1
Introduction
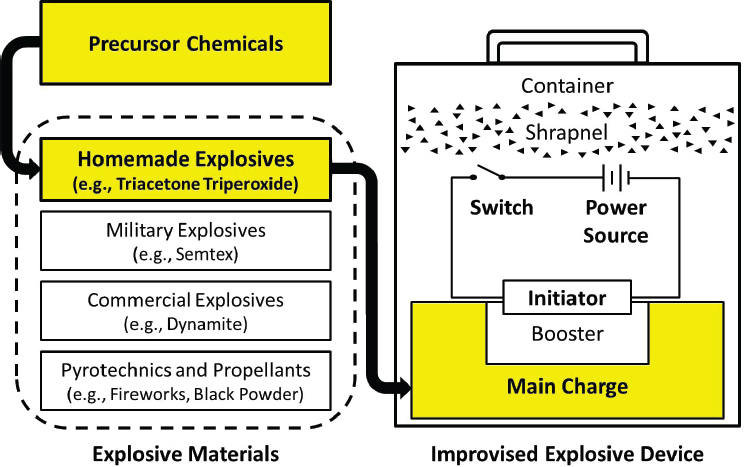
An improvised explosive device (IED), as defined in this report, is “a device placed or fabricated in an improvised manner incorporating destructive, lethal, noxious, pyrotechnic or incendiary chemicals and designed to destroy, incapacitate, harass or distract. It may incorporate military stores, but is normally devised from non-military components.”1,2 IEDs can vary widely in size, but most have at least four components: a power source, an initiator, a main charge, and a switch (see Figure 1-1). In addition, an IED can employ a casing or container, a booster, and added fragmentation or shrapnel, such as nails or screws. None of the four core components are difficult to obtain, and some, such as batteries, switches, and even certain explosive materials, are ubiquitous. The main charge can include homemade, military, or commercial explosives, or pyrotechnics and propellants (see Figure 1-1).
While most explosives incidents reported in the United States involve commercial explosives (e.g., dynamite) or pyrotechnics (e.g., fireworks, flash powder) and propellants (e.g., black and smokeless powders),3 there are also consistent reports of homemade explosives (HMEs) derived from precursor chemicals. HMEs are defined in this study (based on United Nations [UN] literature1) as explosives produced from precursor chemicals either physically blended or combined in a chemical reaction.
The United States has not experienced an attack with a large-scale IED since the truck bombings of the World Trade Center in New York City in 1993 and the Alfred P. Murrah Federal Building in Oklahoma City in 1995, but more-recent attacks with smaller-scale IEDs, including the bombings in Boston (2013) and New York and New Jersey (2016), starkly demonstrate the ongoing threat of IEDs, even if all did not employ HMEs. The Boston attack, which involved
pyrotechnic filler, resulted in three deaths and more than 260 injuries, and millions of dollars in economic losses.4
Twenty years after the Oklahoma City bombing, the ingredients, components, and instructions for producing IEDs remain accessible to terrorists, violent extremists, and criminals—collectively referred to in this report as malicious actors—who are intent on inflicting casualties,5 damaging critical infrastructure,6 and eliciting fear. Instructional videos and how-to guides for making IEDs are readily available and transmitted via the internet and in-person meetings between would-be bombers and their mentors are facilitated using modern telecommunications and global travel.7 Precursor chemicals can be obtained legally from brick-and-mortar retailers (e.g., hardware, drug, and garden supply stores) or online, because of their widespread legitimate uses. IED attacks in France,8 Belgium,9 and the United Kingdom10 provide further evidence of IEDs’ global relevance. Criminal enterprises and homegrown extremists may use IEDs less frequently in the United States than elsewhere in the world, but the consequences can be serious.
CHARGE TO THE COMMITTEE AND INTERPRETATION OF SCOPE
At the request of the U.S. Department of Homeland Security (DHS), the National Academies of Sciences, Engineering, and Medicine (the National Academies) assembled an ad hoc committee to identify and prioritize a list of precursor chemicals that have been used or are susceptible for use in IEDs in the United States or internationally; to analyze the movement of priority precursor chemicals through commercial supply chains and identify potential vulnerabilities; and to suggest control strategies, in light of current U.S. and international policy and the various tradeoffs among mandatory and voluntary approaches (Box 1-1).11 As a consequence, the focus of this report is not on the threat of IED attacks overall, but on the accessibility of precursor chemicals to malicious actors.
The committee was directed to focus its assessment solely on precursor chemicals used to make HMEs, but recognizes that a significant number of incidents in the United States used commercial explosives and smokeless, black, and flash powders and pyrotechnic fillers applied as the explosive materials in IEDs (see Chapter 2).3 Thus, no strategy for restricting access to precursor chemicals can eliminate the threat of IED attacks as long as these other explosive materials remain accessible.
The committee prioritized precursors from an expansive list of chemicals (see Chapter 2 for more details), examined all levels of the chemicals’ supply chains for potential vulnerabilities, explored domestic and international policy for insight, and considered security, economic, and other tradeoffs among strategies featuring different combinations of mandatory and voluntary policy mechanisms. Cognizant of the importance of preserving legitimate commerce and use, the committee explored the possibility of strategies that could include new mandatory restrictions on access to precursor chemicals, but it did not presume the necessity of new mandatory restrictions. It also considered other measures and activities, including outreach, training, and reporting, that could supplement new restrictions or be applied independently. Such measures and activities could operate through government channels, industry-led initiatives, or both, under legal mandates or through voluntary participation.
Box 1-2 describes the use of IEDs by terrorist networks. The statement of task pertains to HMEs, specifically the precursor chemicals used to make them, and to concerns that are embedded in the highlighted boxes—labeled Gather and Provide Resources and Improvise Concepts of Operations, Tactics, and Devices—in the threat chain depicted in Figure 1-2. On the basis of the committee’s limited focus on precursor chemicals, and given the prevalence of alternative explosive materials (such as propellants and pyrotechnics) in domestic incidents involving explosives (see Chapter 2), the strategies under consideration in this report might play a part in reducing the likelihood of malicious actors gaining access to precursor chemicals, but cannot be expected to prevent all malicious actors from manufacturing IEDs or taking other harmful actions.
STUDY ORIGINS
Shortly after the World Trade Center and Oklahoma City bombings, Congress mandated a broad study of issues related to detecting, rendering inert, and licensing precursor chemicals and explosives, which was undertaken by the Academies’ Committee on Marking, Rendering Inert, and Licensing of Explosive Materials.13,14 That effort, which focused on precursor chemicals used primarily to produce HMEs for the main charges in large-scale IEDs, consistent with those attacks, yielded the following results that are of particular relevance to the present study:
- a prioritized list of precursors based on availability and criticality in building an effective IED, with the highest priority chemicals including ammonium nitrate, nitromethane, sodium nitrate, potassium nitrate, sodium chlorate, potassium chlorate, potassium perchlorate, nitric acid, and hydrogen peroxide;
- a recommendation to include procedures to easily amend the precursor list based on ongoing threat assessments given that bombing tactics will change over time;
- recommendations for controlling the prioritized materials based on the perceived threat level—ranging from status quo to greatly increased—through increased awareness, record keeping, licensing, adulteration, or banning; and
- a recommendation for further analysis of the costs of possible actions prior to implementation of any controls and with full participation of affected industries.
In the intervening decades, concerns about the use of IEDs in terrorist attacks have contributed to or driven regulatory action in the United States and abroad (see Figure 1-3).15-17 The United States (see Chapter 3) and other countries (see Chapter 4) have taken different approaches, with the subjects of concern ranging from high-volume commerce to small, individual transactions.
In 2007, Congress mandated that DHS implement the Chemical Facility Anti-Terrorism Standards (CFATS) program, which identifies and regulates high-risk chemical facilities to ensure they have security measures in place to guard against theft and public health hazards.17,18 CFATS focuses entirely on facilities and storage and does not cover chemicals in transport. Some of the precursor chemicals that are controlled under CFATS, and the justification for their presence, resulted from the inclusion of the chemicals on the short list that was recommended by the 1998 committee.14
In 2008, Congress mandated the expansion of security controls to ammonium nitrate (AN), and DHS proposed supporting regulatory action.19-21 AN, which has a legitimate role in agricultural, industrial, and other applications, has gained notoriety in the United States and internationally for its use in bombings with large-scale IEDs, including those employed in the bombing of Sterling Hall at the University of Wisconsin22 in 1970, which was the first major domestic incident to employ HMEs, and later in Oklahoma City.23 In 2011, a Norwegian extremist acquired AN under the pretense of agricultural use and employed it in an explosion that killed eight and injured more than 200 in Oslo.24 Some countries, including Northern Ireland25 and Turkey,26 have banned AN from their markets. The proposed U.S. Ammonium Nitrate Security Program (Box 1-3) would introduce a registration regime throughout the United States’ supply chain and set requirements for transactions, but efforts to complete the rulemaking process have been under contention for almost a decade.
It is difficult to make concrete conclusions on the global use of HMEs because the available data are sparse and lexicons are inconsistent. The 2015 U.S. Bomb Data Center (USBDC) report on explosives incidents indicates use of—or intent to use—military explosives, commercial blasting agents, commercial pyrotechnics and propellants, and a variety of HMEs (Box 1-4).3 AN is just one of several precursor chemicals that have been used in IEDs.
In 2014, European Union (EU) Regulation No 98/2013 entered into force throughout the EU with a goal of enhancing protections to citizens from the
threat of terrorism.28 It introduced a common framework for controlling access to, introducing, and possessing and using certain substances or mixtures that could be used to make HMEs. Members of the general public have restricted access to and use of the chemicals listed in Annex I of the regulation. The regulatory default is a ban on sales to the general public, but any of the 28 EU member states (MS) may grant access through licenses or registration. In addition, the regulation also introduces rules for retailers who market such substances (see Chapter 4).
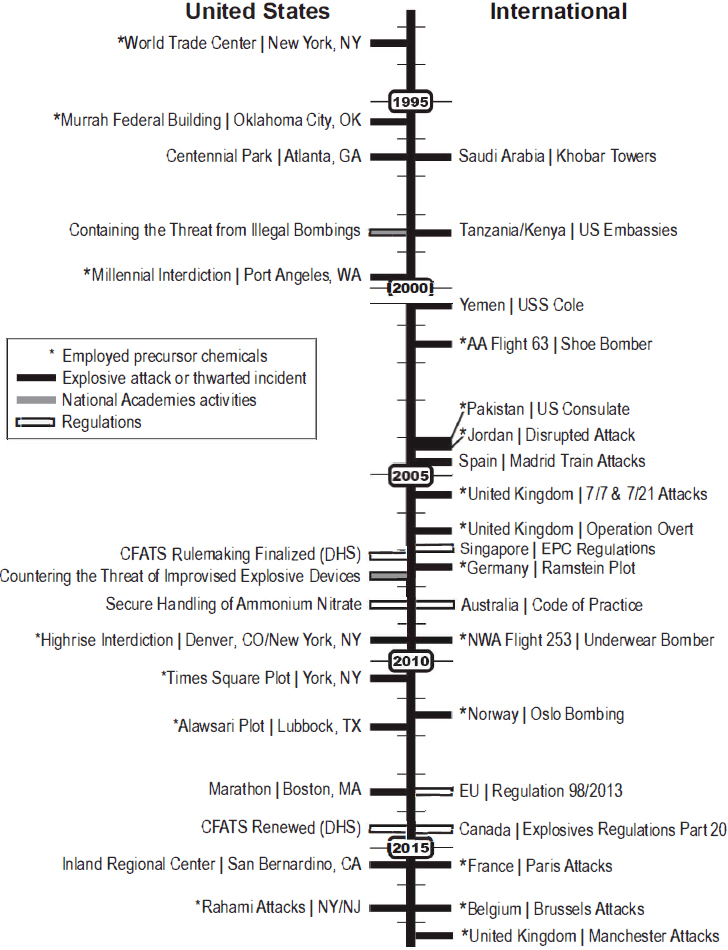
The charge to the committee appears to flow naturally from past events and policy developments, both in the United States and internationally. Although the statement of task focuses on a single dimension of the threat of IED attacks, namely access to precursor chemicals, it does so comprehensively, seemingly reflective of past and ongoing efforts to increase security.
ANALYTICAL APPROACH
History, including that of IED attacks, suggests that a push for a policy response—from the public and from government officials—often follows a crisis, but event-driven policy making based on spontaneous intuitive thinking might
yield less desirable outcomes than policy making based on slower-paced deliberative thinking.29,30 The former tends to be myopic, to operate rapidly, automatically, and effortlessly, and to emphasize simple associations, including emotional reactions, recent past experience, and simple decision rules. The latter allocates attention to effortful and intentional mental activities, in which individuals weigh tradeoffs and recognize relevance, interconnectedness, and the need for coordination, and focuses on long-term strategies for coping with extreme events. Adding to the challenges of making policy in a crisis-ridden environment is the potential for an overreaction to fearsome risk or action bias: when the prospect of a loss triggers strong emotions, people tend to neglect the probability of an event and exaggerate the benefits of preventative, risk-reducing, or ameliorative measures.31
This report provides policy makers with a framework, tools, and information to encourage deliberative thinking, such as that undertaken by this committee, before crises occur and to discourage intuitive thinking and action bias during
and after crises. Even if event-driven policy making is unavoidable, it might be possible to lay a foundation for better policy responses, so that in-the-moment decision-making can look more like thoughtful decision-making.
Framework and Tools
In this report, the committee attempts to identify (1) conditions under which malicious actors can legally or illegally obtain particular precursor chemicals to produce HMEs that are used to construct IEDs, both large and small, and (2) the means of reducing the likelihood that these precursor chemicals could fall into the wrong hands, for use in terrorist attacks. The committee’s framework for considering supply chains, policy, potential vulnerabilities, and control strategies follows a logical progression, consistent with the statement of task. It starts, in Chapter 2, with a winnowing process by which the committee identified a short list of precursor chemicals of particular concern. After grouping the list of chemicals by priority, it then, in Chapters 3–5, does the following:
- constructs supply chains for the highest priority precursor chemicals;
- characterizes the policy mechanisms pertaining to those chemicals and analogous policies;
- maps out the policy mechanisms in relation to the supply chains to identify potential vulnerabilities;
- examines the design and implementation of international policies on precursor chemicals for insight to possible control strategies; and
- identifies and assesses the tradeoffs among potential control strategies.
In the course of its deliberations, the committee drew implicitly and explicitly from tools of risk management and regulatory assessment (see Appendices B and G).
The committee conceptualized risk in terms of a threatening or hazardous condition, the resulting consequences that can arise from the threat or hazard, and the probability and severity of those consequences. Thus, one might observe that DHS’s statement of task speaks largely to probability through the initial likelihood that malicious actors will be able to obtain precursor chemicals. The national security literature provides a simple tool—a matrix that juxtaposes probability and severity—for assessing and prioritizing risk as part of a five-step risk management process (see Appendix B, Figures B-1 and B-3).32,33 The process calls on the policy community to identify hazards; assess probability and severity; develop controls or other policy mechanisms to mitigate risks; implement policy; and supervise, review, and evaluate, continuously.
To develop controls or other policy mechanisms, the same literature indicates that policy makers should balance risk against costs. Taking a step in that direction, the committee considered tradeoffs among security, economic, and other
factors associated with a small set of potential strategies for addressing access to precursor chemicals (see Chapter 5), drawing notionally from principles of regulatory assessment, including those of benefit-cost analysis. Given the limitations on the time, resources, and scope of this project, including access to reliable bombing data, the committee did not undertake a full, formal analysis; rather it presents the results of the qualitative, analytical exercise with which it explored the benefits, costs, and uncertainties of alternative strategies.
Data Gathering
To support its deliberations, the committee gathered information from experts and stakeholders from government agencies, industry (including trade associations), and academia. A list of those experts and stakeholders can be found in the Acknowledgments. Information on the movement of specific chemicals through the supply chain and related policy mechanisms was presented or provided directly to the committee during one of several data-gathering meetings and in follow-up communications. The committee’s discussions with agencies, groups, and individuals concerned with precursor chemicals were extremely valuable. Additionally, the committee chair, a committee member, and a staff officer conducted a site visit in April 2017 to the European Commission in Brussels, Belgium, and to the United Kingdom’s Home Office in London, England, to learn more about international policy on precursor chemicals and opportunities for risk mitigation. The committee sourced additional references from public documents, including the scientific literature and government reports, but no controlled or classified materials were used to construct any aspect of the report.
Definitions
Many terms used in this report lack universally agreed-upon definitions. For the purposes of this report, the committee sets out its use of some terms that appear across chapters.
The committee defined improvised explosive device (IED) as “A device placed or fabricated in an improvised manner incorporating destructive, lethal, noxious, pyrotechnic or incendiary chemicals and designed to destroy, incapacitate, harass or distract. It may incorporate military stores, but is normally devised from non-military components.”1,2
The committee defined homemade explosives (HMEs) as explosives produced from precursor chemicals either physically blended or combined in a chemical reaction.
The committee defined precursor chemicals as chemicals that can be used, through blending or chemical reaction, to produce HMEs.
The committee addresses vulnerabilities in relation to the potential for un-
explained loss, diversion, theft, and other forms of misappropriation along commercial supply chains.
The committee uses the term displacement to describe policy-induced shifts in terrorists’ strategies and tactics. For example, if a policy interferes with terrorists’ access to certain precursor chemicals, they might shift from one precursor chemical to another, from HMEs to other forms of explosive materials, or from IEDs to entirely different methods of attack.
The committee uses the term mandatory to describe policy mechanisms that are prescribed in and enforceable under federal, state, or local law or ordinance and the term voluntary to describe policy mechanisms that lack the same legal basis and force. Mandates, at whatever level of government, often or even typically involve corresponding regulatory action.
The committee reserves the term control for mandatory restrictions on access to precursor chemicals. The terms measure and activity are applied more broadly, to encompass policy mechanisms, such as outreach, training, or reporting, which could be set up under mandates or through voluntary participation, depending on the specific circumstances under consideration. Similarly, the committee also uses the term policy intervention broadly.
The committee uses the term control strategy to refer to a package of policy mechanisms that can consist of different combinations of new controls, existing controls, and additional measures and activities, each as defined above. On that basis, a strategy for restricting access to precursor chemicals and reducing the likelihood that terrorists will gain access to them would include some form of control, be it a new control, existing controls, or both, but it could take a hybrid approach, by also including a mix of additional mandatory and voluntary policy mechanisms.
ORGANIZATION OF THE REPORT
Chapter 2 discusses the precursor chemicals that can be used for IEDs, the means by which the committee developed a short list of chemicals of particular concern, and the criteria that the committee used to prioritize the chemicals on the short list. Specifically, it discusses whether a chemical lends itself to producing large-scale vehicle-borne IEDs (VBIEDs), smaller-scale person-borne IEDs (PBIEDs), or both; the history of or potential for use of a precursor; and the independence or dependence of a chemical’s role in synthesis, defined as the utility of the chemical in the absence of others. The chapter concludes by categorizing the short list of chemicals into three groups (Groups A, B, and C), with Group A being the highest priority and the primary focus of the in-depth supply chain analysis.
Chapter 3 examines how the precursor chemicals flow from import or manufacturer to end user and characterizes the policy mechanisms that pertain to those precursor chemicals. It uses a generalized supply chain diagram, derived
from a series of chemical-specific diagrams (Appendix D), that maps out the common nodes, such as factories, commercial distributors, and retailers. It then presents an overlay of existing policy mechanisms (mandatory and voluntary) and discusses them pursuant to their impact on access to the precursor chemicals. The chapter ends with an assessment of the potential vulnerabilities of the supply chains, defined in terms of susceptibility to unexplained loss, diversion, theft, or other misappropriation, by identifying those nodes with relatively low levels of visibility and oversight.
Chapter 4 reviews international policy on precursor chemicals. Locations of focus include Australia, Canada, Singapore, and the EU (with additional focus on the United Kingdom’s implementation strategy). The committee turned to international policy for creative solutions to the potential vulnerabilities that it found in the U.S. supply chain.
Chapter 5 draws from each of the foregoing chapters to introduce a set of possible control strategies, consisting of different combinations of controls and other mandatory and voluntary policy mechanisms, and presents the results of a qualitative assessment of tradeoffs among the strategies. A strategy could include a new control, as defined, or it could supplement existing controls with other measures and activities, subject to varying degrees of government involvement and oversight. Chapter 5 considers the tradeoffs among strategies qualitatively, largely in terms of potential benefits and costs, relative to specific policy objectives, namely restricting access to precursor chemicals, gathering information, and minimizing burdens on legitimate commerce and use.
Chapter 6 presents recommendations and suggestions to stakeholders that oversee or have an interest in the manufacture, transport, sale, or use of precursor chemicals, based on the committee’s deliberations and assessment. While these suggestions focus on control strategies to mitigate potential vulnerabilities in the U.S. supply chain, primarily at the retail level, the chapter also highlights other opportunities that came to the fore over the course of the project.














