cloud provider. At the same time, cloud providers worry about attack vectors from the supply chain, hardware, software, and operating systems. In particular, cloud providers are concerned about the integrity of hardware and software; in the world of zero trust, nothing is trusted and everything is verified. For example, it is important to validate system integrity and ensure that hardware does not contain counterfeit parts. Furthermore, Oracle cannot automatically trust its customers because it does not know how they will behave once on the systems. In addition to its continuous security processes, Oracle has processes that protect against customers’ data, processing, and access to infrastructure. This new approach is essential when hardware is reused. He emphasized that cloud providers have a responsibility to protect infrastructure and help customers establish better security practices so that their businesses can run smoothly and better decisions can be made.
Mr. Sack explained that many commercial customers do not have the level of expertise needed to understand their hardware, their operating system, or the way their architecture was connected. Many customers do not know how they are connected to the enterprise, to the Internet, or to other agencies. The cloud provider offers that level of expertise at each of these layers, with an understanding of offensive, defensive, and continuous monitoring perspectives of chip architectures. Cloud providers remain aware of executive orders around critical software to ensure that they provide their customers with the right information about software assurance. He pointed out that although encryption acts as a safeguard, it does not provide a safeguard forever, because quantum computers will be able to decipher encrypted information in the future. Because the National Institute of Standards and Technology has not settled on guidance for the use of quantum resistant algorithms, it is important to anticipate the future so as to be able to incorporate defenses—Oracle has a team focused on quantum capabilities. He cautioned that the transition to new cryptography algorithms could create an opportunity for customers to lose data, and cloud providers want to reduce that possibility.
Mr. Sack said that if the commercial cloud is not sufficient for the government, then it would not be sufficient for all of the banks and healthcare organizations, for example, that are currently using it. Cloud providers are investing billions of dollars to provide a level of security assurance so that customers can focus on their data. Of the six major cloud providers (Amazon Web Services, Oracle, Alibaba, Microsoft Azure, Google, and IBM) in the world, five are U.S.-based companies, which he described as a tremendous advantage for government partnership. Working together, it is possible to leverage investment dollars to improve the government and the world by raising the assurance level; having better insight into the supply chain, the software supply chain, and threats; and understanding how the cloud is being used by adversaries and nation states. He emphasized the need for trust in data, infrastructure, and algorithms, and confidence in the decisions they allow at a faster rate.
Given the prediction that 14 percent of the world’s carbon emissions will come from data centers by 2040, Ms. Westphal pointed out that environmental responsibility is becoming an issue of national security. She wondered how cloud providers consider the environmental impact of their growth. Mr. Sack replied that Oracle has a green initiative to rethink how it builds data centers as well as how power is produced for them. Ms. Westphal also asked how the Air Force could be a good cloud customer, and Mr. Sack suggested increased cooperation between the Air Force and the cloud provider to share cyber threat information. In response to a follow-up question from Dr. Pamela Drew, former executive vice president and president of information systems, Exelis, about customer best practices and challenges, Mr. Sack said that Oracle has
been working closely with the Air Force to bring data into a single data center, and to enable levels of compartmentalization with additional controls and networking. He noted that it is difficult for people to think differently, but learning occurs for both the cloud provider and the customer: Oracle has to learn new techniques, and the Air Force has to learn to trust new techniques. He added that risk management is a key aspect of the provider-customer partnership.
Mr. Munson asked if customers who have joined the Oracle cloud have significantly reduced their in-house IT staff. Mr. Sack responded that many customers who have moved to the Oracle cloud have reduced their IT staff’s amount of effort or reallocated their time away from mundane tasks assumed by the cloud, but have not reduced the actual number of staff. He emphasized that because Oracle has service-level agreements around the mundane tasks, it is held accountable for those. Instead of focusing on infrastructure security and software installation and patching, in-house IT staff can now focus on data security and analytics and outcomes. Mr. Munson expressed concern that those IT staff become less knowledgeable and more dependent on the cloud. However, Mr. Sack confirmed that because trust has to be established, most enterprise customers still want a level of insight into the way the cloud works. Mr. Munson asked how cloud providers were affected by the SolarWinds incident, and Mr. Sack stressed that Oracle was not affected because it builds its own software. Approximately 90 percent of Oracle’s work is within its own control. He added that there is a consortium of cloud providers who share threat information with one another in an effort to protect the industry as a whole. Mr. Santee inquired about the risk of storing data on-premises versus storing in the cloud. Mr. Sack noted that the safest approach is to store data more than once and in different places. Most enterprises now have more data in the cloud than on-site; this approach is safe, and the processing capability and cost outweigh some of the other risks.
A FRAMEWORK FOR DIGITAL TRANSFORMATION: PANEL ONE
Mr. Jason Brown, strategic cloud advisor, public sector, Google, explained that Google relies on zero-trust security, assuming that there is a breach in the network at all times. Google developed technology that depends on machine learning for device-level security to sweep the network in search of potential breaches. Because Google is a mobile organization, its level of risk for threats is high. However, he expressed confidence that Google is the most secure unclassified network on which he has worked.
Having served many years as a member of the Air Force, Mr. Brown described the military’s perception of risk as outdated; people often focus on the military’s tendency to be risk-averse, but the real risk is created by the military’s “technical debt.” Philosophies around perimeter defense, for example, are outdated risk frameworks. Technical debt is a challenge across DoD, the public sector, and the commercial sector, increasing risk for all.
He portrayed software and data as some of the military’s most impactful weapons. However, despite the destruction from ransomware attacks that has shut down entire enterprises, some still refuse to believe that data and software are being weaponized. He emphasized that because of the Air Force’s technical debt, it has been unable to fully understand the impact of COVID-19 on its ability to complete its mission, in terms of logistics and maintenance, operations, personnel, health data, supply chain, and training. For example, the A4 has more than 350 separate systems and databases, written in different codes, and the federal government has more than 12,000 operational data centers. Bad actors could easily take advantage of this environment. COVID-19 also revealed the fragility of the supply chain. The supply chain is being mapped for various weapons systems for several organizations and military units, and those data will feed simulations; therefore, it is critical to understand the level of resilience of these supply chains. He stressed that data are a strategic asset—data can reveal strengths and weaknesses of the United States and its adversaries, as well as serve as a source of deterrence. Technical debt could be reduced by taking an application programming interface (API)-first approach, he continued, which makes it possible to obtain data from one location and either move them to a data warehouse in a cloud environment or extract them for use. For example, the Air Force’s Project Brown Heron pursues data sources, brings them into a data warehouse, and reveals trends to answer difficult questions about readiness.
Mr. Brown asserted that although transformation is a lengthy process, several success stories exist. One case study of value is that of Delta Airlines, which used an API-first strategy. Delta was one of the latest Internet adopters and had siloes between its business areas, but in the late 1990s, Delta initiated a transformative warehousing effort, the Delta Nervous System. By 2019, Delta had $6 billion in profit and had reduced maintenance cancellations from 5,000 in 2010 to less than 100 in 2018. Delta was successful owing to efforts to modernize its enterprise software architecture. The Lego Company provides another useful case study. About 20 years ago, its supply chain was a disaster; the company had to redefine operations to apply discipline to the supply chain via digital transformation. It started with maintenance, then moved to human resources, and then to manufacturing. He emphasized that those who transform the fastest start with logistics, like maintenance, instead of starting with operations, which is a highly complex area. Logistics and maintenance also have a much higher return on investment. For example, when Kessel Run digitized a process, moving from planning on a white board to using an app, it saved 300,000 pounds of fuel per day.
In closing, Mr. Brown emphasized his passion for education. He championed the Air Force’s Digital University, which helps airmen to become familiar with technology or pursue commercial certifications. At Google, employees are encouraged and incentivized to upskill, which is a necessity as technology continues to evolve quickly. Upskilling is essential for anyone who has to make a decision around technical debt, not just for airmen on the front line, he continued. Whereas the A4 is spending ~90 percent of its IT budget to maintain existing systems and only ~10 percent on new systems, the private sector is spending 50 percent in each area. Thus, he underscored that the Air Force needs to adopt a different perception of risk as well as a better understanding of the technology needed to surpass its technical debt.
Dr. Langston asked if studies have been conducted to determine how much money the Air Force could save if it shifted its unclassified operations to Google. Mr. Brown replied that a recent Google study revealed that Microsoft has 85 percent of the public sector market (for Office and related products). Google has offered some government leaders a continuity of operations planning capability; several public sector agencies already use Google workspaces, but Google would like to do more business with the U.S. government. Dr. Langston also wondered why the Air Force does not store its unclassified data in a Google data center. Mr. Brown reiterated that Google is the most secure network on which he has worked. He described Google’s self-service culture—its internal search engine, MOMA, makes it possible to find information internally on almost anything, although there are different levels of access. As a result, Google employees rarely send attachments; instead, information is found via a link to a Google drive. Documents that are created at Google are called assets and are added as links to asset libraries, which enables information-sharing. He emphasized that these non-complex approaches are attainable for the public sector—airmen are already using this technology in their personal lives on a daily basis.
Rear Adm. Simpson supported Dr. Sotiriadis’s assertion that any useful statement about the future should at first appear absurd. He emphasized the need for the Air Force to change the way it plans, budgets, and executes. For too long, the Air Force has focused on China in terms of a peer-to-peer fight over the straits of Taiwan. However, China is planning for and investing in a different fight, which is for long-term advantage in the commercial global technology economy. Both Russia and China have been aggressively attacking U.S. routes of trust—essentially attacking democracy as an optimal way to organize a government and deliver for its citizens. If the United States believes that it is the “dynamism” from a capitalist economy of small business-led innovation that ultimately wins, he continued, it should be concerned that China may be executing to that strength, while the United States focuses only on the domestic supply chain. The United States is thus beginning to lose influence in the global market. He expressed concern that the United States is taking the wrong approach as the world shifts from the era of industrial manufacturing to the information era. He advocated for the United States to improve its relationships with international partners and allies instead of focusing only on U.S. supply chains. The signal the United States is currently sending to its allies is that it puts a premium on American products in an information economy where it wants to have global influence. In the past, the United States has been a leader in the global technology market because of trust from other nations, so it is not surprising that China and Russia are attacking that element of trust. He
stressed that it is important to evaluate the “trust cost” in addition to the monetary cost as the United States develops power.
Rear Adm. Simpson described the Air Force’s current priorities: multi-mission balance, efficacy in contested battlespace (air, space, and cyber), JADC2 and the communication challenge, and aircraft modernization. However, he suggested that the Air Force is missing a top-line priority: decreasing the defense spending return-on-investment gap between the United States and China. China spends one-third to one-half of what the United States spends on defense each year, yet in the past 10 years, China has built more capital ships, introduced more classes of combat ships, and successfully integrated aircraft carriers with attached air wings. China has made significant strides in space and is ahead of the United States in developing high-end robotic and AI capabilities for drone fleets. Thus, the Chinese get much greater return on investment on their defense spending than the United States, while closing capability gaps rapidly. He underscored that China is better leveraging the synergy between commercial and defense research and development, and it is leading in 5G, the Internet of Things, and the race to commercial AI. He remarked that the United States has ceded influence to China in the global economy and global strategic interest. To address this challenge, he advocated for the Air Force to embrace a new partnership with the defense industrial base to determine a path toward better, faster, and cheaper and added that supply chain risk has to be better managed. He noted that China builds most of the world’s commercial ships today (in the 1950s, it was the United States). The United States is in a better position with commercial manned aviation, but China is closing that gap quickly. China’s strategy to reduce or eliminate its supply chain dependency on the United States and the European Union stands to threaten the United States. Most concerning, he continued, is that China has a clear lead in commercial unmanned aircraft manufacturing (i.e., small drones). He proposed that the Air Force to prioritize transformation of its combat power, acquisition, and sustainment, as well as measurement of its defense spending return on investment against China’s.
In closing, Rear Adm. Simpson turned to a discussion of tactical issues in the Air Force. Although the Air Force spends science and technology dollars on innovative technologies, he explained that the transition to better, faster, and cheaper capabilities has been somewhat ineffective. For example, DevSecOps is performed by DoD program managers, who then transfer a capability to the operators; however, in the commercial world, operators and developers are one and the same, creating a continuous process. He described Platform One as “usefully disruptive” and impressive; however, that effort is still somewhat siloed. He stressed that there needs to be a recognition that a structural reorganization is essential to create shared repositories and build on capabilities.
Open Discussion
Dr. Langston noted that, in its vision for digital transformation, DoD does not seem to be addressing the return-on-investment issue or the bureaucratic barriers to rapid progress. Rear Adm. Simpson suggested that the Air Force practice using AI for mundane tasks, with the goal of eventually eliminating legacy processes and repurposing legacy people. He articulated that the Air Force needs to focus on the implementation of innovation. Mr. Brown pointed out that some congressional sponsors still have a vested interested in prolonging the lives of legacy systems. As a result, some people on the flight line inefficiently first write on paper and then plug that information into a system later. He reiterated that there is ample opportunity to replace, standardize, and innovate around digital transformation in terms of logistics, thus generating a return on investment and building momentum before moving to the removal of legacy systems.
Ms. Westphal asked how the Air Force could better work with Congress on issues related to funding. Rear Adm. Simpson proposed that the Air Force to dedicate its best talent to determine how to increase the return on investment of combat power. Although members of Congress are focused on best representing and supporting their constituents, they could also consider the importance of preserving national power and the ability to fight and win the nation’s wars. Repurposing defense dollars both creates returns and makes lives better for the constituents within a member’s congressional jurisdiction—for example, standing up an AI factory or a software factory creates job opportunities for local community college and university
graduates, and leads to combat value. Because current business processes can be a detriment to moving forward with digital transformation, Mr. Brown described the need for additional oversight from entities other than Congress. Gen. Holmes noted that part of the problem is time; congressional terms (2 years) are shorter than the time frame in which the Air Force operates, especially considering the nature of long-term competition with China. He also highlighted a particularly difficult bureaucratic hurdle in DoD: everyone has a voice and everyone has a vote, making it easier to reject proposals and slow progress.
Mr. Santee observed that data and communications are becoming a weapons system in the contested environment, and he wondered about the services’ perspectives on this issue. Rear Adm. Simpson noted that China has decreased the separation between its economic and military power. He cautioned the United States against focusing on the speed of the OODA loop; instead, better decision making is enabled by the “quality of the trip” around the OODA loop. He suggested unifying the right knowledge at the right time to achieve the greatest defense return on investment and protecting that (as opposed to defending the tactical OODA loop, which prioritizes speed for human decision making). Mr. Brown championed technology that improves the quality of decision making, and he emphasized the need to consider what the increasing use of mobile devices means for operations in a tactical environment.
A FRAMEWORK FOR DIGITAL TRANSFORMATION: PANEL TWO
Dr. Annie Green, data governance specialist, George Mason University, perceived that the Air Force is still missing the foundation for digital transformation. To make better decisions, it is critical to understand how all of an organization’s components work together. She explained that because systems are interconnected networks, levels of abstraction contextualize decision making. It is also important to have the ability to “encapsulate” in a sensitive realm and to restrict access. All of these considerations are part of the digital “ecosystem.” All of the moving components in this ecosystem can best be managed with computers, which store more and process faster than a human. She emphasized that these are not new approaches: the original digital twin (i.e., a duplicate of a real-world entity) helped bring the astronauts of Apollo 13 home safely. She highlighted the need for both top-down (e.g., unity of effort) and bottom-up (e.g., use cases) approaches in the strategic realm of the Air Force as it develops a roadmap for transformation. Strategy formulation begins with environment scanning, where data that represent the reality can be used for machine learning or algorithm development.
Dr. Green described the supply chain and the work-centered analysis chain, the latter of which emphasizes where people fit in to the ecosystem of successful product delivery. Eighty-seven percent of value in any enterprise comes from intangible assets, such as innovation, relationships, expertise and competence, and structure. Leveraging the intangible asset of intellectual capital leads to improvement and decreases costs, creating a path for an organization’s growth. Although organizations may already operate in this fashion, there is no visibility into how intangible assets could be used.
A 2018 study from MuleSoft revealed that corporate executives seek increased IT operational efficiency (83%), improved customer experience (71%), increased business efficiency (70%), quicker introduction of new products and services (58%), improved employee experience (51%), and improved partner experience (27%). Dr. Green explained that the vital functions of any enterprise include the employee (e.g., the warfighter), the partner, the information, the technology, the customer, and the competitor, as well as the product and the process. She pointed out that the competitor and the information are often not given enough attention, despite the fact that enterprises revolve around access to information. With knowledge management, a common language is created—and this enterprise taxonomy establishes a path for enterprise leadership and management to identify intangible assets, indicators, and measures (“enterprise memory”). This provides a foundation to construct a neural network of interactions as well as algorithms and machine learning for the strategy formulation process, which augments the thought processes of the enterprise leadership and management who are developing the enterprise strategic plan. She underscored that strategy is key to defining a network, asking the right questions, and determining how to answer those questions.
Dr. Green asserted that it is crucial to plan, and to know which data and information drive enterprise strategy. Data are how the enterprise “thinks”; therefore, it is important to ensure that the data captured and used in enterprise algorithms have purpose, authenticity, integrity, and completeness. Flawed data increase the risk of moving the enterprise along a destructive path, no matter which digital solution has been introduced. Thus, she continued, the sources of the data and information driving the strategic decisions of enterprise leadership and management should be validated (“data lineage”), and the data and information used in algorithms should be planned. She described Peter Drucker’s “The Information Executives Truly Need” and the four categories of diagnostic information that provide insight: foundation information (e.g., measures of cash flow and liquidity projections), productivity information (e.g., measures of performance of key resources), competence information (e.g., measures associated with core competencies), and resource-allocation information (e.g., measures associated with the allocation of scarce resources, such as capital and high-performing people). This diagnostic information is defined based on the enterprise taxonomy, where it becomes possible to identify areas for decision making.
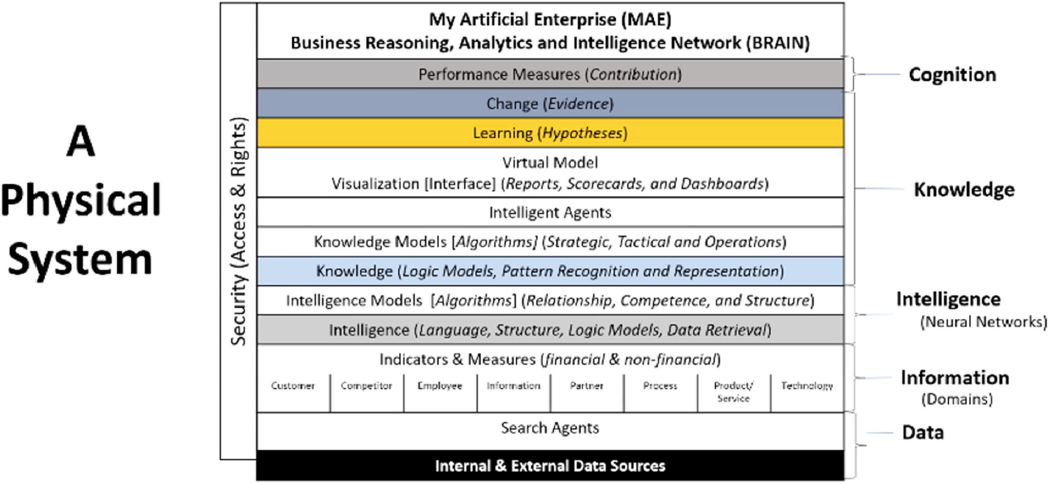
She outlined the imperative for the Air Force to make better decisions based on authentic data. Enterprise cognition can enable this practice, with a language to describe and understand the forces and interrelationships that shape the behavior of leadership and management; the capability to change systems to be more in tune with the processes of the natural and economic world of the enterprise environment; and the capability to establish goals and decisions based on what the enterprise knows or needs to know to implement and execute successful strategies. She explained that data emulate memory within a system, information is structured and aligned with familiar terms, intelligence highlights the relationships between them to illuminate places in need of actionable change, knowledge is actionable data, and cognition makes the decision that feeds back into a system. This cognitive enterprise system (see Figure 6.1) absorbs the information through a structure that identifies the functions, concepts, and elements of an enterprise.
Mental models make sense of the enterprise, and decisions and actions are uncovered to support enterprise decision makers. The context layers of an enterprise emulate the human thought process, but if the data (“the memory”) are not correct, people have to rely only on perceptions to make decisions. This cognitive enterprise system has all of the components of a true system: (1) what, why, who, where, when, and how; (2) people, process, information, and technology; (3) knowledge, skills, and abilities; (4) risks, obstacles, outcomes, and benefits; (5) frameworks and methodologies; and (6) measurements and maturity. Moving forward, she continued, the next step is to build a digital transformation business case (see Figure 6.2).
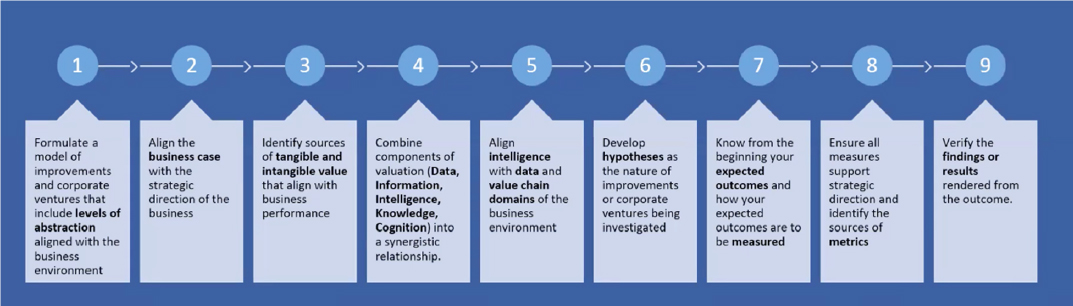
Mr. Jay Zaidi, founder, AlyData, identified four tenets of successful digital transformation:
- Organizations cannot solve complex challenges (e.g., digital transformation, governance, risk, compliance, or supply chain transparency) without defining the business value chain and the associated data supply chain.
- Organizations have to be able to visualize the business value chain and the data supply chain based on ontologies and taxonomies, and then link operational data and operational metadata to the supply chain for better insight.
- Organizations need the ability to link the metadata and the data to develop a dynamic view and to interrogate the underlying data for insights.
- The business value chain and the data supply chain coupled with relevant operational metadata can provide timely, actionable insights to mitigate risk, reduce operational costs, and enable better governance.
Mr. Zaidi posited that data are a proxy for the operations of any digital organization. In other words, if an organization is engaging in a digital transformation, it is either creating more data or reorganizing existing data for new uses. Many organizations face challenges related to important processes of regulation, governance, and optimization, all of which have an underlying data component but occur in different dimensions. For example, governance addresses data privacy, security, and access, and optimization requires understanding the full data supply chain to reduce time to value.
However, he continued, it is difficult to increase speed of action when the lines of business, technology, data, and people remain siloed. He asserted that a new approach is needed to navigate this “invisible landscape of fragmented tribal knowledge” to discover, understand, and utilize data and ensure robust governance, analytics, and AI. The data architecture, data catalogue, data privacy, data lineage, data quality, and data science are all key components for data management and governance. The data and AI governance are layered on top of these foundational pieces to ensure accountability and oversight, and the metadata (i.e., contextual information related to each of these components) connect to capture significant relationships.
Mr. Zaidi described a case study on the use of the global positioning system (GPS), the purpose of which is to enable movement from Point A to Point B as efficiently as possible. This technology could be useful for organizations that want to do future state planning; conduct “what-if” scenarios; do impact analysis; do discovery work; understand gaps in the ecosystem; or make changes to applications, processes, or technical components. “GPS for Data Assets” is a dynamic enterprise data ecosystem visualization and management layer that includes many of the underlying components (e.g., data quality and observability tools and metadata, enterprise architecture-related artifacts and tools, customer data platform, data privacy
tools) to provide a holistic view. Given that research shows that 90 percent of information transmitted is more effective when conveyed visually and 40 percent of people respond better to visually represented information, visualization of information from different siloes and in different formats is an important part this effort. Current models are translated, digitized, and transformed into visual lineage-type views to display environments and ensure that all team members are working from the same view of the ecosystem. The goal is to gather, connect, and visualize information to enable better decision making, analysis, and discovery. By capturing all of the underlying metadata and overlaying those with data, it is possible to conduct a level of analysis that is not possible in siloes. To reach this end state, he suggested the following approach: create a community of practice comprised of business, technology, and data experts; define an ontology and taxonomy for the domain and modify it; automatically ingest technical metadata from various data sources (e.g., file stores, databases, spreadsheets, data warehouses, data lakes) using prebuilt harvesters; and crowdsource missing business metadata or tribal knowledge that is not documented but is owned by associates.
Dr. Anthony Rhem, chief executive officer, AJ Rhem and Associates, described how to leverage AI-powered knowledge delivery to enable to digital transformation. He defined digital transformation as the process of using digital technologies to create new or modify existing business processes, culture, and customer experiences to meet the changing business and market environments and thus to fundamentally change operations and value delivery. AI-powered knowledge delivery is facilitated by the knowledge-as-a-service framework, which blends knowledge management and AI to deliver the right knowledge to the right person in the right context and enable fast, efficient, and accurate decision making.
He explained that knowledge-as-a-service uses a distributed computing model; connects tacit and explicit knowledge through ontology management and knowledge mapping; blends tacit and explicit knowledge (which are constantly updated, adhering to the organization’s content life cycle management processes); makes use of AI through predictive analytics and knowledge flow optimization; and provides a dynamic, accurate, and personal delivery of knowledge. He posited that knowledge-as-a-service is most useful in the following cases: (1) an organization has an abundance of information and knowledge and needs a mechanism to understand it; (2) knowledge needs to be accessed in a timely manner; (3) access to the collective knowledge of an organization needs to be improved; (4) workers need personalized knowledge that responds to their specific needs; (5) workers need to be more productive by executing tasks and learning more efficiently and effectively; and (6) workers need to collaborate and share knowledge to foster innovation. AI plays an important role in knowledge-as-a-service by elevating how the delivery of knowledge occurs to the people who need it. He noted that AI is used to scale the volume and effectiveness of knowledge distribution; to predict trending knowledge areas that knowledge workers need; and to leverage supervised learning algorithms that will learn over time, which will deliver more personalized knowledge to an individual to solve a particular problem. AI also facilitates the delivery of Smart Search, which enables search to take advantage of ontologies between the tangible content and the people conducting the search. AI also makes it possible to leverage RPA to deliver personalized knowledge.
Dr. Rhem remarked that knowledge-as-a-service can be implemented through the digital workplace (Figure 6.3). The business case for the implementation of the digital workplace in digital transformation is that it enables personnel to be more productive and effective. The digital workplace could be used to ensure that those on the ground in the Air Force have access to the knowledge they need to complete their missions. The digital workplace aligns technology, employees, and business processes to improve operational efficiency and meet organizational goals; is the platform that staff members would use to access all corporate knowledge to execute their jobs; is enabled by cloud services, mobile, and AI; and removes geographic barriers from collaboration and processes and ensures that knowledge is available any time and any place. The digital workplace prioritizes personnel through improved collaboration and employee engagement; new staff workstreams via the use of personas; more productive business relationships within and beyond natural working groups; increased employee productivity; improved business processes and content management to facilitate the intelligent delivery of knowledge; and alignment with the organization’s digital transformation goals.
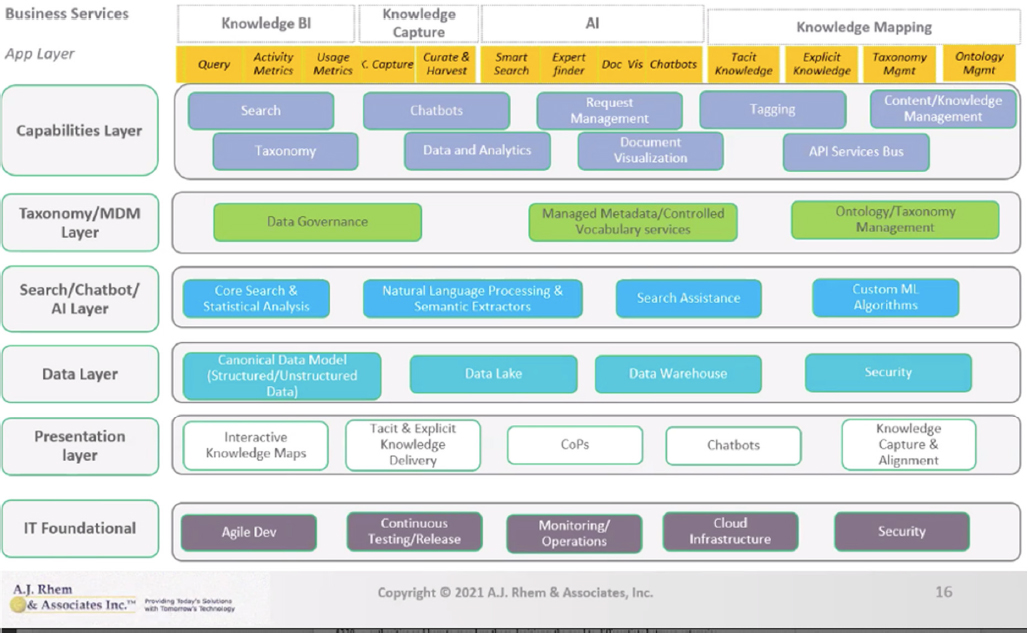
In closing, Dr. Rhem noted that the benefits of knowledge-as-a-service in the digital workplace include
- Enhanced communication and innovation by creating a more collaborative culture;
- Increased productivity executing tasks and learning more efficiently and effectively;
- Personalized knowledge access;
- Prediction of trending knowledge areas that knowledge workers need; and
- Identification of targeted knowledge for real-time engagement and content consumption to aid in decision making and improve outcomes.
This page intentionally left blank.


















