




























































































Below is the uncorrected machine-read text of this chapter, intended to provide our own search engines and external engines with highly rich, chapter-representative searchable text of each book. Because it is UNCORRECTED material, please consider the following text as a useful but insufficient proxy for the authoritative book pages.
18 APPENDIX A LITERATURE REVIEW CONTENTS Introduction ................................................................................................................................... 19 A. Institutional Context for Emergency Management .................................................................. 21 B. Nature and Degree of Hazards/Threats .................................................................................... 26 C. Emergency Management Program ........................................................................................... 48 D. Stakeholders â Regional Collaboration.................................................................................... 75 E. Emergency Management Training ........................................................................................... 78
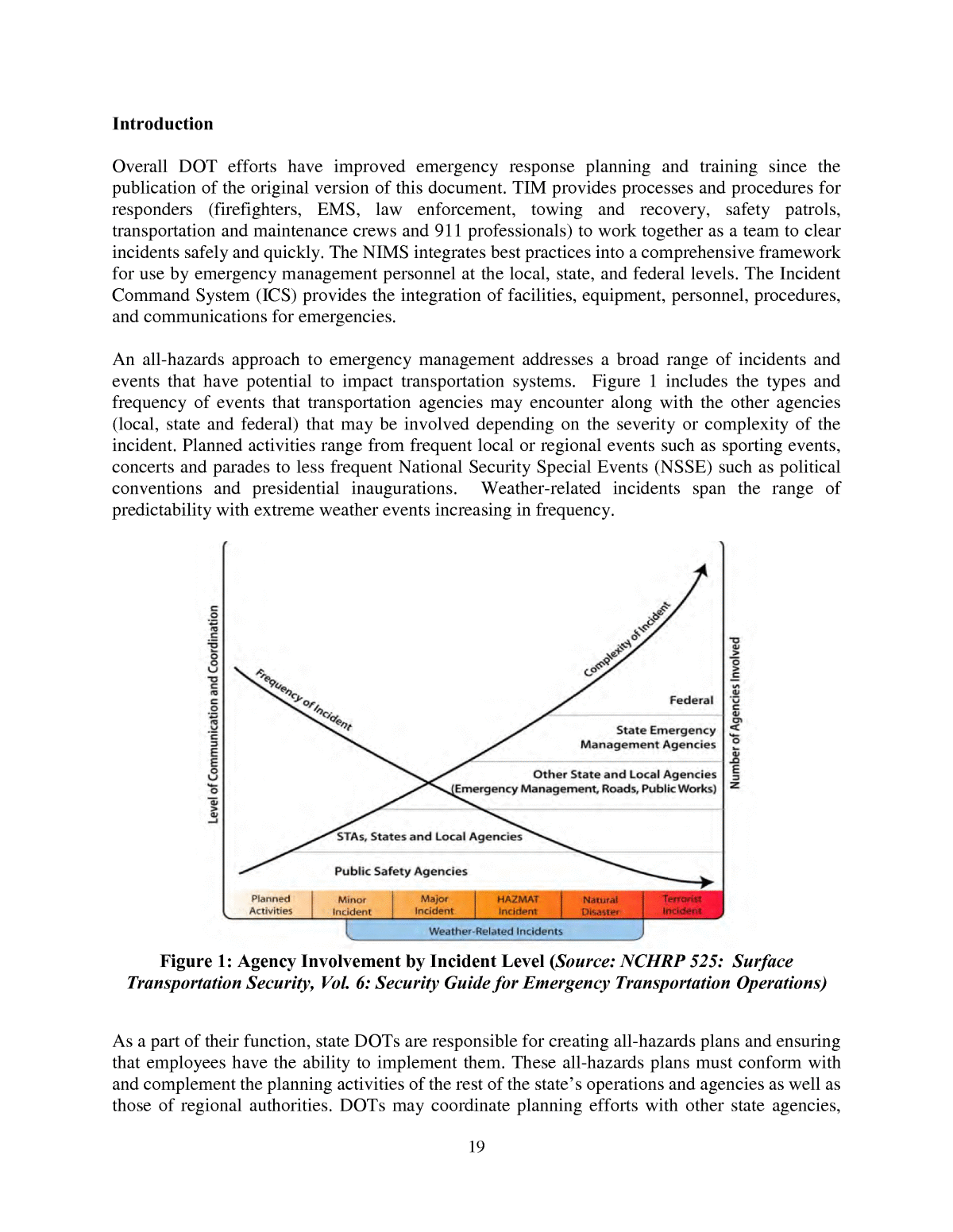
19 Introduction Overall DOT efforts have improved emergency response planning and training since the publication of the original version of this document. TIM provides processes and procedures for responders (firefighters, EMS, law enforcement, towing and recovery, safety patrols, transportation and maintenance crews and 911 professionals) to work together as a team to clear incidents safely and quickly. The NIMS integrates best practices into a comprehensive framework for use by emergency management personnel at the local, state, and federal levels. The Incident Command System (ICS) provides the integration of facilities, equipment, personnel, procedures, and communications for emergencies. An all-hazards approach to emergency management addresses a broad range of incidents and events that have potential to impact transportation systems. Figure 1 includes the types and frequency of events that transportation agencies may encounter along with the other agencies (local, state and federal) that may be involved depending on the severity or complexity of the incident. Planned activities range from frequent local or regional events such as sporting events, concerts and parades to less frequent National Security Special Events (NSSE) such as political conventions and presidential inaugurations. Weather-related incidents span the range of predictability with extreme weather events increasing in frequency. Figure 1: Agency Involvement by Incident Level (Source: NCHRP 525: Surface Transportation Security, Vol. 6: Security Guide for Emergency Transportation Operations) As a part of their function, state DOTs are responsible for creating all-hazards plans and ensuring that employees have the ability to implement them. These all-hazards plans must conform with and complement the planning activities of the rest of the stateâs operations and agencies as well as those of regional authorities. DOTs may coordinate planning efforts with other state agencies,
20 including the state's emergency management agency; county highway departments; with various agencies of the U.S. DOT; and with DOTs from other states to ensure activities can be easily integrated when necessary. DOTs also need to plan to receive and use resources provided by other states and the federal government during operations.
21 A. Institutional Context for Emergency Management Recent guidance at the national level has been reshaping the focus and long-term direction of transportation agencies. Since the publication of the Guide in 2010, four significant national level directives and executive orders have been issued, with an emerging focus on the complementary goals of infrastructure protection and system resiliency as part of security and emergency management. ⢠PRESIDENTIAL POLICY DIRECTIVE 8: NATIONAL PREPAREDNESS (2011) strengthens security and resilience through five preparedness mission areas - Prevention, Protection, Mitigation, Response, and Recovery. ⢠PRESIDENTIAL POLICY DIRECTIVE-21: CRITICAL INFRASTRUCTURE SECURITY AND RESILIENCE (2013) focuses on the need for secure critical infrastructure that is able to withstand and rapidly recover (resilient) from all hazards. ⢠2013 NATIONAL INFRASTRUCTURE PROTECTION PLAN: PARTNERING FOR CRITICAL INFRASTRUCTURE SECURITY AND RESILIENCE emphasizes the importance of resilience, the need to reduce all-hazards vulnerabilities and mitigate potential consequences of incidents or events that do occur. ⢠EXECUTIVE ORDER 13636: IMPROVING CRITICAL INFRASTRUCTURE CYBERSECURITY (2013) provides a technology-neutral cybersecurity framework and means to promote and the adoption of cybersecurity practices. ⢠EXECUTIVE ORDER 13653, PREPARING THE UNITED STATES FOR THE IMPACTS OF CLIMATE CHANGE (2013) requires federal agencies to integrate considerations of the challenges posed by climate change effects into their programs, policies, rules and operations to ensure they continue to be effective, even as the climate changes. ⢠The MOVING AHEAD FOR PROGRESS IN THE 21ST CENTURY ACT (MAPâ21), the previous transportation reauthorization legislation, focused on performance management and established a series of national performance goals. The goals related to safety, congestion reduction, freight movement and economic vitality and environmental sustainability are of particular relevance to emergency management. MAP-21 also required incorporating performance goals, measures, and targets into transportation planning. ⢠The FAST ACT, enacted in 2015, expands the focus on the resiliency of the transportation system. âIt is in the national interest to encourage and promote the safe and efficient management, operation, and development of resilient surface transportation systems that will serve the mobility needs of people and freight and foster economic growth and development within and between states and urbanized areas through metropolitan and statewide transportation planning processes.â It requires strategies to reduce the vulnerability of existing transportation infrastructure to natural disasters and expands the scope of consideration of the metropolitan planning process to include improving transportation system resiliency and reliability.
22 National Disaster Recovery Framework, Second Edition â Information Sheet Citation. âNational Disaster Recovery Framework, Second Edition â Information Sheet,â Emergency Management Agency (FEMA), Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library-data/1466017528262- 73651ed433ccfe080bed88014ac397cf/InformationSheet_Recovery_Framework.pdf Synopsis. The National Disaster Recovery Framework describes âhow the whole community works together to restore, redevelop, and revitalize the health, social, economic, natural, and environmental fabric of the community.â The new Framework incorporates the edits to the National Preparedness Goal and new lessons learned. Additional changes made to the framework include: âIncreased focus on Recoveryâs relationship with the other four mission areas. Updated Recovery Support Functions (RSFs) to reflect changes in Primary Agencies and Supporting Organizations. Additional language on science and technology capabilities and investments for the rebuilding and recovery efforts.â National Response Framework, Third Edition â Information Sheet Citation. âNational Response Framework, Third Edition â Information Sheet,â Emergency Management Agency (FEMA), Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library-data/1466014891281- 6e7f60ceaf0be5a937ab2ed0eae0672d/InformationSheet_Response_Framework.pdf Synopsis. The NRF is aligned with NIMS and provides capabilities to save lives, protect property, and meet basic human needs. Response activities occur before, during, and after an incident and can overlap with the start of Recovery activities. The following changes were made to the framework: ⢠The addition of a new core capability, Fire Management and Suppression. ⢠Three revised core capability titles o Logistics and Supply Chain Management; o On-scene Security, Protection, and Law Enforcement; and o Public Health, Healthcare, and EMS. ⢠Three revised core capability definitions o Environmental Response/ Health and Safety; o Fatality Management Services; and o Logistics and Supply Chain Management. National Mitigation Framework, Second Edition â Information Sheet Citation. âNational Mitigation Framework, Second Edition â Information Sheet,â Emergency Management Agency (FEMA), Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library-data/1466014552462- 1b78d1a577324a66c4eb84b936c68f16/InformationSheet_Mitigation_Framework.pdf
23 Synopsis. The National Mitigation Framework covers the capabilities necessary to reduce the loss of life and property by lessening the effects of disasters, and focuses on risk (understanding and reducing it), resilience (helping communities recover quickly and effectively after disasters), and a culture of preparedness. The new Framework incorporates the edits to the National Preparedness Goal and new lessons learned including a revised core capability title, Threats and Hazards Identification. In addition, the following changes have been made: âAdditional language on science and technology efforts to reduce risk and analyze vulnerabilities within the mitigation mission area. Updates on the Mitigation Framework Leadership Group (MitFLG), which is now operational. Updates to the Community Resilience core capability definition to promote preparedness activities among individuals, households and families.â National Protection Framework, Second Edition â Information Sheet Citation. âNational Protection Framework, Second Edition â Information Sheet,â FEMA, Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library- data/1466013587164- 86696df20638bbf24e25d70070eda114/InformationSheet_Protection_Framework.pdf Synopsis. The National Protection Framework focuses on âactions to deter threats, reduce vulnerabilities, and minimize the consequences associated with an incident.â The new Framework incorporates the edits to the National Preparedness Goal and new lessons learned. In addition, the following changes have been made: âUpdated Cybersecurity Core Capability Critical Tasks to align with the Mitigation, Response, and Recovery Mission Areas. Additional language on science and technology investments to protect against emerging vulnerabilities are included within the protection mission area. Additional language on interagency coordination within the protection mission area to support the decision making processes outlined within the framework.â National Prevention Framework, Second Edition â Information Sheet Citation. âNational Prevention Framework, Second Edition â Information Sheet,â FEMA, Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library- data/1466011024787- 91b8e49bf7344dd6dadca441c26272ad/InformationSheet_Prevention_Framework.pdf Synopsis. The National Prevention Framework focuses on terrorism and addresses the capabilities necessary to avoid, prevent, or stop imminent threats or attacks. Some core capabilities overlap with the Protection mission area. The updates include edits to the Nation Preparedness Goal, and lessons learned. Other edits include: âUpdates to Coordinating Structure language on Joint Operations Centers and the Nationwide Suspicious Activity Reporting Initiative. Clarification on the relationship and differences between the Prevention and Protection mission areas. Updated language on the
24 National Terrorism Advisory System (NTAS) as part of the Public Information and Warning core capability. Additional language on science and technology investments within the prevention mission area.â National Preparedness Goal, Second Edition â Information Sheet Citation. âNational Preparedness Goal, Second Edition â Information Sheet,â FEMA, Washington, DC, 2015, [Online]. Available: http://www.fema.gov/media-library- data/1443624338930- 32e9ed3ac6cf8e95d7d463ed9b9685df/NationalPreparednessGoal_InformationSheet_2015.pdf Synopsis. The 2011 National Preparedness Goal was updated in 2015. The key changes are described in the National Preparedness Goal, Second Edition â Whatâs New Fact Sheet. The National Preparedness Goal itself has not changed: âA secure and resilient nation with the capabilities required across the whole community to prevent, protect against, mitigate, respond to, and recover from the threats and hazards that pose the greatest risk.â The following changes were made to the National Preparedness Goal document: ⢠Introduction: Language added to stress the importance of community preparedness and resilience. ⢠Risk and the Core Capabilities: Enhanced items on cybersecurity and climate change. ⢠Preliminary Targets: Updated preliminary targets. ⢠New Core Capability: A new core capability, Fire Management and Suppression, was added. ⢠Core Capability Titles: Revised the following core capability titles: o Threats and Hazard Identification (Mitigation) â revised to Threats and Hazards Identification; o Public and Private Services and Resources (Response) â revised to Logistics and Supply Chain Management; o On-scene Security and Protection (Response) â revised to On-scene Security, Protection, and Law Enforcement; and o Public Health and Medical Services (Response) â revised to Public Health, Healthcare, and EMS. ⢠Core Capability Definitions: Several of the core capability definitions were revised.
25 NIPP 2013: Partnering for Critical Infrastructure Security and Resilience Citation. National Infrastructure Protection Plan (NIPP) 2013: Partnering for Critical Infrastructure Security and Resilience, US Department of Homeland Security, Washington, DC, 2013, [Online]. Available: https://www.dhs.gov/national-infrastructure-protection-plan Synopsis. From DHS.gov: âOur Nationâs well-being relies upon secure and resilient critical infrastructureâthe assets, systems, and networks that underpin American society. The National Infrastructure Protection Plan (NIPP) â NIPP 2013: Partnering for Critical Infrastructure Security and Resilience â outlines how government and private sector participants in the critical infrastructure community work together to manage risks and achieve security and resilience outcomes.â âNIPP 2013 represents an evolution from concepts introduced in the initial version of the NIPP released in 2006 and revised in 2009. The National Plan is streamlined and adaptable to the current risk, policy, and strategic environments. It provides the foundation for an integrated and collaborative approach to achieve the vision of: â[a] Nation in which physical and cyber critical infrastructure remain secure and resilient, with vulnerabilities reduced, consequences minimized, threats identified and disrupted, and response and recovery hastened.â NIPP 2013 meets the requirements of Presidential Policy Directive-21: Critical Infrastructure Security and Resilience, signed in February 2013. The Plan was developed through a collaborative process involving stakeholders from all 16 critical infrastructure sectors, all 50 states, and from all levels of government and industry. It provides a clear call to action to leverage partnerships, innovate for risk management, and focus on outcomes.â The NIPP 2013 has six chapters, two appendices, and four supplements. After an Executive Summary, the Introduction (Chapter 1) gives an overview of the NIPP 2013 and its evolution from the 2009 NIPP. Chapter 2 defines the vision, mission, and goals of the NIPP 2013, while Chapter 3 describes the Critical Infrastructure Environment in terms of key concepts, risk, policy, operations, and partnership. Core Tenets are established in Chapter 4. Ways to collaborate to manage risk are given in Chapter 5. The final chapter is a Call to Action (âSteps to Advance the National Effortâ). The Sector-Specific Plans of the 16 critical infrastructure sectors are being updated to align with the NIPP 2013. The web page for NIPP 2013 also contains links to training courses, critical infrastructure partnership courses, security awareness courses, and the relevant authorities (i.e. laws, regulations, and guidance). NIPP Supplemental Tool: Incorporating Resilience into Critical Infrastructure Projects http://www.dhs.gov/sites/default/files/publications/NIPP%202013%20Supplement_Incorporatin g%20Resilience%20into%20CI%20Projects_508.pdf NIPP Supplemental Tool: Executing a Critical Infrastructure Risk Management Approach http://www.dhs.gov/sites/default/files/publications/NIPP%202013%20Supplement_Executing%2 0a%20CI%20Risk%20Mgmt%20Approach_508.pdf
26 B. Nature and Degree of Hazards/Threats Hazards have continued to evolve since the First Edition was published. In more recent times transportation agencies have been experiencing more and more devastating events either due to natural causes (e.g., Superstorm Sandy, extensive Midwest flooding, powerful hurricanes), caused by unintentional human intervention (e.g., truck crashes and fires on the Oakland Bay Bridge and in the Boston tunnels, oil train derailments) or intentional acts (e.g. cyber attacks and armed assault including active-shooter incidents). Because todayâs transportation systems are integrated cyber and physical systems, there are greater cyber risks than ever, including the risk of a cyber incident impacting not only data, but the control systems and physical infrastructure of transportation agencies. Risk-Based Transportation Asset Management: Building Resilience into Transportation Assets: Report 5: Managing External Threats Through Risk-Based Asset Management Citation. âReport 5: Managing External Threats Through Risk-Based Asset Managementâ, Risk- Based Transportation Asset Management: Building Resilience into Transportation Assets, FHWA, U.S. Department of Transportation, Washington, DC, March 2013, [Online]. Available: http://www.fhwa.dot.gov/asset/pubs/hif13018.pdf Synopsis. From the TRID Database: âThis is the fifth of five reports examining how risk management complements asset management. This last report examines how physical, climatic, seismic and other external threats can be addressed in risk-based asset management programs. The first four reports and the literature review emphasized the definition of risk as the positive or negative effect of uncertainty or variability upon agency objectives. Those reports emphasized that risks could be positive in that some types of uncertainty can create opportunities. However, this report will focus more on negative risks, or threats. These risks generally are external, and while highly probable over a long period of time, are difficult to predict in the short term. Randomness and variability complicate planning for them. In August 2011, Hurricane Irene reached one of the nationâs most northern states, Vermont, and damaged 480 bridges out of a total network of 2717 bridges. In one day, more bridge deterioration occurred than normally would occur over many years. Accurate prediction of such events is nearly impossible. Such a significant storm had not struck Vermont for 83 years. In managing risks to assets from external threats, this report emphasizes the Three Rs, which are Redundancy, Robustness and Resiliency. These will be defined, described and illustrated through several agency examples. Asset management plays a critical role in each, particularly Robustness and Resiliency. Including the Three Rs in asset planning efforts can better prepare agencies to cope with an increasingly unpredictable world.â The report consists of five major sections. The first is an introductory section. The second section discusses Climate Change and Extreme Weather Risks. The FHWAâs Vulnerability Assessment Model is presented in the third section. The fourth section discusses Risked-Based Approaches to Protecting Assets. Summary and Conclusions make up the fifth section. A Guide for Assessing Community Emergency Response Needs and Capabilities for Hazardous Materials Releases
27 Citation. A Guide for Assessing Community Emergency Response Needs and Capabilities for Hazardous Materials Releases. HMCRP Report, Battelle Memorial Institute, Issue 5, 2011, 119p, [Online]. Available: http://www.trb.org/Publications/Blurbs/165201.aspx Synopsis. From the TRID Database: âThis Guide presents comprehensive, step-by-step guidance on assessing hazardous materials emergency response needs at state, regional, and local levels; matching state, regional, and local capabilities with potential emergencies involving different types of hazardous materials; and assessing how quickly resources can be brought to bear in an emergency. The methodology described in the Guide is designed to be scalable, allowing the implementation results to be aggregated at the local level up through regional, state, and national levels. Also, the Guide is designed to connect as many components as possible to already- established standards, guidelines, regulations, and laws, so that the Guide will remain current as these underlying components are updated. In addition, the Guide discusses appropriate means for maintaining currency of the information over time. The Guide and accompanying spreadsheet tool (on the attached CD-ROM), which leads planners through the assessment process, will be most useful for local jurisdictions that have limited resources and expertise in hazardous materials emergency response planning.â Protecting Americaâs Roads, Bridges, and Tunnels: The Role of State DOTs in Homeland Security Citation. âProtecting Americaâs Roads, Bridges, and Tunnels: The Role of State DOTs in Homeland Security,â AASHTO, Washington, DC, Jan 2005, [Online]. Available: http://scotsem.transportation.org/Documents/Protecting_Americas_Roads.pdf Synopsis. According to AASHTOâs page on Bridge and Tunnel Security, this publication is an âAASHTO brochure providing an overview of the vital role that State DOTs â builders and operators of the nationâs busiest roads, tunnels, and bridges â often play when emergency situations occurâ. It explains âwhy the security of our roads, bridges, and tunnels is important, what DOTs are doing to improve it, and the keys to better partnership.â The document has four sections. The introductory section (âState DOTsâGuardians of The Nationâs Transportation Infrastructureâ) argues that DOTsâ foremost expanded roles include all-hazards emergency management and critical asset protection. The two body sections explain DOTsâ expertise and needs in their respective domain. The first body section (âA Vital Support Role in Emergency Managementâ) notes that DOTsâ all-hazards emergency management expertise includes the key functions of: traveler information; traffic management; transportation facilities, personnel, and equipment; and infrastructure reconstruction capabilities. At the same time, resources are needed to address the enhancement of Intelligent Transportation System (ITS) capabilities; improvement of emergency response; and better communications. The second body section (âProtecting Critical Transportation Assetsâ) notes that DOTs have several available countermeasures: deterrence and detection, defense, and design and re-design. But to address critical asset protection, DOTs need resources to address: bridge retrofits, bridge reconstruction, tunnel protection costs.â
28 In its concluding section (âThe Road Ahead â Setting an Agenda for Partnership in Securityâ), this publication advocates that DOTs be âconsidered as first responders in terms of support from the Department of Homeland Security.â For strengthening this partnership, four cornerstones are proposed: ⢠recognition of vital role of DOT in emergency management and homeland security, ⢠responsiveness to road, bridge, and tunnel asset protection needs, ⢠additional resources for DOT to meet homeland security challenges, and ⢠support for transportation-related security research. NCHRP Report 750: Strategic Issues Facing Transportation, Volume 2: Climate Change, Extreme Weather Events, and the Highway System: Practitionerâs Guide and Research Report, 2014 Citation. Parsons Brinckerhoff, Cambridge Systematics, and Stratus Consulting, NCHRP Report 750: Strategic Issues Facing Transportation Volume 2: Climate Change, Extreme Weather Events, and the Highway System: A Practitionerâs Guide and Research Report, Transportation Research Board of the National Academies, Washington, DC, 2014, [Online]. Available: http://www.trb.org/Main/Blurbs/169781.aspx Synopsis. From the TRID Database: âThis report presents guidance on adaptation strategies to likely impacts of climate change through 2050 in the planning, design, construction, operation, and maintenance of infrastructure assets in the United States (and through 2100 for sea-level rise).In addition to the practitionerâs guide and research report, this project also developed the following items: 1. âa software tool that runs in common web browsers and provides specific, region-based information on incorporating climate change adaptation into the planning and design of bridges, culverts, stormwater infrastructure, slopes, walls, and pavements; 2. âtables that provide the same information as the previously mentioned software tool, but in a spreadsheet format that can be printed; and 3. âtwo spreadsheets that illustrate examples of the benefit-cost analysis of adaptation strategies discussed in Appendix B of Part I of NCHRP Report 750, Volume 2.â This report discusses physical countermeasures against storm surge, floods, extreme temperature, and permafrost instability. Storm surge countermeasures include shoreline revetments, elevated approach roadways, extended wingwalls, enhanced scour protection and strengthened deck tie- downs. Additional flood countermeasures include floodplain culverts, hardening the slopes of approach roadways, adding/raising spans, and protecting coatings. Countermeasures against extreme temperature include widening expansion joints, redesigning bearings, and strengthening beams and girders. Countermeasures against permafrost instability include mitigation techniques such as the use of reflective surfaces, air convection embankment, geosynthetic reinforcement, thermosyphons, berms, air ducts, insulation materials and lightweight fill materials.
29 Hazard Data Sources and Tools Information on potential hazards, including probability and possible effects, can be obtained from the FEMA, State Emergency Management and Civil Defense Agencies, National Weather Service (NWS), Environmental Protection Agency (EPA), U.S. Department of the Interior, U.S. Geological Survey, U.S. Army Corps of Engineers, and Department of Natural Resources (DNR). FEMA 433: Using HAZUS-MH for Risk Assessment, FEMA. Available: http://www.fema.gov/fema-433-using-hazus-mh-risk-assessment FEMA Map Service Center Available: http://msc.fema.gov/webapp/wcs/stores/servlet/FemaWelcomeView?storeId=10001&catalogId= 10001&langId=-1 This FEMA source provides map information for a variety of users affected by floods, including homeowners and renters, real estate and flood determination agents, insurance agents, engineers and surveyors, and federal and exempt customers. There are flood maps, databases, map viewers, documents and publications providing comprehensive information. Further aspects of the site include FEMA issued flood maps available for purchase, definitions of FEMA flood zone designations, and information about FIRMettes, a full-scale section of a FEMA Flood Insurance Rate Map (FIRM) that users can create and print at no charge. FEMA Flood Map Service Center (MSC) Available: http://msc.fema.gov/portal/ The FEMA Flood MSC is the official public source for flood hazard information produced in support of the National Flood Insurance Program (NFIP). The MSC contains official flood maps, access a range of other flood hazard products, and tools for better understanding flood risk. subsection of Interior Geospatial Emergency Management System (IGEMS) Available: http://igems.doi.gov/ The Department of Interior Geosciences and Environmental Change Science Center (GECSC), which replaced the Natural Hazards Support System (NHSS), provides online maps containing the latest available information on earthquakes, earthquake shakemaps, streamflow data, floods, volcanoes, wildfires, and weather hazards. National Weather Service Geographic Information Systems (GIS) Data Portal (NOAA) Available: http://www.nws.noaa.gov/gis/shapepage.htm Current weather, forecasts and past weather data are available in Shapefile and other formats from the Data Portal. Hazards include tornados, hurricanes, rain, snowfall, floods and other weather-related hazards.
30 Advanced Hydrologic Prediction Service (NOAA) Available: http://www.nws.noaa.gov/oh/ahps/ The NOAA Advanced Hydrologic Prediction Service (AHPS) is a web-based suite of forecast products that displays the magnitude and uncertainty of occurrence of floods or droughts, from hours to days and months, in advance. The majority of the observed water level data displayed on the AHPS web pages originates from the United States Geological Survey's (USGS) National Streamflow Information Program which maintains a national network of stream gauges. In addition, real-time water level information is collected from other federal, state, and local stream gauge networks. Climate Change & Extreme Weather Vulnerability Assessment Framework (2012) Available: http://www.fhwa.dot.gov/environment/climate_change/adaptation/publications/vulnerability_a ssessment_framework/page00.cfm#Toc345418472 The FHWA's Climate Change and Extreme Weather Vulnerability Assessment Framework is a guide for transportation agencies interested in assessing their vulnerability to climate change and extreme weather events. It gives an overview of key steps in conducting vulnerability assessments and uses in practice examples to demonstrate a variety of ways to gather and process information. Space Weather Space weather events are naturally occurring phenomena in the space environment that have the potential to disrupt technologies and systems in space and on Earth. These phenomena can affect satellite and airline operations, communications networks, navigation systems, the electric power grid, and other technologies and infrastructures critical to the daily functioning, economic vitality, and security of our nation. Space weather can affect communication and navigation systems that are critical for safe and efficient transportation systems Over the last several years, both industry and the federal government have played an active role in maintaining and advancing the nationâs ability to forecast and mitigate the various impacts of space weather. These actions include taking steps to replace aging satellite assets essential to monitoring and forecasting space weather, proposing space weather standards for both the national and international air space, developing regulations to ensure the continued operation of the electric grid during an extreme space weather event, proposing a new option for replacing crucial Extra High Voltage (EHV) transformers damaged by space weather, and developing domestic production sources for EHV transformers. NOAA Space Weather Prediction Center Available: http://www.swpc.noaa.gov/ The official U.S. government space weather bureau
31 SpaceWeather.com Available: spaceweather.com This website maintains all space weather information including current conditions. White House Workshop on Space Weather, 2015 The White House held a workshop titled âSpace Weather: Understanding Potential Impacts and Building Resilienceâ in October of 2015 and released the following supporting commitments to enhance space weather preparedness: ⢠Releasing New Space Environment Data. The U.S. Air Force (USAF), in partnership with the National Oceanic and Atmospheric Administration (NOAA), will provide Space Environment Data from the current GPS constellation and other U.S. Government satellites. This data could be used to validate space weather forecast models, potentially enhancing space weather prediction capabilities. As a first step, USAF and NOAA will make data from January 2014 â a month characterized by a high level of solar activity â freely available on data.gov, providing an opportunity for users to explore the scientific value of the data. Within three months of this release, the Office of Science and Technology Policy will chair an interagency group to evaluate the utility of the released data and to determine if the open data archive should be expanded to include additional historical and near real-time data. ⢠Launching a Space Weather Data Initiative. In accordance with President Obamaâs Executive Order on making open and machine-readable the new default for government information, as well as on demonstrated successes of unleashing innovation and technology for disaster response and recovery, the administration will launch a Space Weather Data Initiative. The goals of this initiative are to (1) make easily accessible and freely available on data.gov an unprecedented amount of space weather-related data; (2) engage with the private sector and the open data community to leverage the open data and promote the development of data-driven tools, applications, and technology to enhance space weather preparedness; and (3) expand U.S. Government capacity for using open data, innovation, and technology to support effective and efficient response to and recovery from space weather events. ⢠Increasing International Collaboration. To strengthen international coordination and cooperation on space weather preparedness, the Department of State will organize workshops and meetings in Washington, DC with embassy staff from a multitude of nations. These workshops and meetings will provide an opportunity for other countries to learn more about the purpose and goals of the National Space Weather Strategy and accompanying Action Plan; ensure that policymakers in and leaders of partner nations recognize space weather as a global challenge; and facilitate the sustained, coordinated participation of partner nations in relevant international space weather initiatives. ⢠Including Space Weather in Transportation âFundamentalsâ Reports. Space weather can affect communication and navigation systems that are critical for safe and efficient transportation systems. By incorporating space weather considerations into two reports that provide comprehensive and up-to-date guidance on the major elements of a stateâs all- hazards transportation security and emergency management program â Security 101: A
32 Physical Security Primer for Transportation, and A Guide to Emergency Response Planning at State Transportation Agencies âofficials will have the information they need to incorporate space weather considerations into transportation security guidelines and emergency response plans. The American Association of State Highway and Transportation Officials (AASHTO) â a nonprofit association representing highway and transportation departments in the 50 states, the District of Columbia, and Puerto Rico â will ensure that space weather is included in the next edition of these two AASHTO Special Committee on Transportation Security and Emergency Management âfundamentalsâ reports. ⢠Incorporating Space Weather into Emergency Management Training and Activities. Space weather events can, directly or indirectly, cause or exacerbate major disasters or emergencies, and can interfere with or impair disaster response, relief, and recovery efforts. The National Emergency Management Association (NEMA) â a professional association of and for emergency management directors, dedicated to enhancing public safety by improving the nationâs ability to prepare for, respond to, and recover from all emergencies and disasters â will increase training and education related to space weather. Specifically, NEMA will: o Partner with the International Association of Emergency Managers to host a space weather focused webinar for members of both groups, reaching up to 1200 state and local emergency managers, and others working in the emergency management field; o Incorporate space weather into training and education opportunities for newly appointed state emergency management directors; and o Incorporate space weather into the NEMA Homeland Security Committeeâs policy focus on infrastructure resilience. ⢠Raising Awareness of Space Weather in the Aviation Sector. As part of their commitment to promote safety, security and a healthy U.S. airline industry, Airlines for America â Americaâs largest airline trade association â will work with member carriers and their affiliates to educate the community on space weather and its effects on aviation, which include degradation or loss of satellite navigation signals and radio transmissions for communication. Fact Sheet: New Actions to Enhance National Space Weather Preparedness https://www.whitehouse.gov/sites/default/files/microsites/ostp/space_weather_fact_sheet_final.p df National Space Weather Strategy and National Space Weather Action Plan National Space Weather Strategy Available: https://www.whitehouse.gov/sites/default/files/microsites/ostp/final_nationalspaceweatherstrateg y_20151028.pdf National Space Weather Action Plan Available:
33 https://www.whitehouse.gov/sites/default/files/microsites/ostp/final_nationalspaceweatheraction plan_20151028.pdf The newly released National Space Weather Strategy (Strategy) and Space Weather Action Plan (Action Plan) were developed by an interagency group of experts, with input from stakeholders outside of the federal government, to clearly articulate how the federal government will work to fill these gaps by coordinating, integrating, and expanding existing policy efforts; engaging a broad range of sectors; and collaborating with international counterparts. The Strategy identifies goals and establishes the guiding principles that will guide these efforts in both the near and long term, while the Action Plan identifies specific activities, outcomes, and timelines that the federal government will pursue accordingly. The Action Plan broadly aligns with investments proposed in the Presidentâs Budget for Fiscal Year 2016 and will be reevaluated and updated within 3 years of the date of publication or as needed. Taken together, the Strategy and Action Plan will facilitate the integration of space weather considerations into federal planning and decision making to achieve preparedness levels consistent with national policies, and enhance the resilience of critical technologies infrastructures to the potentially debilitating effects of space weather on the people, economy, and security of the United States. Cybersecurity Protection of Transportation Infrastructure from Cyber Attacks: A Primer Citation: Countermeasures Assessment and Security Experts, LLC; Western Management and Consulting, LLC, NCHRP Web-Only Document 221/TCRP Web-Only Document 67: Protection of Transportation Infrastructure from Cyber Attacks: A Primer. Transportation Research Board of the National Academies, Washington, DC, 2016, 183p. Available: http://trid.trb.org/view/1408236 Synopsis: This primer, a joint product of two Transportation Research Board Cooperative Research Programs, provides transportation organizations basic reference material concerning cybersecurity concepts, guidelines, definitions and standards. The primer delivers fundamental strategic, management and planning information associated with cybersecurity and its applicability to transit and state department of transportation operations. The primer presents fundamental definitions and rationales that describe the principles and practices that enable effective cybersecurity risk management. The goals of the primer are to increase awareness of cybersecurity as it applies to highway and public transportation; plant the seeds of organizational culture change; address those situations where the greatest risks lie; and provide industry-specific approaches to monitoring, responding to and mitigating cyber threats. Individual chapters address: myths of cybersecurity; risk management, risk assessment and asset evaluation; plans and strategies, establishing priorities, organizing roles and responsibilities; transportation operations cyber systems; countermeasures; training; and security programs and support frameworks. Critical Infrastructure Protection: Sector-Specific Agencies Need to Better Measure Cybersecurity Progress.
34 Citation. Wilshusen, Gregory C. Critical Infrastructure Protection: Sector-Specific Agencies Need to Better Measure Cybersecurity Progress. U.S. Government Accountability Office, 2015, 82p. Available: http://trid.trb.org/view/1375467 Synopsis: U. S. critical infrastructures, such as financial institutions, commercial buildings, and energy production and transmission facilities, are systems and assets, whether physical or virtual, vital to the nationâs security, economy, and public health and safety. To secure these systems and assets, federal policy and the NIPP establish responsibilities for federal agencies designated as sector-specific agencies (SSA), including leading, facilitating, or supporting the security and resilience programs and associated activities of their designated critical infrastructure sectors. The Government Accountability Office's (GAOâs) objectives were to determine the extent to which SSAs have (1) identified the significance of cyber risks to their respective sectorsâ networks and industrial control systems (ICS), (2) taken actions to mitigate cyber risks within their respective sectors, (3) collaborated across sectors to improve cybersecurity, and (4) established performance metrics to monitor improvements in their respective sectors. To conduct the review, GAO analyzed policy, plans, and other documentation and interviewed public and private sector officials for 8 of 9 SSAs with responsibility for 15 of 16 sectors. GAO recommends that certain SSAs collaborate with sector partners to develop performance metrics and determine how to overcome challenges to reporting the results of their cyber risk mitigation activities. Four of these agencies concurred with GAOâs recommendation, while two agencies did not comment on the recommendations. Maritime Critical Infrastructure Protection: Department of Homeland Security's (DHS) Needs to Enhance Efforts to Address Port Cybersecurity Citation. Wilshusen, Gregory C. Maritime Critical Infrastructure Protection: DHS Needs to Enhance Efforts to Address Port Cybersecurity. U.S. Government Accountability Office, 2015, 14p. Available: http://trid.trb.org/view/1371372 Synopsis: The nationâs maritime ports handle more than $1.3 trillion in cargo each year: a disruption at one of these ports could have a significant economic impact. Increasingly, port operations rely on computerized information and communications technologies, which can be vulnerable to cyber-based attacks. Federal entities, including the DHSâs Coast Guard and the FEMA, have responsibilities for protecting ports against cyber-related threats. The GAO has designated the protection of federal information systems as a government-wide high-risk area since 1997, and in 2003 expanded this to include systems supporting the nationâs critical infrastructure. This statement by Gregory C. Wilshusen, Director, Information Security Issues, addresses (1) cyber-related threats facing the maritime port environment and (2) steps DHS has taken to address cybersecurity in that environment. In preparing this statement, GAO relied on work supporting its June 2014 report on cybersecurity at ports. (GAO-14-459). In its June 2014 report on port cybersecurity, GAO recommended that the Coast Guard include cyber risks in its updated risk assessment for the maritime environment, address cyber risks in its guidance for port security plans, and consider reestablishing the sector coordinating council. GAO also recommended that FEMA ensure funding decisions for its port security grant program are informed by subject matter expertise and a comprehensive risk assessment. DHS has partially addressed two of these recommendations since GAOâs report was issued.
35 Guidebook on Best Practices for Airport Cybersecurity Citation. Murphy, Randall J; Sukkarieh, Michael; Haass, Jon; Hriljac, Paul. ACRP Report 140: Guidebook on Best Practices for Airport Cybersecurity, Transportation Research Board of the National Academies, Washington, DC, 2015, 162p. Available: http://trid.trb.org/view/1360787 Synopsis: Cybersecurity is a growing issue for all organizations, including airports. While the risks to traditional information technology (IT) infrastructure are often highlighted, many airports also rely on industrial control systems (ICS)that introduce risks that are less apparent. The increasing practice of Bring Your Own Device (BYOD), whereby employees use their own personal devices for business purposes such as email and remote access to airport systems, brings its own risks that must be managed. These risks cannot be eliminated, but they can be reduced through implementation of industry standards, best practices, and awareness programs for employees. This report provides resources for airport managers and IT staff to reduce or mitigate inherent risks of cyberattacks on technology-based systems. Traditional IT infrastructure such as servers, desktops, and network devices are covered along with increasingly sophisticated and interconnected industrial control systems (ICS), such as baggage handling, temperature control, and airfield lighting systems. Accompanying this guidebook is a CD-ROM (CRP-CD-171) of multimedia material that can be used to educate all staff at airports about the need, and how, to be diligent against cybersecurity threats. A Summary of Cybersecurity Best Practices Citation. McCarthy, Charlie; Harnett, Kevin; Carter, Art. A Summary of Cybersecurity Best Practices. Volpe National Transportation Systems Center; National Highway Traffic Safety Administration, 2014, 40p. Available: http://trid.trb.org/view/1329314 Synopsis: This report contains the results and analysis of a review of best practices and observations in the field of cybersecurity involving electronic control systems across a variety of industry segments where the safety-of-life is concerned. This research provides relevant benchmarks that are essential to making strategic decisions over the next steps for the National Highway Traffic Safety Administration's (NHTSAâs) research program. This publication is part of a series of reports that describe the authors' initial work under the goal of facilitating cybersecurity best practices in the automotive industry (Goals 1 and 2). The information presented herein increases the collective knowledge base in automotive cybersecurity; helps identify potential knowledge gaps; helps describe the risk and threat environments; and helps support follow-on tasks that could be used to establish security guidelines. Assessment of the Information Sharing and Analysis Center Model Citation. McCarthy, Charlie; Harnett, Kevin; Carter, Art; Hatipoglu, Cem. Assessment of the Information Sharing and Analysis Center Model. Volpe National Transportation Systems Center; National Highway Traffic Safety Administration, 2014, 46p. Available: http://trid.trb.org/view/1341933 Synopsis: An Information Sharing and Analysis Center (ISAC) is a trusted, sector-specific entity that can provide a 24-hour per day and 7-day per week secure operating capability that establishes
36 the coordination, information sharing, and intelligence requirements for dealing with cybersecurity incidents, threats, and vulnerabilities. An ISAC can serve as an industry resource by which to gather key information about cybersecurity events and issues and identify, communicate, and analyze potential impacts of such concerns to the sector. This report presents findings from an assessment of the ISAC model, and how ISACâs are effectively implemented in other sectors. The report also explains how a new sector ISAC could be formed by leveraging existing ISAC models. This publication supports the goal of facilitating the establishment of a cybersecurity information sharing forum in the automotive sector (Goal 2). Maritime Critical Infrastructure Protection: DHS Needs to Better Address Port Cybersecurity Citation. Maritime Critical Infrastructure Protection: DHS Needs to Better Address Port Cybersecurity. U.S. Government Accountability Office, 2014, 54p. Available: http://trid.trb.org/view/1312046 Synopsis: U.S. maritime ports handle more than $1.3 trillion in cargo annually. The operations of these ports are supported by information and communication systems, which are susceptible to cyber-related threats. Failures in these systems could degrade or interrupt operations at ports, including the flow of commerce. Federal agenciesâin particular DHSâand industry stakeholders have specific roles in protecting maritime facilities and ports from physical and cyber threats. The GAOâs objective was to identify the extent to which DHS and other stakeholders have taken steps to address cybersecurity in the maritime port environment. GAO examined relevant laws and regulations; analyzed federal cybersecurity-related policies and plans; observed operations at three U.S. ports selected based on being a high-risk port and a leader in calls by vessel type, e.g. container; and interviewed federal and nonfederal officials. GAO recommends that DHS direct the Coast Guard to (1) assess cyber-related risks, (2) use this assessment to inform maritime security guidance, and (3) determine whether the sector coordinating council should be reestablished. DHS should also direct the FEMA to (1) develop procedures to consult DHS cybersecurity experts for assistance in reviewing grant proposals and (2) use the results of the cyber risk assessment to inform its grant guidance. DHS concurred with GAOâs recommendations. Critical Infrastructures: Background, Policy, and Implementation Citation. Moteff, John D. Critical Infrastructures: Background, Policy, and Implementation. Congressional Research Service, 2014, 39p. Available: http://trid.trb.org/view/1312743 Synopsis: The nationâs health, wealth, and security rely on the production and distribution of certain goods and services. The array of physical assets, functions, and systems across which these goods and services move are called critical infrastructures (e.g., electricity, the power plants that generate it, and the electric grid upon which it is distributed). The national security community has been concerned for some time about the vulnerability of critical infrastructure to both physical and cyberattack. In May 1998, President Clinton released Presidential Decision Directive No. 63. The Directive set up groups within the federal government to develop and implement plans that would protect government-operated infrastructures and called for a dialogue between government and the private sector to develop a National Infrastructure Assurance Plan that would protect all of the nationâs critical infrastructures by the year 2003. While the Directive called for both physical and cyber protection from both man-made and natural events, implementation focused on cyber
37 protection against man-made cyber events (i.e., computer hackers). Following the destruction and disruptions caused by the September 11 terrorist attacks in 2001, the nation directed increased attention towards physical protection of critical infrastructures. Over the intervening years, policy, programs, and legislation related to physical security of critical infrastructure have stabilized to a large extent. However, current legislative activity has refocused on cybersecurity of critical infrastructure. This report discusses in more detail the evolution of a national critical infrastructure policy and the institutional structures established to implement it. The report highlights two primary issues confronting Congress going forward, both in the context of cybersecurity: information sharing and regulation. Critical Infrastructure Protection: More Comprehensive Planning Would Enhance the Cybersecurity of Public Safety Entitiesâ Emerging Technology Citation. Critical Infrastructure Protection: More Comprehensive Planning Would Enhance the Cybersecurity of Public Safety Entitiesâ Emerging Technology. U.S. Government Accountability Office, 2014, 41p. Available: http://trid.trb.org/view/1290381 Synopsis: Individuals can contact fire, medical, and police first responders in an emergency by dialing 911. To provide effective emergency services, public safety entities such as 911 call centers use technology including databases that identifies phone number and location data of callers. Because these critical systems are becoming more interconnected, they are also increasingly susceptible to cyber-based threats that accompany the use of Internet-based services. This, in turn, could impact the availability of 911 services. The U.S. GAO was asked to review federal coordination with state and local governments regarding cybersecurity at public safety entities. The objective was to determine the extent to which federal agencies coordinated with state and local governments regarding cybersecurity efforts at emergency operations centers, public safety answering points, and first responder organizations involved in handling 911 emergency calls. The five identified federal agencies (Departments of Homeland Security, Commerce, Justice, and Transportation and Federal Communications Commission (FCC)) have to varying degrees, coordinated cybersecurity-related activities with state and local governments. These activities included (1) supporting critical infrastructure protection-related planning, (2) issuing grants, (3) sharing information, (4) providing technical assistance, and (5) regulating and overseeing essential functions. However, except for supporting critical infrastructure planning, federal coordination of these activities was generally not targeted towards or focused on the cybersecurity of state and local public safety entities involved in handling 911 emergency calls. Under the critical infrastructure protection planning activity, the DHS coordinated with state and local governments and other federal stakeholders to complete the Emergency Services Sector-Specific Plan. The plan is to guide the sector, including the public safety entities, in setting protective program goals and objectives, identifying assets, assessing risks, prioritizing infrastructure components and programs to enhance risk mitigation, implementing protective programs, measuring program effectiveness, and incorporating research and development of technology initiatives into sector planning efforts. It also addressed aspects of cybersecurity of the current environment. However, the plan did not address the development and implementation of more interconnected, Internet-based planned information technologies, such as the next generation of 911 services. According to DHS officials, the plan did not address these technologies, in part, because the process for updating the sector- specific plan will begin after the release of the revised National Infrastructure Protection Planâa unifying framework to enhance the safety of the nationâs critical infrastructure. A revised plan was
38 released in December 2013, and, according to DHS, a new sector-specific plan is estimated to be completed in December 2014. Until DHS, in collaboration with stakeholders, addresses the cybersecurity implications of the emerging technologies in planning activities, information systems are at an increased risk of failure or being unavailable at critical moments. Under the other four activities, federal agencies performed some coordination related activities for public safety entities including administering grants for information technology enhancements, sharing information about cyber-based attacks, and providing technical assistance through education and awareness efforts. For example, the Departments of Transportation and Commerce allocated $43.5 million in grants to states over a 3-year period, starting in September 2009, to help implement enhancements to 911 system functionality. While these grants were not targeted towards the cybersecurity of these systems, cybersecurity was not precluded from the allowed use of the funds. GAO recommends that the Secretary of Homeland Security collaborate with emergency services sector stakeholders to address the cybersecurity implications of implementing technology initiatives in related plans. The Critical Infrastructure Gap: U.S. Port Facilities and Cyber Vulnerabilities Citation. Kramek, Joseph. The Critical Infrastructure Gap: U.S. Port Facilities and Cyber Vulnerabilities. Brookings Institution, 2013, 50p. Available: http://trid.trb.org/view/1325343 Synopsis: This paper looks at the current state of cybersecurity as it relates to U.S. ports. Topics include port security prior to and post-September 11th, the Maritime Transportation Security Act, the Port Security Grant Program, and cybersecurity awareness, preparedness and recovery. Case studies outlining current port security and practices are presented for the Port of Baltimore, Maryland, the Port of Houston, Texas, the Port of Los Angeles, California, the Port of Long Beach, California, the Port of Vicksburg, Mississippi, and the Port of Beaumont, Texas. Of the six ports studied most had not conducted a cybersecurity vulnerability assessment nor developed a cyber incident response plan. Policy recommendations are provided to address port cybersecurity improvements. Critical Infrastructure Security: Assessment, Prevention, Detection, Response Citation. Critical Infrastructure Security: Assessment, Prevention, Detection, Response. WIT Press, 2012, 326p. Available: http://trid.trb.org/view/1247665 Synopsis: This book examines best practices and trends in infrastructure security at both the physical and digital level. Methods and tools for assessing, preventing, detecting and responding to security threats are outlined. The book is divided into five parts: (1) Security risk and vulnerability assessment; (2) Modeling and simulation tools; (3) Cybersecurity; (4) Monitoring and surveillance; (5) Security systems integration and alarm management. Homeland Security: DHSâs Progress and Challenges in Key Areas of Maritime, Aviation, and Cybersecurity Citation. Homeland Security: DHSâs Progress and Challenges in Key Areas of Maritime, Aviation, and Cybersecurity. U.S. Government Accountability Office, 2009, 25p. Available: http://trid.trb.org/view/906303
39 Synopsis: Securing the nationâs transportation and information systems is a primary responsibility of the DHS. Within DHS, the Transportation Security Administration (TSA) is responsible for securing all transportation modes; U.S. Customs and Border Protection (CBP) is responsible for cargo container security; the U.S. Coast Guard is responsible for protecting the maritime environment; and the National Protection and Programs Directorate is responsible for the cybersecurity of critical infrastructure. This statement focuses on the progress and challenges DHS faces in key areas of maritime, aviation, and cybersecurity. It is based on U.S. GAO products issued from June 2004 through November 2009, as well as ongoing work on air cargo security. DHS has made progress in enhancing security in the maritime sector, but key challenges remain. For example, as part of a statutory requirement to scan 100 percent of U.S.-bound container cargo by July 2012, CBP has implemented the Secure Freight Initiative at select foreign ports. However, CBP does not have a plan for fully implementing the 100 percent scanning requirement by July 2012 because it questions the feasibility, although it has not performed a feasibility analysis of the requirement. Rather, CBP has planned two new initiatives to further strengthen the security of container cargo, but these initiatives will not achieve 100 percent scanning. Further, TSA, the Coast Guard, and the maritime industry took a number of steps to enroll over 93 percent of the estimated 1.2 million users in the Transportation Worker Identification Credential (TWIC) program (designed to help control access to maritime vessels and facilities) by the April 15, 2009 compliance deadline, but they experienced challenges resulting in delays and in ensuring the successful execution of the TWIC pilot. While DHS and the Coast Guard have developed a strategy and programs to reduce the risks posed by small vessels, they face ongoing resource and technology challenges in tracking small vessels and preventing attacks by such vessels. In the aviation sector, TSA has made progress in meeting the statutory mandate to screen 100 percent of air cargo transported on passenger aircraft by August 2010 and in taking steps to strengthen airport security, but TSA continues to face challenges. TSAâs efforts include developing a system to allow screening responsibilities to be shared across the domestic air cargo supply chain, among other steps. Despite these efforts, TSA and the industry face a number of challenges including the voluntary nature of the program, and ensuring that approved technologies are effective with air cargo. TSA also does not expect to meet the mandated 100 percent screening deadline as it applies to air cargo transported into the U.S., in part due to existing screening exemptions for this type of cargo and challenges in harmonizing security standards with other nations. GAO is reviewing these issues as part of its ongoing work and will issue a final report next year. In addition, TSA has taken a variety of actions to strengthen airport security by, among other things, implementing a worker screening program; however, TSA still faces challenges in this area. DHS has made progress in strengthening cybersecurity, such as addressing some lessons learned from a cyber attack exercise, but further actions are warranted. Since 2005, GAO has reported that DHS has not fully satisfied its key responsibilities for protecting the nationâs computer-reliant critical infrastructures and has made related recommendations to DHS, such as bolstering cyber analysis and warning capabilities and strengthening its capabilities to recover from Internet disruptions. DHS has since developed and implemented certain capabilities to satisfy aspects of its responsibilities, but it has not fully implemented GAOâs recommendations and, thus, more action is needed to address the risk to critical cybersecurity infrastructure. Freight Rail Security: Actions Have Been Taken to Enhance Security, but the Federal Strategy Can Be Strengthened and Security Efforts Better Monitored
40 Citation. Freight Rail Security: Actions Have Been Taken to Enhance Security, but the Federal Strategy Can Be Strengthened and Security Efforts Better Monitored. U.S. Government Accountability Office, 2009, 129p. Available: http://trid.trb.org/view/889626 Synopsis: An attack on the U.S. freight rail system could be catastrophic because rail cars carrying highly toxic materials often traverse densely populated urban areas. The DHS TSA is the federal entity primarily responsible for securing freight rail. The U.S. GAO was asked to assess the status of efforts to secure this system. This report discusses (1) stakeholder efforts to assess risks to the freight rail system and TSAâs development of a risk-based security strategy; (2) actions stakeholders have taken to secure the system since 2001, TSAâs efforts to monitor and assess their effectiveness, and any challenges to implementing future actions; and (3) the extent to which stakeholders have coordinated efforts. Federal and industry stakeholders have completed a range of actions to assess risks to freight rail since September 2001, and TSA has developed a security strategy; however, TSAâs efforts have primarily focused on one threat, and its strategy does not fully address federal guidance or key characteristics of a successful national strategy. Specifically, TSAâs efforts to assess vulnerabilities and potential consequences to freight rail have focused almost exclusively on rail shipments of certain highly toxic materials, in part, because of concerns about their security in transit and limited resources. However, other federal and industry assessments have identified additional potential security threats, including risks to critical infrastructure and cybersecurity. Although many stakeholders agreed with TSAâs initial strategy, going forward TSA has agreed that including other identified threats in its freight rail security strategy is important, and reported that it is reconsidering its strategy to incorporate other threats. Additionally, in 2004, GAO reported that successful national strategies should identify performance measures with targets, among other elements. TSAâs security strategy could be strengthened by including targets for three of its four performance measures and revising its approach for the other measure to ensure greater consistency in how performance results are quantified. Federal and industry stakeholders have also taken a range of actions to secure freight rail, many of which have focused on securing certain toxic material rail shipments and have been implemented by industry voluntarily; however, TSA lacks a mechanism to monitor security actions and evaluate their effectiveness, and new requirements could pose challenges for future security efforts. GAOâs Standards for Internal Control in the federal government calls for controls to be designed to ensure ongoing monitoring. While the freight rail industry has taken actions to better secure shipments and key infrastructure, TSA has limited ability to assess the impacts of these actions because it lacks a mechanism to systematically track them and evaluate their effectiveness. Having such information could strengthen TSAâs efforts to efficiently target its resources to where actions have not been effective. New, mandatory security planning and procedural requirements will also necessitate additional federal and industry efforts and resources, and may pose some implementation challenges for both federal and industry stakeholders. Federal and industry stakeholders have also taken a number of steps to coordinate their freight rail security efforts; however, federal coordination can be enhanced by more fully leveraging the resources of all relevant federal agencies. GAO previously identified a number of leading practices for effective coordination that could help TSA strengthen coordination with federal and private sector stakeholders. Cybersecurity Resources Protection of Transportation Infrastructure from Cyber Attacks: A Primer (2016)
41 Citation. NCHRP Web-Only Document 221/TCRP Web-Only Document 67: Protection of Transportation Infrastructure from Cyber Attacks: A Primer, Transportation Research Board of the National Academies, Washington, DC, 2016. Available: https://www.nap.edu/download/23516 Synopsis. This Primer provides transportation organizations with reference materials concerning cybersecurity concepts, guidelines, definitions, and standards. It delivers strategic, management, and planning information associated with cybersecurity and its applicability to transit and state DOT operations. It includes definitions and rationales that describe the principles and practices that enable effective cybersecurity risk management. The primer provides transportation managers and employees with greater context and information regarding the principles of information technology and operations systems security planning and procedures. The report is supplemented with an Executive Briefing for use as a 20-minute presentation to senior executives on security practices for transit and DOT cyber and industrial control systems (ICS). Guide to Industrial Control Systems (ICS) Security, Second Edition Citation. Special Publication 80-82, Guide To Industrial Control Systems (ICS) Security, Second Edition, National Institute For Standards And Technology, 2015. Available: http://csrc.nist.gov/publications/ drafts/800-82r2/sp800_82_r2_second_draft.pdf Synopsis. The Industrial Control Systems (ICS) security guide advises on how to reduce the vulnerability of computer-controlled industrial systems to malicious attacks, equipment failures, errors, inadequate malware protection and other threats. The Second Edition of the Guide includes new guidance on how to tailor traditional IT security controls to accommodate unique industrial control systems (ICS) performance, reliability and safety requirements, as well as updates to sections on threats and vulnerabilities, risk management, recommended practices, security architectures and security capabilities and tools. Recommended Practice: Securing Control and Communications Systems in Transit Environments Citation. APTA Standards Development Program Recommended Practice: Securing Control and Communications Systems in Transit Environments, APTA. Available: Part I: http://www.apta.com/resources/standards/documents/apta-ss-ccs-rp-001-10.pdf Part II: http://www.apta.com/resources/standards/documents/apta-ss-ccs-rp-002-13.pdf Part IIIa and IIIb in development Synopsis. This document covers recommended practices for securing control and communications systems in transit environments. These recommended practices address the importance of control and communications security to a transit agency, provide a survey of the various systems that constitute typical transit control and communication systems, and identify the steps that an agency would follow to set up a successful security program. The documents address the security of the following passenger rail and/or bus systems: SCADA, traction power control, emergency ventilation control, alarms and indications, fire/intrusion detection systems, train control/signaling,
42 fare collection, automatic vehicle location (AVL),physical security feeds (CCTV, access control), public information systems, public address systems, and radio/wireless/related communication. NIST Cybersecurity Framework Available: http://www.nist.gov/cyberframework/ The National Institute of Standards and Technology (NIST), the Federal Information Processing Standards (FIPS), with transportation specific guidance available from APTA and FHWA, have developed recommended practices and standards. There are international standards and recommendations from the International Organization for Standardization (ISO), the Information Systems Audit and the Control Association (ISACA), and Control Objectives for Information and related Technology (COBIT). U.S. Department of Transportation (USDOT) Cybersecurity Action Team The U.S. Department of Transportation (USDOT) developed a Cybersecurity Action Team, as part of Executive Order 13636, to implement o the Departmentâs Cyber Incident Response Capability Program. The team monitors, alerts and advises the ITS and surface transportation communities of incidents and threats, and leverages the extensive body of assessments and research done by FHWA staff related to the security threats and vulnerabilities of the United Statesâ transportation systems. US-CERT and Industrial Control Systems (ICS-CERT) Cyber Information Sharing and Collaboration Program Incident Hotline: 1-888-282-0870 Website: https://www.us-cert.gov/ The U.S. Computer Emergency Readiness Team (US-CERT), part of DHS' National Cybersecurity and Communications Integration Center (NCCIC), provides technical assistance, coordinates cyber information sharing and proactively manage cyber risks through its 24x7 operations center. US-CERT distributes vulnerability and threat information through its National Cyber Awareness System (NCAS), and operates a Vulnerability Notes Database to provide technical descriptions of system vulnerabilities. Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) Available: https://ics-cert.us-cert.gov/ The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) operates cybersecurity operations centers focused on control systems security as part of the NCCIC. The team: ⢠Responds to and analyzes industrial control systems (ICS) related incidents ⢠Provides onsite support for incident response and forensics ⢠Conducts malware analysis ⢠Coordinates responsible disclosure of ICS vulnerabilities/mitigations ⢠Shares vulnerability information and threat analysis through information products
43 and alerts ⢠Provides security awareness training courses (see http://ics-cert.us-cert.gov/Training- Available-Through-ICS-CERT). Transportation Security Administration (TSA) Transportation Systems Sector Cybersecurity Working Group (TSSCWG) Available: https://www.dhs.gov/publication/cipac-trans-cybersecurity-agendas The TSA has authority to regulate cybersecurity in the transportation sector and provides cybersecurity pamphlets, a weekly newsletter, cybersecurity exercise support, and incident- specific threat briefings. TSA has pursued collaborative and voluntary approaches with industry. TSA DHS facilitates the Cybersecurity Assessment and Risk Management Approach (CARMA) for companies requesting assessments. TSA has hosted cybersecurity- focused Intermodal Security Training and Exercise Program (I-STEP) exercises, most recently in August 2014. TSA and its industry partners established the TSSCWG to advance cybersecurity across all transportation modes. The TSSCWG strategy, completed in mid-2012, stated, âThe sector will manage cybersecurity risk through maintaining and enhancing continuous awareness and promoting voluntary, collaborative, and sustainable community action.â The TSSCWG is developing implementation guidance for adoption of the NIST framework. National Institute of Standards and Technology (NIST) Cybersecurity Framework Available: http://www.nist.gov/cyberframework/ The NIST is an agency of the U.S. Department of Commerce. The Computer Security Division (CSD), a component of NISTâs Information Technology Laboratory (ITL), provides standards and technology to protect information systems against threats to information and services. Executive Order 13636, Improving Critical Infrastructure Cybersecurity (2013) directed NIST to work with stakeholders to develop a voluntary cybersecurity framework â based on existing standards, guidelines, and practices - for reducing cyber risks to critical infrastructure. Cybersecurity Framework (CSF) Reference Tool Available: http://www.nist.gov/cyberframework/csf_reference_tool.cfm A runtime database solution, have been created the allows the user to browse the Framework Core by functions, categories, subcategories, informative references, search for specific words, and export the current viewed data to various file types. NIST National Vulnerability Database Available: http://nvd.nist.gov National Vulnerability Database (NVD) is the U.S. government repository of standards-based vulnerability management data that includes databases of security checklists, security-related software flaws, misconfigurations, product names, and impact metrics.
44 NIST Computer Security Division's Computer Security Resource Center (CSRC) Available: http://csrc.nist.gov/index.html This Center facilitates broad sharing of information security tools and practices, provides a resource for information security standards and guidelines, and identifies key security web resources to support users in industry, government, and academia. The CSRC is the primary gateway for gaining access to NIST computer security publications, standards, and guidelines plus other useful security-related information. NIST Security Publications Available: http://csrc.nist.gov/publications/PubsSPs.html NIST has published over 300 Information Security guides that include FIPS, the Special Publication (SP) 800 series, ITL Bulletins, and NIST Interagency Reports (NIST IR). Most commonly referenced NIST publications include: ⢠Special Publication 800-12: An Introduction to Computer Security: The NIST Handbook (1995). Elements of security, roles and responsibilities, common threats, security policy, and program management. Initially created for the federal government, most practices are applicable to the private sector. ⢠Special Publication 800-14 Generally Accepted Principles and Practices for Securing Information Technology Systems (1996) describes common security principles that are used. It provides a high-level description of what should be incorporated within a computer security policy. It describes what can be done to improve existing security as well as how to develop a new security practice. Eight principles and 14 practices are described within this document. ⢠Special Publication 800-16 Information Technology Security Training Requirements: A Role- and Performance-Based Model (2014). Learning continuum model, security literacy and basics, role-based training. ⢠Special Publication 800-30, Risk Management Guide for Information Technology Systems (2012). Risk management, assessment, mitigation. ⢠Special Publication 800-37 Guide for Applying the Risk Management Framework to Federal Information Systems (2010) ⢠Special Publication 800-39 Integrated Enterprise-Wide Risk Management: Organization, Mission, and Information System View (2011). ⢠Special Publication 800-53, Recommended Security Controls for Federal Information Systems and Organizations (2013). Security control fundamentals, baselines by system-impact level, common controls, and tailoring guidelines that are applied to a system to make it "more secure". ⢠Special Publication 800-60, Revision 1, Guide for Mapping Types of Information and Information Systems to Security Categories, (2008). Security objectives and types of potential losses, assignment of impact levels and system security category. ⢠Special Publication 800-82, Guide to Industrial Control Systems ( I C S ) Security (2014). Overview of industrial control systems (ICS), threats and vulnerabilities, risk factors, incident scenarios, security program development. ⢠Special Publication 800-97, Establishing Wireless Robust Security Networks: A
45 Guide to IEEE 802.11i (2007) ⢠Special Publication 800-100, Information Security Handbook: A Guide for Managers (2006). Governance, awareness and training, capital planning, interconnecting systems, performance measures, security planning, contingency planning. ⢠Special Publication 800-122, Guide to Protecting the Confidentiality of Personally Identifiable Information (PII) (2010). Identifying, PII, impact levels, confidentiality safeguards, incident response. ⢠Special Publication 800-150 Guide to Cyber Threat Information Sharing, (2016) ⢠Special Publication 800-160 Systems Security Engineering: An Integrated Approach to Building Trustworthy Resilient Systems, Second Public Draft (2016) Information Sharing and Analysis Centers (ISACâs) Available: http://www.isaccouncil.org/home.html The purpose of ISAC is to serve as the conduit for cross modal lessons learned and best practices in ICS cybersecurity, and to provide a forum for partnership, outreach, and information sharing. ⢠Surface Transportation Information and Sharing Analysis Center Available: https://www.surfacetransportationisac.org/ The ST-ISAC was formed at the request of the Department of Transportation. The ISAC provides a secure cyber and physical security capability for owners, operators and users of critical infrastructure. Security and threat information is collected from worldwide resources, then analyzed and distributed to members to help protect their vital systems from attack. The ISAC also provides a vehicle for the anonymous or attributable sharing of incident, threat and vulnerability data among the members. Members have access to information and analytical reporting provided by other sources, such as the U.S. and foreign governments; law enforcement agencies, technology providers and international computer emergency response teams (CERTâs). ⢠Public Transportation Information Sharing and Analysis Center Available: http://www.apta.com/resources/safetyandsecurity/Pages/ISAC.aspx The PT-ISAC is a trusted, sector-specific entity which provides to its constituency a 24/7 Security Operating Capability that established the sector's specific information/intelligence requirements for incidences, threats and vulnerabilities. Based on its sector-focused subject matter analytical expertise, the ISAC then collects, analyzes, and disseminates alerts and incident reports It provides to its membership and helps the government understand impacts for their sector. It provides an electronic, trusted ability for the membership to exchange and share information on all threats, physical and cyber, in order to defend public transportation systems and critical infrastructure. This includes analytical support to the government and other ISACâs regarding technical sector details and in mutual information sharing and assistance during actual or potential sector disruptions, whether caused by intentional or natural events.
46 ⢠Over the Road Bus Information Sharing and Analysis Center (OTRB ISAC) The OTRB ISAC provides cyber and physical security warning and incident reporting for the OTR transportation segment. Information and news are compiled and extracted from multiple sources by OTRB ISAC analysts for the purpose of supporting ISAC member homeland security awareness. News alerts and reports are distributed to members by the OTRB ISAC. ⢠MultiState-ISAC (MS-ISAC) Available: http://msisac.cisecurity.org/ The MS-ISAC is the focal point for cyber threat prevention, protection, response and recovery for the nationâs state, local, tribal, and territorial (SLTT) governments. The MS- ISAC 24x7 cybersecurity operations center provides real-time network monitoring, early cyber threat warnings and advisories, vulnerability identification and mitigation and incident response. The Multi-State Information Sharing and Analysis Center (MS-ISAC) is a collaborative state and local government-focused cybersecurity entity that is significantly enhancing cyber threat prevention, protection, and response and recovery throughout the states of our nation. The mission of the MS-ISAC is to provide a common mechanism for raising the level of cybersecurity readiness and response in each state/territory and with local governments. The MS-ISAC provides a central resource for gathering information on cyber threats to critical infrastructure and providing two-way sharing of information between and among the states, territories and with local government. ⢠Supply Chain ISAC Available: https://secure.sc-investigate.net/SC-ISAC/ISACHome.aspx The Supply Chain ISAC offers the most comprehensive forum for collaboration on critical security threats, incidents and vulnerabilities to the global supply chain. Its mission is to facilitate communication among supply chain dependent industry stakeholders, foster a partnership between the private and public sectors to share critical information, collect, analyze and disseminate actionable intelligence to help secure the global supply chain, provide an international perspective through private sector subject matter experts and help protect the critical infrastructure of the United States. National Cyber Investigative Joint Task Force â Analytical Group Available: http://www.fbi.gov/about-us/investigate/cyber/ncijtf In 2008, the U.S. President mandated the National Cyber Investigative Joint Task Force (NCIJTF) to be the focal point for all government agencies to coordinate, integrate, and share information related to all domestic cyber threat investigations. The Federal Bureau of Investigation (FBI) is responsible for developing and supporting the joint task force, which includes 19 intelligence agencies and law enforcement. Internet Crime Complaint Center (IC3) Available: http://www.ic3.gov/default.aspx
47 The Internet Crime Complaint Center (IC3) is a partnership between the FBI and the National White Collar Crime Center (NW3C). Internet crime complaints are reported online on the IC3 site. IC3 analysts review and research the complaints, disseminating information to the appropriate federal, state, local, or international law enforcement or regulatory agencies for criminal, civil, or administrative action, as appropriate. InfraGard Available: https://www.infragard.org/ InfraGard is a partnership between the FBI, state and local law enforcement agencies, and the private sector - businesses, academic institutions and other participants - dedicated to sharing information and intelligence to prevent hostile acts against the U.S. With over 80 chapters, InfraGard chapters conduct local meetings pertinent to their area. National Cybersecurity Center of Excellence (NCCoE) Available: http://nccoe.nist.gov/ Established in 2012 through a partnership among NIST, the State of Maryland and Montgomery County, the National Cybersecurity Center of Excellence is dedicated to furthering innovation through the rapid identification, integration and adoption of practical, standards-based cybersecurity solutions.
48 C. Emergency Management Program Transportation plays a critical and unique role in emergency response. As the National Response Framework (NRF) states, âThe ability to sustain transportation services, mitigate adverse economic impacts, meet societal needs, and move emergency relief personnel and commodities will hinge on effective transportation decisions at all levels.â Transportationâs unique role stems from the broad range of capabilities and responsibilities a transportation agency has: large and distributed workforces, easy access to heavy equipment and a robust communications infrastructure. To be ready for the agencyâs role, a comprehensive emergency management program must be in place within the agency. As a part of their function, state DOTs are responsible for creating all-hazards plans and ensuring that employees have the ability to implement them. These all-hazards plans must conform with and complement the planning activities of the rest of the stateâs operations and agencies as well as those of regional authorities. DOTs may coordinate planning efforts with other state agencies, including the state's Emergency Management Agency; county highway departments; with various agencies of the U.S. DOT; and with DOTs from other states to ensure activities can be easily integrated when necessary. DOTs also need to plan to receive and use resources provided by other states and the federal government during operations. In conducting these activities, DOTs should consider applicable standards and best practices for incorporating risk and resilience into functions and systems. Comprehensive Preparedness Guide 201, Second Edition (2013) Citation. Comprehensive Preparedness Guide 201, Second Edition, FEMA, 2013. Available: http://www.fema.gov/media-library- data/8ca0a9e54dc8b037a55b402b2a269e94/CPG201_htirag_2nd_edition.pdf Synopsis. The Comprehensive Preparedness Guide (CPG) provides for the development of local, state, tribal, territorial, and insular area emergency operations plans. FEMA released CPG 201 in 2012, with a Second Edition following in 2013. The First Edition of CPG 201 presented the basic steps of a Threat and Hazard Identification and Risk Assessment (THIRA) that included a process for identifying community-specific threats and hazards. It addressed setting capability targets for each core capability identified in the National Preparedness Goal; the Second Edition of CPG 201 included an estimation of resources needed to meet those capability targets. The Second Edition also included changes to the THIRA process, streamlining the number of steps to conduct a THIRA and providing additional examples. THIRA Information Sheet Available: http://www.fema.gov/media-library-data/1388146249060- 7b2abfe6be10c67c4070ed42deaaadf1/THIRA%20Information%20Sheet_20131104.pdf CPG 201 Supplement 1: THIRA Guide Toolkit Available: http://www.fema.gov/media-library-data/20130726-1831-25045- 0138/cpg_201_supp_1_thira_guide_toolkit_final_040312.pdf
49 Information Sheet ESF #1 Transportation Available: http://www.fema.gov/media-library-data/20130726-1913-25045- 2201/final_esf_1_transportation_20130501.pdf Managing Catastrophic Transportation Emergencies: A Guide for Transportation Executives Citation. Managing Catastrophic Transportation Emergencies: A Guide for Transportation Executives. AASHTO, 2015. Available: http://www.trb.org/Main/Blurbs/171299.aspx Synopsis. This Guide provides guidance to new chief executive officers (CEOs) about the roles and actions that CEOs take during emergency events. A Pre-Event Recovery Planning Guide for Transportation Citation. NCHRP Report 753: A Pre-Event Recovery Planning Guide for Transportation, Transportation Research Board of the National Academies, Washington, DC, 2013. Available: http://onlinepubs.trb.org/onlinepubs/nchrp/nchrp_rpt_753.pdf Synopsis. This Guide discussed the impact that response can have on recovery, noting that the response efforts can mitigate the damages and consequences of an event, and potentially reduce the time to recovery, such as quickly assessing damage and removing debris. Some response decisions, such as where to put debris, can have an impact on both short term and long-term recovery, as learned during the aftermath of Hurricane Katrina in New Orleans. Highlighting the differences between response and recovery, Report 753 also noted the importance of response and recovery team members understanding each otherâs roles and responsibilities, because often the two functions overlap. Considering Security and Emergency Management in The Planning of Transportation Projects: A Guide for Planners of New Transportation Projects, FHWA (2012) Citation. Considering Security and Emergency Management in The Planning of Transportation Projects: A Guide for Planners of New Transportation Projects, FHWA 2012. Available: http://www.planning.dot.gov/documents/consideringsecurityandem.pdf Synopsis. The U.S. FHWA has released this report designed to help ensure that security and emergency management are considered during the planning phase of highway-related infrastructure projects. Surface Transportation Security, Volume 6: Guide for Emergency Transportation Operations Citation. NCHRP Report 525: Surface Transportation Security, Volume 6: Guide for Emergency Transportation Operations, Transportation Research Board of the National Academies, Washington, DC, 2005. Available: http://www.trb.org/Main/Public/Blurbs/156212.aspx
50 Synopsis. This Guide supports development of a formal program for the improved management of traffic incidents, natural disasters, security events, and other emergencies on the highway system. It outlines a coordinated, performance-oriented, all-hazard approach called âEmergency Transportation Operationsâ (ETO). The guide focuses on an enhanced role for state DOTs as participants with the public safety community in an interagency process. Using Highways During Evacuation Operations for Events with Advance Notice: Routes to Effective Evacuation Planning Primer Series Citation. Houston, Nancy. Using Highways During Evacuation Operations for Events with Advance Notice: Routes to Effective Evacuation Planning Primer Series. No. FHWA-HOP-06- 109. 2006. Available: http://www.ops.fhwa.dot.gov/publications/evac_primer/00_evac_primer.htm Synopsis. Evacuations may involve hundreds or hundreds of thousands of people. Regardless of the numbers, in each and every instance, the transportation network plays a key role in evacuating people out of harmâs way. Recognizing the unique challenges posed by the disaster environment on mobility and the safe and secure movement of people and goods, the U.S. DOTâs FHWA seeks to improve evacuation planning and implementation by bringing to the emergency management community new ways of better using the transportation network before and during evacuations. This document constitutes the first of a primer series entitled âRoutes to Effective Evacuations.â This primer is intended as a tool to aid local and state planners to maximize the use of the highway network in the development and execution of evacuation plans for their communities, states or regions. Final Report for the Application of Technology to Transportation Operations in Biohazard Situations Citation. Final Report for the Application of Technology to Transportation Operations in Biohazard Situations, FHWA, 2005. Available: http://www.its.dot.gov/eto/docs/transops_biohazard/executive.htm Synopsis. The U.S. FHWA has released a report that examines the role of transportation agencies during a biohazard situation. The report is designed to help state and local transportation agencies perform the roles expected of them during all phases of a biohazard incident. According to the report, those roles can differ significantly from the ones they typically perform during other types of emergencies. A Guide to Transportationâs Role in Public Health Disasters Citation. NCHRP Report 525: Surface Transportation Security, Volume 10: A Guide to Transportationâs Role in Public Health Disasters. Transportation Research Board of the National Academies, Washington, DC, 2006. Available: http://www.trb.org/Main/Public/Blurbs/156474.aspx
51 Synopsis. This Guide examines development of transportation response options to an extreme event involving chemical, biological, or radiological agents. The report contains technical information on chemical, biological, and radiological threats, including vulnerabilities of the transportation system to these agents and consequence-minimization actions that may be taken within the transportation system in response to events that involve these agents. The report also includes a spreadsheet tool, called the Tracking Emergency Response Effects on Transportation (TERET), that is designed to assist transportation managers with recognition of mass-care transportation needs and identification and mitigation of potential transportation-related criticalities in essential services during extreme events. The report includes a userâs manual for TERET, as well as a PowerPoint slide introduction to chemical, biological, and radiological threat agents designed as an executive-level communications tool based on summary information from the report.. Simplified Guide to the Incident Command System (ICS) for Transportation Professionals Citation. Simplified Guide to the Incident Command System (ICS) for Transportation Professionals, FHWA, 2006. Available: http://www.ops.fhwa.dot.gov/publications/ics_guide/index.htm Synopsis. The purpose of this Simplified Guide is to introduce the ICS to stakeholders who may be called upon to provide specific expertise, assistance, or material during highway incidents but who may be largely unfamiliar with ICS organization and operations. These stakeholders include transportation agencies and companies involved in towing and recovery, as well as elected officials and government agency managers at all levels. This document may also be beneficial to public safety professionals, who are familiar with ICS but may not fully understand how ICS concepts are applicable to transportation agencies. Public Transportation Emergency Mobilization and Emergency Operations Guide Citation. TCRP Report 86: Public Transportation Security, Volume 7: Public Transportation Emergency Mobilization and Emergency Operations Guide, Transportation Research Board of the National Academies, Washington, DC, 2005. Available: http://www.trb.org/Main/Blurbs/156130.aspx Synopsis. This report examines activities that may be taken by public transportation agencies working with their local communities to promote the early recognition of emergency events, expedite response to emergency events, establish multiagency coordination, and ensure that public transportation resources are available to support the response to an emergency event. Incorporating Security into the Transportation Planning Process Citation. NCHRP Report 525: Surface Transportation Security, Volume 3: Incorporating Security into the Transportation Planning Process, Transportation Research Board of the National Academies, Washington, DC, 2005. Available: http://www.trb.org/Main/Blurbs/155903.aspx
52 Synopsis. This report examines the status, constraints, opportunities, and strategies for incorporating security into transportation planning at the state and metropolitan levels. The report also examines security-related projects in state and metropolitan priority programming decisions. Continuity of Operations (COOP) Planning Guidelines for Transportation Agencies Citation. NCHRP Report 525: Surface Transportation Security, Volume 8: Continuity of Operations (COOP) Planning Guidelines for Transportation Agencies, Transportation Research Board of the National Academies, Washington, DC, 2005. Available: http://www.trb.org/Main/Blurbs/156474.aspx Synopsis. The report is designed to assist transportation agencies in evaluating and modifying existing operations plans, policies, and procedures, as called for in the NIMS. The planning guidelines in this report are supplemented online with downloadable worksheets, a template for a completed COOP plan, a series of brochures that can be used to explain the COOP planning process to staff, a draft PowerPoint presentation that may be customized and presented to transportation executive leadership, and more than 300 resource documents organized in an electronic COOP library. FHWA Emergency Transportation Operations Website Available: http://ops.fhwa.dot.gov/eto_tim_pse/index.htm The Office of Operations ETO home page, features information on the ETO for Disasters, Traffic Planning for Special Events (PSE) and Traffic Incident Management (TIM) programs. The site provides tools, guidance, capacity building and good practices that aid local and state DOTs and their partners in their efforts to improve transportation network efficiency and public/responder safety when a non-recurring event either interrupts or overwhelms transportation operations. Non- recurring events may range from traffic incidents to traffic PSE to disaster or emergency transportation operations (Disaster ETO). Work in ETO program areas focuses on using highway operational tools to enhance mobility and motorist and responder safety. Traffic Incident Management (TIM) TIM is a planned and coordinated program to detect and remove incidents and restore traffic capacity as safely and quickly as possible. TIM Gap Analysis Primer Available: http://ops.fhwa.dot.gov/eto_tim_pse/about/tim.htm#t3 Synopsis. This document provides guidance to federal, state and local TIM programs and their involved partners on the components needed to develop and sustain a successful full-fledged TIM program. The objectives of this primer are to: ⢠Identify and summarize the current state of TIM practice and activities at the national and state/local levels. ⢠Identify and summarize gaps found in TIM activities/information for national and state/local departments and agencies.
53 ⢠Identify and outline a framework for achieving a complete TIM program for the different levels of government utilizing national guidelines. ⢠Outline the key elements that are contained in successful TIM programs. The information contained within this document is geared towards multidisciplinary TIM stakeholders from both the public and private sectors. This includes but is not limited to personnel from transportation agencies, law enforcement, fire and rescue, EMS, public safety communications, emergency management, towing and recovery, hazardous materials (HazMat), utilities, contractors, and traffic information media. Making the Connection: Advancing Traffic Incident Management in Transportation Planning Citation. Making the Connection: Advancing Traffic Incident Management in Transportation Planning, FHWA, 2013. Available: http://www.ops.fhwa.dot.gov/publications/fhwahop13044/index.htm Synopsis. The intent of this primer is to inform and guide TIM professionals and transportation planners to initiate and develop collaborative relationships and advance TIM programs through the metropolitan planning process. The primer aims to inspire planners and TIM professionals to create transportation plans and programs that support regional TIM programs through TIM- focused objectives, performance measures, and TIM strategies and projects. The ultimate goal of this primer is to strengthen, support, and elevate regional TIM programs as a crucial, lower-cost strategy for reliability, safety, environmental improvements, and mobility. Senior Executive Transportation & Public Safety Summit Report Citation. Senior Executive Transportation & Public Safety Summit: National Traffic Incident Management Leadership & Innovation Roadmap for Success, FHWA, 2012. Available: http://ops.fhwa.dot.gov/eto_tim_pse/publications/publicsafetysummit/index.htm Synopsis. The 2012 Senior Executive Transportation & Public Safety Summit Report summarizes the proceedings, findings, and recommendations from a two-day Senior Executive Summit on Transportation and Public Safety, held June 26 and 27, 2012 at the United States Department of Transportation (USDOT) in Washington, DC. This forum of senior-level, multidisciplinary executives representing the transportation, law enforcement, fire and rescue, and EMS communities addressed major challenges and innovative solutions in enhancing the state of the practice nationally in TIM. Secretary of Transportation Ray LaHood, FHWA Deputy Administrator Greg Nadeau, and FHWA Executive Director Jeff Paniati provided opening remarks expressing the commitment of the entire Department to support safe, quick traffic incident response on the nation's roadways. Participants at the Summit discussed innovative practices in TIM policies, legislation, training and outreach. Summit highlights included discussions and presentations on the following issues: Improving responder and motorist safety and consistency among jurisdictions; Supporting TIM outreach initiatives and messaging; Enhancing state and local legislation and policies that advance TIM planning and operations, including Driver Removal and Authority Removal legislation; Supporting urgent and clearly-defined research strategies, such as model Move Over and Driver Removal laws, the effects of emergency lighting, and the impact
54 of TIM performance measures; Implementing the National TIM Responder Training course developed through the Transportation Research Boardâs Second Strategic Highway Research Program (SHRP 2); Improving the efficiency of the highway system through possible cost recovery strategies, better investment of cost-efficient resources, and improved communication among responders about roles and responsibilities; and Developing an action-based executive group equipped to provide leadership, support, and guidance in advancing priority actions. Analysis, Modeling, and Simulation for Traffic Incident Management Applications Citation. Analysis, Modeling, and Simulation for Traffic Incident Management Applications, FHWA, 2012. Available: http://ops.fhwa.dot.gov/publications/fhwahop12045/index.htm Synopsis. Traffic incidents are a major source of congestion. Implementing TIM strategies has proven to be a highly cost effective way of reducing non-recurrent congestion. This publication provides the current state of practice of various analytical methodologies and related TIM applications. It, also, identifies some research activities to improve analysis of incident impacts and TIM strategies. This document provides a synthesis of analysis, modeling, and simulation methods for incident impacts. The focus is on incidents effects on congestion and reliability as well as secondary incidents, for the purpose of estimating TIM benefits and evaluating programs and proposed strategies. Traffic Incident Management Cost Management and Cost Recovery Primer Citation. Traffic Incident Management Cost Management and Cost Recovery Primer, FHWA, 2012. Available: http://ops.fhwa.dot.gov/publications/fhwahop12044/index.htm Synopsis. This publication provides mid-level managers at transportation and other stakeholder agencies with the resources they need to explain the benefits of TIM and TIM cost management and cost recovery to executive leadership. It also provides the same mid-level managers with information that will help them implement TIM cost management and cost recovery techniques. This document focuses on "recoverable costs" related to TIM, as there are costs associated with TIM that cannot accurately be measured or replaced; however, costs related to responder and motorist injury, disability, fatality, and the related medical and societal costs are not addressed here as those issues are addressed in a variety of ways in the existing literature. Best Practices in Traffic Incident Management Citation. Best Practices in Traffic Incident Management, FHWA, 2010. Available: http://ops.fhwa.dot.gov/publications/fhwahop10050/index.htm Synopsis. This report describes task-specific and cross-cutting issues or challenges commonly encountered by TIM responders in the performance of their duties, and novel and/or effective strategies for overcoming these issues and challenges (i.e., best practices).
55 Field Operations Guide for Safety/Service Patrols Citation. Field Operations Guide for Safety/Service Patrols, FHWA, 2009. Available: http://ops.fhwa.dot.gov/publications/fhwahop10014/index.htm Synopsis. This guide was produced by the FHWA and was developed for use by Safety/Service Patrol operators and supervisors. It is expected that Safety/Service Patrol personnel will carry the guide in their vehicle to use as a quick reference while performing patrol tasks. They should refer to this guide on a regular basis as a refresher on steps and tasks associated with managing incidents - particularly for those situations not encountered every day. This guide is not designed to stand alone, but in conjunction with training and exercises that will indoctrinate the Safety/Service patrol operators into these good practices as well as agency formal Standard Operating Guidelines or Procedures. Traffic Incident Management Handbook Citation. Traffic Incident Management Handbook, FHWA, 2010. Available: http://ops.fhwa.dot.gov/eto_tim_pse/publications/timhandbook/index.htm Synopsis. The Traffic Incident Management Handbook (TIM) (the Handbook or TIM Handbook) includes the latest advances in TIM programs and practices across the country, and offers practitioners insights into the latest innovations in TIM tools and technologies. Emergency Vehicle Visibility and Conspicuity Report Citation. Emergency Vehicle Visibility and Conspicuity Report, US Department of Justice, 2009. Available: https://www.usfa.fema.gov/downloads/pdf/publications/fa_323.pdf Synopsis. The study report highlights the results of a U.S. Department of Justice - National Institute of Justice (NIJ) supported project intended to enhance emergency vehicle and roadway operations safety for firefighters, law enforcement officers, and other emergency responders. This report discusses best practices in emergency vehicle visibility and conspicuity, including cutting edge international efforts. It covers retroreflective striping and chevrons, high-visibility paint, built-in passive light, and other reflectors for law enforcement patrol vehicles, fire apparatus, ambulances and other EMS vehicles, and motorcycles. National Preparedness and National Planning Frameworks The federal government requires state DOTs to incorporate principles and concepts of national initiatives that provide common approaches to incident management and response in emergency response plans and operations. National initiatives include the NRF with its designated emergency support functions (ESFs) and the NIMS with its protocols for multiagency interaction and communication. State and local NIMS compliance is a prerequisite for federal preparedness funds. The National Disaster Recovery Framework includes designated recovery support functions (RSFs).
56 Presidential Policy Directive 8: National Preparedness (2011) http://www.dhs.gov/xlibrary/assets/presidential-policy-directive-8-national-preparedness.pdf National Preparedness Goal, Second Edition â Information Sheet Citation. âNational Preparedness Goal, Second Edition â Information Sheet,â FEMA, Washington, DC, 2015, [Online]. Available: http://www.fema.gov/media-library- data/1443624338930- 32e9ed3ac6cf8e95d7d463ed9b9685df/NationalPreparednessGoal_InformationSheet_2015.pdf Synopsis. The 2011 National Preparedness Goal was updated in 2015. The key changes are described in the National Preparedness Goal, Second Edition â Whatâs New Fact Sheet. The National Preparedness Goal itself has not changed: âA secure and resilient nation with the capabilities required across the whole community to prevent, protect against, mitigate, respond to, and recover from the threats and hazards that pose the greatest risk.â The following changes were made to the National Preparedness Goal document: ⢠Introduction: Language added to stress the importance of community preparedness and resilience. ⢠Risk and the Core Capabilities: Enhanced items on cybersecurity and climate change. ⢠Preliminary Targets: Updated preliminary targets. ⢠New Core Capability: A new core capability, Fire Management and Suppression, was added. ⢠Core Capability Titles: Revised the following core capability titles: o Threats and Hazard Identification (Mitigation) â revised to Threats and Hazards Identification; o Public and Private Services and Resources (Response) â revised to Logistics and Supply Chain Management; o On-scene Security and Protection (Response) â revised to On-scene Security, Protection, and Law Enforcement; and o Public Health and Medical Services (Response) â revised to Public Health, Healthcare, and EMS. ⢠Core Capability Definitions: Several of the core capability definitions were revised. Overview of the National Planning Frameworks (2013) http://www.fema.gov/media-library-data/20130726-1914-25045- 2057/final_overview_of_national_planning_frameworks_20130501.pdf National Planning Frameworks: ⢠National Prevention Framework ⢠National Protection Framework ⢠National Mitigation Framework ⢠National Response Framework ⢠National Disaster Recovery Framework
57 National Prevention Framework, Second Edition â Information Sheet Citation. âNational Prevention Framework, Second Edition â Information Sheet,â FEMA, Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library- data/1466011024787- 91b8e49bf7344dd6dadca441c26272ad/InformationSheet_Prevention_Framework.pdf Synopsis. The National Prevention Framework focuses on terrorism and addresses the capabilities necessary to avoid, prevent, or stop imminent threats or attacks. Some core capabilities overlap with the Protection mission area. The updates include edits to the Nation Preparedness Goal, and lessons learned. Other edits include: âUpdates to Coordinating Structure language on Joint Operations Centers and the Nationwide Suspicious Activity Reporting Initiative. Clarification on the relationship and differences between the Prevention and Protection mission areas. Updated language on the National Terrorism Advisory System (NTAS) as part of the Public Information and Warning core capability. Additional language on science and technology investments within the prevention mission area.â National Protection Framework, Second Edition â Information Sheet Citation. âNational Protection Framework, Second Edition â Information Sheet,â FEMA, Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library- data/1466013587164- 86696df20638bbf24e25d70070eda114/InformationSheet_Protection_Framework.pdf Synopsis. The National Protection Framework focuses on âactions to deter threats, reduce vulnerabilities, and minimize the consequences associated with an incident.â The new Framework incorporates the edits to the National Preparedness Goal and new lessons learned. In addition, the following changes have been made: âUpdated Cybersecurity Core Capability Critical Tasks to align with the Mitigation, Response, and Recovery Mission Areas. Additional language on science and technology investments to protect against emerging vulnerabilities are included within the protection mission area. Additional language on interagency coordination within the protection mission area to support the decision making processes outlined within the framework.â National Mitigation Framework, Second Edition â Information Sheet Citation. âNational Mitigation Framework, Second Edition â Information Sheet,â Emergency Management Agency (FEMA), Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library-data/1466014552462- 1b78d1a577324a66c4eb84b936c68f16/InformationSheet_Mitigation_Framework.pdf
58 Synopsis. The National Mitigation Framework covers the capabilities necessary to reduce the loss of life and property by lessening the effects of disasters, and focuses on risk (understanding and reducing it), resilience (helping communities recover quickly and effectively after disasters), and a culture of preparedness. The new Framework incorporates the edits to the National Preparedness Goal and new lessons learned including a revised core capability title, Threats and Hazards Identification. In addition, the following changes have been made: âAdditional language on science and technology efforts to reduce risk and analyze vulnerabilities within the mitigation mission area. Updates on the Mitigation Framework Leadership Group (MitFLG), which is now operational. Updates to the Community Resilience core capability definition to promote preparedness activities among individuals, households and families.â National Response Framework, Third Edition â Information Sheet Citation. âNational Response Framework, Third Edition â Information Sheet,â Emergency Management Agency (FEMA), Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library-data/1466014891281- 6e7f60ceaf0be5a937ab2ed0eae0672d/InformationSheet_Response_Framework.pdf Synopsis. The NRF is aligned with NIMS and provides capabilities to save lives, protect property, and meet basic human needs. Response activities occur before, during, and after an incident and can overlap with the start of Recovery activities. The following changes were made to the framework: ⢠The addition of a new core capability, Fire Management and Suppression. ⢠Three revised core capability titles o Logistics and Supply Chain Management; o On-scene Security, Protection, and Law Enforcement; and o Public Health, Healthcare, and EMS. ⢠Three revised core capability definitions o Environmental Response/ Health and Safety; o Fatality Management Services; and o Logistics and Supply Chain Management. National Disaster Recovery Framework, Second Edition â Information Sheet Citation. âNational Disaster Recovery Framework, Second Edition â Information Sheet,â Emergency Management Agency (FEMA), Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library-data/1466017528262- 73651ed433ccfe080bed88014ac397cf/InformationSheet_Recovery_Framework.pdf Synopsis. The National Disaster Recovery Framework describes âhow the whole community works together to restore, redevelop, and revitalize the health, social, economic, natural, and environmental fabric of the community.â
59 The new Framework incorporates the edits to the National Preparedness Goal and new lessons learned. Additional changes made to the framework include âIncreased focus on Recoveryâs relationship with the other four mission areas. Updated RSFs to reflect changes in Primary Agencies and Supporting Organizations. Additional language on science and technology capabilities and investments for the rebuilding and recovery efforts.â Resilience Resilience is âthe ability to prepare and plan for, absorb, recover from and more successfully adapt to adverse eventsâ (Disaster Resilience: A National Imperative, National Research Council 2012). The National Infrastructure Advisory Council (NIAC), a presidential advisory council, conducted a study on resilience that was published under the title Critical Infrastructure Resilience, Final Report and Recommendations (2009). NIAC defines infrastructure resilience as the âability to reduce the magnitude and/or duration of disruptive eventsâ. In the context of transportation systems, increasing the resilience of transportation networks could include adaptations or elements that can be incorporated into the planning and design of specific asset types. For example, TRB Report 750: Strategic Issues Facing Transportation, Volume 2: Climate Change, Extreme Weather Events, And The Highway System: Practitionerâs Guide And Research Report provided specific guidance on potential adaptations for bridges, culverts, storm water infrastructure, slopes/walls, and pavement in light of extreme weather events. The most recent transportation reauthorization legislation, titled âFixing Americaâs Surface Transportation Actâ or the âFAST Actâ, became public law on December 4, 2015 and includes, in SEC. 1201. Metropolitan Transportation Planning, an addition to Title 23 US Code Section 23 requiring MPOs to consider investments that âimprove the resiliency and reliability of the transportation system and reduce or mitigate stormwater impacts of surface transportation.â Disaster Resilience: A National Imperative Citation. Disaster Resilience: A National Imperative, The National Academies, 2012. Available: http://www.nap.edu/catalog/13457/disaster-resilience-a-national-imperative Synopsis. Resilience is defined in this report as âthe ability to prepare and plan for, absorb, recover from and more successfully adapt to adverse events.â It provides a discussion of how to increase the nationâs resilience to disasters through a vision of the characteristics of a resilient nation in the year 2030. Systems Resilience and Climate Change Citation. Systems Resilience and Climate Change, Transportation Research Record: Journal of the Transportation Research Board, Volume 2532, 2015. Available: http://trrjournalonline.trb.org/toc/trr/2532
60 Synopsis.This edition of TRBâs Transportation Research Record includes 18 papers that examine resilience and climate change issues related to transportation: ⢠Roadmaps for Adaptation Measures of Transportation to Climate Change ⢠Resilience Versus Risk: Assessing Cost of Climate Change Adaptation to Californiaâs Transportation System and the City of Sacramento, California ⢠Barriers to Implementation of Climate Adaptation Frameworks by State DOTs ⢠Resilience of Coastal Transportation Networks Faced with Extreme Climatic Events ⢠Analysis of Transportation Network Vulnerability Under Flooding Disasters ⢠Vulnerability Evaluation of Logistics Transportation Networks Under Seismic Disasters ⢠Integrating Stochastic Failure of Road Network and Road Recovery Strategy into Planning of Goods Distribution After a Large-Scale Earthquake ⢠Multimodal Transit Connectivity for Flexibility in Extreme Events ⢠Risk and Resilience Analysis for Emergency Projects ⢠Unmanned Aircraft Systems Used for Disaster Management ⢠Multimodal Evacuation Simulation and Scenario Analysis in Dense Urban Area: Philadelphia, Pennsylvania, Case Study ⢠Spatiotemporal Population Distribution Method for Emergency Evacuation: Case Study of New Orleans, Louisiana ⢠Joint Evacuation and Emergency Traffic Management Model with Consideration of Emergency Response Needs ⢠Supporting Mobility-Impaired Populations in Emergency Evacuations ⢠Agent-Based Evacuation Model Considering Field Effects and Government Advice ⢠Selecting Four-Leg Intersections for Crossing Elimination in Evacuations ⢠Using Dynamic Flashing Yellow for Traffic Signal Control Under Emergency Evacuation ⢠Hurricane Evacuation Route Choice of Major Bridges in Miami Beach, Florida Resilience: Key Products and Projects Citation. Resilience: Key Products and Projects, TRB, updated monthly. Available: http://www.trb.org/SecurityEmergencies/Blurbs/166648.aspx. Synopsis. Updated monthly, this presentation is a slideshow summary of the Transportation Research transportation security and resilience activities. These cross the main areas of TRB inquiry (freight, transit, highways and airports). Fundamental Capabilities of Effective All-Hazards Infrastructure Protection, Resilience and Emergency Management for State DOTs Citation: Fundamental Capabilities of Effective All-Hazards Infrastructure Protection, Resilience and Emergency Management for State DOTs, AASHTO, 2015. Available: http://scotsem.transportation.org/Documents/SCOTSEM/Fundamental%20Capabilities%20of%2 0Effective.pdf Synopsis. A Guide prepared to assist state DOTs understand the fundamentals of preventing incidents within their control, protect transportation users, supporting other responders, recover from incidents and evaluate responses. It also introduces concepts supporting resilience programs.
61 This is an update to the 2007 publication Fundamentals of Effective All-Hazards Security Management for State DOTs. Integrating Hazard Mitigation and Comprehensive Planning Workshop Citation. Integrating Hazard Mitigation and Comprehensive Planning Workshop, Philadelphia, PA, April 25, 2016. Available: http://www.dvrpc.org/Resiliency/HMP/pdf/2016-04- 25_Workshop_Summary.pdf Synopsis. The workshop emphasized the important relationship between land use planning and hazard mitigation, noting that how we design, build, and regulate our communities impacts their ability to withstand hazards. Increasing National Resilience to Hazards and Disasters Citation. Increasing National Resilience to Hazards and Disasters, Committee on Science, Engineering and Public Policy, the National Academies of Sciences, Engineering and Medicine. Available: http://sites.nationalacademies.org/PGA/COSEPUP/nationalresilience/index.htm Synopsis. The ad hoc committee conducted a study and issued a consensus report that integrates information from the natural, physical, technical, economic and social sciences to identify ways in which to increase national resilience to hazards and disasters in the United States. The ad hoc committee report: ⢠Defines ânational resilienceâ and frames the primary issues related to increasing national resilience to hazards and disasters in the United States. ⢠Provides goals, baseline conditions, or performance metrics for resilience at the U.S. national level. ⢠Describes the state of knowledge about resilience to hazards and disasters in the United States. ⢠Outlines additional information or data and gaps and obstacles to action that need to be addressed in order to increase resilience to hazards and disasters in the United States. ⢠Presents conclusions and recommendations about what approaches are needed to elevate national resilience to hazards and disasters in the United States. Crisis Response and Disaster Resilience 2030: Forging Strategic Action in an Age of Uncertainty, Progress Report Highlighting the 2010-2011 Insights of the Strategic Foresight Initiative, FEMA, January 2012 Citation. Crisis Response and Disaster Resilience 2030: Forging Strategic Action in an Age of Uncertainty, Progress Report Highlighting the 2010-2011 Insights of the Strategic Foresight Initiative, FEMA, January 2012. Available: http://www.fema.gov/media-library-data/20130726- 1816-25045-5167/sfi_report_13.jan.2012_final.docx.pdf Synopsis. The FEMA established the Strategic Foresight Initiative (SFI) that has brought together a wide cross section of the emergency management community to explore key future issues, trends and other factors, and to work through their implications. This report presents the findings from
62 foresight efforts thus far, including: uncertainties that define and drive the future environment; strategic needs and gaps our community will have to address; a look into the emergency management community of 2030; and finally, suggested next steps for the community to prepare for the future. The strategic needs in particular â grouped into Essential Capabilities, Innovative Models and Tools, and Dynamic Partnerships â are intended as a catalyst for leaders throughout the emergency management community to prepare themselves and the nation for the challenges and opportunities the future holds. Building Resilient States: A Framework for Agencies Citation. Building Resilient States: A Framework for Agencies, Smart Growth America. Available: http://www.smartgrowthamerica.org/resilience/ Synopsis. Smart Growth Americaâs State Resilience Program offers resources, tools, and ideas for state leaders and agencies to build more resilient places and reduce the risk of natural hazards to human life and investments. Drawing on the work of pioneering state leaders, federal agencies, and national experts, this program represents the cutting edge of land use and engagement strategies for hazard resilience. Materials are based on the experience of peer agencies from across the country, the latest research on programs and activities that states control, and proven approaches for building municipal partnerships. Community and Regional Resilience: Perspectives from Hazards, Disasters, And Emergency Management Citation. Susan L. Cutter, Lindsey Barnes, Melissa Berry, Christopher Burton, Elijah Evans, Eric Tate, and Jennifer Webb, Hazards and Vulnerability Research Institute, University of South Carolina. Community and Regional Resilience: Perspectives from Hazards, Disasters, And Emergency Management, 2008. Available: http://www.resilientus.org/wp-content/uploads/2013/03/FINAL_CUTTER_9-25- 08_1223482309.pdf Synopsis. Hazards and disaster research provides a fertile field and rich tradition in both the conceptual understanding of hazards vulnerability and community resilience in the face of disasters and the empirical place-based evidence to support geographic and temporal variability in community vulnerability and resilience. Drawing from the social sciences, natural sciences, and engineering, hazards and disasters scholars and practitioners have enabled a richer understanding of the impacts of hazards and disasters on places and the requisite monitoring required for the effective implementation of vulnerability reduction and resilience enhancing public policies. The NOAA salons also emphasized that geographic scale and unit of analysis are critical components in developing resilience metrics, especially given the underlying questions of resilience to what and for whom. The development and actual deployment of coastal resilience indicators is still in the nascent stage, but there is considerable local, state, regional, and national interest in such measures. The desire is to create the equivalent of âan index of leading resilience indicatorsâ for the nationâ indicators that combine the best science and practice that are available. While we are not there yet, the
63 perspectives from the hazards, disasters, and emergency management communities show considerable promise and illuminate the path forward. Resource Guide on Resilience Citation. Resource Guide on Resilience, International Risk Governance Council (IRGC). Available: https://www.irgc.org/irgc-resource-guide-on-resilience/ Synopsis. IRGC developed a web-based resource guide on resilience for researchers and practitioners. The resource guide available on this page is a collection of authored pieces that review existing concepts, approaches and illustrations or case studies for comparing, contrasting and integrating risk and resilience, and for developing resilience. Most papers focus also on the idea of measuring resilience. Although this idea may not sound right to some, there are ongoing efforts for evaluating resilience, developing resilience indicators, and measuring the effectiveness of actions taken to build resilience. These efforts are worth considering because indicators and metrics for resilience are needed to trigger interest and investment from decision-makers. This guide is designed to help scientists and practitioners working on risk governance and resilience evaluation. It stresses the importance of including resilience building in the process of governing risk, including in research, policy, strategies, and practices. It emphasizes the need to develop metrics and quantitative approaches for resilience assessment and instruments for resilience management. A Multidimensional Review of Resilience: Resources, Processes, and Outcomes Citation. Marcus L. Snell, Daniel A. Eisenberg, Thomas P. Seager, Susan Spierre Clark, Young Joon Oh, John E. Thomas, and Lauren R. McBurnett. A Multidimensional Review of Resilience: Resources, Processes, and Outcomes. Available at https://www.irgc.org/irgc-resource-guide-on- resilience/ Synopsis. This paper reviews a sampling of resilience literature from a variety of disciplines and identifies at least three dimensions of resilience: resources, processes, and outcome priorities. Critical Infrastructure Resilience Citation. Eric D. Vugrin, Sandia National Laboratories. Critical Infrastructure Resilience. Available: https://www.irgc.org/wp-content/uploads/2016/04/Vugrin-Critical-Infrastructure- Resilience-1.pdf Synopsis. The Infrastructure Resilience Analysis Methodology (IRAM) provides a comprehensive framework for analyzing and managing critical infrastructure resilience (Biringer, Vugrin, & Warren, 2013). The IRAM is a hybrid methodology that includes performance-based metrics to quantify resilience and resilience attributes to inform analysis and improvement. The IRAM quantifies resilience with two primary sets of metrics: systemic impact (SI) and total recovery effort (TRE). Resilience: Approaches to Risk Analysis and Governance: An introduction to the IRGC Resource Guide on Resilience
64 Citation. Igor Linkov, Benjamin D. Trump, and Cate Fox-Lent. Resilience: Approaches to Risk Analysis and Governance: An introduction to the IRGC Resource Guide on Resilience. Available: https://www.irgc.org/wp-content/uploads/2016/04/Linkov-Trump-Fox-Lent-Resilience- Approaches-to-Risk-Analysis-and-Governance-1.pdf Synopsis. This paper includes (I) a comparison of risk and resilience management strategies, (II) a description of common features within resilience analysis and thinking, and (III) a discussion of the benefits that resilience management brings to the field of risk management. This paper serves as a general introduction to the concept and application of resilience, specifically as it relates to traditional risk management, and in particular about suggestions for metrics or indicators that can be developed to assess resilience in a system, and the performance of resilience strategies. Measuring the Resilience of Infrastructure Systems Citation. Henry H. Willis, RAND Corporation. Measuring the Resilience of Infrastructure Systems. Available: https://www.irgc.org/wp-content/uploads/2016/04/Willis-Measuring-the- Resilience-of-Infrastructure-Systems.pdf Synopsis. This paper defines resilience â meaning both what it is and what aspects of the system must be measured âand understanding why resilience is being measured. Planning for a More Resilient Future: A Guide to Regional Approaches Citation. Planning for a More Resilient Future: A Guide to Regional Approaches, NADO. Available: https://www.nado.org/wp- content/uploads/2015/10/Regional_Resilience_report_FINAL.pdf Synopsis. This report summarizes the rapidly-growing body of research on resilience, describing the main ideas that are driving policy and practice across the country, and examining current thinking on regional and economic resilience. It is accompanied by an online guide to resources on the practice of resilience, available at www.nado.org. The guide includes examples of ways to approach planning for resilience, a primer on the expansive federal policy framework which determines the priorities for funding resilience initiatives and describes the current state of philanthropic engagement in resilience efforts. Enhancing Community Resilience: Practical Resources in Addressing the Collaboration Gaps Citation. Stephen Diarmuid Walsh MIPI AIED, Martina Madden, Stephen M. Purcell, Future Analytics Consulting (FAC) Limited. Enhancing Community Resilience: Practical Resources in Addressing the Collaboration Gaps. Available: https://www.irgc.org/wp- content/uploads/2016/04/Walsh-Madden-Purcell-Enhancing-Community-Resilience.pdf Synopsis. This paper examines Community Resilience, with particular reference to the âcollaboration gapâ and the manner in which it impedes the unification of communities and responding professionals in terms of reacting to the effects of an adverse event (disaster relief). The purpose of this paper is to highlight the impact of the âcollaboration gapâ and to then present resources which may enable communities and responding professionals to react together in order
65 to mitigate and recover from the effects of an adverse event, thereby enhancing the resilience of communities. Resilience Planning in Transportation A Resiliency Framework for Planning in State Transportation Agencies Citation. Amoaning-Yankson, Stephanie. A resiliency framework for planning in state transportation agencies. Available: https://smartech.gatech.edu/bitstream/handle/1853/49123/AMOANING-YANKSON-THESIS- 2013.pdf?sequence=1&isAllowed=y Synopsis. This thesis presents a framework for resiliency planning in state DOTs and other transportation agencies. The development of this framework is motivated by the need for more resilient transportation systems, due of the increasing frequency and the effect both natural and man-made catastrophic disasters have on transportation systems. The resiliency framework is based on the urban transportation planning framework and is thus applied in the broader context of general transportation planning. The resiliency framework is then applied in a preliminary review to three statewide transportation plans to show the resiliency deficiencies of those plans and how the framework may be applied to increase resiliency. These plans are selected from three different states with diversity of locations and without any preconceived notions about their incorporation of resiliency in their planning process. This preliminary review reveals a reactive nature towards investments that increase an agencyâs resilience. This may be attributed to the problem of limited funding for transportation investments, as well as, limited knowledge by the transportation agencies about the return on such resiliency investments, mostly due to the uncertainty associated with the occurrence of catastrophic disasters, especially the predictability of weather-related events. However, post-disaster transportation system overhauls provide enough evidence for the need for more systemic ways of addressing resiliency in planning processes. Improving the Resiliency of Transit Systems Threatened by Natural Disasters Citation. Improving the Resiliency of Transit Systems Threatened by Natural Disasters Transit Cooperative Research Program, Project A-41, in progress (completion expected February 2017). Available: http://apps.trb.org/cmsfeed/TRBNetProjectDisplay.asp?ProjectID=3744 Synopsis. The objectives of this research are to develop (1) a handbook with an associated suite of digital presentation materials to address planning principles, guidelines (including metrics), strategies, tools, and techniques to enable public transit systems to become more resilient to natural disasters and climatic events; and (2) a draft recommended practice for public transit resilience to natural disasters and climatic events suitable as input to the APTA Standards Program. The handbook and its associated suite of digital presentation materials should be appropriately designed for use by public transit agency executive staff to plan, budget, and institutionalize effective practices to improve resilience, addressing (a) capital project planning and asset management (including financial planning and risk assessment for natural disasters and climatic events), (b) operations and maintenance, and (c) administration. They should provide sufficient detail to allow users to adapt them to their individual entities. Federal and Transit Agencies Taking Steps to Build Transit Systemsâ Resilience but Face Challenges
66 Citation. Federal and Transit Agencies Taking Steps to Build Transit Systemsâ Resilience but Face Challenges, GAO December 2014. Available: http://www.gao.gov/assets/670/667391.pdf Synopsis. This report examines (1) how DHS and DOT help transit agencies make their systems resilient; (2) actions selected transit agencies take to make their systems resilient; and (3) challenges transit agencies face with making their systems resilient. GAO examined documentation and interviewed officials from DHS and DOT, and officials from nine transit and five emergency management agencies. GAO selected a non-generalizable sample of agencies in five locations, chosen for transit ridership volume and variation in geography, types of risks, and transit modes. FloodCast: A Framework for Enhanced Flood Event Decision Making for Transportation Resilience Citation. FloodCast: A Framework for Enhanced Flood Event Decision Making for Transportation Resilience, NCHRP Project 20-59(53) Available: http://apps.trb.org/cmsfeed/TRBNetProjectDisplay.asp?ProjectID=3725 Synopsis. The objectives of this research are to develop a strategic framework and a prototype tool for enhanced flood event decision making. The framework and tool should help state DOTs plan, manage risks, mitigate hazards, and respond to flood and flash flood events. The framework and tool should address not only immediate flood impacts, but also cascading, escalating impacts. Given the large amount and diversity of applicable data and tools, the framework design should be flexible and scalable to accommodate the available data sets and allow users to easily share both data and products with other users, thereby fostering collaboration across government organizations and the private sector. Guidelines to Incorporate the Costs and Benefits of Adaptation Measures in Preparation for Extreme Weather Events and Climate Change, Citation. Guidebook: Incorporating the Costs and Benefits of Adaptation Measures in Preparation for Extreme Weather Events and Climate Change, NCHRP Project 20-101, report in progress. Available: http://apps.trb.org/cmsfeed/TRBNetProjectDisplay.asp?ProjectID=3881 Synopsis. The objectives of this research are to develop (a) a stand-alone document providing guidance for practitioners on methods and tools, including illustrative case studies where applicable, to: (i) efficiently mine, manage, and document existing data sources; (ii) acquire and use data from new and innovative sources; and (iii) apply, and communicate the results from, a flexible and scalable framework for analyzing the costs and benefits of adaptation measures in preparation for extreme weather events and climate change conducted by various transportation organizations; (b) a final report that documents the entire research effort and includes the research teamâs recommendation of research needs and priorities for additional related research; and (c) an updated PowerPoint presentation describing the research and results suitable (upon revision) for posting on the TRB website. The Innovative DOT: A Handbook of Policy and Practice
67 Citation. âThe Innovative DOT: A Handbook of Policy and Practice,â State Smart Transportation Initiative and Smart Growth America, 2014. Available: http://www.ssti.us/wp/wp-content/uploads/2014/01/The-Innovative-DOT-1.8.15.pdf Synopsis. This Handbook, developed by the State Smart Transportation Initiative and Smart Growth America, contains a resiliency section that provides guidance for state DOTs on how to incorporate climate change adaptation into long-range transportation planning. It provides state DOTs with a comprehensive list of reforms that will address potential climate-related vulnerabilities and reduce the likelihood, magnitude, duration and cost of disruption associated with extreme weather. The resiliency section, entitled âIncorporate Climate Change Resilience into Long-Range Planning,â is included into the larger handbook, which provides general guidance to state DOTs on ways to improve their transportation systems. The resiliency section summarizes the potential effects of climate change on a stateâs transportation system, describes how climate change adaptation planning can help a state protect its transportation assets, and outlines steps state DOTs can take to assess vulnerability and identify and implement changes to improve the systemâs resilience. The section reviews the effects of climate change and the impact extreme weather can have on a stateâs transportation assets. For example, the increased intensity, variability, duration, and frequency of weather events could lead to shortened infrastructure lifespans, increased risk of catastrophic failures, and increased costs. It provides guidance for state DOTs on ways to implement resilience in transportation systems through operational and infrastructure changes. There are three key adaptation planning steps that state DOTs can take to assess system vulnerability and risks and identify and implement changes to improve the systemâs resilience. These steps include: (1) documenting environmental changes and selecting the most appropriate climate models to predict future conditions; (2) identifying climate change-related stressors and their impacts on the transportation system, and inventorying transportation assets, focusing on characteristics that could help or hinder adaptation; and (3) developing and assessing alternative strategies for adapting infrastructure and operations. The handbook also highlights FHWA-sponsored pilot projects for incorporating resilience into transportation planning. These pilots were intended to encourage state and regional agencies in the development of climate adaptation plans using FHWAâs Climate Change and Extreme Weather Vulnerability Assessment Framework. Three of the states that conducted pilot projects (Washington, California, and Massachusetts) are featured in the handbook as case studies. Washington completed the vulnerability and risk assessment step by identifying at-risk transportation assets and planning to further develop a set of specific adaptation strategies for the assets. California has begun developing and selecting strategies for transportation infrastructure, and has developed guidance to assist MPOs and regional transportation planning agencies with assessing their vulnerability and incorporating climate adaptation into the development of their regional plans. Massachusetts committed funding to address climate impacts according to recommendations made in the stateâs 2011 Climate Change Adaptation Report, which included recommendations for improving transportation facilitiesâ preparedness for extreme weather events. The handbook was commissioned by the U.S. DOTâs FHWA to assist state DOTs with prioritizing reforms by offering strategies that can be undertaken to improve a stateâs transportation system.
68 NY Metropolitan Transportation Council, Resilience Planning, Plan 2040 Citation. NY Metropolitan Transportation Council Transportation Plan 2040. Available: https://www.nymtc.org/Regional-Planning-Activities/Resiliency-Planning Synopsis. Improving the resiliency of the transportation system was included in Plan 2040's regional goals. The Plan include various strategies for climate adaptation throughout the entire transportation system and stresses the importance of collaboration between all member agencies in planning for future severe weather events. Greater resiliency will mitigate the adverse impacts of disruptions on the movement of people and goods due to weather, climate, or other acts of nature. The following outcomes are associated with the regional resiliency goal: ⢠Adaptation measures for critical components of the transportation system to accommodate variable and unexpected conditions without catastrophic failure; ⢠Greater resiliency of the regional supply chain by identifying options for goods movement during and after events; ⢠Cooperative partnerships with federal, state, local agencies, and other stakeholders to adapt the transportation system and improve recovery from disruptions. Transportation Sector Resilience, Final Report and Recommendations Citation. Transportation Sector Resilience, Final Report and Recommendations, National Infrastructure Advisory Council (NIAC), July 10, 2015. Available: https://www.dhs.gov/sites/default/files/publications/niac-transportation-resilience-final-report- 07-10-15-508.pdf Synopsis. The President directed the NIAC to examine the resilience of the nationâs transportation sector to determine potential gaps and identify opportunities for the federal government to improve the sectorâs resilience and security. Throughout this study, infrastructure resilience is defined as the ability to reduce the magnitude or duration of disruptive events that is accomplished by anticipating, absorbing, adapting to, or rapidly recovering from the disruption. The Councilâs key findings are presented within three major topic areas: Finding 1: Understanding Systemic Risks ⢠Transportation risks are not well understood across modes, regions, and critical interdependent sectors, creating uncertainty about national level consequences that could arise from a major system disruption. ⢠Owners and operators have limited visibility of risks across adjoining systems, jurisdictions, modes and critical dependent infrastructures. In particular, emerging risks related to cyber disruptions. Finding 2: Incorporating Resilience into Operational Practice ⢠Although national resilience policies are generally well established, they have not yet been integrated into comprehensive national transportation plans and strategies that coordinate
69 decision making and risk management across modes at local, state, regional, and national levels. ⢠Gaps in leadership, coordination, and workforce capabilities have made it difficult for organizations to effectively incorporate resilience as an embedded function of good operating practice. ⢠There is no structured senior-level engagement between public and private sectors partners, and among transport modes and interdependent sectors, to address national level transportation risks. Finding 3: Investing in Resilient Infrastructure ⢠Chronic underinvestment in transportation infrastructure and the inability to monetize resilience for investment decisions have prevented resilience from being integrated into the built infrastructure. ⢠There is no national consensus on the need for investment in resilient transportation infrastructure due in part to a limited understanding among the public, political leaders, and industry leaders about the role and value of resilience. ⢠Uncertainty over the likelihood, costs, and consequences of emerging risks makes it difficult for owners and operators to invest in long-term resilience. There are three overarching recommendations: the need to 1) baseline current risks and establish a federal vision for transportation resilience; 2) develop the analytic tools, models, and exercises to better understand and plan for emerging risks and interdependencies; and 3) use the results of these efforts to operationalize resilience by increasing funding and implementing effective federal practices, procedures, and procurement processes. Resiliency Metrics for Transportation Planning Citation. Resiliency Metrics for Transportation Planning, Caltrans Division of Research, Innovation and System Information, 2015, Available: http://www.dot.ca.gov/newtech/researchreports/preliminary_investigations/docs/resiliency_metri cs_preliminary_investigation.pdf Synopsis. One of Caltransâ strategic objectives is to attain a more resilient and integrated transportation system, and this Preliminary Investigation sought information to support that goal. Caltrans is particularly interested in information to support development of a resiliency score or other metric that the department can use to prioritize projects based on expected resiliency and adaptability to change. Caltrans has a stated initial interest in three types of resiliency: climate, system and financial. The agency is also interested in learning what types of vulnerabilities are addressed in resiliency efforts across the United States and internationally. Adapting Bridge Infrastructure to Climate Change: Institutionalizing Resilience in Intergovernmental Transportation Planning Processes in the Northeastern USA. Citation. Anna Schulz, Asim Zia, Christopher Koliba Schulz, A., Zia, A. & Koliba, Adapting bridge infrastructure to climate change: institutionalizing resilience in intergovernmental transportation planning processes in the Northeastern USA. C.
70 Mitig Adapt Strateg Glob Change (2015). doi:10.1007/s11027-015-9672-x. Available: http://link.springer.com/article/10.1007/s11027-015-9672-x Synopsis. Multi-level governance networks provide both opportunities and challenges to mainstream climate change adaptation due to their routine decision making and coordination processes. This paper explores institutionalizing resilience and adaptation to climate change in the intergovernmental transportation planning processes that address bridge infrastructure in the Northeastern United States (USA), specifically in Vermont and Maine. The research presented here relies on nine interviews with policymakers and planners, a survey of transportation project prioritization criteria, development of a longitudinal bridge funding database, and its integration with publicly available geospatial data. It presents a novel spatial analysis methodology, a modified version of which could be adopted by transportation agencies for prioritizing scarce adaptation funds. Although transportation agencies are undertaking a variety of mitigation activities to address business-as-usual needs, climate change adaptation and resilience efforts remain underprioritized. Adaptation is a global concern, but impacts vary dramatically between regions and require localized solutions. Bridges and culverts, which are especially vulnerable to climate-induced flooding impacts, have complex maintenance and design processes and are subject to convoluted adaptation planning procedures. Critical gaps in resources and knowledge are barriers to improved adaptation planning. Restructuring the transportation project prioritization procedures used by planning organizations to explicitly include adaptation may provide a novel strategy to institutionalize resilience in transportation. These procedures must be considered in the context of the intergovernmental networks that exist to support transportation infrastructure. Although these networks will likely vary across countries, the approaches introduced here to study and address transportation infrastructure adaptation may be applied to many settings. State Agency Chiefs Break Down Issues Facing DOTs in CEO Roundtable Panels Citation. State Agency Chiefs Break Down Issues Facing DOTs in CEO Roundtable Panels, AASHTO Journal, 15 January 2016. Available: https://www.tsp2.org/2016/01/18/state-agency-chiefs-break-down-issues-facing-dots-in-ceo- roundtable-panels/ Synopsis. California DOT Director Malcolm Dougherty moderated a panel discussion on resiliency and the ways in which state DOTs are planning for and responding to changes in climate and extreme weather events. His panelists were Pennsylvania DOT Director Leslie Richards, Delaware Transportation Secretary Jennifer Cohan and Colorado DOT Executive Director Shailen Bhatt. All described recent severe weather events that had damaged their transportation networks. âI think it is fair to say that every state has had its share of adverse events,â said Dougherty, whose state recently suffered severe flooding, mudslides and fires. âThat is what weâre betting on right now . . . what Iâm certain of is that weâre going to get more of this,â said Bhatt, who also talked about the severe mountain flooding that washed out many roads and rail tracks in Colorado during September 2013.
71 Richards said that in Pennsylvania, one of the nationâs most flood-prone states, officials recently commissioned the stateâs first resiliency study. She said plans need to include educational campaigns and public outreach. While most states face severe weather events, Delaware also sees challenges from rising sea levels as Cohan said her state has the nationâs lowest mean elevation with dikes and levees already protecting lands. She said resilience planning needs to focus not only on what can be protected, but also on what should be protected and at what cost. âThis is an extremely passionate issue in Delaware,â said Cohan. She noted that her department is vacating its first road this year due to rising sea levels. âWe have to start somewhere and this was the logical first step.â Port Resilience Planning in the Port of New York and New Jersey Citation. Dr. Tiffany Smythe, Principal Investigator, Center for Maritime Policy and Strategy U.S. Coast Guard Academy, New London, CT. Port Resilience Planning in the Port of New York and New Jersey. Available: http:// www.cga.edu/WorkArea/DownloadAsset.aspx?id%3D5050&usg=AFQjCNE6Ipl3dIoEf8szZxB wQzi1TWr4ng&sig2=_ysxkmx4Y1TOU8rFr8m1BQ&bvm=bv.134495766,d.eWE06320 Synopsis. The purpose of this academic study is to examine resilience planning in the Port of NY and NJ with the goal of helping port, emergency management, and planning professionals to enhance the value of their ongoing port resilience planning work. While the concept of âresilienceâ to coastal storms and other natural hazards is increasingly used in public discourse, little social science research has been done to examine the application of this concept within the context of ports and to learn from the practitioners who are doing this work. This study is focused on two questions: (1) What do practitioners envision as a resilient port and how do they prioritize among the range of nearâterm and longâterm resiliency considerations? and (2) Who is involved in coastal storm, port resilience, and climate change adaptation planning, and in what ways do individuals collaborate across planning networks, jurisdictions, agencies, and sectors to accomplish this work? Increasing Trans Resilience in the Gulf Coast Citation. Increasing Trans Resilience in the Gulf Coast, US Climate Resilience Toolkit, National Oceanic and Atmospheric Administration (NOAA), 2016. Available: https://toolkit.climate.gov/case-studies/increasing-transportation-resilience-gulf-coast Synopsis. The study identified innovative approaches for using climate data in transportation vulnerability assessments, consistent strategies for evaluating vulnerability and adaptation options, and tools and resources that can assist other transportation agencies in conducting similar assessments. Resilience Plans â State Examples Vermontâs Roadmap to Resilience http://www.iscvt.org/wp-content/uploads/2014/06/vermonts-roadmap-to-resilience-web.pdf
72 Vermont is now working to develop an integrated, long-term strategy for resilience â one that weaves together state, regional and local initiatives, and better equips the state to prepare for, respond to and bounce back from future climate impacts and the natural disasters that we know will come. The Resilient Vermont project is a stakeholder-driven process to identify practical steps to reduce our vulnerabilities and minimize the risks to our citizens, our communities, our economy and our environment. NY State Community Resilience http://cdrpc.org/wp-content/uploads/2016/04/03312016-Community-Resilience.pdf This document includes an overview of requirements and activities in resilience in NY state. Iowa State Freight Plan http://www.iowadot.gov/iowainmotion/freight.html The Iowa DOT has embarked on numerous freight planning activities to help achieve this objective, many of which will be detailed in the Iowa Freight Plan. This plan is a way to connect all of these initiatives and allow them to move forward towards a common goal of optimal freight transportation in the state. In addition, the plan will guide Iowa DOT's investment decisions to maintain and improve the freight transportation system, and ultimately strengthen the stateâs economy and raise the quality of life for its citizens. Oregon Resilience Plan: Reducing Risk and Improving Recovery for the Next Cascadia Earthquake and Tsunami, 2013 http://www.oregon.gov/OMD/OEM/osspac/docs/Oregon_Resilience_Plan_Final.pdf Oregon Resilience Plan set out to help Oregonians know what to expect from the stateâs infrastructure should that disaster strike this year, and to propose the level of infrastructure reliability that a resilient state should provide. The planâs recommendations highlight ways to close the gap that separates expected and desired performance. The Transportation Task Group (Chapter Five) assessed the seismic integrity of Oregonâs multimodal transportation system, including bridges and highways, rail, airports, water ports, and public transit systems, examined the special considerations pertaining to the Columbia and Willamette River navigation channels, and characterized the work deemed necessary to restore and maintain transportation lifelines after a Cascadia earthquake and tsunami. The groupâs scope included interdependence of transportation networks with other lifeline systems. Texas State Freight Resiliency Plan http://ftp.dot.state.tx.us/pub/txdot- info/library/reports/gov/tpp/spr/resiliency/resiliency_phase_1.pdf The Texas Department of Transportationâs (TxDOT) recognized that the highway system is a major component of a resilient freight network. As the managing organization responsible for maintaining the stateâs highways, TxDOT developed this plan to provide a comprehensive
73 framework for identifying key freight infrastructure corridors and strategies to ensure a resilient freight transportation network in the State of Texas. Resilience Plans â Transportation Specific Examples 2060 Florida Transportation Plan http://www.adaptationclearinghouse.org/resources/2060-florida-transportation-plan-a.html http://www.dot.state.fl.us/planning/ftp/ The â2060 Florida Transportation Planâ provides transportation planning guidance for the state, and includes emergency preparedness and resilience planning in its long-range objectives. The Plan, developed by the Florida Department of Transportation (FDOT), sets high-level transportation objectives for the state, and offers implementation strategies to meet those objectives. The Plan articulates two long-range objectives related to climate change resiliency: improving Floridaâs ability to use the transportation system to respond to emergency and security risks and increasing the resilience of stateâs critical infrastructure to the impacts of climate trends and events. The Plan offers several strategies to improve the stateâs ability to respond to emergency risks, calling on the FDOT to: ⢠Implement a comprehensive approach for enhancing transportation security and emergency management through developing and regularly updating statewide and regional emergency response plans to define roles and strategies related to preparedness, prevention, detection, protection, response, recovery, and mitigation; ⢠Support emergency evacuation, response, and post-disaster recovery activities through transportation planning and management decisions; and ⢠Increase the use of technology to improve transportation safety, security, and emergency management, including public sector actions to develop standards and adapt infrastructure to facilitate vehicle, communications, and related technology investments. In addition to emergency management, the Plan also recognizes the need for system owners to identify where the risk for service interruptions will be greatest from the impacts of climate change. To reduce vulnerability and increase resilience, the Plan calls for the development of more refined data and decision making tools to help decision-makers integrate climate trends and their potential impacts into decisions about the design, construction, maintenance, and operation of transportation infrastructure. All objectives and implementation strategies in the Plan are nonbinding. In 2015-2016, FDOT updated the Florida Transportation Plan; the Vision Element and the Policy Element of the FTP were released in August and December 2015, respectively, and Strategic Intermodal System Policy Plan was completed in February 2016. The new plan establishes a vision to shift focus from maintaining infrastructure to adapting infrastructure, which includes making it resilient to impacts of extreme weather events, climate trends, and sea-level rise. The FTP Policy Element includes goals and objectives designed to guide the state towards this and other aspects of the overall vision for the stateâs transportation system. To support the goal of adapting infrastructure and increasing resilience, the Policy Element recommends incorporating extreme weather risks into long-range planning, project development, design, and operations and
74 maintenance; and continuing to support research to better understand impacts of extreme weather and climate trends on transportation infrastructure. Illinoisâ State Long-Range Transportation Plan http://apps.dot.illinois.gov/Checkbox/Survey.aspx?s=c6649fca145b4c9d986e49310dad579e Includes Resilience goal â âensure infrastructure is prepared to withstand and sustain hazards and extreme eventsâ Oregon Bridge Resilience Plan Slides: https://www.crpanel.org/wp-content/uploads/2016/07/Oregon-Bridge-Resilience-Plan- NISTwebinarJuly13_2016-2.pdf Presentation: https://arameetings.webex.com/mw3100/mywebex/nbrshared.do NYSDOT Climate Change Resiliency Efforts http://nysmpos.org/wordpress/wp-content/uploads/2015/07/26_E-Lennon-NYSDOT-Resilience- Activities-for-NYSAMPO-2015.pdf Mass MBTA Winter Resiliency Plan http://www.mass.gov/governor/press-office/press-releases/fy2015/governor-announces-mbta- winter-resiliency-plan.html California Transportation Sector Plan http://resources.ca.gov/docs/climate/safeguarding/Transportation%20Sector%20Plan.pdf Safeguarding California: Reducing Climate Risk (Safeguarding California), details several recommended actions to enhance the stateâs transportation systemâs resiliency to climate impacts and improve its ability its ability to provide access to places, goods, and services. This implementation plan builds on the foundation provided by Safeguarding California by describing climate-related vulnerabilities of the transportation sector, outlining current activities, identifying next steps, and proposing monitoring and evaluation metrics.
75 D. Stakeholders â Regional Collaboration National Incident Management System (NIMS) Available: http://www.fema.gov/national-incident-management-system The NIMS is a systematic, proactive approach to guide departments and agencies at all levels of government, nongovernmental organizations, and the private sector to work together seamlessly and manage incidents involving all threats and hazardsâregardless of cause, size, location, or complexityâin order to reduce loss of life, property and harm to the environment. NIMS is the essential foundation to the National Preparedness System (NPS) and provides the template for the management of incidents and operations in support of all five National Planning Frameworks. NIMS updates since the 2010 Guide was published provided important new definitions, policy direction and guidance explaining: (1) the NIMS relationship to the National Preparedness Framework; (2) additions to cover intelligence and cyber issues; (3) support, coordination, collaboration, and command and management tactical and non-tactical operations; (4) use and interoperability of Emergency Communications; and (5) inclusion of âwhole communityâ concepts in the NIMS. The NIMS 2016 refresh retains key concepts and principles from earlier NIMS versions while incorporating new Presidential directives, legislative changes, and lessons learned from exercises, actual incidents, and planned events. The NIMS refresh: ⢠Reiterates concepts and principles of the original 2004 version and the updated 2008version; ⢠Reflects and incorporates lessons learned from exercises, real world incidents, and policy updates, such as the NPS, and NIMS-related guidance ,including the 2013 NIMS Intelligence/Investigation Function Guidance and Field Operations Guide; ⢠Reflects progress in resource typing and mutual aid and builds a foundation for the development of a national qualification system; ⢠Clarifies that NIMS is more than just the Incident Command System (ICS) and that it applies to all stakeholders with roles in incident management across all five mission areas (Prevention, Protection, Mitigation, Response, and Recovery); ⢠Explains the relationship among ICS, the Center Management System (CMS) for operations centers and coordination centers, and Multiagency Coordination Groups(MAC Groups); and ⢠Enhances information management processes to improve data collection plans, social media integration, and the use of GIS. A Guide to Regional Transportation Planning for Disasters, Emergencies and Extreme Events Citation. NCHRP Report 777: A Guide to Regional Transportation Planning for Disasters, Emergencies and Extreme Events, Transportation Research Board of the National Academies, Washington, DC, 2014. Available: http://onlinepubs.trb.org/onlinepubs/nchrp/nchrp_rpt_777.pdf
76 Synopsis. The Guide uses foundational planning principles, case studies, tips, and tools to explain implementation of transportation planning for possible multijurisdictional disasters, emergencies, and other major events. In addition to the guide, there is a contractor's final research report and a PowerPoint presentation describing the entire project. Information-Sharing Guidebook for Transportation Management Centers, Emergency Operations Centers, and Fusion Centers (2010) Citation. Information-Sharing Guidebook for Transportation Management Centers, Emergency Operations Centers, and Fusion Centers, FHWA, 2010. Available: Hhttp://Ops.Fhwa.Dot.Gov/Publications/Fhwahop09003/Tmc_Eoc_Guidebook.Pdf Synopsis. This guidebook provides an overview of the mission and functions of transportation management centers, emergency operations centers, and fusion centers. The guidebook focuses on the types of information these centers produce and manage and how the sharing of such information among the centers can be beneficial to both the day-to-day and emergency operations of all the centers. Challenges exist to the ability to share information, and the guidebook addresses these challenges and options for handling them. The guidebook also provides some lessons learned and best practices identified from a literature search and interviews/site visits with center operators. Role of Transportation Management Centers in Emergency Operations Guidebook (2012) Citation. Role of Transportation Management Centers in Emergency Operations Guidebook, FHWA, 2012. Available: http://www.ops.fhwa.dot.gov/publications/fhwahop12050/fhwahop12050.pdf Synopsis. This Guidebook explores ways to increase communication, collaboration, and cooperation between transportation management centers (TMCs) and emergency response agencies. The document addresses both technical and institutional barriers that prevent TMCs from fully supporting emergency operations and provides specific activities and practices such as joint planning and training activities for TMCs to become more effective in emergency operations. Communication with Vulnerable Populations: A Transportation and Emergency Management Toolkit Citation. TRCP Report 150: Communication With Vulnerable Populations: A Transportation And Emergency Management Toolkit, Transportation Research Board, 2011. Available: http://www.trb.org/main/blurbs/166060.aspx Synopsis. The Toolkit describes how to create a communication process to reach vulnerable populations regarding their transportation options in emergencies. The toolkit provides a guiding framework and tools for constructing a scalable, adaptable communication process built on a network of agencies from public, private, and nonprofit sectors. Together, these partners will form interconnected communication channels with the ability to carry out the function of emergency communication not necessarily possible by working alone.
77 A Guidebook for Successful Communication, Cooperation, And Coordination Strategies Between Transportation Agencies and Tribal Communities Citation. NCHRP Report 690: A Guidebook for Successful Communication, Cooperation, and Coordination Strategies Between Transportation Agencies and Tribal Communities, Transportation Research Board of the National Academies, Washington, DC, 2011. Available: http://www.trb.org/main/Blurbs/165472.aspx Synopsis. This Guidebook includes guidelines designed to help DOTs and tribal communities work together to achieve successful transportation projects on tribal lands. The report explores a wide range of issues and topics to be considered and offers a flexible approach that can be adapted to most situations. The report also includes case studies to illustrate successful practices. The report on the project that led to the development of NCHRP Report 690 was published as NCHRP Web-Only Document 171. Uses of Social Media in Public Transportation Citation. TCRP Synthesis 99: Uses of Social Media in Public Transportation, Transportation Research Board of the National Academies, Washington, DC, 2012. Available: http://www.trb.org/main/blurbs/167067.aspx Synopsis. This report explores the use of social media among transit agencies and documents successful practices in the United States and Canada. For the purposes of the report, social media are defined as a group of web-based applications that encourage users to interact with one another, such as blogs, Facebook, LinkedIn, Twitter, YouTube, Flickr, Foursquare, and MySpace. An eReader friendly PDF version of TCRP Synthesis 99 is also available. Expanding Role of Public Works in Emergency Management Citation. Bergner, Dave and Kimberly Vasconez, âExpanding Role of Public Works in Emergency Management,â Leadership and Management in Engineering, Vol. 12, No. 3, 2012, pp. 126-133. Synopsis. This paper examines the evolving mission of public works in emergency management. Maintenance and operations personnel of state DOTs and public works agencies are vital in the response and recovery phases of disasters and other emergencies, and assist with rescue, evacuation, and sheltering and provide temporary traffic control, perimeter security, animal control, transportation of supplies and equipment, onsite vehicle service, debris management, and restoration of infrastructure. The convergence of all-hazards emergency management and TIM in recent years means that public works has a different role in planning and preparing for and responding to disasters and events. The profusion of laws, mandates, and programs and the rapidly evolving body of training and knowledge can make staying abreast of these changes overwhelming.
78 E. Emergency Management Training National Incident Management System (NIMS) Training Available: http://training.fema.gov/is/nims.aspx NIMS ICS All-Hazards Position Specific Training Program Official Website http://training.fema.gov/allhazards/ The NIMS is a systematic, proactive approach to guide departments and agencies at all levels of government, nongovernmental organizations, and the private sector to work together seamlessly and manage incidents involving all threats and hazardsâregardless of cause, size, location, or complexityâin order to reduce loss of life, property and harm to the environment. NIMS is the essential foundation to the NPS and provides the template for the management of incidents and operations in support of all five National Planning Frameworks. NIMS updates since the 2010 Guide was published provided important new definitions, policy direction and guidance explaining: (1) the NIMS relationship to the National Preparedness Framework; (2) additions to cover intelligence and cyber issues; (3) support, coordination, collaboration, and command and management tactical and non-tactical operations; (4) use and interoperability of Emergency Communications; and (5) inclusion of âwhole communityâ concepts in the NIMS. The following NIMS and ICS courses are highlighted on the NIMS training page: ICS and NIMS Courses ⢠ICS-100: Introduction to the Incident Command System ⢠ICS-200: ICS for Single Resources and Initial Action Incidents ⢠ICS-300: Intermediate ICS for Expanding Incidents ⢠ICS-400: Advanced ICS for Command and General Staff ⢠IS-700: NIMS, An Introduction ⢠IS-701: NIMS Multiagency Coordination System (MACS) ⢠IS-702: NIMS Publication Information Systems ⢠IS-703: NIMS Resource Management ⢠IS-704: NIMS Communication and Information Management (unavailable) ⢠IS-706: NIMS Intrastate Mutual Aid â An Introduction ⢠IS-800: National Response Framework, An Introduction ⢠G-191: Incident Command System (ICS)/ Emergency Operations Center Interface* ⢠G-402 Incident Command System (ICS) Overview for Executives/Senior Officials* ⢠G-775: Emergency Operations Center (EOC) Management and Operations* *G191, G402, and G-775 are coordinated by local emergency management agencies.
79 All-Hazards Position Specific Courses ⢠E/L 950: All-Hazards Position Specific Incident Commander ⢠E/L 952: All-Hazards Position Specific Public Information Officer ⢠E/L 954: All-Hazards Position Specific Safety Officer ⢠E/L 956: All-Hazards Position Specific Liaison Officer ⢠E/L 958: All-Hazards Position Specific Operations Section Chief ⢠E/L 960: All-Hazards Position Specific Division/Group Supervisor ⢠E/L 962: All-Hazards Position Specific Planning Section Chief ⢠E/L 964: All-Hazards Position Specific Situation Unit Leader ⢠E/L 965: All-Hazards Position Specific Resources Unit Leader ⢠E/L 967: All-Hazards Position Specific Logistics Section Chief ⢠E/L 969: All-Hazards Position Specific Communications Unit Leader ⢠E/L 970: All-Hazards Position Specific Supply Unit Leader ⢠E/L 971: All-Hazards Position Specific Facilities Unit Leader ⢠E/L 973: All-Hazards Position Specific Finance/Admin. Section Chief ⢠E/L 975: All-Hazards Position Specific Finance/Admin. Unit Leader Course ⢠E/L 984: Task Force/Strike Team Leader ⢠E/L 986: Air Support Group Supervisor ⢠E/L 987: Introduction to Air Operations Contact information for State or Territorial Emergency Management Agencies can be found at https://training.fema.gov/programs/aps/stolist.aspx FEMA Emergency Management Institute (EMI) Available: http://training.fema.gov/emi.aspx As noted on the FEMA EMI website, FEMA EMI is located in Emmitsburg, Maryland on the campus of the National Emergency Training Center (NETC) and trains more than 2 million annually through onsite and offsite training and partnerships with emergency management training systems, colleges, universities; and technology-based mediums. EMI supports implementation of NIMS, the NRF, the National Disaster Recovery Framework (NDRF), and the National Preparedness Goal (NPG) and is âthe emergency management communityâs flagship training institution, and provides training to federal, state, local, tribal, volunteer, public, and private sector officials to strengthen emergency management core competencies for professional, career-long training.â Courses offered by EMI include the following: ⢠IS-100: Introduction to the Incident Command System (ICS)
80 ⢠IS-200: ICS for Single Resources and Initial Action Incidents ⢠ICS-300: Intermediate ICS for Expanding Incidents ⢠ICS-400: Advanced ICS ⢠IS-552: The Public Works Role in Emergency Management ⢠IS-554: Emergency Planning for Public Works ⢠IS-556: Damage Assessment for Public Works ⢠IS-558: Public Works and Disaster Recovery ⢠IS-559: Local Damage Assessment ⢠IS-632: Introduction to Debris Operations ⢠IS-700: Introduction to the NIMS ⢠IS-701.a: NIMS Multiagency Coordination System (MACS) ⢠IS-703.a: NIMS Resource Management ⢠IS-706: NIMS Intrastate Mutual AidâAn Introduction ⢠IS-800: Introduction to the National Response Framework Note that IS stands for Independent Study. IS courses are offered online and are free of charge. They include interactive quizzes and a final exam; a certificate will be issued to the student upon successful completion of the exam. Links can also be found on the FEMA EMI website to FEMA Independent Study (IS) Program and an online searchable catalog, the National Training and Education Directorate (NTED) which offers courses focused on helping responders function in mass consequence events and to the DHS Center for Domestic Preparedness (CDP) which focuses on delivering WMD training. Other FEMA resources that can be accessed via the website include FEMA NIMS Training Program webpage, FMA ICS Training Program and Resource Center, FEMA NRF Resources, and the FEMA National Fire Academy. Traffic Incident Management (TIM) Training Available: http://www.fhwa.dot.gov/goshrp2/solutions/all/l12_l32/national_traffic_incident_management_r esponder_training_program National Exercise Program (NEP) Available: http://www.fema.gov/national-exercise-program The NEP is a component of the NPS and allows the examination and validation of federal and whole communityâs core capabilities, and indicates national progress towards the NPG. More specifically, the NEPâs purpose is âto design, coordinate, conduct, and evaluate exercises that rigorously test the nationâs ability to perform missions and functions that prevent, protect against, respond to, recover from, and mitigate all hazards.â Each Program cycle is a two-year, progressive schedule of exercises of various types that are selected based on their support to the goal, and principal objectives.
81 The website also provides a link to the NEP document dated March 2011. FEMA.gov Exercise Webpage Available: www.fema.gov/exercise FEMAâs exercise webpage describes the NEP, the Homeland Security Exercise and Evaluation Program (HSEEP) which is used by NEP, the National Exercise and Simulation Center (NESC) which links planning, training, exercise, and response personnel with modeling and simulation capabilities. The webpage also describes the Radiological Emergency Preparedness (REP) Program and the Chemical Stockpile Emergency Preparedness Program (CSEPP) Program Exercises. Emergency Management Professional Program (EMPP) Available: http://training.fema.gov/empp/ FEMAâs EMI established an EMPP. The EMPP is a framework for acquiring the knowledge, skills, and abilities to enter and progress through the Emergency Management field. The EMPP includes three academies: ⢠National Emergency Management Basic Academy â focus is on foundational knowledge and skills ⢠National Emergency Management Advanced Academy (formerly the Leaders Academy) â focus is on Advanced Concepts and Issues in Emergency Management; Advanced Leadership & Management; Critical Thinking and Complex Problem Solving ⢠National Emergency Management Executive Academy - Strategic Leadership and Critical Thinking FEMA contacts for the programs are provide on this webpage. Emergency Management Performance Grant (EMPG) FY 2016 Program Requirements DHS Notice of Funding Opportunity (NOFO) Fiscal Year 2016 EMPG Available: https://www.fema.gov/media-library-data/1455571902574- a84f5a1b2f450795a70cce1f5ee7b967/FY_2016_EMPG_NOFO_FINAL.pdf EMPG-funded activities include updating emergency plans, conducting training, and designing and conducting exercises to validate core capabilities, maintain current capabilities, and enhance capability for high-priority core capabilities with low capability levels. EMPG recipients and subrecipients are expected to address capability targets and gaps identified through the annual THIRA and SPR process. EMPG program recipients are also required to develop a Multiyear Training and Exercise Plan (TEP) addressing THIRA risks and exercising/validating THIRA capability requirements in a progressive manner. Recipients should develop and maintain a progressive exercise program and a multiyear TEP consistent with HSEEP. EMPG program funds related to training should support NIMS implementation and emphasize NIMS Training Program core competencies. NIMS Training - Independent Study (IS) 100, IS 200, IS 700, and IS 800 are required for EMPG-funded personnel. In addition, they are required to complete either the courses in the Professional Development Series or the National Emergency Management Basic Academy.
82 Exercise required include no less than four quarterly exercises (i.e., one EMPG-funded exercise and/or an exercise that includes EMPG-funded personnel per quarter) of any type and one full- scale exercise within a 12-month period. The exercises should increase in complexity and have common program priorities. In addition, EMPG-funded personnel are required to participate in no fewer than three exercises in a 12-month period. Allowable training- and exercise-related costs are described in the document and in Appendix B, and include the establishment, support, conduct, and training attendance. The Work Plan in Appendix C includes a Program and Budget Narrative, Personnel Data Table, Training Data Table, Exercise Data Table, and Grant Activities Outline. Emergency Management Accreditation Program (EMAP). September 2012, EMAP Lexington, Kentucky. Available: https://www.emap.org/index.php The Emergency Management Standard by EMAP is the set of 64 standards by which programs that apply for EMAP accreditation are evaluated. The Emergency Management Standard is designed as a tool for continuous improvement as part of the voluntary accreditation process for local and state emergency management programs. The Emergency Management Standard covers: ⢠Program Management ⢠Administration and Finance ⢠Laws and Authorities ⢠Hazard Identification, Risk Assessment and Consequence Analysis ⢠Hazard Mitigation ⢠Prevention ⢠Operational Planning ⢠Incident Management ⢠Resource Management and Logistics ⢠Mutual Aid ⢠Communications and Warning ⢠Operations and Procedures ⢠Facilities ⢠Training ⢠Exercises, Evaluations and Corrective Action ⢠Crisis Communications, Public Education and Information Emergency Management Standard Citation. Emergency Management Accreditation Program (EMAP), Emergency Management Standard, 2013. Available: https://www.emap.org/index.php/root/for-programs/23-2013- emergency-management-standard/file
83 Synopsis. The purpose of the EMAP Standard is described in Chapter 1 as follows: The Emergency Management Standard establishes the minimum acceptable performance criteria for an Emergency Management Program and intends that the standard be fair and equitable for all who choose to adopt it. Users of the standard are also mentioned in Chapter 1 as being Emergency Management Programs seeking EMAP accreditation and those seeking a self-assessment standard for their Emergency Management Program. The document notes that there is a three-year review cycle for the standard. Program elements of an accredited Emergency Management Program are discussed and described in the standard. Training is described in section 4.13. According to the document, a training program should include âthe assessment, development and implementation of appropriate training for Program officials, emergency management response personnel and the public.â The key elements of a training program include: ⢠Training needs assessment, curriculum, course evaluations, and records of training. ⢠Training for emergency personnel consistent with their current and potential responsibilities, including specialized training related to the threats facing the jurisdiction. Regularly scheduled training âbased on the training needs assessment, internal and external requirements, and mandates (i.e. NIMS) and addresses deficiencies identified in the corrective action process.â ⢠Maintenance of appropriate training records. ⢠Exercises, Evaluations and Corrective Actions are described in section 4.14. According to the document, an accredited Emergency Management Program should have an exercise, evaluation and corrective action process. The key elements include: ⢠A documented exercise program that âregularly tests the skills, abilities, and experience of emergency personnel as well as the plans, policies, procedures, equipment, and facilities of the Emergency Management Programâ and is tailored to the jurisdictionâs hazards. ⢠The Emergency Management Program âshall evaluate plans, procedures, and capabilities through periodic reviews, testing, post-incident reports, lessons learned, performance evaluations, exercises, and real world events.â ⢠A process for corrective actions to prioritize and track the resolution of deficiencies in real world and exercise events, and to revise relevant plans. FHWA SHRP2 Solutions: Training for Safer, Faster, Stronger, More Integrated Incident Response. National Traffic Incident Management Responder Training Program Available: http://www.fhwa.dot.gov/goshrp2/Solutions/SafetyTopic/L12_L32A_L32B/National_Traffic_In cident_Management_Responder_Training_Program The Second Strategic Highway Research Program (SHRP 2) has developed a multidisciplinary and interjurisdictional training program for TIM. The SHRP2 training program, National TIM
84 Responder Training Program, meets the challenge of âfaster clearance and improved safetyâ for both motorists and responders, and is endorsed by the International Association of Chiefs of Police, the International Association of Fire Chiefs, and the National Volunteer Fire Council. The program incorporates effective practices and standards and was developed through the second Strategic Highway Research Program (SHRP2). The program is available at no cost from the National Highway Institute (NHI) in two forms â a four-hour in-person training which promotes interaction among police, firefighters, DOT, medical personnel, and other incident responders and a four- hour, web-based version, FHWA-NHI-133126. Various resources (fact sheets, brochures, communications toolkit, train-the-trainer course overview) are available for download on this website. National TIM Responder Training Program Frequently Asked Questions (FAQs) Available: http://www.fhwa.dot.gov/goshrp2/Content/Documents/TIM_Training_FAQs.pdf Synopsis. The FAQs describes the training program as a ânational curriculum developed by responders for responders.â It also notes that there is a Train-the-Trainer course for participants who would like to become a trainer. TIM is described as âthe process of coordinating the resources of a number of different public and private sector partners to detect, respond to, and clear traffic incidents as quickly as possible to reduce the duration and impacts of incidents, while protecting the safety of on-scene responders and the traveling public.â AASHTO National Traffic Incident Management Coalition Available: http://ntimc.transportation.org/Pages/ObjectivesandStrategies.aspx This AASHTO website provides links to numerous TIM publications, brochures, videos, and training resources. National Highway Institute (NHI) Training Available: https://www.nhi.fhwa.dot.gov/default.aspx TIM-related courses include the following: The NHI offers courses relevant to TIM. These courses include National Traffic Incident Management Responder Training (133126) course, Design and Operation of Work Zone Traffic Control, Work Zone Traffic Control for Maintenance Operations, Flagger Training, Successful Traffic Signal Management, Advanced Work Zone Management and Design, Principles of Evacuation Planning Tutorial, and Managing Travel for Planned Special Events. For additional information and to search for courses, visit the NHI website (âNational Highway Institute: Search for Courses,â NHI n.d.: https://www.nhi.fhwa.dot.gov/default.aspx). Protection of Transportation Infrastructure from Cyber Attacks: A Primer Citation. NCHRP Web-Only Document 221/TCRP Web-Only Document 67: Protection of Transportation Infrastructure from Cyber Attacks: A Primer, Transportation Research Board of
85 the National Academies, Washington, DC, 2016. Available: https://www.nap.edu/download/23516 Synopsis. This Primer describes the key cybersecurity training principles and highlights the importance of cybersecurity culture in the chapter on Training. The Primer makes the case for creating a robust cybersecurity culture by noting that people are essential to building a cybersecurity culture and are also the most vulnerable element in protecting an agencyâs cyber assets. The key concepts and information introduced in this chapter are based on NIST training resources along with the following references: APTA Recommended Practices Part 2, The Transportation Roadmap (August 2012), the Cybersecurity Framework (February 12, 2014), and the Homeland Security Workforce Assessment Act signed into law December 2014. The legislation requires DHS to create a strategy âto enhance the readiness, capacity, training, recruitment and retention of its cybersecurity workforce.â The Primer also refers to the Federal Information Security Modernization Act (2014) governing federal IT and cybersecurity and requires role-based training for federal personnel and other users of federal IT systems. While this Actâs focus is on federal personnel, the guidance which will be provided based on this Act should be of interest to transportation agencies. Therefore, according to the Primer, much focus needs to be placed by senior management on culture-building initiatives including awareness and training. The Primer also presents NISTâs cybersecurity learning continuum model in which learning progresses from security awareness to cybersecurity essentials to role-based training to education and/or experience. The Training chapter also describes Functions and User categories, awareness content and resources, training content and resources, evaluation techniques, performance indicators, and the importance of continuous improvement. With respect to delivery methods, the use of interactive training techniques, technologies, shared resource models, and interagency and interjurisdictional activities are discussed. Transportation System Management & Operations (TSM&O) Workforce Development White Papers Three White Papers were developed as a result of the NOCoE Workforce Development Summit on June 22-23, 2016. ⢠The first paper provides general background and context regarding TSM&O as a program activity and TSM&O staffing within transportation agencies and the private sector. ⢠The second paper addresses the needed staff competencies and related education and training. ⢠The third White Paper focuses on TSM&O workforce recruitment, retention and professional career development. White Paper No. 2: Competencies, Education and Training
86 Available: https://transops.s3.amazonaws.com/uploaded.../Summit%20White%20Paper%202.pdf Synopsis. The second White Paper describes the TSM&O workforce characteristics, key positions, and the size and nature of the workforce development problem. The White Paper presents a competencies matrix by function (Exhibit 1) and a training resources table (Exhibit 2) showing available resources by function. The categories of functions includes: ⢠Sr. Policy, Strategic Management ⢠Sr. Program Management ⢠Mid-level Program Management ⢠Program Planners ⢠System Engineering and Related Technical Specialties ⢠Mid-level Project Management ⢠Field Staff In addition, the White Paper estimates training demand for each of these functions and how they may be met. Exhibit 3 presents training available by source and level. White Paper No. 3: Recruitment, Retention and Career Development, National Operations Center of Excellence Available: https://transops.s3.amazonaws.com/uploaded.../Summit%20White%20Paper%203.pdf The third White Paper is based on a May 2016 survey of the AASHTO TSM&O Subcommittee members and Operations Academy graduates regarding TSM&O recruitment and retention. The top two issues of the 34 responding agencies were lack of existing training vs. emerging needs and the lack of a clear career path. Other key findings included: ⢠âMost agencies have retained a level staffing or increased slightly, perhaps reflecting continuing overall state DOT staffing restrictions. ⢠Most states appear to be having some difficulty filling key technical positions âespecially in systems engineering, IT and ITS device maintenance âand approximately half were significantly dependent on consultants. ⢠About one-half of responses indicated that new hires were generally knowledgeable in one or more specific TSMO topic areas (e.g., traffic signals) with the other half with little knowledge. None indicated that their new hires were TSM&O savvy. ⢠Difficulties in recruitment related to salary competition and/or lack of required skills/certifications.â Exploring the Role and Adoption of Technology-Based Training and Employment Services Citation. Gan, Katherine, et al. Exploring the Role and Adoption of Technology-Based Training and Employment Services. Final Report. Prepared for the US Department of Labor. September 27, 2013. Available: https://wdr.doleta.gov/research/FullText_Documents/ETAOP_2015- 09_Attach.pdf
87 Synopsis. As part of the U.S. Department of Laborâs national initiative to explore the role and adoption of technology-based learning (TBL) within the public workforce, descriptive information about TBL use at the state and local levels of the workforce system was collected through an online survey of state workforce agency administrators and executive directors of Local Workforce Investment Boards. Factors regarding the adoption of TBL included: ⢠Development of infrastructure through new investments and leveraging existing resources. ⢠Integration of personal support through design components or tutoring or mentoring. ⢠Use of a digital âon-rampâ which is attentive to participantsâ levels of technological literacy. ⢠Active promotion and marketing of TBL. ⢠Commitment to technical assistance. Curriculum for New State DOT Transit Grant Managers in Administering Federal and State Transit Grants Citation. Knapp, Sue, et al. NCHRP Web-only Document 203: Curriculum for New State DOT Transit Grant Managers in Administering Federal and State Transit Grants, Transportation Research Board of the National Academies, Washington, DC, 2014. Available: http://www.trb.org/Publications/Blurbs/171298.aspx Synopsis. The curriculum is organized into modules and submodules appropriate for state transit staff. Module topics include: ⢠Introduction to FTA grants ⢠Legal authority & annual certifications ⢠Grant administration ⢠Financial management ⢠Project management & grantee oversight ⢠Planning ⢠Procurement ⢠Asset management ⢠Safety & security ⢠Subrecipient personnel-related issues ⢠Subrecipient service requirements & restrictions ⢠Training & technical assistance Safety & Security In the description of the Safety & Security module, it is noted that Section 5329, MAP-21 (49 USC 5329) provides FTA with the authority to establish a national transit safety framework, requires DOT to establish a national transit safety plan which includes safety performance criteria and standards and a Safety Certification Training Program for federal and state workers, contractors who conduct oversight, and transit workers responsible for safety oversight, and requires FTA funding recipients to create an agency safety plan and certify it meets FTA
88 requirements. Up to 0.5% of Section 5307 or 5311 funds can be used to fund transit worker training in the Safety Certification Training Program. Training & Technical Assistance The key concepts in this module include FTA requirements for states. States are required to: ⢠Inform subrecipients of federal requirements and provide technical assistance to meet the requirements ⢠Subrecipients are required to train their own staff in several topic areas including: o Safety o ADA o Drug & Alcohol ⢠FTA requires states to certify that they have well-trained and well-informed staff when carrying out proposed projects ⢠States need to provide training to potential subrecipient applicants for applicants serving predominantly minority populations ⢠FTAâs Rural Transportation Assistance Program (RTAP) funds subrecipient training and technical assistance. States have RTAPs that conduct state-sponsored training and offer training scholarships, and provide technical assistance. Additional FTA-funded training programs noted in this module include: ⢠Transportation Safety Institute (TSI) ⢠National Transit Institute (NTI) ⢠National RTAP ⢠National Center on Senior Transportation (NCST) ⢠Easter Seals Project Action (ESPA) Additional recommended resources include: ⢠Community Transportation Association of America (CTAA) ⢠American Public Transportation Association (APTA) Attracting, Recruiting, and Retaining Skilled Staff for Transportation System Operations and Management Citation. Cronin, Brian, et al. NCHRP Report 693: Attracting, Recruiting, and Retaining Skilled Staff for Transportation System Operations and Management, Transportation Research Board of the National Academies, Washington, DC, 2012. Available: http://www.trb.org/Publications/Blurbs/166342.aspx Synopsis. The report helps transportation agencies recruit and retain qualified professional staff in Systems Operation and Management (SOM). Findings are based on an analysis of SOM career paths, skill requirements, and training needs to identify successful programs, state-of-the-art initiatives, and best industry practices. For the core job function of Real-time Operations, competencies were grouped into Operations Strategies, Systems and Technology, Safety, Security, and Management of Real-time Operations Systems.
89 ⢠âOperations Strategies â Maintenance of the capacity and safety of highways by controlling traffic, responding to incidents, clearing snow and other obstructions, and providing information to users on highway conditions and alternatives. ⢠Systems and Technology â Knowledge and understanding of the departmentâs operating systems as well as the technology required to carry out real-time operations. ⢠Safety â Focus on crash avoidance by enhancing driver performance, including advanced collision avoidance systems and the automated highway system. ⢠Security â Precautions taken to guard against the danger, risk, or safety threats of major highways. Management of Real-Time Operations Systems â The integration of key activities to ensure real-time monitoring of the traffic and travel conditions of major highways and sharing that information to improve transportation system security; address congestion; improve response to emergencies, weather events, and surface transportation incidents; and facilitate national and regional highway traveler information.â (page 21). Exhibit 28 provides an Overview of Strategic SOM Workforce Recommendations by Career Stage. For entry-level or new SOM workers, mentoring programs are recommended. Pages 106-108 describe the steps necessary to implement a mentoring program. TCRP F-Series Reports The F-series publications provide an excellent source of training literature focused primarily on the transit industry. In particular TCRP Report 162: Building a Sustainable Workforce in the Public Transportation IndustryâA Systems Approach, 2013, provides information on 11 training and development strategies and implementation steps along with sample programs implemented at specific agencies and Professional Capacity Building strategies that can complement an agencyâs training initiatives. Washington State Transportation Training Coalition Available: http://www.wsttc.org/ The Washington State Transportation Training Coalition is a collaboration of transit, highway, university and insurance. According to the site, Washington State Transit Insurance Pool (WSTIP) in partnership with WSDOT, Washington State Transit Association, Community Transportation Association of the Northwest, and Eastern Washington University Tribal Technical Assistance Program comprises the coalition. The Training Coalition coordinates approximately 20 training events each year at various locations throughout the state. Southern California Regional Transit Training Consortium Available: http://www.scrttc.com The Southern California Regional Transit Training Consortium (SCRTTC), through its network of Community Colleges, Universities, Transit Agencies, Public and Private Organizations develop and deliver training to transit workforce. The SCRTTC also assists them in finding appropriate employment within the transit industry.
90 NCHRP Web-Only Document 215: Incident Command System (ICS) Training for Field- Level Supervisors and Staff Citation. Edwards, F.L., Goodrich, D.C., Griffith, J., NCHRP Web-Only Document 215: Incident Command System (ICS) Training for Field-Level Supervisors and Staff, Mineta Transportation Institute, Transportation Research Board of the National Academies, Washington, DC, 2015, [Online]. Available:http://onlinepubs.trb.org/onlinepubs/nchrp/nchrp_w215.pdf Synopsis. According to its page on TRBâs web site, this publication âprovides training materials and guidance for transportation field personnel to help their organizations operate safely in an emergency or traffic management event. This course is intended to review the basic ICS structures and terminologies aimed to ensure safety, personnel accountability, and support for the agencyâs financial reimbursement efforts. The product includes lesson plans, guidance on classroom set up, complete slide shows with scripts or instructor prompts, instructions for creating materials, and some information about training for adults. Specifically, the materials include: 1. A video presentation with voice-over 2. An Instructor Guide and Student Course Evaluation 3. An Instructor Guide and Student Evaluation 4. Discussion-Based Training Scenarios 5. ICS Quick Start Cards 6. A Supervisorâs Folder The TRB web page for this publication continues, âThe course material provided in this project assumes that instructors have completed classes on delivering training to adults, have certificates in at least ICS 100, 200 and 300, and have some experience with ICS, at the field level or in an emergency operations center (EOC). It is also assumed that instructors may have had experience working with a transportation agency in emergency planning or training, or as a field supervisor, and to have also completed ICS 400 and E/L449 ICS âIncident Command System Curricula TTTâ courses.â The report itself consists of 12 chapters. Chapter 1 discusses how to use the Instructor Guide. Chapter 2 discusses how the course and pilot programs were developed, and revealed the results of interviews and surveys providing feedback from pilot program participants. The Lesson Plans are in Chapter 3. Chapters 4 and 5 include the materials for Module 1, Chapters 6 and 7 the materials for Briefing Training, and Chapters 8 and 9 the materials for the Discussion-Based Scenarios. Chapter 10 consists of the ICS Quick Start Cards and accompanying instructions. Chapter 11 describes the materials in the Supervisorâs Folder. The report concludes in Chapter 12 with references related to the Incident Command System (ICS) and the Traffic Incident Management System (TIMS). Homeland Security Exercise and Evaluation Program (HSEEP) Citation. HSEEP, DHS, 2013. Available: https://www.fema.gov/media-library-data/20130726- 1914-25045-8890/hseep_apr13_.pdf
91 Synopsis. The HSEEP provides a set of guiding principles for exercise programs, as well as a common approach to exercise program management, design and development, conduct, evaluation, and improvement planning. HSEEP exercise and evaluation doctrine is flexible, adaptable, and is for use by stakeholders across the whole community and is applicable for exercises across all mission areas â prevention, protection, mitigation, response, and recovery. The HSEEP document is organized in the following manner: ⢠Chapter 1: HSEEP Fundamentals describes the basic principles and methodology of HSEEP. ⢠Chapter 2: Exercise Program Management provides guidance for conducting a Training and Exercise Planning Workshop (TEPW) and developing a Multiyear Training and Exercise Plan (TEP). ⢠Chapter 3: Exercise Design and Development describes the methodology for developing exercise objectives, conducting planning meetings, developing exercise documentation, and planning for exercise logistics, control, and evaluation. ⢠Chapter 4: Exercise Conduct provides guidance on setup, exercise play, and wrap-up activities. ⢠Chapter 5: Evaluation provides the approach to exercise evaluation planning and conduct through data collection, analysis, and development of an AAR. ⢠Chapter 6: Improvement Planning addresses corrective actions identified in the exercise IP and the process of tracking corrective actions to resolution. Fundamental principles for exercise programs and individual exercises include the following: ⢠They should be guided by Elected and Appointed Officials. ⢠They are capability-based and objective driven. Exercises evaluate performance against capability-based objectives based on the NPGâs series of core capabilities. ⢠A progressive planning approach with an increasing level of complexity over time should be used. ⢠Whole community integration should take place throughout the exercise planning and execution process. ⢠HSEEPâs common methodology for exercises should be used so that diverse organizations can readily collaborate and have a shared understanding. ⢠Exercises should be informed by risk. Key elements of HSEEPâs approach to exercise program management include: ⢠Engaging Elected and Appointed Officials to Provide Intent and Direction. ⢠Developing a Multiyear TEP and Establishing Multiyear Exercise Program Priorities. These priorities inform the development of individual exercise objectives, ensuring coordinated and integrated. ⢠Using a Progressive Approach. Which builds towards an increasing level of complexity over time. ⢠Maintaining a Rolling Summary of Exercise Outcomes. A rolling summary report provides elected and appointed officials and other stakeholders with an analysis of issues, trends, and key outcomes from all exercises conducted as part of the exercise program. ⢠Managing Exercise Program Resources. An effective exercise program utilizes the full range of available resources for exercise budgets, program staffing, and other resources.
92 Phases of the Exercises Cycle The exercise cycle phases described in HSEEP include: ⢠Design and Development ⢠Conduct ⢠Evaluation ⢠Improvement Planning Design and Development: Exercise planning team members determine exercise objectives and design the scenario and ensure that they are aligned with the overall multiyear plan. They also engage with key officials, state EMA, and other stakeholders; create documentation and the exercise plan; and, coordinate logistics. Safety of exercise participants is a key aspect of the exercise logistics. Exercise design and development steps include: â⢠Setting the exercise foundation by reviewing elected and appointed officialsâ guidance, the TEP, and other factors; ⢠Selecting participants for an exercise planning team and developing an exercise planning timeline with milestones; ⢠Developing exercise-specific objectives and identifying core capabilities based on the guidance of elected and appointed officials; ⢠Identifying evaluation requirements; ⢠Developing the exercise scenario; ⢠Creating documentation; ⢠Coordinating logistics; and ⢠Planning for exercise control and evaluation.â Design: The core components include establishing the scope, objectives, scenario, documentation, and media and public relations guidance. Objectives: Generally, planners should select a reasonable number of specific, measurable, achievable, relevant, and time-bound (SMART) exercise objectives Regarding the planning teams and reporting structure, a sample planning team structure and recommendations regarding organizational structure are provided in HSEEP: ⢠Planning team structure: The team can be structured according to an ICS-type structure with the Exercise Planning Team Leader in the Commander position. Operations develops and evaluates the scenario. Planning develops/compiles all documentation and may be responsible for any simulated actions by absent positions/agencies necessary for the exercise. Logistics elements include service such as transportation, signage, food, medical, and security and support such as communications and supplies. Administration/Finance Section provides financial and administrative support. ⢠The importance of understanding the exercise objectives and identifying core capabilities associated with each objective and designing the exercise and evaluation plan around the capabilities to be tested are emphasized in HSEEP. ⢠Training and Exercise Planning Workshop (TEPW): TEPWs, based on guidance from officials, establish exercise program strategy and structure, and set priorities and a multiyear schedule of training and exercise. TEPWs encourage efficiency, effectiveness, and coordination of exercise initiatives. TEPW participants are diverse and include elected and appointed officials, persons with administrative responsibility and those in relevant disciplines, and representatives from relevant NGOs or social support organizations. They
93 review and take into account jurisdiction-specific threats and hazards from THIRA and risk assessments, AAR results, regulations and other external requirements. Conduct: Conduct-related activities include preparing for exercise play, managing exercise play, and conducting immediate exercise wrap-up activities. Conduct techniques for Discussion-based exercises and Operations-based exercises are presented in this section. Participant roles and responsibilities are also described in HSEEP, Table 4.1. Evaluation: Evaluation compares performance of exercise teams, individuals, equipment, protocols, systems, and plans against objectives. The evaluation section includes information on planning, exercise documentation and analysis, identification of strengths and improvement areas, and development of AARs. Evaluation planning begins at the start of exercise design and development. Exercise evaluation guides (EEGs) are designed to streamline data collection, and facilitate assessment of core capabilities, objectives, capability targets and critical tasks in a consistent manner. Improvement Planning: Improvement planning identifies improvements based on corrective actions revealed during the exercise. The improvement planning results are included in or appended to the AAR. Improvements may include changes to plans, procedures, organizational structures, processes, equipment or other resources, training. Individual corrective actions should be monitored until they have been implemented. Interactive Training for All-Hazards Emergency Planning, Preparation, and Response for Maintenance and Operations Field Personnel Citation. NCHRP Synthesis Report 468: Interactive Training for All-Hazards Emergency Planning, Preparation, and Response for Maintenance and Operations Field Personnel, Transportation Research Board of the National Academies, Washington, DC, 2015. Available: http://www.trb.org/Main/Blurbs/172182.aspx Synopsis. The genesis of this Synthesis was the increasing challenges facing state DOTâs and public works agencies: ⢠State DOTs and public works agencies are being challenged with expanding roles in all- hazards emergencies and increasing public expectation of safe and secure transportation infrastructure and quick restoration of public services. The Synthesis also stresses the importance of Maintenance and Operations personnel of DOTs, tribal, and local public works agencies with respect to emergency preparedness and response. Their preparedness is critical to public safety as they are frontline personnel during emergencies and disasters. They are usually first on the scene and the last to leave. This Synthesis Report identifies interactive emergency training tools and sources that may be applied by maintenance and operations field personnel of state DOTs and public works agencies. The report also identifies potential obstacles to their implementation and develops a toolkit of
94 relevant training and exercise information. The target audience of the Synthesis was the managers of M&O field personnel. Chapter 1 introduces NIMS, the importance of training and exercises and their place in the Preparedness Cycle, the Emergency Operations Plan and other plans and procedural documents. Chapter 2 describes emergency training and exercise needs of M&O field personnel including NIMS, TIM, federal directives, mutual aid and grants, winter maintenance and operations, evacuation, continuity of operations, supervisor training, and exercises. Chapter 3 covers the following emergency training and exercise delivery methods: ⢠Field Crew Meetings ⢠Just-in-Time Training ⢠Interjurisdictional and Interagency Training and Exercises ⢠Joint Training ⢠Asynchronous Training ⢠Train-the-Trainer ⢠Planned Events, Incidents, and Exercises ⢠Computer-Assisted Simulations ⢠Classroom Training ⢠Online Training with Live Instructors ⢠Blended Training ⢠Exercises Chapter 4 on emergency training and exercise practices discusses implementation challenges, training needs and solutions, findings on the use of exercises and additional findings. Challenges: Key challenges were scheduling difficulties and limited budgets. Additional challenges included lack of qualified training staff, personnel turnover, distance issues, senior management issues, inadequate facilities and other resources, insufficient information about available training, and infrequent need for training. Interactive Solutions: For adult learners whose motivation is problem-centered, interactive training is ideal. The interactive solutions identified in the Synthesis included both Synchronous methods and Asynchronous methods. Synchronous methods require a live instructor and take place at a fixed time. Participants are able to interact with the instructor and with each other through the web or in-person. Asynchronous methods, however, are more flexible and can take place according to the learnerâs schedule and pace. It can also be less costly than synchronous training. Table 30 presents Implementation Issues and Possible Solutions. Additional findings included: Peer-to-Peer Training, Field Training, In-House Training, Professional Organizations and Certifications, and other Training. Findings on use of exercises included: Discussion-based exercises, Operations-based exercises, exercise evaluation, exercise scenarios, training and exercises for PWs, training and exercises for contractors, and law enforcement and fire departments.
95 Chapter 5 described the development of the Toolkit which presents key courses and catalogs, guidance documents, source organizations, and source-specific information. Chapter 6 presented the conclusion to the Synthesis and a summary of the key findings and further research needs. The appendices include: A â Toolkit, F â Washington DOT EOP Training and Exercises, G â Arizona DOT Emergency Planning, Management, and Maintenance Training Matrices, H â Missouri DOT Training Plan, and I â Missouri DOT NIMS Training Guide. Toolkit: The purpose of the Toolkit was to provide all-hazards emergency training resources including source organizations, key courses and course catalogs guidance documents were presented in an Excel spreadsheet, were interactive to varying extents, and encompassed a variety of delivery methods. Those organizations that were a source of emergency operations and hazards awareness training and exercises include the following: 1. Federal (FEMA) 2. Federal (other DHS) 3. Federal (U.S.DOT) 4. Federal (other federal departments, administrations, agencies, etc.) 5. State 6. Local 7. University/college 8. Associations and coalitions 9. Private firm. Incorporating Transportation Security Awareness into Routine State DOT Operations and Training Citation. NCHRP Report 793: Incorporating Transportation Security Awareness into Routine State DOT Operations and Training, Transportation Research Board of the National Academies, Washington, DC, 2014. Available: Http://Onlinepubs.TRB.Org/Onlinepubs/NCHRP/NCHRP_Rpt_793.Pdf Synopsis. This Report outlines techniques to integrate all-hazards security awareness concepts and reminders into routine state DOT operations, maintenance, and training. The Report is structured as follows: Section 1 â introduces transportation security and role of state DOTs Section 2 â presents organizational readiness and five key âQuestions to Askâ before implementation of a security awareness program Section 3 â identifies components of a security awareness campaign including general messages and delivery methods Section 4 â provides relatively inexpensive methods to promote security awareness Appendices Appendix A â Overview of current training and resources
96 Appendix B â Contact list of transportation security training organizations Appendix C â Directory of transportation security resources The Report notes that many DOTs may believe security is not DOT business. However, because transportation systems are vulnerable to various hazards and threats, DOTs play a significant role in infrastructure security and have the responsibility of controlling access to critical components, coordinating with law enforcement to ensure quick response, conducting risk and vulnerability assessments, and taking action to address the effects of risks and vulnerabilities. Hence, security awareness is important for all employees and is the cornerstone of a security culture in which security is an integral part of daily routine. The Report states that all transportation employees contribute to security by being vigilant and detecting suspicious activity, and by deterring unlawful acts simply by their presence. The Report also notes that all employees should also understand the risks to transportation systems and assets, know how to recognize a security risk, what to do and what to do, and how to report a security threat. Section 3, Figure 1 provides a security reporting procedures flowchart used by Texas DOT. Training sources described in Appendix A and B include DHS/TSA, TRB, NTI, CTSSR, FHWA, NHI, FTA, FMCSA, PHMSA, FEMA, LTAP/TTAP, other federal training, SEMA, RDPC, other sector resources, and other security resources. Security awareness programs described in Appendix C include If You See Something, Say Somethingâ¢, First Observerâ¢, Highway Watch, and Transit Watch. Guidelines for Transportation Emergency Training Exercises Citation. NCHRP Report 525: Surface Transportation Security, Vol. 9/TCRP Report 86: Vol. 9, Guidelines for Transportation Emergency Training Exercises, Transportation Research Board of the National Academies, Washington, DC, 2006. Available: http://onlinepubs.trb.org/onlinepubs/nchrp/nchrp_rpt_525v9.pdf Synopsis. The report is designed to assist transportation agencies in developing drills and exercises in alignment with the NIMS. The report describes the process of emergency exercise development, implementation, and evaluation. In addition, the available literature and materials to support transportation agencies such as state DOTs, traffic management centers, and public transportation systems are described NCRRP Report 2 A Guide to Building and Retaining Workforce Capacity or the Railroad Industry (2015) Citation. NCRRP Report 2 A Guide to Building and Retaining Workforce Capacity or the Railroad Industry, Transportation Research Board, 2015. Available: http://www.trb.org/Main/Blurbs/173352.aspx Synopsis. The report addresses current workforce development issues for the railroad industry, and identifies best practices for creating and maintaining a competent workforce. The authors note
97 that the majority of the current workforce is or will be retiring, creating an urgency regarding knowledge transfer and the need to address the requirements of younger workers. The reportâs authors identified the following key training successes, challenges, and recommendations. Successes: ⢠On-the-job training creates positive training experiences. ⢠State-of-the-art railroad education and training centers include the Railroad Education and Development Institute. Challenges: ⢠Experienced workers may be averse to provide on-the-job training due to liability concerns. ⢠Lack of qualified trainers ⢠Lack of consistent and standardized training programs ⢠Adapting training to different education and experience levels Recommendations: ⢠A culture of preceptorship and mentoring should be created. ⢠Increased standardization and focus on training should be promoted. ⢠World-class training facilities and programs to deliver both classroom and hands-on training should be established. TCRP Web-Only Document 60/NCHRP Web-Only Document 200: Command-Level Decision Making for Transit Emergency Managers Citation. Pigora, Mary Ann. TCRP Web-Only Document 60/NCHRP Web-Only Document 200: Command-Level Decision Making for Transit Emergency Managers. Transportation Research Board of the National Academies. Washington, DC, 2013 [Online]. Available: http://www.trb.org/TCRP/Blurbs/169839.aspx. Synopsis. TRBâs TCRP Web-Only Document 60 and NCHRP Web-Only Document 200: Command-Level Decision Making for Transit Emergency Managers describes the development and implementation of Transit Emergency Response Application (TERA). The project goal was to develop a TERA âto achieve the goals as outlined in the National Response Framework through simulation guided experiential learning.â As stated in the report, âTERA provides training and exercise for command-level roles in the transit agency emergency operations center in relation to mitigating transit-specific emergencies and supporting state and local emergency management authorities in natural or man-made disaster incidents.â The Transit Scenarios included: flood, hurricane, earthquake, power outage, hazardous materials, and active shooter. TERA was later expanded with supplemental NCHRP funding to include state DOT roles. These expansion activities were executed in Phase 3 of the project. The research approach introduced in Chapter 1 and described more fully in Chapter 2, involved three phases and the following sample activities per Phase: Phase 1
98 ⢠Training Needs Analysis ⢠Role-based learning objective profiles ⢠Prioritized list of potential TERA scenarios Phase 2 ⢠Developed storyboards and facilitator/user guides ⢠Developed a prototype module ⢠Performed field testing of the prototype module Phase 3 ⢠Developed the scenario-based training system ⢠Executed Test Plan Chapter 3 presents the project findings. Table 3, Scenarios with Task Function Differentiators, is included in this Chapter. The Table provides a listing of various natural disaster and terrorism scenarios and also identifies sources and task function differentiators for each scenario. Chapter 4 recommends an approach to obtaining organizational acceptance for TERA and lists sources of technical and financial support along with training and system support. Chapter 5 presents the conclusions of the project report. Appendix A provides scenario outlines for ⢠Flood with Hazmat spill ⢠Subway Bombing/Active Shooter ⢠Hurricane ⢠Earthquake ⢠Cyber Attack on the Power Grid ⢠Hazmat Appendix B describes command-level transit agency role profiles. Appendix C describes training objectives for transit agency roles. Appendices D â K are only available through request via Stephan Parker. They include Scenario Scripts and Tasks by Role. Emergency management professionals in the transportation, transit, rail, and airport domains may register to use TERA for free at www.tera.train-emst.com. Advancing Workforce Health at the Department of Homeland Security: Protecting Those Who Protect Us Citation. Advancing Workforce Health at the Department of Homeland Security: Protecting Those Who Protect Us, National Academies Press, Washington, DC, 2014, [Online].
99 Available: http://www.nap.edu/catalog/18574/advancing-workforce-health-at-the-department-of- homeland-security-protecting Synopsis. From the TRID Database: âThe more than 200,000 men and women that make up the DHS workforce have been entrusted with the ultimate responsibility â ensuring that the homeland is safe, secure, and resilient against terrorism and other hazards. Every day, these dedicated individuals take on the critical and often dangerous challenges of the DHS mission: countering terrorism and enhancing national security, securing and managing the nationâs borders, enforcing and administering U.S. immigration laws, protecting cyber networks and critical infrastructure, and ensuring resilience in the face of disasters. In return, DHS is responsible for protecting the health, safety, and resilience of those on whom it relies to achieve this mission, as well as ensuring effective management of the medical needs of persons who, in the course of mission execution, come into DHS care or custody. âSince its creation in 2002, DHS has been aggressively addressing the management challenges of integrating seven core operating component agencies and 18 supporting offices and directorates. One of those challenges is creating and sustaining a coordinated health protection infrastructure. This report examines how to strengthen mission readiness while better meeting the health needs of the DHS workforce. This report reviews and assesses the agencyâs current occupational health and operational medicine infrastructure and, based on models and best practices from within and outside DHS, provides recommendations for achieving an integrated, DHS-wide health protection infrastructure with the necessary centralized oversight authority.â Protecting the homeland is physically and mentally demanding and entails many inherent risks, necessitating a DHS workforce that is mission ready. Among other things, mission readiness depends on (1) a workforce that is medically ready (free of health-related conditions that impede the ability to participate fully in operations and achieve mission goals), and (2) the capability, through an operational medicine program, to provide medical support for the workforce and others who come under the protection or control of DHS during routine, planned, and contingency operations. The recommendations of this report will assist DHS in meeting these two requirements through implementation (of) an overarching workforce health protection strategy encompassing occupational health and operational medicine functions that serve to promote, protect, and restore the physical and mental well-being of the workforce.â This report has nine chapters and includes an extensive Summary. The first chapter is the Introduction. The second chapter presents the history and the challenges of the DHS Workplace and Health System. Chapter 3 presents a Comprehensive Framework for Ensuring the Health of an Operational Workforce. Chapter 4 discusses the Current State of Workforce Health Protection at DHS, and Chapter 5 discusses the need for Leadership Commitment to Workforce Health and the current strategic approach. While Chapter 6 discusses Organizational Alignment and Coordination, Chapter 7 discusses Functional Alignment. The topic of Chapter 8 is Information Management and Integration. The report concludes with Considerations for Implementation (Chapter 9). FY Fiscal Year 2016 Transit Security Grant Program Fact Sheet
100 Citation. âFiscal Year 2016 Transit Security Grant Program Fact Sheet,â FEMA, Washington, DC, [Online]. Available:http://www.fema.gov/media-library-data/1467253705754- fbe7bb22b360adbe19e8ba1a4a8ef4e8/FY_2016_TSGP_Fact_Sheet_Final.pdf Synopsis. The 2016 Transit Security Grant Program (TSGP) is appropriated by the Department of Homeland Security Appropriations Act, 2016 (Pub. L. No. 114-113) and authorized by Section 1406 of the Implementing Recommendations of the 9/11 Commission Act of 2007, (Pub. L. No 110-53) (6 U.S.C. 1135). Owners and operators of transit systems apply for TSGP funds which are intended âto protect and increase the resilience of critical surface transportation infrastructure and the traveling public from acts of terrorism.â (TSGP Fact Sheet) Reviewers of applications include representatives from FEMA, DHS Office of Infrastructure Protection (IP), TSA, and FTA. Available funds are $87,000,000. Link for the main TSGP site: https://www.fema.gov/fiscal-year-2016-transit-security-grant-program 2016 Transit Security Grant Program (TSGP) Security Plan Requirements Citation. âFY 2016 TRANSIT SECURITY GRANT PROGRAM (TSGP) Security Plan Requirements,â FEMA, Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library-data/1455411216354- 30530ec96cc6eccdf07c0fb8e0e24637/FY_2016_TSGP_Security_Plan.pdf Synopsis. To be eligible for TSGP funds, the transit agencyâs security plan should include the following: âA prioritized list of all items included in the public transportation agencyâs security assessment that have not yet been addressed ⢠A detailed list of any additional capital and operational improvements identified by DHS or the public transportation agency and a certification of the public transportation agencyâs technical capacity for operating and maintaining any security equipment that may be identified in such list ⢠Specific procedures to be implemented or used by the public transportation agency in response to a terrorist attack, including evacuation and passenger communication plans and appropriate evacuation and communication measures for the elderly and individuals with disabilities ⢠A coordinated response plan that establishes procedures for appropriate interaction with state and local law enforcement agencies, emergency responders, and federal officials in order to coordinate security measures and plans for response in the event of a terrorist attack or other major incident; ⢠A strategy and timeline for conducting training under Section 1408 of the 9/11 Act ⢠Plans for providing redundant and other appropriate backup systems necessary to ensure the continued operation of critical elements of the public transportation system in the event of a terrorist attack or other major incident ⢠Plans for providing service capabilities throughout the system in the event of a terrorist attack or other major incident in the city or region which the public transportation system serves ⢠Methods to mitigate damage within a public transportation system in case of an attack on the system, including a plan for communication and coordination with emergency responders ⢠Other actions or procedures as the Secretary of
101 Homeland Security determines are appropriate to address the security of the public transportation systemâ Link for the main Transit Security Grant Program site: https://www.fema.gov/fiscal-year-2016-transit-security-grant-program Fiscal Year (FY) 2016 Transit Security Grant Program (TSGP) Notice of Funding Opportunity (NOFO) â Key Changes Citation. âFiscal Year (FY) 2016 Transit Security Grant Program (TSGP) Notice of Funding Opportunity (NOFO) â Key Changes,â FEMA, Washington, DC, 2016, [Online]. Available: http://www.fema.gov/media-library-data/1455627528293- 1f7286cb288bde4e6f0860881273f9d0/FY_2016_TSGP_Key_Changes_Final.pdf Synopsis. To ensure that agencies focus on their individual risks and threats, priority scoring groups were eliminated and replaced with three equal Funding Priority Areas: â1. Operational Activities: Training, drills/exercises, public awareness, security planning 2. Operational Deterrence: Operational Packages, Directed/Surge Patrols on Overtime 3. Capital Projects* * For capital projects only, priority consideration will be given in the following order: 1. Top Transit Asset List (TTAL) Infrastructure 2. Multi-User High-Density Key Infrastructure ⢠Tunnel Hardening ⢠High-Density Elevated Operations ⢠Multi-User High-Density Stations ⢠Hardening of supervisory control and data acquisition, other industrial control systems (ICS), or other anti- terrorism cyber security programs ⢠Sustainment/maintenance 3. Single-User High-Density Key Infrastructure ⢠Anti-terrorism security enhancement measures for high-density stations and bridges ⢠Sustainment/maintenance 4. Key Operating Asset Protection ⢠Physical hardening/security of control centers ⢠Secure stored/parked trains, engines, and buses (bus/rail yards) ⢠Maintenance facilities ⢠Bus/train hardening ⢠Sustainment/maintenance 5. Other mitigation activities ⢠Interoperable communications ⢠Anti-terrorism security enhancement measures for low-density stations ⢠Sustainment/maintenance ⢠Other uses of funds, as outlined in Public Law 110-53 Section 1406(b)(1)â Scoring criteria include ⢠Cost effectiveness ⢠Feasibility of increasing security ⢠Sustainability ⢠Timely completion ⢠Baseline assessment for security enhancement review alignment Link for the main Transit Security Grant Program site: https://www.fema.gov/fiscal-year-2016-transit-security-grant-program Transit Safety and Security Program (TSSP) Certification, Transportation Safety Institute Available: http://www.rita.dot.gov/tsi/about/transit_safety
102 Synopsis. The TSSP Certification is administered by the FTAâs Transit Safety and Security Division. The certification program provides information on the development and implementation of system safety, security, and emergency management program plans, and is targeted towards rail and bus safety and security professionals. The bus-oriented certificate requires successful completion of the following courses: ⢠Transit Rail System Safety (Learn basic rail system safety and safety management systems (SMS) principles, as well as the required elements of MAP-21 rule making and the State Safety Oversight Rule 49 CFR Part 659. Study hazard analysis and its implementation throughout the system life cycle, from planning and design, through construction, implementation of revenue service, and disposition. Explore system safety in the acquisition and operations phases, safety certification program, certifiable items list, security, and emergency response.) ⢠Transit Rail Incident Investigation (This course provides participants with the knowledge and skills to successfully investigate various types of transit incidents and comply with the requirements of State Safety Oversight Rule 40 CFR Part 659. This will be achieved utilizing the systems approach to incident investigation used by the National Transportation Safety Board. Examples are drawn from light rail, commuter rail, and heavy rail operations. The course will assist participants to better understand how the investigation process shall be used to prevent rail transit incidents and allow for successful implementation of corrective actions plans.) ⢠Transit System Security (Develop an increased knowledge of Transit System Security and how it relates to SMS. Gain new resources to reduce crime and improve customer and employee security. Learn how to use a uniform format for developing and implementing security policies and procedures through a system security plan with crime prevention as the major component. Included are basic security terms, the eight steps in the threat and vulnerability identification, and resolution process.) ⢠Effectively Managing Transit Emergencies(Nature of emergencies and disasters; emergency management concepts; Development of an emergency management plan; emergency management training.) The rail-oriented certificate requires successful completion of the following courses: ⢠Transit Bus System Safety (contains information on Threat and vulnerability analyses, Hazard identification and resolution, and Emergency/All-hazards management) ⢠Fundamentals of Bus Collision Investigation (Learn about effective tools and techniques relating to data collection, on-scene evidence documentation, damage and debris evidence analysis, witness interview techniques, computation of simple speed estimates, and report writing. Gain in-depth practical application knowledge of accident reconstruction techniques and the use of mathematical formulas to evaluate contributing factors associated with bus collisions/investigations. This course also includes and introduction to SMS principles, basic collision investigation procedures. Knowledge of high school algebra will greatly assist participants to successfully complete this course) ⢠Transit System Security ⢠Effectively Managing Transit Emergencies
103 Approved Transit Courses for Homeland Security Grants Courses approved by the Department of Homeland Security/Office of Domestic Preparedness are eligible for a Homeland Security Grant. They include the following: ⢠FT00432 â Transit System Security ⢠FT00531 â Crime Prevention Through Environmental Design (Provides system security concepts and initiatives, the three CPTED principles, and facilities design and operations planning) ⢠FT00538 â Transit System Security: Design Review (Creates a proactive impact on employee and customer safety and security in the design review process for new facilities, new starts, rehabilitation of existing facilities, or extensions to current systems) ⢠FT00463 â Transit Response to Bus Hijacking Seminar ⢠FT00456 â Effectively Managing Transit Emergencies ⢠FT00550 â Identify IED Threats to Public Transit ⢠FT00532 â Transit Response to Rail Hijacking Seminar ACRP Report 95: Integrating Community Emergency Response Teams (A-CERTS) at Airports Citation. ACRP Report 95: Integrating Community Emergency Response Teams (A-CERTS) at Airports, Transportation Research Board of the National Academies, Washington, DC, 2013. Synopsis. Airport emergency response resources are likely to become overwhelmed after a major incident. The following A-CERT team models have been successful as stopgap measures: 1. Use of airport employees who normally do not have an emergency response role 2. Use of existing outside CERT teams or recruiting outside volunteers 3. A combination of the above This report notes that A-CERT teams may be useful for a wide range of purposes which may or may not be emergency-related. They include: General â Staff family support centers. â Staff informational centers during high traffic periods such as holidays. â Provide assistance with parking, including special event parking. â Provide traffic control support. â Provide evacuation assistance by leading evacuees to marshaling points. â Assist in management of marshaling points. â Provide food and water to airport responders. â Assist first responders during special events. â Act as victims for drills and exercises. Air shows â Assist with parking and traffic control. â Assist with crowd control. â Provide first aid assistance.
104 â Provide food and water to workers. â Assist with clean-up efforts. Natural disaster response and recovery â Flooding -Provide sandbagging assistance. -Augment evacuation efforts. â Tornado -Secure loose items, aircraft, and equipment. -Augment evacuation efforts. â Earthquake response - Conduct damage assessment of airport facilities. - Provide glass and debris clean-up. Other uses include the following: Serve as training instructors for other CERT volunteers. Provide National Incident Management System (NIMS)/Incident Command System (ICS) training for airport personnel. Conduct damage assessments. Conduct perimeter/fence inspections. Conduct airport debris inspections and removal. Provide shelter management, especially shelter-in-place following flight cancellations due to storms, volcanic ash, or other hazards. Assist law enforcement in conducting bomb searches. Serve as scribes for command posts using web-based systems. Serve as observers, evaluators, or safety officers for drills and exercises. Recruit additional CERT members. Serve as tour guides for school or civic groups. Serve as drivers. Assist airport law enforcement and security personnel by serving as escorts for special events or construction projects. Provide security when airport perimeter is breached by a disaster or accident. Provide scene security assistance. Provide coordination of emergency vehicles/staging officers. Assist with triage in mass casualty events. Provide record keeping. Provide maintenance assistance (e.g., snow removal, debris removal, electrical, plumbing, heating and air conditioning). Provide Americans with Disabilities Act (ADA)-compliance assessment and recommendations. Assist with search and rescue. Provide human resources for situational long-term recovery efforts.
105 Staff phone banks. Provide communications assistance (i.e., act as runners). Provide secondary communications capabilities (e.g., amateur radio). Provide assistance with mass casualty patient transport. Coordinate untrained volunteers. Provide assistance responding to or recovering from acts of terrorism, vandalism, or criminal activity Additional details regarding an airport CERT training program is contained in the report. Also, A- CERT training manual is available via the TRB website. 2014 National Strategy for Transportation Security (NSTS) Citation. 2014 National Strategy for Transportation Security (NSTS): Report to Congress, April, 2015 DHS/TSA Synopsis. The NSTS âpresents a forward-looking, risk-based plan to protect the freedom of movement of people and goods while preserving civil rights, civil liberties, and privacy; it identifies priority objectives to enhance the security of infrastructure, conveyances, workers, travelers, and operations.â The report addresses the transportation strategic planning requirement in Section 1202(b) of the Intelligence Reform and Terrorism Prevention Act in title 49 of the U.S. Code. NSTS goals are: Goal 1: Manage risks to transportation systems from terrorist attack and enhance system resilience. Goal 2: Enhance effective domain awareness of transportation systems and threats. Goal 3: Safeguard privacy, civil liberties, and civil rights, and the freedom of movement of people and commerce. The report components include a base plan and the appended modal security plans for Aviation, Maritime, Highway and Motor Carrier, Mass Transit and Passenger Rail, Freight Rail, and Pipelines, and intermodal security plan. The base plan is structured as follows: II. Sector Risk Profile, III. Guiding Principles, IV. Sector Mission, Vision, Goals, and Objectives, V. Cross Modal Priorities, VI. Performance, VII. Roles and Responsibilities, and VIII. Challenges and Path Forward Appendices: ⢠Appendix A 2014 Aviation Security Plan ⢠Appendix B 2014 Maritime Security Plan ⢠Appendix C 2014 Surface Security Plans ⢠Appendix D 2014 Intermodal Security Plan Training and exercises receive attention in the base plan and in the modal security plans as ways to enhance preparedness, response, and recovery.
106 ⢠A priority activity in response and recovery from a terrorist attack is to âpromote participation in local security exercises to ensure public and private familiarity with plans, procedures, and capabilities.â (page 12) ⢠To address chemical and biological Threats against transit, a priority is to assure availability of response training for frontline employees. ⢠Domestic Nuclear Detection Office (DNDO) develops the Global Nuclear Detection Architecture, a framework to detect, analyze, and address nuclear and radiological threats against aviation, maritime, and land transportation modes. DNDO also has training and exercise programs to support their mission. Due to changing and emerging threats, a challenge is noted as the need for security officials to have advanced technological capabilities and continual training. Included below are highlights from the Highway and Motor Carrier, Mass Transit and Passenger Rail, and Freight Rail sections of Appendix C â 2014 Surface Security Plans. Highway and Motor Carrier Attack scenarios for highway and motor carrier include IEDs or Vehicle-Borne IEDs on critical infrastructure, small arms or IED attacks on passenger or school buses, use of trucks or vehicles with explosives or toxic materials as a weapon, and contamination of food products during transport. These scenarios led to the risk-based priority of enhancing frontline employee security training and awareness. A related programming priority is the use of I-STEP and the Exercise Information System to promote security strategies. A challenge for highway and motor carrier security is noted as the changing threats and personnel turnover which require continual updating of security training. A path forward includes transitioning the First ObserverTM program to a web-based training program and sharing of training materials and relevant information with stakeholders. Mass Transit and Passenger Rail: Based on the following mass transit and passenger rail attack scenarios: ⢠IED attacks on trains or infrastructure; ⢠Active-shooter situations; ⢠Sabotage of control systems; and, ⢠Chemical/biological attack. A risk-based priority is to promote best practices for security planning, assessments, training, and exercises. Programming priorities include establishing an exercise program to test and improve resilience and promoting use of public awareness campaigns. The use of I-STEP is cited as a way to address the challenges of increasing operational deterrence at high-risk transit stations and enhance modal resilience. The TSGP is also noted as being a priority tool for hardening assets and funding public awareness campaigns, anti-terrorism law enforcement positions, and preparedness drills and exercises. Freight Rail:
107 Freight railâs primary risk scenario includes an IED attack on hazardous materials and attacks on critical transportation system infrastructure. This scenario bolsters the following risk- based training and exercise priorities: ⢠âProvide effective training for frontline employees in security sensitive positions. ⢠Conduct effective exercises employing realistic threat scenarios that evaluate and identify opportunities to improve security and resilience.â (page 42) NCHRP Synthesis 472: FEMA and FHWA Emergency Relief Funds Reimbursements to State Departments of Transportation Citation. Nakanishi, Yuko J. and Auza, Pierre M. NCHRP Synthesis 472: FEMA and FHWA Emergency Relief Funds Reimbursements to State Departments of Transportation. Transportation Research Board of the National Academies, Washington, DC, 2015, [Online]. Available:http://onlinepubs.trb.org/onlinepubs/nchrp/nchrp_syn_472.pdf Synopsis. The Summary states that this Synthesis âfocuses on state DOT experiences and practices related to the federal disaster reimbursement programs: FHWA Emergency Relief (ER) and the FEMA Public Assistance (PA)â. The Synthesis consists of five chapters, and its case studies include ten (10) state DOTs and two (2) state emergency management agencies or offices. After an introductory Chapter 1, the report presents an overview of the FHWA and FEMA programs in Chapter 2. Chapter 3 examines the challenges and experiences of case study state DOTs with the two federal programs. In contrast, Chapter 4 compares and contrasts these state DOTs by aspects of their current practices, such as roles and responsibilities, disaster assessment practices, financial management systems, cost sharing, etc. In its Conclusion (Chapter 5), the Synthesis summarizes its findings (challenges and effective practices of state DOTs) and shares useful resources for the two federal programs. Appendix D contains detailed write-ups of each case study participant DOT. Other appendices include ⢠Presidential Declarations (Appendix B), ⢠New York State DOT Detailed Damage Inspection Report (DDIR) form instructions (Appendix E), ⢠California DOT (Caltrans) Damage Assessment Form (Appendices F and G), ⢠Vermont Agency of Transportation (VTrans) checklists (Appendix H), ⢠Louisiana Department of Transportation and Development (DOTD) emergency forms and equipment/supply checklist (Appendix I), and ⢠Public Assistance Grant Program Summary (Appendix J). Findings regarding state DOT training practices related to reimbursement programs included training of personnel including disaster inspection teams and financial personnel on FWHA ER and FEMA PA reimbursement programs and procedures. Agencies used scenarios from prior disasters to improve training. Also, the importance of training on documentation was emphasized in the Synthesis. A good understanding of effective documentation procedures including
108 NIMS/ICS procedures and forms along with other activities that streamline emergency work will help agencies recover costs in an efficient manner and meet program deadlines. Sources of FHWA ER training included FHWA Division Offices and state DOTâs FHWA ER coordinators. FHWA ER coordinators provide relevant training to state DOT personnel involved in the reimbursement process. State DOTs also provided a range of FHWA ER training to LPAs, including annual or semiannual training, training by request, and just in-time training. Examples of assistance and training provided by state DOTs are given on page 59 of the Report. In some cases, the state DOT also provides training state EMA personnel. With respect to FEMA PA training, FEMA offers an independent study (IS), Course 634: Introduction to FEMAâs Public Assistance Program, and a 4-day course at FEMAâs EMI facility in Maryland. State EMAs may also provide training and assistance to state DOTs and LPAs. State DOTs noted that they would appreciate additional training on FEMA PA and FHWA ER programs and procedures, and the funds needed to deliver such training to their staff and to LPAs. NCHRP Report 667 Model Curriculum Citation. NCHRP Report 667: Model Curriculum for Highway Safety Core Competencies, Transportation Research Board of the National Academies, Washington, DC, 2010, [Online]. Available: http://www.trb.org/Main/Blurbs/164418.aspx Synopsis. Safety workforce development is an important concern within the transportation safety community. Retirements among experienced professionals could leave a gap in the knowledge base and slow progress on building a safe and efficient transportation system. Critical to the success of any workforce development effort is ensuring a sufficient number of professionals are entering the field. In April 2002, FHWA hosted a workshop to discuss topics related to workforce development specifically for the road safety community and to identify strategies for building the supply of road safety professionals. To further the ideas and goals of the workshop, the TRB created a Joint Subcommittee on Road Safety Workforce Development to accomplish the following objectives: ⢠Raise awareness of the need for education and training opportunities for road safety professionals; ⢠Develop a set of core competencies for road safety professionals; and ⢠Encourage use of the core competencies in training and education programs, hiring decisions, performance evaluations, and professional development. This report presents a model curriculum based on the core competencies developed by the joint task force. The curriculum is named Road Safety 101 (Model Curriculum for Highway Safety Core Competencies) to highlight the fact that the course meets university standards and represents a beginning understanding of road safety as a discipline. The NCHRP funded the program in 2007, followed by a pilot test in 2008â2009 which included a blended learning environment (e.g., five webinars, several online assignments, and a three-day classroom seminar). In 2009, NCHRP
109 provided additional resources to continue pilot testing the curriculum using different learning environments (e.g., one all classroom and one online). All instructional components of this project were developed utilizing Instructional Systems Design (ISD) methodology and processes. The ISD model was designed in 1975 to solve Department of Defense training problems. It grew out of the systems analysis concepts that became popular after World War II. Today, it is the most extensively used instructional design model. A CD is attached with this report that contains the training materials including the instructor and participant guides, PowerPoint presentations and speaker notes, and other ancillary materials, such as certificate examples, an evaluation form, a participant sign in sheet, etc. Appendix A of this report provides an outline of the materials contained on the CD. Clear Roads Winter Maintenance Training Reference Materials Citation. âReference Materials: Training for Supervisors and Operators,â Clear Roads (www.clearroads.org), n.d., St. Paul, MN, [Online]. Available: http://clearroads.org/training- reviewed-modules/ Synopsis. Clear Roads pooled fund project collected winter maintenance training material (publications and course materials) from DOTs around the country. Get Ready: NIMS-Compliant Training for Public Works Citation. Bergner, David, âGet Ready: NIMS-Compliant Training for Public Works,â APWA Reporter, Jan. 2013, p.41. Synopsis. Bergner notes that Public Works is a fundamental component of emergency management as local government is expected to handle the first 72 hours of an emergency without outside aid. However, when assistance is needed, they should be able to communicate and coordinate with other emergency responders. The adoption of NIMS is a prerequisite for obtaining federal funds for response, recovery and mitigation. Unfortunately, according to Bergner, most Public Works personnel involved in emergency response (inspectors, technicians, dispatchers, mechanics, and clerks as well as field workers and supervisors) lack even basic training on NIMS and ICS. It's time for TIM: Public Works and Traffic Incident Management Citation. Bergner, David, âIt's time for TIM: Public Works and Traffic Incident Management,â APWA Reporter, Jan. 2014, p.47. Synopsis. Bergner writes that Public Works and DOTs are often needed to assist with TIM which is vital to keeping responders and the public safe and reducing unnecessary and costly congestion. Public Works/ DOTs are also needed for removal and repair of damaged pavement, structures or roadside devices, and clearing debris. In some jurisdictions the PW/DOT agency may be involved in hazmat containment or clean-up.
110 While law enforcement vehicles and fire trucks carry little, if any, temporary traffic control equipment, nearly all PW/DOT Maintenance and Operations personnel are certified in Temporary Work Zone Traffic Control, by the International Municipal Signal Association (IMSA), American Traffic Safety Services Association (ATSSA), the state LTAP or by the agency itself, and know how to establish a traffic incident management area (TIMA). Bergner states that the TIM Responder course is an excellent opportunity for all disciplines, including Public Works, to better recognize, relate to and respect each other. Bergner notes that TIM courses are available from FHWA, Emergency Responder Safety Institute (ERSI) http://learning.respondersafety.com and the I-95 Corridor Coalition. Additionally, APWAâs Emergency Management committee is revising the Highway Incident Manual at the request of the National Incident Management System Consortium (NIMSC). Expanding Role of Public Works in Emergency Management Citation. Bergner, Dave and Kimberly Vasconez, âExpanding Role of Public Works in Emergency Management,â Leadership and Management in Engineering, Vol. 12, No. 3, 2012, pp. 126-133. Synopsis. This paper examines the evolving mission of public works in emergency management. Maintenance and operations personnel of state DOTs and public works agencies are vital in the response and recovery phases of disasters and other emergencies, and assist with rescue, evacuation, and sheltering and provide temporary traffic control, perimeter security, animal control, transportation of supplies and equipment, onsite vehicle service, debris management, and restoration of infrastructure. The convergence of all-hazards emergency management and TIM in recent years means that public works has a different role in planning and preparing for and responding to disasters and events. The profusion of laws, mandates, and programs and the rapidly evolving body of training and knowledge can make staying abreast of these changes overwhelming. The Incident Command System (ICS) and Winter Operations Citation. Bergner, Dave, âThe Incident Command System and Winter Operations,â APWA Reporter, Jan. 2013, p.36. Synopsis. Public works agencies need to incorporate ICS concepts and formats into their winter weather operations. Winter weather operations is a very significant function of local Public Works departments and state DOTs. Even a slight amount of snow and ice on our transportations systems has detrimental impact. Because every Public Works department is unique as to size, structure, scope of services and systems, winter operations plans should be adaptable as well. ICS can be adapted and modified to the individual agency and a particular situation. The Role of Public Works in Traffic Incident Management and Other Emergencies and Disasters
111 Citation. Bergner, Dave, âThe Role of Public Works In Traffic Incident Management And Other Emergencies And Disasters,â Submitted for publication in the Journal of Public Works and Infrastructure, Vol. 2, August 12, 2014, 17 pp. Synopsis. Emergency Management has now become a vital Public Works function in the United States since the terrorist attacks of September 11, 2001, and Hurricane Katrina in August 2005. Public Works departments then must be more proactive in recognition of their enhanced role including its federal designation as a âfirst responder.â Another aspect involving emergencies is Traffic Incident Management. Public works/ transportation personnel are involved in responding to traffic incidents of all types. Many of the policies, procedures, and protocols for responding to traffic incidents are useful for other planned and unplanned events, including the larger disasters. National Fire Protection Association (NFPA) Available: http://www.nfpa.org/ The NFPA offers resources on codes, standards, guidance and training on fire, electrical, and related hazards. Occupational Safety and Health Administration (OSHA) Available: www.osha.gov As described on its website, the Occupational Safety and Health Act of 1970 created the OSHA âto assure safe and healthful working conditions for working men and women by setting and enforcing standards and by providing training, outreach, education and assistance.â OSHA standards address workplace hazards including working with hazardous materials, personal protective equipment, fire protection, fall protection, and bloodborne pathogens and provides various training resources.
